Abstract
The Internet of Things (IoT) networks are the most prone to internal as well as external attacks in addition to energy consumption problems. Conventional security solutions are not able to address these issues effectively due to the limited resources of sensor nodes participating in IoT communications. In this work, an Efficient and Secure Fog Based Routing Mechanism (ESFRM) is proposed to protect the network from faulty internal as well as external attacks. Every node participating in IoT communications calculates the comprehensive trust value of the next intermediate node which is the addition of direct trust, indirect trust and energy trust values before forwarding the data. This comprehensive trust value is then compared with the comprehensive threshold trust value to decide whether the particular node is a rogue node or a valid normal node. Further, an enhanced RSA (Rivest, Shamir, Adleman) algorithm is implemented to provide three levels of data security from Cluster Head (CH) to fog node, from fog node to cloud server and directly from CH to cloud server. For this purpose, an efficient CH selection technique is also proposed in this work. The proposed methodology is compared with the Secure Energy-efficient Fog-based Routing (SEFR) protocol and Trust-aware Secure Routing Protocol (TSRP). The evaluation results show that the proposed ESFRM outperforms the conventional schemes with respect to energy consumption, malicious node detection and transmission rate.
Keywords:
Internet of Things (IoT); cloud-native fog computing; advanced algorithms; wireless communications; security in IoT MSC:
62F99; 65C99
1. Introduction
The Internet of Things (IoT) network is made up of small devices commonly known as sensor nodes that are used in physical and environmental conditions to monitor a wide range of parameters including temperature, pressure, light, heat, motion, sound, vibration and many more. These sensor nodes are often deployed in risky and unattended territory where they accumulate myriad types of environmental data and transmit it to the base station or sink node via hop-by-hop or intermediate nodes for further processing [1,2,3,4,5,6,7]. The IoT networks have been the buzz of the contemporary period due to their amazing effects that have taken the globe by storm. In order to deal with diverse problems, the sensor nodes are now being widely employed, thereby jacking up the number of devices to manifold. Contrary to the past, where human resources were needed to monitor environmental factors in stable areas, the unsteady areas or regions used to remain unrevealed due to potential dangers and the incapacity of people to access the extremely volatile locations. Due to this, the sensor nodes are now used in these situations to lessen the difficulties faced by the general public. However, sensor nodes are installed in dangerous/hostile and even unattended premises where they are more prone to various kinds of attacks [8,9,10]. Moreover, owing to the absence of any predefined topology in the IoT network, every node requires the capacity of routing for data forwarding. As a result, the nodes are increasingly exposed to myriad routing assaults [11]. Although a lot of traditional cryptographic, detecting malicious nodes and routing algorithms [12,13,14,15,16,17,18,19,20] have been designed to make IoT networks secure and safe these algorithms demand heavy computations/calculations and processing which cause lots of energy utilization. In addition to this, the cryptography and authentication-based algorithms work only on the IoT network comprising all the trustworthy and cooperative nodes, therefore, they are not suitable to cope with internal node attacks launched by malicious and faulty sensor nodes [21,22,23,24]. In order to detect and remove faulty/malicious nodes to prevent these rogue nodes from launching internal node attacks within the network, trust-based security mechanisms have been proven to be most efficient and effective [25]. Aside from the internal node attacks in IoT networks, efficient energy utilization is also a serious factor to consider since it has a significant influence on network performance. In addition to energy constraints, the storage and processing capacities of sensor nodes are also limited in fog cloud environment. In order to address the issues faced in the cloud environment and to alleviate the strain on cloud servers, the scientific community has developed a new idea called fog extending the functionality of cloud computing. The fog processing is a sort of distributed processing paradigm in which some data processing, calculation, and storage are carried out between the devices that generate the data on the cloud server [26]. These objects, often referred to as fog devices, are positioned close to the sensor nodes that produce data. Therefore, the data that needs an immediate reply is analyzed, computed and processed here at fog devices and finally, the result is sent back to the desired location. The data that is frequently needed is also retained at fog devices, and the remaining information is sent to the cloud server for further processing in addition to long-term storage. This capability significantly reduces the workload on the server, bandwidth use, data dropping ratio, and latency rate and serves as a crucial tool to minimize response rate [27,28].
Since the fundamental objective of sensor nodes in fog-based IoT is to communicate the sensed data towards the intended destination, therefore, secure and efficient routing is a dire requirement to make the entire network secure, safe and reliable from internal as well as external attacks. Moreover, the data is most susceptible to disruption by intruders and even this data can be subverted by malicious/rogue intermediate nodes when sensed facts, figures, or evidence are communicated by participating member nodes to Base Station (BS) or sink node and then subsequently to fog node or cloud server. Rogue/malicious intermediary nodes perform a number of assaults to block the data from getting to its final destination. Examples of possible internal threats to the IoT include black hole attacks, sinkhole attacks, selective forwarding, Sybil attacks, warm hole attacks, and HELLO flood assaults, among others.
The main contribution of this paper aiming at making the entire network safe and secure from malicious internal node attacks, which are based upon trust awareness, is discussed below to detect and expel faulty/malicious nodes from the IoT network.
- The comprehensive trust value of each IoT network is computed which is comprised of direct trust, indirect trust and energy trust value.
- In order to identify and remove malicious nodes as quickly as possible, the volatilization factor has been included in the selection of Cluster Head (CH) to minimize energy utilization and to manage the densely IoT network.
- Aside from this, an enhanced RSA algorithm has also been employed in the proposed paradigm to protect data originality from external attackers.
The remainder of this paper is structured as follows: The relevant work is described in Section 2. Section 3 explains the proposed model of trust-aware security, encryption algorithm and cluster head selection technique. Section 4 shows the simulations with results discussion and finally in Section 5 conclusion is given.
2. Literature Review
A hybrid offline and online encryption approach to implement digital signature and encryption is demonstrated to speed up packet delivery and decrease communications problems in [29]. The high computing complexity and uncertain forms of defendable assaults are mostly its disadvantages. A novel encryption technique utilizing elliptic curve cryptography (ECC) and homomorphic encryption is used to provide the safe transmission of data in the clustering of WSNs [30]. It is used to outline the kinds of assaults, including hello flood, denial-of-service and compromised cluster heads. Still, this approach results in a high incidence of packet loss and a significant delay. The hello flood and selective forwarding attacks are successfully thwarted by creating unique 176-bit keys for each sensor by using the ECC technique to produce binary strings for each sensor and the rate of packet loss and the latency are both decreased in [31]. However, after 1000 rounds of the method, each node’s residual energy fluctuates significantly, which results in uneven energy usage. A better approach is put out to expedite multiuser message broadcasting authentication based on the four components such as system activation, user addition, multiuser broadcast authentication and user revocation to enable safe data transport in RSA [32]. A trust-based drone energy-saving data-collecting strategy to employ the drone path’s quadratic optimization algorithm to identify routing paths is presented in [33]. Additionally, trust inference and evolve procedures are also used to determine the sensor node’s level of trust. As a result, it can efficiently determine an ideal data-gathering route and balance the network’s energy usage. In order to save energy, the Beta Reputation and Direct Trust (BRDT) approach uses the beta and direct trust paradigm for safe and reliable communication in IoT networks [34]. Nevertheless, there are frequently too many cluster heads as a result of the wide communication range overlaps, which a causes lot of energy wastage. Furthermore, BRDT does not specify the defendable assaults. To counter black-hole attacks, Grade Trust, a secured routing system based on the trust levels of nodes, is discussed in [35]. Where only a black-hole attack can be thwarted by Grade Trust, despite an increase in packet delivery ratio. In [36], a secure routing technique based on clustering is implemented an energy-efficient clustering technique to encrypt the data of the network using a trusted hardware module which can successfully fend off several assaults such as data confidence and integrity attacks as well as comparison node attacks. However, the cluster head nodes must have equipment for persistent energy supply which raises the bar for the IoT configuration. A trust-based energy-preserving multi-hop routing system is proposed to combine encryption and a trust management-based protocol [37]. There are some inaccuracies when computing the trust values of neighbor nodes because of indirect trust value calculation. The direct and indirect trust values of nodes as well as the incentive factor, energy trust and quality-of-service (QoS) indicators must be considered to improve the safe routing pathways. Therefore, a lightweight and fast deployable trust-based secure routing protocol (TBSRP) is developed to identify and isolate the misbehaving nodes to minimize the computational complexity of the nodes [38]. Additionally, the TBSRP employs a distributed trust mechanism to dynamically identify malicious nodes and isolate them as soon as feasible. The most trustworthy and quickest routing path is chosen based on the nodes’ trust level and hop count. However, it does not account for nodes’ energy levels when computing their trust levels, which might lead to choosing the next hop from nodes with high trust but low energy. The energy-efficient clustering approach suggested for an IoT network, is a revolutionary and adaptive energy-efficient fuzzy (AEEF) clustering that boosts efficiency by up to 10% and directly impacts longevity [39]. In this study, the author refined the energy distribution method and used fuzzy logic clustering to imitate human reasoning and cognition. Rather than strictly binary cases of truth, fuzzy logic includes 0 and 1 as extreme cases of truth but with various intermediate degrees of truth, both of which have a direct impact on scalability. In particular, the AEEF algorithm presented a Landslide Detection System (LDS), which streamlines routing paths and finds the best routes via sinks to shorten delays and be useful in the event of landslides. The Reliable Cluster Head Selection Technique (RCHST) utilizes Integrated Energy and Trust-based Semi-Markov Prediction (IETSMP) to combine energy and trust parameters as RCHST-IETSMP [40]. This method leverages short-path communication using effective distance to carry out a basic comparison between the interacting sensor nodes of the IoT network and has the ability to aid the user in data processing and sensing. It takes advantage of the Hyper-Erlang process to lengthen a sensor network’s lifespan. The lifespan is a crucial element of an IoT network, whereas the Hyper-Erlang process requires more resources to extend the network’s lifetime. Dynamic directional routing (DDR) is designed for Mobile Wireless Sensor Networks (MWSNs) for effective and reliable routing that anticipates the next opportunity through advanced calculations of a fitness function [41]. Furthermore, it chooses the particular specified search angle that forecasts the total potential candidate for the following hope node. The discovery phase and the data forwarding phase are the two primary aspects of this protocol. It connects certain sophisticated characteristics of prediction with the fundamental Threshold sensitive Low Energy Adaptive Clustering Hierarchy (T-LEACH) structure. Due to the fact that T-LEACH chooses cluster heads at random which has an adverse effect on the algorithm’s overall efficiency, the DDR can only make limited improvements to its prediction, leading to low latency. The vulnerability and system weaknesses that are raised by the expansion of IoT networks have raised many concerns for the research community. Earlier, software-based intrusion detection systems (IDSs) were suggested as a solution to the security issues but over time, it became apparent that there is no clear and defined software methodology for IDSs. In order to extend the longevity and technology, the authors presented a Software Engineering (SE) (https://www.mdpi.com/1424-8220/20/5/1375, accessed on 14 August 2023) based solution for IoT in which three crucial SE phases are utilized as requirements, design and software testing to design the IDS [42]. When IDS is used for an IoT network, this approach performs well in terms of energy usage and network longevity. Since the broadcast design transmits many messages at once, it requires a lot of energy to do so, making it inefficient to implement. The key disadvantage of the suggested method is that complicated designs still require a correct structure to be solved. In order to attain the energy efficiency of IoT networks, the authors presented the Gaussian elimination approach with the Distributed Energy-Efficient Clustering DEEC Gaussian (DEEC Gaussian) in [43]. The Gaussian elimination algorithm is used to increase residual energy and improve optimal energy along with aggregation of IoT operations whereas the DEEC algorithm is used to provide a high-performance level of heterogeneity and achieve energy-efficient clustering that is used to increase the network lifetime in stable ways. Overall, none of the aforementioned encryption techniques, however, cannot successfully fight against assaults initiated from within the IoT network.
The paper introduces an Efficient and Secure Fog-Based Routing Mechanism (ES-FRM) to tackle the vulnerability of Internet of Things (IoT) networks to both internal and external attacks, as well as energy consumption challenges. Each IoT node calculates a comprehensive trust value for the next intermediate node, taking into account direct trust, indirect trust, and energy trust values before forwarding data. By comparing this trust value with a predefined threshold, the system identifies rogue nodes and ensures network protection.
3. Methodology
The proposed methodology is explained in conjunction with the system preliminaries of mathematical models that have been used to get the intended results. For the last several years, it is undeniable that the research aim in IoT is to find the safe, reliable and efficient transmission of data from source to destination. Hence, the proposed work goal is to implement a trust-aware security mechanism to make the data transmission path secure, smooth and seamless. This is accomplished by anticipating the future behavior of the nodes by evaluating their history and excluding compromised nodes that can execute various malicious activities. The proposed methodology is applied in three stages as shown in Figure 1.
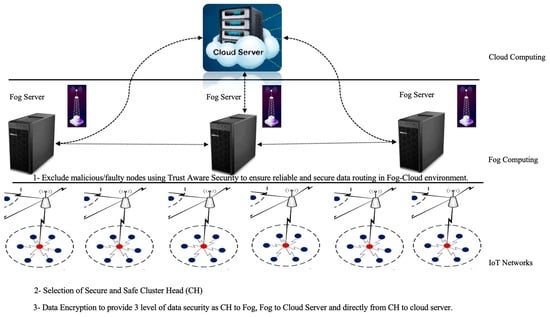
Figure 1.
A block diagram of an IoT network to implement the proposed methodology of Efficient and Secure Fog Based Routing.
The proposed methodology is based on trust-aware security, which has been considered one of the primary requirements for the sensor nodes to take part in data transmission. The comprehensive trust value of every sensor node is calculated through the four parameters such as direct trust value, indirect trust value, energy trust value and volatilization factor. This comprehensive trust value is compared with the predefined threshold comprehensive trust value of every node and if the comprehensive trust value of any node is greater than or equal to the threshold comprehensive trust value, that node is declared as trustworthy otherwise it is notified as a malicious and faulty node. In this proposed paradigm, the IoT is thought to be made up of n sensor nodes spread throughout the m × m square region of interest. Once every node collects data, it transmits to respective cluster head, after which it is passed to a sink node or BS via trustworthy neighbors. Aside from this, the proposed model makes the assumption that all the sensor nodes are supposed to be placed randomly across a 500 × 500 m2 region of interest. All of the nodes are immovable, so once they are installed, they cannot be moved and each node in the IoT has its own unique ID. There are mathematical preliminaries are used to get the results of the proposed methodology which are discussed in the next sub-sections. The unit of trust value would be a dimensionless value expressed on a scale by combining the factors discussed in the above section, just like usage and remaining power of any node and many more. The scale is between 0 to 150 (watt unit of energy) in case of individual calculation and 0 to 300 watts in case of T-comp calculation.
3.1. Trust
The level of confidence that one node has in other nodes is known as the trust. Each node in the wireless sensor network has the ability to determine how trustworthy its neighbors are. Additionally, the term “neighboring nodes” refers to nodes that are situated within the transmission range of that specific node. Hence, calculating the trust value of every neighboring node is a prerequisite for taking part in data transmission, which can be changed over a period of time. Moreover, the node having a trust value higher than other nodes is most likely to be selected as the next data-relaying node.
3.2. Direct Trust
The method of gathering data for trust computation is deemed one of the most crucial elements of trust management schemes. The direct trust value of any node is computed by considering the numerous trust metrics of that particular node in various events of the network. The trust metrics, or the QoS attributes that can be considered are listed in as 0 to 1 [1]. The provided trust metric information for various events is crucial and can help the system’s trust management system for the node to make the right decisions. The direct trust is determined by the sending device itself while taking into account trust parameters. As a result, Equation (1) is used to determine the direct trust value of the nearby nodes so that every node can ascertain the direct trust value of each of its neighbors by using this equation.
The earlier portion of this equation illustrates the historical trust value, and the later part represents the current trust value. Moreover, the variables θ and (1 − θ) are weighting parameters and have been employed to adjust the current and past trust values. The n is very important here which represents the number of nodes participating in an IoT network as the initial and current state of the network, whereas x and y show the coordinates and location of the nodes. In addition to this, the value of θ should be greater than 0 and less than 1 as per the specific application of the IoT network, whereas α1 and α2 are the volatilization factors and have been added to reduce the previous trust values of malicious nodes. Additionally, the symbols Vt and Bt represent the ratios of the total number of received and sent messages, respectively, out of all messages and are calculated using Equation (2).
Equation (2) is used to compute the ratio of received data packets out of all packets of sensor y, whereas Equation (3) is used to calculate the ratio of sent data packets out of all packets.
3.3. Indirect Trust Value
The indirect trust of any node is computed by getting indirect information from the common neighboring nodes. So, Equation (4) has been used in the proposed methodology to calculate the indirect trust value of any node.
As seen in Equation (4), ch is the complete set of shared neighbors that both the trust evaluator nodes and the nodes whose trust is being assessed. Here p represents the total number of common neighbors. Moreover, in order to compute the indirect trust value from any node x to other node y, first of all, direct trust is calculated from node x to common neighbors Ci and subsequently from common neighbors Ci to node y, as illustrated in Equation (4). After calculating the common neighbor node’s direct trust value, it is compared to the threshold direct trust value. If their direct trust value is more than the threshold value or equal to it, it is proclaimed to be a trusted neighbor; otherwise, it is excluded from the list of common trusted neighboring nodes.
3.4. Volatilization Factor
The volatilization factors α1 and α2 have been added to the suggested work in order to quickly remove any sensor nodes that have been transformed from reliable working nodes to potentially dangerous nodes that could endanger the safety of the route, as shown in Equations (5) and (6).
The variables a1 and a2 have been applied to adjust the fluctuations in trust values of environmental factors for flat or geometry-based atmospheres. Additionally, T represents the current time in the network, whereas t stands for the threshold of time. While mod (T, t) has been used to prevent the labeling of numerous lawful nodes that have been deployed in some distant areas but are not taking part in data transfer as malicious nodes.
3.5. Residual Energy
The residual energy Er of a sensor node is the energy that is spent during the transmission and reception of data through the network, and Equation (7) is used to determine the energy trust value of the node [3].
where K is the total number of bits, and Eelec is the electronic energy consumed to receive one bit of data. The total energy for sending the data of node y is calculated using Equation (8).
Here, d0 represents the threshold distance and calculated using Equation (9), Eelec shows the energy utilization in the electronics for sending or receiving one bit. The terms and are amplifier energy consumptions for a short and long-distance transmissions.
is calculated using this formula
If it is supposed that the node y’s initial energy is E0, then its remaining energy is computed via Equation (10).
Finally, Equation (11) is used to calculate the energy trust value of each sensor device.
After calculating energy trust value , it can be deduced that this node can only take part in data transmission if its residual energy is more than or equal to the threshold energy of the node.
3.6. Comprehensive Trust Value
The comprehensive trust value of any node is calculated by adding direct trust, indirect trust and energy trust values of the node as given in Equation (12).
Here the ω1, ω2 and ω3 are the weighting coefficients for direct trust, indirect trust and energy trust values, respectively, and 0 < , , < 1, + + = 1.
3.7. Encryption of Data
A method that solves one of cryptography’s most difficult problems is RSA encryption [2]. The creation of keys for data encryption is the first step in the RSA algorithm. It calls for the use of two prime numbers (S and T), which are determined by primality testing. The prime numbers used in RSA must be extremely large and sufficiently spaced apart. Smaller or closer numbers are much more likely to break. Despite this, the process has been simplified by using smaller digits. S and T are the two prime numbers that are used as key factors, then multiplex factor is given by Equation (13).
Here R is a multiplex key of prime factors that can be scaled using Equation (14).
where λ(R) is the scaling factor that is used to make the key values stable. Now the encryption can be done using Equation (15).
where E represents the final data after encryption, which is known as Cipher text. Here e is the estimated values of the plaintext normally given and m is the mobility of the message that is also initialized at the start.
Finally, the division matrix D of message and data packages is calculated using Equation (16), where d1 is the initial distance between the nodes. This whole mathematical process is shown in Figure 2 to find the appropriate cluster head sensor node, as per its security parameters. Algorithm 1 is used to calculate the overall trust value of an IoT node participating in an IoT network.
| Algorithm 1. The pseudocode for calculating Trust Value |
| Input: Node, Security, Energy Output: Trust value calculation and communication. Trust value of the node: T_Value = (Successful_Trans + Unsuccessful_Trans) / (Trans + Successful_Trans); if (T_Value = adequate for communication); Allow communication with the node. else calculate the trust value for the security model of the node. T_Security = Access Control + Encrypted Packets + Secure Routed Packets; if (T_Security = adequate for communication); Allow communication with the node. else calculate the trust value for the energy consumption if (T_Energy = adequate for communication); Allow communication with the node. else calculate the trust value of mobility. T_Energy = Mobility + Energy_cons; if (T_Mobility = adequate for the communication); Allow the communication. else calculate the trust for the node in the reliability model. T = SentData + Energy; if (T = adequate for communication); Allow communication; else calculate the overall trust for the node. Overall_Trust=T_Value + T_Security + T_Energy+T_Mobility; if (Overall_Trust = adequate for communication); Allow the communication. else Deny communication with the node. end. |
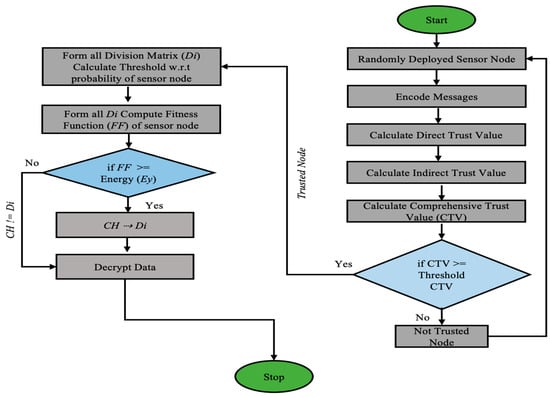
Figure 2.
The mathematical implementation of Efficient and Secure Fog Based Routing in IoT network.
4. Results and Discussion
To check the performance of the proposed secure and efficient fog-based routing mechanism for IoT networks, it has to be understood that the data must not be intercepted by any hostile nodes as it travels from source to destination. Therefore, to ensure secure data communication for all participating nodes they must not carry out any attacks, such as black hole attacks, flood attacks, sinkhole attacks etc. Energy preservation is also considered the most important factor for any IoT network during all this communication to enhance the network lifespan. For this purpose, the proposed technique implemented the clustering technique, which is to produce clusters aiming to save the energy of a sensor node. Hence, the data received by the intended node must be the same as the sent. This implies that there must not be any intrusion or alteration by any attackers in packets on their way to the destination. The proposed methodology was simulated using the parameters as shown in Table 1. The overall results are compared on the basis of comprehensive trust values, encoding and decoding of packets at three different levels such as from CH to Fog, Fog to Cloud and directly from CH to Cloud in the following sub-sections.

Table 1.
The simulation parameters of Efficient and Secure Fog Based Routing in IoT network.
4.1. Direct Trust, Indirect Trust and Comprehensive Trust
The direct trust value for every node denoted by T1 is computed using various availability metrics such as the node’s packet forwarding history, packet delay, residual energy, reputation, etc. Next, the indirect trust value T2 is derived using the recommendations of the shared neighbors, as shown in Figure 3. The direct trust and indirect trust values are first calculated and combined with weighting variables to provide a comprehensive trust value, which is represented as a T-comp against each node. Due to the drop in their earlier trust values as well as in the ratio of delivered data packets because of volatilization factors, the comprehensive trust values of hostile nodes executing black hole attacks are significantly lowered, as shown in Figure 3.
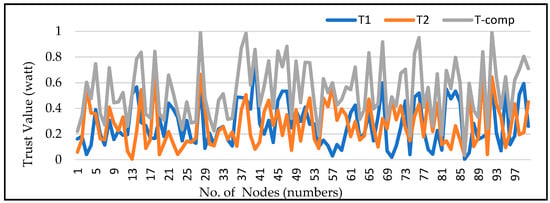
Figure 3.
IoT Network of 100 Sensor Node.
Additionally, due to the hello flood attack, the volatilization factor causes the value of received data packets of faulty nodes to become zero, which pushes the node’s overall comprehensive trust value below the threshold comprehensive trust values. Moreover, the comprehensive trust values of nodes launching selective forwarding and sinkhole attacks are also lowered than the threshold comprehensive trust value. As a result, the route would become safe and secure since all nodes whose comprehensive trust value appears below the threshold would be disqualified for data transfer.
4.2. Comparison of Comprehensive Trust Values
Figure 4 explains the comparison of the comprehensive trust value of the proposed Efficient and Secure Fog Based Routing Mechanism (ESFRM) and Trust-aware Secure Routing Protocol (TSRP) approach by putting the intended parameter values. The results show that the ESFRM is providing 16.44% better results than TSRP.
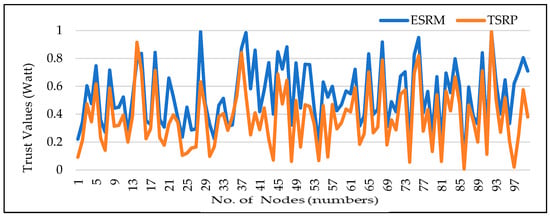
Figure 4.
Comparison of Comprehensive Trust Value.
4.3. Encoding of Data from CH to Fog Nodes
The encoding of data when it travels from the cluster head to the fog node is shown in Figure 5. The data packets are encrypted so that no one can intercept them and compromise their integrity. The lower curve shows the values of the original data denoted by (xd), and the red upper curve denoted by (encode) shows the data when it has been encrypted.
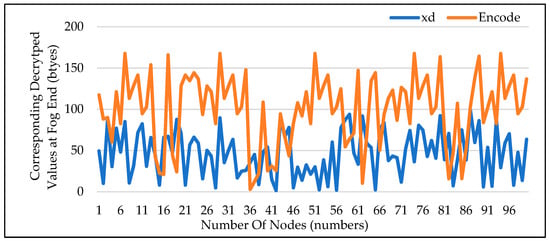
Figure 5.
Encoding from CH to Fog Node.
4.4. Decoding of Data at Fog End
When data reaches the fog node, Figure 6 shows how it is decoded. The decryption key is used to decode the data at the fog node, where it will be quickly processed before being sent to the cloud server. As can be seen, the original data values are the same even though the curves are displaced as a result of mixing the decryption key. The original content is the same as was sent by the source.
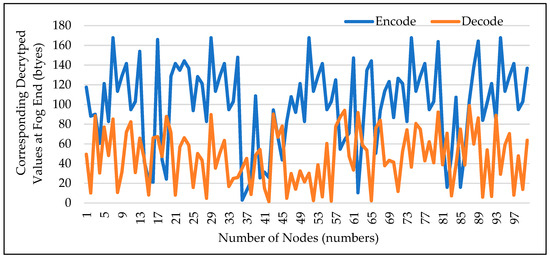
Figure 6.
Decoding from CH to Fog Node.
4.5. Encoding of Data from Fog Node to Cloud Server
Figure 7 shows how data is encrypted as it travels from a fog node to a cloud server. Data is transported to the cloud for further processing and long-term storage after having briefly processed here at the fog node because the cloud server is where the data will ultimately reside. The bottom curve represented by (yd) in this figure shows the original decoded data values. When the data is encrypted using an encryption key, the original values are displaced as a result of the encryption key. Values of the encrypted data are represented by the upper curve.
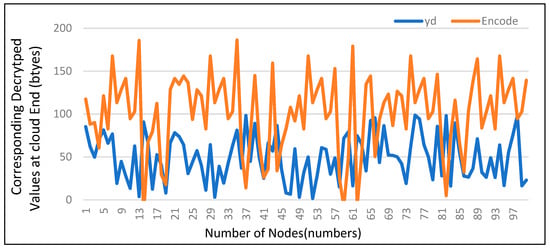
Figure 7.
Encoding from Fog Node to Cloud Server.
4.6. Decoding of Data at Cloud Server
The decoding of data after it reaches the cloud server is described in Figure 8. The integrity of the data stays the same when it is decrypted using the decryption key at the cloud end, demonstrating that it was not altered on the way to the cloud server.
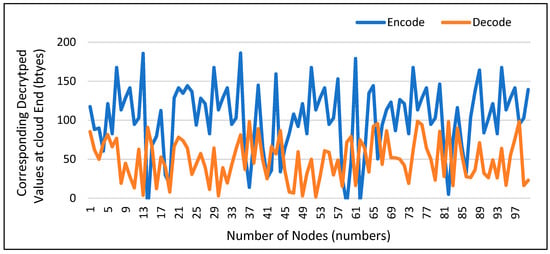
Figure 8.
Decoding of Data at Cloud Server.
4.7. Data Encoding Directly from CH to Cloud Server
In contrast to the (SEFR) study, the encryption of data directly from cluster head to cloud server is also implemented in proposed paradigm. In Figure 9, (zd) with blue curve shows the original data at cluster head, and the red curve explains the encrypted data when the encryption key is applied.
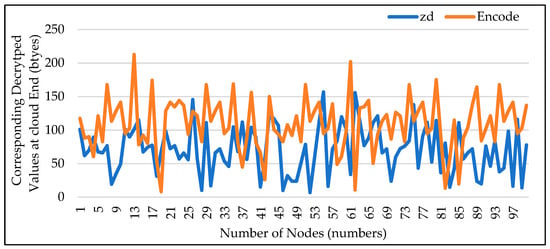
Figure 9.
Data Encoding from CH to Cloud Server.
4.8. Data Decoding from CH to Cloud Server
Figure 10 illustrates how data is decoded when it is received straight from the CH to the cloud end. In this case, the data is thoroughly processed after being decrypted using the decryption key. Additionally, it can be seen that when the data is decrypted, the original content of the data is preserved, which serves as the primary protection against outsiders accessing the data’s original values.
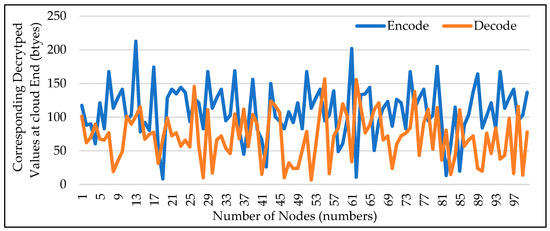
Figure 10.
Decoding of Data for Direct Transmission at Cloud End.
4.9. Two Way Energy Utilization
Figure 11 shows the two-way energy utilization of sensor nodes during the transmission of sensed data from CH to fog nodes and subsequently to the cloud server. This image shows how much energy is used from the CH to the fog node in S1 and the energy used from the fog nodes to the cloud server in S2. The results explain that communication of data from CH to the fog node consumed more energy because of no processing, filtering and refining of data here at the initial stage after being sensed. Additionally, when data reaches a fog node, it is refined and processed, appropriate computations are conducted, and operations are prompted here rather than transmitting the complete data set to the cloud server. Because of this, only the data that is not currently needed is transferred to the cloud server for processing and storage. As a result, sending data from a fog node to the cloud server, represented by S2 in the above diagram, uses less energy on average.
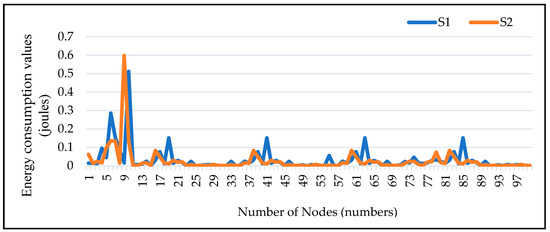
Figure 11.
Energy Consumption of 2- Way Transmission.
4.10. Energy Consumption for Direct Transmission from CH to Cloud Server
Figure 12 shows how much energy is utilized when data is transferred straight from a CH to a cloud server without the use of any between nodes. The idea is that data is sent directly to the cloud server in this case rather than the fog node, which, on average, uses more energy as shown in the figure. This is because it is obvious that without an intermediate relaying node, more energy from the source node is used to send the data to the cloud server.
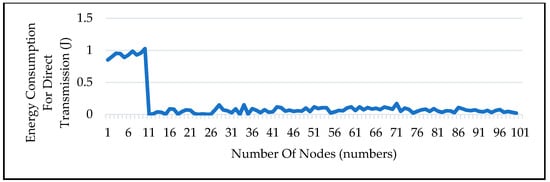
Figure 12.
Energy Consumption from CH to Cloud Server.
4.11. Energy Consumption Comparison between Proposed and Base Study
The energy usage comparison between the suggested paradigm (ESFRM) and the (SEFR) is shown in Figure 13. As a result, it is demonstrated that the proposed study used an average of 13.67% less energy than that of the based technique when applying intended parameter values.
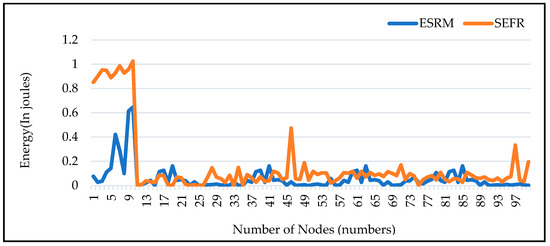
Figure 13.
Energy Consumption Comparison between Proposed and Base Study.
4.12. 2-Way and Direct Transmission Rate of Nodes
Figure 14 shows the data transmission rate of all the network participants from the CH to fog, the fog node to the cloud server, as well as directly from CH to the cloud server. The average rate is more effective in two-way communication than in direct transmission, as can be observed because in two-way transmission, data is not intended to go as far as it does in direct transmission. Data is transmitted from the CH to the fog node, and then from the fog node to the cloud server. We receive a better transmission rate as a result.
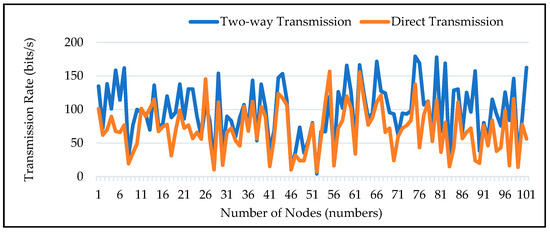
Figure 14.
Transmission Rate of Nodes for Two Way Transmission and DT.
4.13. Overall Threshold Comparison between ESRM and TSRP
The comparison of the overall threshold values between the suggested and the base research is shown in Figure 15. These threshold values indicate how many data packets are transferred in a given amount of time. The proposed technique is showing results that are 16% better than the TSRP as the number of nodes grows.
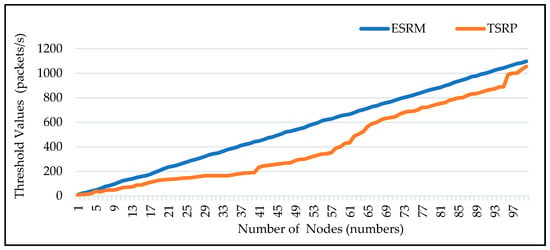
Figure 15.
Transmission Rate of Nodes for Two Way Transmission and DT.
The comprehensive trust value of each node is evaluated and compared against a predefined threshold to determine whether it should be categorized as a rogue node or a suitable normal node. To enhance data security during transmission, an advanced RSA algorithm is employed, safeguarding data as it moves from the Cluster Head (CH) to fog nodes, from fog nodes to the cloud server, and even directly from CH to the cloud server. Additionally, the protocol utilizes a clustering technique to ensure efficient Cluster Head selection. Extensive simulations demonstrate that the proposed Enhanced Secure Fog-based Routing Mechanism (ESFRM) surpasses the performance of the Trust-Based Secure Routing Protocol (TSRP) by achieving a 16.44% higher malicious nodes detection rate. Furthermore, ESFRM exhibits a remarkable energy efficiency advantage, consuming approximately 13.67% less energy compared to the Secure Energy-efficient Fog-based Routing (SEFR) protocol.
5. Conclusions
Due to the uncertain and rapidly changing behavior of the sensor nodes, energy-efficient and reliable routing remained a great matter of concern in resource-constrained-fog-based IoT networks. Therefore, this paper proposes Energy Efficient and Secure Fog Based Routing Mechanism (ESFRM) to defend against various internal as well as external attacks. The main purpose of ESFRM is to identify the malicious and faulty internal nodes as soon as possible to prevent them from disrupting the normal transmission of data from source to destination node. For this purpose, comprehensive trust value is computed which encompasses the volatilization factor in addition to direct trust, indirect trust and energy trust values. The comprehensive trust value of every node is compared with the threshold comprehensive trust value to decide whether it is a rogue node or an appropriate normal node. Moreover, an enhanced RSA algorithm has been utilized to prevent unauthorized access when data is traveled from CH to fog node, fog node to cloud server and directly from CH to cloud server in addition to clustering technique for the sake of efficient CH selection. The simulation results show that the malicious nodes detection rate of the proposed ESFRM is 16.44% higher than TSRP and it utilizes, on average, 13.67% less energy than SEFR. In the future, the proposed methodology can be implemented and extended within the IDS to secure the IoT network from internal as well as external attacks.
Author Contributions
Conceptualization, T.S.M. and J.T.; Data curation, M.R.M.; Formal analysis, S.A. and M.R.M.; Funding acquisition, A.K.; Investigation, S.A.; Methodology, T.S.M., J.T. and H.A.; Supervision, A.K.; Writing—original draft, T.S.M., S.A. and H.A.; Writing—review & editing, M.R.M. and A.K. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Data is contained within the article.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Taherdoost, H. Security and Internet of Things: Benefits, Challenges, and Future Perspectives. Electronics 2023, 12, 1901. [Google Scholar] [CrossRef]
- Yang, G. An Overview of Current Solutions for Privacy in the Internet of Things. Front. Artif. Intell. 2022, 5, 812732. [Google Scholar] [CrossRef] [PubMed]
- Matin, M.A.; Islam, M.M. Overview of Wireless Sensor Network; IntechOpen: London, UK, 2023; pp. 4–6. Available online: https://www.intechopen.com/books/wireless-sensor-networks-technology-and-protocols/overview-of-wireless-sensor-network (accessed on 21 June 2023).
- Sreejith, V.R.; Surve, N.; Vyas, K.R.; Gudino, L.J. Area based routing protocol for mobile wireless sensor networks. Int. Conf. Inf. Netw. 2018, 2018, 782–786. [Google Scholar]
- Prathusha, B.L.; Chilambuchelvan, A. GSR: Geographic Secured Routing using SHA-3 algorithm for node and message authentication in wireless sensor networks. Future Gener. Comput. Syst. 2017, 76, 98–105. [Google Scholar] [CrossRef]
- Alromih, A.; Al-Rodhaan, M.; Tian, Y. A Randomized Watermarking Technique for Detecting Malicious Data Injection Attacks in Heterogeneous Wireless Sensor Networks for Internet of Things Applications. Sensors 2018, 18, 4346. [Google Scholar] [CrossRef]
- Sarma, H.K.D.; Kar, A.; Mall, R. A Hierarchical and Role Based Secure Routing Protocol for Mobile Wireless Sensor Networks. Wirel. Pers. Commun. 2016, 90, 1067–1103. [Google Scholar] [CrossRef]
- Selvi, M.; Thangaramya, K.; Ganapathy, S.; Kulothungan, K.; Khannah Nehemiah, H.; Kannan, A. An Energy Aware Trust Based Secure Routing Algorithm for Effective Communication in Wireless Sensor Networks. Wirel. Pers. Commun. 2019, 105, 1475–1490. [Google Scholar] [CrossRef]
- Rajeshkumar, G.; Valluvan, K.R. An Energy Aware Trust Based Intrusion Detection System with Adaptive Acknowledgement for Wireless Sensor Network. Wirel. Pers. Commun. 2017, 94, 1993–2007. [Google Scholar] [CrossRef]
- Yu, X.; Li, F.; Li, T.; Wu, N.; Wang, H.; Zhou, H. Trust-based secure directed diffusion routing protocol in WSN. J. Ambient. Intell. Humaniz. Comput. 2022, 13, 1405–1417. [Google Scholar] [CrossRef]
- Sun, Z.; Wei, M.; Zhang, Z.; Qu, G. Secure Routing Protocol based on Multi-objective Ant-colony-optimization for wireless sensor networks. Appl. Soft Comput. J. 2019, 77, 366–375. [Google Scholar] [CrossRef]
- Qiuwei, Y.; Xiaogang, Z.; Hongjuan, F.; Xiqiang, C. Survey of Security Technologies on Wireless Sensor Networks. J. Sens. 2015, 2015, 842392. [Google Scholar] [CrossRef]
- Kesavan, V.T.; Radhakrishnan, S. Cluster based secure dynamic keying technique for heterogeneous mobile Wireless Sensor Networks. China Commun. 2016, 13, 178–194. [Google Scholar] [CrossRef]
- Alghamdi, T.A. Secure and energy efficient path optimization technique in wireless sensor networks using dh method. IEEE Access 2018, 6, 53576–53582. [Google Scholar] [CrossRef]
- Bilgin, B.E.; Baktir, S. A light-weight solution for blackhole attacks in wireless sensor networks. Turk. J. Electr. Eng. Comput. Sci. 2019, 27, 2557–2570. [Google Scholar] [CrossRef]
- Karlof, C.; Wagner, D. Secure routing in wireless sensor networks: Attacks and countermeasures. In Proceedings of the 1st IEEE International Workshop on Sensor Network Protocols and Applications SNPA 2003, Anchorage, AK, USA, 11 May 2003; pp. 113–127. [Google Scholar] [CrossRef]
- Perrig, A.; Szewczyk, R.; Tygar, J.D.; Wen, V.; Culler, D.E. SPINS: Security protocols for sensor networks. Wirel. Netw. 2002, 8, 521–534. [Google Scholar] [CrossRef]
- Shaikh, R.A.; Lee, S.; Khan, M.A.U.; Song, Y.J. LSec: Lightweight security protocol for distributed wireless sensor network. In Personal Wireless Communications; PWC 2006. Lecture Notes in Computer Science, 4217; Springer: Berlin/Heidelberg, Germany, 2006. [Google Scholar] [CrossRef]
- Zhang, Y.; Liu, W.; Lou, W.; Fang, Y. Location-based compromise-tolerant security mechanisms for wireless sensor networks. IEEE J. Sel. Areas Commun. 2006, 24, 247–260. [Google Scholar] [CrossRef]
- Abdelhakim, M.; Lightfoot, L.E.; Li, T. Reliable data fusion in wireless sensor networks under Byzantine attacks. In Proceedings of the MILCOM 2011 Military Communications Conference, Baltimore, MD, USA, 7–10 November 2011; pp. 810–815. [Google Scholar]
- Saidi, A.; Benahmed, K.; Seddiki, N. Secure cluster head election algorithm and misbehavior detection approach based on trust management technique for clustered wireless sensor networks. Ad Hoc Netw. 2020, 106, 102215. [Google Scholar] [CrossRef]
- Hong, Z.; Shao, Q.; Liao, X.; Beyah, R. A secure routing protocol with regional partitioned clustering and Beta trust management in smart home. Wirel. Netw. 2019, 25, 3805–3823. [Google Scholar] [CrossRef]
- Fang, W.; Zhang, W.; Chen, W.; Liu, Y.; Tang, C. TMSRS: Trust management-based secure routing scheme in industrial wireless sensor network with fog computing. Wirel. Netw. 2020, 26, 3169–3182. [Google Scholar] [CrossRef]
- Isaac Sajan, R.; Jasper, J. Trust-based secure routing and the prevention of vampire attack in wireless ad hoc sensor network. Int. J. Commun. Syst. 2020, 33. [Google Scholar] [CrossRef]
- Fang, W.; Zhang, W.; Chen, W.; Liu, J.; Ni, Y.; Yang, Y. MSCR: Multidimensional secure clustered routing scheme in hierarchical wireless sensor networks. Eurasip J. Wirel. Commun. Netw. 2021, 2021, 14. [Google Scholar] [CrossRef]
- Shaheen, Q.; Shiraz, M.; Butt, S.A.; Gani, A.; Khan, M.A. An analytical survey of wsns integration with cloud and fog computing. Electronics 2021, 10, 2625. [Google Scholar] [CrossRef]
- Bhargava, K.; Ivanov, S. A fog computing approach for localization in WSN. In Proceedings of the 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Montreal, QC, Canada, 8–13 October 2017; pp. 1–7. [Google Scholar]
- Pradeepa, M.A.M.; Gomathi, B. Towards Fog Computing based Cloud Sensor Integration for Internet of Things. Int. J. Comput. Sci. Eng. Commun. 2017, 5, 1761–1773. [Google Scholar]
- Senthil kumaran, U.; Ilango, P. Secure authentication and integrity techniques for randomized secured routing in WSN. Wirel. Netw. 2015, 21, 443–451. [Google Scholar] [CrossRef]
- Elhoseny, M.; Elminir, H.; Riad, H.; Yuan, X. A secure data routing schema for WSN using Elliptic Curve Cryptography and homomorphic encryption. J. King Saud Univ.—Comput. Inf. Sci. 2016, 28, 262–275. [Google Scholar] [CrossRef]
- Elamurugu, V.; Evanjaline, D.J. An Efficient and Secure Text Encryption Scheme for Wireless Sensor Network (WSN) Using Dynamic Key Approach. Int. J. Comput. Netw. Appl. 2021, 8, 788–794. [Google Scholar] [CrossRef]
- Bashirpour, H.; Bashirpour, S.; Shamshirband, S.; Chronopoulos, A. An Improved Digital Signature Protocol to Multi-User Broadcast Authentication Based on Elliptic Curve Cryptography in Wireless Sensor Networks (WSNs). Math. Comput. Appl. 2018, 23, 17. [Google Scholar] [CrossRef]
- Jiang, B.; Huang, G.; Wang, T.; Gui, J.; Zhu, X. Trust based energy efficient data collection with unmanned aerial vehicle in edge network. Trans. Emerg. Telecommun. Technol. 2020, 3. [Google Scholar] [CrossRef]
- Priayoheswari, B.; Kulothungan, K.; Kannan, A. Beta reputation and direct trust model for secure communication in wireless sensor networks. In Proceedings of the International Conference on Informatics and Analytics, Pondicherry, India, 25–26 August 2016; Volume 25. [Google Scholar]
- Airehrour, D.; Gutierrez, J.; Kumar Ray, S. GradeTrust: A secure trust-based routing protocol for MANETs. In Proceedings of the 2015 International Telecommunication Networks and Applications Conference (ITNAC), Sydney, Australia, 18–20 November 2015; pp. 65–70. [Google Scholar]
- Wang, T.; Zhang, G.; Yang, X.; Vajdi, A. A trusted and energy efficient approach for cluster-based wireless sensor networks. Int. J. Distrib. Sens. Netw. 2016, 12. [Google Scholar] [CrossRef]
- Raza, S.; Haider, W.; Durrani, N.M.; Khan, N.K.; Abbasi, M.A. Trust based energy preserving routing protocol in multi-hop WSN. Lect. Notes Comput. Sci. 2015, 9466, 518–523. [Google Scholar]
- Ahmed, A.; Abu Bakar, K.; Channa, M.I.; Haseeb, K. Countering Node Misbehavior Attacks using Trust Based Secure Routing Protocol. TELKOMNIKA 2015, 13, 260. [Google Scholar] [CrossRef]
- Ahmed, S.; Gupta, S.; Suri, A.; Sharma, S. Adaptive energy efficient fuzzy: An adaptive and energy efficient fuzzy clustering algorithm for wireless sensor network-based landslide detection system. IET Netw. 2021, 10, 1–12. [Google Scholar] [CrossRef]
- Famila, S.; Jawahar, A.; Vimalraj, S.L.S.; Lydia, J. Integrated Energy and Trust-Based Semi-Markov Prediction for Lifetime Maximization in Wireless Sensor Networks. Wirel. Pers. Commun. 2021, 118, 505–522. [Google Scholar] [CrossRef]
- Almesaeed, R.; Jedidi, A. Dynamic directional routing for mobile wireless sensor networks. Ad Hoc Netw. 2021, 110, 102–120. [Google Scholar] [CrossRef]
- Almomani, I.; Alromi, A. Integrating software engineering processes in the development of efficient intrusion detection systems in wireless sensor networks. Sensors 2020, 20, 5. [Google Scholar] [CrossRef]
- Aroba, O.J.; Naicker, N.; Adeliyi, T. A Hyper-Heuristic Heterogeneous Multisensor Node Scheme for Energy Efficiency in Larger Wireless Sensor Networks Using DEEC-Gaussian Algorithm. Mob. Inf. Syst. 2021, 2021. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).