Abstract
The extensive application of the Internet of Things (IoT) and artificial intelligence technology has greatly promoted the construction and development of smart cities. Smart home as the foundation of smart cities can optimize home lifestyles. However, users access the smart home system through public channels, and the transmitted information is vulnerable to attack by attackers, and the privacy and data security of the home user will be difficult to be guaranteed. Therefore, how to protect users’ data and privacy security becomes critical. In this paper, we design a provably secure authentication scheme for the smart home environment, which ensures that only legitimate users can use smart devices. We use the informal model to verify the security of the scheme and formally analyze the security and correctness of the scheme through the Real or Random model. Finally, through the comparison of security and performance analysis, it is proven that our scheme has higher security under similar performance.
MSC:
68M25
1. Introduction
The Internet of things (IoT) [,], cloud computing [,], big data [,], artificial intelligence [,], 5G and other technologies have promoted the construction and development of smart city. Smart city [] covers all fields of life, such as smart transportation [,], smart healthcare [], smart home, smart grid, etc., which are an indispensable part of smart city. As the foundation of smart city, smart home [,] is also the field closest to people’s daily life. It can provide an information exchange function for families. People can operate and monitor smart home devices through the Internet and know what happens at home any time, improving people’s comfort in life and optimizing people’s lifestyles. The smart home environment includes various smart devices, such as refrigerators, cameras, curtains, etc. People can control smart devices through smartphones or tablets to enjoy their services. For example, users can view the camera remotely to understand what is happening at home; the users can control the temperature of the air conditioner through the smart phone.
A typical smart home architecture shown in Figure 1 consists of four entities: registration authority (RA), gateway, smart device, and users. RA is a trusted entity that mainly authorizes the gateway as the home registration center. Gateway is a semi-trusted entity that helps users to communicate with smart home devices and is responsible for registration. Smart device refers to all kinds of smart home appliances in the family, such as smart refrigerators, smart air conditioners, etc., where they are semi-trusted entities, and are connected to the gateway by wireless networks to provide users with various services. Only family members can register with the gateway to become legal users. In this architecture, users need to connect the home devices via the gateway, and then operate the home devices through the smart home APP or voice assistant, such as adjusting the indoor temperature, switching lights, adjusting curtains, playing music, etc. Although the smart home has changed people’s lives, it faces many security threats and challenges. For example, since smart home devices are connected to the Internet, malicious attackers can access users’ private information by intercepting transmitted messages via open channels. Therefore, ensuring a secure smart-home IoT access control scheme is very important.
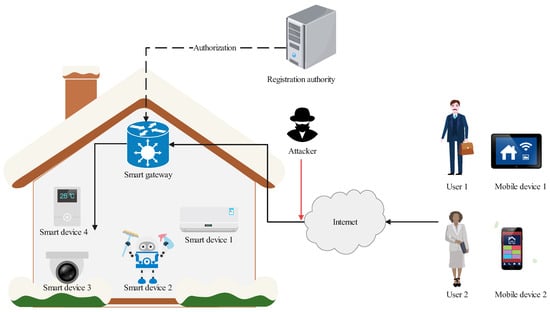
Figure 1.
The architecture of smart home.
At present, some scholars protect users’ privacy through differential privacy [], quick response (QR) code [] and other technologies, and many scholars have proposed many authentication and key agreement (AKA) schemes [,,,,,,,,] to protect the confidentiality and security of transmitted information, but most of their schemes have various security problems, such as unable to achieve mutual authentication, unable to resist offline password guessing (OPG) attacks, insider attacks, impersonation attacks, etc. In order to protect and improve the security of information, Intel has proposed a new set of CPU instruction extensions called software guard extensions (SGX) [,] technology. It is a kind of hardware that can create a trusted execution environment (TEE) to protect code and data, which even high-level system software cannot access. The system will allocate a pre-reserved physical memory area for SGX technology, which is called enclave page cache (EPC), and the code and data are stored in a secure environment, called enclave. The application protected by SGX is divided into two parts: trusted part and untrusted part. The trusted part will run in the safe memory and conduct integrity measurement when loaded into Enclave to ensure the integrity and security of data. The program access address is in the Enclave and the physical address is in the EPC. Because the two achieve access control through a unique mapping relationship, it can ensure that external programs cannot access the enclave memory. SGX provides automatic generation functions Ecall and Ocall. Some privacy data is stored in Enclave memory through Ecall function. After confidential calculation is completed in Enclave, the calculated results are returned through Ocall function.
To ensure the secure transmission of remote control data, we propose a scheme based on SGX, which can help our scheme effectively resist insider attacks. Our main contributions are as below:
- (1)
- We propose a new framework that features the ability to be registered within a family. Different from the past, we authorize the smart gateway as a home registration center by the registration authority (RA), so that users and smart devices can complete registration at home, which also facilitates the addition of future members and devices. This process can be completed only at home.
- (2)
- According to our survey, this is the first paper to apply SGX to smart home environments. Using SGX can be effective to prevent insider attacks.
- (3)
- We demonstrate the security of the proposed scheme using Real-Or-Random (RoR) model and informal security analysis. Furthermore, we compare the proposed scheme with other existing schemes, and the results reveal that our scheme offers higher security with similar performance.
2. Related Work
Numerous authentication and key agreement (AKA) schemes have been put forward to ensure the secure transmission of information in smart home systems. Some authentication schemes are listed in Table 1. Jeong et al. [] devised an authentication scheme based on home network environment. The author proved that their scheme is secure, but the user’s identity is immediately transmitted on the public channel, which does not realize user anonymity, and is unable to withstand tracking attacks. Vaidya et al. [] proposed a lightweight AKA scheme for secure remote access to the home network. However, Kim et al. [] demonstrated that their scheme is unable to provide user anonymity, mutual authentication, and cannot resist OPG attacks. Later, Kim et al. [] put forward an enhanced scheme based on Vaidya et al. []. Li et al. [] put forward a lightweight AKA scheme for the home energy management system. The wireless node and the control center completed authentication and established session key, but the user and the control center lacked the authentication process. Han et al. [] devised an authentication scheme to solve the problem of secure pairing of consumer electronic products in the smart home environment, but their scheme requires manufacturers to be online all the time is unrealistic. Santoso and Vun [] devised a secure two-factor AKA scheme, which uses elliptic curve cryptography (ECC) technology and is suitable for the smart home environment based on the IoT. Kumar et al. [] also proposed a lightweight scheme for this environment and realized the establishment of session key between gateway and smart device. However, other scholars have proved that anonymity and untraceability cannot be provided.
Ashibani and Mahmoud [] designed an identity-based AKA scheme. The scheme uses ECC and pairing operations with high computational complexity, which can realize secure mutual authentication between users and smart devices. However, they ignore that smart devices have limited computing power. In order to solve the above problems, Wazid et al. [] designed a lightweight remote user authentication scheme. The home gateway helps user and smart device complete authentication and establish session key, and proves that their scheme is secure. Unfortunately, Shuai et al. [] discovered that Wazid et al.’s [] scheme cannot withstand desynchronization attacks, and when the gateway is damaged, the user authentication table in the gateway is easy to be leaked. Users’ privacy is very easy to disclose. Shuai et al. [] devised an AKA scheme using ECC. However, Kuar et al. [] have demonstrated that their scheme cannot resist OPG, insider, and session key disclosure (SKD) attacks. Kaur et al. [] proposed a two factor authentication scheme, but Yu et al. [] stated that it cannot withstand simulated attacks and provide mutual authentication. Chifor et al. [] devised an authentication scheme that can provide fast online identity authentication and realize password free authentication between users and smart devices. Ghosh et al. [] designed a secure multi-level authentication scheme, which can resist many common attacks. Dey and Hossian [] designed an authentication scheme using the public key cryptosystem and asserted that their scheme was resistant to various common attacks. However, Gaba et al. [] found that their scheme is unable to resist smart device stolen (SDS) attacks, and could not guarantee anonymity and confidentiality. Then, Gaba et al. [] designed an ECC-based authentication scheme to ensure the positioning security of household devices. Naoui et al. [] designed an authentication framework based on the user’s configuration file, request time, location and other context information. Poh et al. [] proposed a scheme to protect data privacy. However, Irshad et al. [] proved that their scheme could not achieve the confidentiality of user authentication parameters. They propose a new two-factor AKA scheme that ensures perfect froward secrecy (PFS) by using a circular fuzzy extractor. Banerjee et al. [] designed a lightweight anonymous AKA scheme suitable for this environment. Unfortunately, AL-Turjman and Deebak [] discovered that their scheme could not provide identity protection and traceability. Zou et al. [] devised a more secure scheme. Yu et al. [] devised a three factor AKA scheme, but Alzahrani et al. [] found that Yu et al.’s scheme [] cannot provide mutual authentication. Piraytesh et al. [] proposed a hyperelliptic curve cryptosystem-based AKA scheme in smart home, which they claim ensures good performance. Guo et al. [] designed an AKA scheme based on smart home, and introduced fog nodes into the scheme to process the data of smart devices faster.
At present, some scholars have applied SGX to other environments to design schemes. Sun et al. [] used SGX to design schemes to better protect dynamic identity authentication. Liu et al. [] devised an AKA scheme that applies SGX to wireless sensor networks (WSNs). The scheme also uses dynamic authentication certificate (DAC) to ensure more effective secure communication.

Table 1.
The summary of authentication schemes.
Table 1.
The summary of authentication schemes.
| Schemes | Advantages | Shortcomings |
|---|---|---|
| Shuai et al. [] | (1) Provides mutual authentication (2) Can resist impersonation attacks | (1) Cannot resist insider attacks (2) Cannot resist SKD attacks (3) Cannot resist OPG attacks |
| Yu et al. [] | (1) Can provide user anonymity (2) Can resist PFS attacks | (1) Cannot provide mutual authentication |
| Zou et al. [] | (1) Can resist SDS attacks (2) Provides mutual authentication | − |
| Kaur et al. [] | (1) Can resist OPG attacks (2) Provides user anonymity | (1) Cannot resist impersonation attacks (2) Cannot provide mutual authentication |
| Vaidya et al. [] | (1) Can resist SKD attacks (2) Provides PFS | (1) Cannot provide user anonymity (2) Cannot provide mutual authentication (3) Cannot resist OPG attacks |
| Santoso and Vun [] | (1) Provides user anonymity (2) Provides PFS | − |
| Wazid et al. [] | (1) Can resist insider attacks (2) Provides PFS (3) Can resist OPG attacks | (1) Cannot resist desynchronization attacks |
| Banerjee et al. [] | (1) Provides PFS (2) Can resist OPG attacks | (1) Cannot provide user anonymity and untraceability |
3. The Proposed Scheme
In this section, we introduce the proposed scheme in detail, the network model of this scheme is shown in Figure 2. The proposed scheme includes three phases: authorization gateway, registration, and access and control. The notations used in the paper are listed in Abbreviations.
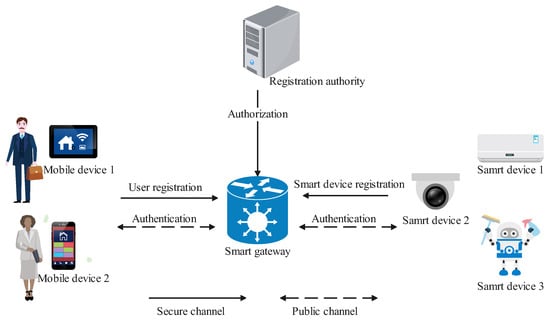
Figure 2.
Network model of smart home.
3.1. Authorization Gateway Phase
selects , computes the temporary identity of , and transmits to ; stores in memory. Then, selects , x. Then, computes , stores in SGX, and publish .
3.2. Registration Phases
At this phase, users and smart devices register with the gateway as a legal entity, and all registration information is transmitted on the secure channel.
3.2.1. User Registration Phase
- (1)
- chooses identity , password and biometrics , and then transmits the to the ;
- (2)
- selects random number , computes , and sends to ;
- (3)
- calculates , , and stores in their own mobile device. Table 2 shows the detailed process.
 Table 2. User registration phase.
Table 2. User registration phase.
3.2.2. Smart Device Registration Phase
- (1)
- chooses its own identity and transmits it to the ;
- (2)
- selects random number , computes , stores in memory, and stores . Finally, it sends to ;
- (3)
- stores in its own memory.
3.3. Access and Control Phase
The assists the and the in completing identity authentication and establishing a session key. Messages between devices are also transmitted through public channels. The detailed process is shown in Table 3.

Table 3.
Login and authentication phase.
- (1)
- enters , , , calculates , , and verifies . If the verification passes, this shows that the is legitimate; Otherwise, the session terminates. selects , computes , , , , . At last, transmits message to .
- (2)
- When the obtains message , it validates the timestamp’s correctness. Next, sends to the SGX interface. SGX match and x according to . Then, computes , , , , and verifies . If the verification passes, selects , computes , , and sends message to the .
- (3)
- Upon receiving the , verifies the timestamp , then computes , , and verifies . If the verification is successful, it selects , and computes , , , , and transmits the to .
- (4)
- When receives the , it verifies the . Next, computes , and verifies . If the verification is successful, it proves that is a legitimate device. Then it selects the timestamp , and then send to the .
- (5)
- After receiving the message , computes , , , and verifies . If the two values are the same, will use the to transmit information with .
4. Security Analysis
4.1. Formal Analysis
We use RoR model to formally analyze the scheme to prove the security of the proposed scheme. The steps of proof will be described in detail below.
RoR Model
RoR model [,] simulates the probability of an attacker cracking the scheme in polynomial time through different rounds of games and judges the security of the proposed scheme by whether the attacker can calculate the session key.
Our proposed agreement has three participants: , , and . We define , , and to represent the user instance, the gateway instance, and the smart device instance, respectively. Based on the ROR model, needs to follow the following capabilities in each game.
- (1)
- : This query is a passive attack and can enable to eavesdrop on messages sent by entities, where O = {, ,}.
- (2)
- : can send the message send it to O and obtain the response from O.
- (3)
- : This query means that can obtain the hash of a certain string.
- (4)
- : executing this query can obtain data in the mobile device.
- (5)
- : flips a coin c to guess the real session key. In the case of , the can obtain the session key, otherwise the attacker obtains a random string.
Theorem 1.
In RoR model, can break the proposed scheme in polynomial time is . Here, indicates the range space of the hash function; indicates the advantage of cracking elliptic curve Diffie-Hellman problem (ECDHP); refers to the query; l indicates the bit length of biological information; refers to the space size of the password dictionary.
Proof.
We defined 4 games - to simulate ’s attack process. During the proof process, is defined as the probability that can successfully compute the session key in each game, indicates that the can break the advantage of scheme . The following is the specific process of the game.
: In , needs to select a bit c to start the game simulating the real attack. So we have
: adds the query to . At , intercepts the , , and . When this query ends, will execute query to compute the session key . and are confidential to . Therefore, there is no difference between and .
: adds and operations to the game. wants to tamper with the message stolen on the public channel, but the authentication values are all based on hash functions, and the authentication values are composed of random numbers and dot product. Since random numbers are different, hash functions do not collide. In addition, since the cannot obtain the x of and cannot solve the ECDHP, the cannot calculate . Therefore, based on and birthday paradox, we can obtain
: adds operation, which can be used by to obtain user information . In addition, selects a low entropy password based on the password dictionary to guess the correct password of , and the probability that would correctly predict the biological key is . Suppose the system allows the to enter a limited number of wrong passwords, we have
Finally, guesses bit b through the operation to win the game. So we can obtain
According to , we have
Therefore, we can obtain
□
4.2. Informal Analysis
4.2.1. Impersonation Attack
Suppose that attempts to impersonate a legitimate user and communicate with other entities communicate to establish a session key. Because is only responsible for registration and does not store any entity information, he cannot impersonate users by obtaining information. If obtains the information stored in the gateway and intercepts the information on the public channel to compute , but because it cannot obtain , he cannot compute , and , so he cannot successfully compute , and he cannot be authenticated through the gateway. Therefore, cannot impersonate a legitimate user. In the same way, tries to become a legitimate smart device, but because he cannot obtain the , he cannot compute the , so he cannot successfully compute , and he cannot be authenticated through the gateway. So our scheme is immune to impersonate attack.
4.2.2. Session Key Disclosure (SKD) Attack
Suppose intercepts the messages , and attempts to calculate , but the are private and cannot obtain these values. Therefore, cannot compute , , and through values of . Obviously, he cannot calculate . Thus, our scheme is immune to SKD attack.
4.2.3. Smart Device Stolen (SDS) Attack
Suppose obtains the stored in the smart home device, intercepts and , and tries to compute , , because the smart device only stores the pseudo identity of the device, the attacker cannot obtain , so he cannot compute , so he cannot calculate the . Thus, our scheme can resist the SDS attack.
4.2.4. Privacy and Anonymity
can identify the real identity of and according to the intercepted public channel information. In our proposed scheme, we use hash function and random number to hide the real identity of and , thus providing anonymity for them. In each session, because the random number is different, even if can intercept the pseudo identity of and , he cannot identify the real identity of their real identities. Therefore, our scheme can protect the entity’s privacy from being disclosed.
4.2.5. Mutual Authentication
The gateway authenticates user and smart device using and , respectively. Although can eavesdrop on these two values, cannot correctly compute and change the verification value because he cannot obtain , and cannot compute , . Similarly, although the verification value is transmitted on the public channel, cannot obtain the . He cannot correctly calculate and change . As long as a changes any of the verification values, it will be detected immediately and the session will be terminated. So our scheme can realize mutual authentication.
5. Security and Performance Comparison
We use the proposed scheme to compare the existing schemes [,,] in terms of security, computing cost and communication cost, and the detailed introduction and comparison results are described below.
5.1. Security Comparison
The proposed scheme is compared with the three schemes regarding security, and the comparison results are listed in Table 4. Shuai et al.’s scheme [] is unable to withstand OPG, insider, and SKD attacks. The scheme of Yu et al. [] cannot realize mutual authentication; Kaur et al. [] cannot withstand impersonation attack and violated mutual authentication. The proposed scheme and Zou et al.’s scheme [] can resist common attack.

Table 4.
Comparisons of security.
5.2. Computation Costs Comparison
We use an IQOO9 mobile phone to emulate and and a Lenovo desktop computer to emulate the . The mobile phone’s processor is a snapdragon 8-core processor with 12G of running memory and the Lenovo desktop computer’s CPU is the Intel(R) Core(TM)i5-8500 CPU@ 3.00 GHz with 16G of running memory. The software used on the computer is IntelliJ idea 2020.3, and the program is written using JAVA and cryptographic library JPBC-2.0.0 []. In Table 5, we select four main operations: hash function , point scalar multiplication , symmetric decryption , and symmetric encryption . We ran various operations 100 times on the mobile phone and computer to take the average running time. In Table 6, we based on the results in Table 5 to show the comparison of computation costs between our and recently proposed schemes [,,,]. For example, our scheme requires for . The cost is ms.

Table 5.
Computation costs of complex operations.

Table 6.
Computation costs.
In Table 6, and Figure 3, the costs of [,,] for are less than our scheme. Our scheme requires an additional ms than [] and ms than [,]. In fact, the two values are reasonable in practice. More importantly, the three schemes have some security weaknesses mentioned in Table 4. Overall, our scheme provides both security and efficiency for .
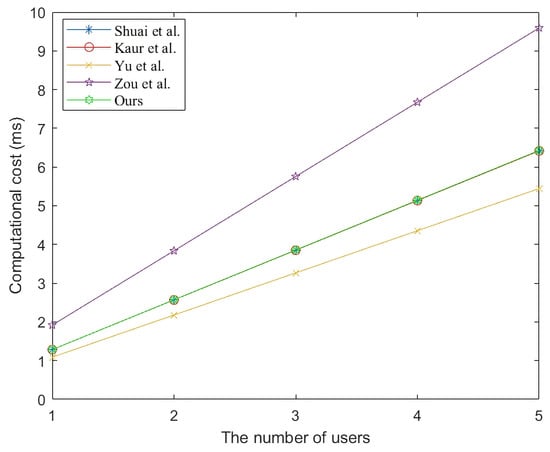
Figure 3.
The computation cost of users [,,,].
In Table 6, and Figure 4, the costs of [,,] for are less than our scheme. Our scheme requires an additional ms than [,] and ms than []. In fact, the two values are reasonable in practice. More importantly, the three schemes have some security weaknesses mentioned in Table 4. Overall, our scheme provides both security and efficiency for .
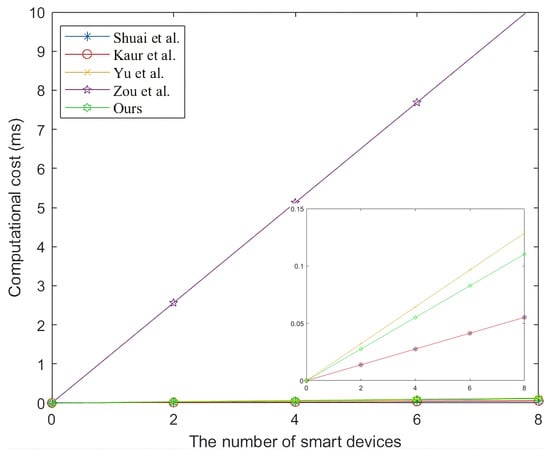
Figure 4.
The computation cost of smart devices [,,,].
5.3. Communication Costs Comparison
In Table 7, we show the communication costs between our and recently proposed schemes [,,,]. Note that the lengths of symmetric encryption and decryption , hash functions , timestamp T, integer , identify and ECC are defined by 256 bits, 256 bits, 128 bits, 160 bits, 32 bits, and 320 bits, respectively. Here, the total communication costs of our scheme are computed by bits. The communication costs of Shuai et al.’s scheme [] requires bits, Kaur et al.’s scheme [] requires bits, Yu et al.’s scheme [] requires bits, Zou et al.’s scheme [] requires bits. Finally, the results in Table 7 are depicted in Figure 5. It can be seen that Zou et al.’s scheme [] has the highest communication cost, Shuai et al.’s scheme [] has the lowest communication cost, and our scheme is lower than Zou et al.’s scheme [], slightly higher than Kaur et al.’s scheme [].

Table 7.
Communication costs.
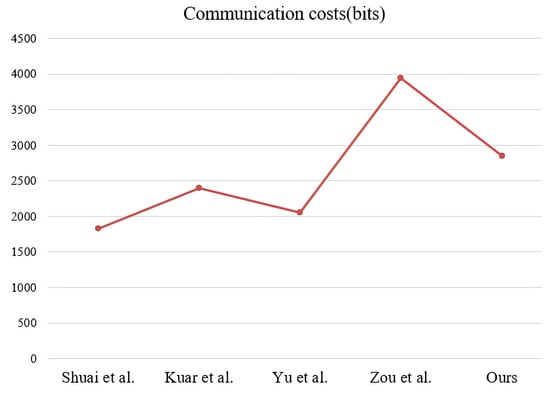
Figure 5.
The results of communication costs [,,,].
6. Conclusions
As the foundation of smart cities, smart homes are closer to people’s lives, so ensuring the security of data transfers between entities is critical. In this paper, we propose an AKA scheme suitable for smart home environments and use the combination of SGX and gateway to prevent insider attacks effectively. Moreover, we also prove the proposed scheme’s security through informal security analysis and the RoR model. Finally, we compare the proposed scheme with existing schemes regarding security, computation, and communication costs. Based on the comparison results, our scheme performs better and is more suitable for this environment. In the future, smart home authentication schemes should incorporate multiple approaches such as multi-factor authentication and biometrics. Additionally, users should set strong passwords for smart home devices and limit the number of people who can access smart devices. We will continue to improve the smart home authentication scheme to meet the growing security needs.
Author Contributions
Conceptualization, T.-Y.W.; methodology, T.-Y.W. and Q.M.; software, Y.-C.C.; formal analysis, S.K.; investigation, C.-M.C.; writing—original draft preparation, T.-Y.W., Q.M., Y.-C.C., S.K. and C.-M.C. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The data is included in the article.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| IoT | Internet of Things |
| SGX | Software guard extensions |
| TEE | Trusted execution environment |
| EPC | Enclave page cache |
| ROR | Real-or-random |
| AKA | Authentication and key agreement |
| OPG | Offline password guessing |
| SKD | Session key disclosure |
| PFS | Perfect froward secrecy |
| SDS | Smart device stolen |
| Notations | Meanings |
| The i-th user | |
| Identity of | |
| ’s password | |
| Pseudo identity of | |
| The registration authority | |
| x | RA’s secret key |
| The gateway | |
| The k-th user | |
| ’s pseudo identity | |
| The j-th smart device | |
| ’s identity | |
| ’s pseudo identity | |
| , | The session key |
References
- Wu, T.Y.; Guo, X.; Chen, Y.C.; Kumari, S.; Chen, C.M. SGXAP: SGX-Based Authentication Protocol in IoV-Enabled Fog Computing. Symmetry 2022, 14, 1393. [Google Scholar] [CrossRef]
- Mei, Q.; Yang, M.; Chen, J.; Wang, L.; Xiong, H. Expressive Data Sharing and Self-Controlled Fine-Grained Data Deletion in Cloud-Assisted IoT. IEEE Trans. Dependable Secur. Comput. 2022; early access. [Google Scholar] [CrossRef]
- Zhang, J.; Li, M.; Chen, Z.; Lin, B. Computation offloading for object-oriented applications in a UAV-based edge-cloud environment. J. Supercomput. 2022, 78, 10829–10853. [Google Scholar] [CrossRef]
- Wu, T.Y.; Meng, Q.; Kumari, S.; Zhang, P. Rotating behind Security: A Lightweight Authentication Protocol Based on IoT-Enabled Cloud Computing Environments. Sensors 2022, 22, 3858. [Google Scholar] [CrossRef] [PubMed]
- Wang, S.; Chen, Z.; Zhu, W.; Wang, F.Y. Deep random walk of unitary invariance for large-scale data representation. Inf. Sci. 2021, 554, 1–14. [Google Scholar] [CrossRef]
- Cheng, H.; Shi, Y.; Wu, L.; Guo, Y.; Xiong, N. An intelligent scheme for big data recovery in Internet of Things based on multi-attribute assistance and extremely randomized trees. Inf. Sci. 2021, 557, 66–83. [Google Scholar] [CrossRef]
- Pan, J.S.; Lv, J.X.; Yan, L.J.; Weng, S.W.; Chu, S.C.; Xue, J.K. Golden eagle optimizer with double learning strategies for 3D path planning of UAV in power inspection. Math. Comput. Simul. 2022, 193, 509–532. [Google Scholar] [CrossRef]
- Zou, W.; Guo, L.; Huang, P.; Lin, G.; Mei, H. Linear time algorithm for computing min-max movement of sink-based mobile sensors for line barrier coverage. Concurr. Comput. Pract. Exp. 2022, 34, e6175. [Google Scholar] [CrossRef]
- Hundera, N.W.; Jin, C.; Geressu, D.M.; Aftab, M.U.; Olanrewaju, O.A.; Xiong, H. Proxy-based public-key cryptosystem for secure and efficient IoT-based cloud data sharing in the smart city. Multimed. Tools Appl. 2022, 81, 29673–29697. [Google Scholar] [CrossRef]
- Chaudhry, S.A. Combating identity de-synchronization: An improved lightweight symmetric key based authentication scheme for IoV. J. Netw. Intell. 2021, 6, 12. [Google Scholar]
- Wu, T.; Guo, X.; Chen, Y.; Kumari, S.; Chen, C. Amassing the security: An enhanced authentication protocol for drone communications over 5G networks. Drones 2021, 6, 10. [Google Scholar] [CrossRef]
- Wu, T.Y.; Meng, Q.; Yang, L.; Kumari, S.; Nia, M.P. Amassing the Security: An Enhanced Authentication and Key Agreement Protocol for Remote Surgery in Healthcare Environment. Comput. Model. Eng. Sci. 2023, 134, 317–341. [Google Scholar] [CrossRef]
- Shuai, M.; Yu, N.; Wang, H.; Xiong, L. Anonymous authentication scheme for smart home environment with provable security. Comput. Secur. 2019, 86, 132–146. [Google Scholar] [CrossRef]
- Kong, H.; Lu, L.; Yu, J.; Chen, Y.; Tang, F. Continuous authentication through finger gesture interaction for smart homes using WiFi. IEEE Trans. Mob. Comput. 2020, 20, 3148–3162. [Google Scholar] [CrossRef]
- Zhao, J.; Chen, Y.; Zhang, W. Differential privacy preservation in deep learning: Challenges, opportunities and solutions. IEEE Access 2019, 7, 48901–48911. [Google Scholar] [CrossRef]
- Pan, J.S.; Sun, X.X.; Chu, S.C.; Abraham, A.; Yan, B. Digital watermarking with improved SMS applied for QR code. Eng. Appl. Artif. Intell. 2021, 97, 104049. [Google Scholar] [CrossRef]
- Yu, S.; Jho, N.; Park, Y. Lightweight three-factor-based privacy-preserving authentication scheme for iot-enabled smart homes. IEEE Access 2021, 9, 126186–126197. [Google Scholar] [CrossRef]
- Zou, S.; Cao, Q.; Wang, C.; Huang, Z.; Xu, G. A robust two-factor user authentication scheme-based ECC for smart home in IoT. IEEE Syst. J. 2021, 16, 4938–4949. [Google Scholar] [CrossRef]
- Kaur, D.; Kumar, D. Cryptanalysis and improvement of a two-factor user authentication scheme for smart home. J. Inf. Secur. Appl. 2021, 58, 102787. [Google Scholar] [CrossRef]
- Ge, M.; Kumari, S.; Chen, C.M. AuthPFS: A Method to Verify Perfect Forward Secrecy in Authentication Protocols. J. Netw. Intell. 2022, 7, 734–750. [Google Scholar]
- Pirayesh, J.; Giaretta, A.; Conti, M.; Keshavarzi, P. A PLS-HECC-based device authentication and key agreement scheme for smart home networks. Comput. Netw. 2022, 216, 109077. [Google Scholar] [CrossRef]
- Guo, Y.; Zhang, Z.; Guo, Y. SecFHome: Secure remote authentication in fog-enabled smart home environment. Comput. Netw. 2022, 207, 108818. [Google Scholar] [CrossRef]
- Nyangaresi, V.O. Lightweight anonymous authentication protocol for resource-constrained smart home devices based on elliptic curve cryptography. J. Syst. Archit. 2022, 133, 102763. [Google Scholar] [CrossRef]
- Yakubu, B.M.; Khan, M.I.; Khan, A.; Jabeen, F.; Jeon, G. Blockchain-based DDoS attack mitigation protocol for device-to-device interaction in smart home. Digit. Commun. Netw. 2023; in press. [Google Scholar] [CrossRef]
- Sun, H.; Xiao, S. DNA-X: Dynamic network authentication using SGX. In Proceedings of the 2nd International Conference on Cryptography, Security and Privacy, Guiyang, China, 16–19 March 2018; pp. 110–115. [Google Scholar] [CrossRef]
- Liu, X.; Guo, Z.; Ma, J.; Song, Y. A secure authentication scheme for wireless sensor networks based on DAC and Intel SGX. IEEE Internet Things J. 2021, 9, 3533–3547. [Google Scholar] [CrossRef]
- Jeong, J.; Chung, M.Y.; Choo, H. Integrated OTP-based user authentication scheme using smart cards in home networks. In Proceedings of the 41st Annual Hawaii International Conference on System Sciences (HICSS 2008), Waikoloa, HI, USA, 7–10 January 2008; p. 294. [Google Scholar] [CrossRef]
- Vaidya, B.; Park, J.H.; Yeo, S.S.; Rodrigues, J.J. Robust one-time password authentication scheme using smart card for home network environment. Comput. Commun. 2011, 34, 326–336. [Google Scholar] [CrossRef]
- Kim, H.J.; Kim, H.S. AUTH HOTP-HOTP based authentication scheme over home network environment. In Proceedings of the International Conference on Computational Science and Its Applications, Santander, Spain, 20–23 June 2011; Springer: Berlin/Heidelberg, Germany, 2011; Volume 6784, pp. 622–637. [Google Scholar]
- Li, Y. Design of a key establishment protocol for smart home energy management system. In Proceedings of the 2013 Fifth International Conference on Computational Intelligence, Communication Systems and Networks, Madrid, Spain, 5–7 June 2013; pp. 88–93. [Google Scholar] [CrossRef]
- Han, K.; Kim, J.; Shon, T.; Ko, D. A novel secure key paring protocol for RF4CE ubiquitous smart home systems. Pers. Ubiquitous Comput. 2013, 17, 945–949. [Google Scholar] [CrossRef]
- Santoso, F.K.; Vun, N.C. Securing IoT for smart home system. In Proceedings of the 2015 International Symposium on Consumer Electronics (ISCE), Madrid, Spain, 24–26 June 2015; pp. 1–2. [Google Scholar] [CrossRef]
- Kumar, P.; Gurtov, A.; Iinatti, J.; Ylianttila, M.; Sain, M. Lightweight and secure session-key establishment scheme in smart home environments. IEEE Sens. J. 2015, 16, 254–264. [Google Scholar] [CrossRef]
- Ashibani, Y.; Mahmoud, Q.H. An efficient and secure scheme for smart home communication using identity-based signcryption. In Proceedings of the 2017 IEEE 36th International Performance Computing and Communications Conference (IPCCC), San Diego, CA, USA, 10–12 December 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Susilo, W. Secure remote user authenticated key establishment protocol for smart home environment. IEEE Trans. Dependable Secur. Comput. 2017, 17, 391–406. [Google Scholar] [CrossRef]
- Chifor, B.C.; Bica, I.; Patriciu, V.V.; Pop, F. A security authorization scheme for smart home Internet of Things devices. Future Gener. Comput. Syst. 2018, 86, 740–749. [Google Scholar] [CrossRef]
- Ghosh, N.; Chandra, S.; Sachidananda, V.; Elovici, Y. SoftAuthZ: A context-aware, behavior-based authorization framework for home IoT. IEEE Internet Things J. 2019, 6, 10773–10785. [Google Scholar] [CrossRef]
- Dey, S.; Hossain, A. Session-key establishment and authentication in a smart home network using public key cryptography. IEEE Sens. Lett. 2019, 3, 1–4. [Google Scholar] [CrossRef]
- Gaba, G.S.; Kumar, G.; Monga, H.; Kim, T.H.; Kumar, P. Robust and lightweight mutual authentication scheme in distributed smart environments. IEEE Access 2020, 8, 69722–69733. [Google Scholar] [CrossRef]
- Naoui, S.; Elhdhili, M.E.; Saidane, L.A. Lightweight and secure password based smart home authentication protocol: LSP-SHAP. J. Netw. Syst. Manag. 2019, 27, 1020–1042. [Google Scholar] [CrossRef]
- Poh, G.S.; Gope, P.; Ning, J. PrivHome: Privacy-preserving authenticated communication in smart home environment. IEEE Trans. Dependable Secur. Comput. 2019, 18, 1095–1107. [Google Scholar] [CrossRef]
- Irshad, A.; Usman, M.; Chaudhry, S.A.; Bashir, A.K.; Jolfaei, A.; Srivastava, G. Fuzzy-in-the-loop-driven low-cost and secure biometric user access to server. IEEE Trans. Reliab. 2020, 70, 1014–1025. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Park, Y. An efficient, anonymous and robust authentication scheme for smart home environments. Sensors 2020, 20, 1215. [Google Scholar] [CrossRef] [PubMed]
- Fadi, A.T.; Deebak, B.D. Seamless authentication: For IoT-big data technologies in smart industrial application systems. IEEE Trans. Ind. Inform. 2020, 17, 2919–2927. [Google Scholar]
- Alzahrani, B.A.; Barnawi, A.; Albarakati, A.; Irshad, A.; Khan, M.A.; Chaudhry, S.A. SKIA-SH: A Symmetric Key-Based Improved Lightweight Authentication Scheme for Smart Homes. Wirel. Commun. Mob. Comput. 2022, 2022, 8669941. [Google Scholar] [CrossRef]
- Abdalla, M.; Fouque, P.A.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In Proceedings of the International Workshop on Public Key Cryptography, Les Diablerets, Switzerland, 23–26 January 2005; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3386, pp. 65–84. [Google Scholar]
- Wu, T.Y.; Meng, Q.; Yang, L.; Guo, X.; Kumari, S. A provably secure lightweight authentication protocol in mobile edge computing environments. J. Supercomput. 2022, 78, 13893–13914. [Google Scholar] [CrossRef]
- Xiang, A.; Zheng, J. A situation-aware scheme for efficient device authentication in smart grid-enabled home area networks. Electronics 2020, 9, 989. [Google Scholar] [CrossRef]
- De Caro, A.; Iovino, V. jPBC: Java pairing based cryptography. In Proceedings of the 2011 IEEE Symposium on Computers and Communications (ISCC), Kerkyra, Greece, 28 June–1 July 2011; pp. 850–855. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).