Abstract
To support more complex and robust online services, enterprise-class applications prefer to interconnect multiple servers as the pedestal to enhance the system’s interoperability. However, the multiserver architecture always struggles to reconcile the trade-off between convenience and security, leaving users exposed to a variety of network attack threats. Existing security authentication schemes based on the Chebyshev Chaotic Map for multiserver architectures cannot provide three-factor (including password, biometric feature, and smart card) security. Therefore, we propose a novel Physical-Unclonable-Function-based Lightweight Three-Factor Authentication (PUF-LTA) scheme, which can achieve three-factor security. The PUF-LTA scheme mainly includes two components: (1) PUF-assisted registration and (2) lightweight mutual authentication with one-time interaction. During the PUF-assisted registration process, to defend against side-channel attacks on smart cards, the login credentials of users are XORed with the unique identifier generated by the PUF so that the adversary cannot obtain these secret login credentials. During the lightweight mutual authentication process, we combine the Chebyshev polynomial map and symmetric encryption/decryption to negotiate the session key between users and servers, which only needs one interaction. The security performance of PUF-LTA is theoretically proved by leveraging the random oracle model. In contrast with relevant multiserver authentication schemes, PUF-LTA is more efficient and suitable for resource-constrained multiserver environments because it can ensure secure three-factor authentication and support flexible biometrics and password updates with less computation cost.
Keywords:
authentication protocol; multiserver architecture; three-factor security; physical unclonable function MSC:
68M12; 94A62; 94A60
1. Introduction
With significant developments in cloud/edge computing and Internet of Things (IoT), intelligent terminals have become an integral part of human society [1,2,3]. Intelligent terminals often serve as a basic interaction tool among users, experts, and institutions, constantly supporting various remote-access services (e.g., online payment, e-health, and e-commerce) and scanning data (e.g., transactional data, medical diagnosis data, and military data).
As the number of intelligent terminals increases rapidly, it is difficult for conventional single server architecture to respond to high concurrent requests from large-scale terminals in real time due to limited computation, communication, and storage resources. This is because these participants communicate mostly over a public channel, such as wireless communication, and information transmitted over public channels is vulnerable to many cyberattacks (e.g., eavesdropping, replay, interception, modification, and impersonation attacks) [4,5,6].
The single-server authentication scheme is not feasible and burdensome when applied in a multiserver scenario. On one hand, it is very inconvenient for users to register on each server because remembering all usernames and passwords on different servers is very hard. On the other hand, users will suffer from password leakage if they register the same password on different servers. Moreover, existing schemes for the multiserver architecture often adopt modular exponentiation operations or elliptic curve scalar multiplication, which leads to high computation overhead [7,8,9,10].
Hence, designing a robust and lightweight multiserver mutual authentication scheme is crucial for high-level security requirements. Chebyshev’s chaotic map is considered a promising approach to tackle the aforementioned issues because of its efficient computation. To improve authentication efficiency, Chatterjee et al. [11] designed an authentication scheme that integrates Chebyshev’s chaotic map, symmetric encryption/decryption, and a one-way hash function to provide a three-factor authentication protocol for multiserver environments. However, according to the analysis by Yu et al. [12], their integrated scheme still could not resist user impersonation attacks, and it also could not provide enough guarantee for user untraceability. Above all, their scheme did not achieve three-factor security as they claimed. Based on this, an extended authentication scheme was designated by Yu et al., and this scheme was claimed to have the ability to defend against all known security attacks and achieve three-factor security in multiserver environments. Unfortunately, because of design flaws, server impersonation attacks, user impersonation attacks, and man-in-the-middle attacks still can be committed successfully in their scheme. Meanwhile, during the authentication process, user untraceability was not achieved for the scheme-linked personally identifiable information in the user authentication request. It is noteworthy that their scheme still did not achieve three-factor security because biometric information could be obtained by any other legitimate user.
Generally, there are three components in a multiserver authentication architecture, including a registration center (RC), users, and servers. In the authentication process, RC publishes system parameters and offers registration services. Subsequently, users and servers conduct mutual authentication, which means the client verifies the authenticity of the server’s identity, and the server also needs to verify the authenticity of the client’s identity. Ultimately, users can securely access services from the server upon successful mutual authentication. To reduce the computation complexity and improve the security of multiserver authentication, a novel Physical-Unclonable-Function-empowered Lightweight Three-factor Authentication (PUF-LTA) scheme is designed in this paper that requires only one registration for users to access all servers. It ensures true three-factor security, simplifying the user experience and reducing the overall administrative burden.
The main contributions of this paper are listed as follows:
- (1)
- We analyze the three-factor multiserver authentication scheme proposed by Yu et al. [12], and the result shows that their scheme cannot resist man-in-the-middle attacks or user/server impersonation attacks. Furthermore, their scheme also cannot guarantee untraceability or three-factor security.
- (2)
- A novel Physical-Unclonable-Function-based Lightweight Three-factor Authentication (PUF-LTA) scheme is proposed for multiserver environments. In our scheme, the login credentials of users and servers are protected by the PUF, supporting three-factor security. Additionally, during the mutual authentication phase of PUF-LTA, only a one-time interaction is required between users and servers to negotiate their session key. This is because Chebyshev’s chaotic map and symmetric encryption/decryption are skillfully integrated during the negotiation process.
- (3)
- Leveraging random oracle models, the security of the proposed PUF-LTA is theoretically proven. To validate the practicality and efficiency of the proposed PUF-LTA for multiserver architectures, comparisons of security performance, and computation complexity are provided.
The structure of this paper is organized as follows. The related work of multiserver authentication and the preliminaries of this paper are presented in Section 2 and Section 3, respectively. We briefly review Yu et al.’s scheme in Section 4. Section 5 clarifies the vulnerabilities of their scheme. The workflow of the proposed PUF-LTA is presented in Section 6, while the formal and informal security analysis of the PUF-LTA are comprehensively provided in Section 7. Section 8 demonstrates the performance comparison and results discussion against existing methods. We conclude our work in Section 9.
2. Related Work
In the single-server environment, it is general to utilize a password-based authentication mechanism to provide secure authentication over a public channel. Unfortunately, such authentication schemes [13,14,15,16] are impractical and insecure when they are applied to multiserver environments. On one hand, it is troublesome for users to register with each server and remember their different login credentials (e.g., usernames and passwords). On the other hand, strong binding between server access rights and user passwords leads to serious vulnerability if the passwords are leaked or smart cards are lost. For example, the scheme of Li et al. [17] is a password-based authentication framework combined with a neural network for multiserver environments. In the password-based authentication scheme, each user is required to register in the registration center, and then the registered users have unrestricted access to all different servers with the same password. Therefore, their scheme will be unsafe as long as a user’s password is leaked. To resist online dictionary guessing attacks and password testing attacks, Zhang et al. [18] designated a single-sign-on authentication scheme that utilized a password-based threshold to thwart adversaries from compromising the identity servers. Specifically, their scheme introduces multiple identity servers and issues authentication tokens in a thresholded way.
The n-factor authentication protocol enhances the security of the system by adding some static information (e.g., smart card, biological information) as verification proofs. Hence, it is also introduced extensively into multiserver environments to provide stronger identity authentication. In 2014, a robust three-factor authentication scheme was proposed in [19], which integrates biometrics and Elliptic Curve Cryptography (ECC) into a multiserver environment. Although this is the first three-factor authentication scheme that can truly be applied in a multiserver environment, the computation cost and communication cost are substantial, and their scheme also fails to resist server/user impersonation attacks. To address the above drawbacks, Odelu et al. [20] proposed a new three-factor multiserver authentication protocol. However, according to the analysis of Zhang et al., their scheme cannot resist Denial of Service (DoS) attacks or insider attacks, and it lacks robustness, which may lead to system collapse. Then, Zhang et al. [21] proposed an improved three-factor multiserver authentication protocol, which integrates Chebyshev’s chaotic map and a secure sketch algorithm to further reduce computation costs. Unfortunately, the leakage of long-lived master keys could lead to the leakage of past session keys in their scheme, which means their scheme was still vulnerable to Perfect Forward Secrecy. Sudhakar et al. [22] designed a two-factor multiserver authentication protocol, but Cho et al. [23] clarified that their protocol could not guarantee the user’s privacy and would suffer from many cyberspace attacks (e.g., session key disclosure attacks, internal corruption attacks, replay attacks, and man-in-the-middle attacks). Therefore, Cho et al. proposed a more powerful multiserver three-factor protocol for e-governance systems, which aims to integrate a fuzzy extractor to utilize both Elliptic Curve Cryptography (ECC) and biometric features to accomplish two-way authentication. Unfortunately, none of these solutions have achieved three-factor secrecy, that is, when an adversary can obtain two of three factors (password, smart card, or biological information), he/she can launch some attacks. The importance of three-factor secrecy lies in the fact that as long as users ensure that one of the three factors is not obtained by attackers, the security of the solution can be guaranteed.
Recently, a Physical Unclonable Function (PUF), acting as a nonvolatile hardware security technique, has been utilized in loT systems to accomplish mutual authentication among devices [24,25,26,27,28]. Subsequently, the PUF could also be applied in multiserver authentication schemes to improve security. In 2021, Zhang et al. [29] integrated the PUF and cancelable biometrics to accomplish a user authentication scheme in a multiserver environment. Their scheme generates cancelable biometrics through biometrics fusion processing and then provides a multiserver authentication scheme based on secret sharing and Biometrics-as-a-Service. Based on this, their scheme not only ensures the privacy of the user but also enhances the credibility of the biometrics. According to the properties of the PUF, once a physical device deployed with a PUF is attacked, the output value of the PUF will change, which can effectively protect the security of the data stored on the physical device.
Furthermore, Self-Certified Public Key Cryptography (SCPKC) has also been utilized in authentication protocols for multiserver environments. Based on SCPKC, He et al. [30] designed a mobile user authentication protocol, which also provides user anonymity. Compared with two other anonymous mobile user authentication protocols, the computational and communicational costs of their scheme are less than 74.93% and 37.43%. However, Ying et al. [31] stated that their protocol still incurs a significant computational complexity due to the integration of bilinear pairing and scalar multiplication computation. Therefore, Ying et al. further proposed a lightweight protocol, which utilizes SCPKC and ECC. Their scheme utilizes ECC instead of any pairing operation to reduce computational overhead. Besides, their scheme ensures user anonymity and untraceability based on dynamic identities. Unfortunately, Ul Haq et al. [32] found that some specific attacks (e.g., user impersonation attacks, identity guessing attacks, and password guessing attacks) can be carried out against Ying et al.’s scheme, and both strong user anonymity and two-factor security are not truly accomplished. Therefore, Ul Haq et al. designed a new two-factor authentication scheme based on SCPKC to refine Ying et al.’s scheme. Their scheme improves the efficiency of computation and communication compared with Ying et al.’s scheme. Furthermore, Xiong et al. [33] proposed a new multiserver authentication scheme for mobile cloud computing (MCC) environments, which integrates hierarchical access control into the authentication protocol. In 2023, Soni et al. [34] proposed a novel multiserver authentication framework for intelligent healthcare systems, which consists of signature-based static authentication and machine-learning-based continuous monitoring.
3. Preliminaries
3.1. Chebyshev’s Chaotic Map
Chebyshev’s chaotic map can defined as , where , , , , . When . The semigroup property of Chebyshev’s chaotic map can be represented as [35].
Zhang et al. [36] stated that the semigroup property of Chebyshev’s chaotic map holds for Chebyshev polynomials defined on the interval . That is to say, , where , , , , and is a large prime number.
The chaotic map discrete logarithm problem : If there is a Chebyshev chaotic map , where is a large prime number, and and are known, it is computationally infeasible in polynomial-time to calculate the value of .
The Computation of Chaotic Maps Diffie–Hellman Problem : If there is an extended Chebyshev polynomial and , where , and is a large prime number, means that it is computationally infeasible in polynomial-time to calculate the value of .
3.2. Fuzzy Extractor
Biometric information is not completely consistent for the same user (e.g., the different contact surfaces during fingerprint collection). Moreover, considering the threat of information leakage, users hesitate to upload their original biometric information to servers. Therefore, the fuzzy extraction technique is important for biometric application. Dodis et al. [37] proposed the fuzzy extractor algorithm to extract and recover the biometric information. The fuzzy extractor algorithm consists of the generation algorithm and the reproduction algorithm . In contrast to conventional cryptographic keys, their algorithm is neither precisely reproducible nor distributed uniformly. That is, the fuzzy extractor algorithm extracts a uniformly distributed key from repeated noisy readings of a high-entropy secret.
- (1)
- The generation of the biological key:
is the biological information and is the generation function, is the biological key, and is the recovery parameter which should be saved.
- (2)
- The recovery of the biological key:
is the recovery function, is the recovery biometric key, is a new biometric information input by user, and is the recovery parameter that is saved in the user’s device.
3.3. Physical Unclonable Function
The Physical Unclonable Function could generate a unique ‘fingerprint’ or trust anchor for a physical entity [38]. Actually, every integrated circuit (IC) has some subtle differences because normal manufacturing cannot avoid slight deviations. For a physical entity with an integrated circuit (IC), the PUF exploits this deviations to generate a unique challenge–response pair.
The PUF has the properties as follows:
- The output of a PUF is dependent on the physical characteristics of the IC.
- The output of a PUF must be unpredictable.
- The PUF circuit is unclonable.
- The output of the PUF will change as long as any alteration happens to the physical characteristics of the system.
Ideally, physically cloning a PUF is infeasible, and PUFs do not store any secrets but generate the response upon a challenge. More importantly, when a PUF circuit is attacked by any active manipulation (e.g., side-channel attacks), its CRP mapping mechanism will be destructed and the challenge-response pair will also change.
3.4. System Model
Figure 1 is a multiserver model. Any service provider may have one or more servers, and users can use multiserver authentication to obtain services from these servers. A multiserver system includes users, servers, and a registration center (RC). RC will publish the system initialization parameters first; then users and servers should register to the RC through a secure channel, respectively; finally, over a public channel, a user and a server will conduct mutual authentication, negotiate the session key, and securely communicate.
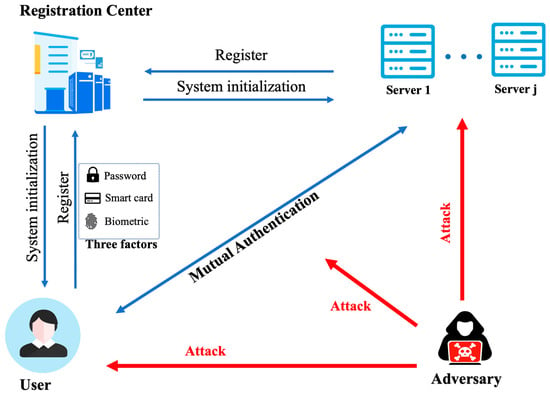
Figure 1.
Network model of a multiserver environment.
3.5. Adversarial Model
According to the Dolev–Yao model [39] and the security requirements of multiserver authentication, we define the adversary model as follows:
- (1)
- An adversary could register as a legitimate user or server, but the registration center is completely trustworthy.
- (2)
- Users and servers can conspire to impersonate another entity. For example, they can impersonate a user to access another server or impersonate a server to provide false resources to other users.
- (3)
- An adversary has the ability to intercept, eavesdrop, modify, and replay all messages transmitted by public channels.
- (4)
- An adversary can obtain any two of the three factors to launch attacks but cannot simultaneously obtain all three factors.
4. Review of a Multi-Server Authentication Scheme
Yu et al. [12] proposed an extended chaotic-map-based authentication and key agreement scheme for a multiserver environment. Their scheme mainly consists of five phases: the system setup phase, server registration phase, user registration phase, login and authentication phase, and user password and biometric update phase. Here, we omit the last phase. Table 1 lists the notations used in this paper.

Table 1.
Notations used in this paper.
4.1. System Setup Phase
The chooses two random numbers and in and sets them as the system master keys. Then, chooses a secure one-way hash function .
4.2. Server Registration Phase
Step 1: chooses identity and transmits it to over a secure channel.
Step 2: Once is received, computes and publishes . Afterward, transmits back to through a secure channel.
Step 3: receives and stores it safely.
4.3. User Registration Phase
Step 1: inputs and , and enters . Then, utilizes the biometric hash function to obtain and computes , . Finally, sends to to register over a secure channel.
Step 2: Upon registration request, calculates , , , where . Then, computes , , , where , and m denotes the maximum number of servers. Next, are stored into the , and is distributed to each safely.
Step 3: keeps the card safely.
4.4. Login and Authentication Phase
Step 1: inserts and inputs , , and enters . calculates , , and and then verifies whether ; if not, rejects the session; else, randomly selects a number , chooses the server’s identity , and computes , , , , , and . Finally, sends to server .
Step 2: Upon the login request from , calculates , , , , and and verifies whether equals . If not, rejects the session. Else, selects a random number and calculates , , , and . Afterward, sends to .
Step 3: Upon receiving , calculates . verifies whether , if not, rejects the session; otherwise, computes h() and and obtains the session key . Finally, sends to .
Step 4: receives and verifies whether h() holds, if not, discards the session; otherwise, calculates and negotiates the same session key with : .
5. Cryptanalysis of a Multi-Server Authentication Scheme
5.1. User Traceability
Assuming that an adversary is a legitimate user , he/she can register a legal and obtain , .
During the login and authentication phase, , where was transmitted in public channel, is public, and is written into the adversary’s . Then, the adversary can extract from , where . It is obvious that is bound with .
In this case, if an adversary is a legal user, they can distinguish whether two sessions are initiated by one user through .
5.2. User Impersonation Attack
Firstly, we assume that an adversary is a legal user and they can register as a legal . The adversary computes his/her and obtains , from . Then, the adversary obtains and finally obtains the server’s .
Then, the messages sent in the public channel can be eavesdropped on by the adversary. The adversary sends to the server to impersonate the legal user. As long as the server sends , the adversary computes , = , obtains , , and computes .
Finally, certifies that the adversary is legal after receiving .
5.3. Server Impersonation Attack
At first, an adversary can register a legal , therefore, the adversary knows and obtain , from . Then, the adversary obtains , and finally gets server’s .
Then, the adversary can eavesdrop on the messages in the public channel and obtain from . The adversary tries to impersonate the legal server. The adversary computes , = , and verifies whether equals . Next, the adversary chooses a random number and calculates , , , . Afterward, the adversary sends to .
Next, computes , verifies whether holds, computes h(), , and obtains the session key . Finally, sends to the adversary.
In the end, the adversary computes and impersonates the server successfully.
5.4. Man-in-the-Middle Attack
At first, an adversary can register a legal ; therefore, the adversary knows and obtains , from . Then, the adversary obtains and finally obtains the server’s .
Next, the adversary selects a random number and calculates .
After receiving from , the adversary computes , = , and verifies whether equals . Next, the adversary computes , , and . Afterward, the adversary sends to .
After receiving from the adversary, computes , verifies whether holds, computes h(), , and obtains the session key . Finally, sends to the adversary. In the end, the adversary computes and impersonates the server successfully.
Meanwhile, the adversary computes , , and and sends to server .
After receiving from the adversary, server computes , , , , and and verifies whether equals . Then, chooses a random number and calculates , , , and . Afterward, sends to , but the message is hijacked by the adversary. After the adversary receives and computes , h(, , they obtains the session key . Finally, the adversary sends to .
Step 4: receives and verifies whether equals h(), if not, rejects the session; otherwise, verifies that is the legitimate user. Then, calculates and negotiates the session key with the adversary: .
Finally, the adversary commits a man-in-the-middle attack successfully.
5.5. Three-Factor Security
According to the definition of three-factor security, if an adversary can obtain the user’s biometric and the information stored in smart card , then the adversary can guess the ’s password and compute , , , , and and check whether or not. If yes, the guessed password is correct. Otherwise, they reguess it again till the correct password is found.
Once the adversary obtains the correct password, he/she can know the correct , . And the adversary can also obtain from the public channel and obtains . Because , the adversary can guess the correct , and the adversary can also launch user impersonation attacks.
Therefore, Yu et al.’s scheme cannot achieve three-factor security.
6. The Proposed Scheme
The proposed scheme consists of five phases: (1) System initialization. (2) Sever registration. (3) User registration. (4) Mutual authentication and key agreement. (5) User password and biometric update phase.
6.1. System Initialization
The selects two random numbers and in as master keys of the system. Then, chooses a secure one-way hash function .
6.2. Sever Registration
selects as an identity of server , computes , and generates a random number , computes , then sends to through a secure channel, and then publishes .
After receiving from , generates a challenge and computes and then stores secretly.
Figure 2 depicts this phase. It is worth mentioning that using 1 and 2 in calculating the hash functions of and can reduce the problem of selecting and storing random numbers.
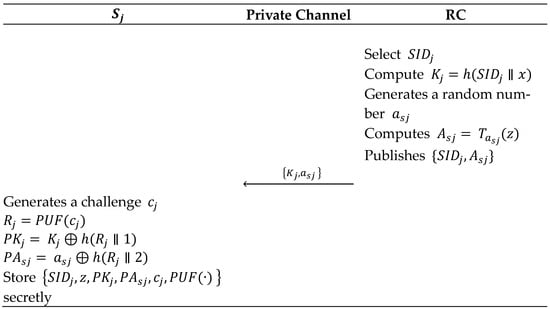
Figure 2.
Sever registration phase.
6.3. User Registration
Step 1: The user generates an identity number and password and inputs their biometrics . Then, the fuzzy function is utilized to obtain . Then, makes a request to the registration center to register over a secure channel.
Step 2: Upon the request of , calculates , where is registration time, . And then, sends to over a secure channel.
Step 3: Upon sending the message from , calculates , and generates a challenge and computes , , . Finally, stores {PPIDi, Ai, PCi, ci, PUF (·), n, h(·), into and keeps card safely.
Figure 3 depicts this phase. It is worth mentioning that using when calculating can effectively resist password and identity guessing attacks.
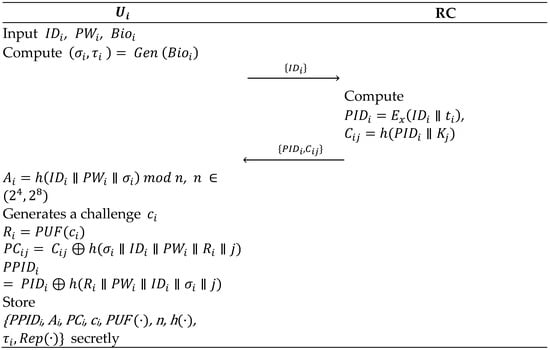
Figure 3.
User registration phase.
6.4. Mutual Authentication and Key Agreement
Figure 4 depicts mutual authentication and key agreement phase.

Figure 4.
Mutual authentication and key agreement.
Step 1: inserts smart card and inputs the identity number , password , and biometrics . Then, computes and verifies whether holds, if not, rejects the session; otherwise, computes , , . Then, generates two random numbers, , and selects the identity of the server and computes , , . sends to via a public channel.
Step 2: Upon the login request from , decrypts and obtains . Then, verifies the freshness of and computes . If , rejects the session; otherwise, generates a random number and calculates , , . Finally, sends to through a public channel.
Step 3: receives from and decrypts it via Decrypt . checks the freshness of and the validity of . Then, computes . If , terminates the session; othewiser sets the session key = . The mutual authentication between and is established successfully.
6.5. User Password and Biometric Update Phase
Step 1: inserts card , inputs and , and their biometrics . Then, computes and verifies whether equals , if not, discards the login request; otherwise, asks to enter a new password and new biological information.
Step 2: Upon receiving the new password and new biometric feature of , uses the fuzzy extractor to calculate , , , .
Step 3: replaces , , , with , , , and .
7. Security Analysis
7.1. Provable Security
Based on the random oracle model, we formally prove the semantic security of our scheme below:
Our scheme is denoted as Scheme II and involves three entities:
- (a)
- A user with identity , password , and biometrics ;
- (b)
- A registration center with a private key ;
- (c)
- An application server with identity .
They all are treated as an oracle with three possible states:
- (a)
- ;
- (b)
- ;
- (c)
- .
In this model, there is a probabilistic polynomial-time () adversary and a challenger . The security of our scheme is proved by a challenge–response game between the adversary and the challenger . In this game, simulates varieties of attacks by inquiring to in polynomial-time. The queries are listed as follows:
- (1)
- Hash : An initially empty list is maintained by challenger in this query. When executes this query with input , returns an output if the tuples () exists. Otherwise, challenger selects a random number and sends to . Meanwhile, inserts () in to maintain consistency.
- (2)
- Execute (): In this query, the adversary can eavesdrop on the entire authentication process of Scheme II. If asks to execute this query, calculates the messages according to the steps in II and returns the results to .
- (3)
- Send (, ): In this query, can attack Scheme II actively. When executes this query with a message , checks if is valid. If it is valid, calculates some results as the steps of Scheme II; otherwise, ignores this query.
- (4)
- Reveal (): In this query, returns the current session key between and to .
- (5)
- Corrupt (): can obtain any two of three factors: password and smart card, smart card and biometric, or biometric and password. It is impossible to obtain three factors simultaneously. In this query, outputs different results as follows:If c = 0, outputs the secret data stored in of to .If c = 1, outputs the password of to .If c = 2, outputs the biometric information of to .
- (6)
- Test (): In this query, generates a random secret coin . If b = 1, returns with the correct session key. If b = 0, randomly generates a number with the same length of the session and returns it to .
Definition 1
(AKA-Secure). Pr[S] is denoted as the success probability of to breach Scheme II. If executes the test query and guesses a correct bit , we say that breaches the semantic security of Scheme II. Then, the advantage of to breach the semantic security of Scheme II is denoted as = , where AKA represents the authenticated key agreement. Our Scheme II achieves semantic if is negligible for any adversary .
Theorem 1.
We assume that is the password space, , represents the size of the biometric information, and represents the length of . Suppose , and denote the number of queries that executes send, execute, and hash . Then, we have
In polynomial-time , the probability of to successfully solve the CDH problem is denoted as , where .
Proof.
We prove the security of the session key in Scheme II by executing the following games , . Let refer to the event that tries to breach the secrecy of the session key negotiated in each . Additionally, we assume that an event E may happen when executes Scheme II such that the event E is independent of and can be detected by . It is noteworthy that and are indistinguishable, except when E occurs.
Therefore,
- (1)
- : In this game, the simulation of breaching the semantic security of Scheme II is executed in the random oracle model (ROM), and we have
- (2)
- In this game, simulates the ROM by executing queries, including execute, send, and hash queries. In the hash query, tries to find the collisions for . From the conclusion of a birthday attack, the success probability of a hash collision is . Executing a send query or an execute query can generates the message. Therefore, the success probability of to find a collision is controlled by at most , where . Then, we have:
- (3)
- : Here, can execute Corrupt () to obtain the secret information stored in on the condition that the device is lost or stolen. simulates as follows:
- (a)
- executes a Corrupt () query to guess the password of from password space within a number of send queries. Hence, the probability of a successful guess is .
- (b)
- executes a Corrupt () query and speculates the biometric key of .
- (i)
- The probability of successful guessing (-bit) is .
- (ii)
- can take advantage of the false positive to guess , which is chosen randomly from a uniform distribution .
Because can guess either the password or biometric key but not both, can execute either the or queries. The total probability of success is
- (4)
- In this game, to breach the security of mutual authentication, executes the queries of send (), send (), and send () to .
- (a)
- Send () query: selects two random numbers, , and calculates , , . Then, the query answers .
- (b)
- Send () query: Compute , . If , rejects the session; otherwise, generates a random number and calculates , . Afterwards, the query responds with .
- (c)
- Send () query: Compute . checks the freshness of and the validity of . Then, computes . If , terminates the session; otherwise = .
Assume that the adversary tries to generate the false value . This game is indistinguishable from the previous game , except when refuses a valid or refuses a valid . Therefore, we have
- (5)
- In this game, tries to guess the . If tries to compute the session key , the CDH problem must be solved for the instance within the polynomial-time bound , where , since are randomly chosen from uniformly, and either implements the execute query or send query.Therefore, we obtain
If employs a private oracle , then seeks the valid value in and conveys it to . Otherwise, sends a random bit string . tries to guess a bit , and the probability of successfully guessing is not more than . Therefore, we obtain
Finally, we add (1)–(7) and have
□
7.2. Informal Security Analysis
- (1)
- Perfect Forward Secrecy
This feature means that even if the password and biometrics of user are exposed to an adversary, all prior session keys still remain secure. We make the assumption that all private keys of the server and , , of the user are compromised, and the adversary obtains , which is stored in the smart card. Then, the adversary still cannot acquire the due to the property of the PUF. Moreover, because the session key is , even if an adversary can know all the long-term keys used in this protocol, it is computationally infeasible for the adversary to calculate because of the intractability of the Computational Diffie–Hellman Problem (CDHP).
- (2)
- Known-Key Security
This property means that the adversary cannot compute the next session key, even if he/she has obtained some previous session keys. To be specific, the session key is variable in our scheme due to the random number {. Therefore, the adversary cannot know any useful information and cannot compute the next session key, even if they can acquire the session key.
- (3)
- Session Key Secrecy
Based on our protocol, the user and the server can negotiate a session key for later communication when they finish the mutual authentication and key agreement phase. The session key will be = = .
- (4)
- User Anonymity and Untraceability
In our scheme, although the authentication request message {} includes the user’s pseudoidentity , the adversary cannot obtain the because of the unknown encryption key . Specifically, the user computes , , . It is clear that the user’s identity is encrypted by a key negotiate between the user and the server. Moreover, the computes , where is the registration time. As a result, the user is anonymous to the server and adversary.
In addition, the random numbers , are different in each session, so the authentication request message {} is also different in each session. So, our scheme achieves untraceability.
- (5)
- Replay Attack
In our scheme, three random numbers are utilized to resist the replay attack. Therefore, even if an adversary replays the message {}, they cannot calculate the session key without knowing the random numbers .
- (6)
- Offline Identity/Password Guessing Attacks
Because the user’s identity and password is included in , , if an adversary obtains all the information stored in the device, obtains the user’s biometric information, and guesses () to satisfy , , there are candidates for the () pair when n = 256. Moreover, the adversary cannot know which pair is right due to the property of the PUF.
- (7)
- Three-Factor Secrecy
If an adversary can know the user’s biometric information and all the information stored on the device, he/she cannot guess the correct () pair. If an adversary can know the user’s biometric information and password, he/she cannot know the {} from the authentication messages. If an adversary can know the password and all the information stored in the device, he/she cannot know the user’s biometric information .
- (8)
- Device Lost Attack
of stores , where , , , . So, an adversary cannot obtain {} due to the property of the PUF. Therefore, according to above analysis, we can know that an adversary can’t obtain any valuable information to launch attacks even if he/she gets the information stored in device.
- (9)
- User/Server Impersonation Attacks
Suppose an adversary wants to impersonate the user to access the server; however, they cannot forge the valid message {}, because they cannot know {}, which are protected by the PUF.
Suppose an adversary wants to impersonate the server to pass the authentication by the user, however, they cannot forge the valid message . Moreover, the adversary does not know the secret key of the server, so the secret message cannot be decrypted. So the adversary cannot obtain and cannot forge a session key.
- (10)
- Man-in-the-Middle Attack
Our scheme achieves trustworthy mutual authentication between and , and any adversary can neither impersonate users nor servers. So, our scheme can resist man-in-the-middle attacks.
- (11)
- Stolen-Verifier Attack/Physical Capturing Attacks
Because the important information is stored in the user’s device and the servers, and they are all protected by the PUF, our scheme can resist stolen-verifier attacks and physical capturing attacks.
8. Performance Analysis
In Table 2, we present a comparison of the security features between our scheme and some related multiserver schemes [11,12,23,31,33,34].

Table 2.
Security features comparison.
We also simulated the computation cost in the environment of Intel Pentium4 2600 MHz processor with 1024 MB RAM. Table 3 displays the execution time for different operations. Table 4 shows the comparison of computation costs between ours and related protocols. The computation cost of bitwise operation like XOR is negligible.

Table 3.
Execution time of cryptographic operations.

Table 4.
Comparison of Computation Costs.
We focus on the mutual authentication and key agreement phase because the server and user registration phase executes only once. In terms of the mutual authentication and key agreement phase, our scheme’s computation cost for a user is 86.56 ms, and it is 85.56 ms for a server. According to Table 4, it is obvious that our authentication scheme costs less than [23,31,33,34]. Our scheme’s computation costs are more than [11,12], but this is acceptable because our scheme has stronger security.
It is assumed that the output of hash function is 160 bits (SHA-1 hash function), the block size of symmetric encryption/decryption (AES) is 128 bits, the elliptic curve point is 320 bits, and the identity, random number, timestamp, and other parameters is 128 bits. We focus on the mutual authentication and key agreement phase because the server and user registration phase executes only once. During the mutual authentication and key agreement phase, only two messages, and , are transmitted in our scheme. To be specific, , , and . The length of two interactive messages is (128 + 3 × 128 + 160) + 128 × ((128 + 128 + 128 + 160)/128) = 1312.
9. Conclusions
We have shown that Yu et al.’s three-factor multiserver authentication scheme has several security flaws, and we designed a new three-factor lightweight authentication based on Chebyshev’s chaotic map and the PUF. We analyzed our authentication scheme through the random oracle model and proved our scheme is secure. Furthermore, our scheme eliminates the requirement for RC during mutual authentication and only requires a one-time mutual interaction. Therefore, our scheme is more efficient and practical in multiserver environments, especially for resource-restrained mobile devices.
Author Contributions
Y.Z., designing, experimentation, writing, and security proof; Q.X., conceptualization, methodology, validation, review, editing, revise, funding. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by the National Natural Science Foundation of China (Grant No. U21A20466), and the Hangzhou Joint Fund of the Zhejiang Provincial Natural Science Foundation of China (Grant No. LHZSZ24F020002).
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Celik, A.; Romdhane, I.; Kaddoum, G.; Eltawil, A.M. A Top-Down Survey on Optical Wireless Communications for the Internet of Things. IEEE Commun. Surv. Tutor. 2023, 25, 1–45. [Google Scholar] [CrossRef]
- Tange, K.; De Donno, M.; Fafoutis, X.; Dragoni, N. A Systematic Survey of Industrial Internet of Things Security: Requirements and Fog Computing Opportunities. IEEE Commun. Surv. Tutor. 2020, 22, 2489–2520. [Google Scholar] [CrossRef]
- Gai, K.; Guo, J.; Zhu, L.; Yu, S. Blockchain Meets Cloud Computing: A Survey. IEEE Commun. Surv. Tutor. 2020, 22, 2009–2030. [Google Scholar] [CrossRef]
- Schlette, D.; Caselli, M.; Pernul, G. A Comparative Study on Cyber Threat Intelligence: The Security Incident Response Perspective. IEEE Commun. Surv. Tutor. 2021, 23, 2525–2556. [Google Scholar] [CrossRef]
- Rawal, B.S.; Berman, L.; Ramcharan, H. Multi-client/Multi-server split architecture. In Proceedings of the The International Conference on Information Networking 2013 (ICOIN), Bangkok, Thailand, 27–30 January 2013; Volume 201, pp. 696–701. [Google Scholar]
- Ul Haq, I.; Wang, J.; Zhu, Y.; Maqbool, S. A survey of authenticated key agreement protocols for multi-server architecture. J. Inf. Secur. Appl. 2020, 55, 102639. [Google Scholar]
- Lee, T.F. Enhancing the security of password authenticated key agreement protocols based on chaotic maps. Inf. Sci. 2015, 290, 63–71. [Google Scholar] [CrossRef]
- Lu, Y.; Li, L.; Peng, H.; Xie, D.; Yang, Y. Robust and Efficient Biometrics Based Password Authentication Scheme for Telecare Medicine Information Systems Using Extended Chaotic Maps. J. Med. Syst. 2015, 39, 65. [Google Scholar] [CrossRef]
- Kumari, S.; Li, X.; Wu, F.; Das, A.K.; Arshad, H.; Khan, M.K. A user friendly mutual authentication and key agreement scheme for wireless sensor networks using chaotic maps. Future Gener. Comp. Syst. 2016, 63, 56–75. [Google Scholar] [CrossRef]
- Abbasinezhad-Mood, D.; Nikooghadam, M. Efficient Anonymous Password-Authenticated Key Exchange Protocol to Read Isolated Smart Meters by Utilization of Extended Chebyshev Chaotic Maps. IEEE Trans. Industr. Inform. 2018, 14, 4815–4828. [Google Scholar] [CrossRef]
- Chatterjee, S.; Roy, S.; Das, A.K.; Chattopadhyay, S.; Kumar, N.; Vasilakos, A.V. Secure Biometric-Based Authentication Scheme Using Chebyshev Chaotic Map for Multi-Server Environment. IEEE Trans. Depend. Secure 2018, 15, 824–839. [Google Scholar] [CrossRef]
- Yu, Y.; Taylor, O.; Li, R.; Sunagawa, B. An Extended Chaotic Map-Based Authentication and Key Agreement Scheme for Multi-Server Environment. Mathematics 2021, 9, 798. [Google Scholar] [CrossRef]
- He, D.; Bu, J.; Chan, S.; Chen, C.; Yin, M. Privacy-Preserving Universal Authentication Protocol for Wireless Communications. IEEE Trans. Wirel. Commun. 2011, 10, 431–436. [Google Scholar] [CrossRef]
- Tsai, J.L.; Lo, N.W.; Wu, T.C. Novel Anonymous Authentication Scheme Using Smart Cards. IEEE Trans. Industr. Inform. 2013, 9, 2004–2013. [Google Scholar] [CrossRef]
- Huang, X.; Chen, X.; Li, J.; Xiang, Y.; Xu, L. Further Observations on Smart-Card-Based Password-Authenticated Key Agreement in Distributed Systems. IEEE Trans. Parall. Distr. 2014, 25, 1767–1775. [Google Scholar] [CrossRef]
- Wang, D.; He, D.; Wang, P.; Chu, C.H. Anonymous Two-Factor Authentication in Distributed Systems: Certain Goals Are Beyond Attainment. IEEE Trans. Depend. Secure 2015, 12, 428–442. [Google Scholar] [CrossRef]
- Li, L.H.; Lin, L.C.; Hwang, M.S. A remote password authentication scheme for multiserver architecture using neural networks. IEEE Trans. Neural. Networ. 2001, 12, 1498–1504. [Google Scholar]
- Zhang, Y.; Xu, C.; Li, H.; Yang, K.; Cheng, N.; Shen, X. PROTECT: Efficient Password-Based Threshold Single-Sign-On Authentication for Mobile Users against Perpetual Leakage. IEEE Trans. Mobile. Comput. 2021, 20, 2297–2312. [Google Scholar] [CrossRef]
- He, D.; Wang, D. Robust Biometrics-Based Authentication Scheme for Multiserver Environment. IEEE Syst. J. 2015, 9, 816–823. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K.; Goswami, A. A Secure Biometrics-Based Multi-Server Authentication Protocol Using Smart Cards. IEEE Trans. Inf. Foren. Sec. 2015, 10, 1953–1966. [Google Scholar] [CrossRef]
- Zhang, M.; Zhang, J.; Tan, W. Remote three-factor authentication protocol with strong robustness for multi-server environment. China Commun. 2017, 14, 126–136. [Google Scholar] [CrossRef]
- Sudhakar, T.; Natarajan, V.; Gopinath, M.; Saranyadevi, J. An Enhanced Authentication Protocol for Multi-Server Environment Using Password and Smart Card. Wirel. Pers. Commun. 2020, 115, 2779–2803. [Google Scholar] [CrossRef]
- Cho, Y.; Oh, J.; Kwon, D.; Son, S.; Yu, S.; Park, Y.; Park, Y. A Secure Three-Factor Authentication Protocol for E-Governance System Based on Multiserver Environments. IEEE Access 2022, 10, 74351–74365. [Google Scholar] [CrossRef]
- Herder, C.; Yu, M.D.; Koushanfar, F.; Devadas, S. Physical Unclonable Functions and Applications: A Tutorial. Proc. IEEE 2014, 102, 1126–1141. [Google Scholar] [CrossRef]
- Che, W.; Saqib, F.; Plusquellic, J. PUF-Based Authentication. In Proceedings of the 2015 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Austin, TX, USA, 2–6 November 2015; pp. 337–344. [Google Scholar]
- Wang, W.; Chen, Q.; Yin, Z.; Srivastava, G.; Gadekallu, T.R.; Alsolami, F.; Su, C. Blockchain and PUF-Based Lightweight Authentication Protocol for Wireless Medical Sensor Networks. IEEE Internet Things 2022, 9, 8883–8891. [Google Scholar] [CrossRef]
- Gu, C.; Chang, C.H.; Liu, W.; Yu, S.; Ma, Q.; O’neill, M. A Modeling Attack Resistant Deception Technique for Securing PUF based Authentication. In Proceedings of the 2019 Asian Hardware Oriented Security and Trust Symposium (AsianHOST), Xi’an, China, 16–17 December 2019; pp. 1–6. [Google Scholar]
- Zhou, X.; Wang, S.; Wen, K.; Hu, B.; Tan, X.; Xie, Q. Security-Enhanced Lightweight and Anonymity-Preserving User Authentication Scheme for IoT-Based Healthcare. IEEE Internet Things 2023, 1. [Google Scholar] [CrossRef]
- Zhang, H.; Bian, W.; Jie, B.; Xu, D.; Zhao, J. A Complete User Authentication and Key Agreement Scheme Using Cancelable Biometrics and PUF in Multi-Server Environment. IEEE Trans. Inf. Forensics Secur. 2021, 16, 5413–5428. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Kumar, N.; Wu, W. Efficient and Anonymous Mobile User Authentication Protocol Using Self-Certified Public Key Cryptography for Multi-Server Architectures. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2052–2064. [Google Scholar] [CrossRef]
- Ying, B.; Nayak, A. Lightweight remote user authentication protocol for multi-server 5G networks using self-certified public key cryptography. J. Netw. Comput. Appl. 2019, 131, 66–74. [Google Scholar] [CrossRef]
- Ul haq, I.; Wang, J.; Zhu, Y. Secure two-factor lightweight authentication protocol using self-certified public key cryptography for multi-server 5G networks. J. Netw. Comput. Appl. 2020, 161, 102660. [Google Scholar] [CrossRef]
- Xiong, L.; Li, F.; He, M.; Liu, Z.; Peng, T. An Efficient Privacy-Aware Authentication Scheme With Hierarchical Access Control for Mobile Cloud Computing Services. IEEE Trans. Cloud Comput. 2022, 10, 2309–2323. [Google Scholar] [CrossRef]
- Soni, P.; Pradhan, J.; Pal, A.K.; Islam, S.H. Cybersecurity attack-resilience authentication mechanism for intelligent healthcare system. IEEE Trans. Ind. Inform. 2023, 19, 830–840. [Google Scholar] [CrossRef]
- Kocarev, L.; Tasev, Z. Public-key encryption based on Chebyshev maps. In Proceedings of the International Symposium on Circuits and Systems, ISCAS ’03, Bangkok, Thailand, 25–28 May 2003; Volume 3, pp. 28–31. [Google Scholar]
- Zhang, L. Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos Solitons Fractals 2008, 37, 669–674. [Google Scholar] [CrossRef]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy Extractors: How to Generate Strong Keys from Biometrics and Other Noisy Data. In Proceedings of the Advances in Cryptology—EUROCRYPT 2004, Interlaken, Switzerland, 2–6 May 2004; Cachin, C., Camenisch, J.L., Eds.; Springer: Berlin/Heidelberg, Germany, 2004; pp. 523–540. [Google Scholar]
- Gao, Y.; Al-Sarawi, S.F.; Abbott, D. Physical unclonable functions. Nat. Electron. 2020, 3, 81–91. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inform. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).