Abstract
A think-globally-act-locally (TGAL) technique is proven to be an effective method to address the state explosion issue for complex discrete event systems modeled with Petri nets. This paper introduces a TGAL-based method for computing and analyzing the reachability graph (RG) of Petri net models. Given a net system, the TGAL technique strategically introduces a global idle place (GIP) to iteratively generate its RG by updating the token count. At each step, the reachable markings (RMs) and legal markings (LMs) obtained by the previous iterations are considered to calculate the corresponding states of the current step. According to the enforced control requirement, a system state is required to be computed and classified only once during an iterative process. This method only calculates the necessary number of RMs and reduces computational redundancy, which minimizes the computational cost. Four typical Petri net models from existing studies are employed to demonstrate the method.
Keywords:
discrete event system; Petri net; reachability graph analysis; think-globally-act-locally approach MSC:
93C65
1. Introduction
Discrete event systems (DESs) are event-driven systems with discrete-states that evolve with the occurrences of discrete events. For DESs, supervisory control techniques are employed to restrict their behavior to implement the various control requirements [1,2,3,4]. As a graphical tool for the effective modeling and investigating of complex systems, Petri nets play a vital role in the field of supervisory control of DESs. A large number of supervisory control policies have been proposed for DESs modeled with Petri nets [5,6,7,8,9,10].
In the context of Petri nets, supervisory control techniques are categorized into two groups: structural analysis [11,12] and reachability graph (RG) analysis [13]. In general, structural analysis methods are usually available for certain Petri net models with special structures, namely, siphons and resource circuits [12]. Unlike structural analysis methods, an RG analysis approach can enforce the desired control requirement for a generalized net model. Nevertheless, an RG analysis method has to enumerate and classify all reachable markings (RMs) of a net system, which grow exponentially with the scale of the system [14]. It limits the application of RG analysis methods to complex systems. Consequently, deciding how to completely calculate the RG of large-scale systems becomes the key to the effective utilization of these methods [15,16,17].
Generally, the RG calculation depends on three factors: next-state function, iterative strategies, and variable ordering. In [18], a symbolic method is developed to implicitly generate the RMs of bounded Petri net systems. By utilizing a binary decision diagram (BDD), this method compresses a large number of RMs into encoded data with small structures and accurately manipulates RMs. However, the effectiveness of this method is highly dependent on the ordering of variables. Furthermore, Chen et al. introduce a BDD-based technique to generate the RG of a net system [19]. Given a deadlock-free control specification for a net system, its RMs are classified into two groups: legal markings (LMs) and illegal markings (ILMs). They first compute the sets of LMs and first-met bad markings (FBMs), where an FBM is an ILM reached by triggering a transition at an LM. Then, two minimal covering sets of LMs and FBMs are obtained to compute an optimal supervisor. As a result, this method is more powerful for generating RGs of complex net models than those traditional techniques in [18,20,21].
In order to mitigate the state explosion issue, Ma et al. develop a compact representation of the RG, referred to as a basis RG (BRG) [22]. This method distinguishes between the transitions of a net system as either implicit or explicit, where the subnet induced by implicit transitions needs to be acyclic. By only considering explicit transitions, a set of basis markings is calculated to construct the corresponding BRG, which can efficiently represent all RMs of a net system. In general, the BRG has a small number of nodes and arcs since the number of RMs is much larger than that of basis markings. In [23], an effective methodology is proposed to generate the RMs for a large-sized net system, by using multi-valued decision diagrams (MDDs). This method can generate the RMs concurrently and compactly store the set of RMs. Consequently, it is more efficient than the techniques based on the RG and the BRG.
On the other hand, a think-globally-act-locally (TGAL) technique is developed by Uzam et al. in [24]. This method strategically designs a global idle place (GIP) to enumerate the RG of a net system iteratively. The introduction of the GIP will not change any basic property of the net model. Due to the limitation of the available resources in the GIP, the corresponding net model has a small number of RMs at each iteration. It is obvious that this method mitigates the state explosion issue for a complex system. Furthermore, in order to construct monitors with weighted arcs, a think-globally-act-locally approach with weighted arcs (TGALW) is proposed in [25]. They transform a Petri net model into a special form, which has the isomorphic RG to the original net system. In theory, this method has the same complexity as the TGAL approach in terms of the RG computation.
Similarly, a number of TGAL-based methods for optimal control of a net system are proposed in [26,27]. At each iteration, these methods generate and analyze the RG of the corresponding net system. A set of optimal control places is calculated during an iterative process. Compared with the previous TGAL [24] and TGALW [25] approaches, these methods guarantee the resulting net system with more RMs. Nevertheless, the existing TGAL-based approaches suffer from the problem of repeated calculation. First, the computation of previously derived RMs is reiterated in subsequent iterations. Then, the analysis of previously classified RMs is reiterated in subsequent iterations. As a consequence, these methods cause a huge waste of computing power.
This paper introduces a TGAL-based approach to compute and analyze the RG of a Petri net system. Compared with the previous TGAL-based methods [24,25,26,27], the proposed method calculates and analyzes a minimized number of RMs. This means that this method is more advantageous in terms of computational cost. Moreover, compared with the approaches in [24,25,26,27], the proposed method takes less time to calculate the RG of a net model, i.e., its performance is better in terms of computation time. Ultimately, the primary contributions of this study are presented in the following.
- (1)
- A TGAL-based approach is developed to compute the RG of a net system. At each step, by considering the previously computed states, the partial RMs of the corresponding net model are directly obtained. Then, the enabled transitions of the obtained states are analyzed to generate the remaining RMs of the corresponding net model. It is obvious that all RMs calculated at the current step are new states. Finally, its complete RG is derived through iterations. In this case, all nodes of the RG are required to be enumerated only once during an iteration.
- (2)
- A TGAL-based method is proposed to explore the RG of a net system. The TGAL method only updates the token count in the GIP at each step, which will not change the legal performance of a state. The previously obtained LMs are still legal for subsequent iterations, i.e., analyzing all RMs at the next step is unnecessary. At each iteration, according to the previously computed LMs, the newly generated states are classified. Finally, the complete RG of the net system is analyzed iteratively.
The remainder of this paper is structured as follows. In Section 2, a TGAL-based policy is provided to generate and analyze the RG of a Petri net system. Section 3 presents several net systems to demonstrate the proposed technique. Ultimately, Section 4 provides a summary of this work and outlines potential directions for future research. Appendix A provides a descriptionof Petri nets [28] and an analysis of the RG [27].
2. Computation and Analysis of an RG
This section proposes a TGAL-based method to generate and classify the RMs of a Petri net model. Given a net system , the TGAL approach introduces a GIP into the net system , where , T, F, . The net system with is represented as , where , (), and for all , . Initially, the GIP has one token, i.e., a net is generated to calculate its RG. Next, one token adds to to analyze a net model . This iterative process continues until the number of RMs does not change by increasing tokens in . In such a case, all RMs of the net system are enumerated iteratively. Suppose that M and are RMs for and , respectively, where . For markings M and , the following definition is obtained.
Definition 1.
Let and be two net systems, and M and be two RMs for and , respectively, where . Markings M and are referred to as N-identical if for all , holds, which is represented as .
By Definition 1, and are obtained if M and are N-identical markings, where . Obviously, markings M and signify the same state of a system. In such a case, M and are required to be computed only once during an iteration. If has already been obtained, M is generated by only changing the token count in . In this case, the partial RMs of the net are yielded directly if all markings of the net are known, where .
Example 1.
We assume and to be two RMs obtained during an iteration. By Definition 1, M and are N-identical markings due to . In this case, can be computed by only increasing the token count in for M. Markings M and correspond to the same state of a system.
Then, the RMs of are analyzed to further calculate the RMs of the next step, namely, a net , where . Suppose that M is an RM that is computed in the -th iteration and the enabled transition at M is t. In the b-th iteration, transition t may be enabled at , where M and denote N-identical markings and . In this case, firing t at yields an RM, which must be a new state of the system obtained at the b-th step. Consequently, the newly enabled transitions are considered to compute a set of RMs in the b-th iteration. We use to represent the set of transitions enabled at marking M, defined as . Assume that is the set of RMs for and represents the set of enabled transitions, where . Algorithm 1 presents a TGAL-based approach to generate the RMs of a net system .
| Algorithm 1 Computation of RMs for a net model |
|
In Algorithm 1, a part of RMs for the net () can be directly obtained by considering the markings in , that is, the token count in the GIP is increased by one for a marking in . Then, the remaining RMs of are computed by utilizing the previously generated markings. Finally, we enumerate all RMs in .
Example 2.
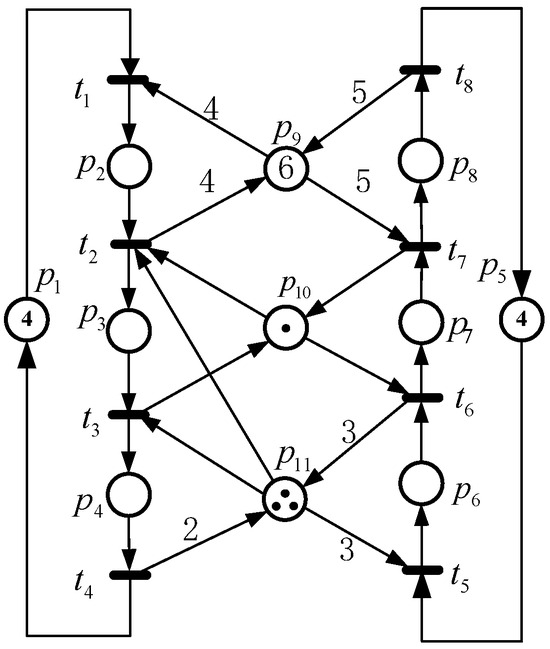
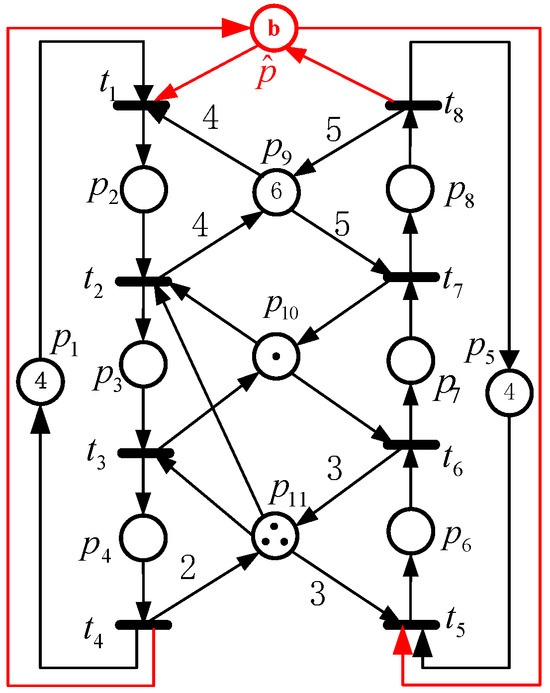
A net system depicted in Figure 1 is considered. By introducing a GIP , the corresponding net shown in Figure 2 is constructed, where b represents the token count in . When , we derive a net system . There is a marking for . At M, we have the set of enabled transitions . By Algorithm 1, an RM is generated directly for a net system (i.e., ). Similarly, at , , is calculated. We have . It is clear that firing at generates a new marking . Meanwhile, by analyzing , an RM is obtained for . Finally, this method enumerates all RMs of .

Figure 1.
A net system from [14].

Figure 2.
A net system .
For an optimal control requirement, the RMs in are required to be classified into LMs and ILMs. We suppose M and to be two N-identical markings for and , respectively, where . According to Definition 1, M and represent the same state of a system. At each iteration, the control requirement of the system will not be changed over time. The legality of marking M is independent of the token count in the GIP . We only need to analyze M for to determine whether is legal or not for . As a consequence, at each iteration, the sets of LMs and ILMs can be computed by considering the previously partitioned states. The following propositions are obtained.
Proposition 1.
Let M and be two N-identical markings for and , respectively, where . Then, M is legal (resp. illegal) for if and only if is an LM (resp. an ILM) for .
Proof.
Given a net system , a net model is constructed by adding a GIP , where b represents the token count in . We suppose M and to be N-identical markings for and , respectively, where . According to Definition 1, M and denote the same marking of the net system . Given a control specification, marking has only two cases: legal and illegal. Compared with , markings M and have a different number of tokens in . Nevertheless, only changing the token count in will not lead to the reallocation of the system resources. This means that M and are LMs (resp. ILMs) for and , respectively, if and only if is legal (resp. illegal) for . In this case, whether M is legal for can be directly determined by checking for . That is to say, M is legal (resp. illegal) for if and only if is an LM (resp. an ILM) for . Finally, the conclusion is true. □
Proposition 2.
A marking is legal if there is an LM M such that holds, where σ is a transition sequence.
Proof.
Since M is an LM, there is at least a transition sequence from M to the initial marking . Suppose that there is a transition sequence such that holds. In such a case, we have and , where . By the definition of LMs, marking is legal, which completes the proof. □
Suppose that is a set of RMs for the net and is a set of LMs for the net , where . According to Propositions 1 and 2, Algorithm 2 is proposed to calculate LMs and ILMs of a net system .
| Algorithm 2 Calculation of LMs and ILMs for a net model |
|
By considering the states in , Algorithm 2 first computes a part of the LMs and adds them into the set . Then, is obtained. A marking is selected to determine whether it is legal or not, if a marking that meets , M is an LM and is obtained, where is a transition sequence. By analyzing each marking in , a set of LMs is figured out from . Meanwhile, a set of ILMs for the net is computed with .
Example 3.
Continue to consider the net system depicted in Figure 2. When , a net system is obtained, which has an LM . By Algorithm 2, is an LM for a net system (namely, ). At the same time, marking is legal since there is transition such that holds. Finally, this method partitions the RMs for into a set of LMs and a set of ILMs.
Finally, a TGAL-based technique is introduced to generate and classify the RMs for a Petri net model, as presented in Algorithm 3.
| Algorithm 3 Analysis of RG for a net system |
|
Algorithm 3 first constructs a GIP for a net system and denotes the corresponding net as , where b () represents the token count in . Initially, the token count in is one, namely, . For a net system , we calculate the set of RMs . According to the control requirement, the markings in are considered to derive a set of LMs and a set of ILMs . Then, one token adds to , i.e., a net () is generated. By the markings in , Algorithm 1 computes the set of RMs for . Meanwhile, based on the LMs in , the sets of LMs and ILMs for are calculated utilizing Algorithm 2. We terminate this process if the number of RMs does not grow with the increase in the tokens in . Finally, the sets of RMs, LMs, and ILMs for the original net system are obtained iteratively.
Next, the complexity of Algorithm 3 is reviewed. This approach is still necessary to enumerate all of the RMs of a system. It is obvious that the number of RMs increases exponentially as the scale of the net system grows, i.e., the proposed method exhibits exponential complexity in theory. Nevertheless, this method can effectively alleviate the state explosion issue, as only a small number of new RMs are generated at each iteration. Compared with the previous TGAL-based methods [24,25,26,27], it greatly reduces the repeated calculations of a marking, that is, each marking of the system needs to be computed and classified only once. Consequently, it has more advantages in terms of computation time.
Example 4.

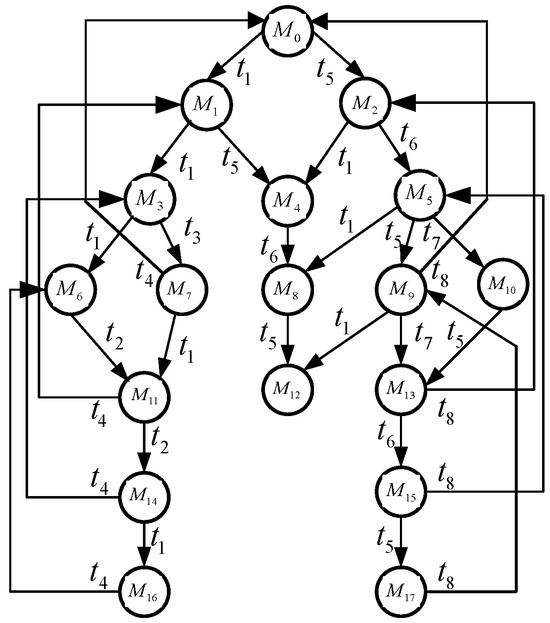

We continue to analyze the net system depicted in Figure 1. By Algorithm 3, a set of RMs is computed iteratively, which contains 18 markings. Then, the RMs are partitioned into LMs and ILMs. Table 1 presents iteration steps, where the first column indicates the iteration count and the second column is the RM count computed at the b-th step. The counts of LMs and ILMs are given in the third and fourth columns, respectively, and the last column signifies the calculation time. Since the net system only has 18 RMs, the computation time of each step is close to zero seconds. Figure 3 shows the obtained RG, where , , , , , , and are generated at the first iteration (namely, ). When , , , , , , , , and are computed. At the third step (i.e., ), we obtain markings , , and . Table 2 gives the details of RMs in the RG.

Table 1.
Iteration steps of the net system depicted in Figure 1.

Figure 3.
RG of the net shown in Figure 1.

Table 2.
RMs of the net system shown in Figure 1.
3. Examples
In this section, we utilize some typical net systems of FMSs to demonstrate the proposed method. We design C++ programs to generate the sets of RMs, LMs, and ILMs for a net model. In this work, all of the computations for these examples were performed on a computer running Windows 11, equipped with an Intel Core 2.8 GHz CPU and 16GB of memory.
First, a net system depicted in Figure 4 is selected, which is from the literature [29].
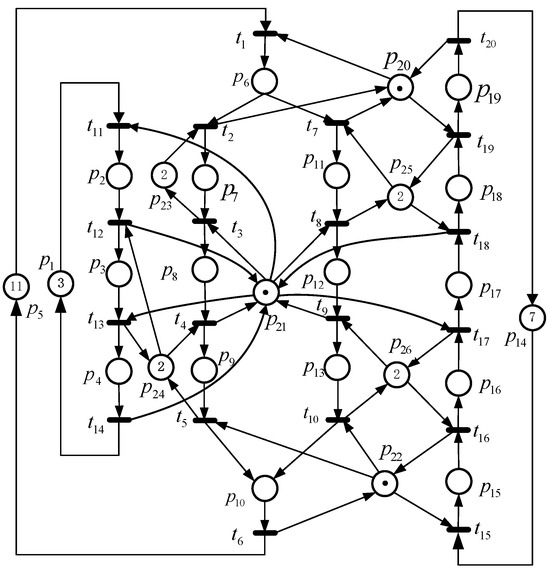
Figure 4.
A net system from [29].
This net system contains 26,750 RMs, of which 21,581 and 5169 are LMs and ILMs, respectively. We utilize the proposed technique to compute the RG of this net system. In Table 3, the details of the iteration steps are presented. Table 4 compares the performance of the several algorithms applied for this net system. From the perspective of space complexity analysis, compared with the approaches in [24,26], our method only computes 19.5% and 18.6% of the total number of RMs and LMs, respectively. This means that this method does not involve the repeated enumeration and analysis of a system state. From the perspective of time complexity analysis, compared with the techniques in [24,26], this method can save 70.0% and 24.7% of the time cost, respectively. That is to say, it performs better than the methods in [24,26].

Table 3.
Iteration steps of the net system depicted in Figure 4.

Table 4.
Performance comparison of different methods.
Then, a net system from [25], depicted in Figure 5, is employed to demonstrate this technique. This net system has 54,869 RMs, including 51,506 LMs and 3363 ILMs. Table 5 presents the iteration steps of the proposed method. Table 6 provides a comparative analysis of the performance of different techniques for this net system. In terms of space complexity, compared with the methods in [24,26], the number of RMs and LMs are reduced by 296,657 and 277,205, respectively. In terms of time complexity, it only takes 9.0% of the computation time used by the approach in [26]. Meanwhile, this method saves 177.0 s to generate its RG compared with the approach in [24].
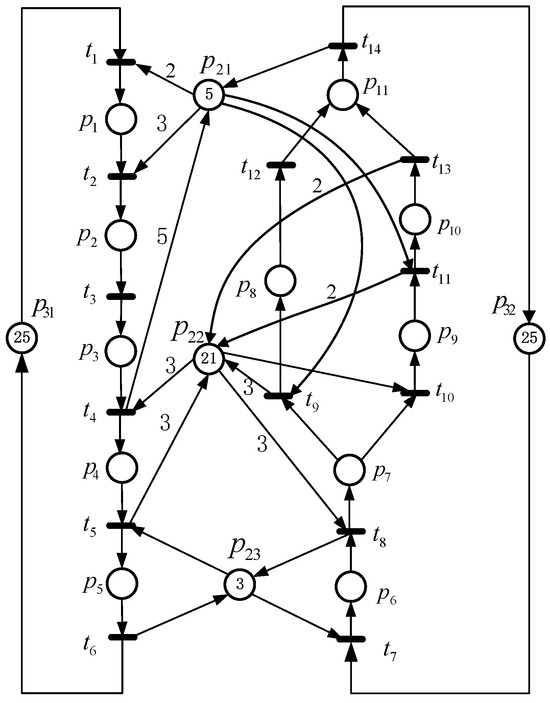
Figure 5.
A net system from [25].

Table 5.
Iteration steps of the net system depicted in Figure 5.

Table 6.
Performance comparison of different methods.
We continue to use the net system shown in Figure 6 to test the proposed approach, which has 68,531 RMs. According to the deadlock-free control specification, the numbers of LMs and ILMs are 66,400 and 2131, respectively. By introducing a GIP, the proposed method generates its RG iteratively, and Table 7 presents the iteration steps. Table 8 gives a comparative analysis of the performance of different algorithms applied to this net system. Similarly, the space complexity of this method is lower, i.e., the proposed method only requires calculating 18.6% of the RMs and 18.5% of the LMs compared with the techniques in [24,26]. In terms of time complexity, compared with the approaches in [24,26], it saves 8,792.3 s and 103.8 s, respectively. Consequently, the performance of those in [24,26] is poor compared with the proposed method.
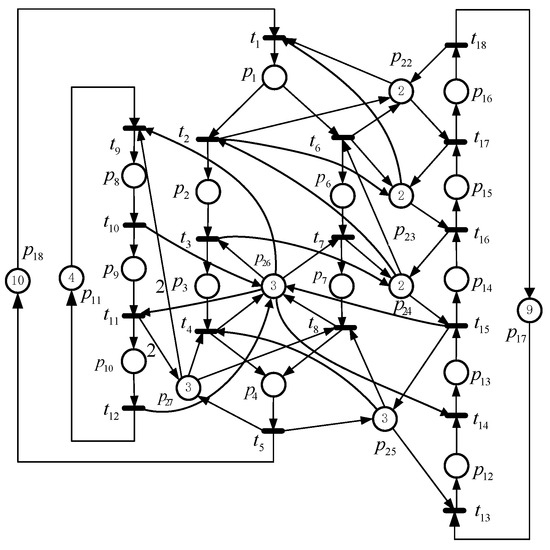
Figure 6.
A net system from [25].

Table 7.
Iteration steps of the net system depicted in Figure 6.

Table 8.
Performance comparison of different methods.
Finally, we select a net system depicted in Figure 7 to illustrate this method. This net system has 316,228 RMs, 308,790 and 7438 of which are LMs and ILMs, respectively. By employing this technique, Table 9 gives the details of the iteration steps. In Table 10, a comparative analysis of the performance of several approaches implemented on the net system shown in Figure 7 is presented. Our method demonstrates significantly lower space complexity compared with the approaches in [24,26], i.e., only 15.3% of the RMs and 15.2% of the LMs are calculated. In terms of computation time, it saves 139,157.2 s and 854.9 s compared with the techniques in [24,26], respectively. Obviously, the performance of this method outperforms the approaches in [24,26].
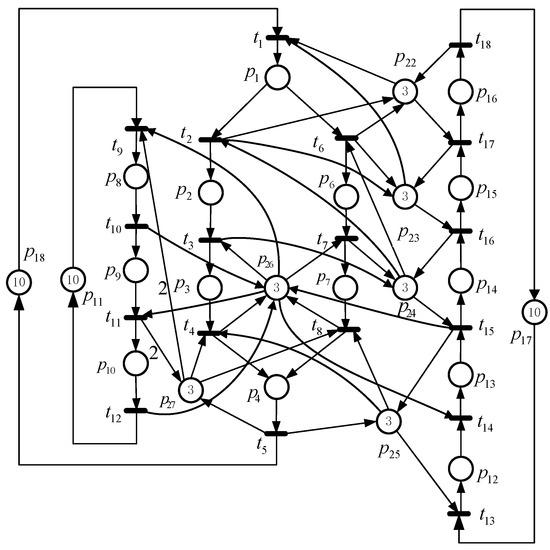
Figure 7.
A Petri net model.

Table 9.
Iteration steps of the net depicted in Figure 7.

Table 10.
Performance comparison of different methods.
4. Conclusions
This paper introduces a TGAL-based approach to calculate and analyze the RG of Petri net models. Given a generalized net system, this method systematically generates its RG through the introduction of a GIP. At each iteration, the previously obtained states are selected to compute and classify the RMs of the current step. During an iterative process, a system state is required to be computed and analyzed only once. In terms of time complexity and space complexity, this approach outperforms the techniques in [24,26]. In particular, it has more advantages in terms of computation time than our previous algorithms in [26,27]. Furthermore, compared with the techniques in [13,14], the proposed method has an advantage in terms of space complexity since RMs are partially generated at each iteration step. Consequently, this method is more advantageous than the approaches in [13,14] to compute the RG of a large-scale net system. Nevertheless, the proposed method also exhibits a drawback, i.e., it involves frequently reading and writing a large number of states at each iteration. One of our future research directions is to consider improving the state storage method to enhance the efficiency of the algorithm for complex systems. Another is to extend the proposed method to other types of Petri nets, such as time Petri nets, colored Petri nets, and object Petri nets.
Author Contributions
Conceptualization, C.L., Y.C. and M.U.; methodology, C.L., Y.C. and Z.L.; software, C.L. and H.M.; validation, F.J.; data curation, C.L.; writing—original draft preparation, C.L. and Y.C.; and writing—review and editing, C.L., Y.C. and Z.L. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the Qinghai University Research Ability Enhancement Project under Grant 2025KTSQ28; in part by the Science and Technology Development Fund, MSAR, under Grants 0029/2023/RIA1 and 0029/2022/AGJ; in part by the Program of Guangdong under Grant 2023A0505020003; and in part by the School-Enterprise Joint Project (Design and Research of Integrated Photovoltaic Storage and Charging Microgrid System) under Grant SGQHXNFSNYJS2400216.
Data Availability Statement
Data will be made available on request.
Conflicts of Interest
Author Huimin Ma was employed by the company State Grid Qinghai Electric Power Company, UHV Company. The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Appendix A. Preliminaries
This appendix outlines the basics of Petri nets [28] and provides an analysis of the RG [29].
Appendix A.1. Petri Nets
A Petri net [28] is a quadruple , where P and T are finite and non-empty sets of places and transitions, respectively. The flow relation of a net is represented by arcs with arrows from places to transitions or from transitions to places, denoted as . is a mapping that assigns a weight to an arc: if , and otherwise, where and comprise the set of non-negative integers. The preset and postset of a node are and , respectively. Furthermore, the preset and postset of a set are and , respectively. A marking represents a mapping . The number of tokens in place p at marking M is denoted as . Generally, marking M can be written as . The pair is called a marked Petri net or a net system. Incidence matrix of net N is a integer matrix with .
A transition is enabled at marking M if for all , . This fact is denoted as . Once a transition t fires, it yields a marking , denoted as , where , for all . Marking is said to be an RM from if there is a sequence of transitions such that holds. is called the set of RMs of a net model N from the initial marking , often denoted by . An RG is a graphical representation of , whose nodes are markings in and whose arcs are labeled by the transitions of N, denoted as .
Let be a net system with . A transition is live at if for all , there is such that holds. is live if for all , t is live at . It is dead at if there is not a transition such that holds.
Appendix A.2. Analysis of Reachability Graph
In [27], a manufacturing-oriented Petri net (M-net for short) is introduced, which is a generalization of the models for flexible manufacturing systems (FMSs). In an M-net, places can be partitioned into three types: idle, operation (activity), and resource places, whose sets are denoted as , , and , respectively. An idle place represents a raw part before entering a production sequence. The token count in an idle place denotes the number of concurrent operations that can happen in the production sequences. An operation place means an operation to be processed for a part in a production sequence, and initially it has no token. A resource place signifies types of available resources, such as robots and machines. In the initial state, tokens in a resource place are equal to the number of available resource units.
Given a deadlock-free control specification for a net model , a marking is legal if its successor can go back to the initial marking; otherwise, it is an ILM. The set of LMs, denoted as , is defined as
Meanwhile, the set of ILMs, denoted as , is defined as
References
- Coffman, E.G.; Elphick, M.J.; Shoshani, A. Systems deadlocks. ACM Comput. Surv. 1971, 3, 67–78. [Google Scholar] [CrossRef]
- Yamalidou, K.; Moody, J.; Lemmon, M.; Antsaklis, P. Feedback control of Petri nets based on place invariants. Automatica 1996, 32, 15–28. [Google Scholar] [CrossRef]
- Tricas, F.; Garcia-Valles, F.; Colom, J.M.; Ezpeleta, J. An Iterative Method for Deadlock Prevention in FMS; Springer: New York, NY, USA, 2000. [Google Scholar]
- Dou, H.; You, D.; Wang, S.G.; Zhou, M.C. Designing liveness-enforcing supervisors for manufacturing systems by using maximally good step graphs of Petri nets. IEEE Trans. Autom. Sci. Eng. 2024, 1–12. [Google Scholar] [CrossRef]
- Abubakar, U.S.; Liu, G.Y. Adaptive supervisory control for automated manufacturing systems using borrowed-buffer slots. Inf. Sci. 2024, 667, 1–15. [Google Scholar] [CrossRef]
- Ezpeleta, J.; Tricas, F.; Garcia-Valles, F.; Colom, J.M. A banker’s solution for deadlock avoidance in FMS with flexible routing and multiresource states. IEEE Trans. Robot. Autom. 2002, 18, 621–625. [Google Scholar] [CrossRef]
- Du, N.; Hu, H.S.; Zhou, M.C. Robust deadlock avoidance and control of automated manufacturing systems with assembly operations using Petri nets. IEEE Trans. Autom. Sci. Eng. 2020, 17, 1961–1975. [Google Scholar] [CrossRef]
- Liu, G.Y.; Li, P.; Wu, N.Q.; Yin, L. Two-step approach to robust deadlock control in automated manufacturing systems with multiple resource failures. J. Chin. Inst. Eng. 2018, 41, 484–494. [Google Scholar] [CrossRef]
- Giua, A. Supervisory control of Petri nets with language specifications. In Control of Discrete-Event Systems; Springer: Berlin/Heidelberg, Germany, 2013; pp. 235–255. [Google Scholar]
- Attar, M.; Lucia, W. Data-driven robust backward reachable sets for set-theoretic model predictive control. IEEE Control. Syst. Lett. 2023, 7, 2305–2310. [Google Scholar] [CrossRef]
- Wang, S.G.; Wang, C.Y.; Zhou, M.C. Controllability conditions of resultant siphons in a class of Petri nets. IEEE Trans. Syst. Man Cybern.—Part A Syst. Humans 2012, 42, 1206–1215. [Google Scholar] [CrossRef]
- Hu, H.S.; Liu, Y.; Zhou, M.C. Maximally permissive distributed control of large scale automated manufacturing systems modeled with Petri nets. IEEE Trans. Control. Syst. Technol. 2015, 23, 2026–2034. [Google Scholar]
- Huang, Y.S.; Pan, Y.L.; Zhou, M.C. Computationally improved optimal deadlock control policy for flexible manufacturing systems. IEEE Trans. Syst. Man Cybern.—Part A Syst. Humans 2012, 42, 404–415. [Google Scholar] [CrossRef]
- Huang, Y.S.; Chung, T.H.; Su, P.J. Synthesis of deadlock prevention policy using Petri nets reachability graph technique. Asian J. Control 2010, 12, 336–346. [Google Scholar] [CrossRef]
- Yang, B.Y.; Hu, H.S. Maximally permissive deadlock and livelock avoidance for automated manufacturing systems via critical distance. IEEE Trans. Autom. Sci. Eng. 2022, 19, 3838–3852. [Google Scholar] [CrossRef]
- Ghaffari, A.; Rezg, N.; Xie, X.L. Design of a live and maximally permissive Petri net controller using the theory of regions. IEEE Trans. Robot. Autom. 2003, 19, 137–141. [Google Scholar] [CrossRef]
- Hu, H.S.; Liu, Y. Supervisor simplification for AMS based on Petri nets and inequality analysis. IEEE Trans. Autom. Sci. Eng. 2013, 11, 66–77. [Google Scholar] [CrossRef]
- Pastor, E.; Cortadella, J.; Roig, O. Symbolic analysis of bounded Petri nets. IEEE Trans. Comput. 2001, 50, 432–448. [Google Scholar] [CrossRef]
- Chen, Y.F.; Li, Z.W.; Khalgui, M.; Mosbahi, O. Design of a maximally permissive liveness-enforcing Petri net supervisor for flexible manufacturing systems. IEEE Trans. Autom. Sci. Eng. 2011, 8, 374–393. [Google Scholar] [CrossRef]
- Miner, A.S.; Ciardo, G. Efficient reachability set generation and storage using decision diagrams. In Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1999; Volume 1639, pp. 6–250. [Google Scholar]
- Pastor, E.; Cortadella, J.; Roig, O.; Badia, R.M. Petri net analysis using Boolean manipulation. In Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1994; Volume 815, pp. 416–435. [Google Scholar]
- Ma, Z.Y.; Tong, Y.; Li, Z.W.; Giua, A. Basis marking representation of Petri net reachability spaces and its application to the reachability problem. IEEE Trans. Autom. Control. 2017, 62, 1078–1093. [Google Scholar] [CrossRef]
- Dong, Y.F.; Li, Z.W.; Wu, N.Q. Symbolic verification of current-state opacity of discrete event systems using Petri nets. IEEE Trans. Syst. Man Cybern. Syst. 2022, 52, 7628–7641. [Google Scholar] [CrossRef]
- Uzam, M.; Li, Z.W.; Abubakar, U.S. Think-globally-act-locally approach for the synthesis of a liveness-enforcing supervisor of FMSs based on Petri nets. Int. J. Prod. Res. 2016, 54, 4634–4657. [Google Scholar] [CrossRef]
- Uzam, M.; Gelen, G.; Saleh, T.L. Think-globally-act-locally approach with weighted arcs to the synthesis of a liveness-enforcing supervisor for generalized Petri nets modeling FMSs. Inf. Sci. 2016, 363, 235–260. [Google Scholar] [CrossRef]
- Li, C.Z.; Chen, Y.F.; Li, Z.W.; Barkaoui, K. Synthesis of liveness-enforcing Petri net supervisors based on think-globally-act-locally approach and vector covering for flexible manufacturing systems. IEEE Access 2017, 5, 16349–16358. [Google Scholar] [CrossRef]
- Li, C.Z.; Li, Y.Y.; Chen, Y.F.; Wu, N.Q.; Li, Z.W.; Ma, P.Y.; Kaid, H. Synthesis of liveness-enforcing Petri net supervisors based on a think-globally-act-locally approach and a structurally minimal method for flexible manufacturing systems. Comput. Inform. 2022, 41, 1310–1336. [Google Scholar] [CrossRef]
- Murata, T. Petri nets: Properties, analysis and applications. Proc. IEEE 1989, 77, 541–580. [Google Scholar] [CrossRef]
- Ezpeleta, J.; Colom, J.M.; Martinez, J. A Petri net based deadlock prevention policy for flexible manufacturing systems. IEEE Trans. Robot. Autom. 1995, 11, 173–184. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).