Abstract
The Internet of Things (IoT) has experienced significant growth and is now a fundamental part of the next-generation Internet. Alongside improving daily life, IoT devices generate and collect vast amounts of data that can be leveraged by AI-enabled big data analytics for diverse applications. However, due to the machine-to-machine communication inherent in IoT, ensuring data security and privacy is crucial to mitigate various malicious cyber attacks, including man-in-the-middle, impersonation, and data poisoning attacks. Nevertheless, designing an efficient and adaptable IoT security framework poses challenges due to the limited computational and communication power of IoT devices, as well as their wide-ranging variety. To address these challenges, this paper proposes an Access Key Agreement (AKA) scheme called the “Reliable Device-Access Framework for the Industrial IoT (RDAF-IIoT)”. RDAF-IIoT verifies the user’s authenticity before granting access to real-time information from IIoT devices deployed in an industrial plant. Once authenticated at the gateway node, the user and IIoT device establish a session key for future encrypted communication. The security of the proposed RDAF-IIoT is validated using a random oracle model, while the Scyther tool is employed to assess its resilience against various security attacks. Performance evaluations demonstrate that the proposed scheme requires lower computational and communication costs compared to related security frameworks while providing enhanced security features.
MSC:
94A60
1. Introduction
The Industrial Internet of Things (IIoT) is an emerging technology rapidly changing manufacturing and industrial terrain. IIoT leads to intermixing sensors, software, and other technologies into industrial processes to optimize and automate them [1,2,3]. With IIoT, devices and equipment are connected to the Internet, enabling them to intercommunicate real-time data and insights. This connectivity facilitates factories to monitor and examine their production processes, determine inefficiencies, and make data-driven decisions to improve their operations. The advantages of IIoT are myriad. IIoT can enable manufacturers to diminish expenses and enhance productivity by enhancing operational efficiency. In addition, IIoT also improves product quality, reducing downtime and enhancing worker safety [4,5,6].
With the integration of various devices, sensors, and systems, the Industrial Internet of Things (IIoT) presents numerous potential attack vectors that malicious actors can exploit. Among the primary concerns is the security of data. The vast amount of data generated by IIoT systems needs to be collected, processed, and stored securely. Unauthorized access to this data can have severe consequences, leading to significant economic and reputational damage. To mitigate these risks, robust security measures, including encryption and authentication, must be implemented in IIoT environments. In this paper, we propose an authentication and key agreement (AKA) scheme called “reliable device-access framework for the Industrial IoT (RDAF-IIoT)” to enable secure access to real-time information from devices deployed in IIoT environments. The proposed RDAF-IIoT scheme prioritizes computational efficiency by leveraging hash functions and symmetric encryption instead of computationally expensive operations.
2. Related Work
Within the existing literature, numerous AKA schemes or frameworks have been suggested to ensure secure access to real-time data for users. In this context, the authors of [7] introduced an AKA security framework for wireless sensor networks (WSNs) utilizing a hash function and XOR operation. Furthermore, they identified vulnerabilities in the scheme proposed by [8], including insider attacks, random parameters leakage (RPL), and perfect forward secrecy attacks. Another AKA framework for WSNs was proposed by the authors of [9], incorporating elliptic curve cryptography (ECC), hash function, and XOR. However, this framework is susceptible to man-in-the-middle (MITM), insider attacks, stolen smart card attacks, and RPL attacks. The authentication framework presented in [10] exhibits weaknesses against RPL, stolen smart cards, and password-guessing attacks. In the realm of IoT-enabled software-defined networks, an authentication framework using the symmetric encryption algorithm AES and ECC is proposed in [3]. The security of this scheme is validated using the random oracle model (ROM) and Scyther. Additionally, a user AKA scheme for WSNs based on symmetric encryption and ECC is devised in [11], with its security verified through ROM and AVISPA. However, the AKA scheme put forth in [11] can be compromised by malicious but valid users of the system. For the Internet of drones, a user authentication framework is provided in [12], designed using ECC and authenticated encryption. The security of this framework is demonstrated through Scyther and ROM. Similarly, an authenticated encryption and hash function-based AKA scheme is proposed in [2,13] for smart home and IIoT environments, with its security verified using ROM and Scyther. Lastly, an AKA scheme based on hyper-ECC is proposed in [14] for the Internet of drones environment.
In [15], a robust authentication scheme for WSNs based on temporal credentials is proposed. However, the AKA scheme presented in [16], which utilizes ECC and a hash function, exhibits weaknesses against denial-of-service (DoS), key compromise, and impersonation attacks. Similarly, ref. [17] introduces a multifactor AKA scheme employing AES and a hash function. Nevertheless, this scheme is vulnerable to DoS, replay, and de-synchronization attacks. In [18], a three-party AKA framework is proposed, but it lacks adequate user anonymity protection and does not offer an efficient method for password change. An anonymous AKA scheme constructed using the chaotic map and hash function is presented in [19], with its security validated using the Burrows–Abadi–Needham (BAN) logic model. However, vulnerabilities exist in an AKA scheme utilizing ECC and a hash function for the cloud-enabled IoT environment, as noted in [20]. The scheme involves four participants during the AKA phase and undergoes security validation using BAN logic and AVISPA. Furthermore, [12] proposes an AKA scheme based on AEAD and a hash function, and its security is demonstrated through ROM and Scyther. Lastly, an AKA scheme utilizing a hash function is presented in [21], which is susceptible to various security attacks, as highlighted in [20].
A secure AKA scheme based on ECC and a secure hash function is introduced in [22] for the IoT environment. The scheme’s security is validated using Scyther. However, the security framework proposed in [23], which utilizes ECC and a secure hash function, is vulnerable to stolen smart card attacks. Additionally, the security framework proposed in [24] fails to prevent DoS attacks, while the scheme presented in [25] is weak against DoS attacks as well. In the context of the IIoT environment, an AKA security framework is proposed in [17], but it is unable to withstand various security attacks. The scheme in [17] is constructed using symmetric encryption and a hash function. Various security frameworks are summarized in Table 1.

Table 1.
Summary of User Authentication Frameworks.
2.1. Research Contributions
The main contributions of the paper are listed as follows.
- In this article, an AKA framework is proposed called RDAF-IIoT, which is constructed using “Advanced Encryption Standard in Cipher Block Chaining mode (AES-CBC)” and hash function. RDAF-IIoT enables users to achieve authentication with a gateway. In addition, RDAF-IIoT enables users and sensing devices to communicate securely after establishing a secure channel (session key) with the assistance of a gateway. RDAF-IIoT is a three-factor AKA security framework, which also enables the users to change the password without involving the gateway.
- The proposed RDAF-IIoT is corroborated informally to validate its resiliency against various security attacks, such as DoS, MITM, impersonation, and replay attacks. The security of the session key is corroborated using well known random oracle model. In addition, RDAF-IIoT is implemented using Scyther, and the analysis of Scyther shows that the RDAF-IIoT is secure.
- To evaluate the performance of the proposed RDAF-IIoT, RDAF-IIoT is compared with the state-of-the-art security frameworks, such as Srinivas et al. [35], Challa et al. [25], Wazid et al. [34], and Irshad et al. [3] regarding communication and computational costs. The proposed RDAF-IIoT requires [74.73% to 78.63%] low computational and [30.38% to 51.91%] low communication costs while rendering enhanced security functions than the related security frameworks.
2.2. Paper Organization
The remaining paper is organized as follows. Section 3 explicates the models, such as authentication and attack, used in the construction of the RDAF-IIoT. Section 4 provides the explanation of RDAF-IIoT. In Section 5, the informal, ROM, and Scyther-based security analyses are presented. Performance comparison is presented in Section 6. Concluding remarks are explicated in Section 7.
3. System Models
3.1. Authentication Model
The authentication model comprises the following components. Figure 1 shows the authentication model employed for the proposed RDAF-IIoT.
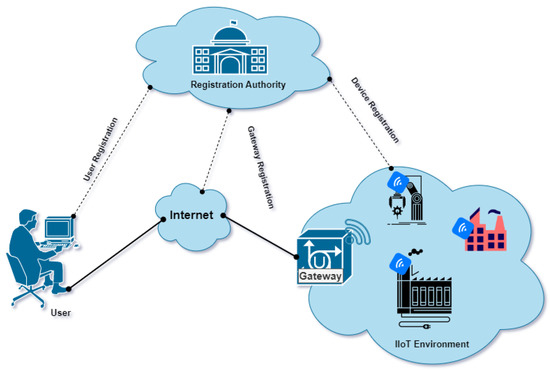
Figure 1.
Smart IIoT environment.
Gateway: : The registration authority (RA) is liable for registering gateway nodes (), and equips Internet functionality to the IIoT-enabled devices stationed in the IIoT circumstances. In addition, keeps the private credentials associated with the users and sensing devices. The can connect the users through cellular and other internet connectivity.
Smart Sensing Node: (): All are equipped with sensing, storage, and processing modules; however, these resources are constricted. In addition, are the resource-constricted devices employed to sense the surrounding IIoT environment. can communicate with using wireless communication protocols, such as WiFi/6LoWPAN/Zigbee communication protocols. Using these wireless channels, sends the collected information to .
User: : has the smart devices (), fitted with the biometric sensor. can intercommunicate with through and with using cellular communication technology or wired network. mandates obtaining the real-time data from stationed in the IIoT environment. Thus, a secure channel establishment scheme is proposed for the IIoT environment to prevent authorized information access in this paper. Table 2 demonstrates the various symbols employed in this paper.

Table 2.
Notations Used in RDAF-IIoT.
3.2. Attack Model
The “Dolev–Yao (DY) model” [14,44,45] is repeatedly employed to investigate the security of AKA schemes. According to DY Model, the attacker can effectuate the MITM and impersonation attacks by capturing and modifying all the communication in the AKA schemes. An attacker can obtain a valid user’s identity for the traceability attack. In addition, in the registration procedure, the RA and other participants interact with each other via a secure channel. However, , , and communicate using the insecure channel while executing AKA process. The “Canetti–Krawczyk (CK) model”, which constructs additional noteworthy speculation than the DY model, is also contemplated. A malicious adversary can procure secure data incorporating the master key, session private credentials, and private key, employing the CK model.
4. The Proposed RDAF-IIoT Framework
The RDAF-IIoT comprises the registration of sensing device, user, and AKA phases. All the phases are explicated in detail in the following subsections.
4.1. Registration of Sensing Device
In this phase, the registration of the sensing device is performed. RA is responsible for the registration of the sensing device by executing the following procedure.
4.1.1. Step RDS-1
The RA selects a unique identity and long-term secret key for the gateway.
4.1.2. Step RDS-2
The RA selects the unique identity for the sensor device and computes the secret key for the sensing device as . Finally, RA stores the parameters {, } in the memory of the sensing device.
4.2. Registration User
In this phase, RA registers a user before allowing him/her to access the resource of the IIoT environment. For the registration of the user, RA executes the following steps.
4.2.1. Step RU-1
The user generates as random number , unique identity , and password . In addition, has a smart device capable of sensing the biometric information of . After sensing , computes
In Equation (1), the biometric key and helper data is computed by taking as the input parameter. The encryption key is computed in (2). In addition, , , and are computed by taking the , , and as the input parameters. Finally, derives the verification parameter in (5).
4.2.2. Step RU-2
Moreover, selects a unique pseudo identity and sends the credentials {, } to using the secure channel. stores the parameters {, } in its own database. In response, sends the parameters, such as the list of the devices and , to using a secure channel.
Remark 1.
In this paper, the fuzzy extractor (FE) is employed to derive the biometric key from the biometric information of the user. FE is the combination of two functions; one is a generator function dented by , and the other is a reproduction function . function takes the and generate the biometric key and helper data. Moreover, the function is used to reproduce the biometric key by taking the helper data and . To reproduce the biometric key the condition , where is the error tolerance and is the hamming distance.
4.2.3. Step RU-3
, on receiving these parameters computes,
By performing the XOR operation between and , the variable is obtained. Similarly, is obtained by performing XOR between and . Subsequently, stores the parameters {, , , , , , } in its own database.
4.3. Authenticated Key Agreement Phase
In this phase, the user and sensor node establish a session key during the execution of AKA phase. For this purpose, the following steps are executed in AKA phase.
4.3.1. Step AKA-1
inserts its secret credentials, such as the identity and at the available interface of the smart device of the user . In addition, imprints the biometric impression on the biometric sensor deployed at and computes
Equation (8) computes the biometric key using the input parameters and , while Equation (9) calculates the encryption key for achieving encryption. Additionally, the initialization vector is determined in Equation (10). By following the encryption process outlined in Equation (11), the credentials, namely , , and , can be obtained using , , and as the input parameters. To authenticate the user’s secret credentials locally, the verification parameter is computed in Equation (12) and validated in Equation (13). If the condition in Equation (13) is satisfied, / derives the parameters from , , , and as indicated in Equations (14) and (15).
picks randomly and timestamps , and computes
Equation (16) calculates the initialization vector, which plays a role in the encryption process. The encryption process itself is executed in Equation (17), utilizing the symmetric key . Furthermore, Equation (18) computes the verification parameter, which is employed to ensure data integrity. Lastly, constructs the message : and transmits it to through the open communication channel.
4.3.2. Step AKA-2
validates the timeliness of the received message by checking the condition , where represents the delay time, is the generation time, and is the received time of the message. If the message passes the validity check, proceeds to verify and . If there is no match found, terminates the AKA process. Otherwise, it retrieves the parameter and performs further computations.
The initialization vector is computed in (19), which is used in the decryption process. In addition, from the decryption process, obtains the plaintext and and computes the verification parameter in (21). Finally, to ensure the integrity of the received message, corroborates the condition in (22). If the condition does not hold, stops the AKA process.
4.3.3. Step AKA-3
generates , and pick new and computes
Here, in (23), the plaintext is computed, and it will be encrypted using the encryption key derived in (24). In addition, the initialization vector is computed in (25), which is used in the encryption process to enhance the randomness of the ciphertext. Finally, and by performing the encryption, and the verification parameter is computed in (27). Moreover, updates with and with in its own database. Finally, a message : is constructed by and transmitted to using the public communication channel.
4.3.4. Step AKA-4
is received at and its timeliness is validated through the condition . If the message is not replayed, then computes
If the condition in (31) holds, the message is considered to be a valid message.
4.3.5. Step AKA-5
To response , selects and and computes
Finally, constructs the message and transmitted the message to using the open communication channel.
4.3.6. Step AKA-6
validates the timeliness of the received message via the condition . The condition will be false if the message is replayed; otherwise, is considered as a valid message and computes
The received message will be a valid message if the condition in (42) holds. Otherwise, drops the received message and stops the AKA phase. In addition, the validness of the condition (42) indicates both the session keys, which are derived at and , are the same, and mutual authentication successfully accomplished. Finally, computes and updates with . The authentication process is summarized in Figure 2.
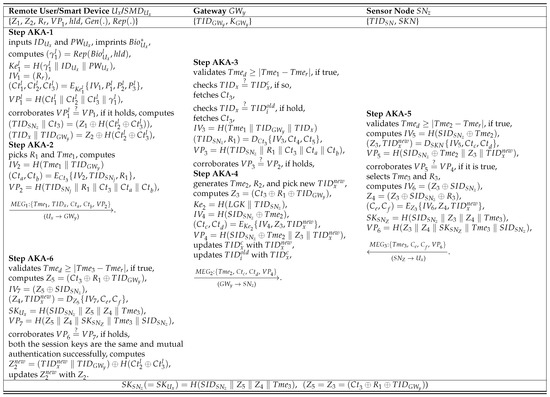
Figure 2.
RDAF-IIoT AKA phase.
4.4. Bio-Metric/Password Change Phase
During this phase, the user has the option to change their password and update their biometric information. The following steps must be followed to successfully complete the bio-metric/password update phase.
4.4.1. Step BCP-1
need to provide the old biometric information and password and compute
If the condition (48) holds, a prompt message is generated to intimate to provide the new parameters.
4.4.2. Step BCP-2
after receiving the new parameters, such as and . Moreover, picks computes
Finally, replaces the credentials {, , , , , , } with {, , , , , , } in the memory of .
5. Security Validation
The security strengths of the proposed RDAF-IIoT are validated through informal and formal security analysis. For the formal security analysis, the well-known mathematical method ROM is employed. In addition, Scyther, a software tool, is also used for the formal analysis.
5.1. Informal Security Analysis
In this section, the resiliency of the proposed RDAF-IIoT is corroborated against various attacks through informal (non-mathematical) analysis.
5.1.1. MITM Attack
There are three messages exchanged during the AKA phase. such as :{, , , , }, :, and :. After capturing any of these communicated messages, tries to modify the contents of messages. As , , and are validated at the receiving node to ensure the integrity of , , and , respectively. However, without knowing short-term and long-term secret credentials associated with , , and , it is hard for to compute , , and for the message , , and , respectively. In this way, the proposed RDAF-IIoT is resistant to MITM attack.
5.1.2. DoS Attack
The proposed RDAF-IIoT, achieves the local authentication by computing
In the event that the condition stated in (63) is satisfied, / transmits the AKA message to . Conversely, if the condition is not met, / terminates the execution process. By employing a local authentication mechanism, the proposed RDAF-IIoT effectively safeguards against potential DoS attacks by thwarting the efforts of malicious yet legitimate / entities attempting to flood with a high volume of AKA messages.
5.1.3. Impersonation Attack
During the AKA phase, sends message, such as : to for further authentication of . However, to impersonate as the valid , needs to generate a bogus using random parameters. Moreover, without knowing the the parameters , , and , cannot fabricate a valid . Similarly, cannot generate a valid message, such as :, and : without having the valid parameters used in the construction of these messages. Thus, the proposed scheme cannot provide protection against impersonation attacks.
5.1.4. Password Guessing Attack
After capturing of , obtains the parameters {, , , , , , } through the power analysis attack. To perform the password-guessing attack, selects the random secret credentials, such as and , and and computes
In order to successfully change the password, the condition in (69) must hold. However, without knowing the valid secret parameters, such as and , and or associated with the valid , it hard for to compute above computation. In this way, the proposed scheme is resistant to the password guessing attack.
5.1.5. Identity Guessing Attack
after capturing the messages, such as :, :, and : cannot obtain the real identity of . In addition, from the parameters {, , , , , , } cannot obtain the real identity of . In this way, the proposed scheme is resistant to the identity guessing attack.
5.1.6. Replay Attack
All the communicated messages, such as , , and during the AKA phase of the scheme are incorporated with the latest timestamps. The conditions , , and are checked at the receiving node for , , and , respectively, to detect the if the particular message is replayed or not. If the received message is not within the allowed time delay, the receiving node drops the messages and considers the received message as the replayed message. Hence, the RDAF-IIoT is resistant to replay attacks.
5.1.7. RPL Attack
In RDAF-IIoT, the session key is generated as , which the combination of both the long term and short term parameters. Without knowing both long-term and short-term parameters, it is hard for to generate a valid session key. Thus, the proposed RDAF-IIoT is resistant to RPL attack.
5.2. ROM Based Validation
The security of RDAF-IIoT is examined formally by employing ROM. The components of the ROM are demonstrated in Table 3. Capabilities of are examined in Section 3.2. In addition, effectuates the queries presented in Table 4 to generate various attacks on RDAF-IIoT.

Table 3.
ROM Components.

Table 4.
ROM Queries.
Theorem 1.
Let , , , and , denote hash and send queries, password dictionary space, length/space of bio-metric key, hash output length, respectively. denotes the advantage of in breaking the security of AES. The advantage of polynomial time () adversary to compromise the security of the session key generated between and can be determine as follows
Proof.
The proof of the Theorem (1) is derived in the same way as performed in [41,46,47,48]. Under ROM, interacts with instances attempts to guess the bit “b”. If guesses the correct bit, then RDAF-IIoT fails to provide the desired security. For proving the security of the proposed RADF-IIoT, the four games are contemplated, where the likelihood of to calculate the correct bit “b” is represented by . All the games under ROM are explained as follows.
: This game corresponds to the real attack under the ROM. By definition, the following can be reached
: executes the Execute and Send queries to captures , , and . The objective of after capturing these messages is to construct the session key, derived as where. Moreover, performs the Test query to know whether the obtained session key is the real or arbitrary number. It is worth mentioning that the constructed session key is the amalgamation of both the long and short-term parameters, such as , , , , , and . In addition, cannot access the database of , and the biometric key cannot be extracted by . Thus, the eavesdropping attack does not enable to obtain any advantage. Hence, both and are indistinguishable. So, the following can be reached.
: An active attack is established by and Send queries. As in RDAF-IIoT, the hash function generates SK on and . In addition, the parameter , , and are also computed using the hash function. strives to locate the collision by making queries to compromise the security of SK. However, the likelihood of collision occurrence is nominal. Thus, by the birthday paradox.
: is used by to generate an passive attack in this game. The purpose of is to obtain the data, such as {, , , , , , and } stored in the memory of the smart device of the user. The objective of is the update the password and biometric information of the user. However, the biometric key is of length , where the is the length of the biometric key and the probability of guessing the biometric key is , which is nominal. In addition, is allowed to perform only a few wrong passwords tries. Under these conditions, the following can be reached.
: An active attack is effectuated by in this game. The objective of is to retrieve the sensitive and secret parameters from , , and . As all the communicated messages are encrypted using symmetric encryption (AES). AES is secure to use, so to obtain the sensitive credentials from the , , and , it is necessary for to break the security of AES in polynomial time. It is hard for to break the security of AES in polynomial time. Hence, the following can be reached
As all the games are completed by , in repose receives no significant advantage to obtain correct bit “b”. Thus, following can be reached
From (77), following can be achieved
Upon considering the triangular inequality, the following can be reached.
□
5.3. Scyther-Based Security Verification
Scyther serves as a user-friendly tool for verifying, falsifying, and analyzing security protocols. It stands out among other advanced tools by offering several novel components. By employing a pattern refinement algorithm, Scyther efficiently generates concise representations of trace sets, aiding in the examination of attack categories and potential protocol behaviors. Extensively used in research, Scyther is a freely available security protocol verification tool. The proposed implementation of the RDAF-IIoT employs the security protocol description language (SPDL). The SPDL script defines three prominent roles: , , and . Each role is associated with specific claims outlined within the SPDL script. Scyther verifies all the claims, as demonstrated in Table 5 and Figure 3.

Table 5.
Scyther Claim Verification.
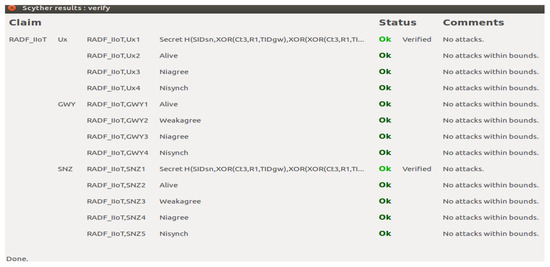
Figure 3.
Scyther analysis of the device access phase of RDAF-IIoT.
6. Performance Comparison
The proposed RDAF-IIoT is compared with Srinivas et al. [35], Challa et al. [25], Wazid et al. [34], and Irshad et al. [3] regarding computational and communication costs. In addition, the security functionality is also considered as a performance measure. To compute the computational time, a system with “Intel(R) Core(TM) i5-2400 CPU @ 3.10 GHz”, operating system “Ubuntu,” and RAM 8 GB is used to simulate as . In addition, a system with “CPU Quad Core 1.2 GHz, BCM2837, operating system Ubuntu, and RAM 1 GB RAM’ (Raspberry Pi-3 (RPI3))’ is used to simulate the smart sensing device and smart device of the user. All the cryptographic primitives are implemented using the cryptographic library called “Pycrypto” and each cryptographic primitive is executed 100 times to estimate the average computational time. Table 6 tabulates the computational complexities of various cryptographic primitives.

Table 6.
Computational Time Cryptographic Functions and Size of Various Parameters.
6.1. Security Comparison
The proposed RDAF-IIoT is contrasted with Wazid et al. [34], Srinivas et al. [35], and Challa et al. [25] regarding the security features and functions. The scheme of Wazid et al. [34] is not secure against the identity de-synchronization attack. Srinivas et al. [35] yields a security strategy weak against identity guessing, MITM, and user and device impersonation attacks. In addition, the authentication strategy suggested in [35] has a design defect, due to which the authentication procedure cannot be accomplished. The security framework suggested in Challa et al. [25] user anonymity, privilege insider, password guessing, and stolen smart card attack. Nevertheless, the security framework RDAF-IIoT is more secure and reliable than the contrasted security framework, as shown in Table 7.

Table 7.
Security Comparison.
6.2. Computational Cost
In this subsection, the computational cost of the proposed RDAF-IIoT is estimated. The computational time of ECC, ECC point addition, hash operation, symmetric encryption, and FE-based key generation is denoted by , , , , and , respectively. To derive the computational cost of the proposed RDAF-IIoT, computational complexities listed in Table 6 are employed. Total computational cost of RDAF-IIoT is ms, which is 78.63%, 74.73%, 77.36%, and 75.58% better than Srinivas et al. [35], Challa et al. [25], and Wazid et al. [34]. Figure 4, Figure 5 and Figure 6 and Table 8 show the computational cost comparison at , , and . Moreover, Figure 7 exhibits that with increasing the number, the proposed RDAF-IIoT requires less computational resources than Srinivas et al. [35], Challa et al. [25], and Wazid et al. [34].
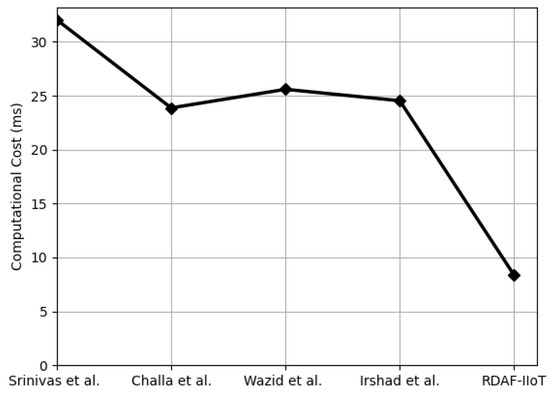
Figure 4.
Comparisons of computational cost at {[3,25,34,35]}.
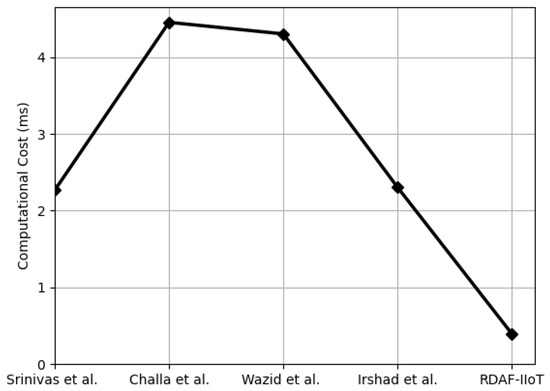
Figure 5.
Comparisons of computational cost at {[3,25,34,35]}.
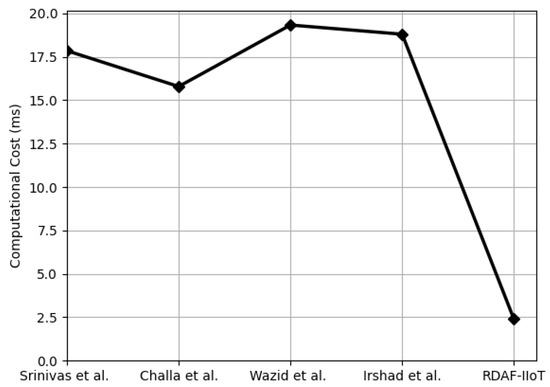
Figure 6.
Comparisons of computational cost at {[3,25,34,35]}.

Table 8.
Computational Cost.
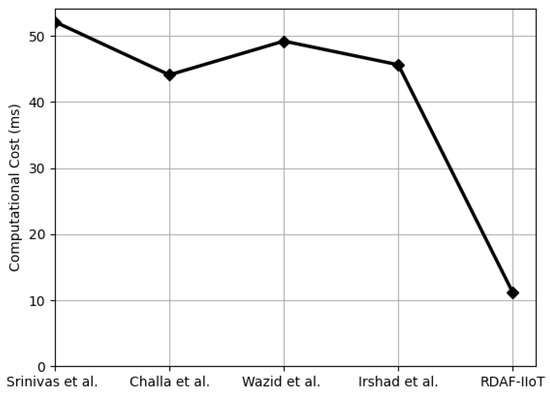
Figure 7.
Total computational cost required to complete the AKA phase {[3,25,34,35]}.
6.3. Communication Cost
To calculate the communication, which is required to accomplish the AKA phase, the parameters presented in Table 6 are used. There are three messages, such as : , :, and : {, , , } communicated during the AKA phase of the proposed RDAF-IIoT. The size of , , is {32 + 128 + 128 + 128 + 256} = 672 bits, {32 + 128 + 128 + 256} = 544 bits, and {32 + 128 + 128 + 128+ 256 } = 544 bits, respectively. Cumulative communication of the proposed RDAF-IIoT is {672 + 544 + 544 } = 1760 bits. The security framework of Srinivas et al. [35], Challa et al. [25], Wazid et al. [34], and Irshad et al. [3] require 2656 bits, 2528 bits, 3660 bits, and 3040 bits, respectively. Table 9 and Figure 8 show the communication efficiency of the proposed security framework than the relevant state of the security scheme.

Table 9.
Communication Cost.
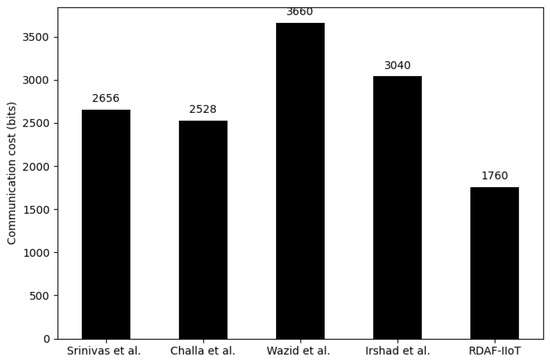
Figure 8.
Communication cost required to accomplish AKA phase {[3,25,34,35]}.
6.4. Discussion
The proposed RADF-IIoT adopts a resource-efficient approach by utilizing XoR operations, hash functions, and symmetric encryption, rather than relying on complex and computationally intensive public key cryptosystems. This design choice enables RADF-IIoT to minimize the computational resources required compared to other related security frameworks. By leveraging these lightweight cryptographic primitives, RADF-IIoT achieves efficient and effective security measures while reducing computational overhead.
Furthermore, in the proposed RADF-IIoT, the AKA process involves the exchange of a small number of parameters with small message sizes. This characteristic contributes to a reduced communication overhead in the RDAF-IIoT while still maintaining robust security features. By minimizing the amount of data transmitted during the authentication and key agreement process, the proposed RADF-IIoT optimizes communication efficiency without compromising the overall security of the system.
7. Conclusions
A security scheme to set up a session key between the user and the IIoT device is proposed in this paper called RDAF-IIoT. Moreover, during the AKA phase of RADF-IIoT, the established session key is used to achieve encrypted communication to avert various security attacks. It is through the informal security analysis proved that RDAF-IIoT is resistant to MITM and impersonation attacks. ROM is employed to corroborate the security of the session key generated in AKA phase of the proposed RDAF-IIoT. In addition, Scyther is utilized to corroborate that RDAF-IIoT is protected. Furthermore, the performance analysis illustrates that the proposed RDAF-IIoT required [74.73% to 78.63%] lower computational and [30.38% to 51.91%] lower communication costs than the related security schemes while providing enhanced security features.
Funding
This research was funded by King Khalid University under grant number RGP2/312/44.
Data Availability Statement
No external datasets were used in this study.
Acknowledgments
The authors extend their appreciation to the Deanship of Scientific Research at King Khalid University for funding this work through large group Research Project under grant number RGP2/312/44.
Conflicts of Interest
The author declares no conflict of interest.
References
- Kumar, A.; Saha, R.; Conti, M.; Kumar, G.; Buchanan, W.J.; Kim, T.H. A comprehensive survey of authentication methods in Internet-of-Things and its conjunctions. J. Netw. Comput. Appl. 2022, 204, 103414. [Google Scholar] [CrossRef]
- Tanveer, M.; Abbas, G.; Abbas, Z.H.; Bilal, M.; Mukherjee, A.; Kwak, K.S. LAKE-6SH: Lightweight User Authenticated Key Exchange for 6LoWPAN-Based Smart Homes. IEEE Internet Things J. 2022, 9, 2578–2591. [Google Scholar] [CrossRef]
- Irshad, A.; Mallah, G.A.; Bilal, M.; Chaudhry, S.A.; Shafiq, M.; Song, H. SUSIC: A Secure User Access Control mechanism for SDN-enabled IIoT and Cyber Physical Systems. IEEE Internet Things J. 2023. Early Access. [Google Scholar] [CrossRef]
- Wang, H.; Meng, J.; Du, X.; Cao, T.; Xie, Y. Lightweight and anonymous mutual authentication protocol for edge IoT nodes with physical unclonable function. Secur. Commun. Netw. 2022, 2022, 1203691. [Google Scholar] [CrossRef]
- Sui, T.; Mo, Y.; Marelli, D.; Sun, X.; Fu, M. The Vulnerability of Cyber-Physical System Under Stealthy Attacks. IEEE Trans. Autom. Control 2021, 66, 637–650. [Google Scholar] [CrossRef]
- Sui, T.; Sun, X.M. The vulnerability of distributed state estimator under stealthy attacks. Automatica 2021, 133, 109869. [Google Scholar] [CrossRef]
- Kwon, D.K.; Yu, S.J.; Lee, J.Y.; Son, S.H.; Park, Y.H. WSN-SLAP: Secure and lightweight mutual authentication protocol for wireless sensor networks. Sensors 2021, 21, 936. [Google Scholar] [CrossRef]
- Moghadam, M.F.; Nikooghadam, M.; Jabban, M.A.B.A.; Alishahi, M.; Mortazavi, L.; Mohajerzadeh, A. An Efficient Authentication and Key Agreement Scheme Based on ECDH for Wireless Sensor Network. IEEE Access 2020, 8, 73182–73192. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X. A privacy-preserving and provable user authentication scheme for wireless sensor networks based on internet of things security. J. Ambient. Intell. Humaniz. Comput. 2017, 8, 101–116. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X. A new and secure authentication scheme for wireless sensor networks with formal proof. Peer-to-Peer Netw. Appl. 2017, 10, 16–30. [Google Scholar] [CrossRef]
- Sahoo, S.S.; Mohanty, S.; Sahoo, K.S.; Daneshmand, M.; Gandomi, A.H. A Three Factor based Authentication Scheme of 5G Wireless Sensor Networks for IoT System. IEEE Internet Things J. 2023. Early Access. [Google Scholar] [CrossRef]
- Tanveer, M.; Kumar, N.; Hassan, M.M. RAMP-IoD: A robust authenticated key management protocol for the Internet of Drones. IEEE Internet Things J. 2021, 9, 1339–1353. [Google Scholar] [CrossRef]
- Tanveer, M.; Alkhayyat, A.; Kumar, N.; Alharbi, A.G. REAP-IIoT: Resource-Efficient Authentication Protocol for the Industrial Internet of Things. IEEE Internet Things J. 2022, 9, 24453–24465. [Google Scholar] [CrossRef]
- Eddine Berini, A.D.; Ferrag, M.A.; Farou, B.; Seridi, H. HCALA: Hyperelliptic curve-based anonymous lightweight authentication scheme for Internet of Drones. Pervasive Mob. Comput. 2023, 92, 101798. [Google Scholar] [CrossRef]
- Chen, C.T.; Lee, C.C.; Lin, I.C. Efficient and secure three-party mutual authentication key agreement protocol for WSNs in IoT environments. PLoS ONE 2020, 15, e0232277. [Google Scholar]
- Kumar, D.; Singh, H.K.; Ahlawat, C. A secure three-factor authentication scheme for wireless sensor networks using ECC. J. Discret. Math. Sci. Cryptogr. 2020, 23, 879–900. [Google Scholar] [CrossRef]
- Vinoth, R.; Deborah, L.J.; Vijayakumar, P.; Kumar, N. Secure multifactor authenticated key agreement scheme for industrial IoT. IEEE Internet Things J. 2020, 8, 3801–3811. [Google Scholar] [CrossRef]
- Ostad-Sharif, A.; Arshad, H.; Nikooghadam, M.; Abbasinezhad-Mood, D. Three party secure data transmission in IoT networks through design of a lightweight authenticated key agreement scheme. Future Gener. Comput. Syst. 2019, 100, 882–892. [Google Scholar] [CrossRef]
- Qiao, H.; Dong, X.; Jiang, Q.; Ma, S.; Liu, C.; Xi, N.; Shen, Y. Anonymous Lightweight Authenticated Key Agreement Protocol for Fog-Assisted Healthcare IoT System. IEEE Internet Things J. 2023. Early Access. [Google Scholar] [CrossRef]
- Wang, C.; Wang, D.; Duan, Y.; Tao, X. Secure and Lightweight User Authentication Scheme for Cloud-Assisted Internet of Things. IEEE Trans. Inf. Forensics Secur. 2023, 18, 2961–2976. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Susilo, W. Secure Remote User Authenticated Key Establishment Protocol for Smart Home Environment. IEEE Trans. Dependable Secur. Comput. 2020, 17, 391–406. [Google Scholar] [CrossRef]
- Vinoth, R.; Deborah, L.J. An efficient key agreement and authentication protocol for secure communication in industrial IoT applications. J. Ambient. Intell. Humaniz. Comput. 2023, 14, 1431–1443. [Google Scholar] [CrossRef]
- Choi, Y.; Lee, D.; Kim, J.; Jung, J.; Nam, J.; Won, D. Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2014, 14, 10081–10106. [Google Scholar] [CrossRef] [PubMed]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Conti, M.; Jo, M. Design of secure user authenticated key management protocol for generic IoT networks. IEEE Internet Things J. 2017, 5, 269–282. [Google Scholar] [CrossRef]
- Challa, S.; Wazid, M.; Das, A.K.; Kumar, N.; Reddy, A.G.; Yoon, E.J.; Yoo, K.Y. Secure signature-based authenticated key establishment scheme for future IoT applications. IEEE Access 2017, 5, 3028–3043. [Google Scholar] [CrossRef]
- Li, X.; Wu, F.; Khan, M.K.; Xu, L.; Shen, J.; Jo, M. A secure chaotic map-based remote authentication scheme for telecare medicine information systems. Future Gener. Comput. Syst. 2018, 84, 149–159. [Google Scholar] [CrossRef]
- Chatterjee, S.; Roy, S.; Das, A.K.; Chattopadhyay, S.; Kumar, N.; Vasilakos, A.V. Secure biometric-based authentication scheme using Chebyshev chaotic map for multi-server environment. IEEE Trans. Dependable Secur. Comput. 2016, 15, 824–839. [Google Scholar] [CrossRef]
- Tanveer, M.; Zahid, A.H.; Ahmad, M.; Baz, A.; Alhakami, H. LAKE-IoD: Lightweight Authenticated Key Exchange Protocol for the Internet of Drone Environment. IEEE Access 2020, 8, 155645–155659. [Google Scholar] [CrossRef]
- Das, A.K.; Wazid, M.; Kumar, N.; Vasilakos, A.V.; Rodrigues, J.J. Biometrics-based privacy-preserving user authentication scheme for cloud-based industrial Internet of Things deployment. IEEE Internet Things J. 2018, 5, 4900–4913. [Google Scholar] [CrossRef]
- Shuai, M.; Xiong, L.; Wang, C.; Yu, N. A secure authentication scheme with forward secrecy for industrial internet of things using Rabin cryptosystem. Comput. Commun. 2020, 160, 215–227. [Google Scholar] [CrossRef]
- Tanveer, M.; Khan, A.U.; Alkhayyat, A.; Chaudhry, S.A.; Zikria, Y.B.; Kim, S.W. REAS-TMIS: Resource-Efficient Authentication Scheme for Telecare Medical Information System. IEEE Access 2022, 10, 23008–23021. [Google Scholar] [CrossRef]
- Tanveer, M.; Abbas, G.; Abbas, Z.H.; Waqas, M.; Muhammad, F.; Kim, S. S6AE: Securing 6LoWPAN using authenticated encryption scheme. Sensors 2020, 20, 2707. [Google Scholar] [CrossRef]
- Sutrala, A.K.; Obaidat, M.S.; Saha, S.; Das, A.K.; Alazab, M.; Park, Y. Authenticated key agreement scheme with user anonymity and untraceability for 5G-enabled softwarized industrial cyber-physical systems. IEEE Trans. Intell. Transp. Syst. 2021, 23, 2316–2330. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Alazab, M. Designing authenticated key management scheme in 6G-enabled network in a box deployed for industrial applications. IEEE Trans. Ind. Inform. 2020, 17, 7174–7184. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Wazid, M.; Vasilakos, A.V. Designing secure user authentication protocol for big data collection in IoT-based intelligent transportation system. IEEE Internet Things J. 2020, 8, 7727–7744. [Google Scholar] [CrossRef]
- Xu, H.; Hsu, C.; Harn, L.; Cui, J.; Zhao, Z.; Zhang, Z. Three-factor anonymous authentication and key agreement based on fuzzy biological extraction for Industrial Internet of Things. IEEE Trans. Serv. Comput. 2023. [Google Scholar] [CrossRef]
- Ma, M.; He, D.; Wang, H.; Kumar, N.; Choo, K.K.R. An Efficient and Provably Secure Authenticated Key Agreement Protocol for Fog-Based Vehicular Ad-Hoc Networks. IEEE Internet Things J. 2019, 6, 8065–8075. [Google Scholar] [CrossRef]
- Chen, Y.; Yin, F.; Hu, S.; Sun, L.; Li, Y.; Xing, B.; Chen, L.; Guo, B. ECC-Based Authenticated Key Agreement Protocol for Industrial Control System. IEEE Internet Things J. 2022. Early Access. [Google Scholar] [CrossRef]
- Tanveer, M.; Khan, A.U.; Shah, H.; Chaudhry, S.A.; Naushad, A. PASKE-IoD: Privacy-Protecting Authenticated Key Establishment for Internet of Drones. IEEE Access 2021, 9, 145683–145698. [Google Scholar] [CrossRef]
- Sureshkumar, V.; Amin, R.; Vijaykumar, V.; Sekar, S.R. Robust secure communication protocol for smart healthcare system with FPGA implementation. Future Gener. Comput. Syst. 2019, 100, 938–951. [Google Scholar] [CrossRef]
- Tanveer, M.; Ahmad, M.; Khalifa, H.S.; Alkhayyat, A.; Abd El-Latif, A.A. A new anonymous authentication framework for secure smart grids applications. J. Inf. Secur. Appl. 2022, 71, 103336. [Google Scholar] [CrossRef]
- Tanveer, M.; Khan, A.U.; Ahmad, M.; Nguyen, T.N.; El-Latif, A.A.A. Resource-Efficient Authenticated Data Sharing Mechanism for Smart Wearable Systems. IEEE Trans. Netw. Sci. Eng. 2022. Early Access. [Google Scholar] [CrossRef]
- Yuanbing, W.; Wanrong, L.; Bin, L. An Improved Authentication Protocol for Smart Healthcare System Using Wireless Medical Sensor Network. IEEE Access 2021, 9, 105101–105117. [Google Scholar] [CrossRef]
- Tanveer, M.; Bashir, A.K.; Alzahrani, B.A.; Albeshrir, A.; Alsubhi, K.; Chaudhry, S.A. CADF-CSE: Chaotic map-based authenticated data access/sharing framework for IoT-enabled cloud storage environment. Phys. Commun. 2023, 59, 102087. [Google Scholar] [CrossRef]
- Khalid, H.; Hashim, S.J.; Hashim, F.; Ahamed, S.M.S.; Chaudhary, M.A.; Altarturi, H.H.; Saadoon, M. HOOPOE: High Performance and Efficient Anonymous Handover Authentication Protocol for Flying Out of Zone UAVs. IEEE Trans. Veh. Technol. 2023. Early Access. [Google Scholar] [CrossRef]
- Sharma, M.; Narwal, B.; Anand, R.; Mohapatra, A.K.; Yadav, R. PSECAS: A physical unclonable function based secure authentication scheme for Internet of Drones. Comput. Electr. Eng. 2023, 108, 108662. [Google Scholar] [CrossRef]
- Tanveer, M.; Alkhayyat, A.; Naushad, A.; Khan, A.U.; Kumar, N.; Alharbi, A.G. RUAM-IoD: A Robust User Authentication Mechanism for the Internet of Drones. IEEE Access 2022, 10, 19836–19851. [Google Scholar] [CrossRef]
- Tanveer, M.; Khan, A.U.; Kumar, N.; Naushad, A.; Chaudhry, S.A. A Robust Access Control Protocol for the Smart Grid Systems. IEEE Internet Things J. 2022, 9, 6855–6865. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).