Abstract
The Set Coverage Problem (SCP) is an important combinatorial optimization problem known to be NP-complete. The use of metaheuristics to solve the SCP includes different algorithms. In particular, binarization techniques have been explored to adapt metaheuristics designed for continuous optimization problems to the binary domain of the SCP. In this work, we present a new approach to solve the SCP based on the Secretary Bird Optimization Algorithm (SBOA). This algorithm is inspired by the natural behavior of the secretary bird, known for its ability to hunt prey and evade predators in its environment. Since the SBOA was originally designed for optimization problems in continuous space and the SCP is a binary problem, this paper proposes the implementation of several binarization techniques to adapt the algorithm to the discrete domain. These techniques include eight transfer functions and five different discretization methods. Taken together, these combinations create multiple SBOA adaptations that effectively balance exploration and exploitation, promoting an adequate distribution in the search space. Experimental results applied to the SCP together with its variant Unicost SCP and compared to Grey Wolf Optimizer and Particle Swarm Optimization suggest that the binary version of SBOA is a robust algorithm capable of producing high quality solutions with low computational cost. Given the promising results obtained, it is proposed as future work to focus on complex and large-scale problems as well as to optimize their performance in terms of time and accuracy.
Keywords:
combinatorial optimization; metaheuristic; bio-inspired algorithm; secretary bird optimization algorithm; binarization; set covering problem MSC:
68T20; 68W25; 90C27; 90C59; 68Q25
1. Introduction
The use of optimization and, in particular, metaheuristics, is gaining more and more attention in modern industry as it allows to tackle problems that, until some time ago, were not possible to address. Today, it is possible to tackle complex and large-scale problems, with metaheuristics allowing us to obtain good quality solutions in a reasonable processing time [1]. Metaheuristics, in general, allow us to address different types of problems and can also adapt to changes in the environment, being able to work in different domains. All these characteristics make them attractive for solving current real-world problems in a variety of areas, such as logistics [2,3], manufacturing industry [4,5], transport [6,7], health [8,9], and mining [10,11], among others.
The Set Covering Problem (SCP) is a combinatorial optimization problem known to be NP-hard that is ever-present in various industries [12] and one of the 21 problems present in Karp [13]. It involves finding a subset of columns from a binary matrix A of size that covers all rows at the lowest possible cost. This problem has significant applications in various fields, such as emergency service location [14], crew scheduling in mass transportation systems [15], and other related problems discussed in [16]. There is a special case of SCP where all sets have the same cost in this case the task is to minimize the selection of sets to cover the given universe. Practical applications in the industry are engineering design [17] and vehicle path planning [18], among others.
The use of metaheuristics to solve the SCP includes algorithms such as Genetic Algorithms [19], Particle Swarm Optimization [20], Ant Colony Optimization [21], Tabu Search [22], Electromagnetism metaheuristic [23], Artificial Bee Colony [24], and GRASP [25], among others. In particular, binarization techniques have been explored to adapt metaheuristics designed for continuous optimization problems to the binary domain of the SCP.
In this work, we present a new approach to solving the SCP based on the Secretary Bird Optimization Algorithm (SBOA) [26]. The SBOA was selected for this research for several compelling reasons, drawn directly from its original design and validated performance. First, it is a recent metaheuristic whose authors specifically engineered it to address common shortcomings of existing algorithms, aiming to improve convergence speed, enhance optimization accuracy, and effectively avoid local optima. These characteristics are highly desirable for tackling NP-hard problems like the SCP. Second, the SBOA achieves a robust balance between its exploration and exploitation phases by uniquely combining three different search strategies: differential evolution, Brownian motion, and Lévy flights. Finally, its effectiveness is not merely theoretical; the SBOA has demonstrated superior performance against numerous advanced algorithms on standard benchmark suites (CEC-2017 and CEC-2022) and has been successfully applied to solve twelve different constrained engineering problems.
Given these strengths, the SBOA emerges as a strong and novel candidate for adaptation to the binary domain to solve the SCP. The relevance of finding new and efficient solutions for this problem is underscored by its wide range of applications, which have become even more critical in modern industry. For example, in the post-pandemic era, supply chains and logistics face continuous challenges where the SCP is present [27], including the efficient allocation of resources and crews [28,29], balancing assembly lines, and optimizing the location of distribution centers to meet growing demand.
Since the SBOA was originally designed for optimization problems in continuous spaces and the SCP is a binary problem, this work proposes the implementation of several binarization techniques to adapt the algorithm to the discrete domain. These techniques include eight transfer functions with “S”-shaped and “V”-shaped variants and five different discretization methods. Together, these combinations create multiple adaptations of the SBOA that effectively balance exploration and exploitation, promoting an adequate distribution in the search space. The results suggest that the binary version of the SBOA (BSBOA) is a robust algorithm capable of producing high-quality solutions with low computational cost.
This article is organized as follows: We present a brief description of the Set Coverage Problem in Section 2, how to resolve SCP with continuos metaheuristics in Section 3, and an outline of the Secretary Bird Optimitation Algorithm in Section 4. We explain how and make the binary version of the SBOA in Section 5. Finally, we present our results, discussions, conclusions, and possible future lines of research in Section 6, Section 7 and Section 8.
2. Set Covering Problem
The Set Covering Problem (SCP) is a combinatorial optimization problem categorized as NP-hard. Its main objective is to find a minimal subset of elements that completely covers a universal set of requirements while minimizing the associated cost.
2.1. Formal Mathematical Formulation
Formally, let be a universal set composed of m elements, and let be a collection of n subsets, where each subset has an associated cost . The problem consists of identifying an optimal subset that covers all elements in U at the minimum possible cost.
To model this problem and solve it computationally, the formal set-based definition is translated into a matrix formulation. A binary matrix represents the problem A with m rows and n columns. Each of the m rows corresponds to an element of the universal set U and each of the n columns represents an available subset . The value in the matrix, , is 1 if subset j covers element i (that is, ), and 0 otherwise.
To decide which columns (subsets) are chosen, the binary decision variable is used, which takes the value of one if column j is selected for the solution, and zero if it is not.
Thus, the main objective is to minimize the total cost of the solution, summing the costs of only the selected columns, as indicated by Equation (1).
The main constraint of this problem is the coverage constraint, which ensures that each element (row) is covered by at least one selected column. This is achieved with the following equation, which must hold for every row i:
In addition, we must ensure that the decision variable is binary; therefore, .
2.2. SCP Practical Example
Let us assume a company needs to form an oversight committee for a new technology project. For the project to be successful, the committee must cover five areas of expertise: financial, legal, technical, marketing, and logistics. The company has identified six external consultants, each with a different set of skills and an associated cost (fee).
The goal is to apply the Set Covering Problem (SCP) to select the committee with the lowest total cost that guarantees coverage of all required areas of expertise.
2.2.1. Problem Definition
- 1.
- Elements to be Covered: The five required areas of expertise.
- : Financial Expertise.
- : Legal Expertise.
- : Technical Expertise.
- : Marketing Expertise.
- : Logistics Expertise.
- 2.
- Available Sets: The six candidates, each with their cost and skills.
- : Anne (Cost: $4)—Skills: Financial, Legal.
- : Ben (Cost: $3)—Skills: Technical, Marketing.
- : Carla (Cost: $6)—Skills: Legal, Technical, Logistics.
- : David (Cost: $4)—Skills: Marketing, Logistics.
- : Elena (Cost: $5)—Skills: Financial, Technical.
- : Frank (Cost: $4)—Skills: Legal, Marketing.
Thus, Table 1 shows the relationship between both previous lists in the so-called Incidence Matrix. This matrix reflects the coverage (columns) of each element (rows) and allows us to validate whether the requirements (problem constraints) are met.

Table 1.
Incidence Matrix (A), where if consultant j covers requirement i.
2.2.2. Mathematical Formulation
Let if consultant j is selected and 0 otherwise. The problem is formulated to minimize the total cost, subject to the constraint that each area of expertise is covered.
- Objective Function (minimize cost):
- Constraints (cover each expertise):
- Decision Variables:
2.2.3. Optimal Solution
The optimal solution for this problem is to select Anne (), Ben (), and David ().
- Selected Consultants: {Anne, Ben, David}
- Coverage:
- -
- Anne covers the Financial and Legal areas.
- -
- Ben covers the Technical and Marketing areas.
- -
- David covers the Marketing and Logistics areas.
- Minimum Total Cost: .
This combination fulfills all expertise requirements at the lowest possible cost.
2.3. Unicost Set Covering Problem (Unicost SCP)
The unicost problem is a specific variant of the Set Covering Problem (SCP), in which all column costs are equal ( for all ). The primary objective in this case is to minimize the number of selected columns while ensuring that each row is covered by at least one of them. This variant simplifies the general SCP model by focusing exclusively on the minimum number of columns required to cover all rows, emphasizing structural optimization without considering cost variations.
Mathematically, the model can be formulated as follows:
subject to
where is a coefficient indicating whether column j covers row i, is a binary variable that takes the value 1 if column j is selected and 0 otherwise, I is the set of rows, and J is the set of columns.
The unicost problem, like the general SCP, is known to be NP-hard and has been applied in various fields, such as scheduling, logistics, and resource optimization.
3. Continuous Metaheuristics Solving Set Covering Problem
To apply the Secretary Bird Optimization Algorithm (SBOA) to the Set Covering Problem (SCP), it is necessary to adapt the original search approach, designed for a continuous space, to a binary environment. As discussed in Section 1, various metaheuristics have been successfully applied to solve the SCP, including Genetic Algorithms [30], Ant Colony Optimization [31], Particle Swarm Optimization [32], and others. All these metaheuristics have one characteristic in common: they are metaheuristics designed to solve continuous optimization problems that were modified to resolve binary problems like the SCP.
This adaptation is achieved through a Two-Step Technique that converts continuous solutions into binary solutions, ensuring compliance with the SCP requirements. This technique is fundamental for applying bioinspired algorithms to binary combinatorial optimization problems, such as the SCP.
Two-Step Technique
In the literature, there are different ways to binarize continuous metaheuristics [33], but the most widely used is the Two-Step Technique [34]. As its name suggests, the binarization process is performed in two stages:
- Application of a transfer function, which transforms the continuous value into a value within the range .
- Application of a binarization rule, which determines the assignment of a 1 or a 0.
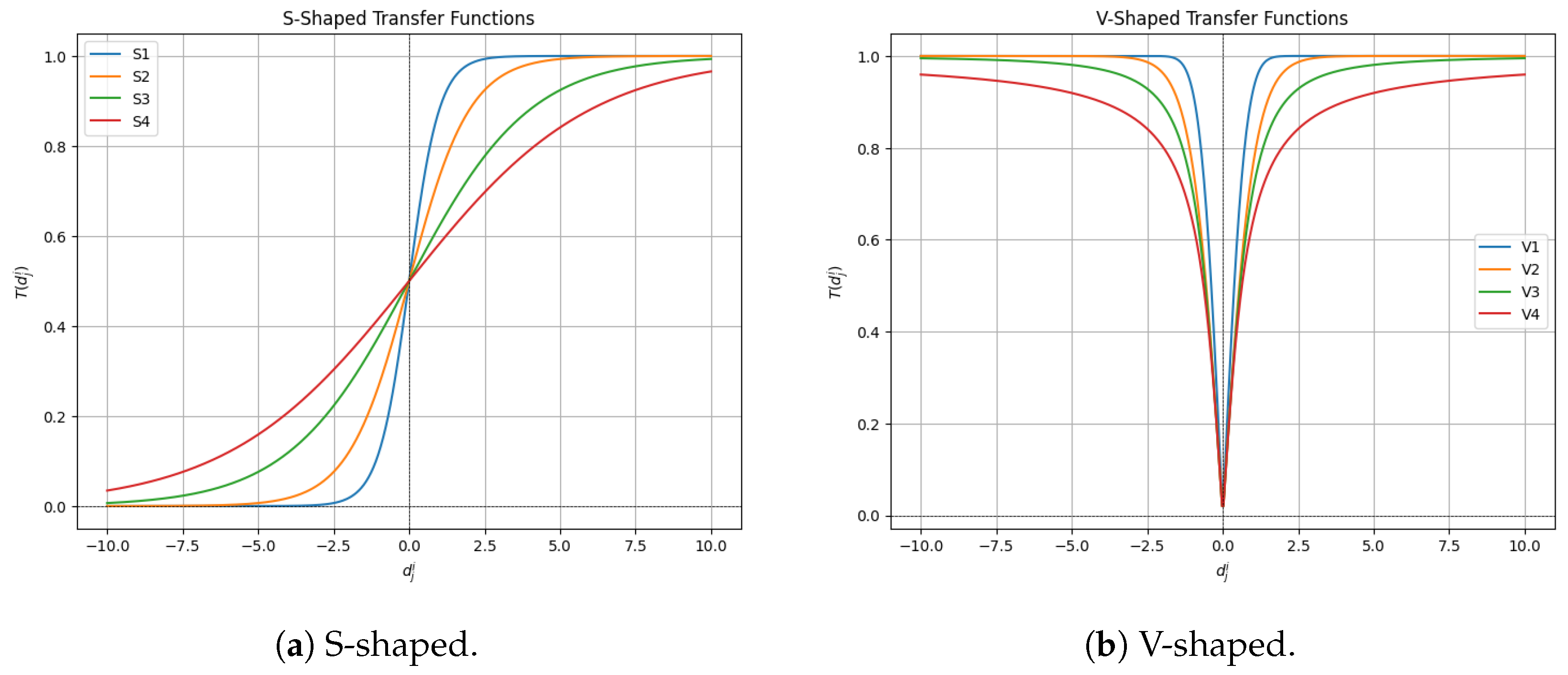
In the literature [33], a variety of transfer functions are proposed for this purpose. They are generally categorized into two main families based on their shape and behavior: S-shaped and V-shaped functions. These two families represent the most common and well-established approaches for mapping continuous search spaces to binary ones.
- S-Shaped Functions: These sigmoidal functions produce a value in the range that represents the probability of a solution’s component becoming ‘1’. An input value close to zero yields a probability near 0.5, while large positive or negative values push the probability towards 1 or 0, respectively. This behavior models a form of probabilistic switch.
- V-Shaped Functions: In contrast, these functions relate the probability of change to the magnitude of the continuous value, rather than its sign. A small step (a value close to zero) results in a low probability of changing the bit, while a large step increases this probability. This is conceptually linked to the notion of velocity or momentum in swarm algorithms, where a larger “move” is more likely to alter the solution’s state.
Table 2 and Figure 1 present the standard functions from both families that are commonly used in this research area. The notation observed in the table corresponds to the continuous value of the j-th dimension of the i-th individual, resulting from the perturbation performed by the continuous metaheuristic.

Table 2.
S-shaped and V-shaped transfer functions.
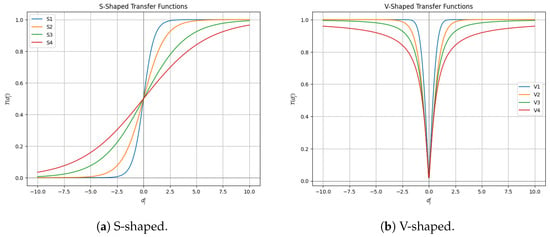
Figure 1.
S-shaped and V-shaped transfer functions.
Additionally, in the literature [33], we can find five different binarization rules, of which we can highlight the following:
- Standard (STD): If the condition is satisfied, the standard binarization rule returns 1; otherwise, it returns 0. Mathematically, it is defined as follows:
- Elitist (ELIT): The best value is assigned if a random value is within the probability; otherwise, a zero value is assigned. Mathematically, it is defined as follows:
- Complement (COM): If the condition is satisfied, the second step operator returns the complement of the actual value.
4. Secretary Bird Optimization Algorithm
The Secretary Bird Optimization Algorithm (SBOA) is a metaheuristic inspired by the natural behavior of the secretary bird, particularly its unique strategies for hunting and evading predators. It was proposed in 2024 by Youfa Fu, Dan Liu, Jiadui Chen, and Ling He [26]. The algorithm was originally designed to solve continuous optimization problems, leveraging its exploration and exploitation phases to efficiently find optimal solutions.
The operation of the SBOA is divided into two main phases that mimic the bird’s survival instincts: exploration, which models its hunting strategy, and exploitation, which models its escape strategy.
4.1. Exploration Phase (Hunting Strategy)
This phase simulates how the secretary bird hunts its prey, like snakes, and corresponds to a global search in the solution space. The process is modeled in three stages that reflect the bird’s hunting tactics:
- Searching for Prey: The bird begins by exploring the terrain to locate hidden prey. The algorithm mimics this by creating a new solution based on the difference between two randomly selected solutions from the population. This enhances diversity and allows the algorithm to scan new, unexplored areas of the search space. This movement is modeled by Equation (11).
- Wearing Down the Prey: Once prey is found, the bird does not attack immediately but circles and provokes it to deplete its energy. The algorithm models this by moving towards the best solution found so far (), simulating how the bird focuses on its target, while introducing a random component to avoid premature convergence. This is shown in Equation (12).
- Attacking the Prey: When the prey is exhausted, the bird executes a swift, lethal attack. To simulate this decisive action, the algorithm performs a “jump” toward the best solution using a Lévy flight (RL). This feature models the bird’s powerful strike, combining frequent small steps with occasional long jumps to accelerate convergence towards the global optimum. The movement is described in Equation (13).
4.2. Exploitation Phase (Escape Strategy)
This phase models how the secretary bird evades predators, which corresponds to a refined local search for a better solution. The bird chooses one of two strategies with equal probability:
- Camouflage (): The bird may hide in its environment to avoid being detected. The algorithm simulates this by making small, subtle adjustments to its current position, moving locally around the best-known solution to refine it.
- Fleeing (): If camouflage is not an option, the bird runs or flies to escape danger. The algorithm models this with a larger, more random movement that allows it to jump to other regions of the search space, effectively avoiding stagnation.
Both escape strategies are modeled using Equation (14).
4.3. Solution Selection
A key aspect of the SBOA is how it determines if a new solution is superior to the current one. The algorithm employs a greedy selection mechanism for this purpose.
The quality of each solution is measured by an objective function (F), which, in the context of the Set Covering Problem, is the total cost to be minimized. After generating a new candidate position in either the exploration or exploitation phase, the algorithm compares the fitness of the new solution () with that of the current one ().
The new solution is accepted only if it offers a better fitness value (i.e., a lower cost). Otherwise, the current solution is kept. This process, shown in Equation (15), ensures that the population’s quality either improves or remains the same in each iteration, guiding the search effectively towards the optimal solution.
The pseudo-code of the SBOA is detailed in the pseudo-code of Algorithm 1.
| Algorithm 1 Secretary Bird Optimization Algorithm. |
Input: Problem Setting , , Output: Best solution
|
5. Binary Secretary Bird Optimization Algorithm
As explained in Section 4, the Algorithm Optimization based on the Behavior of the Secretary Bird (SBOA) is a metaheuristic designed to solve continuous optimization problems. To address problems such as feature selection, it is necessary to transform the solutions into the binary domain.
Furthermore, in Section 3, it was highlighted that the Two-Step Technique is one of the most widely used approaches for binarizing continuous metaheuristics. In [33,34], eight different transfer functions and five binarization rules are described, which can be applied in this context.
In this work, the binarization scheme was chosen based on established findings in the literature that analyze the relationship between different transfer functions, binarization rules, and the exploration–exploitation balance. For the experiments, we use the V3 transfer function and the Elitist discretization method, considering the work carried out by Lanza-Gutierrez et al. in [35], where they recommend the use of V3 to solve small and medium-sized problems and for a better exploration–exploitation relation recommend Elitist as a discretization technique.
Additionally, we selected a function from the V-shaped family because its behavior is particularly well-suited for swarm intelligence algorithms. Unlike S-shaped functions, V-shaped functions relate the probability of a bit changing to the magnitude (or “velocity”) of the agent’s move, not its direction. A larger step size corresponds to a higher probability of flipping a bit. Among these, the V3 transfer function, shown in Equation (16), was chosen due to recommendations in the literature for its robust performance on small and medium-sized problems.
To complement the transfer function, the elitist binarization rule was selected, as shown in Equation (17). This rule introduces a strong exploitation pressure by giving a chance to preserve bits from the best-found solution in the population (). This element of elitism is intended to balance the highly explorative nature of the SBOA’s hunting phases, thereby creating a more focused and effective search process.
In this way, the Binary Secretary Bird Optimization Algorithm (BSBOA) is constructed. The process begins with the initialization of the solutions in the binary domain. In each iteration, the binary solutions are modified using Equations (11)–(14), which represent the movement equations specific to the SBOA. Once the solutions are perturbed, they exit the binary domain, and a binarization process is applied using Equations (16) and (17). This cycle is repeated until the defined number of iterations is completed.
Algorithm 2 presents the binary version of the SBOA, where the key section is the binarization that occurs in line 23.
| Algorithm 2 Binary Secretary Bird Optimization Algorithm. |
Input: Problem Setting , , Output: Best solution
|
Algorithm Complexity Analysis
Each algorithm requires a certain amount of time to perform its optimization tasks, and these can vary for the same problem. Evaluating algorithmic complexity is an effective way to demonstrate performance in terms of runtime. Big O notation is one of the most widely used tools for complexity analysis [36], and we will use it in this paper to analyze the complexity of BSBOA. Let N be the population size, the number of decision variables, and T the maximum number of iterations. Thus, for the initialization process of random solutions, we have a complexity of . During the optimization process, the complexity is O(T × N) + 2 · O(T × N × Dim), which includes the search for the best positions per iteration (O(T × N)), the updating of the positions of all solutions per iteration (O(T × N × Dim)), and the binarization of all solutions per iteration (O(T × N × Dim)). Thus, the algorithmic complexity of our proposal is O(N × (T × Dim + 1)).
6. Experimental Result
To develop the validation of our proposal, we have used the instances offered in OR-library [37] for both the pesos version (SCP) [35] and for the Unicot version (USCP) [17]. Our proposal was compared to two continuous metaheuristics of great relevance, such as Binary Particle Swarm Optimization [38] and Binary Grey Wolf Optimizer [39].
6.1. Parameter Setting
Before performing experimentation, we perform internal tests for parameter configuration. Specifically, we have carried out experimentation with the population size and the number of iterations. For the population size, we tested from [10, 100] in increments of 10, and the population sizes we tested were [20, 50, 70, 100, 150, 200, 300, 400, 500, 600, 700, 800, 900, 1000].
Table 3 shows the subset of instances used for parameter configuration. We have used these instances because we consider that they are representative of the entire portfolio of existing instances of OR-library. The table contains the following details: The first column shows the name of the instance, the second column shows the sample to the type of problem that the instance (SCP or USCP) belongs, the third column refers to the amount of restrictions that the instance possesses, the fourth column refers to the amount of decision variables to optimize, the fifth column refers to the density of some that the matrix has in view of Section 3, and the last column refers to the optimal value of the instance. This experiment was conducted in a team using a Windows 10 operating system, an Intel Core i9-10900 K 3.70 GHz Processor, and 64 GB of RAM.

Table 3.
Instances used for parameter configuration.
Table 4 shows the best configurations for each instance executed, considering computing time and the fitness reached. Thus, it is observed that the ideal population size for this experiment is 10. For the number of iterations, the value changes for each instance; therefore, we have determined that the average iterations will be used in experimentation. Thus, the number of iterations is 600.

Table 4.
Parameter selection.
Thus, Table 5 shows the final configuration of the experimentation carried out in this work. The global configuration used by all the metaheuristics (All MH) and the parameters of each metaheuristic are highlighted.

Table 5.
Configuration of parameters.
6.2. SCP and USCP Instances Resolved
Table 6 and Table 7 show the instances used to solve the SCP and USCP, respectively. Each table shows the instance name (column Instance), the number of constraints (column M), the number of decision variables (column N), the density of ones in the matrix mentioned in Section 2 (column Density %), and the instance’s optimum. It should be noted that the underlined and bold optima are not global optima but the best results reported in the literature. Thus, for the present work, we solved 22 instances for the SCP and 17 instances for the USCP.

Table 6.
Instances used for the SCP.

Table 7.
Instances used for the USCP.
6.3. Results of SCP
This subsection shows the results of running the SBOA with the previously established parameters and compared with the GWO and PSO algorithms. In Table 8 and Table 9, the results are shown when running the different instances of OR-library. For each algorithm and instance, the best known optimal value, the best value achieved, the worst value achieved, the average, and the standard deviation of the solutions obtained of the 30 executions are shown in the tables [40].

Table 8.
Fitness results per SCP instance.

Table 9.
Fitness results per SCP instance.
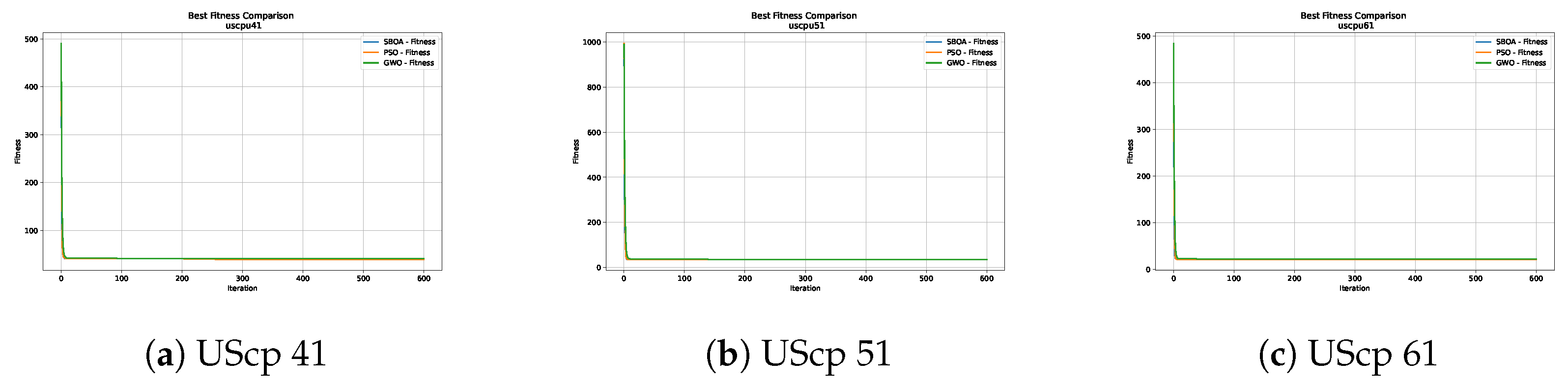
A convergence graph represents how the metaheuristic finds progressively better and better solutions as iterations increase. In order to find good solutions in a reasonable time to provide answers to real-world problems, it is expected that the number of iterations will not be excessive in order to avoid the excessive use of computational resources. As described in Crawford et al. [41] and Lemus-Romani et al. [42], graphs were used to document the optimization process while considering the fitness achieved as the iterations progressed. This is shown in Figure 2, Figure 3, Figure 4 and Figure 5, where the relationship between the number of iterations and the fitness achieved is shown, corresponding to the x and y axes, respectively, where it can be seen that there is good convergence without the algorithm being trapped in a local optimum [43].
Figure 2.
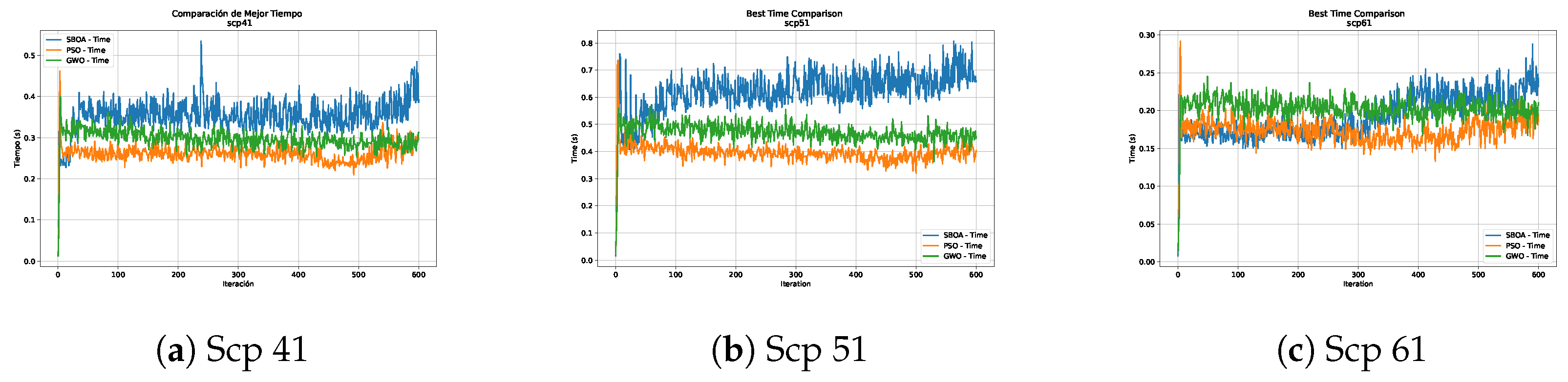
Convergence analysis of the instances Scp 41, Scp 51 and Scp 61.
Figure 3.
Convergence analysis of the instances Scp a1, Scp b1 and Scp c1.
Figure 4.
Convergence analysis of the instances Scp d1, Scp nre1 and Scp nrf1.

Figure 5.
Convergence analysis of the instances Scp nrg1 and Scp nrh1.
On the other hand, in Table 10 and Table 11, the execution of the different instances for the three Algorithms, the SBOA, GWO and PSO, are shown, considering their execution time.

Table 10.
Time per SCP instance.

Table 11.
Time per SCP instance.
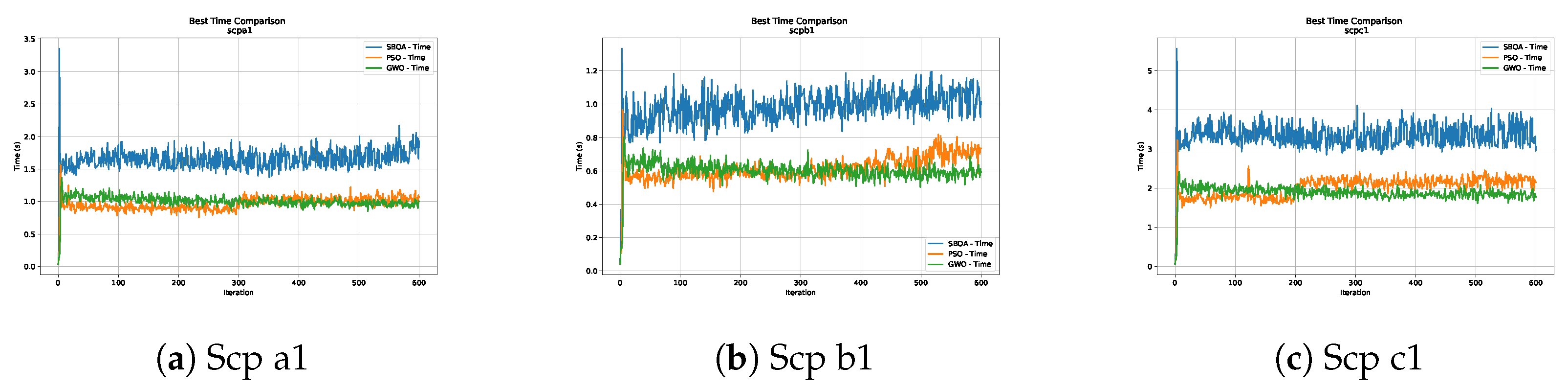
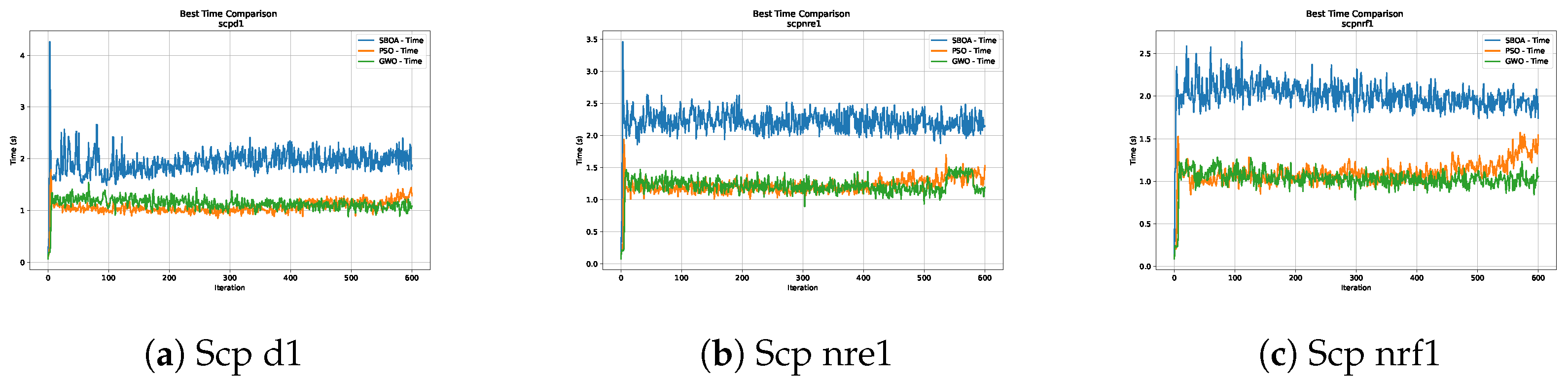
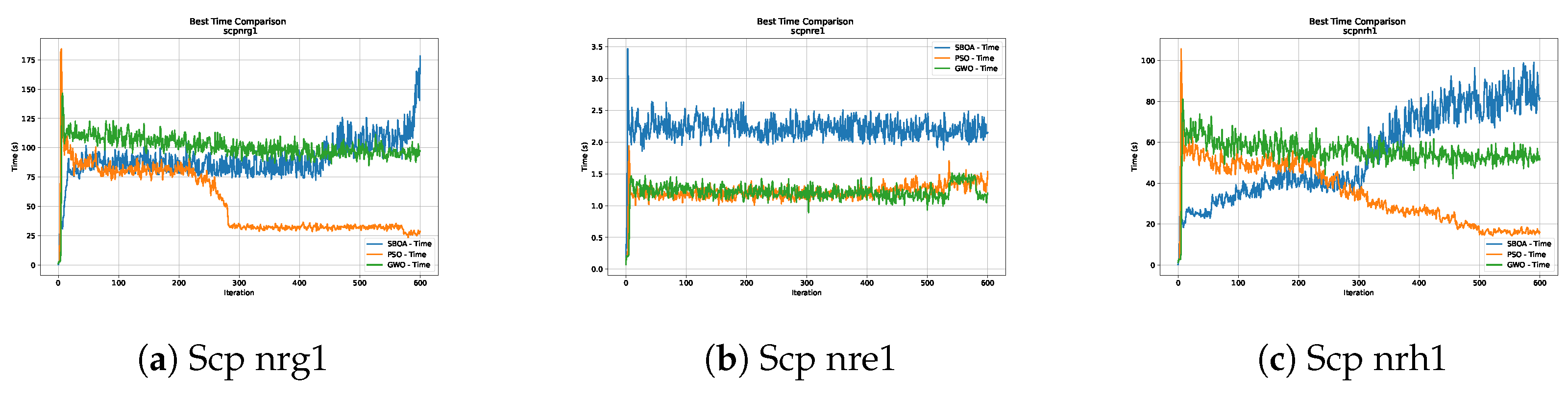
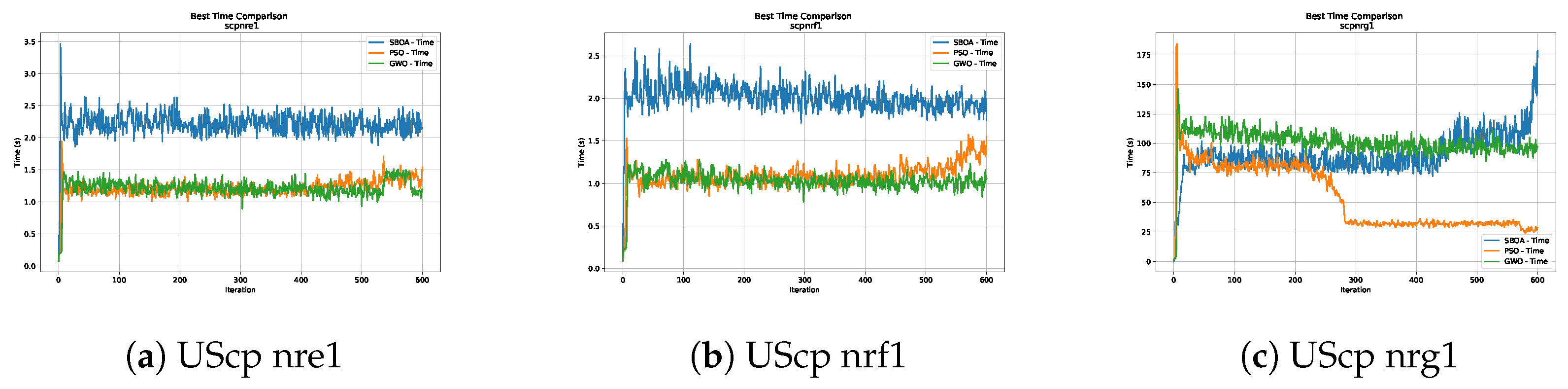
Figure 6, Figure 7, Figure 8 and Figure 9 show graphs with the performance of the three metaheuristics (SBOA, PSO and GWO), where it can be seen that although the times of the SBOA in relation to the iterations were not better than PSO and GWO, they were promising.
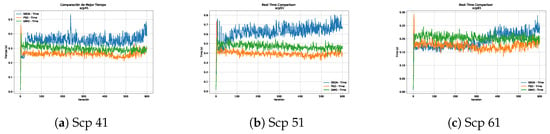
Figure 6.
Time analysis of the instances Scp 41, Scp 51 and Scp 61.
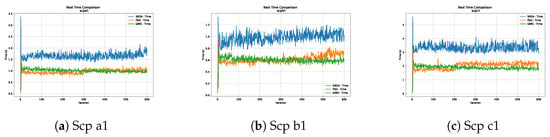
Figure 7.
Time analysis of the instances Scp a1, Scp b1 and Scp c1.
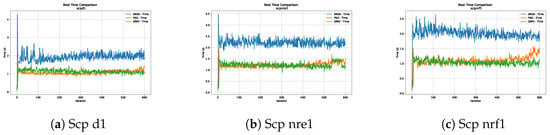
Figure 8.
Time analysis of the instances Scp d1, Scp nre1 and Scp nrf1.
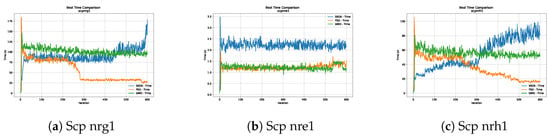
Figure 9.
Time analysis of the instances Scp nrg1, Scp nre1 and Scp nrh1.
6.4. Results of USCP
Table 12 shows the results obtained when running the different instances of the USCP for the three metaheuristics investigated in this work (SBOA, GWO and PSO).

Table 12.
Fitness results per USCP instance.
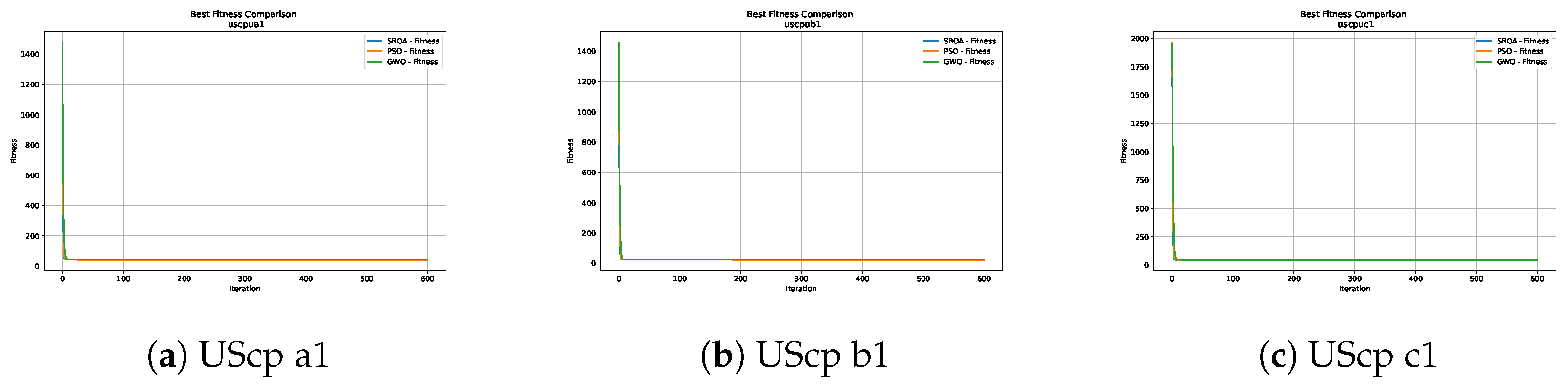
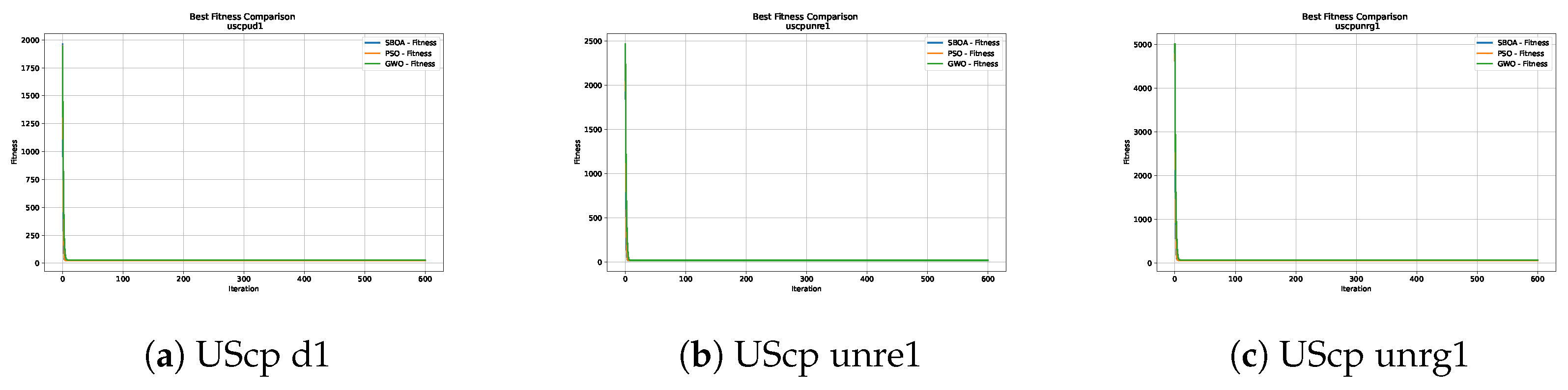
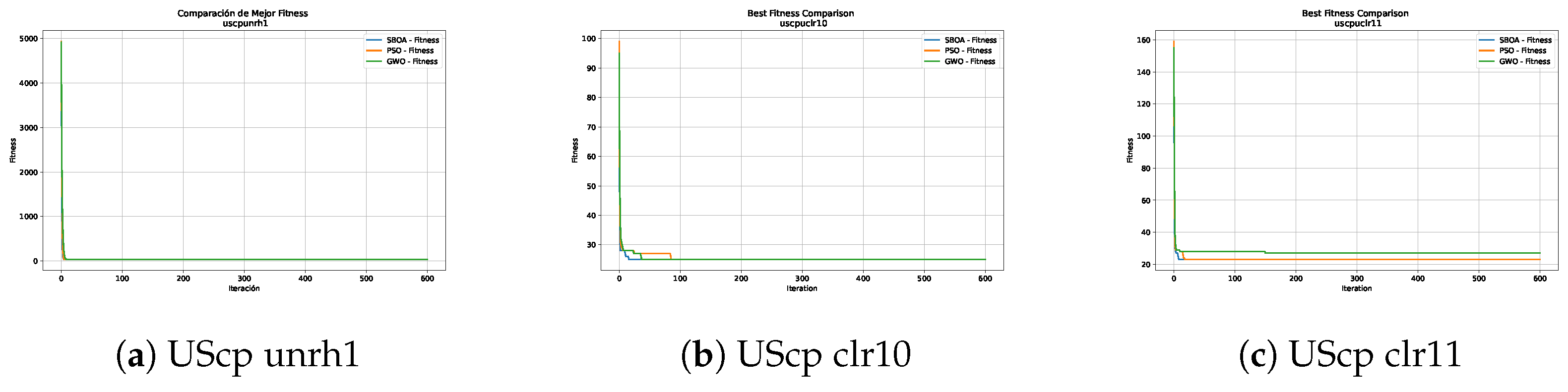
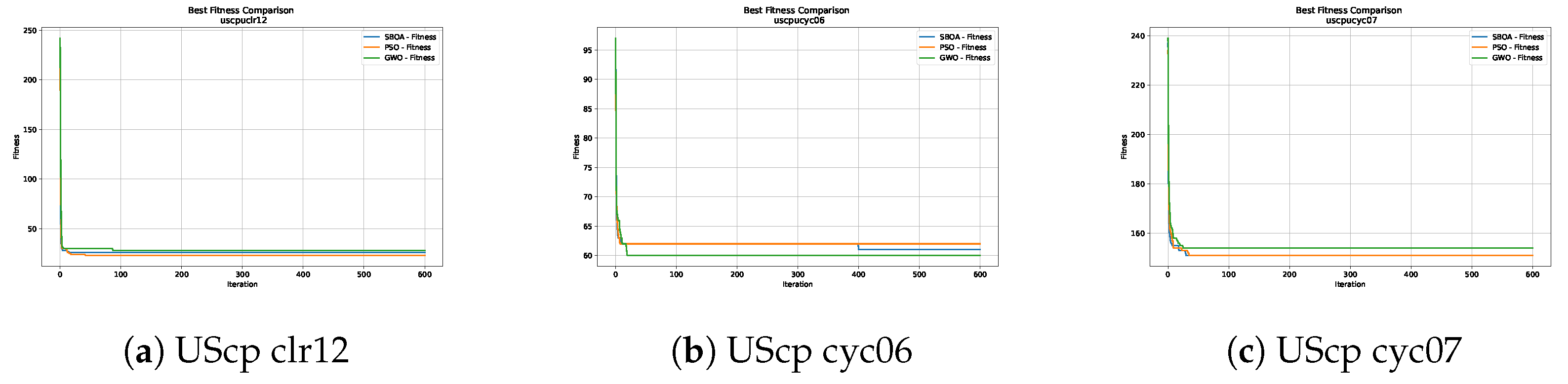
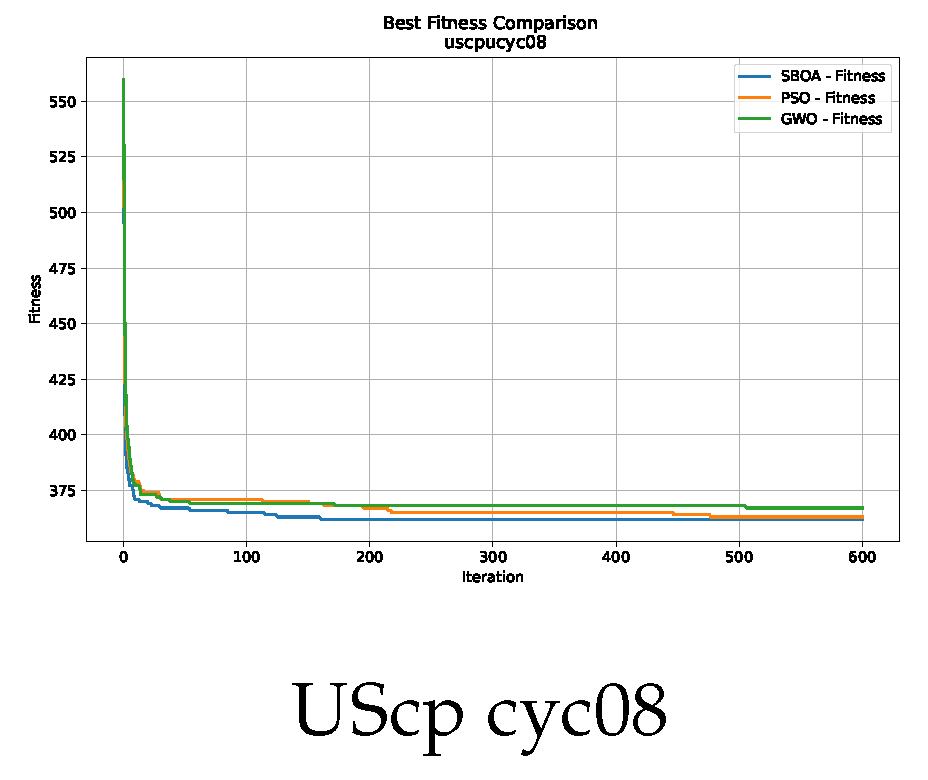
Figure 10, Figure 11, Figure 12, Figure 13, Figure 14 and Figure 15 show the convergence plots of the unicost instances, where it can be observed that, in general, the SBOA achieves good performance with few iterations without being trapped in a local optimum.
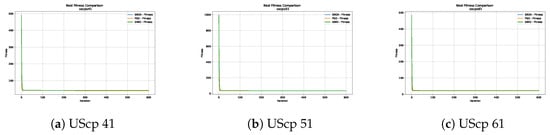
Figure 10.
Convergence analysis of the instances UScp 41, UScp 51 and UScp 61.
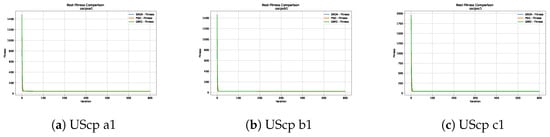
Figure 11.
Convergence analysis of the instances UScp a1, UScp b1 and UScp c1.
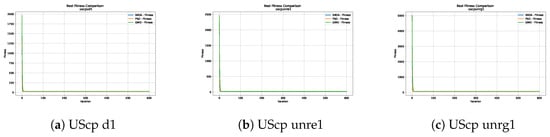
Figure 12.
Convergence analysis of the instances UScp d1, UScp unre1 and UScp unrg1.
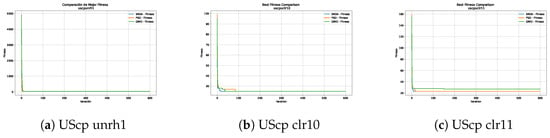
Figure 13.
Convergence analysis of the instances UScp unrh1, UScp clr10 and UScp clr11.
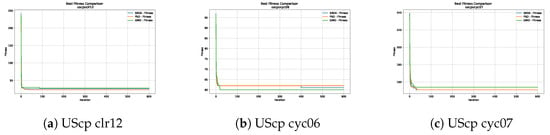
Figure 14.
Convergence analysis of the instances UScp clr12, UScp cyc06 and UScp cyc07.
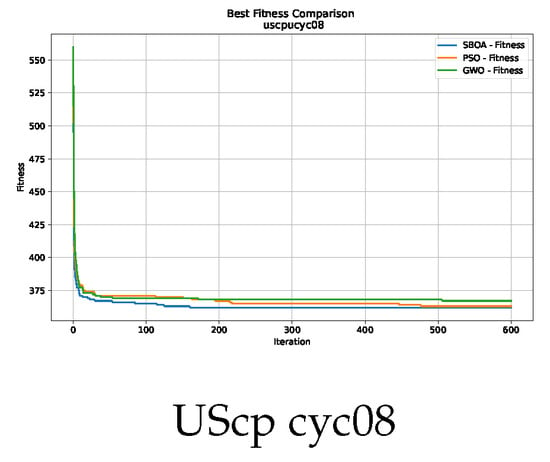
Figure 15.
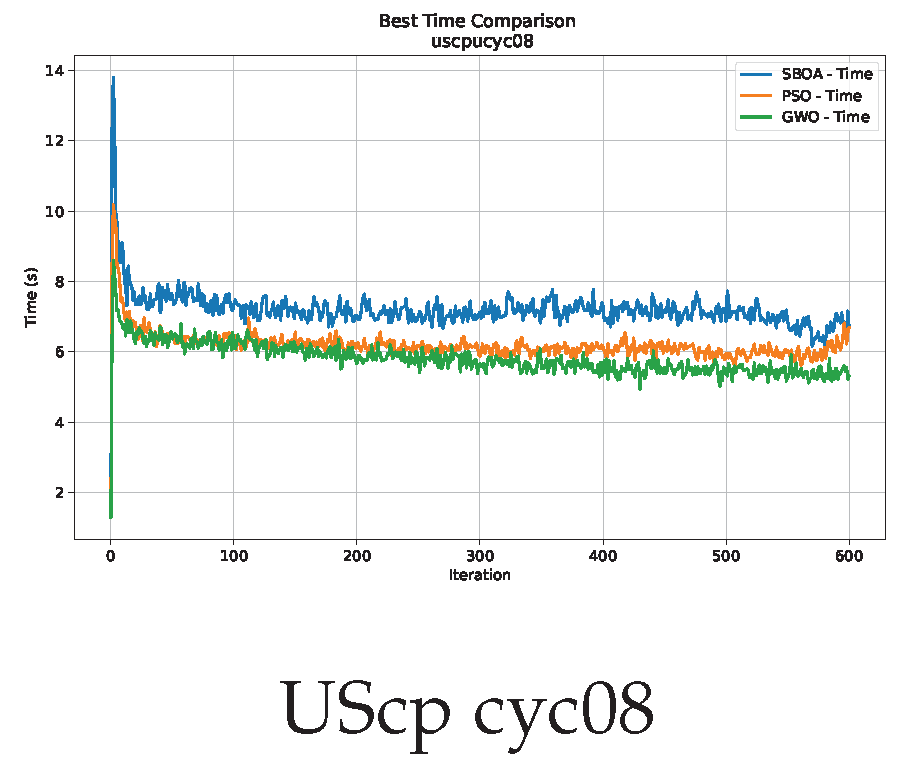
Convergence analysis of the instance UScp cyc08.
Table 13 and Table 14 show the times used for the different USCP instances for the three algorithms studied.

Table 13.
Time per USCP instance.

Table 14.
Time per USCP instance.
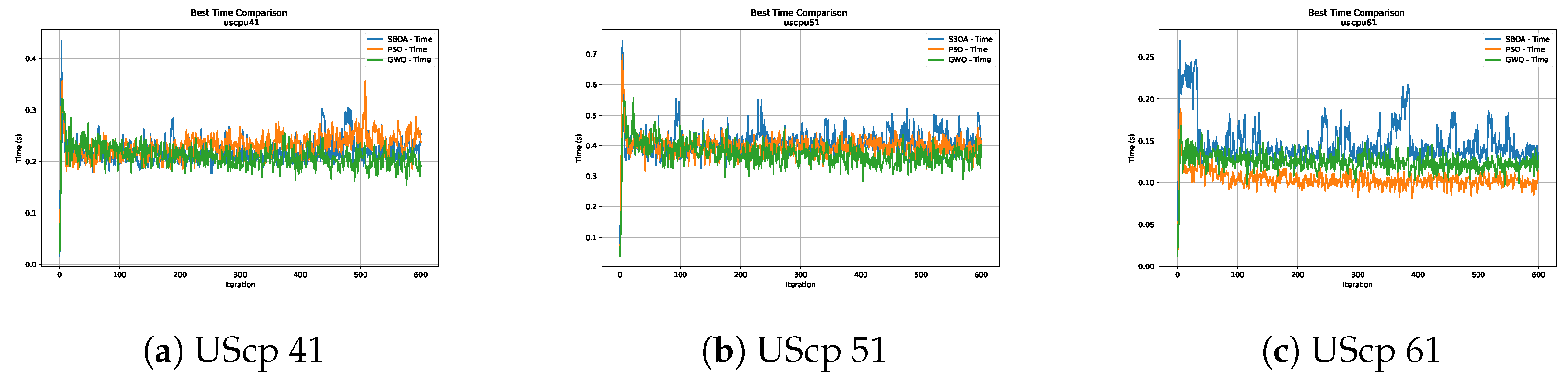
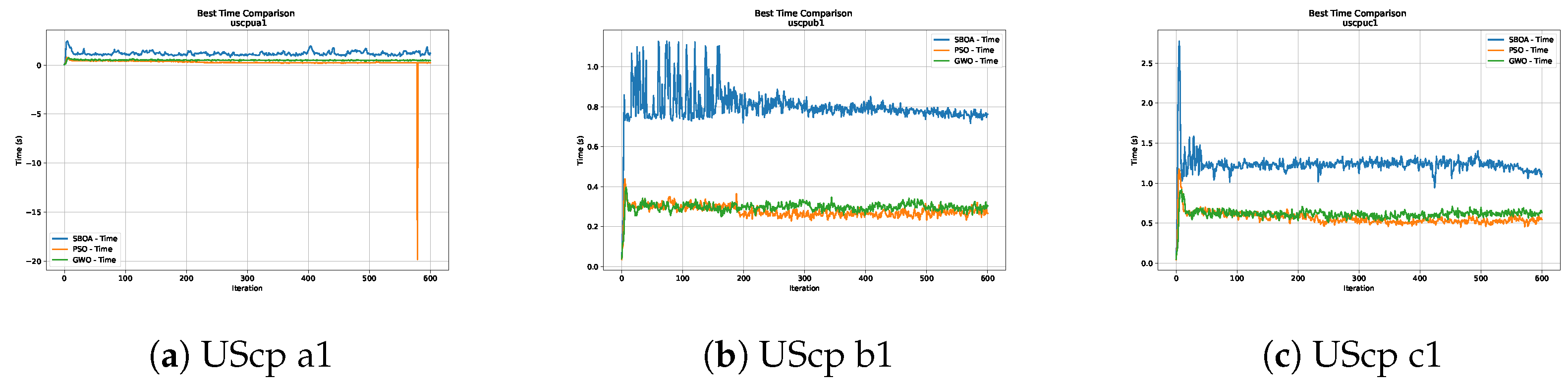
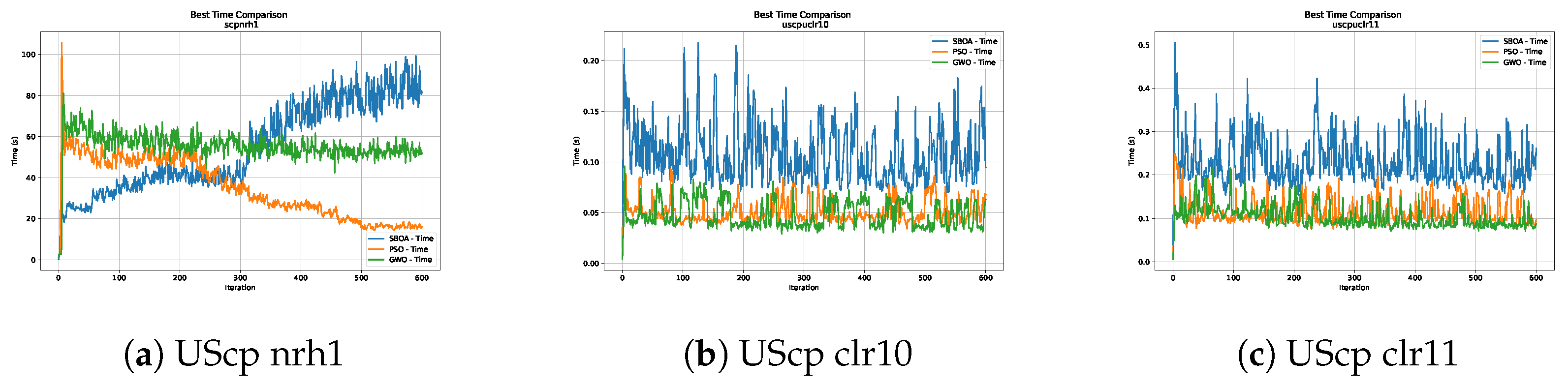
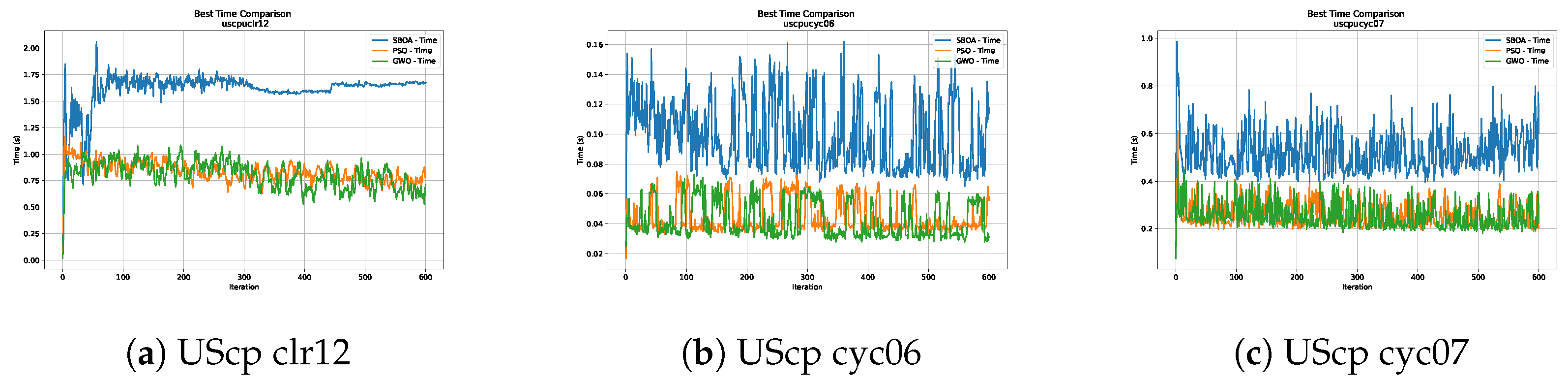
Figure 16, Figure 17, Figure 18, Figure 19, Figure 20 and Figure 21 show graphs with the performance of the three metaheuristics (SBOA, PSO and GWO), enabling us to compare it with the times achieved by the SBOA.
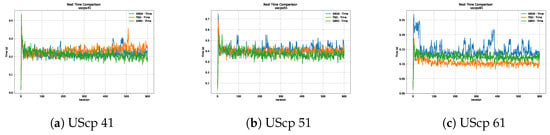
Figure 16.
Time analysis of the instances UScp 41, UScp 51 and UScp 61.
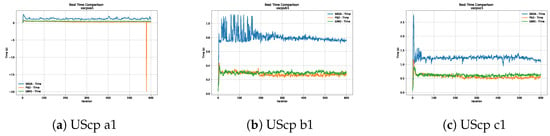
Figure 17.
Time analysis of the instances UScp a1, UScp b1 and UScp c1.
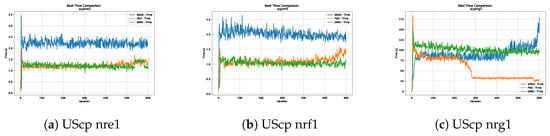
Figure 18.
Time analysis of the instances UScp nre1, UScp nrf1 and UScp nrg1.
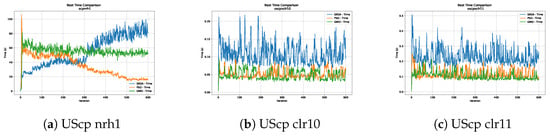
Figure 19.
Time analysis of the instances UScp nrh1, UScp clr10 and UScp clr11.
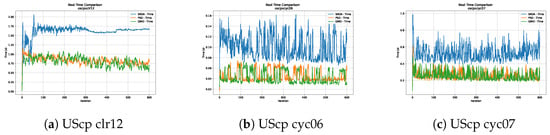
Figure 20.
Time analysis of the instances UScp clr12, UScp cyc06 and UScp cyc07.
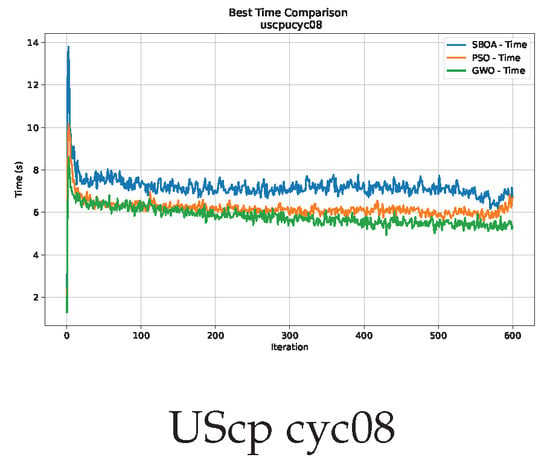
Figure 21.
Time analysis of the instance cyc08.
Statistical Tests
To validate our work, Table 15, Table 16, Table 17 and Table 18 show the statistical significance tests for the algorithms worked on: SBP, PSO and GWO. This table shows the p-values that act as indicators of statistical significance. We use the nonparametric Wilcoxon–Mann–Whitney test to perform this validation [44] since we have two independent samples and we cannot assume normality for at least one of them. The hypotheses considered are the following:
where and represent the average value delivered by algorithms A and B. We consider that if the p-value is less than 0.05, the hypothesis will be rejected, with hypothesis being accepted and these cases are highlighted in bold and underlined in the tables.

Table 15.
Average p-value of the SBOA compared with PSO and GWO for SCP41, ScP42, SCP51, SCP52, SCP61 and SCP62.

Table 16.
Average p-value of the SBOA compared with PSO and GWO for a1, a2, b1, b2, c1, c2, d1 and d2.

Table 17.
Average p-value of the SBOA compared with PSO and GWO for nre1, nre2, nrf1, nrf2, nrg1, nrg2, nrh1 and nrh2.

Table 18.
Average p-value of the SBOA compared with PSO and GWO for u41, u51, u61, ua1, ub1, uc1, uclr10, uclr12, ucyc06, ucyc07, ud1, unre1, unrf1, unre1 and unrh1.
The BSBOA demonstrated remarkable ability in solving the Set Covering Problem (SCP) and its unicost variant (USCP) using the V3 transfer function and elitist rule. For the SCP, it stood out by generating high-quality solutions with lower costs compared to metaheuristics, like GWO and PSO; in the USCP, where costs are homogeneous, it maintained competitive performance with less pronounced differences. Additionally, the BSBOA achieved favorable execution times, establishing itself as an efficient and versatile option for combinatorial optimization problems.
7. Discussion
The experimental outcomes consistently show BSBOA’s ability to yield high-quality solutions, often surpassing GWO and PSO in solution value and robustness (lower standard deviations) for the SCP, while maintaining competitive performance for the USCP. The computational analysis confirms BSBOA’s operational efficiency with a generally low computational burden.
BSBOA’s effectiveness stems from SBOA’s core design, inspired by the secretary bird’s natural behaviors of hunting and evasion, fostering a well-balanced interplay between exploration and exploitation crucial for NP-hard problems. Its systematic adaptation from continuous to binary domains, involving a rigorous exploration of eight transfer functions and five discretization methods, was pivotal. The selection of the V3 transfer function and the Elitist rule, based on prior research for optimal exploration–exploitation balance in medium-sized problems, ensures this effective translation and harmonious interaction with the discrete solution space.
However, it is crucial to acknowledge certain trade-offs and constraints. The iterative nature of the binarization process, applying transfer functions and rules in each cycle, introduces a computational overhead that could be significant for extremely large-scale problems or real-time systems, despite current observed efficiencies. Moreover, while our systematic validation identified an optimal configuration (V3 and Elitist) for the tested instances, the generalizability of this specific setup across all possible SCP and USCP variations, particularly those with distinct structural properties or much higher dimensions, requires further extensive validation. The current reliance on standard benchmark instances, while a common practice, also represents a limitation in fully assessing its performance in the intricate, diverse conditions of real-world applications.
These considerations underscore the ongoing need for refinement and broader validation. Such endeavors are vital to fully realize BSBOA’s potential for industrial and engineering challenges.
8. Conclusions
In this work, a solution to the SCP was provided using the SBOA, which is inspired by the natural behavior of the secretary bird. On the one hand, the SBOA was originally designed to work on continuous space optimization problems; on the other hand, the SCP is a binary problem. Several binarization techniques were proposed to adapt the algorithm to the discrete domain. Combinations of eight transfer functions were used, along with five discretization methods. Subsequently, the binary version of the SBOA was compared with the GWO and PSO algorithms, providing a solution to the SCP and its USCP variant. The BSBOA is positioned as a robust and effective tool for resolving both the SCP and USCP, excelling in solution quality and execution efficiency compared to GWO and PSO. Its ability to handle different levels of complexity and balance exploration and exploitation makes it ideal for practical optimization applications. Future work is to extend its applicability to more complex and large-scale problems, as well as to optimize its performance in terms of time and accuracy.
Author Contributions
Conceptualization, B.C., F.C.-C. and R.S.; methodology, B.C., F.C.-C., C.P.T.M.-l., J.L.A. and F.S.-P.; software, F.C.-C., C.P.T.M.-l., J.L.A. and F.S.-P.; validation, B.C., F.C.-C., R.S., G.A. and G.G.; formal analysis, C.P.T.M.-l., J.L.A. and F.S.-P.; investigation, B.C., F.C.-C., R.S., C.P.T.M.-l., J.L.A., F.S.-P., G.A. and G.G.; resources, C.P.T.M.-l., J.L.A., F.S.-P. and G.A.; writing—original draft preparation, C.P.T.M.-l., J.L.A., F.S.-P. and G.A.; writing—review and editing, B.C., F.C.-C., R.S. and G.G.; supervision, B.C., F.C.-C. and R.S.; funding acquisition, B.C. and R.S. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The original contributions presented in the study are included in the article; further inquiries can be directed to the corresponding authors.
Acknowledgments
Felipe Cisternas-Caneo was supported by the National Agency for Research and Development ANID BECAS/DOCTORADO NACIONAL 21230203.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| SBOA | Secretary Bird Optimization Algorithm |
| BSBOA | Binary Secretary Bird Optimization Algorithm |
| PSO | Particle Swarm Optimization |
| GWO | Grey Wolf Optimizer |
| ACO | Ant Colony Optimization |
| GA | Genetic Algorithm |
| BCSO | Binary Cat Swarm Optimization |
| BBHA | Binary Black Hole Algorithm |
| CS | Cuckoo Search |
| TS | Tabu Search |
| SCP | Set Covering Problem |
| USCP | Unicost Set Covering Problem |
References
- Coelho, P.; Silva, C. Parallel Metaheuristics for shop scheduling: Enabling industry 4.0. Procedia Comput. Sci. 2021, 180, 778–786. [Google Scholar] [CrossRef]
- Ghotb, S.; Sowlati, T.; Mortyn, J. Scheduling of log logistics using a metaheuristic approach. Expert Syst. Appl. 2024, 238, 122008. [Google Scholar] [CrossRef]
- Núñez-López, J.M.; Segovia-Hernández, J.G.; Sánchez-Ramírez, E.; Ponce-Ortega, J.M. Integrating metaheuristic methods and deterministic strategies for optimizing supply chain equipment design in process engineering. Chem. Eng. Res. Des. 2025, 214, 93–104. [Google Scholar] [CrossRef]
- Dhouib, S.; Zouari, A. Adaptive iterated stochastic metaheuristic to optimize holes drilling path in manufacturing industry: The Adaptive-Dhouib-Matrix-3 (A-DM3). Eng. Appl. Artif. Intell. 2023, 120, 105898. [Google Scholar] [CrossRef]
- Yang, C.L.; Yilma, A.A.; Sutrisno, H.; Woldegiorgis, B.H.; Nguyen, T.P.Q. LSTMbased framework with metaheuristic optimizer for manufacturing process monitoring. Alex. Eng. J. 2023, 83, 43–52. [Google Scholar] [CrossRef]
- Huang, B.; Tang, L.; Baldacci, R.; Wang, G.; Sun, D. A metaheuristic algorithm for a locomotive routing problem arising in the steel industry. Eur. J. Oper. Res. 2023, 308, 385–399. [Google Scholar] [CrossRef]
- Zuhanda, M.K.; Hasibuan, S.A.R.S.; Napitupulu, Y.Y.; Hartono. An exact and metaheuristic optimization framework for solving Vehicle Routing Problems with Shipment Consolidation using population-based and Swarm Intelligence. Decis. Anal. J. 2024, 13, 100517. [Google Scholar] [CrossRef]
- Lopes, J.; Guimarães, T.; Duarte, J.; Santos, M. Enhancing Surgery Scheduling in Health Care Settings with Metaheuristic Optimization Models: Algorithm Validation Study. JMIR Med. Inform. 2025, 13, e57231. [Google Scholar] [CrossRef]
- Mzili, T.; Mzili, I.; Riffi, M.E.; Kurdi, M.; Ali, A.H.; Pamucar, D.; Abualigah, L. Enhancing COVID-19 vaccination and medication distribution routing strategies in rural regions of Morocco: A comparative metaheuristics analysis. Inform. Med. Unlocked 2024, 46, 101467. [Google Scholar] [CrossRef]
- Mostafaei, K.; Yousefi, M.; Kreuzer, O.; Kianpour, M.N. Simulation-based mineral prospectivity modeling and Gray Wolf optimization algorithm for delimiting exploration targets. Ore Geol. Rev. 2025, 177, 106458. [Google Scholar] [CrossRef]
- Canales Bustos, L.; Santibañez González, E.; Candia Véjar, A. A multi objective optimization model for the design of an effective decarbonized supply chain in mining. Int. J. Prod. Econ. 2017, 193, 449–464. [Google Scholar] [CrossRef]
- Moradi, N.; Mafakheri, F.; Wang, C. Set covering routing problems: A review and classification scheme. Comput. Ind. Eng. 2024, 198, 110730. [Google Scholar] [CrossRef]
- Karp, R.M. On the computational complexity of combinatorial problems. Networks 1975, 5, 45–68. [Google Scholar] [CrossRef]
- Šarac, D.; Kopić, M.; Mostarac, K.; Kujačić, M.; Jovanović, B. Application of set covering location problem for organizing the public postal network. PROMET-Traffic Transp. 2016, 28, 403–413. [Google Scholar] [CrossRef]
- Mesquita, M.; Paias, A. Set partitioning/covering-based approaches for the integrated vehicle and crew scheduling problem. Comput. Oper. Res. 2008, 35, 1562–1575. [Google Scholar] [CrossRef]
- Crawford, B.; Soto, R.; Monfroy, E. Cultural algorithms for the set covering problem. In Proceedings of the Advances in Swarm Intelligence: 4th International Conference, ICSI 2013, Harbin, China, 12–15 June 2013; Proceedings, Part II 4. Springer: Berlin/Heidelberg, Germany, 2013; pp. 27–34. [Google Scholar]
- Wang, Y.; Pan, S.; Al-Shihabi, S.; Zhou, J.; Yang, N.; Yin, M. An improved configuration checking-based algorithm for the unicost set covering problem. Eur. J. Oper. Res. 2021, 294, 476–491. [Google Scholar] [CrossRef]
- Wu, C.; Murray, A.T. Optimizing public transit quality and system access: The multiple-route, maximal covering/shortest-path problem. Environ. Plan. B Plan. Des. 2005, 32, 163–178. [Google Scholar] [CrossRef]
- Wang, R.L.; Okazaki, K. An improved genetic algorithm with conditional genetic operators and its application to set-covering problem. Soft Comput. 2007, 11, 687–694. [Google Scholar] [CrossRef]
- Crawford, B.; Soto, R.; Monfroy, E.; Palma, W.; Castro, C.; Paredes, F. Parameter tuning of a choice-function based hyperheuristic using particle swarm optimization. Expert Syst. Appl. 2013, 40, 1690–1695. [Google Scholar] [CrossRef]
- Ren, Z.G.; Feng, Z.R.; Ke, L.J.; Zhang, Z.J. New ideas for applying ant colony optimization to the set covering problem. Comput. Ind. Eng. 2010, 58, 774–784. [Google Scholar] [CrossRef]
- Caserta, M. Tabu search-based metaheuristic algorithm for large-scale set covering problems. In Metaheuristics: Progress in Complex Systems Optimization; Springer: Boston, MA, USA, 2007; pp. 43–63. [Google Scholar]
- Naji-Azimi, Z.; Toth, P.; Galli, L. An electromagnetism metaheuristic for the unicost set covering problem. Eur. J. Oper. Res. 2010, 205, 290–300. [Google Scholar] [CrossRef]
- Sundar, S.; Singh, A. A hybrid heuristic for the set covering problem. Oper. Res. 2012, 12, 345–365. [Google Scholar] [CrossRef]
- Reyes, V.; Araya, I. A GRASP-based scheme for the set covering problem. Oper. Res. 2021, 21, 2391–2408. [Google Scholar] [CrossRef]
- Fu, Y.; Liu, D.; Chen, J.; He, L. Secretary bird optimization algorithm: A new metaheuristic for solving global optimization problems. Artif. Intell. Rev. 2024, 57, 1–102. [Google Scholar] [CrossRef]
- Cochran, J.K.; Uribe, A.M. A set covering formulation for agile capacity planning within supply chains. Int. J. Prod. Econ. 2005, 95, 139–149. [Google Scholar] [CrossRef]
- Nam, S.; Shen, H.; Ryu, C.; Shin, J.G. SCP-Matrix based shipyard APS design: Application to long-term production plan. Int. J. Nav. Archit. Ocean Eng. 2018, 10, 741–761. [Google Scholar] [CrossRef]
- Mol, G.; Ermiş, M. Solving the Large-Scale Crew Pairing Problem in the Airline Industry Using the Column Generation Method. In Proceedings of the International Symposium for Production Research, Budva, Montenegro, 9–11 October 2024; Springer: Cham, Switzerland, 2024; pp. 333–348. [Google Scholar]
- Borne, P.; Tangour, F. Metaheuristics for the Optimization in Planning and Scheduling. IFAC Proc. Vol. 2007, 40, 1–7. [Google Scholar] [CrossRef]
- Niu, B.; Wang, Y.; Liu, J.; Yue, G.X.G. Path planning for unmanned aerial vehicles in complex environment based on an improved continuous ant colony optimisation. Comput. Electr. Eng. 2025, 123, 110034. [Google Scholar] [CrossRef]
- Yang, X.; Li, H.; Huang, Y. An adaptive dynamic multi-swarm particle swarm optimization with stagnation detection and spatial exclusion for solving continuous optimization problems. Eng. Appl. Artif. Intell. 2023, 123, 106215. [Google Scholar] [CrossRef]
- Becerra-Rozas, M.; Lemus-Romani, J.; Cisternas-Caneo, F.; Crawford, B.; Soto, R.; Astorga, G.; Castro, C.; García, J. Continuous metaheuristics for binary optimization problems: An updated systematic literature review. Mathematics 2022, 11, 129. [Google Scholar] [CrossRef]
- Crawford, B.; Soto, R.; Astorga, G.; García, J.; Castro, C.; Paredes, F. Putting continuous metaheuristics to work in binary search spaces. Complexity 2017, 2017, 8404231. [Google Scholar] [CrossRef]
- Lanza-Gutierrez, J.M.; Crawford, B.; Soto, R.; Berrios, N.; Gomez-Pulido, J.A.; Paredes, F. Analyzing the effects of binarization techniques when solving the set covering problem through swarm optimization. Expert Syst. Appl. 2017, 70, 67–82. [Google Scholar] [CrossRef]
- Cormen, T.H.; Leiserson, C.E.; Rivest, R.L.; Stein, C. Introduction to Algorithms; MIT Press: Cambridge, MA, USA, 2022. [Google Scholar]
- Beasley, J.E.; Jörnsten, K. Enhancing an algorithm for set covering problems. Eur. J. Oper. Res. 1992, 58, 293–300. [Google Scholar] [CrossRef]
- Kennedy, J.; Eberhart, R.C. A discrete binary version of the particle swarm algorithm. In Proceedings of the 1997 IEEE International Conference on Systems, Man, and Cybernetics. Computational Cybernetics and Simulation, Orlando, FL, USA, 12–15 October 1997; IEEE: Piscataway, NJ, USA, 1997; Volume 5, pp. 4104–4108. [Google Scholar]
- Emary, E.; Zawbaa, H.M.; Hassanien, A.E. Binary grey wolf optimization approaches for feature selection. Neurocomputing 2016, 172, 371–381. [Google Scholar] [CrossRef]
- Houssein, E.H.; Saeed, M.K.; Hu, G.; Al-Sayed, M.M. Metaheuristics for solving global and engineering optimization problems: Review, applications, open issues and challenges. Arch. Comput. Methods Eng. 2024, 31, 4485–4519. [Google Scholar] [CrossRef]
- Crawford, B.; Soto, R.; Lemus-Romani, J.; Becerra-Rozas, M.; Lanza-Gutiérrez, J.M.; Caballé, N.; Castillo, M.; Tapia, D.; Cisternas-Caneo, F.; García, J.; et al. Q-learnheuristics: Towards data-driven balanced metaheuristics. Mathematics 2021, 9, 1839. [Google Scholar] [CrossRef]
- Lemus-Romani, J.; Becerra-Rozas, M.; Crawford, B.; Soto, R.; Cisternas-Caneo, F.; Vega, E.; Castillo, M.; Tapia, D.; Astorga, G.; Palma, W.; et al. A novel learning-based binarization scheme selector for swarm algorithms solving combinatorial problems. Mathematics 2021, 9, 2887. [Google Scholar] [CrossRef]
- Singh, P. The Fast Forward Quantum Optimization Algorithm: A study of convergence and novel unconstrained optimization. Comput. Methods Appl. Mech. Eng. 2025, 443, 118039. [Google Scholar] [CrossRef]
- Mann, H.B.; Whitney, D.R. On a test of whether one of two random variables is stochastically larger than the other. Ann. Math. Stat. 1947, 18, 50–60. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).