Abstract
IOTA is an emerging decentralized computing paradigm for developing blockchain-based Internet of Things (IoT) applications. It has the advantages of zero transaction fees, incremental scalability, and high-performance transaction rates. Despite its well-understood benefits, IOTA nodes need to withstand considerable resource costs to generate the distributed ledger. The main reason for this is that IOTA abandons the original blockchain reward mechanism and does not charge transaction fees. Therefore, in this paper we address the cost optimization issue for IOTA based on Lyapunov optimization theory. We take the first step in investigating the cost optimization problem of IOTA and exploring a new optimization scheme using Lyapunov optimization theory. Our proposed scheme enables IOTA to minimize the total cost of IOTA nodes through a computational optimization algorithm. Then, an optimized transaction rate control algorithm can be designed based on the large deviation theory to reduce orphan tangles that waste computational costs. In addition, we define and deduce the effective width of the tangle to monitor the total throughput and reduce the time spent on cost optimization to avoid unnecessary waste of resources. Lastly, a comprehensive theoretical analysis and simulation experiments demonstrate that the proposed strategy is both efficient and practical.
MSC:
68R10; 68U99; 68V15; 68W01; 68W15; 68W40
1. Introduction
The Internet of Things (IoT) is gradually developing as an emerging global Internet-based information architecture that facilitates the exchange of goods and services [1,2,3,4]. In a traditional IoT model, service providers typically rely on centralized servers to execute tasks. However, this service model suffers from several challenges, including centralization and security issues. Therefore, the emergence of blockchain technology brings opportunities to address the challenges of IoT. IoT applications combined with blockchain technology [5,6,7,8,9,10,11] have tremendously promoted development in many fields, for example, smart cities, the fintech revolution, and decentralized machine networks; however, due to the rapid development of IoT, the traditional single-chain blockchain structure makes it difficult to meet the micropayment requirements, scalability, and high concurrency of IoT. Thus, recent studies have developed DAG-based (i.e., directed acyclic graph structure) distributed ledger technologies such as IOTA [12,13], Obyte [14], and Nano [15]. Among thees, IOTA is the most representative platform specially tailored for IoT. IOTA is a new public chain system specially designed for IoT. It provides a trust layer for any device connected to the global internet, and is mainly used for micropayments, data security transfer, and data anchoring between devices. IOTA can effectively solve the problems of centralization, low concurrency, and high transaction fees in IoT.
Unlike the miners in Bitcoin, Ethereum, or other blockchain applications, IOTA nodes must contribute their computational resources to maintain IOTA network stability for free. This is because the miners can obtain both mining rewards and transaction fees, while in IOTA these kinds of incentives are not available. With the IOTA network continuing to expand, this mechanism inevitably leads to increased costs and pressures for nodes. Therefore, widespread adoption and promotion of IOTA applications is hindered by this inherent cost constraint.
Unfortunately, there has been little research into cost optimization of IOTA. Because maximizing utility is proportional to minimizing cost, solutions must be approached indirectly through existing methods. Jay et al. [16] provided a way to maximize IOTA utility. Their idea is to analyze the critical factors underlying IOTA’s utility and to find the public item. The, they explored the relationship among these factors to achieve the purpose of maximizing the IOTA utility. However, their approach to extracting the public items is too arbitrarily. To address this issue, the design challenges of our proposed solution mainly come from three dimensions. First, an efficient scheme optimizing the computational costs of all IOTA nodes needs to be devised in order to reduce expenditure. Based on the desired scheme, the critical factors can be directly evaluated and the optimal transaction approval rate (i.e., threshold) of IOTA nodes determined in real time to reduce computational costs. Second, the desired scheme can eliminate orphan tangles, which are valid yet rejected ledgers from the IOTA network. Orphan tangles can waste a lot of computing resources and cause network congestion, imposing a performance penalty on IOTA. Third, to reduce the cost optimization frequency and avoid unnecessary wastage of resources, it is necessary to prejudge whether optimization is required each time. Thus, we are motivated to develop a scheme to reduce the cost consumption of IOTA nodes.
Our contributions. This paper presents the first study of IOTA’s cost optimization. We propose a scheme for effectively reducing the tangle generation cost of IOTA nodes while maintaining their strong robustness. Specifically, we first design a thorough optimization algorithm using Lyapunov optimization theory, resulting in an approach that can balance transaction traffic and IOTA node tolerance. In addition, we consider the situation of resource wastage caused by frequent unnecessary optimization. In particular, we appoint a committee elected from IOTA nodes to ensure the correctness of the effective width of the tangle in each time slot. In short, our contributions are listed as follows:
- We introduce Tangless, an efficient transaction cost optimization scheme for IOTA. By leveraging full-fledged optimization theories, Tangless ensures the robustness of the IOTA network with optimal costs for each node.
- We design a computational optimization algorithm based on Lyapunov optimization theory. Our design can effectively reduce the cost of IOTA nodes by introducing a Lyapunov-based optimization framework.
- We develop a transaction rate control algorithm using large deviation theory to reduce orphan transactions in the IOTA network. This algorithm helps to maintain a balance between transaction traffic and IOTA node tolerance, effectively addressing network congestion.
- To the best of our knowledge, we are the first to define and determine the effective width of the tangle, which can help to tackle the issue of cost optimization. Notably, the proposed approach can help to predict the throughput that the IOTA system can tolerate, thereby avoiding unnecessary optimization in the next time slot.
- In this paper, we offer a thorough theoretical analysis and conduct simulation experiments to validate the effectiveness of our proposed scheme.
2. Related Work
In 2015, the IOTA Foundation launched the IOTA project to address the high transaction fees, concurrency, and scalability of blockchains in IoT. The distributed ledger of IOTA is named the tangle. Subsequently, Serguei Popov [17] explained the main working principle of the tangle ledger in a white paper. With the in-depth application of IOTA in IoT, many types of research have been carried out on IOTA [18,19]. In this work, we mainly focus on cost optimization and transaction rate control.
Cost optimization. Cost optimization of blockchains is a current research hotspot [20,21]. However, the existing research primarily focuses on blockchains with a single-chain structure while IOTA is based on a DAG structure. Because IOTA does not adopt a mining incentive mechanism and does not charge transaction fees, nodes cannot receive direct economic incentives for participating in the consensus, while still being exposed to many computational costs. One outstanding challenges is to reduce the overall cost of nodes. In [16], a method for maximizing IOTA utility based on some assumptions was provided by Jay et al. In their analysis, the authors extracted public items from the factors affecting the IOTA utility for optimization. Then, they directly added these items to build the maximum utility equation. However, this approach is too far-fetched to be practical, and the solution lacks credibility. In [22], Helmer et al. focused solely on the energy consumption of IOTA. Thus, it remains necessary to find an effective way to reduce the computational cost of IOTA nodes.
Rate control. Proof-of-Work (PoW) was the first consensus mechanism in the blockchain framework. PoW decides whether a miner has the right to form a block [23]. In the IOTA platform, PoW usually exists as a rate control mechanism, and its computational effort is much lighter than that performed by typical blockchains [24]. If the rate of issuing transactions has a good match with the approving ones, then the tangle continues to grow steadily; however, a sudden surge of new incoming transactions will lead to the transaction queue in each IOTA node being overly backlogged. This can easily lead to network congestion. In addition, time-sensitive transactions may be delayed, potentially causing huge losses. The literature [24] indicates that basic PoW cannot dynamically adjust network traffic on account of the constant difficulty value. Additionally, proposed solutions using adaptive PoW based on the mana value of a node fail to prevent unfairness. Mana is a reputation value, which represents the total funds transferred within a transaction. Wesolowski [25] introduced a sustainable verifiable delay function (VDF) that can resist parallel-accelerated computing; however, due to its complex nature, VDF is not a suitable replacement for PoW. Considering these observations, there is an urgent need for a more effective rate control method.
3. Preliminaries
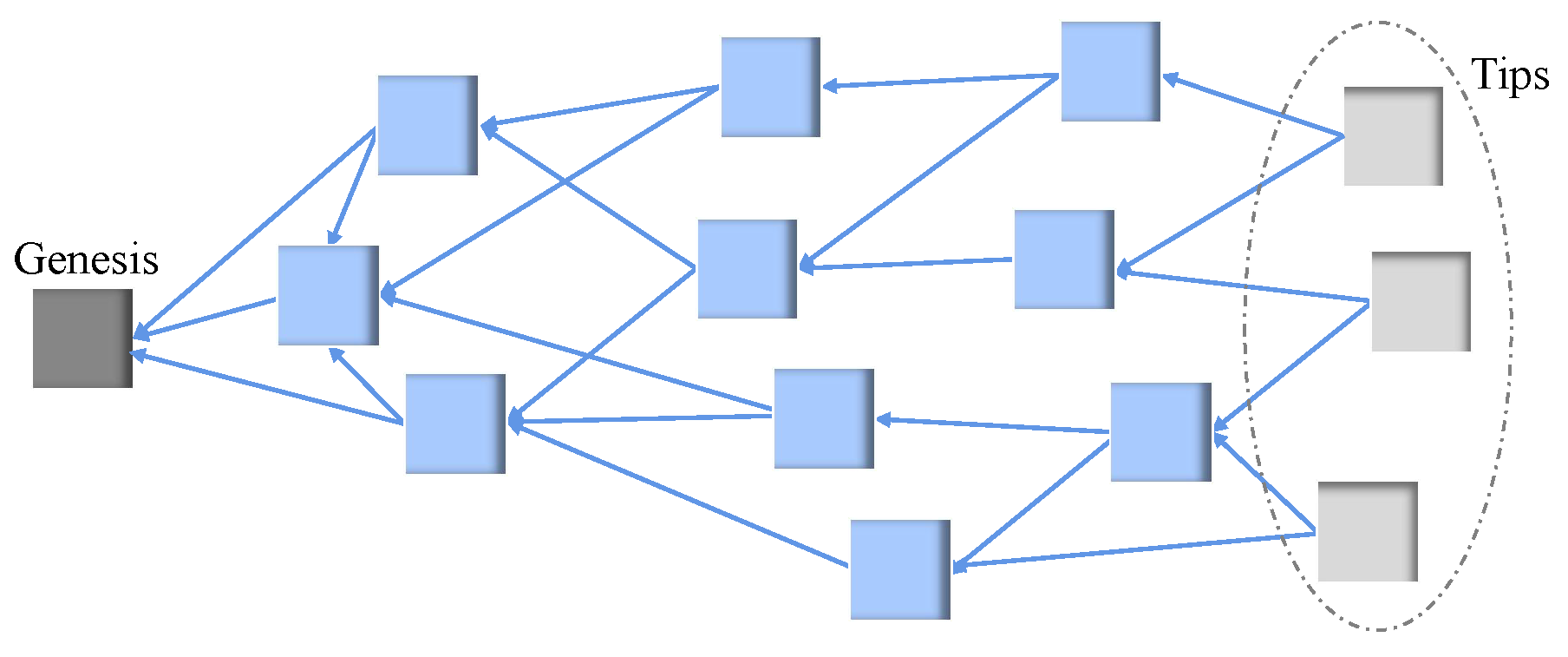
IOTA and Tangle. Maintaining the growth of the IOTA tangle requires all IOTA nodes to reach consensus. Unapproved transactions (terminal transactions) in the tangle are called tips. Incoming transactions approving at least two tips can attach to the tangle. Figure 1 shows the structure of the tangle [1], with the the Genesis transaction on the left and the tips on the right.
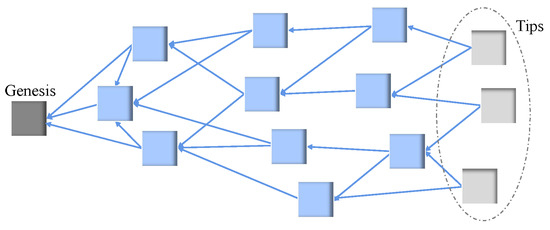
Figure 1.
DAG structure of the tangle.
In the early days of IOTA, the Coordinator was introduced to prevent malicious nodes from harming the developing IOTA network. Both IOTA Ledger and IOTA Chrysalis relied on the Coordinator to reach a consensus. However, if the Coordinator failed, the IOTA network would be paralyzed; thus, it was considered only a temporary solution. The plan was to remove the Coordinator in the future IOTA 2.0 update. IOTA proposed Coordicide [24] (i.e., killing the Coordinator) to replace the Coordinator. This paper analyzes the cost optimization and transaction rate control in Coordicide (IOTA 2.0).
Lyapunov optimization. In 1892, Lyapunov published the famous paper The general problem of the stability of motion and established a general theory of the study of motion stability [26]. Lyapunov stability theory starts from each equilibrium state of the dynamic system, and studies the local stability near it. Over the past hundred years, Lyapunov theory has been widely developed in mechanics, information science, and many other fields. The fundamental idea of Lyapunov optimization is to decompose a long-term optimization objective with long-term constraints into each time slot [27]. The target can then be directly optimized without breaking the agreement that the current time slot needs to follow. Many prior parameters do not require Lyapunov optimization, which has good adaptability to the real-time control of dynamic systems while ensuring relatively low computational complexity.
Supposing a system with n queues, we can use a vector to represent the whole queue. Let , where is a queue backlog vector; then, the Lyapunov function is expressed as . To simplify the calculation, is taken for any i. The function is always non-negative, and is equal to zero if and only if all components of are zero; , called the Lyapunov drift, represents the increment of all queue backlogs from time slot t to time slot . In this paper, we optimize the resource costs of IOTA nodes based on the Lyapunov optimization framework.
Large deviation theory. Large deviation theory is a critical branch of probability theory and limit theory. It helps to estimate the probability of making mistakes in hypothesis testing of a stochastic system, the escape probability of a stochastic system, and the probability of deviations from the deterministic orbit [28]. This theory has found wide application in fields such as information and finance, and is gaining increasing attention. The principle of large deviations can be described as follows.
Let (, ) be a sequence of random variables that take values in ; say that satisfies a large deviation principle in with rate function H if H is a rate function and if, for any measurable set, , , where denotes the interior of B and its closure. In this paper, the tolerable number of effective delayed transactions and the minimum transaction approval rate of a node are deduced using large deviation theory.
4. System Overview
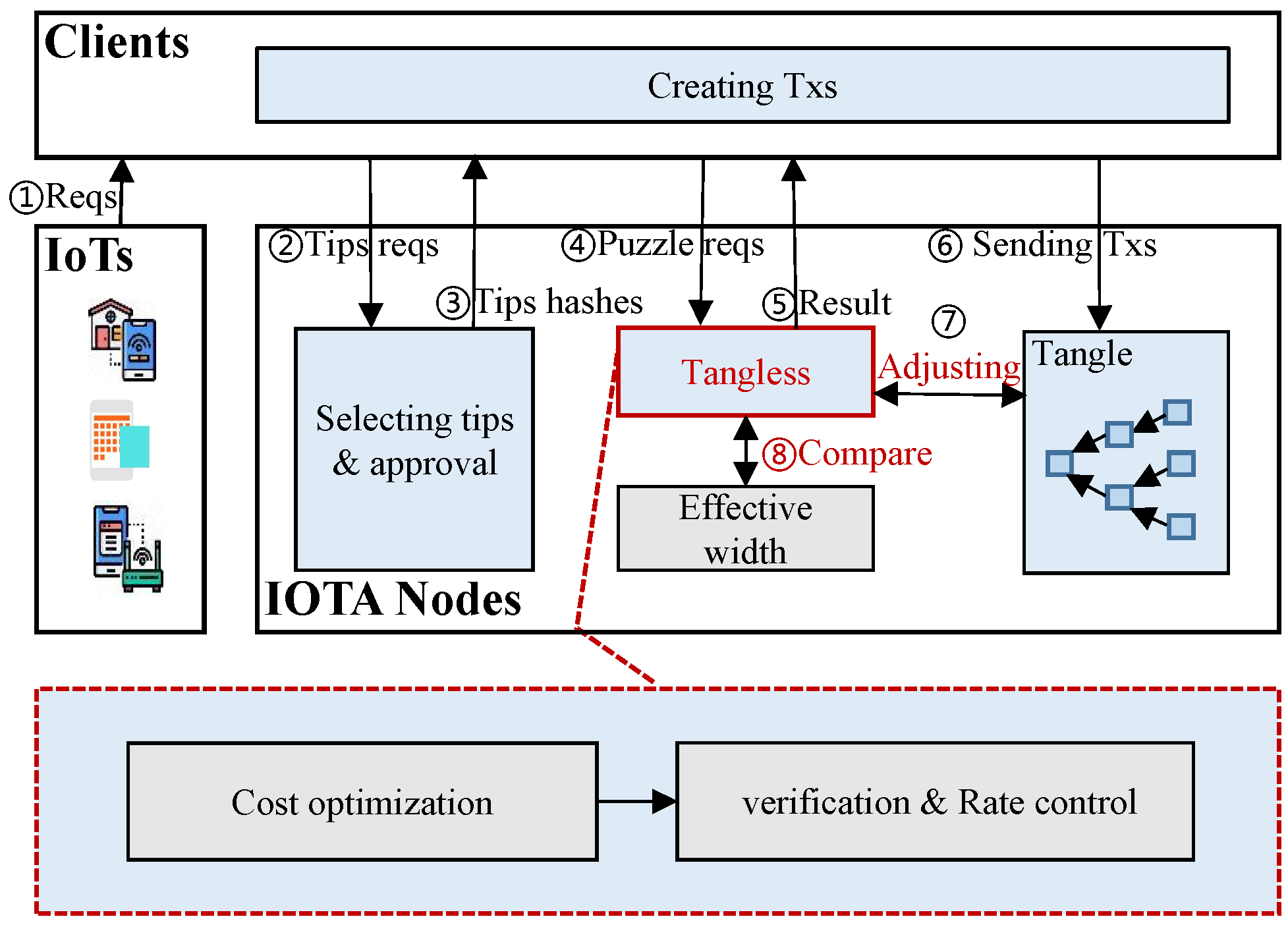
Figure 2 illustrates the system structure of IOTA, containing four types of entities: IoT devices, clients, IOTA nodes, and the committee [1]. When messages arrive at IoT devices, they are delivered to clients immediately. The messages, called transactions, are then packaged by clients and sent to IOTA nodes. Generating transactions involves cooperation between clients and nodes. Specifically, when a node receives a tip-selected request from the client, it selects two terminal transactions to approve and complete the calculation of a cryptographic puzzle. The result is then returned to the client. Upon receiving the results, the client packages the transaction and sends it to the node for verification. If the transaction is legitimate, the node updates its local ledger and broadcasts it to other IOTA nodes through the P2P protocol to complete the consensus processes.
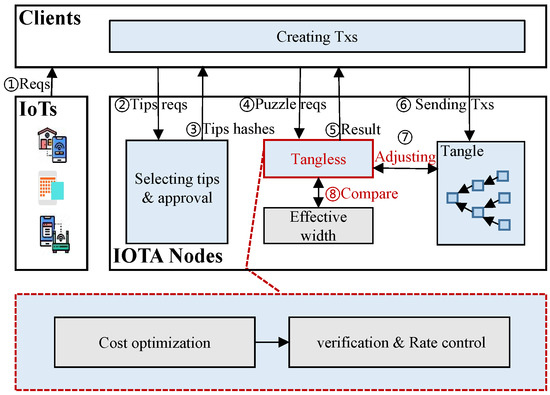
Figure 2.
Overview of the system architecture.
In this work, we propose Tangless, a scheme for IOTA that optimizes node costs and controls transaction rates. To ensure smooth implementation of Tangless, we appoint a committee elected from IOTA nodes to conduct macro-level control.
Tangless is a crucial component in IOTA nodes that operates within the nodes. It consists of a Cost Optimization Module and a Verification and Rate Control Module. The main workflow, as highlighted in red in Figure 2, is as follows: upon initiation, the IOTA system gradually stabilizes as the number of joining nodes meets the system’s requirements. We can denote this time slot as t. At this point, each IOTA node initializes Tangless for the first time. Specifically, with the tangle updating in time slot t, the node transfers the relevant data from the tangle to the Cost Optimization Module for optimization. We employ the computational optimization algorithm to derive the threshold of transaction approval rate . Subsequently, is transmitted to the Verification and Rate Control Module. In this module, we take the first step towards calculating the threshold for the minimum transaction approval rate using large deviation theory. Then, based on the threshold of the transaction approval rate obtained from the cost optimization algorithm, we determine the optimal approval rate of each node. This rate is greater than but close to . Additionally, the new difficulty of Tangless in each node can be calculated using the optimized transaction rate control algorithm. Based on these results, we implement the optimal approval rate for each node for time slot . The proposed Tangless scheme can effectively minimize the resource costs of IOTA nodes and reduce the generation of orphan tangles.
Next, the committee members sum the optimal approval rate of each node to obtain the throughput of the tangle in time slot t. Specifically, the committee regards the current throughput as the initial value of the effective width of the tangle. Through numerical analysis, the committee calculates the quality of the approval parameter. This parameter is an indicator of the service quality provided by the current IOTA system. If the number and status of nodes fluctuate within the allowable range, this parameter will not change; however, if many nodes join or exit the IOTA network, then the parameter must be redetermined. Therefore, the committee members first need to pay attention to network changes. The committee then calculates the effective width of the tangle in subsequent time slots and compares the result with the throughput in the corresponding time slot. If the throughput is higher, then it is necessary to trigger Tangless again.
Remarks. In our design, the task of calculating the effective width of the tangle is carried out by a group of IOTA nodes, which act as a committee to carry out the final macro-level control when detecting the throughput. Each IOTA node has the potential to be chosen as a committee member. Similar to the election mechanism in [29,30], we assume that more than of the active IOTA nodes in the committee are honest. The trustworthiness of an IOTA node depends on the confidence value of its issuing transactions. The confidence level of a transaction is usually used to describe the validity of a message. The confidence level is mainly obtained by running the tip selection algorithm multiple times. The specific approach is to run the tip selection algorithm multiple times on conflicting transactions and select the transaction with the highest confidence value as the valid one. Additionally, we assume that the IOTA system will distinguish time-sensitive transactions, similar to blockchains [31]. Time-sensitive transactions are marked by clients when messages are sent. This enables us to determine which transactions should be prioritized for reception and approval when the throughput temporarily exceeds the effective width of the tangle.
5. Design of Tangless
This section presents our design of Tangless in detail. We first provide the computational optimization algorithm used in Tangless. Then, we propose the optimized transaction rate control algorithm based on the cost optimization of nodes. Moreover, we further introduce the effective width of the tangle, which is compared with the throughput to determine whether to optimize the next time slot.
5.1. Computational Optimization Algorithm
Reducing the expenditure of generating the tangle is the first step of Tangless. However, achieving this goal is challenging for two main reasons. First, the IOTA nodes issuing and approving transactions are unknown and dynamic, leading to unpredictable and unstable transaction queues. Second, long-term real-time optimization problems are generally complex and intertwined with various constraints, making traditional analysis methods ineffective [32]. To overcome the above challenges, we decouple the multi-objective optimization problem to achieve low computational complexity and make decisions without specific information. We leverage the Lyapunov optimization theory to embed transaction-related queues and constraints into the optimization framework, allowing us to solve the complex long-term cost optimization problem.
In what follows, suppose that the IOTA nodes issuing and approving transactions obey a Poisson distribution. Assume n nodes in IOTA, which are numbered with i, . Finally, suppose that IOTA operates in the time interval , which is divided into d time slots of equal length, and that each time slot is marked with t, .
5.1.1. Modeling
For each node, we are interested in the difference between the number of new arriving transactions and the number of transaction approvals in each time slot t. Here, indicates the number of new transactions arriving at node i, which are first buffered in node i’s backlog queue , where they await approval; represents the number of transactions approved by node i. Both satisfy the independent identically distributed condition. Therefore, we can derive the following equation to formally demonstrate the evolution of each node i’s queue backlog:
with .
Next, we need to add temporal consideration to the queuing game to meet the latency demand. Let represent the average time spent by node i from the arrival of a transaction to the approval of the transaction. In light of , the average approving delay constraint can be expressed as . We define H as the maximum delayed approval time of each transaction, which can be determined by the committee according to the network conditions. Meanwhile, regardless of the hardware cost and loss of each node, the average cost of approving two terminal transactions is a, the average cost of verifying a transaction is b, the average cost of updating the local ledger one time is c, the average cost of solving a puzzle is f, and the average cost of broadcasting the tangle one time is g. Thus, the consumption cost of node i in time slot t is
where and .
Taking all of the above into consideration, we mathematically devise the node cost optimization goal as Problem 1:
Notably, the transaction approvals of each time slot are entangled; thus, we cannot achieve the optimal solution of Problem 1 through simple combinatorial optimization.
5.1.2. Lyapunov Optimization
We expect the whole IOTA system to be stable and the tangle to grow steadily. As such, Problem 1 can be addressed using Lyapunov optimization theory. According to [27], we know that if is non-negative and if Equation (3b) holds, then is strongly stable. Similarly, denotes the cumulative backlog of transactions for which node i cannot meet the delay requirements in time slot t. Thus, we can convert Equation (3c) into the stability constraint of the virtual queue , for which the expression is
with . Similar to , satisfies the delay demand constraint in Equation (3c) and is stable [27]. Therefore, Problem 1 can be turned into Problem 2:
We can analyze the evolution of queues using the Lyapunov optimization framework; see Table 1 for the specific parameter definitions.

Table 1.
Definitions of Lyapunov optimization parameters.
Let . To simplify the calculation, is taken for any i. Thus, the Lyapunov function of our scheme is expressed as follows:
If is reduced to a sufficiently small value, we can maintain the backlog of each queue at a low level to meet the queue stability; thus, we introduce the Lyapunov drift under a single-slot condition to achieve this goal. This measures the increase in the backlog of all queues from time slot t to time slot :
We can also understand this drift as the expected change of the Lyapunov function on a time slot. Because new transactions may become lost or invalid during network transmission, we can find a compromise between queue backlog and node cost by introducing and tuning the V value to minimize the drift and cost; here, V is an adjustable variable that describes the relative weight between queue stability and IOTA network cost minimization. In this work, we add a penalty function related to the value of V to both sides of Equation (7) to minimize the total cost of Equation (5a) and ensure the stability of the actual and virtual queues. According to this, the expression of the drift-plus-penalty of Lyapunov optimization is as follows:
where . Therefore, we turn Problem 2 into Problem 3:
From a mathematical standpoint, can be explicitly derived (please refer to Lemma 1).
Lemma 1.
The drift-plus-penalty satisfies
where .
Proof.
According to Equation (6), we can write
Next, describes the detailed derivation process as an example. The derivation of other terms is similar. It is worth noting that
The second line in Equation (12) is proved below.
If , then
Thus, we can know .
If , then
As we can know , we obtain
Similarly, we have
After scaling and simplification, we obtain
For any i and t, both and have upper bounds. We extract these parameters as , that is, . Consequently, when , Lemma 1 holds. □
Next, the approximate optimal solution of Problem 3 is solved through the drift-plus-penalty of Lyapunov optimization. Substituting Equation (2) into Equation (10), we have
According to the opportunistic minimization of expectation [33], we minimize the above expectation by minimizing the function inside the expectation. Therefore, we can realize Equation (18) by calculating the minimum of the following expression. Let
We can achieve the approximate solution to Problem 3 by solving the minimum value of B. In time slot t, the values of and are fixed. In Equation (19), B is a quadratic convex function for and has a minimum value in its definition domain. Thus, Problem 3 can be turned into Problem 4:
We can find the partial derivative of B to in time slot t as follows:
Let . Then, we obtain
When the transaction approval rate of node i satisfies Equation (22), B has a minimum value. Algorithm 1 shows the details of the computational optimization algorithm [1]. In this way, the threshold for the transaction approval rate can be obtained to reduce the tangle generating expenditure.
| Algorithm 1 Computational optimization algorithm. |
|
5.2. Optimized Transaction Rate Control Algorithm
IOTA generates many orphan tangles due to network delay, resulting in wasted computational costs and potentially causing network congestion. Therefore, in this subsection we propose an optimized transaction rate control algorithm based on large deviation theory [28] to eliminate orphan tangles. To this end, we introduce two concepts: the number of tolerable delayed transactions and the minimum transaction approval rate.
5.2.1. Number of Tolerable Delayed Transactions
The queue backlog of new incoming transactions is studied to calculate the loss probability of arrival transactions P and its corresponding decay rate . Furthermore, critical factors are found to prevent the loss of arrival transactions and reduce orphan tangles.
Generally, each IOTA node has the computing power to validate transactions and maintain the tangle. Thus, the stability of can satisfy the waiting delay requirements of incoming transactions. However, a small probability of events violating the above waiting delay still exists. Thus, we determine the cumulative backlog of tolerable delayed transactions of node i () by leveraging the large deviation theory, that is, the number of tolerable delayed transactions. In Section 5.1, and are the issuing rate of new transactions and the approval rate of the transactions of node i, respectively (taking time slots as the time unit). In light of the occurrence of small-probability events, this needs to satisfy . To maintain the stability of the queue, is required, that is, . Let h represent the average time between an arriving transaction and its approval. Based on [17], we suppose that to ensure that the number of terminal transactions in the tangle for each time slot tends to a constant value. According to Equation (4), we can derive another expression for :
in which and indicate the actual length of for node i and the actual transaction approval quantity of node i in time slot t, respectively. Notably, can be negative in this part. Let represent the number of delayed transactions that node i can tolerate. As our main concern is the maximum number of transactions unapproved in time, we concentrate on , which denotes the maximum value of . As this is also the crux of analyzing the robustness of IOTA, it is imperative to analyze the probability of . is defined as follows.
Definition 1 (The number of tolerable delayed transactions ()).
If the number of issuing transactions from node i is greater than the number of transaction approvals by the node in time slot t, node i can still accept the number of transactions for which the latency requirement could not be satisfied.
Due to the above definition, we know that larger means that node i can tolerate more delayed transactions, in other words, node i can endure more delayed transactions as increases. When the difference between the number of delayed and approved transactions for node i is at its highest, delayed transactions overflow easily; therefore, the value of X can be analyzed to determine whether there is an overflow of delayed transactions. If , then the incoming transactions overflow due to delay, and vice versa. Thus, we study probability by discussing the relationship between X and to solve the overflow degree of delayed transactions reaching node i.
Leveraging Cramer’s theorem [28,34,35], we deduce the delayed transactions overflow probability of node i. Let . When , can be expressed as ; thus, we have
where
and
Here, is the Fenchel–Legendre transform of . The logarithmic moment generating function of is
Next, let and express the logarithmic moment generating function of and , respectively. According to Equation (27), we obtain
To solve , we need to deform the function. According to [34], it is known that . Let . Substituting r and into Equations (31) and (32), we have . We calculate the first and second derivatives of G, that is, and , respectively. When , we can know . This indicates that G has a minimum. Letting , we have , which we can put into G to obtain the minimization of G:
Let . After transformation, we obtain ; thus, . When , where , A has the minimum value. Combining this with Equation (25), we can derive as follows:
in which is recognized as the exponential decay rate function of . Notably, is an important index reflecting the loss of delayed transactions. Next, we present another definition.
Definition 2 (Number of effective tolerable delayed transactions ()).
If the number of issuing transactions from node i is greater than the number of transactions approved by the node in time slot t, node i can still accept the minimum number of transactions for which the latency requirement could not be satisfied.
This value should satisfy the condition that the probability of the maximum difference between the number of delayed and approved transactions be less than or equal to the given threshold . This requirement can be mathematically described as . Given , , and , we can derive as follows:
Proof.
Although large q offers high efficiency in accepting more delayed transactions, it leads to long delays in transactions and takes up a great deal of storage space. We can also consider another factor affecting , which is the transaction approval rate. In this case, we should answer the fundamental question of how much computational power an IOTA node needs to approve tips. To address the problem, we introduce the following definition.
Definition 3 (Minimum transaction approval rate ()).
This rate refers to the minimum value of the transaction approval rate of node i to ensure that the loss probability of delayed transactions is less than or equal to the given threshold .
We can know . For , , and , we have
The proof is similar to Equation (35), and is not repeated here. The related algorithm is shown in Algorithm 2.
| Algorithm 2 Minimum transaction approval rate. |
|
Next, we consider how to determine the cost of computational optimization. In light of the above analysis, the optimal transaction approval rate in real time should be close or equal to the threshold in Equation (22) and greater than the value of Equation (36). Under such circumstances, we can effectively reduce the cost of IOTA nodes while reducing the existence of orphan tangles.
5.2.2. Rate Control
Based on the analysis in the previous subsection, the transaction rate control problem can be transformed into the problem of adjusting the PoW difficulty of Tangless in IOTA, which is related to and . Here, indicates the cumulative backlog of new transactions for which node i cannot meet the approval demand in time slot t. By monitoring the change in the value in each time slot, we propose a method for colculating the difficulty of Tangless. While each node in IOTA has a different calculation power, the node must provide greater than space for tolerable delayed transactions in order to reduce overflow. We expect that for stable growth of the tangle; thus, we discuss the change in . Specifically, indicates that the current difficulty of Tangless is too high, while shows that the number of new transaction arrivals of a node and the number of transaction approvals of the node match in time slot t, which is the optimum operating state of the IOTA node. Therefore, we do not need to adjust the difficulty of Tangless. If , then the network load is small. Let represent the difficulty of Tangless in node i in time slot t. The expression is
where is the basic difficulty value. We set , which we call the variation in the difficulty of node i in every time slot. When , the rate control of Tangless will degenerate the fixed PoW, which is the same as IOTA . Algorithm 3 shows the details of the rate control algorithm of Tangless. The algorithm balances transaction traffic and IOTA node tolerance to reduce the generation of orphan tangles, decrease waste of computing resources, and hinder network congestion.
| Algorithm 3 Optimized transaction rate control algorithm. |
|
5.3. Effective Width of the Tangle
With new transactions coming in continuously, it is important to control the throughput to ensure that it always fluctuate around the number of approved transactions that the IOTA network can tolerate. In the previous subsection, we determined the rate of each IOTA node. Algorithm 3 is an improvement of adaptive PoW [24] and is directed against each single IOTA node. In this subsection, we study the change in the transaction throughput of the IOTA system from a macro-level perspective to ensure the stable growth of the tangle, reduce cost optimization frequency, and avoid unnecessary waste of resources.
Monitoring whether the throughput is within the tolerance range of IOTA is proposed mainly to save on IOTA system costs. Specifically, incoming transaction rates that are too fast will place some new transactions at risk of being abandoned due to network congestion. If many terminal transactions are not approved timely, it can produce some orphan tangles. Either situation leads to considerable wastes in the IOTA system. We use the proposed Tangless scheme to address the above issues. Importantly, if nodes were to implement Tangless in every time slot, this would incur a great deal of cost, as the time complexity of the related algorithm is . To solve the issue from an overall perspective, we propose a definition for the effective width of the tangle. We first compare the effective width with the corresponding throughput, then decide whether to implement Tangless for the next step, thereby avoiding resource wastage caused by unnecessarily frequent optimization.
Note that the effective width of the tangle is determined by the committee rather than by all IOTA nodes. By studying the matching degree between the effective width of the tangle and the throughput, we determine whether to necessarily implement the next round of cost optimization and transaction rate control. If the difference between them is within the tolerance of the IOTA system, this indicates that the growth of the tangle is stable. If the throughput is much greater than the effective width of the tangle, that is, beyond the tolerance of the IOTA system, it indicates that the current throughput needs adjustment and that we need to trigger Tangless again. Thus, the definition of the effective width of the tangle is as follows.
Definition 4 (Effective Width of the tangle).
The number of approved transactions per unit of time.
In communication, the effective bandwidth theory can describe the performance of burst traffic in a unified form. A popular method is log moment generating function transformation [34,37], which can be used to solve the effective bandwidth in a communication network. In our work, we regard incoming transactions as data transmitted by the IOTA network and the effective width of the tangle as the effective bandwidth. Thus, the effective width of the tangle can be calculated through the transformation of the log moment generating function. This approach allows us to study the actions to be taken by IOTA in the case of a sudden change in transaction volume.
Consider the case where new transactions are constantly attached to the tangle from moment 0. Let be the total number of new transaction arrivals in the interval between and . Suppose that denote the number of new transaction arrivals in the i-th unit, and are i.i.d. According to [34,38,39], we can conclude that the effective width of the tangle is
where is the log moment generating function of and is some given tail decay parameter (sometimes called an approval quality parameter), with .
Assume that is the average rate at which new transactions arrive (assuming that all nodes have the same computing power), which is assumed to obey a Poisson distribution and to satisfy and ; then, can also be expressed as follows:
Proof.
According to Equation (38), we can obtain
Based on the expectation of a Poisson distribution, we know that
Thus, we have
□
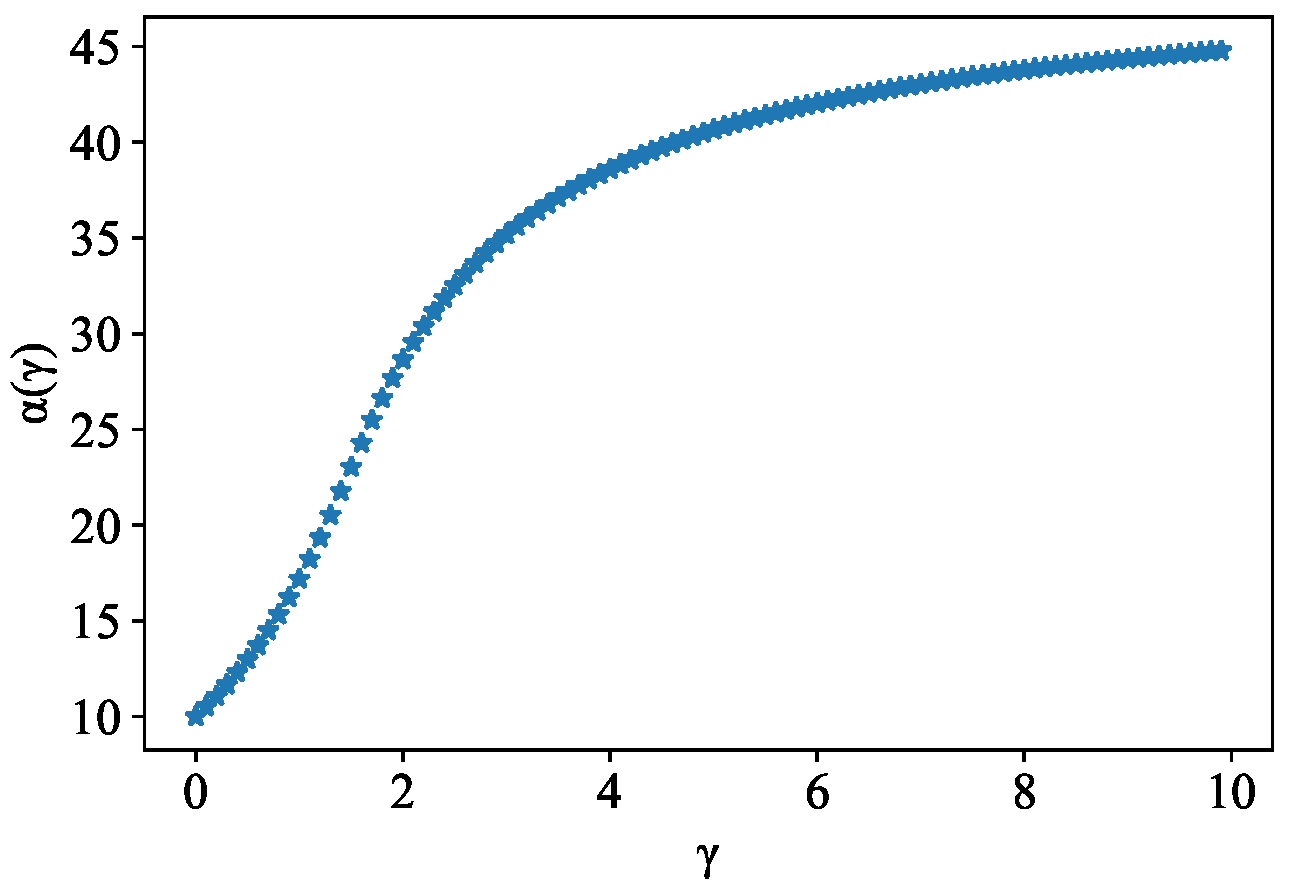
Assuming , this shows that is increasing with , as shown in Figure 3. According to [34], we can see that lies between the mean rate and the peak rate, which is ess. sup. . Here, we can consider x as the number of active nodes in the IOTA network.
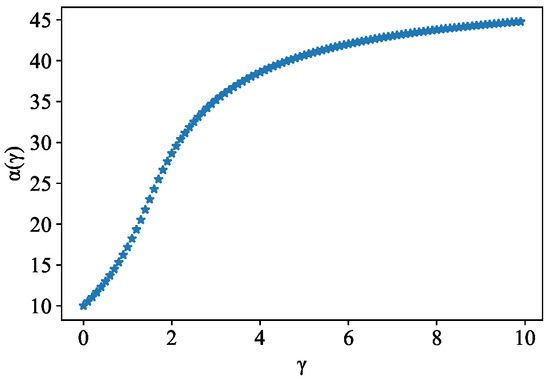
Figure 3.
along with changing trend.
Notably, the approval quality parameter is determined and maintained by the committee. Specifically, after optimizing the costs of IOTA nodes, we need to sum the thresholds of the transaction approval rates of all nodes to obtain the transaction throughput in time slot t. Next, the committee members adjust the parameter of according to the throughput using the numerical analysis method and determine . Significantly, if we know the approval quality parameter, then we can deduce the effective width of the tangle in subsequent time slots. Therefore, in the next time slot, we can first calculate the value of compare it with the current throughput, then decide whether to continue to optimize the costs of IOTA nodes.
As long as the number of IOTA nodes and the nodes’ status both remain unchanged, the approval quality parameter will remain unchanged. Thus, we can obtain the throughput that the network can tolerate. Nevertheless, if Tangless is started in each time slot, resources will be wasted and the efficiencies of nodes will be too low. Motivated by this observation, if the effective width of the tangle does not match the actual throughput in the next time slot (for example, if the fluctuation exceeds ), then we can start Tangless again. The details of the comparison algorithm are provided in Algorithm 4. The time complexity of this algorithm is less than .
| Algorithm 4 Throughput adjustment algorithm. |
|
In this work, we assume that all approved transactions are terminal transactions. The transaction attachment strategy (i.e., the tip selection algorithm) can solve and ensure this situation; however, this is not discussed in our paper.
In light of the above observations, we are also motivated to calculate the expected time for the first approval of the transaction. Let represent the average time that a node needs to perform the calculations required to issue a transaction. We assume that all devices have approximately the same computing power, with representing the rate of that Poisson process; for simplicity, we assume that this rate remains constant in time. According to [17], we suppose that when any node issues a transaction, the state before time units is observed instead of the tangle’s current state, that is, the transaction connected to the tangle at time is only visible to the network until . At a given time , there are approximately “hidden tips” and “exposed tips”, meaning that . Among these, “hidden tips” are not visible at time , as they connect to the tangle in the time interval , while“exposed tips” are still tips at time , having attached to the tangle before time . According to stationarity, we can assume that there are tips in the tangle at time and no longer tips until time . Now, when a new transaction arrives, the probability of a tip being approved is ; thus, the average number of selected tips is . In the steady state, the average number of selected tips should equal 1, meaning that . The expected time of the first approvals is about . When the load is high, the maximum number of tips that can be approved is at time . Thus, the expected time of the first approved transaction should be no more than .
6. Evaluation
In this section, we demonstrate the effectiveness of Tangless by contrasting it with adaptive PoW [24] to demonstrate the resulting improvement. Specifically, we first compare the resource costs of nodes obtained by non-optimization and Lyapunov optimization, then prove the effectiveness of the optimized transaction rate control algorithm. Our scheme was implemented in Python 3.10.2 on a laptop with an 11th-Gen Intel(R) Core(TM) - processor and 16 GB RAM.
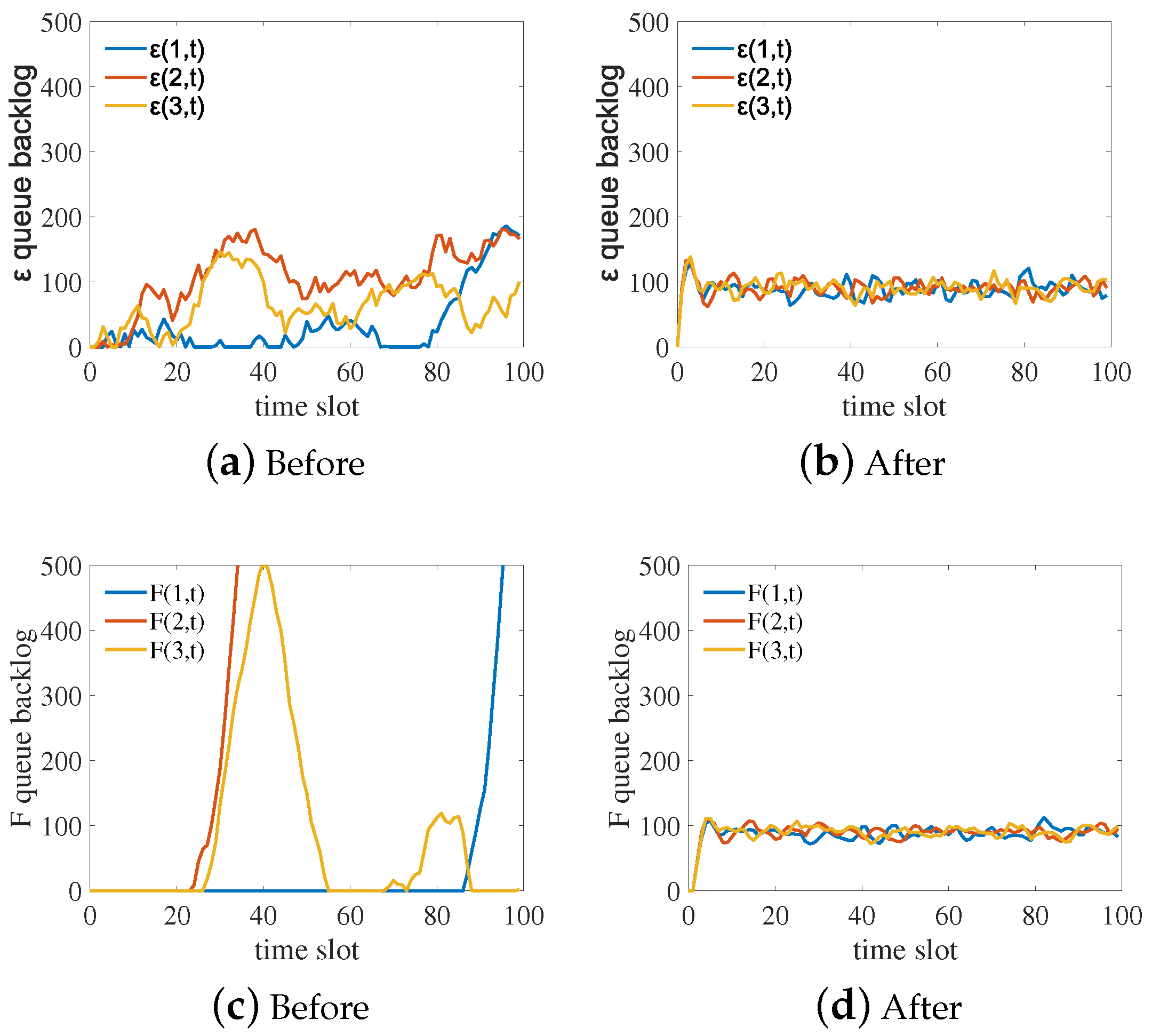
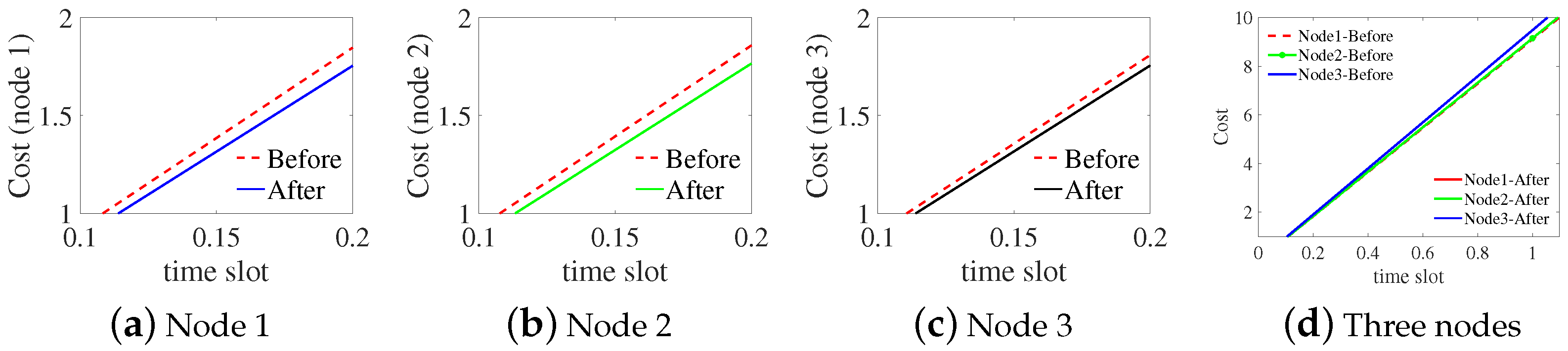
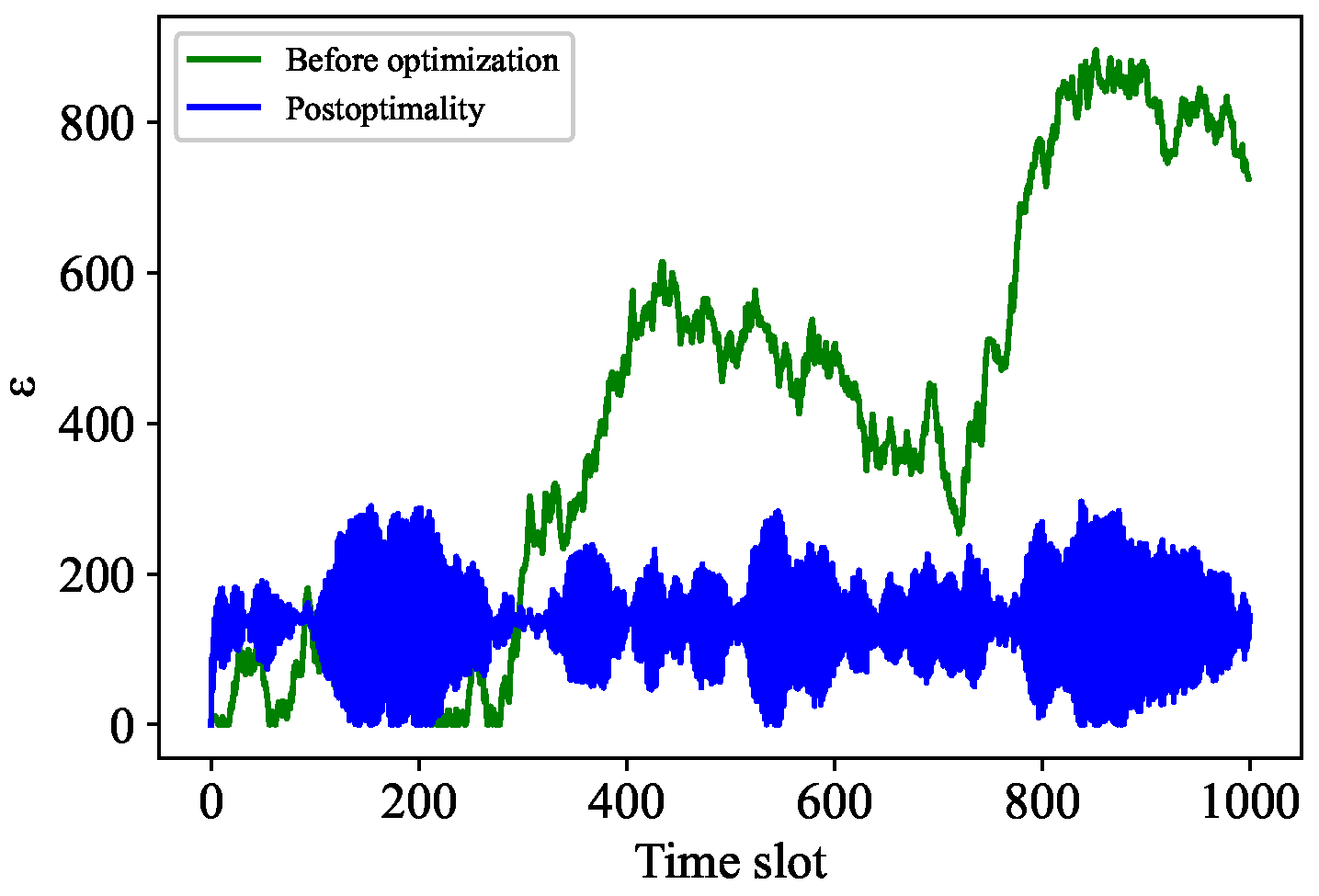
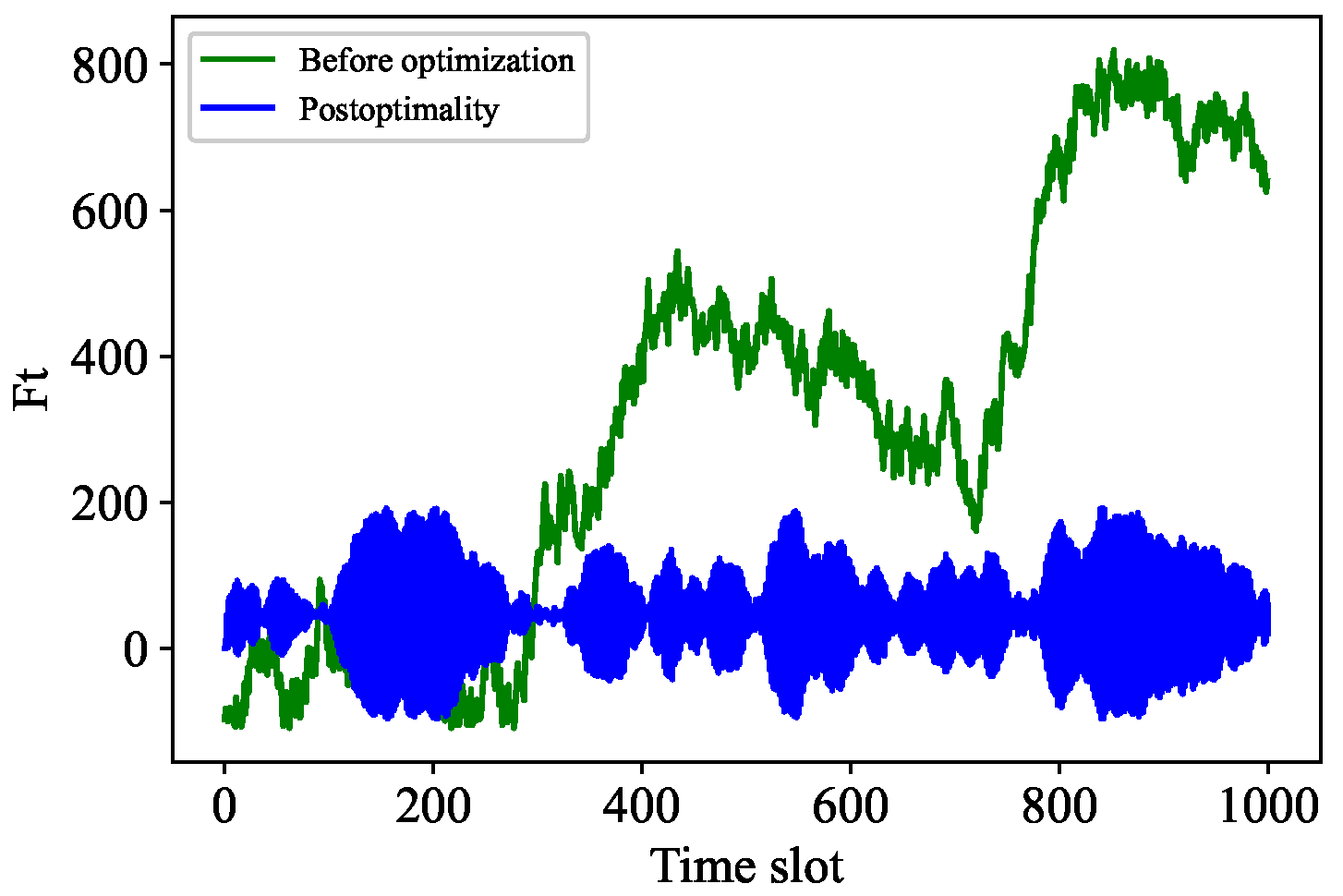
Our experimental simulations, we used the following parameter settings: the IOTA network had n nodes, with , , , , , and . We randomly selected three nodes for analysis, and followed a Poisson distribution. Non-optimized queues and non-optimized F queues are shown in Figure 4a,c, while optimized queues and optimized F queues are shown in Figure 4b,d. The results indicate that the optimized queues change steadily with time. In particular, the accumulated backlog of new transactions fluctuates in a small range after optimization, as shown in Figure 4d [1]. Under the same conditions, the optimized cost of nodes (solid line) is lower than the cost without optimization (dashed line), as shown in Figure 5. According to these results, the computational optimization algorithm of Tangless reduces the resource costs of nodes (see Table 2).
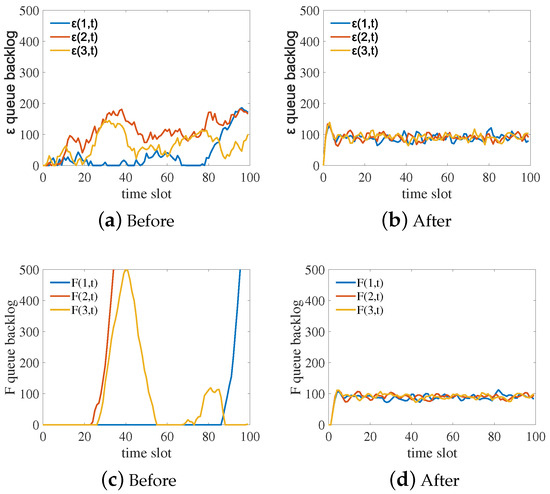
Figure 4.
Comparison of queues before and after optimization.
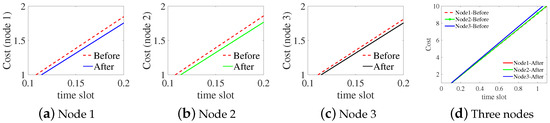
Figure 5.
The comparison of the cost of nodes before and after optimization.

Table 2.
Cost optimization parameters.
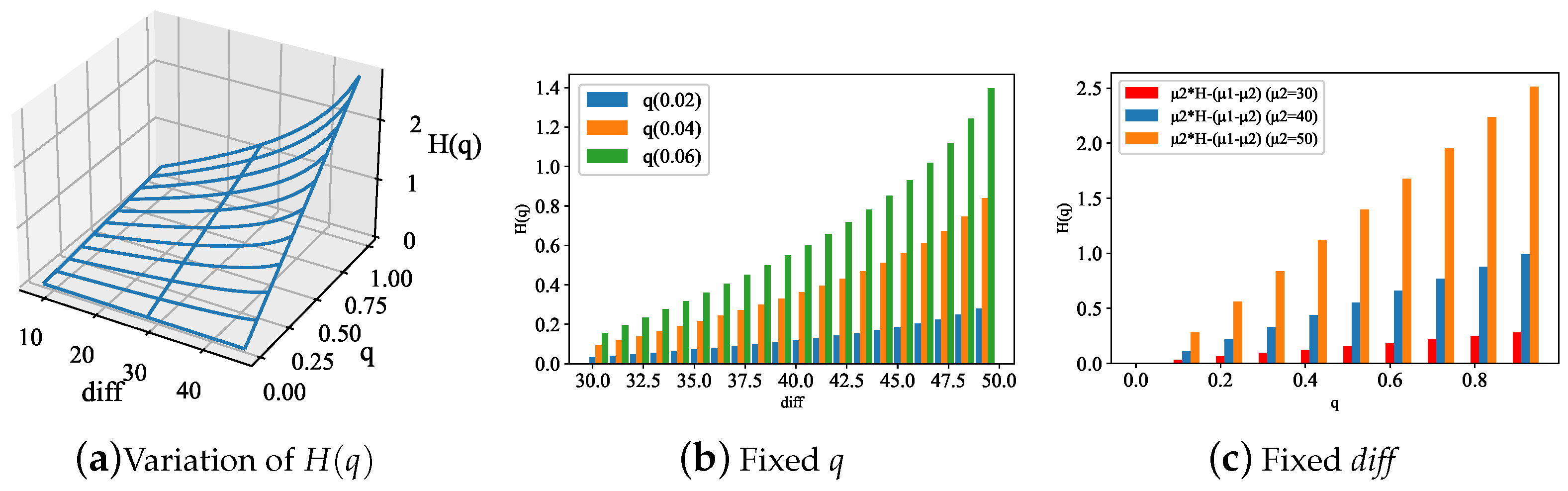
In addition, we focused on evaluating Tangless’ optimized transaction rate control algorithm. First, the influence of relevant parameters was verified using the decay rate of . From large deviation theory, we know that increasing the factors of q or can increase the decay rate . The change in the decay rate with q and is illustrated in Figure 6 [1]. The figure indicates that increases linearly with q, while it increases logarithmically with . Hence, orphan tangles can be further hindered by adjusting the factors of . Then, we can determine the range of based on the obtained value and the threshold of the transaction approval rate in order to control the transaction rate.
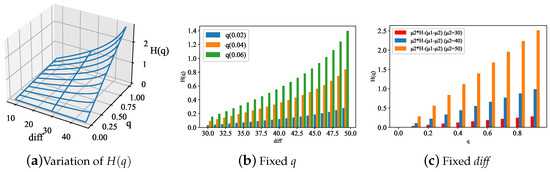
Figure 6.
(decay rate of ); to simplify the expression, we use diff for .
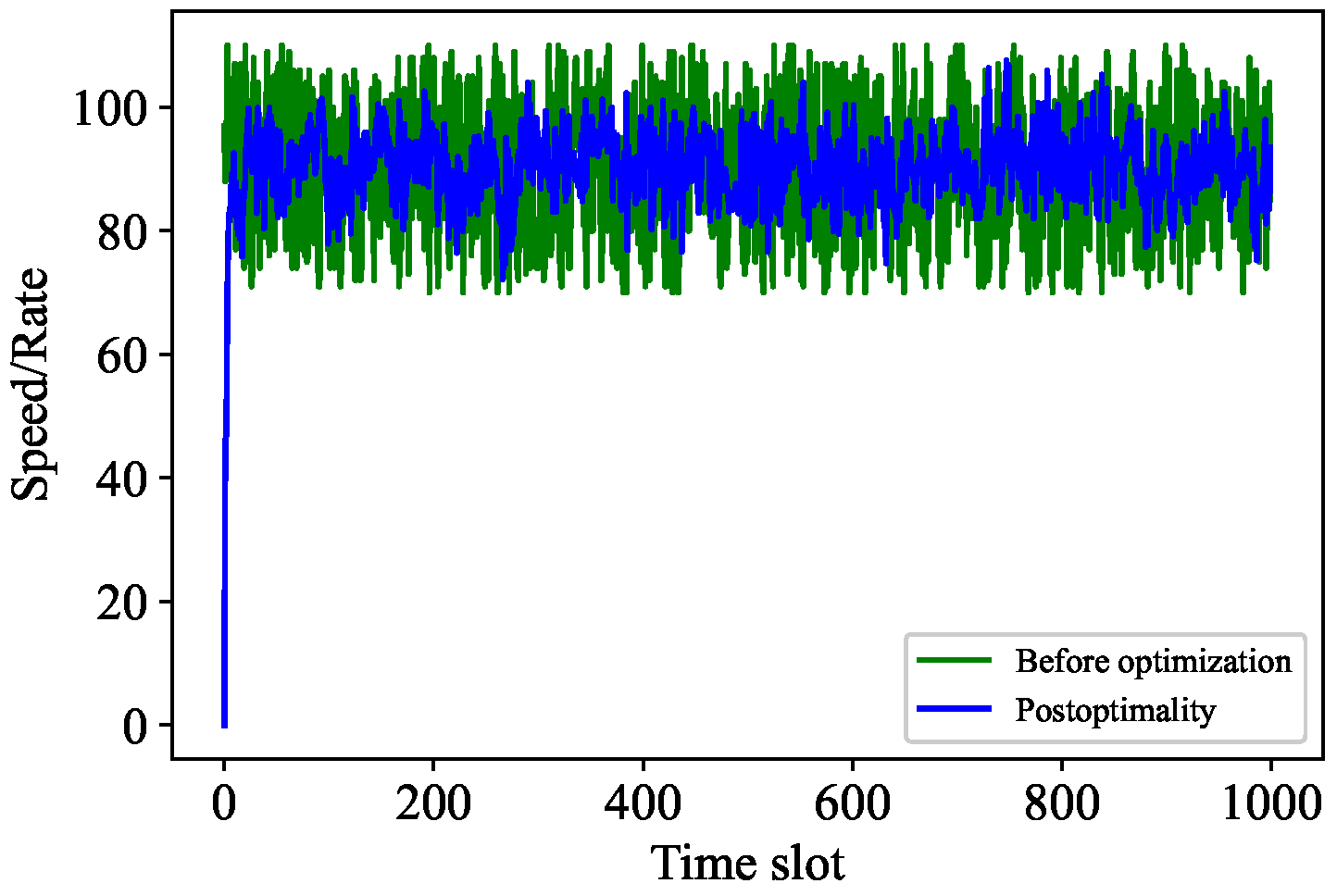
In [24], Serguei Popov et al. proposed the adaptive PoW algorithm to control the transaction rate. However, the adaptive PoW is linked to the mana of nodes, which can lead to some unfairness. In this paper, we ran the optimized transaction rate control algorithm of our Tangless scheme and the adaptive PoW algorithm on a single node to prove the effectiveness of Tangless. Let follow the Poisson distribution, and let its expected value be 90, with as the rate of the IOTA system approving transactions within . The other parameter settings are , ms, , and (i.e., basic difficulty).
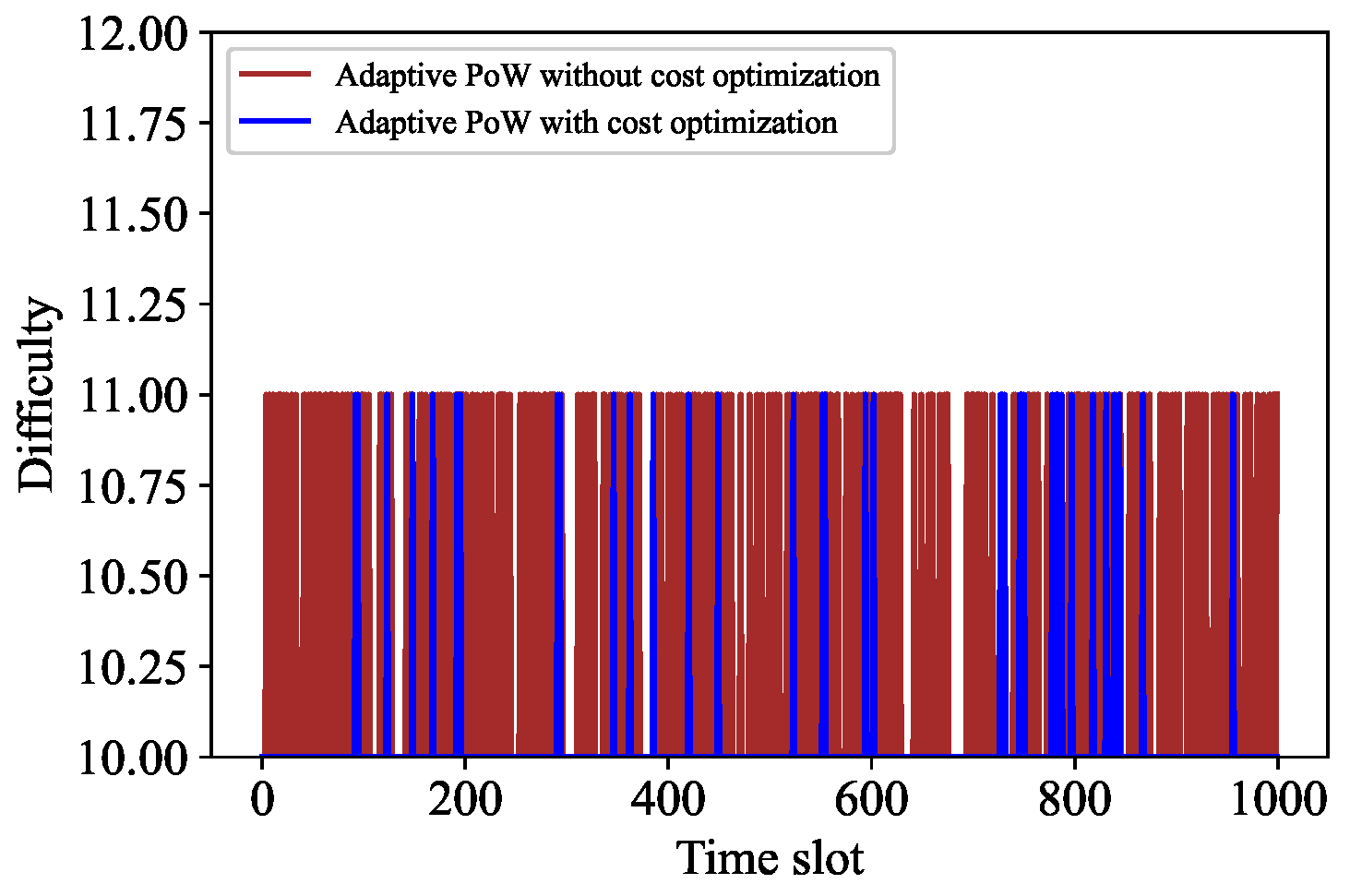
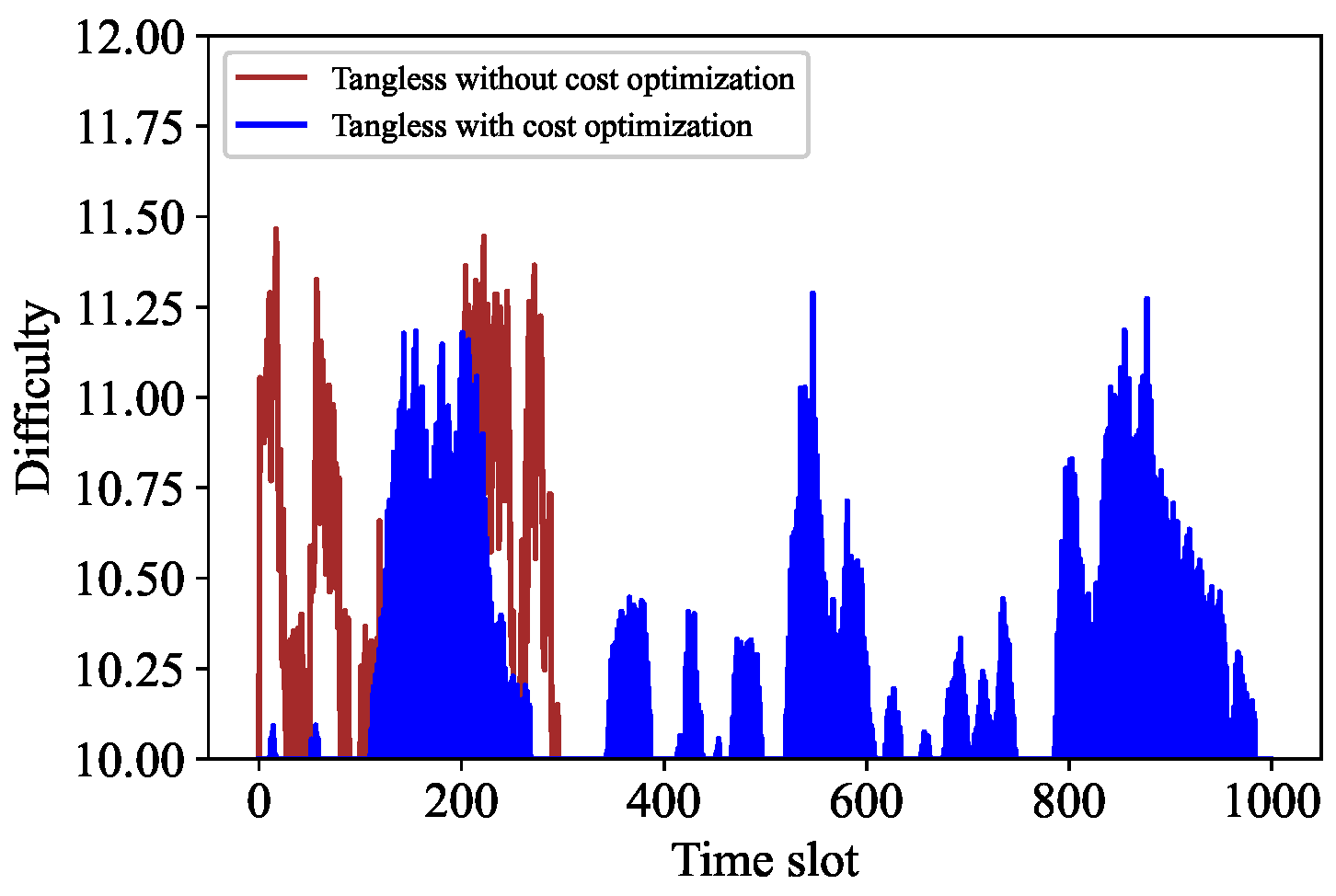
The comparative analysis is carried out from two aspects. First, we compare some parameters of the adaptive PoW algorithm before and after cost optimization. Second, we compare some parameters of Algorithm 3 before and after cost optimization. Specifically, Figure 7 shows the difficulty contrast of adaptive PoW, while Figure 8 indicates the difficulty contrast of Algorithm 3. It can be seen that the change frequency of the adaptive PoW difficulty value decreases, while the change frequency of the difficulty value of our proposed algorithm increases. In addition, Figure 9 and Figure 10 express the contrast of the backlogs of and before and after cost optimization, respectively. After cost optimization, and obviously tend to be stable. Moreover, Figure 10 illustrates the optimal transaction approval rate. It can be observed that the range of this rate’s change is smaller than before optimization, indicating the role of Algorithm 3. Overall, the trend of the optimal transaction approval rate is consistent with the corresponding parameters. These results further prove that Tangless keeps the IOTA system stable while optimizing resource costs. Tangless can dynamically adjust the PoW difficulty depending on the change in transaction flow to match the actual network situation in the next time slot. In light of the above, our proposed Tangless scheme can be considered effective (see Figure 11).
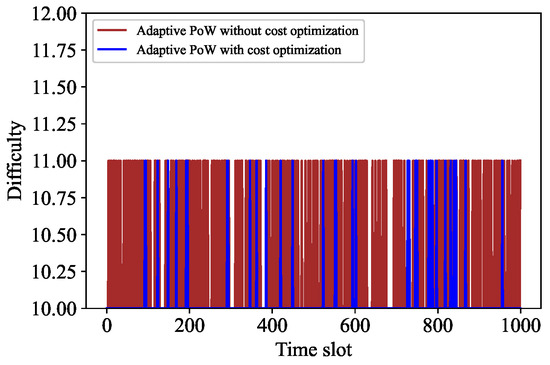
Figure 7.
Rate control without cost optimization.
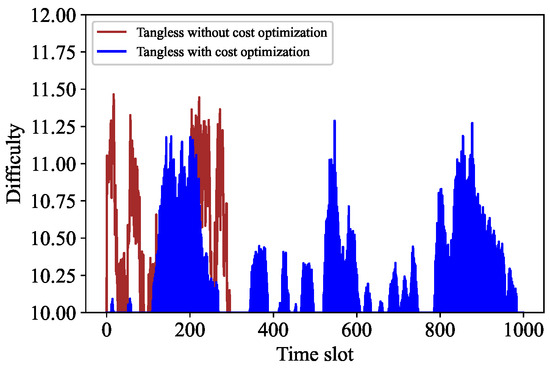
Figure 8.
Rate control of cost optimization.
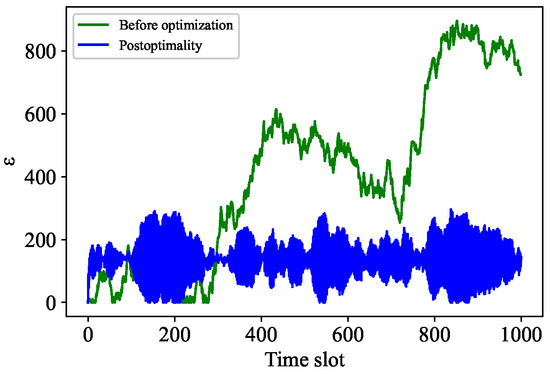
Figure 9.
Rate control without cost optimization.
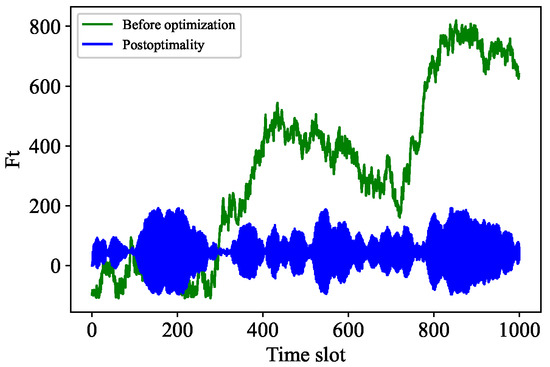
Figure 10.
Rate control of cost optimization.
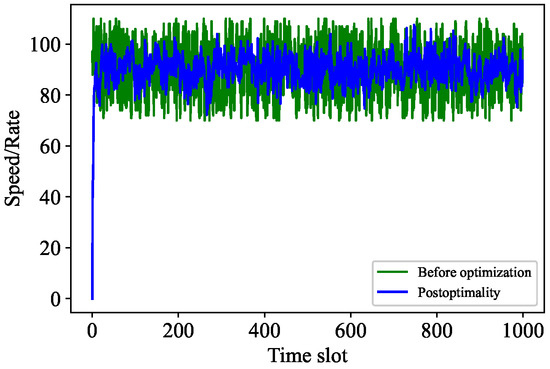
Figure 11.
Rate control of cost optimization.
7. Conclusions
In this paper, we develop a new optimization scheme called Tangless based on Lyapunov optimization theory. First, we design a computational optimization algorithm to reduce the expenditure costs of IOTA nodes. Next, we use large deviation theory to provide an optimized transaction rate control algorithm for eliminating orphan tangles that waste computational costs. Finally, we define and deduce the effective width of the tangle, which can help to monitor the total throughput and reduce the frequency of cost optimization, thereby avoiding unnecessary waste of resources. Tangless can lay a solid technical foundation for promising blockchain-based IoT applications. Our simulation results demonstrate the effectiveness of the proposed Tangless scheme.
Author Contributions
Conceptualization, Y.C.; Methodology, Y.C.; Validation, B.S.; Investigation, Z.Q. and Y.L.; Resources, B.S.; Writing—original draft, Y.C.; Visualization, Y.W.; Supervision, Y.C. All authors have read and agreed to the published version of the manuscript.
Funding
This research was sponsored by the Natural Science Foundation of Inner Mongolia under Grants 2024LHMS06013 and 2024MS07012, the Regional Digital Economy and Digital Governance Research Center under Grants szzl202401, the Research Project on Education and Teaching Reform at Inner Mongolia University of Finance and Economics under Grants JXZD2405, the Fundamental Research Funds for the Central Universities of Inner Mongolia Autonomous Region under Grants NCYWT23034 and NCYWT23043, and the Special Research Project on the Five Major Tasks of the Inner Mongolia Autonomous Region by the Inner Mongolia University of Finance and Economics under Grants NCXWD2419.
Data Availability Statement
The original contributions presented in the study are included in the article, further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Chen, Y.; Guo, Y.; Bie, R. Tangless: Optimizing Cost and Transaction Rate in IOTA by Using Lyapunov Optimizations Theory. In Proceedings of the 2022 18th International Conference on Mobility, Sensing and Networking (MSN), Guangzhou, China, 14–16 December 2022. [Google Scholar]
- Xie, H.; Guo, Y.; Jia, X. Privacy-preserving location-based data queries in fog-enhanced sensor networks. IEEE Internet Things J. 2021, 9, 12285–12299. [Google Scholar] [CrossRef]
- Guo, Y.; Xi, Y.; Wang, H.; Wang, M.; Wang, C.; Jia, X. FedEDB: Building a Federated and Encrypted Data Store Via Consortium Blockchains. IEEE Trans. Knowl. Data Eng. 2023, 36, 6210–6224. [Google Scholar] [CrossRef]
- Zhang, C.; Xie, Q.; Wang, M.; Guo, Y.; Jia, X. Optimal Compression for Encrypted Key-Value Store in Cloud Systems. IEEE Trans. Comput. 2024, 73, 928–941. [Google Scholar] [CrossRef]
- Wu, J.; Jiang, S. On Increasing Scalability and Liquidation of Lightning Networks for Blockchains. IEEE Trans. Netw. Sci. Eng. 2022, 9, 2589–2600. [Google Scholar] [CrossRef]
- Adewuyi, A.A.; Cheng, H.; Shi, Q.; Cao, J.; MacDermott, Á.; Wang, X. CTRUST: A dynamic trust model for collaborative applications in the Internet of Things. IEEE Internet Things J. 2019, 6, 5432–5445. [Google Scholar] [CrossRef]
- Guo, Y.; Zhang, C.; Wang, C.; Jia, X. Towards Public Verifiable and Forward-Privacy Encrypted Search by Using Blockchain. IEEE Trans. Dependable Secur. Comput. 2022, 20, 2111–2126. [Google Scholar] [CrossRef]
- Guo, Y.; Xie, H.; Miao, Y.; Wang, C.; Jia, X. Fedcrowd: A federated and privacy-preserving crowdsourcing platform on blockchain. IEEE Trans. Serv. Comput. 2020, 15, 2060–2073. [Google Scholar] [CrossRef]
- Wang, M.; Guo, Y.; Zhang, C.; Wang, C.; Huang, H.; Jia, X. MedShare: A privacy-preserving medical data sharing system by using blockchain. IEEE Trans. Serv. Comput. 2021, 16, 438–451. [Google Scholar] [CrossRef]
- Li, C.; Qu, X.; Guo, Y. TFCrowd: A blockchain-based crowdsourcing framework with enhanced trustworthiness and fairness. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 168. [Google Scholar] [CrossRef]
- Wang, S.; Zhang, Y.; Guo, Y. A Blockchain-Empowered Arbitrable Multimedia Data Auditing Scheme in IoT Cloud Computing. Mathematics 2022, 10, 1005. [Google Scholar] [CrossRef]
- IOTA Foundation. IOTA Project. Available online: https://www.iota.org (accessed on 1 October 2024).
- Chen, Y.; Guo, Y.; Wang, Y.; Bie, R. Toward Prevention of Parasite Chain Attack in IOTA Blockchain Networks by Using Evolutionary Game Model. Mathematics 2022, 10, 1108. [Google Scholar] [CrossRef]
- Churyumov, A. Byteball: A Decentralized System for Storage and Transfer of Value. 2016. Available online: https://chainwhy.com/upload/zb_users/upload/2018/05/201805071525666705388923.pdf (accessed on 1 October 2016).
- LeMahieu, C. Nano: A feeless distributed cryptocurrency network. Nano 2018, 4. Available online: https://media.abnnewswire.net/media/cs/whitepaper/rpt/91948-whitepaper.pdf (accessed on 24 March 2018).
- Jay, M.; Mollard, A.; Sun, Y.; Zheng, R.; Amigo, I.; Reiffers-Masson, A.; Ruano Rincón, S. Utility maximisation in the Coordinator-less IOTA Tangle. In International Symposium on Ubiquitous Networking; Springer: Cham, Switzerland, 2021; pp. 93–104. [Google Scholar]
- Popov, S. The Tangle. 2018. Available online: https://cryptoverze.s3.us-east-2.amazonaws.com/wp-content/uploads/2018/11/10012054/IOTA-MIOTA-Whitepaper.pdf (accessed on 1 October 2018).
- Soltani, R.; Zaman, M.; Upadhyay, D.; Jain, A.; Sampalli, S. Using IOTA Tangle and Machine Learning for a Defensive Model-Based Approach against Replication Attacks on Wireless Sensor Networks. IEEE Access 2024, 12, 148605–148624. [Google Scholar] [CrossRef]
- Ferenczi, A.; Bădică, C. Optimization of IOTA Tangle Cumulative Weight Calculation Using Depth-First and Iterative Deepening Search Algorithms. Vietnam J. Comput. Sci. 2024, 11, 301–321. [Google Scholar] [CrossRef]
- Hu, W.; Fan, Z.; Gao, Y. Research on smart contract optimization method on blockchain. IT Prof. 2019, 21, 33–38. [Google Scholar] [CrossRef]
- Cao, B.; Wang, X.; Zhang, W.; Song, H.; Lv, Z. A many-objective optimization model of industrial internet of things based on private blockchain. IEEE Netw. 2020, 34, 78–83. [Google Scholar] [CrossRef]
- Helmer, L.; Penzkofer, A. Report on the energy consumption of the IOTA 2.0 prototype network (GoShimmer 0.8.3) under different testing scenarios. arXiv 2022, arXiv:2210.13996. [Google Scholar]
- Nakamoto, S.; Bitcoin, A. A Peer-to-Peer Electronic Cash System. Bitcoin 2008, 4, 2. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 1 October 2024).
- Popov, S.; Moog, H.; Camargo, D.; Capossele, A.; Dimitrov, V.; Gal, A.; Greve, A.; Kusmierz, B.; Mueller, S.; Penzkofer, A.; et al. The Coordicide. IOTA Found. 2020, 12, 1–30. [Google Scholar]
- Wesolowski, B. Efficient verifiable delay functions. In Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Cham, Switzerland, 2019; pp. 379–407. [Google Scholar]
- Lyapunov, A.M. The general problem of the stability of motion. Int. J. Control 1992, 55, 531–534. [Google Scholar] [CrossRef]
- Neely, M.J. Stochastic network optimization with application to communication and queueing systems. Synth. Lect. Commun. Netw. 2010, 3, 1–211. [Google Scholar]
- Dembo, A.; Zeitouni, O. Large Deviation Techniques and Applications. J. R. Stat. Soc. Ser. D 1993, 89, 303–304. [Google Scholar]
- Cai, C.; Zheng, Y.; Du, Y.; Qin, Z.; Wang, C. Towards private, robust, and verifiable crowdsensing systems via public blockchains. IEEE Trans. Dependable Secur. Comput. 2019, 18, 1893–1907. [Google Scholar] [CrossRef]
- Cai, C.; Weng, J.; Yuan, X.; Wang, C. Enabling reliable keyword search in encrypted decentralized storage with fairness. IEEE Trans. Dependable Secur. Comput. 2018, 18, 131–144. [Google Scholar] [CrossRef]
- Lai, W.J.; Hsueh, C.W.; Wu, J.L. A fully decentralized time-lock encryption system on blockchain. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 302–307. [Google Scholar]
- Yu, D.; Zou, Y.; Yu, J.; Zhang, Y.; Li, F.; Cheng, X.; Dressler, F.; Lau, F.C. Implementing the abstract MAC layer in dynamic networks. IEEE Trans. Mob. Comput. 2020, 20, 1832–1845. [Google Scholar] [CrossRef]
- Lee, J.; Jindal, N. Delay constrained scheduling over fading channels: Optimal policies for monomial energy-cost functions. In Proceedings of the 2009 IEEE International Conference on Communications, Dresden, Germany, 14–18 June 2009; pp. 1–5. [Google Scholar]
- Ganesh, A.J. Big Queues; Springer: Berlin/Heidelberg, Germany, 2004. [Google Scholar]
- Chen, Y.; Guo, Y.; Chen, J.; Bie, R. Addressing the Tangle Vulnerability: A Preventive Strategy for IOTA by Using Large Deviation Theory. In Proceedings of the GLOBECOM 2022—2022 IEEE Global Communications Conference, Rio de Janeiro, Brazil, 4–8 December 2022. [Google Scholar]
- Ross, S.M. Introduction to Probability Models; Academic Press: Cambridge, MA, USA, 2014. [Google Scholar]
- Kelly, F.; Yudovina, E. Stochastic Networks; Cambridge University Press: Cambridge, UK, 2014; Volume 2, pp. 133–148. [Google Scholar]
- Fidler, M. An End-to-End Probabilistic Network Calculus with Moment Generating Functions. In Proceedings of the 2006 14th IEEE International Workshop on Quality of Service, New Haven, CT, USA, 19–21 June 2006; pp. 261–270. [Google Scholar]
- Kelly, F. Notes on Effective Bandwidths. Stoch. Netw. Theory Appl. 1997, 4, 1–29. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).