Abstract
Many families of binary nonlinear codes (e.g., Kerdock, Goethals, Delsarte–Goethals, Preparata) can be very simply constructed from linear codes over the ring (ring of integers modulo 4), by applying the Gray map to the quaternary symbols. Generalized Kerdock codes represent an extension of classical Kerdock codes to the ring. In this paper, we develop two novel soft-input decoders, designed to exploit the unique structure of these codes. We introduce a novel soft-input ML decoding algorithm and a soft-input soft-output MAP decoding algorithm of generalized Kerdock codes, with a complexity of , where N is the length of the code, that is, the number of symbols in a codeword. Simulations show that our novel decoders outperform the classical lifting decoder in terms of error rate by some 5 dB.
MSC:
94B35
1. Introduction
Context and motivation. It is well known that linear codes over the integer ring modulo (the ring) are the natural linear codes for -ary phase modulation (-PSK) [1]. Additionally, Hammons et al. demonstrated in [2] that certain notable binary nonlinear codes, recognized for their desirable characteristics, can be derived from quaternary codes (codes over ) through the application of the Gray map. These results have led to an increased interest in designing linear codes over finite rings. Several extensions of these codes to (where p is a prime and S is a positive integer) were also developed [1,3,4,5,6,7,8,9,10,11,12]. Solé [3] suggested in 1988 that p-adic cyclic codes should be investigated [4]. The generalization of binary duadic codes to the setting of Abelian codes over the ring was presented in [5]. Double circulant self-dual codes over were investigated in [6]. Generalized Kerdock and Delsarte–Goethals codes over the ring (an extension of linear Kerdock and Delsarte–Goethals codes to ) were introduced in [7]. Convolutional codes over rings were discussed in [1,8,9], and LDPC codes over rings were investigated in [10,11,12].
Codes over rings were used in classical coding systems because of their rate properties [13,14,15], while in today’s systems, they are considered for applications with great secrecy and reliability [16,17] requirements. On the other hand, modern codes over rings are being used to improve bandwidth efficiency [10] and to better combat phase noise [11,12] in modern wireless systems. Quaternary Kerdock codes were also used to design MIMO codebooks (i.e., a finite set of precoders shared by the transmitter and the receiver) for limited-feedback precoded MIMO systems [18,19]. The proposed Kerdock codebook was shown to have systematic construction, reduced storage, and reduced online search computation [18,19]. It is also possible to develop quantum error correction and quantum communication codes from codes over rings, as discussed in [20,21].
Research in the field of ring-based code decoding has been a significant topic for many years, during which numerous algorithms for both hard and soft decision decoding, designed to exploit the unique and rich structure of codes over rings, have been introduced. A detailed overview of different decoding algorithms for codes over rings is given in Section 2. Classical codes over rings are interesting as component codes in product and turbo coding schemes [16,22,23], but one of the main obstacles to their adoption in modern coding systems is the lack of efficient SISO decoding algorithms. As far as we are aware, generalized Kerdock codes do not yet have any soft decoders specifically designed to exploit their unique structure, so the main objective of this study is to address this gap by presenting maximum likelihood (ML) and maximum a posteriori (MAP) decoding algorithms for them. Furthermore, the MAP decoding algorithm is an SISO algorithm, so it allows the use of these codes in modern coding systems. These algorithms will also allow us to develop and evaluate reduced-complexity suboptimal decoding algorithms for generalized Kerdock codes and other related code families in the future.
Contribution. In our previous paper [24], we developed an SISO MAP decoding algorithm of linear Kerdock codes with the complexity of , where N is the code length of a quaternary code (i.e., the number of quaternary symbols in a codeword). Here, we extend this result to the family of generalized Kerdock codes. In this paper, novel ML and MAP decoding algorithms with a complexity of (where N is the code length of a code) are developed and presented. To the best of our knowledge, these are the first such decoding algorithms for generalized Kerdock codes.
Paper organization. The rest of this manuscript is organized into five individual sections. The literature overview is given in Section 2. Section 3 provides the necessary preliminaries. Section 4 introduces the novel decoding algorithms. Simulation results are presented in Section 5. Section 6 concludes the paper.
Notation. In this paper, we employ the same notation as in [24]. We use bold letters to denote module elements, and by extension vectors, as every vector space is by definition a free module. We use the standard function notation for polynomials. We denote the i-th component of a module element or a polynomial (where Z is a placeholder variable) as . Let and be two elements of equal length N. Then, the Hadamard (pointwise) product is defined as , and the inner product is defined as . We use uppercase letters to represent matrices, with indicating the n-th row of a matrix X. For convenience, let represent an element of all ones. We denote the probability of x as and the conditional probability of x given y as . We use the standard blackboard bold letters to represent sets of numbers and their associated rings/fields, i.e., represents the set of complex numbers, represents the set of real numbers, and represents the set of integers. The set of integers modulo n is denoted as . Given a set , represents the Cartesian square (i.e., the Cartesian product of with itself), and represents the N-ary Cartesian power of . We use cursive letters to represent codes and other sets. Additional notation will be introduced as and when it is utilized throughout the paper.
2. Literature Overview
A variety of strategies have been used in designing decoders for codes over rings, as mentioned in [25]. These include the algebraic (syndrome) decoding approach [26], the lifting decoder technique, introduced in [27] and extended in [28], the coset decomposition approach [29], and the permutation decoding [25,30,31]. Several algebraic decoders of codes over rings were presented in [2,32,33,34,35]. A lifting decoding scheme was introduced in [27,28]. This algorithm works by sequentially applying the hard decision decoding algorithm of a corresponding code to the appropriate p-ary projection of the input and canceling a part of the noise at each step. In this manner, the decoding algorithm is lifted to work with the corresponding code. This is a general hard decision decoding algorithm that can be applied to the generalized Kerdock codes. A simple bitwise APP decoding algorithm of linear codes, based on the lifting decoding scheme, was proposed in [24]. It was shown in [24] that in the case of the classical Kerdock and Preparata codes, this decoder has a complexity of . The Chase decoding of codes based on the lifting decoder technique was proposed in [36,37]. The coset decomposition approach consists of partitioning the code into the subcode and its coset and works for both linear and nonlinear codes. A SISO MAP decoding algorithm of linear Kerdock and Preparata codes, based on the coset decomposition technique, was introduced in [24]. A similar approach was used to develop an ML decoding algorithm, of the same complexity, for quaternary Kerdock codes in [2,38]. Following the coset decomposition strategy, Davis and Jedwab, in [13], introduced two distinct algorithms for the decoding of RM-like codes over rings of characteristic 2. The maximum a posteriori (MAP) decoding of linear codes is usually performed via the Bahl–Cocke–Jelinek–Raviv (BCJR) algorithm—a trellis-based MAP decoder, introduced in [39]. The structure and complexity of the trellis diagram of the classical Kerdock and Preparata codes were investigated in [40] and [41], respectively. The complexity of the trellis-based approach is higher than that of the MAP decoder in [24]. For LDPC codes over rings, a modified message passing is generally used [10,42].
3. System Model
Integer Modulo Rings. Let operators + and · represent addition and multiplication in . Every has a unique dyadic expansion (representation)
Using the notation introduced in [27], let , , represent the projection of onto the ring , defined as
where the first equality follows from the fact that the remainder when dividing by is defined by the first s terms of the dyadic expansion, i.e.,
It is clear that and for all .
It is easy to see that for every positive integer , every element is also an element of . Notice that multiplying some number by , , is equivalent to first projecting the number z onto the and then multiplying it with , where the multiplication is conducted in , i.e., .
Additionally, given and some ,
where ⊕ represents addition in .
Similarly, we have
where ⊗ represents multiplication in .
Using these relationships, we can formally define a natural ring epimorphism [27] as
for . Additionally, for , there exists a group embedding
with the image . The unique preimage of an element is denoted by [27].
Galois Rings. Let represent a Galois ring of characteristic and order . It can be defined as a quotient ring
where represents a polynomial ring over and is a monic polynomial of degree d that is irreducible over (i.e., it does not factor as a product of nontrivial polynomials). This means that the elements of can be represented as polynomials over , of degree at most d, and addition and multiplication are performed modulo the polynomial . The polynomial may be found using Graeffe’s method [2], which is used for finding a polynomial over whose roots are the S-th power of the roots of a corresponding polynomial over .
Let be a primitive irreducible polynomial of degree d. There exists a unique monic polynomial of degree d such that , and divides , where [2]. Following Graeffe’s method, we first divide the into polynomials and , such that , and contains only even powers, while contains only odd powers. Polynomial is given by
We can repeat this process multiple times in order to obtain for some .
Example 1.
Consider the polynomial . We divide into
and
As , we have
where is used to ensure that we have a monic polynomial. In both cases, we have . We can repeat this procedure to obtain
Notice that , for any positive integer . This follows directly from the construction method, as is obtained from , which is obtained from , i.e., .
We can extend the previous integer modulo ring relationships to Galois rings. Given a ring element , let
where is the Galois ring generated by the monic irreducible polynomial . This is a trivial extension that follows from the fact that the modulus operation is applied elementwise. Similarly, we have
Moreover, for every fixed d, there is a ring homomorphism (i.e., a function that preserves the ring operations)
for each S, having kernel [43]. We call this homomorphism a natural projection of ring onto the ring , and we define it as
Notice that the ring
is equivalent to the polynomial ring modulo monic irreducible polynomial . This definition can easily be extended to the projection of the ring onto the ring , denoted , for some .
Let + and · denote addition and multiplication in , and let ⊕ and ⊗ denote addition and multiplication in for some . Then, the following relationships naturally follow from the definition of projection:
The natural projection maps the ring to the Galois field , generated by the primitive polynomial .
Every Galois ring has a primitive element, , such that . Given the Teichmüller set , every element has a unique “multiplicative” representation [7]
The Frobenius map is the ring automorphism defined as [2,7]
The relative trace from to is defined as [2,7]
Notice that represents the usual trace from to , defined as
Some useful properties of the relative trace are the following [44]:
- , for all ;
- for all , ;
- , for all .
The projection of also has a unique “multiplicative” representation, given by
where is the root of the monic irreducible polynomial and . Given the canonical projection homomorphism , defined as the mod-2 reduction, the following commutative relationships can easily be verified [2,44]:
Generalized Kerdock Codes. The generalized Kerdock code over , of dimension and length , introduced in [7], is defined as a set of all valid codewords. A sequence is a codeword in if and only if, for some and ,
with a standard convention of .
The information pair represents the information sequence of length (consisting of d coefficients of the polynomial plus symbol ).
Theorem 1.
The binary image of the generalized Kerdock code is the first-order Reed–Muller code of length , the code.
Proof.
The quaternary projection of the code is given by
where is applied componentwise. Every code symbol , , is given by
Using the properties of the projection map and the relationship between the natural projection and the relative trace, Equation (7) can be rewritten as
where is the root of , is an element of the Galois ring , generated by the monic irreducible polynomial , and . The operator ⊗ represents multiplication in . This is the definition of the quaternary Kerdock code, as presented in [2].
The projection of the generalized Kerdock code onto is the corresponding classical quaternary Kerdock code. It is well known that the binary image of the Kerdock code (the projection) is the code [2,24]. This is also true for the generalized Kerdock code, i.e., . □
Permuting the coordinates of a code produces an equivalent code [26]. Consider a permutation , where . For any codeword , we can define a codeword that belongs to the equivalent generalized Kerdock code defined by . Let be generated by an information pair . Then, is defined as
If the code is constructed by taking the rows of the binary Sylvester-type Hadamard matrix (a binary matrix obtained from a regular Sylvester-type Hadamard matrix, by replacing the 1’s with binary 0’s and ’s with binary 1’s) and their complements as codewords, it is possible to use the fast Hadamard transform for decoding [24,26]. In the remainder of the paper, we will assume that the permutation is chosen so that the associated binary code of the Kerdock code is the code, constructed in this way. This makes applying the fast Hadamard transform possible, significantly reducing the decoding complexity. Permutation can be found beforehand using the Hungarian algorithm [45] and does not affect the decoding complexity of the proposed algorithms.
Channel model and decoding. Let , , be a random -PSK-modulated codeword of a generalized Kerdock code , transmitted over the AWGN channel. The modulation mapping is defined as
and it naturally extends to vectors. Furthermore,
Let be the output of the complex AWGN channel, defined by the conditional probability
where represents the modulus of a complex number.
If all codewords are equally likely and the channel is memoryless, the ML decoder is optimal in terms of minimizing the word-error probability. Given the channel output , the ML decoder proceeds to find the codeword that maximizes the , where , i.e.,
It is well known that the ML decoder can be implemented as the minimum distance decoder,
where represents the norm of a complex vector.
Consider the term in Equation (10),
where represents the complex conjugate and ℜ represents the function that extracts the real part of a complex number. By substituting (11) in Equation (10), we obtain
The terms and can be ignored ( is fixed, while is the same for all codewords because of the PSK modulation), so the ML decoder can be implemented as the correlation decoder, where we compute the correlation between the complex conjugate of all possible modulated codewords and the channel output and we select the codeword that corresponds to the highest correlation, i.e.,
where , and the last equality follows from the fact that the sum of the real part of complex numbers is equivalent to the real part of the sum of complex numbers.
Example 2.
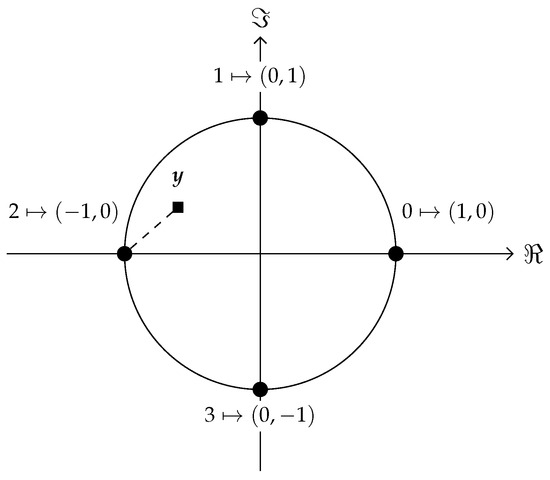
Consider the transmission of a single quaternary symbol over the AWGN channel. As , we select the QPSK modulation scheme, shown in Figure 1, for transmission.

Figure 1.
The constellation diagram of the used QPSK modulation.
For simplicity, the complex numbers are represented as points in the Euclidean plane, where the first coordinate corresponds to the real part of a complex number, and the second coordinate corresponds to the imaginary part of a complex number.
The modulated symbol is sent over the AWGN channel, where Gaussian noise is added to every coordinate independently, and the channel output is received. At the receiver, we compute the squared Euclidean distance between the channel output and every constellation point and select the closest one, i.e., we compute
Notice that when using the complex notation, this decision rule is given by the real part of the product of the complex channel output and the conjugate of a complex constellation symbol.
The MAP decoder operates on a bitwise basis and is optimal in terms of minimizing the bit-error probability. Given the corresponding channel output , the MAP decoder proceeds to find [24,46]
where represents the set of all codewords that have symbol in position j, for all . The MAP decision is by definition
The MAP decoder is well suited for use in a concatenated coding scheme, where we exchange soft messages between different coding blocks.
4. Decoding Algorithms
Let be the linear subcode of the generalized Kerdock code that does not contain the all-one codeword. The size of the code is .
Let be the codeword corresponding to the information sequence given by the components of the polynomial . Then,
where . Notice that the vector is a codeword of the -associated code of , i.e., any codeword of , scaled by , is also a codeword of . As all codewords of the linear generalized Kerdock code form an additive Abelian group, then
for all and .
For convenience, we define three auxiliary matrices, , , and , together with their row sets (sets of row elements),
and
Note that
and
The rows of the matrix are generated as codewords of the code, scaled by .
4.1. ML Decoding Algorithm
The ML decoder begins by calculating the correlation coefficient of the received channel output, , with the complex conjugate of each possible modulated codeword. After that, the decoder selects the codeword with the largest correlation coefficient.
For every possible information pair , let the correlation coefficient between the corresponding codeword and the channel output be defined as
There are possible information pairs, and the computation of the correlation coefficient, using Equation (14), has complexity . The total complexity, when using the brute-force approach, is .
After substituting Equation (6) in Equation (14), we obtain
where the last equality follows from (9). Using the definition in (12), we obtain
Let and
Finally, the correlation coefficient is given by
The correlation coefficient can be viewed as times the fast Hadamard transform (FHT) [2,24] of the vector , . The complexity of applying the FHT to a vector of length N is (note that we compute N correlation coefficients in parallel using the FHT), and we need to compute the FHT for every possible vector .
After this, we search for the correlation coefficient with the largest real part [2], and we output the corresponding codeword. This concludes the algorithm.
Implementation of the ML decoder. Here, we provide a brief rundown of the primary steps in the ML algorithm. Let be a complex matrix of size , with rows , . Furthermore, let be the Sylvester-type Hadamard matrix [26].
Given the channel output , the ML decoder first generates the correlation matrix , with rows
where ℜ is applied componentwise and the row index i is calculated as , , . Matrix R can be generated with complexity , as there are vectors for which we have to compute N correlation coefficients using the FHT. Let be the largest correlation coefficient, which can be found with complexity . Then, the ML decoder outputs the codeword
where , , and . It is clear that the complexity of this decoder is .
4.2. MAP Decoding Algorithm
The MAP decoding algorithm follows the group algebra description of the MAP decoder introduced in [46] and used in [24] to develop the MAP decoder of the quaternary Kerdock and Preparata codes.
Similarly as in [24], let be a set of all polynomials over , modulo , where Z is a dummy variable. Given a polynomial and a monomial , , using a simple change of variable, we have
We start the decoding process by calculating the vector of log-likelihoods , with
where is the n-th component of the channel output .
For every codeword , , we compute
As is a codeword of the code, the expression in (16) can be interpreted as applying a modified FHT to every vector , where
This allows us to compute N different values of in parallel, i.e., instead of computing values, where every computation requires operations in , we apply the modified FHT (with complexity ) to vectors, so the total complexity is reduced from to . By the modified FHT, we assume a fast Hadamard transform applied in , which is defined in Algorithm 1. In this pseudocode, h is used as a control variable for the loop, representing the current step size in the modified FHT algorithm. Variable h starts at 1 and doubles each time, determining the pairs of elements to be combined at each stage of the transform. This ensures that first the adjacent elements are paired (the distance between them is ), and as it progressively increases, so does the distance between the pairs of elements that are combined.
| Algorithm 1 Modified fast Hadamard transform (in-place implementation) |
| Input: , Output: , 1: for ; ; do 2: for ; ; do 3: for to do 4: , , {Save current values} 5: , {Calculate new value} 6: , {Calculate new value} 7: end for 8: end for 9: end for |
Next, for every , we recompute the sums of logarithms of probabilities into products of probabilities, as follows:
Finally, we compute
where the last equality follows from the fact that
The complexity of computing one of the N components of is , so the total complexity of computing is . We can reduce the complexity of this step in a similar way as before. Notice that
which follows from (13). Notice that the computation of can now be interpreted as applying the modified FHT times and then performing a componentwise addition of the results. The complexity of this approach is now . This completes the algorithm.
Implementation of the MAP decoder. We now present a summary of the essential steps in the MAP algorithm. For convenience, we define a mapping , such that . This function can be extended to elements and matrices, by applying to every component independently [24]. Let and .
We begin the decoding procedure by computing the log-likelihood vector , using Equation (15). This can be accomplished with complexity .
Next, we compute matrix with rows
where represents the l-th row of matrix . Matrix T can be computed in steps, as we need to apply the modified FHT to vectors.
Next, we compute the likelihood matrix , with components
This can be accomplished in steps.
Let B be an matrix, with rows
where . This can be accomplished with complexity .
Finally, we form vector by summing all rows of B,
This can be performed in steps. With this, we finish the algorithm description. It is important to note that all the operations here are conducted over the polynomial ring . As the polynomials in can be realized as real vectors of the fixed length of (where is less than N in most practical use cases), the additional complexity can be treated as a constant term, so the total complexity of this algorithm is [24].
5. Simulation Results
In this section, we present the simulation results of our novel decoding algorithms and compare them to the existing techniques in terms of their error-correcting performance. As these decoders are polynomial algorithms, we limit ourselves to short-length (where code length is given as the number of symbols) codes over , , and . Let represent a generalized Kerdock code of length , over the ring , defined in terms of the irreducible monic polynomial () used to design an extension ring, as presented in Section 3. We also include some classical Kerdock codes, as they also fall into the family of the generalized Kerdock code. These codes are the code defined by , the code defined by , the code defined by , the code defined by , the code defined by , and the code defined by .
All simulations were conducted for the additive white Gaussian noise (AWGN) channel. Additionally, every code was coupled with a corresponding -PSK modulation, as there exists a natural straightforward mapping of code symbols onto the PSK symbols (Equation (8)). We assessed the performance of our decoding algorithms by estimating the frame error rate (FER) and symbol error rate (SER) as a function of energy per bit to noise power spectral density ratio () and comparing it to the classical lifting decoder [27]. The classical lifting decoder can be applied to generalized Kerdock codes without modification, but it has a higher error probability, as it is a suboptimal hard-input hard-output (HIHO) decoder. This decoder was implemented as an S-stage decoder, where each stage uses the minimum Hamming distance decoder of the associated binary code. As the minimum Hamming distance decoder of the code can be implemented with a complexity of , the total complexity of the classical lifting decoder is . This complexity is significantly lower than that of the novel algorithms developed in this paper, but so is its error-correcting performance. FER and SER were estimated using the Monte Carlo simulation method with a relative precession , for a range of points, with a step of .
We assume that the ML decoder will make a mistake if the correct codeword is further away from the channel output than some other codeword (e.g., the output of some not-necessarily-optimal decoding algorithm) in terms of the Euclidean distance [24]. We can simulate the lower bound on the ML decoding by counting the number of times the Euclidean distance between the channel output and the correct codeword is greater than the distance between the channel output and the decoded codeword. This bound becomes tight as increases. We compare the FER performance of our novel ML and MAP decoders with the ML bound (Figure 2) and see that they perfectly coincide. This indicates that our novel algorithms are optimal in terms of FER, as was expected.
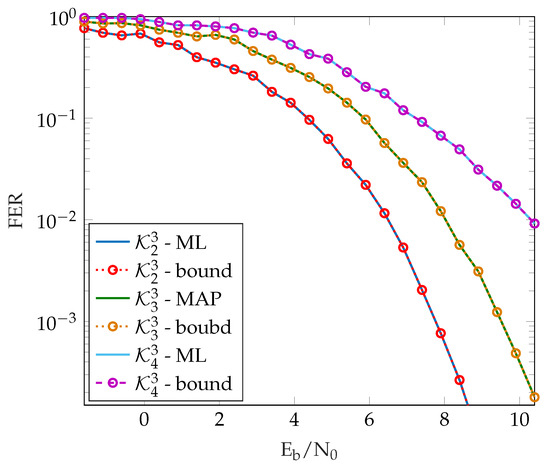
Figure 2.
FER comparison of the ML decoding algorithm with an ML lower bound for different generalized Kerdock codes.
Figure 3 presents the FER of various generalized Kerdock codes using the novel ML decoder, and Figure 4 shows the SER of different generalized Kerdock codes using the novel MAP decoder. We notice that the error-correcting performance improves with code length, while it decreases with base ring size. This is expected behavior, as the error-correcting performance of the code should increase with N, while the increase in the constellation size means that the modulation symbols are closer together and are more susceptible to noise, and this leads to an increase in the probability of error.
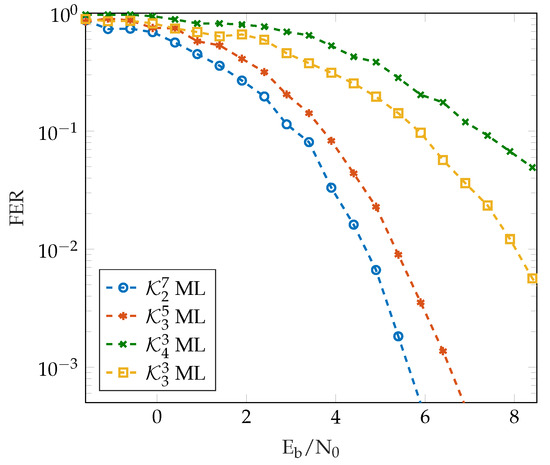
Figure 3.
FER comparison of the ML decoding for different generalized Kerdock codes.
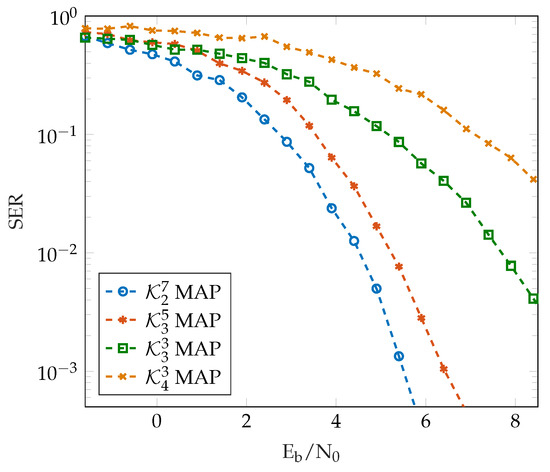
Figure 4.
SER comparison of the MAP decoding for different generalized Kerdock codes.
Figure 5 shows the SER of different generalized Kerdock codes using the novel MAP decoder and the classical lifting decoder. We see in Figure 5 that the MAP decoder exhibits a gain of some when compared to the classical lifting decoder. This is expected, as the novel MAP decoder is an optimal SISO decoding algorithm, while the lifting decoder is a suboptimal HIHO decoding algorithm.
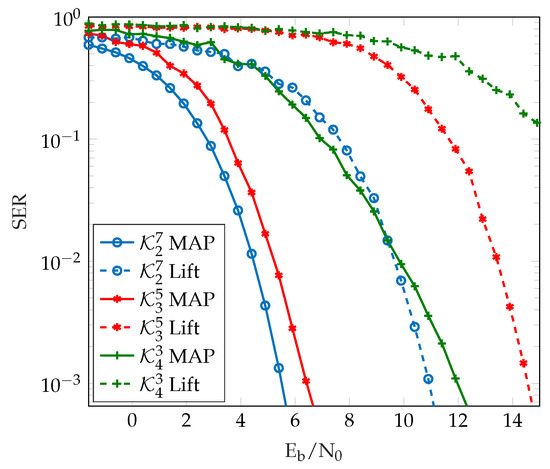
Figure 5.
SER comparison of the MAP and the lifting decoder algorithms for different generalized Kerdock codes.
6. Conclusions
In this manuscript, we presented two novel optimal algorithms for the decoding of generalized Kerdock codes. Their complexity is , and although they are polynomial complexity algorithms, they can be used as a starting point for developing and a benchmark for evaluating the performance of suboptimal decoders. Furthermore, as the MAP decoder is an SISO algorithm, it allows the use of small-length generalized Kerdock codes in modern coding systems as component codes. The novel decoding algorithms were compared with the classical lifting decoding algorithm in terms of error-correcting performance, and it was shown that they achieved a gain of about . In our future work, we will focus on reducing the complexity below that of the MAP decoder without significantly compromising its error-correcting efficiency. The lifting technique is a powerful technique that can be combined with the MAP decoder and used to develop novel suboptimal SISO decoders. We will also use generalized Kerdock codes (and other related codes) as components in modern coding schemes, such as the turbo-product scheme, braided construction, coded modulation schemes, and many others.
Author Contributions
All authors have contributed equally to the paper. All authors have read and agreed to the published version of the manuscript.
Funding
This work was in part supported by the European Union Horizon Europe research and innovation program under the grant agreement No. 101086387 and the Secretariat for Higher Education and Scientific Research of the Autonomous Province of Vojvodina through the project “Visible light technologies for indoor sensing, localization and communication in smart buildings” (142-451-3511/2023).
Data Availability Statement
No new data were created or analyzed in this study. Data sharing is not applicable to this article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Massey, J.; Mittelholzer, T. Convolutional codes over rings. In Proceedings of the 4th joint Swedish-Soviet International Workshop on Information Theory, Gotland, Sweden, 27 August–1 September 1989. [Google Scholar]
- Hammons, A.R.; Kumar, P.V.; Calderbank, A.R.; Sloane, N.J.A.; Sole, P. The Z/sub 4/-linearity of Kerdock, Preparata, Goethals, and related codes. IEEE Trans. Inf. Theory 1994, 40, 301–319. [Google Scholar] [CrossRef]
- Solé, P. Open problem 2: Cyclic codes over rings and p-adic fields. In Coding Theory and Applications, Proceedings of the Coding Theory 1988, Toulon, France, 2–4 November 1988; Cohen, G., Wolfmann, J., Eds.; Springer: Berlin/Heidelberg, Germany, 1989; p. 329. [Google Scholar]
- Calderbank, A.R.; Sloane, N.J.A. Modular and p-adic cyclic codes. Des. Codes Cryptogr. 1995, 6, 21–35. [Google Scholar] [CrossRef]
- Ling, S.; Sole, P. Duadic codes over Z/sub 2k/. IEEE Trans. Inf. Theory 2001, 47, 1581–1588. [Google Scholar] [CrossRef]
- Gulliver, T.; Harada, M. Double circulant self-dual codes over Z/sub 2k/. IEEE Trans. Inf. Theory 1998, 44, 3105–3123. [Google Scholar] [CrossRef]
- Carlet, C. 2k-linear codes. IEEE Trans. Inf. Theory 1998, 44, 1543–1547. [Google Scholar] [CrossRef]
- Mittelholzer, T. Convolutional codes over rings and the two chain conditions. In Proceedings of the IEEE International Symposium on Information Theory, Ulm, Germany, 29 June–4 July 1997; p. 285. [Google Scholar] [CrossRef]
- Napp, D.; Pinto, R.; Toste, M. Column Distances of Convolutional Codes Over pr. IEEE Trans. Inf. Theory 2019, 65, 1063–1071. [Google Scholar] [CrossRef]
- Sridhara, D.; Fuja, T. LDPC codes over rings for PSK modulation. IEEE Trans. Inf. Theory 2005, 51, 3209–3220. [Google Scholar] [CrossRef]
- Ninacs, T.; Matuz, B.; Liva, G.; Colavolpe, G. Non-binary LDPC coded DPSK modulation for phase noise channels. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Ninacs, T.; Matuz, B.; Liva, G.; Colavolpe, G. Short Non-Binary Low-Density Parity-Check Codes for Phase Noise Channels. IEEE Trans. Commun. 2019, 67, 4575–4584. [Google Scholar] [CrossRef]
- Davis, J.A.; Jedwab, J. Peak-to-mean power control in OFDM, Golay complementary sequences, and Reed-Muller codes. IEEE Trans. Inf. Theory 1999, 45, 2397–2417. [Google Scholar] [CrossRef]
- Schmidt, K. Quaternary Constant-Amplitude Codes for Multicode CDMA. IEEE Int. Symp. Inf. Theory 2007, 55, 1824–1832. [Google Scholar] [CrossRef]
- Shakeel, I. Performance of Reed-Muller and Kerdock Coded MC-CDMA System with Nonlinear Amplifier. In Proceedings of the 2005 Asia-Pacific Conference on Communications, Perth, Australia, 3–5 October 2005; pp. 644–648. [Google Scholar]
- Amrani, O. Nonlinear Codes: The Product Construction. IEEE Trans. Commun. 2007, 55, 1845–1851. [Google Scholar] [CrossRef]
- Karp, B.; Amrani, O.; Keren, O. Nonlinear Product Codes for Reliability and Security. In Proceedings of the 2019 IEEE 4th International Verification and Security Workshop (IVSW), Rhodes, Greece, 3 October 2019; pp. 13–18. [Google Scholar]
- Inoue, T.; Heath, R.W. Kerdock codes for limited feedback MIMO systems. In Proceedings of the 2008 IEEE International Conference on Acoustics, Speech and Signal Processing, Las Vegas, NV, USA, 31 March–4 April 2008; pp. 3113–3116. [Google Scholar]
- Inoue, T.; Heath, R.W., Jr. Kerdock Codes for Limited Feedback Precoded MIMO Systems. IEEE Trans. Signal Process. 2009, 57, 3711–3716. [Google Scholar] [CrossRef]
- Güzeltepe, M.; Sarı, M. Quantum codes from codes over the ring + α. Quantum Inf. Process. 2019, 18, 365. [Google Scholar] [CrossRef]
- Güzeltepe, M.; Aytaç, N. Quantum Codes from Codes over the Ring Rq. Int. J. Theor. Phys. 2023, 62, 26. [Google Scholar] [CrossRef]
- Kim, H.; Markarian, G.; Rocha, V.C.d., Jr. Nonlinear Product Codes and Their Low Complexity Iterative Decoding. ETRI J. 2010, 32, 588–595. [Google Scholar] [CrossRef]
- Kim, H.; Markarian, G.; da Rocha, V.C., Jr. Nonlinear turbo product codes. In Proceedings of the XXV Simpósio Brasileiro de Telecomunicações, Recife, PE, Brazil, 3–6 September 2007. [Google Scholar]
- Minja, A.; Šenk, V. SISO Decoding of Linear Kerdock and Preparata Codes. IEEE Trans. Commun. 2022, 70, 1497–1507. [Google Scholar] [CrossRef]
- Barrolleta, R.; Pujol, J.; Villanueva, M. Comparing decoding methods for quaternary linear codes. Electron. Notes Discret. Math. 2016, 54, 283–288. [Google Scholar] [CrossRef]
- MacWilliams, F.; Sloane, N. The Theory of Error-Correcting Codes; Mathematical Studies; Elsevier Science: Amsterdam, The Netherlands, 1977. [Google Scholar]
- Greferath, M.; Vellbinger, U. Efficient decoding of Z/sub p/k-linear codes. IEEE Trans. Inf. Theory 1998, 44, 1288–1291. [Google Scholar] [CrossRef]
- Babu, N.S.; Zimmermann, K. Decoding of linear codes over Galois rings. IEEE Trans. Inf. Theory 2001, 47, 1599–1603. [Google Scholar] [CrossRef]
- Conway, J.; Sloane, N. Soft decoding techniques for codes and lattices, including the Golay code and the Leech lattice. IEEE Trans. Inf. Theory 1986, 32, 41–50. [Google Scholar] [CrossRef]
- Barrolleta, R.D.; Villanueva, M. Partial permutation decoding for binary linear and Z4-linear Hadamard codes. Des. Codes Cryptogr. 2018, 86, 569–586. [Google Scholar] [CrossRef]
- Barrolleta, R.D.; Villanueva, M. Partial Permutation Decoding for Several Families of Linear and Z4-Linear Codes. IEEE Trans. Inf. Theory 2019, 65, 131–141. [Google Scholar] [CrossRef]
- Helleseth, T.; Kumar, P.V. The algebraic decoding of the Z/sub 4/-linear Goethals code. IEEE Trans. Inf. Theory 1995, 41, 2040–2048. [Google Scholar] [CrossRef]
- Byrne, E.; Fitzpatrick, P. Hamming metric decoding of alternant codes over Galois rings. IEEE Trans. Inf. Theory 2002, 48, 683–694. [Google Scholar] [CrossRef]
- Rong, C.; Helleseth, T.; Lahtonen, J. On algebraic decoding of the Z/sub 4/-linear Calderbank-McGuire code. IEEE Trans. Inf. Theory 1999, 45, 1423–1434. [Google Scholar] [CrossRef]
- Ranto, K. On algebraic decoding of the Z/sub 4/-linear Goethals-like codes. IEEE Trans. Inf. Theory 2000, 46, 2193–2197. [Google Scholar] [CrossRef]
- Armand, M.A. Chase decoding of linear Z/sub 4/ codes. Electron. Lett. 2006, 42, 1049–1050. [Google Scholar] [CrossRef]
- Armand, M.A.; Halim, A.; Nallanathan, A. Chase Decoding of Linear Z4 Codes at Low to Moderate Rates. IEEE Commun. Lett. 2007, 11, 811–813. [Google Scholar] [CrossRef]
- Elia, M.; Losana, C.; Neri, F. Note on the complete decoding of Kerdock codes. IEE Proc. I Commun. Speech Vis. 1992, 139, 24–28. [Google Scholar] [CrossRef]
- Bahl, L.; Cocke, J.; Jelinek, F.; Raviv, J. Optimal decoding of linear codes for minimizing symbol error rate (Corresp.). IEEE Trans. Inf. Theory 1974, 20, 284–287. [Google Scholar] [CrossRef]
- Shany, Y.; Reuven, I.; Be’ery, Y. On the trellis representation of the Delsarte-Goethals codes. IEEE Trans. Inf. Theory 1998, 44, 1547–1554. [Google Scholar] [CrossRef]
- Shany, Y.; Be’ery, Y. The Preparata and Goethals codes: Trellis complexity and twisted squaring constructions. IEEE Trans. Inf. Theory 1999, 45, 1667–1673. [Google Scholar] [CrossRef]
- Davey, M.; MacKay, D. Low density parity check codes over GF(q). In Proceedings of the 1998 Information Theory Workshop (Cat. No.98EX131), Killarney, Ireland, 22–26 June 1998; pp. 70–71. [Google Scholar] [CrossRef]
- Bini, G.; Flamini, F. Finite Commutative Rings and Their Applications; The Springer International Series in Engineering and Computer Science; Springer: New York, NY, USA, 2002. [Google Scholar]
- Sison, V. Bases of the Galois Ring GR(pr,m) over the Integer Ring Zpr. arXiv 2014, arXiv:cs.IT/1410.0289. [Google Scholar]
- Kuhn, H.W. The Hungarian method for the assignment problem. Nav. Res. Logist. Q. 1955, 2, 83–97. [Google Scholar] [CrossRef]
- Ashikhmin, A.; Litsyn, S. Simple MAP decoding of first-order Reed-Muller and Hamming codes. IEEE Trans. Inf. Theory 2004, 50, 1812–1818. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).