Abstract
Critical infrastructure is essential for the stability and development of modern society, and a combination of complex network theory and game theory has become a new research direction in the field of infrastructure protection. However, existing studies do not consider the fuzziness and subjective factors of human judgment, leading to challenges when analyzing strategic interactions between decision makers. This paper employs interval-valued intuitionistic fuzzy numbers (IVIFN) to depict the uncertain payoffs in a Stackelberg game of infrastructure networks and then proposes an algorithm to solve it. First, we construct IVIFN payoffs by considering the different complex network metrics and subjective preferences of decision makers. Next, we propose a lexicographic algorithm to solve this game based on the concept of a strong Stackelberg equilibrium (SSE). Finally, we conduct experiments on target scale-free networks. Our results illustrate that in an SSE, for the defender in a weak position, it is better to defend nodes with high degrees. The experiments also indicate that taking fuzziness into account leads to higher SSE payoffs for the defender. Our work aims to solve a Stackelberg game with IVIFN payoffs and apply it to enhance the protection of infrastructure networks, thereby improving their overall security.
Keywords:
infrastructure networks; Stackelberg game; interval-valued intuitionistic fuzzy theory; strong Stackelberg equilibrium MSC:
91A86
1. Introduction
Critical infrastructures, such as power grids, transportation systems, communication networks, and water supply networks, play vital roles in modern society. On 7 October 2023, Hamas launched an attack on Israel, utilizing drones to target and destroy communications equipment at surveillance posts along the borders of the Gaza Strip. In response, Israel launched thousands of missiles to destroy Gaza’s cables, cell towers, and infrastructure needed to keep people online. Therefore, the protection of critical infrastructure networks has become increasingly challenging and deserves further study. Probabilistic risk assessment (PRA) is a conventional and commonly used method for the analysis of infrastructure investment and protection [1,2]. However, such analysis is resource-intensive and quickly becomes complex, even for small systems. Complex network theory has emerged as a novel approach to overcome the limitations of PRA in dealing with the protection of infrastructure systems. Lee and Tien [3] investigated the impact of variations in three parameters of network vulnerability, namely component vulnerabilities, service interdependency redundancies, and system link configurations. Liu et al. [4] investigated interdependent critical infrastructure networks and designed a cascading failure model, examining cascading failure in both syncretic and single networks. Herrera et al. [5] presented a multilayer complex network framework taking into account the heterogeneity of the redundant infrastructure for realistic network modeling. Recent studies have been conducted on complex networks such as network disintegration [6,7,8] and protection [9,10,11]. These studies have provided effective ways to obtain insights into network attacks and to identify the systems and components that must be protected.
To deal with deliberate attacks, the combination of network science and game theory has garnered considerable research attention. Li et al. [12] applied a simultaneous game and defined payoffs according to the topology of the infrastructure system. They then considered two typical strategies under a cost constraint model [13]. Fu et al. [14] proposed a static network attack and defense game model to examine the impact of cascading failures. Sun et al. [15] established a network attack and defense game model based on betweenness virtual flow. Although a simultaneous game is an important game model, Stackelberg games are more commonly used to model attack and defense scenarios in security domains, as they align better with real-life situations [16]. Li et al. [17] applied a Stackelberg game model to complex networks and evaluated the effects of cost-sensitive parameters. Zeng et al. [18,19] proposed a false network construction method and applied Stackelberg and Bayesian Stackelberg game models for the defense of critical infrastructure networks. Fu et al. [20] established a Stackelberg game model based on camouflage strategies and proposed an evolutionary rule to optimize these strategies. Qi et al. [21,22] proposed a link-hiding rule and analyzed its impact in terms of optimization within the context of dynamic attack and defense games played out on complex networks. Liu et al. [23] established an attack-defensive game model based on a Stackelberg game under asymmetric information, obtaining a defensive resource allocation strategy to optimize the network robustness. Liu et al. [24] established a Stackelberg game model based on a 5G network graph and proposed compact particle swarm optimization based on the location-scale distribution to solve the Nash equilibrium.
However, the aforementioned research fails to consider the problem in a fuzzy environment. The topology of real-world infrastructure networks exhibits numerous features; even if the same nodes are removed after an attack, the effects of the attack can vary when measured using different network metrics [25,26]. Hence, the assessment of an attack’s impact (i.e., the payoffs for both the attacker and the defender) naturally contains fuzziness and uncertainty. In addition, subjective factors and human judgment are challenges in the analysis of the strategic interactions between decision makers. Fuzzy set theory, proposed by Zadeh [27] in 1965, provides a preliminary tool to handle these problems. Atanassov extended the notion of fuzzy sets to intuitionistic fuzzy sets by appending a degree of nonmembership [28,29]. Unfortunately, for attack and defense games in infrastructure networks, it may be difficult to identify exact values for the membership and nonmembership degrees of impact after a confrontation. Thus, the payoffs of the game seem to be suitably expressed with interval-valued intuitionistic fuzzy numbers (IVIFN) [30]. The IVIFN is characterized by introducing the degrees of membership and nonmembership as whole intervals instead of crisp values. As is known, IVIFN has been extensively applied in the field of decision making [31,32,33,34,35,36,37], and the research in this field has provided several useful methodologies. Many studies have focused on solving the simultaneous game with IVIFN payoffs. Li [38] proved that matrix games with interval-valued intuitionistic fuzzy set (IVIFS) payoffs have solutions, and he developed a mathematical programming methodology by constructing a pair of auxiliary linear/nonlinear programming models to solve these games. Xia [39] proposed several mathematical programming models to find solutions of IVIFN matrix games based on Archimedean t-conorm and t-norm and transformed them into a pair of primal–dual linear programming models. Kumar et al. [40] developed a solution for a two-person zero-sum game with IVIFN payoffs by introducing a new order function to defuzzify the IVIFNs. Naqvi et al. [41] extended the work of Li [38] by proposing a solution for a matrix game with payoffs characterized by linguistic IVIFSs.
To the best of our knowledge, no existing literature has delved into the modeling of fuzzy payoffs for the game in infrastructure networks. Moreover, to the best of our knowledge, no existing research has studied a method to solve Stackelberg games in an interval-valued intuitionistic fuzzy (IVIF) environment. These limitations highlight the need for further research in the area of infrastructure protection. In this paper, we evaluate attack and defense performance using various complex network metrics and introduce a method of constructing them as IVIFNs. Furthermore, we establish a Stackelberg game with IVIFN payoffs where the defender (leader) commits to a strategy before the attacker (follower) selects its own strategy. Inspired by the work of Conitzer et al. [42], we propose a lexicographic method to solve this game. In this method, we use score and accuracy functions to consider the risk attitude of the decision maker by defining two comparison indices arranged in a hierarchical fashion [34]. We then conduct experiments under different available resources and risk attitudes of both the attacker and the defender. We analyze the results of the experiment using a scale-free network as the target. Overall, the model and solution method proposed in this paper enable the incorporation of more payoff information, accounting for factors such as fuzziness, uncertainty, and decision makers’ subjective preferences in the context of protecting infrastructure networks. This extension enhances the applicability of the game model to real-world scenarios and offers a more rational basis for strategy selection. Furthermore, this research provides insights that can inform defenders in the protection of infrastructure networks.
2. Preliminaries
In this section, we briefly review the basic concepts of IVIFSs and IVIFNs and the different ranking methods of the latter. We also review a classical Stackelberg game (one attacker and one defender) and its SSE.
2.1. Regarding the IVIF Theory
Definition 1.
An IVIFS in the universe of discourse Z is defined by [30] , where and , with the condition . Here, the intervals , and , respectively, represent the membership degree and nonmembership degree of the element to . For each element x, the hesitancy degree of to is defined as .
In [31], Xu called the pair an IVIFN, where , , and .
Definition 2.
Let and be any two IVIFNs; then [30],
- (1)
- iff and ;
- (2)
- iff and ;
- (3)
- ;
- (4)
- ;
- (5)
- .
Definition 3.
Xu’s method of ranking IVIFNs is shown as follows [31]. For an IVIFN , the score function and accuracy function of the IVIFN can be computed as
where and .
Let and be any two IVIFNs; then,
- (1)
- If , then ;
- (2)
- If , then ;
- (3)
- If , then
- (i)
- If , then ;
- (ii)
- If , then ;
- (iii)
- If , then .
However, Xu’s method of ranking IVIFNs has the shortcoming that it cannot distinguish IVIFNs and if and .
Definition 4.
Wang and Wan’s method of ranking IVIFNs is shown as follows [34]. For an IVIFN , the score function and accuracy function of the IVIFN can be computed as
where , , and is the risk attitude parameter of the decision maker.
Let and be any two IVIFNs; then,
- (1)
- If , then ;
- (2)
- If , then ;
- (3)
- If , then
- (i)
- If , then ;
- (ii)
- If , then ;
- (iii)
- If , then .
In this ranking method, the decision maker is considered risk-seeking when and risk-averse when . If , the decision maker is neutral to risk, and Equations (3) and (4) are reduced to Equations (1) and (2). Therefore, Wang and Wan’s ranking method is a general extension of Xu’s ranking method.
2.2. The Stackelberg Game
In a normal-form Stackelberg game, the defender is the leader and the attacker is the follower. and denote the strategy sets of the defender and the attacker. The payoff functions of the attacker and the defender can be represented as and , respectively. The payoffs under different strategy profiles are real numbers. In this game, the attacker obtains the defender’s mixed strategy and chooses the best response strategy. Correspondingly, the defender has the ability to anticipate the attacker’s preferred strategy before committing to a mixed strategy. The Stackelberg game model is shown in Figure 1.
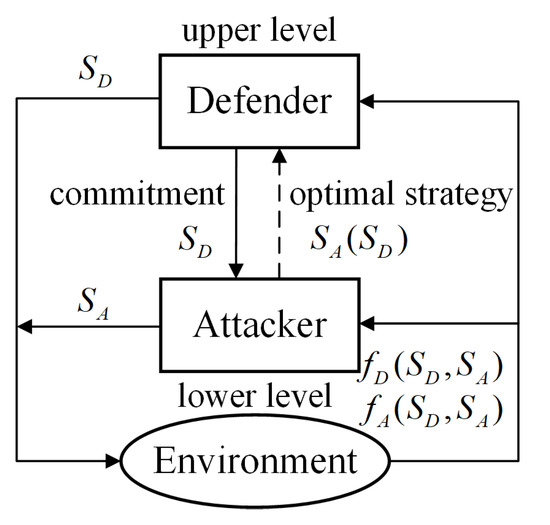
Figure 1.
The framework of the Stackelberg game.
2.3. The Strong Stackelberg Equilibrium
A Stackelberg equilibrium, which is the conceptual solution of Stackelberg games, captures the optimal outcome of the defender’s strategy, since the attacker will always respond optimally to the defender’s strategy [43]. When the attacker has multiple optimal responses to the mixed strategy committed by the defender, a tie occurs. The attacker’s various tie-breaking rules result in different Stackelberg equilibria. In real-world scenarios, we typically assume that the attacker will choose the strategy that benefits the defender, thereby leading to an SSE [44,45]. Hence, the optimal mixed strategy for the defender in an SSE is , which maximizes , where is the set of probability distributions over and is the reaction function for the attacker.
3. Stackelberg Game Model Based on Interval-Valued Intuitionistic Fuzzy Theory
3.1. Basic Assumptions
Consider a target network, such as a railway network, that is formalized in terms of a simple undirected graph , where is the set of nodes and is the set of edges (i.e., the railway stations and the railway lines, respectively, in the railway network). Let be the number of nodes in the network. We denote the number of nodes in the network by . The adjacency matrix of the network G is defined by , where if nodes and are adjacent and otherwise. The following assumptions are made in this model:
- (1)
- There is only one defender, who moves first, and one attacker, who moves after knowing the defender’s strategy commitment.
- (2)
- Both players (i.e., the attacker and the defender) have access to complete information about the target network and possess full knowledge of each other. This means that they are fully informed about all possible strategy profiles and the corresponding payoffs for both sides.
- (3)
- The game consists of a single round, in which both players strive to adopt optimal strategies.
3.2. Cost Model
For node , let and be the attack cost and the defense cost, respectively. The cost or is determined by a specific referential property associated with node , which can be expressed as
where is the attack cost sensitivity parameter and is the defense cost sensitivity parameter. In this paper, the referential property is set as the degree of node . From Equations (5) and (6), the cost associated with a node is determined not only by its degree in the network but also by the cost-sensitive parameters of the players. The parameters and can be determined through expert experience, as well as by considering the actual usage and resource allocation of the infrastructure network.
The available resources of both the attacker and the defender can be defined as follows:
The attack and defense cost constraint parameters are denoted by and , respectively. The values of and represent the attacker’s and defender’s respective cost budgets for attacking or defending.
3.3. Strategies
Based on the cost model presented in Section 3.2, and taking the attacker as an example, the feasible strategies presented in prior studies are defined as follows [13,17].
Suppose that is an attack strategy vector, where represents the strategy set of the attacker. We define as the set of attacked nodes and let if node is attacked ; otherwise, . The total cost of an attack strategy X is denoted by
The cost constraint on the attacker is
Similarly, the cost constraint on the defender is
In an infrastructure network, when one node fails, its function within the network becomes invalid. We assume that node will only fail if it is attacked without protection (i.e., and ). Conversely, if the node is defended (i.e., and ), it will not fail.
The attack and defense strategies defined in Equations (10) and (11) have an expansive strategy space, especially in networks with a large size N. For instance, in a network with , when and . The size of strategy profiles is even larger.
In real-world scenarios, it can be intuitively seen that many decision makers generally choose a better strategy from several options. While there may exist alternative strategies, focusing on the analysis of typical strategies holds greater relevance for decision makers. Therefore, to facilitate the analysis, this paper will consider the following two typical attack and defense strategies [19].
- (1)
- High-degree strategy (HS): In this case, the attacker and the defender allocate all their resources to the nodes with the highest degree. Although the number of nodes selected is small, they have relatively high importance.
- (2)
- Low-degree strategy (LS): In this scenario, the attacker and defender allocate all their resources to nodes with the lowest degree. Although the selected nodes may have lower importance, their quantity is greater.
To obtain an HS (or LS), the nodes are initially sorted in either descending or ascending order based on their referential property. Subsequently, the targets of the attack (or defense) set are incrementally added in this ordered sequence, while continuously checking for any violation of the cost constraint. This process is terminated when adding one more node into the set results in a violation of the constraint.
3.4. Payoffs
To better address uncertainty in attack and defense games in infrastructure networks, it is appropriate to define the payoff for a decision maker as an IVIFN, which is more realistic when dealing with the decision maker’s fuzziness. The payoff functions of the attacker and the defender under this circumstance can be represented as and , respectively. Consider the target network , and let be the set of failing nodes and be the set of removed edges. When a node fails, it loses its ability to maintain its functionality, resulting in the removal of all edges connected to it. denotes the network topology that remains after the attack and defense game is played in a single round. From the perspective of both the attacker and the defender, the change in network topology in the target network G is considered to be the universe of discourse Z. The “satisfaction with the effect of the attack or defense” for the attacker and the defender, when the attacker chooses strategy i and the defender takes strategy j, is represented by the IVIFN on Z, denoted by and , respectively. Because there are only two typical strategies considered in this paper, we have , where strategy 1 represents the HS and strategy 2 represents the LS.
To comprehensively show the effect of the attack and the defense on the target network, we adopt the network efficiency () and the size of the largest connected component () as the functions measuring the network performance. Let be the network in which all attacked nodes become failing nodes without any defense. The alterations in the network topology under the strategy profiles (i,j) can be quantified utilizing Equations (12)–(15). Furthermore, these equations serve as references for the IVIFN payoffs of the attacker and the defender.
Obviously, both and can be used to represent the membership degree with respect to the attacker’s satisfaction, while both and can be used to represent the nonmembership degree with respect to the defender’s dissatisfaction. The membership and nonmembership degrees may vary within certain ranges, and it is more appropriate to consider them as intervals and . In this paper, the membership degree of the attacker and the nonmembership degree of the defender can be obtained based on the aforementioned network metrics, as follows:
where and . We divide the original intervals and into smaller intervals and halve the value range to enhance the accuracy.
Specifically, when more nodes are successfully attacked, the defender’s dissatisfaction and the attacker’s satisfaction increase. To incorporate the subjective preferences of both the attacker and the defender, we modify the expression to reflect the nonmembership of the attacker and the membership of the defender. This can be obtained as follows:
where is a parameter that represents the hesitancy degree of the attacker and the defender, with a higher value of indicating a greater degree of hesitancy. Let denote the number of failing nodes and the total number of nodes. Obviously, we have and . As increases, the membership degree of the defender and the nonmembership degree of the attacker decrease. Because , it is obvious that the IVIFNs that we propose satisfy the condition (i.e., ). Therefore, we can obtain the payoff matrix in Figure 2 based on Equations (16)–(23), where and . The row player is the attacker, and the column player is the defender.
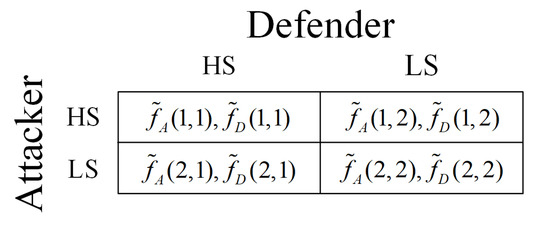
Figure 2.
Payoff matrix of the IVIFS game for the attacker.
The process of generating the IVIFN payoffs of the attacker and the defender under different strategy profiles is shown in Figure 3.
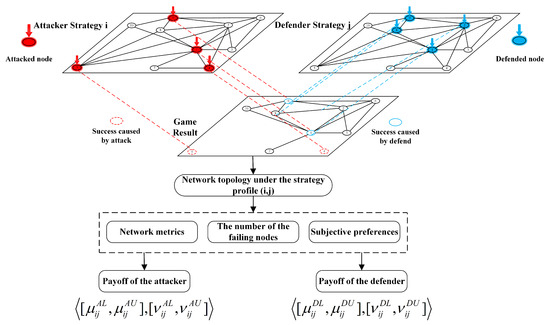
Figure 3.
The process used to generate the IVIFN payoffs of the attacker and the defender in the proposed game model. A network with 10 nodes is shown as an example, and we focus on one game result where the attacker and defender choose strategies involving red and blue nodes, respectively.
4. The Lexicographic Method to Solve a Stackelberg Game with IVIFN Payoffs
4.1. The Lexicographic Method
To solve a Stackelberg game in a crisp condition, Conitzer and Sandholm proposed a multiple linear programming (Multi-LP) algorithm to obtain an SSE solution [42]. Inspired by Multi-LP and the concept of SSE, for a Stackelberg game with the payoffs of IVIFNs, we propose a lexicographic solution method to obtain the optimal strategy profile. For every pure attacker strategy , let represent the probability that the defender commits to the defense strategy and the vector denotes the mixed strategy for the defender. We can derive a mixed strategy for the defender such that (1) pure strategy t is the optimal response for the attacker and (2) the mixed strategy maximizes the defender’s utility under this constraint. The mixed strategy can be derived by solving the following fuzzy mathematical programming model:
where , , and are IVIFNs. The lexicographic order relation is . From Wang’s ranking method in Definition 4, for IVIFNs and , we have if and only if
- (1)
- or
- (2)
- and .
According to Definitions 2 and 4, Equation (24) can be converted into a lexicographic max mathematical programming model as follows:
where indicates the operation of lexicographic maximization.
We develop a lexicographic approach to solve Equation (25) in the sense of Pareto optimality and divide this approach into two stages.
As the scoring function takes priority over the accuracy function in the objective function, the programming model in the first stage is constructed as
The optimal mixed strategy of the defender can be obtained from Equation (26), denoted by . We then have and .
In the second stage, the following programming model is constructed:
By solving Equation (27), we can obtain , and the optimal strategy .
For each pure strategy t of the attacker, we can compute the optimal mixed strategy and the IVIFN utility for the defender. Among these attacker strategies, we choose to maximize the defender’s IVIFN utility, where . The mixed strategy of the defender and strategy of the attacker constitute an optimal strategy profile.
We utilize the aforementioned lexicographic method to solve an example Stackelberg game, where the payoffs are represented by IVIFNs. Let us assume that the risk attitude parameter and the payoff matrices for the attacker and defender are provided as follows:
The rows of the matrices represent the defender, while the columns represent the attacker. When the attacker chooses strategy 1 and applies Equation (26), a feasible solution can be obtained. We then have and . After applying Equation (27), we find that , , and . When the attacker chooses strategy 2 and applies Equation (26), a feasible solution can be obtained. We then have and . After applying Equation (27), we find that , , and .
It is evident that the optimal strategy for the defender is (0,1) and that the attacker’s best response is strategy 1.
4.2. The Lexicographic Algorithm
The specific calculation process to obtain the equilibria of the Stackelberg game with fuzzy number payoffs is shown in Algorithm 1.
| Algorithm 1 The process to obtain equilibrium strategies |
Input: The payoff function (or payoff matrix) of the defender, ; The payoff function (or payoff matrix) of the attacker, ; The strategy set of the defender, ; The strategy set of the attacker, . Output: The equilibrium payoff of the defender, ; The equilibrium payoff of the attacker, ; The defender’s probability distribution when choosing the optimal mixed strategy, ; The attacker’s optimal reaction strategy, .
|
4.3. Advantages and Limitations of the Lexicographic Method
The lexicographic method has the following advantages.
- (1)
- In the lexicographic solution method, the uniqueness of the optimal fuzzy objective values can be guaranteed. It provides a clear and unambiguous ranking of solutions, which is crucial for decision-making processes.
- (2)
- All available information during the solving process, such as the fuzziness of the objectives and the inequality relations within the constraints, is taken into consideration.
- (3)
- The lexicographic method is flexible in the actual decision-making process due to the availability of various similar ranking methods for IVIFNs.
Despite its advantages, the lexicographic method has some limitations.
- (1)
- The proposed method in this paper heavily relies on the input data in the form of IVIFNs. Insufficient or inaccurate payoffs will directly impact the results obtained by the algorithm.
- (2)
- The method proposed in this paper is only applicable to a two-player Stackelberg game and cannot address scenarios with multiple leaders or multiple followers.
5. Experiments
5.1. Experimental Settings
We model a scale-free network with a power-law degree distribution, denoted by [46], to represent infrastructure networks such as power grids, which often exhibit this type of distribution [47]. We set and the cost-sensitive parameter .
To investigate the effect of hesitancy parameter , we set and . According to Definition 1, we present the hesitancy degree for the attacker and defender under different strategy profiles as increases in Table 1. As shown in Table 1, the hesitancy degree under different strategy profiles also increases with the increase in . However, considering real-world scenarios, decision makers typically have a certain hesitancy degree, but it is not excessively high. Therefore, choosing is a more realistic option. Thus, we set in this paper.

Table 1.
The hesitancy degree for the attacker and defender under different strategy profiles versus .
5.2. Payoff Analysis
In Section 3.4, we utilized IVIFNs to represent the payoffs of the attacker and the defender under different strategy profiles in a Stackelberg game in infrastructure networks. This approach was adopted due to the diversity of complex network metrics and the subjective preferences of the players. We analyze the payoffs of the attacker and defender under different strategy profiles when, for example, and (Figure 4a,b and Figure 4c,d, respectively), where , , and .
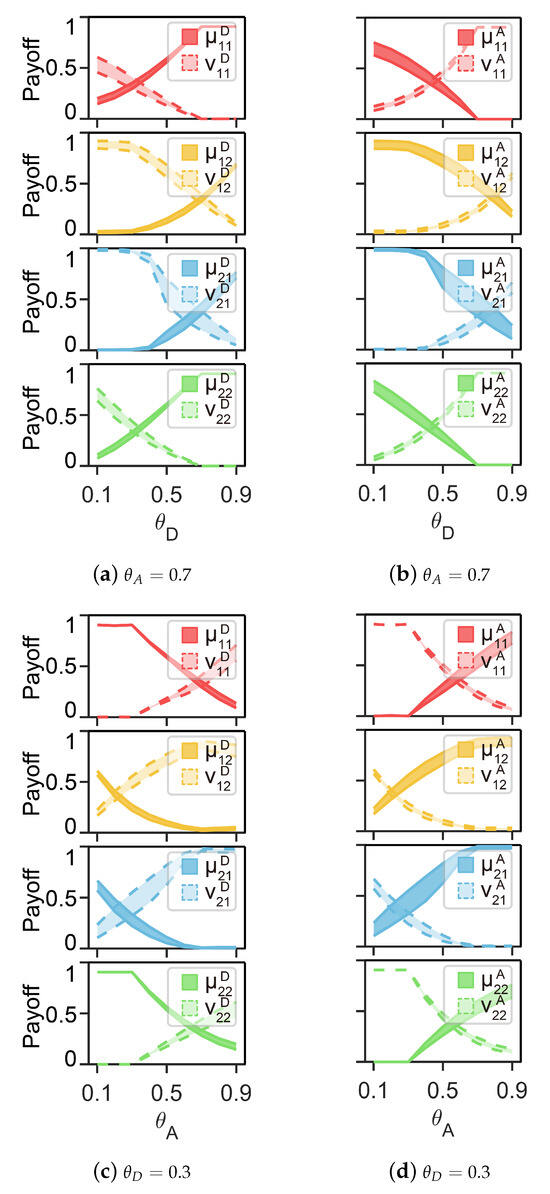
Figure 4.
The defender’s payoffs versus (a) or (c) and the attacker’s payoffs versus (b) or (d) in each strategy profile, where in (a,b), in (c,d). The payoffs of different strategy profiles are represented as IVIFNs, where the intervals of membership degrees are visually depicted using a darker color and are shown by two solid lines representing the upper and lower bounds. On the other hand, the intervals of nonmembership degrees are depicted with a lighter color and are represented by two dashed lines indicating the upper and lower bounds.
From Figure 4, it is evident that when or varies, for , the monotonicity of is consistent with that of , while it demonstrates an inverse trend compared to the monotonicity of and . Because increases and , the defender’s membership in different strategy profiles increases while its nonmembership decreases. On the other hand, the attacker’s membership in different strategy profiles decreases while its nonmembership increases. When increases and , the defender’s membership in different strategy profiles decreases while its nonmembership increases. Conversely, the attacker’s membership in different strategy profiles increases while its nonmembership decreases. It is obvious that when the cost constraint parameter for the attacker or the defender increases, this generally results in an upward trend in the payoffs for different strategy profiles. This can be inferred from the degree of membership and nonmembership.
5.3. The SSE with Different Values of and
We use the score function in Definition 4 to show the SSE payoffs of the attacker and the defender (i.e., and ) in Figure 5.
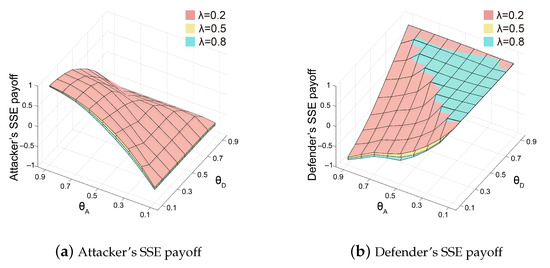
Figure 5.
SSE payoffs of the attacker (a) and the defender (b) under different when .
In Figure 5a, we can see that the SSE payoffs for the attacker have the highest value when it has significantly more resources than the defender and lowest when the attacker has far fewer resources. Simultaneously, the SSE payoffs of the attacker decrease as decreases while increases. Conversely, in Figure 5b, we can see that when the defender’s resources are much lower than those of the attacker, the defender’s SSE payoffs are at their lowest. However, if the defender’s resources surpass those of the attacker, the defender’s SSE payoffs will be high. Simultaneously, overall, the SSE payoffs for the defender increase as decreases while increases. However, when is greater than , regardless of the changes in or , the SSE payoffs for the defender remain at their maximum value. This is because when the defender has more resources, the majority of nodes remain unattacked, resulting in higher and relatively unchanged benefits for the defender. Universally, the SSE payoffs of the attacker and the defender will rise with an increase in .
The SSE strategies of the attacker and the defender with different cases of risk attitude parameters are shown in Figure 6. Upon analyzing the SSE strategies of the attacker and the defender, the following two main characteristics can be observed: (1) regarding the defender, regardless of changes in , when is small () and is large , the probability of adopting the HS is approximately 0.8; (2) regarding the attacker, regardless of changes in , when is small and is large , the attacker will adopt the HS, and the tendency for the attacker to choose HS increases as decreases. For these two characteristics, we provide the following explanation.
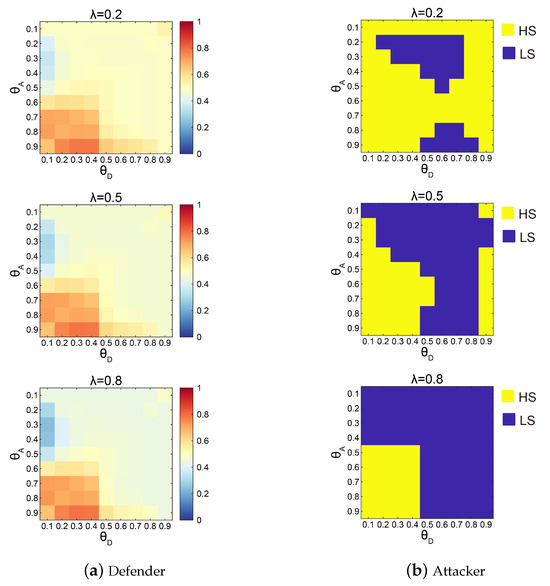
Figure 6.
SSEs of the attacker and the defender when . The various cases of are considered. In (a), the probabilities of the HS in the defender’s mixed SSEs are represented by the colors in the blocks. In (b), the HS and the LS are represented by the yellow and blue blocks, respectively.
For the first characteristic, when in a weak position, the defender is more likely to allocate its limited resources to protecting critical nodes. This aligns with [6], which states that the failure of critical nodes leads to a significant decline in network performance.
For the second characteristic, Figure 7 shows the defender’s optimal utility expressed by the score function in Definition 4 when the best responses of the attacker are the HS and the LS ( and , respectively). According to the theory of breaking ties in SSE, the attacker will choose the best response strategy that maximizes the defender’s utility. From Figure 7, when the defender is in a weak position, we always have , but as decreases, situations where become increasingly prevalent. The reason for this is that, by becoming more risk-seeking, the attacker expresses a preference for the HS, which offers an opportunity for greater utility.
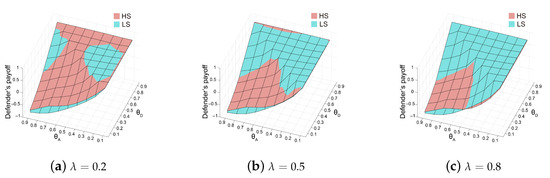
Figure 7.
The defender’s optimal utility expressed by when the best response of the attacker is HS and LS.
5.4. Comparative Analysis
In order to demonstrate the advantage of taking fuzziness into consideration, we conduct an analysis of the target network using crisp payoffs and the solution method described in [18]. We derive the defender’s “crisp strategy” , where the payoffs are expressed as crisp values obtained solely through the size of the largest connected component, and the solving method employed is the Multi-LP method [42]. By substituting into the proposed model in this paper, we can obtain the attacker’s optimal response strategy t by comparing , , which in turn allows us to determine the defender’s payoff, represented by the score function under . As an example, we consider the case of . We compare the SSE payoffs in Figure 6b with the defender’s payoffs under , as shown in Figure 8.
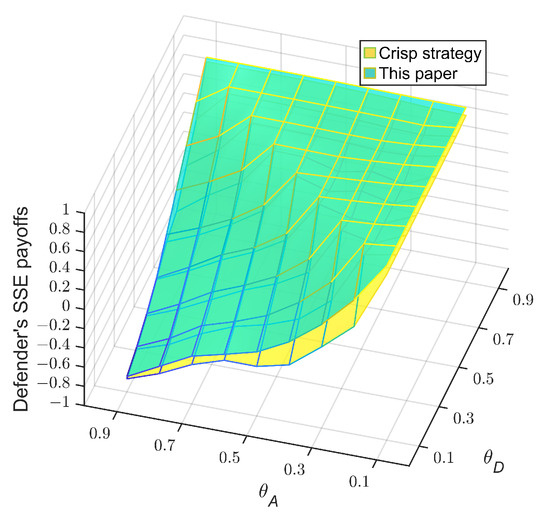
Figure 8.
Comparison of the SSE payoffs obtained from different models and methods.
From Figure 8, it can be observed that taking the fuzziness into consideration can lead to higher SSE payoffs for the defender. Compared to employing the Multi-LP method under the crisp condition, the defender’s SSE payoff can be increased by up to 0.274.
6. Conclusions
Critical infrastructure plays a vital role in the stability and development of modern society, and the protection of such infrastructure has recently drawn extensive attention. In this paper, we analyzed the Stackelberg game for an infrastructure network based on IVIF theory, leading to three main contributions.
First, a Stackelberg game model of infrastructure networks with IVIFN payoffs was introduced considering various complex network metrics and the decision makers’ subjective judgment. The payoffs of the games in infrastructure networks were evaluated as IVIFNs. To show the effect of an attack on or a defense of the target network in the IVIF environment, the network efficiency and size of the largest connected component were used to represent the membership or nonmembership degree, and we modified the satisfaction of the decision makers according to the number of failed nodes. Second, to solve a Stackelberg game with IVIFN payoffs, we proposed a programming model based on the lexicographic method. In the proposed model, we converted the IVIF constraints into their equivalent sets of crisp constraints and utilized the optimization of a deterministic bi-objective function to be solved in a lexicographic manner. The score function and accuracy function with the risk attitude of the attacker and the defender were used, where the priority of the score function was higher than that of the accuracy function. Combined with the proposed model, we designed an algorithm that would utilize the concept of SSE to determine the optimal strategies for the attacker and the defender. Finally, we investigated the IVIFN payoffs and SSEs of the game in a target scale-free network with different cost constraint parameters for the attacker and the defender. We demonstrated the variation in the trends of the payoffs represented by IVIFNs and discovered that the payoffs of both the attacker and the defender were generally monotonic and had opposite trends when changed. We found that under SSE, the defender’s probability of choosing the HS was higher when in a weak position and that the attacker would choose the HS more frequently in various combinations when became lower. We also observed that taking the fuzziness into consideration can lead to higher SSE payoffs for the defender.
This paper studied a Stackelberg game in infrastructure networks with IVIFN payoffs, and an algorithm based on a lexicographic method was proposed to obtain the optimal strategy. In future work, we will investigate a more appropriate method to denote the IVIFN payoffs. This will allow us to better capture the uncertainty of the decision makers’ satisfaction and enhance the accuracy of our analysis. Moreover, for the method of ranking IVIFNs, we will consider using a more appropriate scoring function or accuracy function to improve the quality of the solution.
Author Contributions
Conceptualization, Y.D., J.L. and W.L.; methodology, Y.D. and W.L.; software, Y.D.; validation, Y.D.; formal analysis, Y.D. and J.L.; investigation, J.L. and J.R.; writing—original draft preparation, Y.D. and J.R.; writing—review and editing, J.L., W.L. and Z.L.; visualization, Y.D. and J.R. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
References
- Johnson, C.A.; Flage, R.; Guikema, S.D. Feasibility study of PRA for critical infrastructure risk analysis. Reliab. Eng. Syst. Saf. 2021, 212, 107643. [Google Scholar] [CrossRef]
- Suo, W.; Wang, L.; Li, J. Probabilistic risk assessment for interdependent critical infrastructures: A scenario-driven dynamic stochastic model. Reliab. Eng. Syst. Saf. 2021, 214, 107730. [Google Scholar] [CrossRef]
- Lee, C.; Tien, I. Impacts of varying network parameters on the vulnerability and resilience of interdependent critical infrastructure systems. Sustain. Resilient Infrastruct. 2022, 7, 984–1007. [Google Scholar] [CrossRef]
- Liu, S.; Yin, C.; Chen, D.; Lv, H.; Zhang, Q. Cascading failure in multiple critical infrastructure interdependent networks of syncretic railway system. IEEE Trans. Intell. Transp. Syst. 2022, 23, 5740–5753. [Google Scholar] [CrossRef]
- Herrera, M.; Sasidharan, M.; Cassidy, S.; Parlikad, A.K. Performance assessment of a communication infrastructure with redundant topology: A complex network approach. Comput. Netw. 2023, 228, 109747. [Google Scholar] [CrossRef]
- Albert, R.; Jeong, H.; Barabási, A.L. Error and attack tolerance of complex networks. Nature 2000, 406, 378–382. [Google Scholar] [CrossRef]
- Morone, F.; Makse, H.A. Influence maximization in complex networks through optimal percolation. Nature 2015, 524, 65–68. [Google Scholar] [CrossRef]
- Wang, Z.G.; Deng, Y.; Wang, Z.; Wu, J. Disintegrating spatial networks based on region centrality. Chaos 2021, 31, 061101. [Google Scholar] [CrossRef]
- Fan, N.; Pardalos, P.M. Robust optimization of graph partitioning and critical node detection in analyzing networks. In Proceedings of the 4th International Conference on Combinatorial Optimization and Applications, Kailua-Kona, HI, USA, 18–20 December 2020; Wu, W., Daescu, O., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2010; pp. 170–183. [Google Scholar] [CrossRef]
- Addis, B.; Aringhieri, R.; Grosso, A.; Hosteins, P. Hybrid constructive heuristics for the critical node problem. Ann. Oper. Res. 2016, 238, 637–649. [Google Scholar] [CrossRef]
- Bernaschi, M.; Celestini, A.; Cianfriglia, M.; Guarino, S.; Italiano, G.F.; Mastrostefano, E.; Zastrow, L.R. Seeking critical nodes in digraphs. J. Comput. Sci. 2023, 69, 102012. [Google Scholar] [CrossRef]
- Li, Y.P.; Xiao, Y.; Li, Y.; Wu, J. Which targets to protect in critical infrastructures-a game-theoretic solution from a network science perspective. IEEE Access 2018, 6, 56214–56221. [Google Scholar] [CrossRef]
- Li, Y.P.; Tan, S.Y.; Deng, Y.; Wu, J. Attacker-defender game from a network science perspective. Chaos 2018, 28, 051102. [Google Scholar] [CrossRef] [PubMed]
- Fu, C.; Gao, Y.; Zhong, J.; Sun, Y.; Zhang, P.; Wu, T. Attack-defense game for critical infrastructure considering the cascade effect. Reliab. Eng. Syst. Saf. 2021, 216, 107958. [Google Scholar] [CrossRef]
- Sun, J.; Wang, S.; Zhang, J.; Dong, Q. Attack–defense game in interdependent networks: A functional perspective. J. Infrastruct. Syst. 2023, 29, 04023020. [Google Scholar] [CrossRef]
- Brown, G.; Carlyle, M.; Salmerón, J.; Wood, K. Defending critical infrastructure. Interfaces 2006, 36, 530–544. [Google Scholar] [CrossRef]
- Li, Y.; Qiao, S.; Deng, Y.; Wu, J. Stackelberg game in critical infrastructures from a network science perspective. Phys. A 2019, 521, 705–714. [Google Scholar] [CrossRef]
- Zeng, C.; Ren, B.; Li, M.; Liu, H.; Chen, J. Stackelberg game under asymmetric information in critical infrastructure system: From a complex network perspective. Chaos 2019, 29, 083129. [Google Scholar] [CrossRef]
- Zeng, C.Y.; Ren, B.; Liu, H.; Chen, J. Applying the Bayesian Stackelberg active deception game for securing infrastructure networks. Entropy 2019, 21, 909. [Google Scholar] [CrossRef]
- Fu, C.; Zhang, P.; Zhou, L.; Gao, Y.; Du, N. Camouflage strategy of a stackelberg game based on evolution rules. Chaos Solitons Fractals 2021, 153, 111603. [Google Scholar] [CrossRef]
- Qi, G.; Li, J.; Xu, X.; Chen, G.; Yang, K. An attack-defense game model in infrastructure networks under link hiding. Chaos 2022, 32, 113109. [Google Scholar] [CrossRef]
- Qi, G.; Li, J.; Xu, C.; Chen, G.; Yang, K. Attack-defense game model with multi-type attackers considering information dilemma. Entropy 2022, 25, 57. [Google Scholar] [CrossRef] [PubMed]
- Liu, D.; Zhang, Z. Research on robustness of critical information infrastructure based on attack-defensive game model. J. Phys. Conf. Ser. 2021, 1738, 012112. [Google Scholar] [CrossRef]
- Liu, N.; Liu, S.; Chai, Q.; Zheng, W. A method for analyzing Stackelberg attack-defense game model in 5G by tCPSO. Expert Syst. Appl. 2023, 228, 120386. [Google Scholar] [CrossRef]
- Azevedo, H.; Moreira-Filho, C.A. Topological robustness analysis of protein interaction networks reveals key targets for overcoming chemotherapy resistance in glioma. Sci. Rep. 2015, 5, 16830. [Google Scholar] [CrossRef] [PubMed]
- Tomassini, M. Designing robust scale-free networks under targeted link attack using local information. Physica A 2023, 615, 128563. [Google Scholar] [CrossRef]
- Zadeh, L. Fuzzy sets. Inf. Control 1965, 8, 338–353. [Google Scholar] [CrossRef]
- Atanassov, K.T. Intuitionistic fuzzy sets. Fuzzy Sets Syst. 1986, 20, 87–96. [Google Scholar] [CrossRef]
- Atanassov, K.T. More on intuitionistic fuzzy sets. Fuzzy Sets Syst. 1989, 33, 37–45. [Google Scholar] [CrossRef]
- Atanassov, K.; Gargov, G. Interval valued intuitionistic fuzzy sets. Fuzzy Sets Syst. 1989, 31, 343–349. [Google Scholar] [CrossRef]
- Xu, Z. Methods for aggregating interval-valued intuitionistic fuzzy information and their application to decision making. J. Control Decis. 2007, 22, 215–219. [Google Scholar]
- Wang, F.; Wan, S. Possibility degree and divergence degree based method for interval-valued intuitionistic fuzzy multi-attribute group decision making. Expert Syst. Appl. 2020, 141, 112929. [Google Scholar] [CrossRef]
- Wan, S.; Xu, G.; Dong, J. An Atanassov intuitionistic fuzzy programming method for group decision making with interval-valued Atanassov intuitionistic fuzzy preference relations. Appl. Soft Comput. 2020, 95, 106556. [Google Scholar] [CrossRef]
- Wang, F.; Wan, S. A comprehensive group decision-making method with interval-valued intuitionistic fuzzy preference relations. Soft Comput. 2021, 25, 343–362. [Google Scholar] [CrossRef]
- Wei, A.; Li, D.; Lin, P. An information-based score function of interval-valued intuitionistic fuzzy sets and its application in multiattribute decision making. Soft Comput. 2021, 25, 1913–1923. [Google Scholar] [CrossRef]
- Chen, Z.; Wan, S.; Dong, J. An integrated interval-valued intuitionistic fuzzy technique for resumption risk assessment amid COVID-19 prevention. Inf. Sci. 2023, 619, 695–721. [Google Scholar] [CrossRef] [PubMed]
- Dong, J.; Wan, S. Interval-valued intuitionistic fuzzy best-worst method with additive consistency. Expert Syst. Appl. 2024, 236, 121213. [Google Scholar] [CrossRef]
- Li, D.F. Mathematical-programming approach to matrix games with payoffs represented by Atanassov’s interval-valued intuitionistic fuzzy sets. IEEE Trans. Fuzzy Syst. 2010, 18, 1112–1128. [Google Scholar] [CrossRef]
- Xia, M. Interval-valued intuitionistic fuzzy matrix games based on Archimedean t-conorm and t-norm. Int. J. Gen. Syst. 2018, 47, 278–293. [Google Scholar] [CrossRef]
- Kumar, S.; Kumar, M. A game theoretic approach to solve multiple group decision making problems with interval-valued intuitionistic fuzzy decision matrices. Int. J. Manag. Sci. Eng. Manag. 2021, 16, 34–42. [Google Scholar] [CrossRef]
- Naqvi, D.R.; Verma, R.; Aggarwal, A.; Sachdev, G. Solutions of matrix games involving linguistic interval-valued intuitionistic fuzzy sets. Soft Comput. 2023, 27, 783–808. [Google Scholar] [CrossRef]
- Sandholm, V.C. Computing the Optimal Strategy to Commit to. In Proceedings of the EC ’06: 7th ACM Conference on Electronic Commerce, Ann Arbor, MI, USA, 11–15 June 2006. [Google Scholar]
- Leitmann, G. On generalized Stackelberg strategies. J. Optim. Theory Appl. 1978, 26, 637–643. [Google Scholar] [CrossRef]
- Breton, M.; Alj, A.; Haurie, A. Sequential Stackelberg equilibria in two-person games. J. Optim. Theory Appl. 1988, 59, 71–97. [Google Scholar] [CrossRef]
- Kiekintveld, C.; Jain, M.; Tsai, J.; Pita, J.; Ordóñez, F.; Tambe, M. Computing Optimal Randomized Resource Allocations for Massive Security Games. In Proceedings of the 8th International Conference on Autonomous Agents and Multiagent Systems, AAMAS ’09, Budapest, Hungary, 10–15 May 2009; International Foundation for Autonomous Agents and Multiagent Systems: Richland, SC, USA, 2009; Volume 1, pp. 689–696. [Google Scholar]
- Barabási, A.L.; Albert, R. Emergence of scaling in random networks. Science 1999, 286, 509–512. [Google Scholar] [CrossRef] [PubMed]
- Nesti, T.; Sloothaak, F.; Zwart, B. Emergence of scale-free blackout sizes in power grids. Phys. Rev. Lett. 2020, 125, 058301. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).