Abstract
With the advancement in information and communication technologies (ICTs), the widespread dissemination and sharing of digital images has raised concerns regarding privacy and security. Traditional methods of encrypting images often suffer from limitations such as a small key space and vulnerability to brute-force attacks. To address these issues, this paper proposes a novel eighth-order hyperchaotic system. This hyperchaotic system exhibits various dynamic behaviors, including hyperchaos, sub-hyperchaos, and chaos. The encryption scheme based on this system offers a key space larger than 22338. Through a comprehensive analysis involving histogram analysis, key space analysis, correlation analysis, entropy analysis, key sensitivity analysis, differential attack analysis, and cropping attack analysis, it is demonstrated that the proposed system is capable of resisting statistical attacks, brute force attacks, differential attacks, and cropping attacks, thereby providing excellent security performance.
MSC:
37M25
1. Introduction
The increasing importance of digital images across various domains has been propelled by the rapid progress of information and communication technologies (ICTs). However, the widespread dissemination and sharing of digital images on a large scale have given rise to apprehensions surrounding issues of privacy and security. In order to mitigate these concerns, image encryption technology is widely employed to ensure the confidentiality and integrity of images on diverse devices [1], such as medical, military, satellite, and Internet of Things applications [2]. As a result, addressing these issues has become a critical and urgent challenge in these fields [3].
In recent decades, numerous symmetric image encryption methods have been proposed [4]. Specifically, image encryption techniques based on the Data Encryption Standard (DES) and Advanced Encryption Standard (AES) have been extensively researched and implemented in the field of symmetric encryption. Nevertheless, the security of traditional symmetric encryption algorithms is increasingly being challenged due to the continuous enhancement of computing power and the constant development of cryptanalysis technology. Research indicates that symmetric encryption suffers from drawbacks such as a limited key space and vulnerability to brute force attacks [5].
To overcome these limitations, researchers have turned to chaotic systems that exhibit desirable properties such as high ergodicity, aperiodicity, and sensitivity to initial values [3]. Due to the fact that it is crucial to deliver messages with complete security and to execute them online [6], it is possible to employ chaotic systems to safeguard the security of data transfer and advance the “industrial 4.0 revolution” being developed [7]. Chaotic systems have also been found to be efficient and effective in image encryption. For instance, the Lorenz chaotic system has been applied to image encryption [8], providing strong security and high resistance against common attacks [9]. Another example is the 2D-SCL map, which exhibits good ergodicity and hyperchaotic behavior [10]. However, most existing chaotic systems are traditional chaotic systems that encounter issues such as a small key space and a lack of capability to resist brute force attacks, statistical attacks, and differential attacks. Particularly in light of the developing deep learning landscape [11,12,13], the capacity to analyze complex issues has grown. Therefore, the pursuit of more secure and efficient encryption schemes is an appealing research direction [14].
A hyperchaotic system is characterized by having at least two positive Lyapunov exponents, indicating that its dynamics expand in more than one direction and give rise to a more complex attractor [15]. By increasing the system dimension and incorporating nonlinear terms, the dynamics of a hyperchaotic system become more complex and unpredictable. Compared to traditional chaotic systems, hyperchaotic systems exhibit higher key sensitivity, unpredictability, and pseudo-random properties [16].
In order to establish a more secure system, this work proposes an image encryption algorithm based on a novel eighth-order hyperchaotic system. Dynamic analysis demonstrates that the hyperchaostic system has extremely rich dynamical behaviors, including hyperchaotic, sub-hyperchaotic, chaotic, and limit cycle attractors. On this basis, the image encryption scheme based on this algorithm fully guarantees the confidentiality and integrity of the image by utilizing two different states of the hyperchaotic system [1]. Additionally, it incorporates steps such as row scrambling, column scrambling, and diffusion to enhance security at a higher level. Furthermore, through various analyses of the encryption scheme, including key sensitivity, key space, image histogram, pixel correlation, and other indicators, it has been demonstrated that the proposed algorithm possesses a high level of security and robustness.
The rest of this paper is organized as follows: Section 2 introduces the novel eighth-order hyperchaotic system and analyzes its dynamic characteristics. Section 3 provides an overview of the encryption and decryption schemes based on this system. The experimental results and detailed security analysis are presented in Section 4. Finally, Section 5 concludes the paper.
2. A Novel Eighth-Order Hyperchaotic System and Its Basic Properties
2.1. Equations of a Novel Eighth-Order Hyperchaotic System
Nowadays, some researchers propose low-dimensional chaotic systems to generate pseudo-random sequences to encrypt the original image [17], which means that the encrypted scheme has a small key space and is vulnerable to attacks. Therefore, a higher-dimensional chaotic system is required. Ref. [18] proposed an nth-order chaotic system with hyperbolic sine:
The nonlinear function in this system is , which is defined by , where and . Based on Equation (1), the eighth-order chaotic system with hyperbolic sine is described by
where , are control parameters. When (, ) = (, ) and the initial conditions are (0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1), system (2) has a chaotic attractor, as shown in Figure 1 and the corresponding Lyapunov exponents of this chaotic attractor are (0.49, 0, − 0.60, −0.74, −0.99, −1.16, −1.38, −1.63). Moreover, system (2) has a unique stable equilibrium O(0, 0, 0, 0, 0, 0, 0, 0).
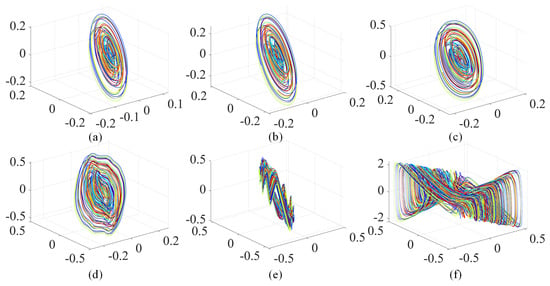
Figure 1.
Chaotic attractor of system (2) with (, ) = (, ): (a) phase plane; (b) phase plane; (c) phase plane; (d) phase plane; (e) phase plane; (f) phase plane.
By coupling a few nonlinear terms, like trigonometric and exponential functions and system (2) to increase the complexity, the following 8D chaotic system is derived:
where ; d is the constant parameter; and f are the coupling parameters; c, , and are control parameters. When () = (, 3, 1, 2, , 2, , ), system (3) has a unique stable equilibrium O(−0.18, −0.18, −0.35, −0.01, −0.33, 0.43, 0, 0.65) and the corresponding eight Lyapunov exponents are (0.36, 0, −0.58, −0.93, −1.04, −1.16, −1.26, 1.39). The chaotic attractor of system (3) is shown in Figure 2.
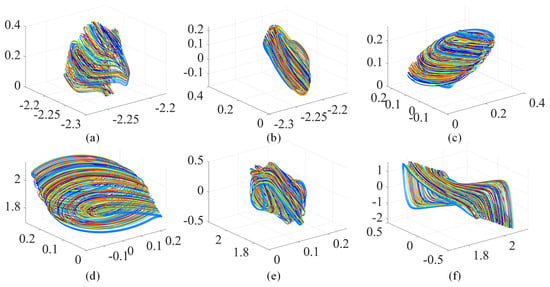
Figure 2.
Chaotic attractor of system (3) with (, , ) = (, 3, 1, 2, , 2, , ): (a) phase plane; (b) phase plane; (c) phase plane; (d) phase plane; (e) phase plane; (f) phase plane.
By coupling a few linear terms and system (3) to control the scope of variables in the system and further improve the complexity [19], a novel eighth-order hyperchaotic system is proposed:
where ; d is the constant parameter; and l are the coupling parameters; c, , and are control parameters, determining the sub-hyperchaotic and hyperchaotic behaviors of the system [20]. Therefore, controllers c, , and and coupling parameters and l cause the classical 8D chaotic system (2) to become a novel eighth-order hyperchaotic system (4) with two positive Lyapunov exponents [21], having eight Lyapunov exponents.
When () = (, 3, 0.75, 2, , 2, −1, 1, −0.01, −3, 1, , , ) and the initial conditions are (0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1), system (4) exhibits a hyperchaotic attractor in Figure 3, and the corresponding eight Lyapunov exponents are (0.34, 0.05, 0, −0.77, −0.96, −1.14, −1.32, −1.96).
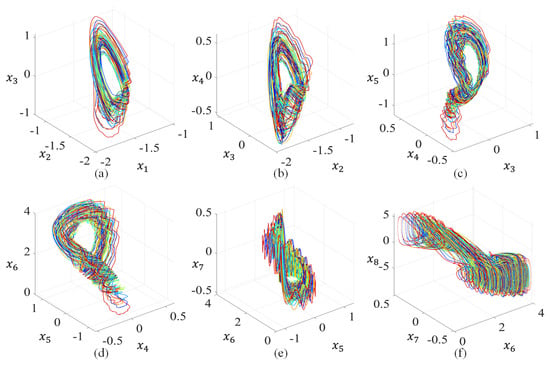
Figure 3.
Hyperchaotic attractor observed from system (4) with (, , ) = (, 3, 0.75, 2, , 2, −1, 1, −0.01, −3, 1, , , ): (a) phase plane; (b) phase plane; (c) phase plane; (d) phase plane; (e) phase plane; (f) phase plane.
When () = (, 3, 0.945, 2, , 2, −1, 1, −0.01, −3, 1, , , ) and the initial conditions are (0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1), system (4) exhibits a sub-hyperchaotic attractor in Figure 4, and the corresponding eight Lyapunov exponents are (0.25, 0, 0, −0.80, −0.96, −1.09, −1.36, −1.98).
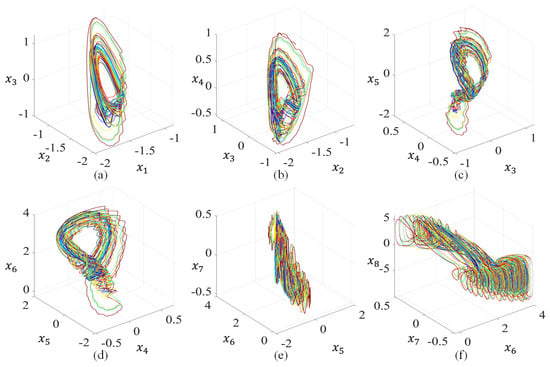
Figure 4.
Sub-hyperchaotic attractor observed from system (4) with () = (, 3, 0.75, 2, , 2, −1, 1, −0.01, −3, 1, , , ): (a) phase plane; (b) phase plane; (c) phase plane; (d) phase plane; (e) phase plane; (f) phase plane.
When the novel eighth-order hyperchaotic system is applied to image encryption, it is necessary to define the default values of the constant parameter and the coupling parameters of the hyperchaotic system () as (, 3, 2, , 2, −1, 1, −0.01, −3, 1, ). The hyperchaotic system is as follows:
where the control parameters are , , , , and the initial conditions are (0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1).
2.2. Observation of Hyperchaos and Complex Dynamics
The Lyapunov exponent of a dynamical system is a quantity that characterizes the rate of separation of infinitesimally close trajectories. Over time, two sets of initially close conditions will gradually separate due to the chaotic nature of the system. The Lyapunov exponent quantifies this exponential separation [22]. By analyzing Lyapunov exponents, valuable insights can be gained regarding a system’s sensitivity to its initial conditions, thereby aiding in the understanding and prediction of the behavior of complex systems [23].
Table 1 shows the properties of the Lyapunov exponent for an ordinary differential dynamical system.

Table 1.
Properties of Lyapunov exponents for ordinary differential dynamical systems.
The Lyapunov exponent spectrum of the system is shown in Figure 5 for . Figure 5 shows a Lyapunov exponent spectrum, in which the eight colored lines represent the eight Lyapunov exponents, the red line represents the first Lyapunov exponent, and the green line represents the second Lyapunov exponent. When the first two Lyapunov exponents are greater than 0 and the third Lyapunov exponent is equal to 0, the system exhibits a hyperchaotic attractor. When the first Lyapunov exponent is greater than 0 and the second Lyapunov exponent is equal to 0, the system exhibits a chaotic attractor. The system exhibits hyperchaotic behavior, with the Lyapunov exponents having the signs (+, +, 0, −, −, −, −, −) when [24]. In individual intervals, a few sub-hyperchaotic regions such as and can be observed, which have the sign of Lyapunov exponents as (+, 0, 0, −, −, −, −, −). In the region of , the system exhibits chaotic behavior, with the Lyapunov exponents having the signs (+, 0, −, −, −, −, −, −). In , the majority of regions exhibit periodic behavior.
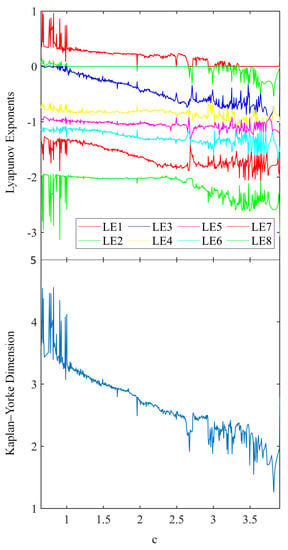
Figure 5.
Lyapunov exponent map and Kaplan–Yorke dimension for a novel eighth-order hyperchaotic system.
The complexity of the attractor can be described by the Kaplan–Yorke dimension, which can be calculated using the following formula:
In the hyperchaotic region, which is defined as , the Kaplan–Yorke dimension falls within the approximate range of . However, for , the Kaplan–Yorke dimension is mostly found within the range of .
Obtaining the equilibrium points is a crucial step in evaluating a new chaotic system, as it allows for the proper identification of the chaotic nature of the system [25].
Let , that is:
When , , , , the given equilibrium point (0.14, 0.17, −0.11, 0.13, −0.87, −0.18, 0.40, 2.48) has been obtained, and the Jacobian matrix can be computed at these equilibrium points. The Jacobian matrix, denoted as , represents the derivative of the multidimensional mapping:
The eight eigenvalues calculated based on the Jacobian matrix are
The eigenvalues corresponding to and , and , and and exhibit a complex conjugate relationship, suggesting a characteristic oscillatory pattern. has a positive real part, indicating divergence. has a negative real part, indicating convergence.
Among the eight eigenvalues under consideration, it is observed that three of them exhibit instability due to the presence of eigenvalues with positive real parts. This implies that any perturbation introduced into the system will amplify over time, leading to a loss of stability at the equilibrium point. Conversely, the remaining five eigenvalues exhibit negative real components, indicating that any disturbance introduced into the system will gradually diminish, thereby preserving the stability of the equilibrium point [26].
The divergence formula for this system is as follows:
The divergence in this system is −5.74. Generally, the divergence of the hyperchaotic system is found to be negative, indicating that the system is a dissipative system.
3. Encryption and Decryption Scheme
The encryption scheme uses two chaotic sequences generated by the novel eighth-order hyperchaotic system Equation (5) when and , which is used to enhance the security of images. The proposed scheme in this study involves row scrambling, column scrambling, and diffusing using chaotic sequence A (), as well as diffusing, column scrambling, and row scrambling using chaotic sequence B (). The encryption algorithm and decryption algorithm are shown in Algorithms 1 and 2.
- Encryption Algorithm:
- Calculate the chaotic sequence A according to the novel eighth-order hyperchaotic system when and initial values are (0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1).
- Calculate the by the average value of a matrix generated by original image.
- Obtain the pixels of the original image and divide the original image into three channels of .
- Calculate the index and from the chaotic sequence A with different keys, where
- Utilize the index based on to perform row scrambling on the output images of the three channels from Step 3.
- Utilize the index based on to perform column scrambling on the output images of the three channels from Step 5.
- Perform XOR operation on the index and the image pixel value from Step 6.
- Calculate the chaotic sequence B according to the novel eighth-order hyperchaotic system when and initial values are (0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1).
- Calculate the index and from the chaotic sequence B with the same formula from Step 4.
- Perform XOR operation on the index and the image pixel value from Step 7.
- Utilize the index based on to perform column scrambling on the output images of the three channels in Step 10.
- Utilize the index based on to perform row scrambling on the output images of the three channels in Step 11.
- Merge the encrypted images of the three channels to generate the final encrypted image.
| Algorithm 1 Encryption Algorithm |
Input: Original Image , First initial conditions, Control parameters, Output: Encrypted image
|
- Decryption Algorithm:
- Calculate the chaotic sequence B according to the novel eighth-order hyperchaotic system when and initial values are (0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1).
- Obtain the pixels of the original image and divide the original image into three channels of .
- Calculate the index and from the chaotic sequence B with different keys.
- Utilize the index based on to perform row recovery on the output images of the three channels from Step 2.
- Utilize the index based on to perform column recovery on the output images of the three channels from Step 4.
- Perform XOR operation on the index and the image pixel value from Step 5.
- Calculate the chaotic sequence A according to the novel eighth-order hyperchaotic system when and initial values are (0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1, 0.1).
- Calculate the index and from the chaotic sequence A with different keys.
- Perform XOR operation on the index and the image pixel value from Step 6.
- Utilize the index based on to perform column recovery on the output images of the three channels from Step 9.
- Utilize the index based on to perform row recovery on the output images of the three channels from Step 10.
- Merge the decrypted images of the three channels to generate the final decrypted image.
| Algorithm 2 Decryption Algorithm |
Input: Encrypted Image , First initial conditions, Control parameters, of Output: Original image
|
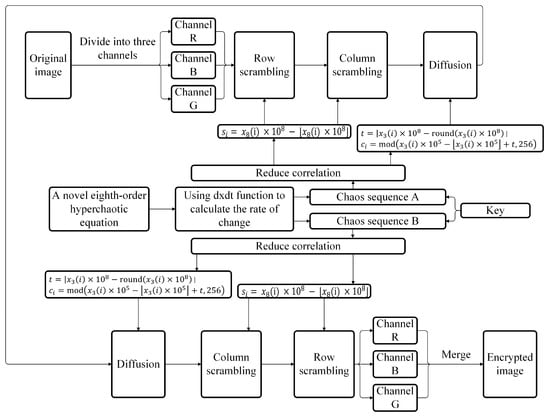
Figure 6.
Scheme of image encryption.
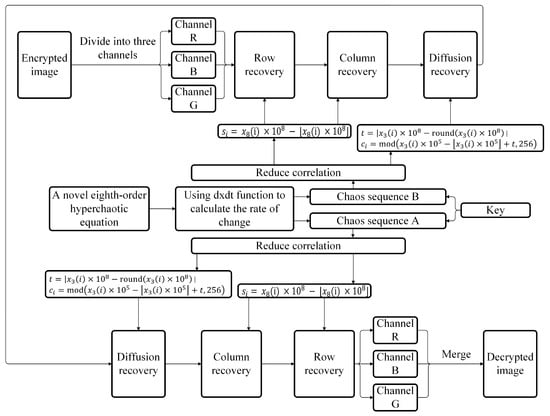
Figure 7.
Scheme of image decryption.
Encryption time, particularly for chaos-based encryption algorithms, determines whether they can be employed in practice [27]. On a computer running Matlab 2022 and equipped with a 3.2 GHz Core R7-5800 U CPU, the speed of the proposed method is evaluated. This test uses a 512 × 512-pixel Lena image. Scrambling and diffusion have running times of 3.0608 and 3.1810 s, respectively. The chaotic sequence generation takes 3.0403 s to complete, while one round of encryption takes 9.5131 s. Since the proposed encryption scheme employs a serial encryption method and has a large key space, which takes longer than other references, a significant amount of effort is required to convert a serial approach to a parallel one and fully utilize the enormous processing power of GPUs [28]. The result of the experiment is that it is evident that there is still room for improvement in the encryption algorithm.
4. Experiments with Related Security Analysis
4.1. Experimental Results
The following is an experimental analysis of the image encryption algorithm proposed in this paper. The experiment involves the use of eight color images, each consisting of 512 × 512 pixels, as depicted in Figure 8. The original images are shown in (a). The encrypted images are shown in (b)–(e), and the decrypted images are shown in (f)–(i).
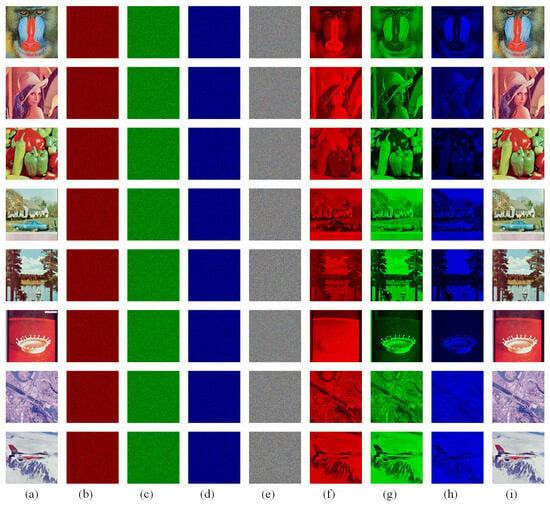
Figure 8.
Image encryption and decryption results: (a) original image; (b–d) encrypted images of three channels of R, G, B; (e) encrypted images of three channels combined; (f–h) decrypted images of three channels of R, G, B; (i) decrypted images of three channels combined.
The result of encrypting a gray image (512 × 512 Lena) is shown in Figure 9, indicating that the image encryption algorithm is also effective for gray images.
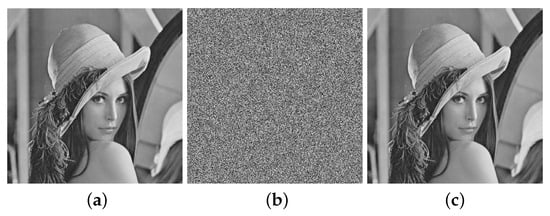
Figure 9.
Gray image encryption and decryption results: (a) original image; (b) encrypted image; (c) decrypted image.
4.2. Histogram Analysis
A histogram is a visual representation that provides an estimation of the distribution of numerical data. It involves plotting the number of pixels at each intensity level to understand the distribution of pixels in an image [29]. To ensure resistance against statistical attacks, the histograms of both the original images and encrypted images need to be described [30].
In order to quantitatively analyze histograms, the experiment uses variances of histograms to assess the uniformity of the encrypted images. Lower variance values indicate a higher level of uniformity in the encrypted images. The formula for calculating the variance of the histograms is as follows [22]:
where Z is the variance of the histogram, and and are the number of pixels i and j in a single channel. In the encryption experiment on the Lena image, the variance of the R channel of the plain image is 770811 and the variance of the R channel of the encrypted image is 262719; the variance of the G channel of the plain image is 490003 and the variance of the G channel of the encrypted image is 262718; the variance of the B channel of the plain image is 950821 and the variance of the B channel of the encrypted image is 262592, the variance of the gray channel of the plain image is 578833 and the variance of the gray channel of the encrypted image is 262698.
Figure 10 is the comparison of the original image and the encrypted image histogram.
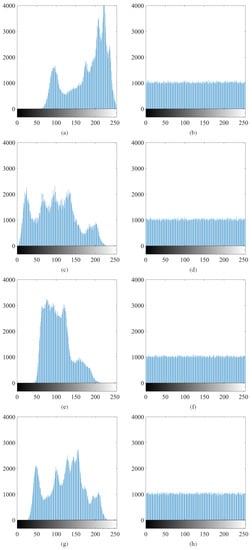
Figure 10.
Comparison of the histograms of the original image and the encrypted image: (a,c,e,g) the histogram of the R, G, B, gray channel of the original image; (b,d,f,h) the histogram of the R, G, B, gray channel of the encrypted image.
Through the calculation of the variance and the analysis of the histogram, the histogram shows the distribution characteristics among the pixels. The encrypted image data of an ideal encryption scheme should be uniformly distributed, which can effectively prevent attackers from obtaining valid information from encrypted images [31], and effectively resist statistical attacks.
4.3. Key Space Analysis
The utilization of a substantial key space has the capability to effectively thwart brute force attacks, thereby mitigating the potential vulnerability of data decryption [32].
If the calculated resolution is , for variable , the area of attraction domain is , there are kinds of choices. There are choices for , choices for , choices for , choices for , choices for , choices for , and choices for . The size of the key space formed by the control variables is . Consider only one control variable c in Equation (5), the key space of the system is . When only the first-order term with a coefficient of 1 in the hyperchaotic equation is considered as the control variable, the key space of the system is . Additionally, the proposed encryption scheme involves two rounds of encryption based on the hyperchaotic system with different control variables, thus the key space is . The actual key space of this scheme will be extremely larger than that value.
4.4. Correlation Analysis
Correlation refers to a statistical association, regardless of causality, between two random variables or sets of bivariate data. In the context of encryption algorithms, it is desirable for encrypted images with low-pixel correlation to be resistant to cryptographic attacks based on statistical analysis [33]. Therefore, a comprehensive understanding of correlations is essential in order to enhance the robustness and effectiveness of image encryption techniques [34].
To calculate the correlation, the following formula is used [35]:
In order to present the importance of correlation more intuitively, Table 2 below will show the pixel value correlation analysis results of eight color images. Table 2 also displays the correlation to a gray house image, indicating that the encryption algorithm still works with gray images.

Table 2.
Correlation coefficient of original images, the first round of encrypted images, and the second round of encrypted images.
It is evident that the correlation value of the original image is close to 1, while the horizontal, vertical, and diagonal correlations of the encrypted image are close to 0 [36]. These values indicate that the correlation between adjacent pixels of the encrypted image is very weak.
Figure 11, Figure 12, and Figure 13, respectively, show the original image, the first round of encrypted image, and the second round of encrypted image in the horizontal, vertical, and diagonal directions of pixel correlation sex. It can be seen from Figure 11 that, since the pixels of the original image are highly correlated, most points in these three directions align with the 45° line. Meanwhile, Figure 12 and Figure 13 show that these points are distributed in the whole area, reflecting the weak pixel correlation in the encrypted image. Therefore, the algorithm proves that it is effective against attacks such as statistical attacks.
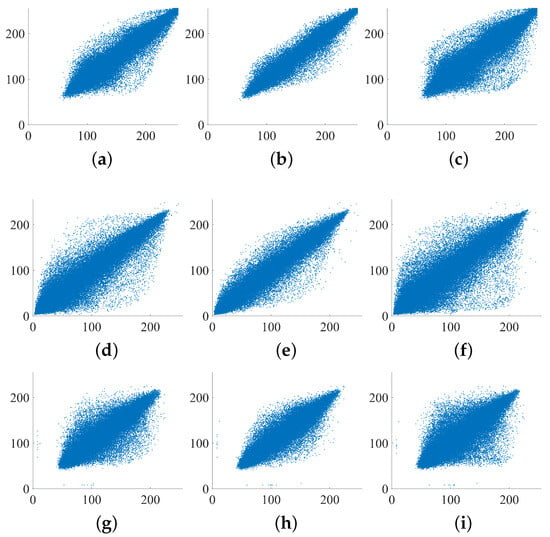
Figure 11.
Correlation analysis of the original image: (a,d,g) correlation between pixels in the horizontal direction of the R, G, B channel of the original image; (b,e,h) correlation between pixels in the vertical direction of the R, G, B channel of the original image; (c,f,i) correlation between pixels in the diagonal direction of the R, G, B channel of the original image.
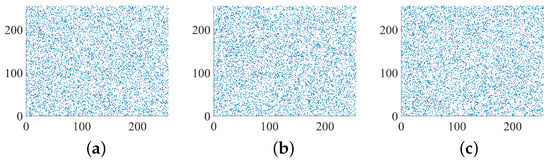
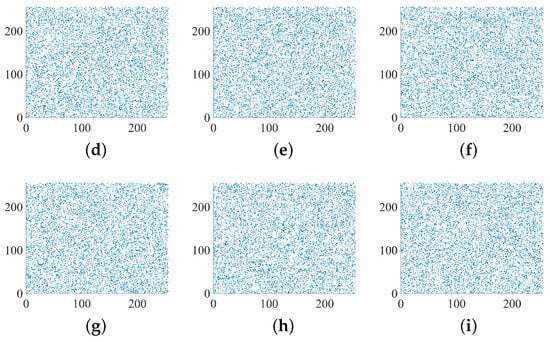
Figure 12.
Correlation analysis of the first round of encrypted image: (a,d,g) correlation between pixels in the horizontal direction of the R, G, B channel of the first round of encrypted image; (b,e,h) correlation between pixels in the vertical direction of the R, G, B channel of the first round of encrypted image; (c,f,i) correlation between pixels in the diagonal direction of the R, G, B channel of the first round of encrypted image.
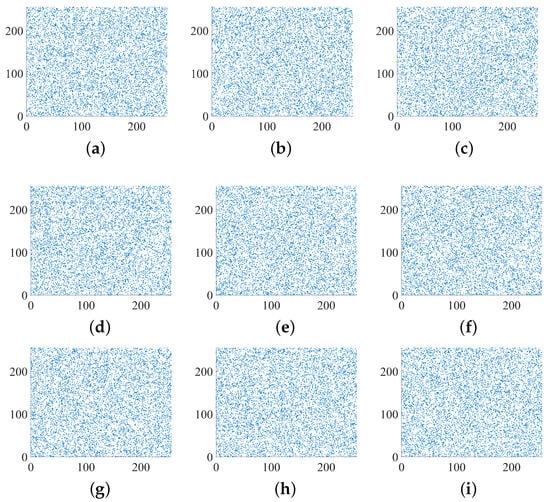
Figure 13.
Correlation analysis of the second round of encrypted image: (a,d,g) correlation between pixels in the horizontal direction of the R, G, B channel of the second round of encrypted image; (b,e,h) correlation between pixels in the vertical direction of the R, G, B channel of the second round of encrypted image; (c,f,i) correlation between pixels in the diagonal direction of the R, G, B channel of the second round of encrypted image.
4.5. Entropy
To measure the expected value of a message and the unpredictability of information content, information entropy (IE) is usually taken to test the strength of a designed encryption algorithm [37], which is defined in Equation (14) for a received message m. The theoretical value of the information entropy is 8 [38].
where L is the length of pixel value in binary form (for images in this experiment, L = 9), denotes the probability of the occurrence of the symbol , and represents the base 2 algorithm. Table 3 is a comparison of the information entropy of the original image and the encrypted image of the eight color images and a gray house image.

Table 3.
Entropy of original image, the first round of encrypted image, and the second round of encrypted image.
4.6. MSE and PSNR Analysis
The most common metric for evaluating the effectiveness of lossy image compression codecs is PSNR. The correct determination of the spatial alignment and level offset between the encrypted picture sequence and the original image sequence is crucial to the PSNR calculation [39]. Given a noise-free m × n monochrome image I and its noisy approximation K, MSE and PSNR are defined as [40]
where is the maximum possible pixel value of the image. When samples are represented using linear PCM with B bits per sample, is . In this paper, the pixels are represented using 8 bits per sample, and is 255.
Table 4 shows the comparison of MSE and PSNR. To reduce the probability of assaults, a lower PSNR value and a higher MSE value are preferred [2]. As a result, it is clear that the PSNR values computed for encrypted pictures using the proposed scheme are comparable to or better than those obtained from other schemes in the literature [41].

Table 4.
MSE and PSNR comparison.
4.7. Ablation Analysis
The ablation analysis shows the improvement in encryption due to two rounds of encryption. The experiment can be divided into four cases and the result is demonstrated in Table 5.

Table 5.
Ablation analysis.
Case 1: Proposed method without scrambling.
Case 2: Proposed method without diffusion.
Case 3: Proposed method without the first round of encryption.
Case 4: Proposed method without the second round of encryption.
It can be seen from the table that, when encryption is performed without diffusion operation, the pixel correlation of the scheme is substantially higher than the proposed scheme, and the UACI is likewise far away from the theoretical value. Without scrambling operations or without one of the rounds being used for encryption, these data are within a respectable range, but the primary benefit of the proposed scheme with two rounds of encryption is the extremely large key space.
4.8. Key Sensitivity Analysis
Key sensitivity analysis is a cryptographic evaluation method that assesses the significance and security of an algorithm [35]. It ensures that even a slight modification to the key will render the original flat image irrecoverable [2].
This encryption system demonstrates a high level of sensitivity to the key. By maintaining constant control variables and initial conditions, a small increment of is added to the key within the scheme. Consequently, the encrypted image exhibits significant differences between the two variables over time, displaying pseudo-random characteristics. This observation suggests that the system’s key is highly sensitive to initial conditions. To illustrate this sensitivity, two similar images are encrypted using keys with minute differences. Figure 14 shows the waveform of and over time and their difference. After performing the subtraction of the encrypted images, it is clearly seen from Figure 15 that the resulting images exhibit significant dissimilarities.
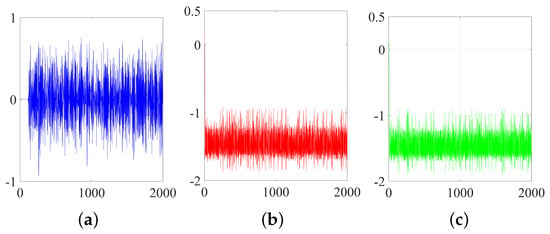
Figure 14.
(a) The difference waveform of and over time; (b) the values of over time; (c) the values of over time.
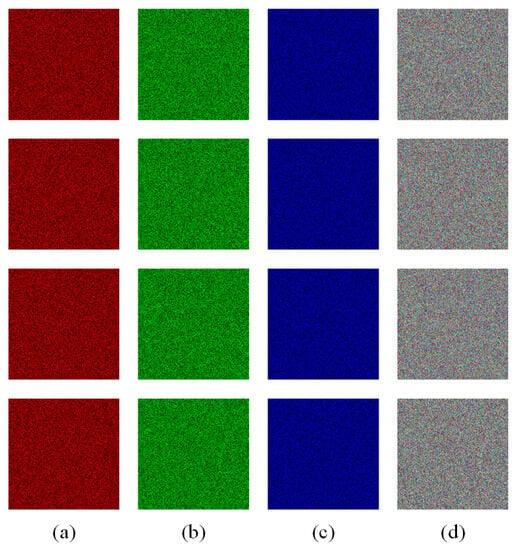
Figure 15.
Key sensitivity test: (a) the difference between the twice encrypted image of the R channel of images; (b) the difference between the twice encrypted image of the G channel of images; (c) the difference between the twice encrypted image of the R channel of images; (d) the difference between the twice encrypted images of three channels of images.
Key sensitivity analysis is usually performed based on the following two indicators: one is the number of pixels rate of change (NPCR), and the other is the uniform average intensity of change (UACI). These two indicators are defined as [44]
where and are two encrypted images of size , and T denotes the largest allowed pixel intensity.
NPCR and UACI are theoretically 99.6043% and 33.4635% [45]. The data presented in Table 6 and Table 7 demonstrates that the test value of the algorithm exhibits a high degree of proximity to the ideal value, indicating a strong level of key sensitivity. In summary, this scheme has high key sensitivity.

Table 6.
NPCR of three channels in key sensitivity analysis.

Table 7.
UACI of three channels in key sensitivity analysis.
4.9. Differential Attack
To avoid differential attacks, a secure cryptosystem should be sensitive to plaintext [46], indicating that even minor alterations in the pixel values of a regular image can result in significant modifications in the corresponding encrypted image [47]. Figure 16 shows the results of differential attack experiments.
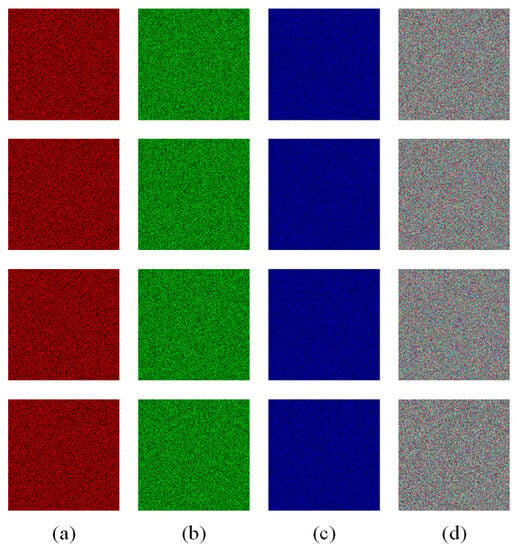
Figure 16.
Differential attack test: (a) the difference between the twice encrypted image of the R channel of images; (b) the difference between the twice encrypted image of the G channel of images; (c) the difference between the twice encrypted image of the R channel of images; (d) the difference between the twice encrypted images of three channels of images.
Table 8 and Table 9 show the NPCR and UACI of the differential attack. The test results indicate a strong correlation between the system’s value and the theoretical value, suggesting that the system is capable of effectively defending against differential attacks.

Table 8.
NPCR of three channels in differential attack experiments.

Table 9.
UACI of three channels in differential attack experiments.
4.10. Cropping Attack
A robust cryptographic system should have the capability to resist potential data loss during transmission and storage [48]. The receiver wants to recover the plain image as much as possible from some of the information received in this case [33]. Thus, the analysis of cropping attacks is a valuable approach to assessing the robustness of encryption schemes [49].
For evaluating and comparing the performance of different encryption algorithms in the face of cropping attacks, a series of experiments is conducted, and the following comparative illustrations are produced. As shown in Figure 17, the images decrypted from the cipher images with data loss rates of 6.25, 12.5%, 23.44%, 25%, 43.75%, and 50% are very similar to the original images and can still provide valuable information about the input images’ visual information.
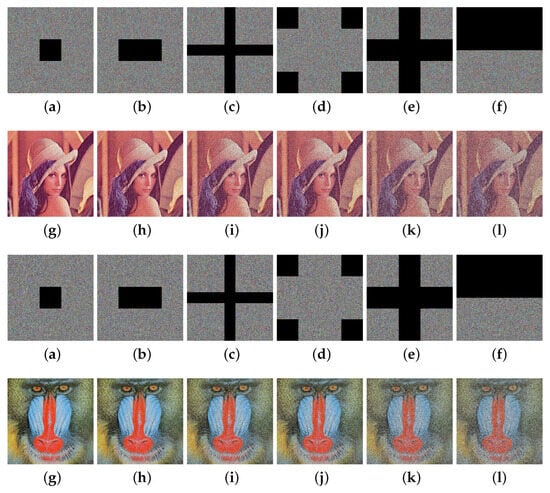
Figure 17.
Cropping attack test [50]: (a) cropped 6.25% of the encrypted image; (b) cropped 12.5% of the encrypted image; (c) cropped 23.44% of the encrypted image; (d) cropped 25% of the encrypted image; (e) cropped 43.75% of the encrypted image; (f) cropped 50% of the encrypted image; (g) decrypted image based on the cropped 6.25% of the encrypted image; (h) decrypted image based on the cropped 12.5% of the encrypted image; (i) decrypted image based on the cropped 23.44% of the encrypted image; (j) decrypted image based on the cropped 25% of the encrypted image; (k) decrypted image based on the cropped 43.75% of the encrypted image; (l) decrypted image based on the cropped 50% of the encrypted image.
4.11. Randomness Tests for the Encrypted Image
In order to guarantee the security of the encryption system, the image should contain properties for further measurable investigation to distinguish between different designs [51]. For the DIEHARD test, which focuses on several types of potential randomness in the sequence [52], the value of each pixel of the encrypted image is transformed into binary. The results of the DIEHARD test in Table 10 show that the proposed scheme exhibits highly random behavior.

Table 10.
Result of DIEHARD tests suite.
4.12. Comparison with Existing Methods
This section compares the scheme with existing encryption schemes by comparing the key space, entropy, CC, NPCR, and UACI. CC is the average value of the correlation of adjacent pixels in the horizontal, vertical, and diagonal directions of the image, and the formula is as follows:
where , , and are correlations of horizontal, vertical, and diagonal of encrypted images.
Table 11 shows the comparison of encrypted Lena images.

Table 11.
Key space, entropy, CC, NPCR, and UACI comparison.
5. Conclusions
The image encryption algorithm based on the novel eighth-order hyperchaotic system proposed in this paper performs a significant level of security in experiments. The algorithm effectively improves the randomness and unpredictability of encrypted images through multiple rounds of diffusion and scrambling operations. In contrast to the conventional chaotic system, the novel hyperchaotic system exhibits superior performance in terms of key space and resistance against attacks, while also demonstrating heightened sensitivity to keys. By comparing the results of other encryption algorithms, it can be seen that the key space of the proposed algorithm is significantly larger than those of other references; NPCR and UACI are closer to the theoretical values; and the pixel correlation is also lower than most references. Based on the aforementioned notable benefits, it is evident that the algorithm demonstrates exceptional performance in the encryption of images.
Author Contributions
Conceptualization, H.Q. and J.L.; methodology, H.Q. and J.L.; software, H.Q., J.L. and X.Z.; validation, H.Q., J.L. and H.Y.; formal analysis, H.Y.; investigation, H.Q.; resources, J.L.; data curation, H.Q.; writing—original draft preparation, H.Q.; writing—review and editing, J.L.; visualization, J.L.; supervision, H.Q.; project administration, J.L.; funding acquisition, J.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Regional Project of the National Natural Science Foundation of China grant number 82260364, Gansu Provincial Science and Technology Department Youth Fund Project grant number 22JR5RA166, Gansu Higher Education Innovation Fund Project grant number 2022B-084.
Data Availability Statement
All experimental pictures in this article come from standard data sets, and all data are generated through algorithms.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Zheng, Q.; Wang, X.; Khurram Khan, M.; Zhang, W.; Gupta, B.B.; Guo, W. A Lightweight Authenticated Encryption Scheme Based on Chaotic SCML for Railway Cloud Service. IEEE Access 2018, 6, 711–722. [Google Scholar] [CrossRef]
- Elias, E.P. Multichannel image encryption using dynamic substitution and JSMP map. Optik 2023, 288, 171183. [Google Scholar] [CrossRef]
- Zhou, Y.; Bao, L.; Chen, C.P. A new 1D chaotic system for image encryption. Signal Process. 2014, 97, 172–182. [Google Scholar] [CrossRef]
- Yassein, M.B.; Aljawarneh, S.; Qawasmeh, E.; Mardini, W.; Khamayseh, Y. Comprehensive study of symmetric key and asymmetric key encryption algorithms. In Proceedings of the 2017 International Conference on Engineering and Technology (ICET), Antalya, Turkey, 21–23 August 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Zhang, Y.-P.; Liu, W.; Cao, S.-P.; Zhai, Z.-J.; Nie, X.; Dai, W.-D. Digital image encryption algorithm based on chaos and improved DES. In Proceedings of the 2009 IEEE International Conference on Systems, Man and Cybernetics, San Antonio, TX, USA, 11–14 October 2009; pp. 474–479. [Google Scholar] [CrossRef]
- Giap, V.N.; Nguyen, Q.D.; Pham, D.H.; Lin, C.M. Wireless Secure Communication of Chaotic Systems Based on Takagi–Sugeno Fuzzy Optimal Time Varying Disturbance Observer and Sliding Mode Control. Int. J. Fuzzy Syst. 2023, 1–15. [Google Scholar] [CrossRef]
- Giap, V.N. Text message secure communication based on fractional-order chaotic systems with Takagi–Sugeno fuzzy disturbance observer and sliding mode control. Int. J. Dyn. Control 2023, 2023, 1–15. [Google Scholar] [CrossRef]
- Yu, Y.; Li, H.X.; Wang, S.; Yu, J. Dynamic analysis of a fractional-order Lorenz chaotic system. Chaos Solitons Fractals 2009, 42, 1181–1189. [Google Scholar] [CrossRef]
- Zou, C.; Zhang, Q.; Wei, X.; Liu, C. Image Encryption Based on Improved Lorenz System. IEEE Access 2020, 8, 75728–75740. [Google Scholar] [CrossRef]
- Chen, C.; Sun, K.; He, S. An improved image encryption algorithm with finite computing precision. Signal Process. 2020, 168, 107340. [Google Scholar] [CrossRef]
- Dou, J.X.; Pan, A.Q.; Bao, R.; Mao, H.H.; Luo, L. Sampling through the lens of sequential decision making. arXiv 2022, arXiv:2208.08056. [Google Scholar]
- Dou, J.X.; Bao, R.; Song, S.; Yang, S.; Zhang, Y.; Liang, P.P.; Mao, H.H. Demystify the Gravity Well in the Optimization Landscape (student abstract). In Proceedings of the AAAI Conference on Artificial Intelligence, Washington, DC, USA, 7–14 February 2023. [Google Scholar]
- Dou, J.X.; Mao, H.; Bao, R.; Liang, P.P.; Tan, X.; Zhang, S.; Jia, M.; Zhou, P.; Mao, Z.H. The Measurement of Knowledge in Knowledge Graphs.
- Mobayen, S.; Vaidyanathan, S.; Sambas, A.; Kacar, S.; Cavusoglu, U. A Novel Chaotic System With Boomerang-Shaped Equilibrium, Its Circuit Implementation and Application to Sound Encryption. Iran. J. Sci. Technol. Trans. Electr. Eng. 2019, 43, 1–12. [Google Scholar] [CrossRef]
- Sun, K.; Liu, X.; Zhu, C.; Sprott, J.C. Hyperchaos and hyperchaos control of the sinusoidally forced simplified Lorenz system. Nonlinear Dyn. 2012, 69, 1383–1391. [Google Scholar] [CrossRef]
- Xiong, Z.; Qu, S.; Luo, J. Adaptive Multi-Switching Synchronization of High-Order Memristor-Based Hyperchaotic System with Unknown Parameters and Its Application in Secure Communication. Complexity 2019, 2019, 3827201. [Google Scholar] [CrossRef]
- Li, Q.; Chen, L. An image encryption algorithm based on 6-dimensional hyper chaotic system and DNA encoding. Multimed. Tools Appl. 2023, 1–18. [Google Scholar] [CrossRef]
- Liu, J.; Ma, J.; Lian, J.; Chang, P.; Ma, Y. An Approach for the Generation of an Nth-Order Chaotic System with Hyperbolic Sine. Entropy 2018, 20, 230. [Google Scholar] [CrossRef]
- Chen, H.; Bai, E.; Jiang, X.; Wu, Y. A Fast Image Encryption Algorithm Based on Improved 6-D Hyper-Chaotic System. IEEE Access 2022, 10, 116031–116044. [Google Scholar] [CrossRef]
- Yang, Q.; Zhu, D.; Yang, L. A new 7D hyperchaotic system with five positive Lyapunov exponents coined. Int. J. Bifurc. Chaos 2018, 28, 1850057. [Google Scholar] [CrossRef]
- Yang, Q.; Bai, M. A new 5D hyperchaotic system based on modified generalized Lorenz system. Nonlinear Dyn. 2017, 88, 189–221. [Google Scholar] [CrossRef]
- Liu, J.; Ma, Y.; Li, S.; Lian, J.; Zhang, X. A new simple chaotic system and its application in medical image encryption. Multimed. Tools Appl. 2018, 77, 22787–22808. [Google Scholar] [CrossRef]
- Koçak, H.; Palmer, K. Lyapunov Exponents and Sensitive Dependence. J. Dyn. Differ. Equ. 2010, 22, 381–398. [Google Scholar] [CrossRef]
- Singh, J.P.; Roy, B. The nature of Lyapunov exponents is (+, +, -, -). Is it a hyperchaotic system? Chaos Solitons Fractals 2016, 92, 73–85. [Google Scholar] [CrossRef]
- Yang, Y.; Gao, J.; Imani, H. Design, analysis, circuit implementation, and synchronization of a new chaotic system with application to information encryption. AIP Publ. 2023, 13, 075116. [Google Scholar] [CrossRef]
- Vaidyanathan, S.; Tlelo-Cuautle, E.; Benkouider, K.; Sambas, A.; Ovilla-Martínez, B. FPGA-Based Implementation of a New 3-D Multistable Chaotic Jerk System with Two Unstable Balance Points. Technologies 2023, 11, 92. [Google Scholar] [CrossRef]
- Lin, Z.; Liu, J.; Lian, J.; Ma, Y.; Zhang, X. A Novel Fast Image Encryption Algorithm for Embedded Systems. Multimed. Tools Appl. 2019, 78, 20511–20531. [Google Scholar] [CrossRef]
- Lee, W.K.; Phan, R.C.W.; Yap, W.S.; Goi, B.M. SPRING: A Novel Parallel Chaos-Based Image Encryption Scheme. Nonlinear Dyn. 2018, 92, 575–593. [Google Scholar] [CrossRef]
- Sankpal, P.R.; Vijaya, P.A. Image Encryption Using Chaotic Maps: A Survey. In Proceedings of the 2014 Fifth International Conference on Signal and Image Processing, Bangalore, India, 8–10 January 2014; pp. 102–107. [Google Scholar] [CrossRef]
- Souyah, A.; Faraoun, K.M. An image encryption scheme combining chaos-memory cellular automata and weighted histogram. Nonlinear Dyn. 2016, 86, 639–653. [Google Scholar] [CrossRef]
- Sang, Y.; Sang, J.; Alam, M.S. Image encryption based on logistic chaotic systems and deep autoencoder. Pattern Recognit. Lett. 2022, 153, 59–66. [Google Scholar] [CrossRef]
- Mamlin, B.W.; Tierney, W.M. The Promise of Information and Communication Technology in Healthcare: Extracting Value from the Chaos. Am. J. Med. Sci. 2016, 351, 59–68. [Google Scholar] [CrossRef]
- Ye, G.; Jiao, K.; Huang, X. Quantum logistic image encryption algorithm based on SHA-3 and RSA. Nonlinear Dyn. 2021, 104, 2807–2827. [Google Scholar] [CrossRef]
- Anishchenko, V.; Vadivasova, T.; Okrokvertskhov, G.; Strelkova, G. Correlation analysis of dynamical chaos. Phys. A Stat. Mech. Its Appl. 2003, 325, 199–212. [Google Scholar] [CrossRef]
- Liu, S.; Ye, G. Asymmetric image encryption algorithm using a new chaotic map and an improved radial diffusion. Optik 2023, 288, 171181. [Google Scholar] [CrossRef]
- Pak, C.; Huang, L. A new color image encryption using combination of the 1D chaotic map. Signal Process. 2017, 138, 129–137. [Google Scholar] [CrossRef]
- Ye, G.; Zhao, H.; Chai, H. Chaotic image encryption algorithm using wave-line permutation and block diffusion. Nonlinear Dyn. 2016, 83, 2067–2077. [Google Scholar] [CrossRef]
- Zhen, P.; Zhao, G.; Min, L.; Jin, X. Chaos-based image encryption scheme combining DNA coding and entropy. Multimed. Tools Appl. 2016, 75, 6303–6319. [Google Scholar] [CrossRef]
- Valandar, M.Y.; Ayubi, P.; Barani, M.J. A new transform domain steganography based on modified logistic chaotic map for color images. J. Inf. Secur. Appl. 2017, 34, 142–151. [Google Scholar] [CrossRef]
- Li, X.; Yu, H.; Zhang, H.; Jin, X.; Sun, H.; Liu, J. Video encryption based on hyperchaotic system. Multimed. Tools Appl. 2020, 79, 23995–24011. [Google Scholar] [CrossRef]
- Elkandoz, M.T.; Alexan, W. Image encryption based on a combination of multiple chaotic maps. Multimed. Tools Appl. 2022, 81, 25497–25518. [Google Scholar] [CrossRef]
- Harun, S.W.; Zhang, X.; Wang, L.; Wang, Y.; Niu, Y.; Li, Y. An Image Encryption Algorithm Based on Hyperchaotic System and Variable-Step Josephus Problem. Int. J. Opt. 2020, 2020, 6102824. [Google Scholar] [CrossRef]
- Alexan, W.; ElBeltagy, M.; Aboshousha, A. Lightweight Image Encryption: Cellular Automata and the Lorenz System. In Proceedings of the 2021 International Conference on Microelectronics (ICM), Nis, Serbia, 12–14 September 2021; pp. 34–39. [Google Scholar] [CrossRef]
- Zhou, Y.; Hua, Z.; Pun, C.M.; Philip Chen, C.L. Cascade Chaotic System with Applications. IEEE Trans. Cybern. 2015, 45, 2001–2012. [Google Scholar] [CrossRef]
- Wang, M.; Wang, X.; Zhang, Y.; Zhou, S.; Zhao, T.; Yao, N. A novel chaotic system and its application in a color image cryptosystem. Opt. Lasers Eng. 2019, 121, 479–494. [Google Scholar] [CrossRef]
- Zhu, C. A novel image encryption scheme based on improved hyperchaotic sequences. Opt. Commun. 2012, 285, 29–37. [Google Scholar] [CrossRef]
- Song, C.Y.; Qiao, Y.L.; Zhang, X.Z. An image encryption scheme based on new spatiotemporal chaos. Opt. Int. J. Light Electron Opt. 2013, 124, 3329–3334. [Google Scholar] [CrossRef]
- Wang, L.; Song, H.; Liu, P. A novel hybrid color image encryption algorithm using two complex chaotic systems. Opt. Lasers Eng. 2016, 77, 118–125. [Google Scholar] [CrossRef]
- Yan, X.; Wang, X.; Xian, Y. Chaotic image encryption algorithm based on arithmetic sequence scrambling model and DNA encoding operation. Multimed. Tools Appl. 2021, 80, 10949–10983. [Google Scholar] [CrossRef]
- Gao, X.; Mou, J.; Xiong, L.; Sha, Y.; Yan, H.; Cao, Y. A fast and efficient multiple images encryption based on single-channel encryption and chaotic system. Nonlinear Dyn. 2022, 108, 613–636. [Google Scholar] [CrossRef]
- Yasser, I.; Khalil, A.T.; Mohamed, M.A.; Samra, A.S.; Khalifa, F. A Robust Chaos-Based Technique for Medical Image Encryption. IEEE Access 2022, 10, 244–257. [Google Scholar] [CrossRef]
- Mohammad Seyedzadeh, S.; Mirzakuchaki, S. A fast color image encryption algorithm based on coupled two-dimensional piecewise chaotic map. Signal Process. 2012, 92, 1202–1215. [Google Scholar] [CrossRef]
- Basha, H.A.; Mohra, A.S.S.; Diab, T.O.M.; Sobky, W.I.E. Efficient Image Encryption Based on New Substitution Box Using DNA Coding and Bent Function. IEEE Access 2022, 10, 66409–66429. [Google Scholar] [CrossRef]
- Wei, X.; Guo, L.; Zhang, Q.; Zhang, J.; Lian, S. A novel color image encryption algorithm based on DNA sequence operation and hyper-chaotic system. J. Syst. Softw. 2012, 85, 290–299. [Google Scholar] [CrossRef]
- Kumar Patro, K.A.; Acharya, B. An efficient colour image encryption scheme based on 1-D chaotic maps. J. Inf. Secur. Appl. 2019, 46, 23–41. [Google Scholar] [CrossRef]
- ul Haq, T.; Shah, T. 12×12 S-box Design and its Application to RGB Image Encryption. Optik 2020, 217, 164922. [Google Scholar] [CrossRef]
- Huang, L.; Li, W.; Xiong, X.; Yu, R.; Wang, Q.; Cai, S. Designing a double-way spread permutation framework utilizing chaos and S-box for symmetric image encryption. Opt. Commun. 2022, 517, 128365. [Google Scholar] [CrossRef]
- Huang, L.; Cai, S.; Xiong, X.; Xiao, M. On symmetric color image encryption system with permutation-diffusion simultaneous operation. Opt. Lasers Eng. 2019, 115, 7–20. [Google Scholar] [CrossRef]
- Hamza, R.; Titouna, F. A novel sensitive image encryption algorithm based on the Zaslavsky chaotic map. Inf. Secur. J. A Glob. Perspect. 2016, 25, 162–179. [Google Scholar] [CrossRef]
- Huang, L.; Cai, S.; Xiao, M.; Xiong, X. A Simple Chaotic Map-Based Image Encryption System Using Both Plaintext Related Permutation and Diffusion. Entropy 2018, 20, 535. [Google Scholar] [CrossRef] [PubMed]
- Lin, C.M.; Pham, D.H.; Huynh, T.T. Synchronization of Chaotic System Using a Brain-Imitated Neural Network Controller and Its Applications for Secure Communications. IEEE Access 2021, 9, 75923–75944. [Google Scholar] [CrossRef]
- Lin, C.M.; Pham, D.H.; Huynh, T.T. Encryption and Decryption of Audio Signal and Image Secure Communications Using Chaotic System Synchronization Control by TSK Fuzzy Brain Emotional Learning Controllers. IEEE Trans. Cybern. 2022, 52, 13684–13698. [Google Scholar] [CrossRef]
- Wu, Y.; Zhang, L.; Berretti, S.; Wan, S. Medical Image Encryption by Content-Aware DNA Computing for Secure Healthcare. IEEE Trans. Ind. Inform. 2023, 19, 2089–2098. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).