Abstract
In this paper, the preview control problem for cyber–physical systems (CPSs) under denial-of-service (DOS) attacks is studied. First, we employ an attack-tolerant strategy to design an augmented error system (AES) for scenarios where both state and reference signal channels are subject to periodic attacks. We then discuss the stochastic stability conditions for the AES and derive the corresponding controller. Subsequently, the preview controller for the original system is developed. Finally, the effectiveness of the obtained results is demonstrated through a numerical simulation using an unmanned ground vehicle (UGV) model, indicating the practical applicability of the proposed control strategy.
Keywords:
cyber–physical systems; preview control; denial-of-service attacks; attack-tolerant strategy; augmented error system MSC:
93C05
1. Introduction
Preview control is a concept that enhances tracking effectiveness and suppresses disturbance by utilizing information about reference signals or disturbances ahead of time [1,2,3]. In a preview control model, measuring these signals in advance and incorporating this “future” information into the controller can save total energy consumption during tracking, thereby improving overall efficiency. Additionally, by applying “future” disturbance information to design a reverse buffer in advance, the impact caused by disturbances can be mitigated. Research on preview control has garnered significant attention, with the augmented error system (AES) being a key technology in the optimal preview control theory [1,2,3]. When designing a preview controller, the AES is first established, which includes the state equation, the error equation, and some equalities regarding previewable signals. Using the maximum principle and solving an equation with previewable signals backwards, an optimal preview controller can be derived. Building upon a fractionation tower model, a series of preview control problems for multi-rate setting systems have been solved [4,5,6]. The core method to address this involves introducing the discrete lifting technique to convert the multi-rate setting system into a single-setting one.
In [7,8], the authors address the preview repetitive control problem. They develop optimal and robust preview repetitive controllers, which are applied in research on permanent magnet synchronous motor drive systems. Similarly, in [9,10,11], preview control technology is applied to carrier-based unmanned aerial vehicles. For the problem of safe auto-landing, deck motion and air-wake disturbances are treated as preview signals. The authors derive optimal and robust control algorithms for both linear and nonlinear models.
Cyber–physical systems (CPSs) are complex dynamic systems that require the transmission and reception of various signals. They are sorts of intelligence systems that can realize the combination and cooperation of multi-dimensional resources [12,13]. By utilizing environmental perception, CPSs can monitor and control physical entities through the integration of embedded computing, network communication, and control engineering. CPSs have been applied to various fields, including autonomous driving [14,15], power systems [16], healthcare [17], etc. Compared to traditional network control systems (NCSs), CPSs offer more efficient and versatile communication modes [18]. CPSs are vital in an interconnected world, bridging the gap between the physical and digital realms. They enable advanced real-time monitoring, automation, and control across a wide range of critical applications to enhance efficiency, safety, and innovation, making them indispensable for the advancement of technology and the functioning of modern society.
However, as CPSs become increasingly essential, they also face significant security threats, such as eavesdropping, denial-of-service (DoS) attacks, man-in-the-middle attacks, spoofing, and falsified messages [19]. These attacks can disrupt communication channels, delay critical signals, and compromise system functionality, leading to potential failures or even catastrophic consequences in vital applications. Among these, DoS attacks are particularly common and easy to implement. By overwhelming network resources or disrupting communication channels, DoS attacks can render essential services unavailable, leading to severe disruptions in operations, financial losses, and even endangering lives in sectors like healthcare, transportation, and energy. Therefore, ensuring the security and resilience of CPSs against such threats is of paramount importance.
Some studies investigate effective defense control strategies from the perspective of attacked systems [20,21,22,23]. In [20], the issue of attack-resilient distributed formation control through online adaptation is explored. A novel distributed control algorithm is proposed, enabling operators to adjust their strategies in real time by utilizing the most recent information gathered on adversaries. The authors of ref. [21] study the problem of designing elastic control strategies for NCSs under DoS attacks. The study proposes analog and digital predictor-based controllers with state resetting, which successfully achieved the targeted control objective across a broad range of DoS signals. In ref. [22], utilizing a simplified model of CPSs and accounting for DoS attacks on the wireless channel of the system’s state signal, a set of attack-tolerance strategies is employed to derive sufficient conditions for ensuring system stochastic stability. Based on these conditions, a controller is subsequently designed. In [23], the problem of output feedback stabilization is examined for a class of discrete-time NCSs with an uncertain transition probability matrix and random packet dropouts. The study establishes sufficient conditions for the existence of an output feedback controller that ensures the stochastic stability of the NCS, utilizing a stochastic Lyapunov function and a linear matrix inequality approach.
When addressing the tracking problems of CPSs, both state and reference sensors can be targeted by attackers. The loss of the reference signals can degrade tracking performance or even cause serious accidents, similar to the blinding effect experienced when driving at night due to oncoming high beams. Motivated by [22,23], this paper examines the preview tracking problem for CPSs under periodic DoS attacks and extends the attack-tolerant strategy to the reference signal channel. Based on this strategy, we discuss the stochastic stability conditions for the constructed AES and design the corresponding preview controller.
Our primary goals are to address the challenges of tracking with DoS attacks in both state and reference signal channels by proposing an attack-tolerant strategy and preview controller. The key contributions of our work include the following:
- (a)
- We propose an attack-tolerant strategy for reference signal channels when the reference signal can be previewed;
- (b)
- Based on the proposed attack-tolerant strategy, we design a corresponding AES and preview controller;
- (c)
- We discuss the stochastic stability of the closed-loop system of the AES under the designed controller.
The paper is organized as follows. In Section 2, we explain the fundamentals, including the system model, DoS attack model, attack-tolerant strategy, and construction of the AES. In Section 3, we present the necessary conditions for the stochastic stability of the AES and propose a preview controller under DoS attacks. In Section 4, the effectiveness of the preview controller from Section 3 is demonstrated through an example involving an unmanned ground vehicle (UGV).
Notations: The notations in this paper are standard. and denote an -dimensional matrix and an matrix, respectively. denotes the set of positive real numbers. stands for the expected value of a random variable. For any matrix , indicates that is positive definite (semi-definite), and denotes the transpositions of . is the identity matrix, and the symbol in a matrix indicates symmetric entries.
2. Problem Statement
Let us consider a class of CPSs with two communication channels subject to DoS attacks, as shown in Figure 1.
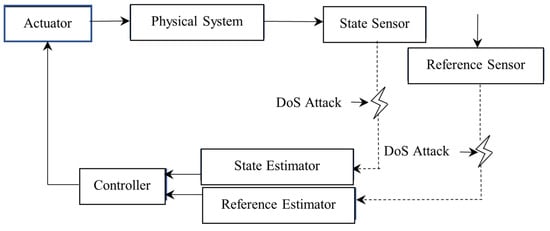
Figure 1.
Structure of CPSs under DoS attacks.
Figure 1 illustrates the structure of CPSs when both the state and reference signal channels are under DoS attacks. Data in Figure 1 are transmitted wirelessly from the state and reference sensors to the controller and through wired channels among other system components. The estimators contain buffers that store the last successfully updated data packets.
Remark 1.
The reference channel described in Figure 1 is justifiable. In [24,25], data on car-following performance, such as the acceleration, speed, and position of tracked vehicles, are collected in a database. All this information can be considered as reference signals and can assist in achieving automatic driving through detectors. However, since the transmission process is wireless, it is susceptible to attacks.
2.1. System Model
First, consider the system defined by
where is the state vector; , , and are the control input, the output vector of the plant, and the disturbance, respectively. , , , and are constant matrices.
We denote the reference signal as . Since future reference signals over a period are available in the preview control problem model, the following assumption is introduced.
Assumption 1 ([26]).
At time instant , the future reference signals are acquirable, where represents the preview length. For after time instant , we have
Remark 2.
Assumption 1 is a common assumption in the preview control problem. In (2), it is reasonable to set beyond the previewable range. From a practical application perspective, when designing a preview controller, more focus should be given to preview information that will imminently impact the system, while the importance of information that is further away should gradually decrease. Information outside the previewable range should be considered invalid. To effec-tively utilize relevant previewable information and exclude invalid data from the controller design, (2) is established.
The measurement of the reference signals, as described above, is shown in Figure 2.
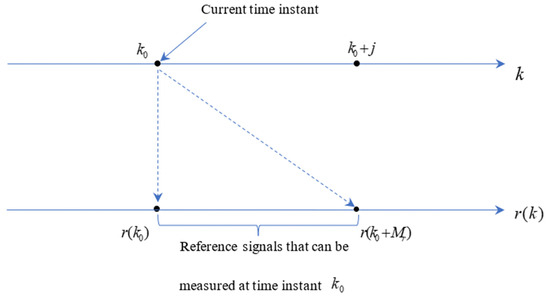
Figure 2.
Reference signals known at time instant in the preview control model.
The tracking error is defined as
Letting
be the sum of , we have
The objective of this paper is to design a preview controller that enables the system output to track the reference signal under periodic DOS attacks. This means that under the designed controller, if , where is a constant, then the system error satisfies .
2.2. DoS Attack Model
In this paper, we consider a type of energy-constrained periodic DoS attack model as described in [22]. Each attack cycle consists of a dormancy stage and an attack stage. During the dormancy stage, , the attackers conserve energy for the upcoming attack. In the attack stage, , they continuously target the estimators, where is the duration of dormancy.
Let and denote the data reception status of the state and reference signals under periodic DoS attacks at time instant , respectively, as follows:
We define and as the probabilities that and during the attack stage and and as the probabilities that and during the dormancy stage, respectively.
Remark 3.
Even during the dormancy stage, packet loss can occur in wireless channels. This is because wireless transmission is subject to multi-path fading and signal degradation, which can in-termittently cause packet loss. These factors are crucial and should be considered when de-signing controllers. As a result, in practice, the values of and are typically less than 1.
2.3. Attack-Tolerant Strategy
To simplify the complexity, this paper adopts a common attack-tolerant strategy from [22] for state signals, extending it to reference signals.
Given the unknown attack strategy of the DoS attackers targeting state signal channel, let represent the state vector used for calculation. If the controller successfully receives the data packets from the sensor, then . Otherwise, . That means that in the state estimator, if the new state information is lost, the previously recorded in the buffer will be used instead. Thus, we have
For the reference signals, the attack-tolerant strategy differs. Let be the reference signal used to calculate . According to Assumption 1, if , then are known, having been used for calculating , and only is unknown. In this case, we set . If , then are updated by . Consequently, can be expressed as
Further, we define
as the sum of used in after introducing the attack-tolerant strategy.
In the following, an AES based on attack-tolerant strategies (8)–(10) is constructed.
2.4. The Construction of the AES
Firstly, we establish some equalities on and .
Denote
Then, we can obtain the following identity
Let
Then, we have
Define
Combining Equations (1), (5), (8), and (10)–(12), we obtain
where
.
As a result, the output in (1) can be expressed as
where . Combining (13) and (15) yields
Thus, (16) represents the AES for calculating the preview controller.
Remark 4.
Unlike the AES construction method in [26], the difference method for the state equation is not used here in (13). The reason for this is that, under the aforementioned attack-tolerant strategies, the AES constructed using the method in [26] must account for the signal reception status at both time instants and . This makes the AES a non-Markov jump system, complicating stability analysis.
3. Preview Controller Design and Stability Analysis
First, consider the preview controller with the following form
where the feedback gain matrices and are block matrices of appropriate dimensions.
Substituting the control input (17) into (16), the closed-loop system becomes
Substituting (8)–(10) into (18) and defining
(18) can be briefly rewritten as
where
and
Since and can only take values of 0 or 1, (19) represents four different systems. We use to distinguish between these systems, and they can be summarized in Table 1.

Table 1.
Values of corresponding to different combinations of and .
Let the state transition probability of from time instant to be denoted by
According to (20) and Table 1, the transition probability depends only on the probabilities of and . Therefore, System (19) is a Markovian jump system.
Next, the stochastic stability of (19) is analyzed.
To ensure that the closed-loop system (19) is stochastically stable, the following definition and lemma are needed.
Definition 1 ([22]).
For the Markov jump system (19) without disturbance, if there exists such that
holds, then (19) is stochastically stable, whereis the initial state of (19).
Lemma 1 (Schur’s complement [27]).
The following three inequalities are equivalent.
- (1)
- ;
- (2)
- ;
- (3)
- .
Then, we can derive the following theorem.
Theorem 1.
For and a given positive scalar , if there exist matrices , such that the following inequalities
hold, where and , then the closed-loop system (19) is stochastically stable.
Proof of Theorem 1.
Consider the Lyapunov function of the form
By analyzing the forward difference in along with System (19), we have
where , , and .
If , then we can obtain
where is the maximal eigenvalue of matrix . Summing both sides of inequality (25) from 0 to , then we have
Letting , (26) is equal to
We set , and according to Definition 1, (27) implies stochastic stability.
By Lemma 1, the inequalities are equivalent to (23), which completes the proof. □
Due to the simultaneous inclusion of and in (23), (23) does not represent linear matrix inequalities (LMIs). To solve for , in , and , we follow the approach in [22] by introducing to replace in (23). Then, using the Cone Complementarity Linearization (CCL) method from [28], the problem of solving (23) is transformed into the following minimization problem constrained by LMIs
where
This minimization problem still cannot be solved directly by the ‘mincx’ solver in the LMI toolbox of Matlab because it contains the quadratic terms . However, we can obtain and the feedback gain matrices and using the following algorithm.
- Step 1: Initialize . Find a feasible solution group , , , and for LMIs in (29).
- Step 2: Minimize the following problemsubject to the LMIs in (29). Denote the feasible solutions for this problem as , , , and .
- Step 3: Ifwhere represents the Frobenius norm of a matrix and is a given stopping criterion, then exit. Otherwise, set and return to step 2.
Additionally, we derive the following corollary for the preview controller of System (1) when both the state and the reference signal channels are subject to DoS attacks.
Corollary 1.
According to Assumption 1, for , and a given positive scalar , if there exist matrices such that the LMIs (23) hold, then the controller (17) functions as the preview controller for System (1) under periodic DoS attacks.
4. Numerical Simulation
Consider an example of an unmanned ground vehicle (UGV) taken from [29]. It is assumed that the UGV travels in a straight line and comes to a complete stop before rotating. The dynamic model is described as follows:
where the variables , , , and represent the position, linear velocity, angular position, and angular velocity, respectively. and denote the mass and moment of inertia. and are the translational and rotational friction coefficients. The inputs and are the force and torque applied of the UGV, and is the output disturbance. We set , , , and . Additionally, and represent the transmission channels.
By applying the forward Euler method to discretize the system with a step size of , we obtain the following discrete-time system:
We set the initial state to and define the reference signal
for straight path movement. For the rotating part, we choose the initial angular position and define the reference signal
and the disturbance
Under the condition of data packet reception, we have Figure 3.
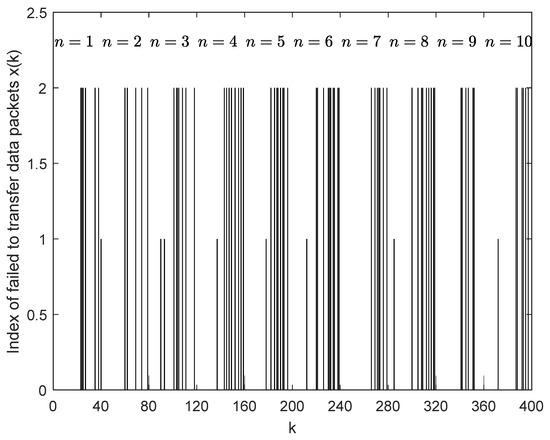
Figure 3.
Packet reception affected by periodic DoS attacks, with and .
Figure 3 illustrates an example of packet reception. In this figure, the long segments represent the packet loss during the attack stages, while the short segments represent the packet loss during the dormancy stages. This is consistent with the packet reception conditions described in Section 2.2, where , and .
The tracking results for System (32) are presented below.
Figure 4 illustrates the output responses using the method from [22] in scenarios with packet loss in both the state signal and reference signal channels. The minimum and values that ensure system stochastic stability are 0.26 and 0.27, respectively. In Figure 4a, the parameters are set to , , and . This subfigure reveals that tracking effectiveness diminishes as decreases, indicating that packet loss in the state signal channel results in degraded tracking performance. In Figure 4b, the parameters are set to , , and . Similarly, this subfigure shows that the tracking effectiveness declines with decreasing , demonstrating that packet loss in the reference signal channel also causes poorer tracking quality. However, the impact on tracking effectiveness is less severe than the loss in the state signal channel.
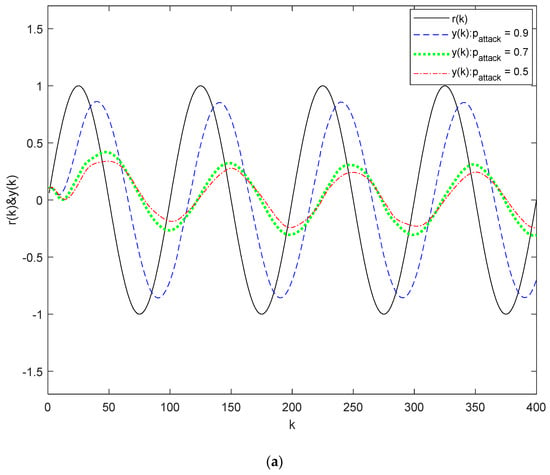
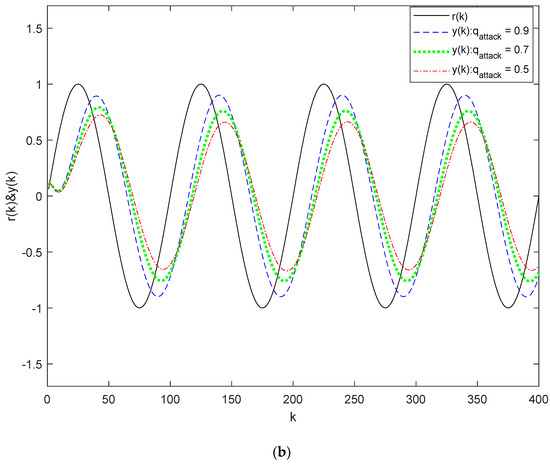
Figure 4.
Output responses for System (32) using the method from [22]: (a) Output responses with different ; (b) Output responses with different .
When using the preview controller, the tracking results are as follows.
Figure 5 compares the output responses under different preview conditions and the method from [22], when there is packet loss in both the state signal and reference signal channels. When , the minimum value that ensures system stochastic stability is 0.26, and the system is stable for any . In Figure 5a, we set , , , and apply varying preview conditions: the method described in [22] (without preview), and . Similarly, in Figure 5b, we use , , , and the same preview conditions. From these subfigures, it is evident that as the preview length increases, the system output can track the reference signal better.
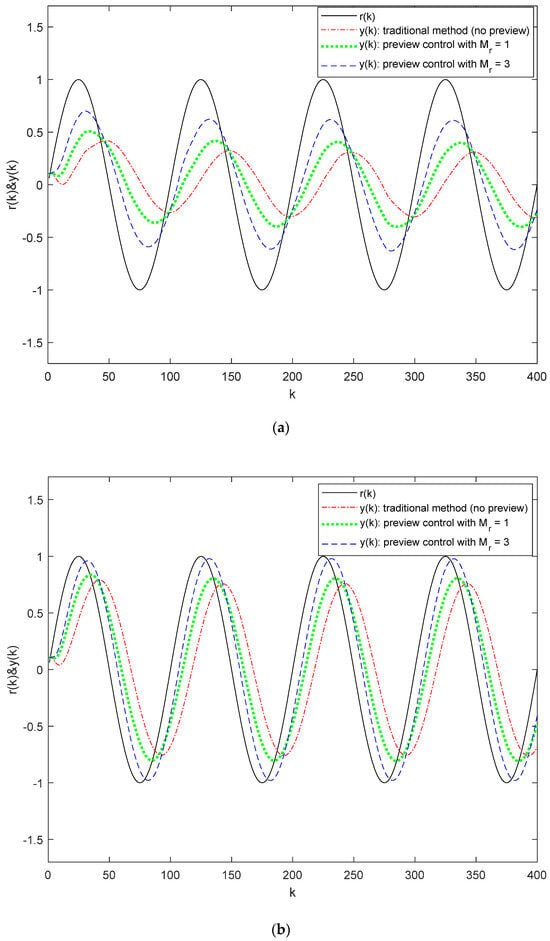
Figure 5.
Output responses for System (32) using the preview controller proposed in this paper and method from [22]: (a) Output responses with packet loss in state signal channel; (b) Output responses with packet loss in reference signal channel.
Next, we consider the case with disturbance, i.e., System (33), and provide an evaluation of the system’s performance. We set in Theorem 1; then, we have the following figures.
Figure 6 illustrates the output responses and error under different preview conditions when there is packet loss in both the state signal and reference signal channels. Figure 6a,c show the system output, and Figure 6b,d show the error. In Figure 6a,b, we set , , , and apply varying preview conditions: the method described in [22] (without preview), and . In Figure 6c,d, we use , , , and the same preview conditions. From these subfigures, it is evident that the system remains stable under the disturbance , and as the preview length increases, the system output can track the reference signal more effectively.

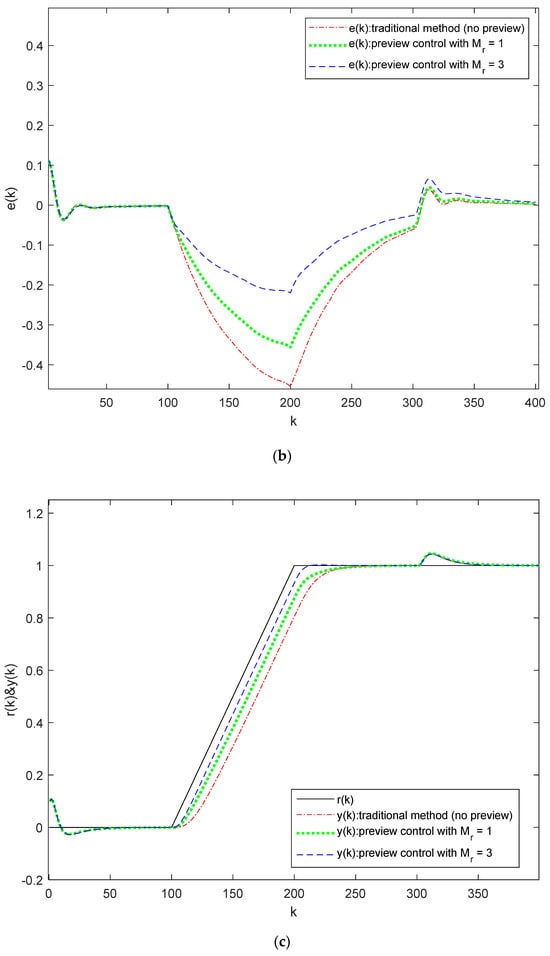
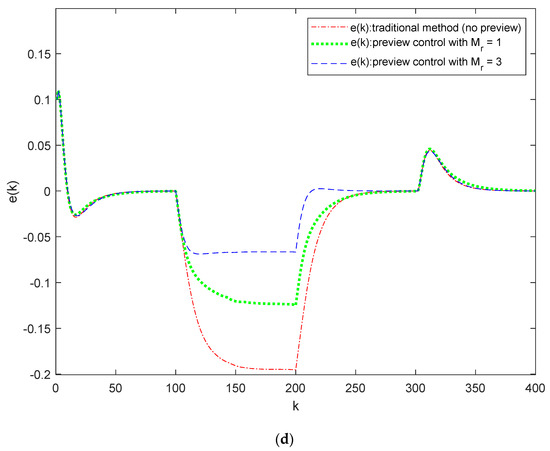
Figure 6.
Output responses and error for System (33) using the preview controller proposed in this paper and the method from [22] (without preview): (a) Output responses with packet loss in state signal channel; (b) Error with packet loss in state signal channel; (c) Output responses with packet loss in reference signal channel; (d) Error with packet loss in reference signal channel.
We use the following index to evaluate the system’s performance
We set , , and . Based on different , we obtain the following table of system performance.
We set , , and . Based on different , we obtain the following table of system performance.
It can be seen from Table 2 and Table 3 that as the level of DoS attacks intensifies, indicated by the decrease in and , the tracking performance of the system gradually deteriorates. Under the same level of DoS attacks, the degradation in tracking performance is more pronounced when packet loss occurs in the state signal channel compared to the reference signal channel. The presence of preview control leads to improvement in the system’s tracking performance.

Table 2.
System performance under different .

Table 3.
System performance under different .
Finally, we analyze the advantages of the reference signal attack-tolerant strategy designed in this paper.
We set ; for different reference signal packet loss scenarios and varying preview conditions, we obtain the following system outputs.
Figure 7 and Figure 8 display the output responses under different packet loss conditions in the reference signal channels, with varying preview conditions. Figure 7a and Figure 8a represent the case without preview, while Figure 7b and Figure 8b correspond to the case with a preview length of . The other parameters used are , , and . By comparing Figure 7a,b, as well as Figure 8a,b, we observe that the tracking error significantly decreases between and , indicating that the preview controller based on the reference signal channel attack-tolerant strategy can mitigate the tracking error between different packet losses in the reference signal channel.

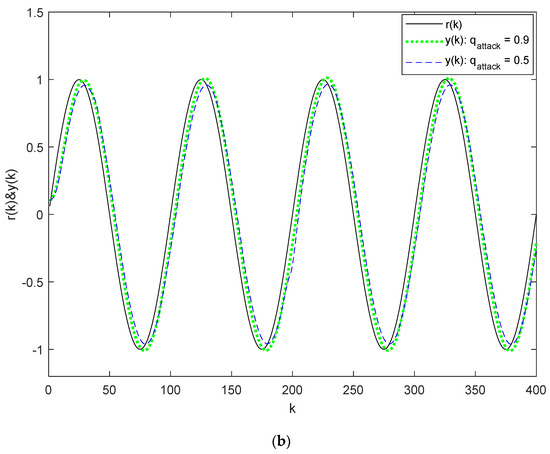
Figure 7.
Output responses for System (32) under different packet loss conditions in the reference signal channel and varying preview conditions: (a) Output responses without preview; (b) Output responses with preview length .

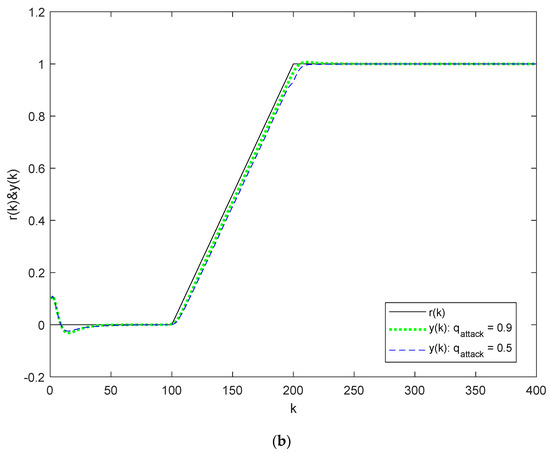
Figure 8.
Output responses for System (33) under different packet loss conditions in the reference signal channel and varying preview conditions: (a) Output responses without preview; (b) Output responses with preview length .
5. Conclusions
This paper presents the design of a preview controller for CPSs subject to periodic DoS attacks. Using an attack-tolerant strategy, a Markovian jump AES is constructed to address these challenges. This study investigates the stochastic stability of the AES and successfully develops a corresponding preview controller. This controller effectively tracks reference signals ahead of time, even under periodic DoS attacks affecting both the state and reference signal channels, and mitigates the tracking error between different packet loss in the reference signal channel. The validity of the proposed approach is demonstrated through a numerical simulation with a UGV model, confirming its practical applicability.
Future research could consider the design of preview controllers for CPSs under actuator saturation and state-constrained conditions and explore the extension of this approach to other types of attacks and evaluate their performance in real-world scenarios.
Author Contributions
Methodology, Writing—original draft, J.W.; Methodology, Software, Writing—review and editing, H.X.; Formal analysis, J.L. and Z.L. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by Interdisciplinary Research Project for Young Teachers of University of Science and Technology Beijing (Fundamental Research Funds for the Central Universities) under Grant FRF-IDRY-20-027.
Data Availability Statement
Data is contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Sheridan, T.B. Three Models of Preview Control. IEEE Trans. Hum. Factors Electron. 1966, HFE-7, 91–102. [Google Scholar] [CrossRef]
- Tomizuka, M. Optimal Continuous Finite Preview Problem. IEEE Trans. Automat. Control. 1975, 20, 362–365. [Google Scholar] [CrossRef]
- Katayama, T.; Ohki, T.; Inoue, T.; Kato, T. Design of an Optimal Controller for a Discrete-Time System Subject to Previewable Demand. Int. J. Control. 1985, 41, 677–699. [Google Scholar] [CrossRef]
- Liao, F.; Takaba, K.; Katayama, T.; Katsuura, J. Design of an Optimal Preview Servomechanism for Discrete-Time Systems in a Multirate Setting. Dyn. Contin. Discret. Impuls. Syst. Ser. B 2003, 10, 727–744. [Google Scholar]
- Liao, F.; Tomizuka, M.; Cao, M.; Wang, D. Optimal Preview Control for Discrete-Time Descriptor Causal Systems in a Multirate Setting. Int. J. Control. 2013, 86, 844–854. [Google Scholar] [CrossRef]
- Liao, F.; Guo, Y.; Tang, Y.-Y. Design of an Optimal Preview Controller for Linear Time-Varying Discrete Systems in a Multirate Setting. Int. J. Wavelets Multires. Inf. Process 2015, 13, 1550050. [Google Scholar] [CrossRef]
- Lan, Y.-H.; Xia, J.-J.; Shi, Y.-X. Robust Guaranteed-Cost Preview Repetitive Control for Polytopic Uncertain Discrete-Time Systems. Algorithms 2019, 12, 20. [Google Scholar] [CrossRef]
- Lan, Y.-H.; He, J.-L.; Li, P.; She, J.-H. Optimal Preview Repetitive Control with Application to Permanent Magnet Synchronous Motor Drive System. J. Franklin Inst. B. 2020, 357, 10194–10210. [Google Scholar] [CrossRef]
- Zhen, Z.; Peng, M.; Xue, Y.; Jiang, S. Robust Preview Control and Autoregressive Prediction for Aircraft Automatic Carrier Landing. IEEE Access 2019, 7, 181273–181283. [Google Scholar] [CrossRef]
- Zhen, Z.; Jiang, S.; Ma, K. Automatic Carrier Landing Control for Unmanned Aerial Vehicles based on Preview Control and Particle Filtering. Aerosp. Sci. Technol. 2018, 81, 99–107. [Google Scholar] [CrossRef]
- Zhen, Z.; Jiang, S.; Jiang, J. Preview Control and Particle Filtering for Automatic Carrier Landing. IEEE Trans. Aerosp. Electron. Syst. 2018, 54, 2662–2674. [Google Scholar] [CrossRef]
- Kim, K.-D.; Kumar, P.R. Cyber-Physical Systems: A Perspective at the Centennial. In Proceedings of the International Congress on Ultra Modern Telecommunications and Control systems and Workshops (CUMTW), St. Petersburg, Russia, 3–5 October 2012; pp. 1287–1308. [Google Scholar]
- Derler, P.; Lee, E.A.; Vincentelli, A.S. Modeling Cyber-Physical Systems. In Proceedings of the Data Stream Mining and Processing (DSMP), Lviv, Ukraine, 21–25 August 2020; pp. 13–28. [Google Scholar]
- Tutsoy, O.; Asadi, D.; Ahmadi, K.; Nabavi-Chasmi, S.Y. Robust Reduced Order Thau Observer with the Adaptive Fault Estimator for the Unmanned Air Vehicles. IEEE Trans. Veh. Technol. 2023, 72, 1601–1610. [Google Scholar] [CrossRef]
- Asadi, D.; Bagherzadeh, S.A. Nonlinear Adaptive Sliding Mode Tracking Control of an Airplane with Wing Damage. J. Aerosp. Eng. 2018, 232, 1405–1420. [Google Scholar] [CrossRef]
- Kazemi, Z.; Safavi, A.A.; Naseri, F.; Urbas, L.; Setoodeh, P. A Secure Hybrid Dynamic-State Estimation Approach for Power Systems under False Data Injection Attacks. IEEE Trans. Ind. Inform. 2020, 16, 7275–7286. [Google Scholar] [CrossRef]
- Gatouillat, A.; Badr, Y.; Massot, B.; Sejdić, E. Internet of Medical Things: A Review of Recent Contributions Dealing with Cyber-Physical Systems in Medicine. IEEE Internet Things 2018, 5, 3810–3822. [Google Scholar] [CrossRef]
- Wang, D.; Wang, Z.; Shen, B.; Alsaadi, F.E.; Hayat, T. Recent Advances on Filtering and Control for Cyber-Physical Systems under Security and Resource Constraints. J. Franklin Inst. B. 2016, 353, 2451–2466. [Google Scholar] [CrossRef]
- Sinha, P.; Jha, V.K.; Rai, A.K.; Bhushan, B. Security Vulnerabilities, Attacks and Countermeasures in Wireless Sensor Networks at Various Layers of OSI Reference Model: A Survey. In Proceedings of the International Conference on Signal Processing and Communication System. (ICSPC), Gold Coast, Australia, 16–18 December 2017; pp. 288–293. [Google Scholar]
- Zhu, M.; Martinez, S. Attack-Resilient Distributed Formation Control via Online Adaptation. In Proceedings of the Conference on Decision and Control and European Control Conference (CDC-ECC), Orlando, FL, USA, 12–15 December 2011; pp. 6624–6629. [Google Scholar]
- Feng, S.; Tesi, P. Resilient Control under Denial-of-Service: Robust Design. Automatica 2017, 79, 42–51. [Google Scholar] [CrossRef]
- Wang, M.-F.; Xu, B.-G. State Feedback Stabilization of Cyber-Physical System under DoS Jamming Attacks. J. Control Decis. 2019, 34, 1681–1687. [Google Scholar]
- Qiu, L.; Zhong, X.; Li, S.; Xu, B. Output Feedback Stabilization of Networked Control Systems with Uncertain Transition Probability Matrix. In Proceedings of the Conference on Intelligent Control and Automation Science (ICONS), Chengdu, China, 2–4 September 2013; pp. 292–297. [Google Scholar] [CrossRef]
- Zhao, D.; Lam, H.; Peng, H.; Bao, S.; LeBlanc, D.J.; Nobukawa, K.; Pan, C.S. Accelerated Evaluation of Automated Vehicles Safety in Lane-Change Scenarios based on Importance Sampling Techniques. IEEE Trans. Intell. Transp. Syst. 2017, 18, 595–607. [Google Scholar] [CrossRef]
- Zhao, D.; Huang, X.; Peng, H.; Lam, H.; LeBlanc, D.J. Accelerated Evaluation of Automated Vehicles in Car-Following Maneuvers. IEEE Trans. Intell. Transp. Syst. 2018, 19, 733–744. [Google Scholar] [CrossRef]
- Liao, F.; Li, L. Robust Preview Control for Uncertain Discrete-Time Systems based on LMI. Optim. Control. Appl. Methods 2017, 38, 1022–1031. [Google Scholar] [CrossRef]
- Boyd, S.; Feron, E.; Ghaoui, L.E.; Balakrishnan, V. Linear Matrix Inequalities in System and Control Theory, 1st ed.; Society for Industrial and Applied Mathematics (SIAM): Pennsylvania, PA, USA, 1994; pp. 7–27. [Google Scholar]
- Chaomel, L.E.; Oustry, F.; Aitrami, M. A Cone Complementarity Linearization Algorithm for Static Output Feedback and Related Problems. IEEE Trans. Autom. Control. 1997, 42, 1171–1176. [Google Scholar]
- Lu, A.-Y.; Yang, G.-H. Secure State Estimation for Cyber-Physical Systems under Sparse Sensor Attacks via a Switched Luenberger Observer. Inf. Sci. 2017, 417, 454–464. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).