Abstract
The growing demand for ultra-reliable and low-latency communication (URLLC) in private 5G environments, such as smart campuses and industrial networks, has highlighted the limitations of conventional Wireline access gateway function (W-AGF) architectures that depend heavily on centralized 5G core (5GC) processing. This paper introduces a novel Centralized Unit (CU)-based Zone-Access Gateway Function (Z-AGF) architecture designed to enhance handover performance and enable Local Breakout (LBO) within Non-Public Networks (NPNs) for non-5G capable (N5GC) devices. The proposed design integrates W-AGF functionalities with the Open Radio Access Network (O-RAN) framework, leveraging the F1 Application Protocol (F1AP) as the primary interface between Z-AGF and CU. By performing local breakout (LBO) locally at the Z-AGF, latency-sensitive traffic is processed closer to the edge, reducing the backhaul load and improving end-to-end latency, throughput, and jitter performance. The experimental results demonstrate that Z-AGF achieves up to 45.6% latency reduction, 69% packet loss improvement, 85.6% reduction of round-trip time (RTT) for local communications under LBO, effective local offloading with quantified throughput compared to conventional W-AGF implementations. This study provides a scalable and interoperable approach for integrating wireline and wireless domains, supporting low-latency, highly reliable services within the O-RAN ecosystem and accelerating the adoption of localized next-generation 5G services.
Keywords:
5G network; communication efficiency; O-RAN; local breakout; URLLC; handover; non-5G capable devices 1. Introduction
The rapid evolution of fifth generation (5G) mobile communication systems has created unprecedented opportunities for both public and private networks, particularly in achieving ultra-reliable low-latency communication (URLLC), massive connectivity, and flexible network slicing [1,2,3]. Among these innovations, Non-Public Networks (NPNs) have emerged as a promising paradigm for enterprises and institutions seeking customized, high-performance networking solutions that address specific latency, reliability, and security requirements [1,2]. Despite the proliferation of 5G-capable devices, a significant portion of end systems in private environments such as laptops, laboratory PCs, and internal departmental servers remain Non-5G-Capable (N5GC) [4,5]. These devices rely heavily on Wi-Fi or fixed network gateways managed by Wireless Access Gateway Functions (W-AGFs) to access network resources [4,6]. In smart campus scenarios, where multiple departments operate their own local networks, W-AGFs serve as the connectivity bridge between N5GC devices and the 5G-enabled infrastructure managed by the Centralized Unit (CU) of the Open Radio Access Network (O-RAN) [7]. However, current W-AGFs are not designed to support session continuity, mobility management, or low-latency handover during user transitions within a CU domain [2,7,8]. When a user moves between Wi-Fi zones such as classrooms, laboratories, or buildings—ongoing sessions to departmental servers may be interrupted, severely degrading the performance of latency-sensitive and real-time applications. Furthermore, W-AGFs lack Quality of Service (QoS) enforcement, path optimization, and URLLC-oriented routing mechanisms [5,7,9], making them unsuitable for next-generation smart campus or industrial IoT applications that demand deterministic performance.
1.1. Motivation
Recent studies have introduced Local Breakout (LBO) as an approach to reduce end-to-end latency and alleviate backhaul congestion by enabling localized routing of data traffic, bypassing the centralized 5G core (5GC) [10,11,12,13], while LBO has shown promise in improving network efficiency, most existing efforts have focused on Fixed Mobile Convergence (FMC) or general next-generation-radio access network (NG-RAN) optimizations [5,6,7]. These solutions do not explicitly address the mobility and session persistence challenges faced by N5GC devices in gateway-centric NPN environments such as smart campuses and enterprise networks.
In distributed smart campus networks, multiple W-AGFs operate independently under a single CU domain, with limited coordination or awareness of device mobility [7,14,15]. This architectural gap results in session interruptions and latency spikes when users move between the access zones. Consequently, there is a pressing need for an integrated mechanism that enables mobility-aware, low-latency, and seamless connectivity for N5GC devices, while maintaining compatibility with existing 5G and open-radio access network(O-RAN) components [7,16,17].
Unlike conventional solutions that rely exclusively on UPF-anchored breakout or Wi-Fi offload, our design leverages the O-RAN CU/F1 architecture. By terminating F1-C/F1-U and preserving CU-based session/mobility control, the Z-AGF extends O-RAN principles to the wireline and non-3GPP access domain.
1.2. Proposed Solution
To bridge this gap, this study introduces a novel centralized unit-based zone access gateway function (Z-AGF) architecture designed to enhance mobility awareness, session persistence, and latency optimization for N5GC devices operating under a CU-O-RAN domain. The Z-AGF integrates with the CU via the F1 Application Protocol (F1AP) for control-plane coordination [17,18,19], and leverages the user-plane enforcement function (UPEF) and local data network (LDN) elements to enable URLLC-aware local breakout [10,11]. In wired environments, the Z-AGF employs a layer 2 tunneling protocol (L2TP) Network Server (LNS) for IP address allocation and traffic management for fixed N5GC devices connected through residential gateways [5,20].
Unlike conventional W-AGF deployment, the proposed Z-AGF introduces cross-gateway coordination and latency-aware routing, ensuring uninterrupted connectivity as devices move across departmental access zones. By integrating session persistence and URLLC-based QoS enforcement, Z-AGF aims to deliver deterministic communication performance for diverse smart campus and enterprise applications.
1.3. Key Contributions
The key contributions of this paper are summarized as follows:
- Novel Z-AGF architecture for seamless N5GC connectivity: We introduce a Zone-Access Gateway Function (Z-AGF) as a CU-coordinated control-plane entity that complements existing CU-O-RAN and W-AGF components to enable session continuity and mobility for N5GC and fixed devices in private 5G environments.
- Practical integration and implementation: We demonstrate the integration of Z-AGF within a private smart-campus deployment using interoperable open-source platforms (Open5GS and UERANSIM), confirming feasibility and alignment with standardized O-RAN/3GPP interfaces.
- Latency-aware mobility enhancement: We design control- and user-plane mechanisms that apply localized breakout and QoS-aware routing at the access edge to support reliable and low-latency communication for delay-sensitive N5GC traffic.
- Experimental validation against a W-AGF baseline: We evaluate Z-AGF performance in terms of handover latency, packet loss, and session continuity, demonstrating consistent gains over a conventional W-AGF/UPF deployment in the examined smart-campus scenario.
These contributions collectively advance support for non-5GC devices in private 5G smart-campus networks, while maintaining compatibility with existing O-RAN and 3GPP procedures.
2. Related Work
The evolution of the Open Radio Access Network (O-RAN) and Non-Public Networks (NPNs) has motivated several studies on mobility management, Local Breakout (LBO), and Quality of Service (QoS) optimization for heterogeneous devices. This section presents a review of existing literature on the 5G Core architecture and its performance when integrated with the W-AGF, the limitations of the W-AGF, CU–O-RAN-based mobility management, and URLLC-aware data delivery for Non-5G-Capable (N5GC) devices.
2.1. 5G System with Access Gateway Function Overview
2.1.1. 5G Core Network Architecture
The 5G Core (5GC) serves as the central traffic controller for 5G networks. It offers greater flexibility, scalability, and service agility compared to earlier generations. The 5GC is built on a Service-Based Architecture (SBA) that interconnects modular network functions such as the AMF, SMF, UPF, AUSF, NSSF, NRF, and UDM [2,9]. The System Architecture for the 5G System (5GS) is defined in 3GPP TS 23.501 [2], which specifies the service-based interfaces and reference points among these functions.
2.1.2. Central Unit (CU) in NG-RAN
In the 5G system, the Radio Access Network (RAN) is standardized by 3GPP as the Next-Generation Radio Access Network (NG-RAN), as specified in TS 38.401 [16]. As in Figure 1, at the heart of NG-RAN is the gNB, the 5G base station that provides radio connectivity to User Equipment (UE) via the NR-Uu interface and connects to the 5GC through the NG interface [18,19]. As in Figure 2 According to TS 38.300 and TR 38.801, the gNB can be deployed as a single integrated node or disaggregated into multiple functional units for enhanced flexibility and scalability [16,17].
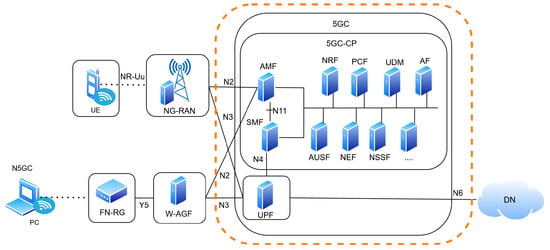
Figure 1.
5G Core Network Architecture with Access Gateway Function (AGF).
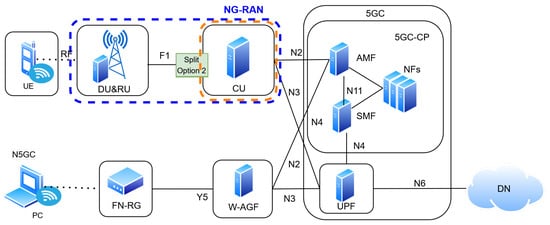
Figure 2.
Next Generation Radio Access Network (NG-RAN) architecture [17].
The Central Unit (CU) is a key element in the disaggregated architecture as shown in Figure 2. Based on the functional split Option 2 described in TR 38.801 and formalized in TS 38.401 [16,17], the CU hosts higher-layer RAN protocols, including the Packet Data Convergence Protocol (PDCP) and Service Data Adaptation Protocol (SDAP) for the user plane, as well as PDCP-C and RRC for the control plane. By centralizing these functions, CU enables unified mobility management, bearer control, and QoS enforcement across distributed RAN components [17,18].
The CU connects to one or more Distributed Units (DUs) through the standardized F1 interface, defined in TS 38.470 and related specifications. As in Figure 3, the F1 interface is logically divided into:
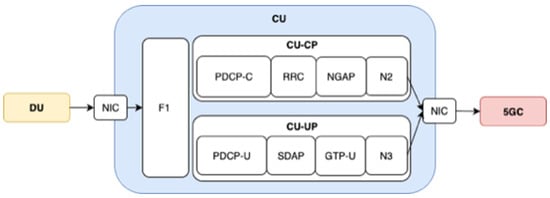
Figure 3.
Central Unit (CU) protocol layers [18].
- F1-C (Control Plane) specified in TS 38.471, using the F1 Application Protocol (F1AP) over SCTP to handle control signaling [17,18].
- F1-U (User Plane) defined in TS 38.472, utilizing GTP-U over UDP/IP for data transport [18,19].
These specifications are consolidated in TS 38.473, ensuring efficient bearer setup, RRC message transfer, and resource coordination between the CU and DU [17,18,19]. The F1 interface supports modular, cloud-native deployment and facilitates multi-vendor interoperability in 5G RANs, making it a key enabler of the next-generation O-RAN evolution [7,16]. This study specifically focuses on functional split Option 2 as in Figure 4, where the F1 interface and F1AP protocol are employed for data and control-plane coordination between the CU and DU, forming the foundation for CU–W-AGF inter-working in the proposed Z-AGF architecture.
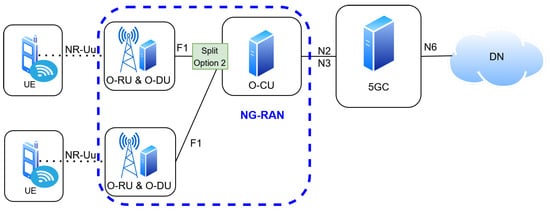
Figure 4.
Central Unit (CU) connected to multiple Distributed Units (DUs) via F1 interface.
2.1.3. Non-Public Network (NPN) in 5G Systems
In addition to public mobile networks, 5G system also support Non-Public Networks (NPNs), as introduced in 3GPP Release 16 and detailed in TS 23.501, TS 23.502, and TS 23.548 [21,22]. An NPN is a 5G deployment restricted to a specific enterprise or organization that provides dedicated connectivity, enhanced security, and performance control [21]. According to 3GPP TS 23.548 [23], two primary NPN categories are defined: the standalone non-public network (SNPN) in Figure 5 and the public network integrated NPN (PNI-NPN)in Figure 6.
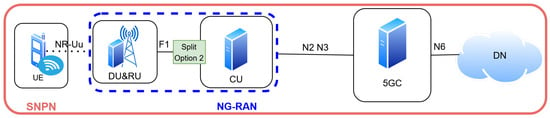
Figure 5.
Standalone Non-Public Network (SNPN) architecture.
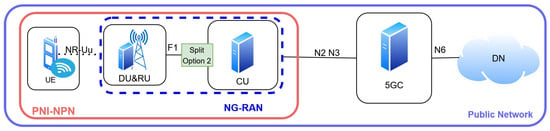
Figure 6.
PublicNetwork Integrated Non-Public Network (PNI-NPN) architecture.
The SNPN operates independently with its own 5G Core (5GC) and RAN, whereas the PNI-NPN leverages a public operator’s 5G Core but maintains a dedicated NPN RAN under enterprise control. In this model, the public 5GC handles control and mobility functions, whereas the NPN RAN delivers enterprise-specific optimizations such as local breakout and URLLC assurance [14].
The NPN RAN plays a critical role in enabling a local breakout, ensuring that enterprise traffic remains within the local domain rather than traversing the operator’s public core. This reduces latency, increases reliability, and secures data privacy [7,10]. Furthermore, the intra-CU handover within the NPN RAN supports seamless device mobility without disrupting the active sessions. These capabilities enable advanced use, including in smart campuses, industrial automation, and private IoT ecosystems. By combining the scalability of public 5GC infrastructureas in Figure 7 with localized NPN control, the PNI-NPN model achieves a balance between enterprise autonomy and operator-grade interoperability meeting stringent latency, mobility, and security requirements while remaining integrated within the broader 5G ecosystem [7,23].
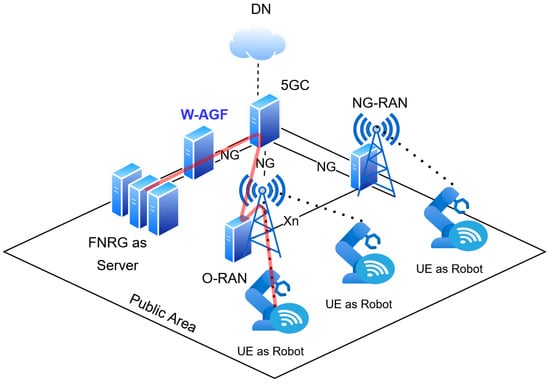
Figure 7.
Baseline Wireless Access Gateway Function (W-AGF) architecture showing traffic routing through the 5GC over NG interfaces in O-RAN environment.
2.2. Wireless–Wireline Convergence (WWC)
The 5G system is designed not only to unify multiple wireless technologies but also to enable convergence between wireless and fixed access networks a concept known as fixed–mobile convergence (FMC). Within the 5G framework, this is formalized as wireless–wireline convergence (WWC) [7,24]. The objective of WWC is to establish a common 5GC that simultaneously supports both 3GPP radio access (NG-RAN) and non-3GPP wireline access, thereby ensuring seamless service delivery across heterogeneous domains [4,20]. To achieve this convergence, 3GPP and the Broadband Forum (BBF) collaborated to define WWC specifications. The BBF’s TR-456 standard introduces the Access Gateway Function (AGF), which serves as an interface between fixed access technologies (e.g., PON, DSL, cable) and 5GC [6]. On the 3GPP side, TS 23.316 [5] and TS 23.501 [2] outlined the architectural and signaling frameworks for converged access. Adoption of WWC offers several advantages. It enables unified authentication and mobility management across both fixed and mobile domains [16], ensures converged QoS enforcement independent of access type, and simplifies operations by consolidating services within a single 5GC platform [6]. By leveraging FMC principles, WWC provides cost efficiency, operational flexibility, and seamless user experience across integrated wireline–wireless environments [11].
2.3. Wireline Access Network
Within the 5G architecture, the WWC framework extends 5GC capabilities to include wireline access networks (WANs) such as fiber, DSL, and cable systems [7]. These fixed access technologies are integrated through the jointly standardized Wireline 5G Access Network (W-5GAN) model, developed by 3GPP, BBF, and CableLabs [6,25]. In the W-5GAN framework, the Access Gateway Function (AGF), defined in BBF TR-456, acts as the primary adaptation entity between fixed access nodes and 5G Core, handling both control-plane and user-plane traffic [4,7]. CableLabs extended this model to DOCSIS systems, allowing cable operators to integrate a legacy broadband infrastructure with 5G-based service domains [6,20,25]. This integration provides several core capabilities:
- (1)
- Unified Authentication, enabling fixed broadband subscribers to use 5G credentials under a common identity management system [20];
- (2)
- Converged QoS Enforcement, ensuring consistent and predictable performance across wireline and wireless links [16]; and
- (3)
- Service Continuity, through session anchoring and context transfer mechanisms within the 5GC.By incorporating wireline access into the Wireless 5th-Generation Access Network framework, operators can reuse the existing broadband infrastructure to deliver true FMC and unified services via a single 5G Core architecture, thereby enhancing efficiency and accelerating 5G service convergence [11].
2.4. Wireline Access Gateway Function (W-AGF)
The 3GPP and Broadband Forum (BBF) jointly define the wireline access gateway function (W-AGF) as a network element that enables convergence between the wireline and wireless access networks under the access gateway function (AGF) model [7,26,27]. The W-AGF acts as a bridge between Non-5G-Capable (N5GC) devices connected via Wi-Fi or fixed broadband and the 5G Core (5GC). This enables IP address allocation, policy enforcement, and user-plane anchoring for fixed-access subscribers.
However, the standard W-AGF is primarily designed for connectivity rather than mobility. It lacks the capability to preserve active sessions during inter-departmental or inter-W-AGF handovers. Moreover, the existing W-AGFs do not implement distributed coordination or QoS differentiation mechanisms suitable for URLLC-based applications [10,15]. This limitation leads to an increased latency and session interruption when N5GC devices move between access domains within enterprise or smart campus NPN environments.
2.4.1. RG Registration Categories Based on SUPI Location and Access Type
Integrating wireline access into the 5GC introduces several Residential Gateway (RG) deployment models, that differ in the placement of the Subscription Permanent Identifier (SUPI) and the access path toward the 5GC [7,8]. As shown in Figure 8, Four standardized categories (a–d) were defined:
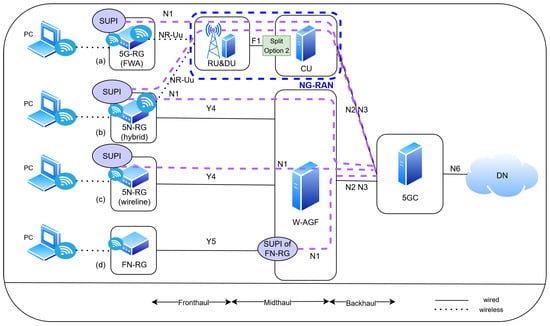
Figure 8.
Residential Gateway (RG) registration models (a–d) based on SUPI and access type in the 5G system.
- 5G-RG (FWA)—SUPI in RG with Wireless Access
In this model, the 5G-RG functions as a 5G UE. The RG stores SUPI and performs NAS signaling directly over the NG-RAN using the N1, N2, and N3 interfaces. Communication occurs wirelessly via the NR-Uu interface, which is typical of Fixed Wireless Access (FWA) deployments. This model provides full 5G features such as authentication, mobility management, and QoS enforcement directly in the RG [7].
- 5N-RG (Hybrid)—SUPI in RG with Wireline Backhaul
The 5N-RG (hybrid) configuration also contains a SUPI but connects to the 5GC via the W-AGF using the Y4 reference point. The RG initiates NAS signaling, and the W-AGF transparently forwards the messages to the 5GC without modifying the identity information, thus bridging wireless-level identity with fixed transport paths [19].
- 5N-RG (Wireline)—SUPI in RG with Fully Fixed Access
This configuration is similar to the hybrid model but relies entirely on fixed broadband (e.g., xPON or DSL). RG maintains its SUPI and registers it through the W-AGF. However, the absence of wireless fallback introduces a stricter dependency on fixed infrastructure for control-plane connectivity [7].
- FN-RG —SUPI in W-AGF (Proxy Model)
In the Fixed Network RG (FN-RG) model, the SUPI is stored within the W-AGF, which acts on behalf of the RG during registration. RG forwards user traffic over the Y5 interface, whereas the W-AGF performs N1/N2 signaling with 5GC. This proxy-based design simplifies legacy CPE support and minimizes on-premises complexity [7].
2.4.2. W-AGF Protocol Architecture and Functional Interworking
The W-AGF serves as a critical interworking function between non-3GPP fixed access networks and the 5G Core (5GC) as in Figure 8. It adapts both the control and user planes, ensuring the seamless integration of fixed broadband and mobile access within a unified 5G service framework [28]. The following subsections illustrate the control and user-plane interactions for both the fixed network residential gateways (FN-RGs) and 5G residential gateways (5G-RGs), as well as a discussion on existing I-UPF-based local breakout support.
- FN-RG Protocol Stack
Figure 9 shows the control-plane protocol stack between the FN-RG, W-AGF, and AMF. On the FN-RG side, signaling relies on the Legacy Wireline Control Plane (L-W-CP), which carries registration and session setup procedures over the Y5 interface.
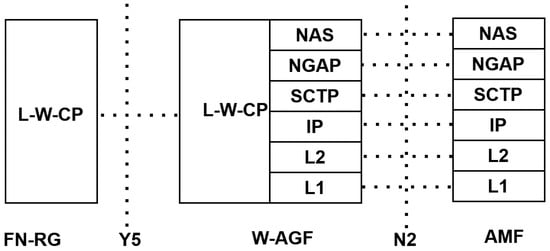
Figure 9.
Control-plane protocol stack between FN-RG, W-AGF, and AMF.
Within the W-AGF, L-W-CP messages are received and adapted to the 3GPP-compliant control-plane protocol stack. Specifically, the W-AGF translates signaling toward the AMF through the N2 interface, transferring Non-Access Stratum (NAS) messages encapsulated in the next-generation application protocol (NGAP) over SCTP/IP [19]. This control-plane interworking ensures that fixed devices register, authenticate, and maintain sessions in the 5GC as if they were native 5G UEs.
Figure 10 illustrates the user-plane protocol stack between the FN-RG, W-AGF, and User-Plane Function (UPF). The FN-RG employs the Legacy Wireline User-Plane (L-W-UP) protocol for traffic transport, which interfaces directly with the end-user PDU layer and forwards packets to the W-AGF via the Y5 interface.
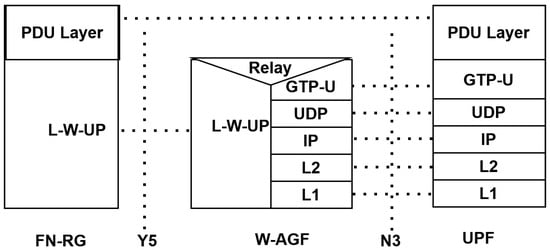
Figure 10.
User-plane protocol stack between FN-RG, W-AGF, and UPF.
Within the W-AGF, L-W-UP traffic is received and relayed to the 5GC user-plane format by encapsulating packets into the GPRS Tunneling Protocol–User-Plane (GTP-U), which runs over UDP/IP and is mapped to the N3 interface [19]. This design ensures compatibility with the UPF, enabling efficient bearer setup and data transfer for wireline clients.
- 5G-RG Protocol Stack
Figure 11 illustrates the control-plane protocol stack between the 5G Residential Gateway (5G-RG), W-AGF, and AMF. On the 5G-RG side, the Wireline Control Plane (W-CP) protocol is employed to carry both Access Stratum (AS) and Non-Access Stratum (NAS) signaling across the Y4 reference point.
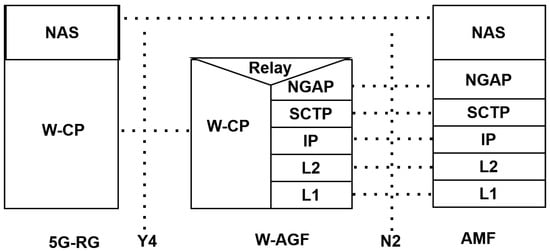
Figure 11.
Control-plane protocol stack between 5G-RG, W-AGF, and AMF using W-CP.
The W-AGF hosts a relay function that maps W-CP signaling into 3GPP-compliant control-plane procedures. Specifically, NAS messages are encapsulated in the Next-Generation Application Protocol (NGAP), which is transported via SCTP/IP over the N2 interface toward the AMF [18,28]. This ensures seamless registration, authentication, and mobility management for devices accessing 5GC through wireline gateways.
The design highlights the evolution from the legacy Wireline Control Plane (L-W-CP) toward a standardized W-CP protocol, fostering interoperability across diverse access technologies under a unified 5G control plane.
Figure 12 shows the user-plane protocol stack between the 5G-RG, W-AGF, and the User-Plane Function (UPF). The 5G-RG employs the Wireline User-Plane (W-UP) protocol to forward PDU session traffic over the Y4 reference point. Within the W-AGF, a relay function adapts W-UP traffic into GTP-U encapsulation, which is tunneled over the UDP/IP to the UPF via the N3 interface [18]. The UPF then terminates the GTP-U tunnel and forwards packets to the corresponding PDU session.
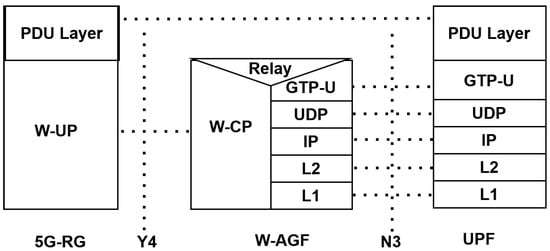
Figure 12.
User-plane protocol stack between 5G-RG, W-AGF, and UPF using W-UP.
Compared to the legacy L-W-UP model (Figure 10), the standardized W-UP protocol offers a tighter alignment with 5GC specifications, ensuring optimized QoS enforcement and session continuity for fixed-network subscribers. This architecture lays the foundation for the seamless integration of fixed broadband services into the 5G core.
2.4.3. Possible Existing Technology: I-UPF Integration
Figure 13 depicts the potential deployment of existing 5G technologies using an Intermediate User-Plane Function (I-UPF) within a Non-Public Network (NPN) scenario such as a smart campus. The architecture integrates multiple access types, including NG-RAN and fixed broadband via FN-RG and W-AGF, which converge toward the 5G core (5GC) [7,19].
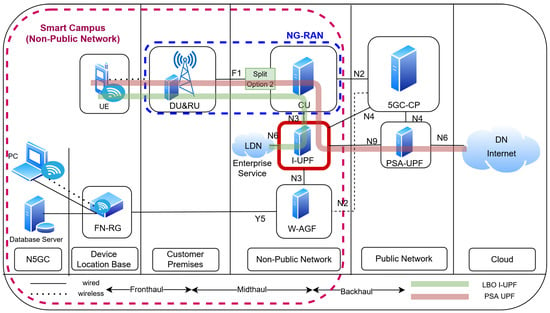
Figure 13.
I-UPF deployment in NPN environment enabling Local Breakout (LBO).
In this configuration, the Centralized Unit (CU) in NG-RAN forwards user traffic over the N3 interface toward the I-UPF. Likewise, fixed access traffic from FN-RG traverses the W-AGF via the Y5 interface, and connect to the I-UPF. The I-UPF enables Local Breakout (LBO), allowing direct access to enterprise-hosted services such as databases, IoT applications, and edge computing nodes [15]. This reduces the backhaul load and dependency on the public data network by retaining latency-sensitive traffic in the local environment.
For traffic requiring external connectivity, the I-UPF forwards packets to the PSA-UPF through the N9 interface before reaching the Data Network (DN) or Internet over N6. The 5GC control plane (5GC-CP) maintains session management and policy enforcement across both UPFs, thereby ensuring seamless operation [10].
2.5. CU–O-RAN-Based Mobility Management
The CU in O-RAN acts as the logical control anchor over the F1-terminated access nodes; building on this foundation, the Z-AGF behaves as a DU-like F1 node for wireline access, enabling CU-supervised mobility for N5GC devices.
Several studies [18,19] have explored CU-level optimization to enhance mobility and user-plane performance, particularly for handover procedures. although CU-based coordination significantly improves the mobility of 5G UEs, its integration with the W-AGF for managing Non-5G-Capable (N5GC) devices remains underexplored.
Recent research on distributed CU/DU deployments highlights hierarchical control architectures that reduce handover latency and improve session continuity in localized domains [10]. However, most approaches remain UE-centric and assume 5G NR connectivity, thereby overlooking the challenges posed by N5GC devices connected via Wi-Fi or fixed gateways. In enterprise and campus environments, multi-departmental CU configurations combined with distributed W-AGFs can enable localized mobility control and scalability. However, there remains a gap in achieving the CU-coordinated supervision of W-AGFs to ensure session persistence and QoS consistency for non-5G capable devices.
2.6. Local Breakout (LBO) and URLLC Integration
Local Breakout (LBO) has emerged as an effective strategy for reducing the backhaul load and end-to-end latency by routing traffic locally instead of traversing the 5G core. LBO facilitates edge computing, real-time analytics, and service localization—essential enablers of smart campuses and industrial IoT deployment. However, most existing LBO solutions operate at the UPF level and lack cross-gateway coordination mechanisms for distributed W-AGFs [6,7].
Existing MEC-based LBO approaches primarily anchor traffic at the UPF/MEC layer and do not integrate CU-coordinated mobility for N5GC devices [10], whereas the proposed Z-AGF performs breakout at the CU edge with preserved session continuity and reduced core involvement.
Moreover, integrating Ultra-Reliable Low-Latency Communication (URLLC) techniques such as latency-aware scheduling, dynamic QoS mapping, and fast reconnection has been examined in several studies [28,29]. These works emphasize QoS assurance for 5G NR but rarely extend to wireline or Wi-Fi-connected devices. Consequently, the true end-to-end reliability and session continuity remain limited for N5GC clients in converged access environments.
2.7. Access-Agnostic 5GC Convergence Alternatives
Achieving an access-agnostic 5G Core (5GC) has been a key objective in 3GPP and recent convergence studies, enabling the 5GC to support heterogeneous access technologies (3GPP NR, Wi-Fi, fixed broadband, industrial Ethernet, etc.) in a unified manner [18,19].
2.7.1. AMF-Based Convergence Sublayer
A convergence sublayer embedded within the AMF abstracts access-specific signaling and provides unified registration and mobility control for native 5G UE, as defined in 3GPP SA2 architecture specifications [19,30]. However, supporting fixed and legacy non-5GC devices still requires modifications on the access side, making this option less suitable for private networks with numerous deployed FN-RGs and CPEs [31].
2.7.2. Common AN/CN Interface Definition
Another approach is the definition of a universal access–core interface to remove protocol diversity between technologies. Although conceptually unified, this requires substantial redesign of existing Wi-Fi and fixed-access infrastructures, and has limited practicality in brownfield deployments [32].
2.7.3. Convergence NAS Protocol on UE and CN
A convergence NAS layer implemented symmetrically at the UE and core sides can enable access-independent attach, session, and mobility procedures. However, this approach lacks backward compatibility with unmodifiable industrial equipment and fixed endpoints without native NAS support [33]. Current convergence methods either require significant modernization of access networks/devices or exclude legacy terminals. This motivates the proposed CU-coordinated Z-AGF architecture, which achieves access-agnostic breakout and mobility without modifying non-5GC devices, while preserving 3GPP/O-RAN compliance at the CU edge.
2.8. Research Gap
Although integrating W-AGF and CU within O-RANs enhances wireline–wireless interoperability, current implementations fail to adequately address session continuity, handover optimization, and latency-aware mobility for Non-5G-Capable (N5GC) devices in private smart campus networks [7]. Existing W-AGF frameworks primarily handle initial access and authentication but lack inter-W-AGF coordination, whereas current LBO and URLLC implementations remain core-centric, leading to high latency, signaling overhead, and session interruptions in Non-Public Network (NPN) domains.
To address these limitations, this study proposes a CU-coordinated Zone Access Gateway Function (Z-AGF) framework that enables mobility awareness, session persistence, and URLLC-based path optimization at the departmental level. The Z-AGF bridges W-AGF and CU functionalities to achieve seamless mobility, localized breakout, and low-latency connectivity for N5GC devices in enterprise and campus networks. The next section details the proposed Z-AGF architecture, design rationale, and operational mechanisms for efficient wireline–wireless inter-working in O-RAN environments.
3. Proposed Approach: Zone Access Gateway Function (Z-AGF)
This section presents the design and operational framework of the proposed Zone Access Gateway Function (Z-AGF).
The Z-AGF is introduced as a novel control and user-plane entity that complements the existing wireless access gateway function (W-AGF) and Centralized Unit (CU) within private smart campus networks. Its primary objective is to ensure seamless mobility, session continuity, and low-latency connectivity for Non-5G-Capable (N5GC) devices connected via Wi-Fi or fixed access networks under a CU domain.
3.1. Architectural Overview
Figure 14 presents the overall architecture of the proposed Z-AGF framework.
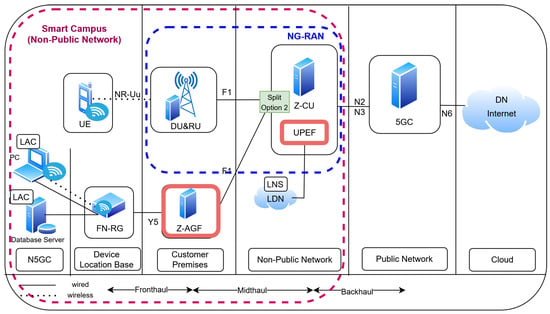
Figure 14.
Proposed Z-AGF architecture integrating wireline access with CU–O-RAN for N5GC devices.
The Z-AGF operates as an F1-terminating O-RAN access-edge entity, maintaining strict compliance with 3GPP/O-RAN specifications through F1AP-based control signaling and CU-coordinated PDCP/SDAP user-plane functions. By interfacing directly with the Zone-CU over the standardized F1-C/F1-U split, the Z-AGF seamlessly integrates mobility, policy, and data-path management for wireline clients connected via Fixed Network Residential Gateways (FN-RGs).
Unlike conventional W-AGF or I-UPF deployments, which depend heavily on the 5G Core (5GC) for session anchoring, Z-AGF introduces a User-Plane Enhancement Function (UPEF) and a Local Data Network (LDN) to enable localized breakout for latency-sensitive traffic. in addition, an integrated l2tp Network Server (LNS) provides scalable IP allocation per departmental zone, ensuring address isolation and efficient routing. This design supports seamless inter-Z-AGF mobility and traffic steering within the smart-campus domain, substantially reducing the backhaul dependency and end-to-end delay.
3.2. Interface Legitimacy and F1AP Adaptation in Z-AGF
The Z-AGF extends CU–O-RAN intelligence to wireline domains by implementing a proxy DU-like abstraction that enables legitimate F1AP communication with the CU. Although the F1 interface is standardized primarily for CU–DU coordination (TS 38.470–38.473) [16,17,18], the Z-AGF operates strictly at the PDCP/SDAP boundary of functional split Option 2 (TS 38.401) [17], avoiding any dependency on lower-layer RLC/MAC/PHY scheduling and radio-specific procedures.
To achieve this, the Z-AGF introduces a lightweight shim-control layer that translates PPPoE/L2TP session parameters into F1-C BearerContextSetup, modification, and release procedures based on TS 38.471–38.473 [17,18,19], preserving TEID/QFI/5QI semantics for QoS enforcement [2]. This allows the CU to retain full ownership of radio-level capabilities, QoS rules, and mobility state machines [7].
On the user-plane side, the Z-AGF encapsulates wireline traffic into F1-U GTP-U flows toward the CU-UP (TS 38.472) [18], allowing transparent session anchoring without modifying 5GC logic [2]. Thus, the Z-AGF behaves as a logical bearer-anchoring DU [7], ensuring interoperability with vendor-neutral CU implementations under standard O-RAN procedures [16].
Mobility-related tunnel updates (uplink/downlink) are coordinated and authenticated by the Z-CU, which performs session-context synchronization across departmental zones, ensuring seamless handover without violating 3GPP DU scope constraints [19].
3.3. Protocol Stack Design
3.3.1. Control Plane Inter-Working
Figure 15 illustrates the control-plane protocol stack for the N5GC devices under the Z-AGF. On the FN-RG side, signaling is initiated through PPPoE and DHCP, traversing the Y5 interface toward the Z-AGF. The Z-AGF adapts this signaling to 3GPP-compliant procedures using the F1 Application Protocol (F1AP) over SCTP/IP and forwards control-plane messages to the CU-CP. Subsequently, NGAP procedures manage the registration and authentication toward the AMF through the N2 interface [29]. This layered interworking ensures seamless session establishment and mobility management while maintaining compliance with the 3GPP TS 38.471 [17] and TS 23.316 specifications [5].
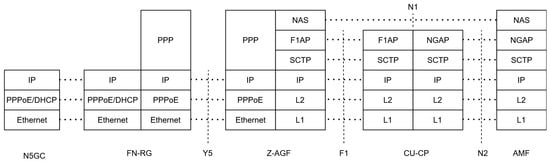
Figure 15.
Control-plane protocol stack between FN-RG, Z-AGF, and 5GC elements.
3.3.2. User-Plane Operations
The user-plane operation shown in Figure 16 maps fixed-access traffic into 5G-compliant GTP-U tunnels. FN-RG packets encapsulated through PPPoE/DHCP are relayed over Ethernet to Z-AGF, where they are translated into F1-U traffic toward CU-UP over UDP/IP. The CU-UP subsequently encapsulate the data into GTP-U tunnels over the N3 interface toward the UPF. This layered architecture ensures end-to-end QoS preservation, efficient bearer handling, and transparent inter-working between fixed and mobile domains.
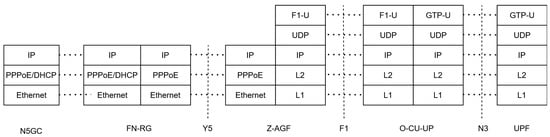
Figure 16.
User-plane protocol stack for N5GC traffic through Z-AGF and CU-UP.
3.3.3. Local Breakout Mechanism
To overcome the limitations of centralized UPF routing, Z-AGF implements a distributed Local Breakout (LBO) mechanism through integrated UPEF and LDN components (Figure 17). Latency-sensitive traffic is dynamically classified at the Z-AGF and redirected to the LDN for local processing, thereby bypassing the 5G core. While latency-sensitive flows are locally offloaded through the UPEF/LDN, all QoS policies remain enforced under PCF rules, charging records are still reported to the CHF via the SMF, and lawful-interception visibility is preserved through NEF/AF exposure, ensuring full 3GPP governance compliance.
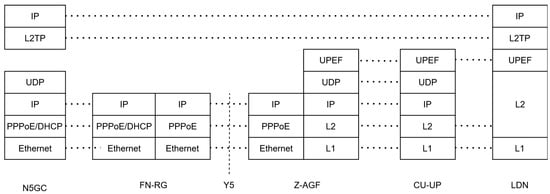
Figure 17.
Z-AGF-enabled Local Breakout (LBO) protocol stack for latency-sensitive traffic via UPEF and LDN.
The UPEF manages encapsulation and session persistence, whereas the LNS dynamically assigns IP addresses within each departmental zone. This localized optimization significantly reduces the round-trip time (RTT) and jitter for enterprise applications, thereby achieving real-time responsiveness and enhanced reliability across departments.
3.4. Z-AGF Call Flow Procedures
Figure 18 illustrates the PDU session establishment process for the N5GC devices under Z-AGF control. The procedure begins with device registration and authentication at the Z-AGF, followed by session establishment through CU and UPF components. The Z-AGF coordinates with the CU-CP for the bearer setup, whereas the CU-UP manages user-plane mapping, ensuring context synchronization between the control and data paths.
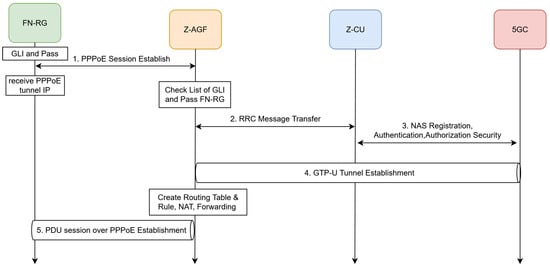
Figure 18.
PDU session establishment sequence for N5GC devices under Z-AGF.
The Local Breakout signaling flow, shown in Figure 19, demonstrates how the Z-AGF redirects traffic to the LDN for localized processing. The CU maintains flow control and policy coordination, ensuring a consistent QoS between the LBO and core-based sessions. This integration enables seamless local service access without disrupting the global 5GC connectivity.
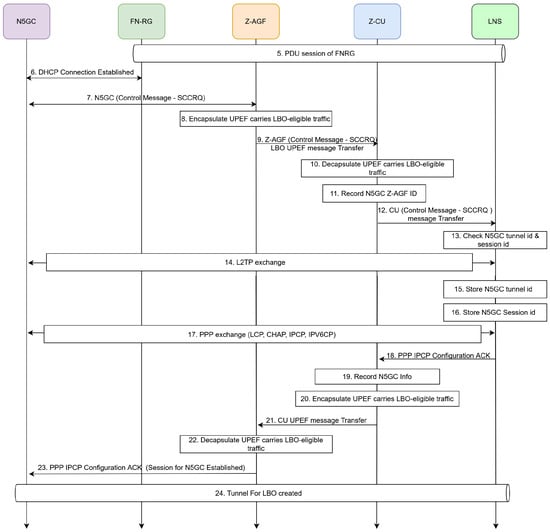
Figure 19.
Local Breakout (LBO) signaling flow between N5GC, Z-AGF, and CU components.
Finally, Figure 20 depicts the inter-Z-AGF handover procedure coordinated by the Z-CU using a Mobility-Based Bridging (MBB) mechanism. When a device moves across zones, Z-CU manages session continuity by pre-synchronizing the session contexts between the source and target Z-AGFs. This enables smooth mobility for N5GC devices without requiring re-authentication or PDU session re-establishment, thereby minimizing interruption and signaling overhead.
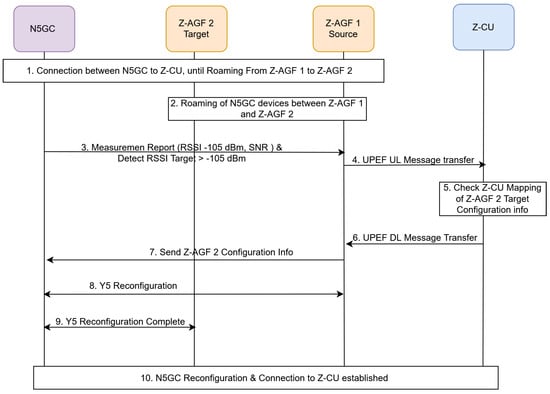
Figure 20.
Inter-Z-AGF handover procedures coordinated by Z-CU using the MBB mechanism.
3.4.1. PDU Session Establishment
As shown in Figure 18, the Z-AGF manages the complete PDU session setup for each FN-RG, including PPPoE discovery, authentication, and signaling coordination with the CU-CP and 5G core. Once the GTP-U tunnel is established between the Z-AGF and CU-UP, FN-RG obtains IP configuration and achieves full connectivity within the CU-coordinated NPN environment.
Z-AGF PDU Session Establishment Procedures:
- FN-RG requests a PPPoE session from the ISP (Z-AGF): its broadcasts a PPPoE Discovery Procedure to the Z-AGF. A PPPoE session was established, and the Z-AGF executed the control procedures for FN-RG registration and session setup.
- Registration and Authentication: The Z-AGF handles the registration and authentication procedure of the FN-RG to the 5G Core Network and sends it through an RRC message transfer.
- PDU Session Acceptance: The Z-AGF receives the PDU Session Establishment Accept message and establishes the corresponding GTP-U tunnel. At this stage, Z-AGF manages the FN-RG’s user plane.
- Tunnel Creation: The tunnel to the Z-AGF was created and is listed in the routing table.
- PDU Session Completion: The PDU session of the FN-RG is successfully established.
3.4.2. Local Breakout (LBO) Procedures
As illustrated in Figure 19, the Local Breakout (LBO) procedure enables latency-sensitive traffic to be routed locally through the Z-AGF without traversing the 5G core. Once the PDU session is established, the N5GC device initiates session control signaling that triggers UPEF encapsulation and the L2TP configuration for direct local path formation between the Z-AGF and CU. This mechanism ensures low-latency communication and optimized bandwidth utilization within the CU-coordinated network domain.
Z-AGF Local Breakout (LBO) Procedures:
- DHCP/PPPoE Connection: A DHCP/PPPoE connection is established between the N5GC device and FN-RG.
- SCCRQ Initiation: The N5GC device sends an SCCRQ message.
- UPEF Encapsulation: The Z-AGF encapsulates the N5GC SCCRQ within the UPEF tunnel.
- UPEF Message Transfer: The encapsulated message is forwarded through the UPEF tunnel.
- CU Decapsulation: The CU decapsulates the received UPEF message.
- Record Z-AGF Information in Z-CU: The Z-CU records Z-AGF information as follows:
- Z-AGF ID = 1
- Z-CU (Z-AGF) IP = 10.50.0.88
- CU Message Handling: The CU transfers the SCCRQ message to the target entity.
- Tunnel and Session Validation: The CU verifies the N5GC device’s tunnel ID and session ID.
- L2TP Procedure: The CU performs L2TP configuration for the N5GC device.
- Record Session Parameters:N5GC Device Tunnel ID (stored)
- Record Session Parameters:N5GC Device Session ID (stored)
- PPP Exchange: PPP negotiation is performed between the N5GC device and the Z-AGF.
- IPCP Configuration: The N5GC device receives a PPP IPCP Configuration ACK message.
- Record N5GC Device Information:
- N5GC ID = 1
- Z-CU Z-AGF ID = 1
- N5GC Z-AGF IP Tunnel = 10.50.0.88
- CU Encapsulation: The CU encapsulates traffic using F1-U.
- F1-U Message Transfer: The CU transfers the encapsulated F1-U message.
- Z-AGF Decapsulation: The Z-AGF decapsulates the F1-U traffic, carrying the LBO payload.
- Final Configuration: The N5GC device receives PPP IPCP Configuration ACK confirmation.
- LBO Tunnel Creation: The LBO tunnel for the N5GC device is successfully created.
3.4.3. Handover Procedures
As shown in Figure 20, the handover procedure in the Z-AGF framework enables seamless mobility for N5GC devices transitioning between different Z-AGF zones under CU-coordination. When a device moves from one departmental zone to another, the Z-CU manages tunnel updates, signaling synchronization, and the Y5 interface reconfiguration to ensure uninterrupted service continuity and session persistence. If tunnel establishment or Z-CU synchronization fails during mobility, the session temporarily falls back to the UPF-anchored route while the Z-CU triggers context refresh or incremental FN-RG reauthentication, ensuring continuity without PDU-session loss.
Z-AGF Handover Procedure for N5GC Devices:
- Connection Establishment: The N5GC device establishes an active connection with the current Z-AGF.
- Roaming Event: The N5GC device initiates a handover, roaming from Z-AGF1 to Z-AGF2.
- Tunnel Detection: The serving Z-AGF detects a new tunnel request from the N5GC device.
- F1AP UL Message Transfer: The Z-AGF sends an F1AP uplink message to initiate a tunnel update request.
- Tunnel Update Request: The request is sent to the Z-CU for coordination.
- Tunnel Information Update: The Z-CU updates the tunnel parameters as follows in Table 1:
 Table 1. Z-CU/Z-AGF tunnel information for an N5GC device before and after handover.
Table 1. Z-CU/Z-AGF tunnel information for an N5GC device before and after handover. - Tunnel Update Response: The Z-CU sends the tunnel update response to confirm the successful modification.
- F1AP DL Message Transfer: The CU transmits a downlink F1AP message carrying the tunnel update response.
- Y5 Reconfiguration (Target Tunnel Setup): The Y5 interface was reconfigured to establish the tunnel toward the target Z-AGF.
- Tunnel Response Delivery: The CU sends the tunnel update response to the target Z-AGF.
- Target Z-AGF Tunnel Detection: The target Z-AGF detects and activates a new N5GC tunnel request.
- Y5 Reconfiguration Completion: The system completes Y5 reconfiguration by breaking the tunnel associated with the source Z-AGF.
- Connection to LNS Established: A new connection to the LNS is established, completing the inter-Z-AGF handover process.
The proposed inter-Z-AGF handover does not require a new registration or NAS protocol update. As shown in Figure 18, the FN-RG/N5GC device completes a standard 5GC registration and PDU-session establishment with the AMF/SMF once, and this NAS context remains anchored at the Z-CU. During mobility between zones, only the F1-U and Y5 tunnel bindings are updated under Z-CU coordination, while the original NAS and PDU-session state is fully preserved. The handover procedure is treated as an intra-CU mobility event and remains fully compliant with existing 3GPP NAS specifications. Therefore, Z-AGF establishes a unified, latency-optimized access framework that extends CU-O-RAN intelligence to wireline domains, enabling seamless N5GC integration in smart campuses and private 5G deployments.
4. Implementation and Experimental Setup
This section presents the implementation setup of the proposed Zone Access Gateway Function (Z-AGF) and its experimental validation within a private 5G smart campus environment.
The objective is to evaluate session continuity, latency performance, and local breakout efficiency for Non-5G-Capable (N5GC) devices operating under the Z-AGF framework.
4.1. Prototype Experimental Environment
The Z-AGF prototype was developed and deployed using a hybrid testbed environment that combines virtualized network functions with emulated access devices, as illustrated in Figure 21. The experimental setup integrates several open-source components to realize the end-to-end Next-Generation Radio Access Network (NG-RAN) architecture and to evaluate the proposed Zone–Access Gateway Function (Z-AGF) concept.
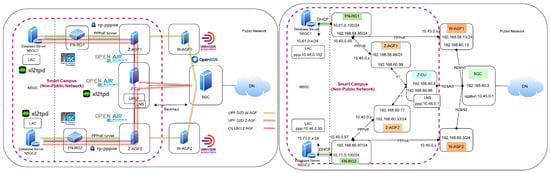
Figure 21.
Experimental testbed integrating Open5GS, UERANSIM, and OpenAirInterface components for Z-AGF implementation and configuration.
The test environment consists of the following major components:
- 5G Core Network: Implemented using the Open5GS platform [22,34], comprising Access and Mobility Management Function (AMF), Session Management Function (SMF), and User-Plane Function (UPF) [35]. These modules were deployed on Ubuntu 22.04 (Jammy) with kernel version 5.15.0, providing reference 5GC functions for the control and user-plane operations.
- Wi-Fi Access and Gateway Layer: The Wireless Access Gateway Functions (W-AGFs) were virtualized and connected to departmental Wi-Fi access points simulated via host-based bridges. Each W-AGF instance interacts with the Z-AGF through a lightweight control channel for session synchronization and mobility coordination. The W-AGF was realized through the UERANSIM [36] framework, operating as a proxy UE over the N2 and N3 interfaces toward the 5GC, and integrated with an rp-pppoe [37] server for PPPoE-based aggregation.
- Z-AGF Module: Implemented as a middleware between the W-AGFs and the Centralized Unit (CU), the Z-AGF was developed in Python 3.13 (control-plane) and C++23 (user-plane). It incorporates three submodules: Mobility Management Module (MMM), Session Persistence Engine (SPE), and QoS Policy Control Unit (QPCU). Z-AGF leverages the OpenAirInterface (OAI) [34,38] stack to support F1 interface signaling and proxy UE interconnection with the CU. An rp-pppoe server provides tunneling support for subscriber sessions through PPPoE encapsulation.
- Centralized Unit (CU): The CU–O-RAN instance was emulated using the OpenAirInterface CU implementation, which manages the F1 Application Protocol (F1AP) signaling and coordinates Z-AGF functions during handovers and QoS updates. The CU interfaces with the UPF for packet forwarding and session management across distributed AGFs.
- Fixed network residential gateway (FN-RGs): Each FN-RG node was implemented using the ISC-DHCP server [39] for dynamic IP allocation to end devices, complemented by xl2tpd [40] for Layer-2 tunneling to local access networks. The FN-RGs emulate customer premises equipment (CPE) devices that act as tunnel endpoints for PPPoE sessions connected to AGFs.
- Database and Analytics: A MongoDB instance stores session contexts, device identifiers, and latency statistics collected during the post-analysis experiments [41].
- UE and Traffic Simulation: The UERANSIM toolkit emulates 5G user equipment (UE) and generates UDP/TCP traffic flows. For N5GC devices, Wi-Fi clients were emulated via virtual interfaces connected through departmental W-AGFs.
The entire testbed was hosted on an Intel Core i9 workstation with 64 GB RAM and VMware-based virtualization. Network namespaces and virtual bridges are configured to isolate each component, allowing the emulation of realistic mobility transitions within a single CU domain. This modular and reproducible environment enables flexible experimentation with different tunneling, access, and interworking mechanisms across fixed and mobile segments.
4.2. Experimental Configuration and Results
As shown in Figure 22, the experimental log outputs from the Z-AGF implementation demonstrate the association of an FN-RG with the 5G Core and the corresponding IP allocation process. The upper log segment SMF/UPF confirms that the FN-RG, identified by its SUPI 208997000000002), successfully establishes a PDU session with the UPF allocating IPv4 address 10.45.0.6 for data connectivity. The lower log segment Z-AGF captures the PPPoE session setup at the access gateway, where the FN-RG identifier is authenticated and mapped to the same allocated IP address.
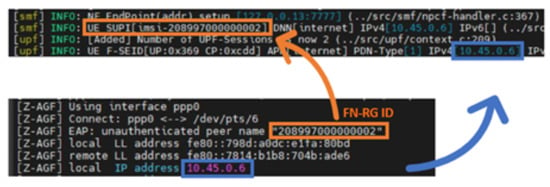
Figure 22.
Experimental log outputs showing FN-RG association, SUPI mapping, and IP allocation via Z-AGF–5GC interworking.
These results validate that the Z-AGF correctly manages end-to-end mapping between the FN-RG identity, control-plane signaling (via SMF), and user-plane IP allocation (via UPF). The successful binding of the SUPI and IP address (10.45.0.6) confirms the proposed Z-AGF protocol stack design and its ability to integrate fixed network access into the 5G Core while remaining compliant with 3GPP architectural procedures.
5. Results and Discussion
This section presents an experimental evaluation and analysis of the proposed Zone Access Gateway Function (Z-AGF)architecture in comparison with conventional approaches, namely the Wireless Access Gateway Function (W-AGF) and Intermediate User-Plane Function (I-UPF). The experiments were conducted in an emulated 5G Non-Public Network (NPN) environment integrating Open5GS, OpenAirInterface (OAI),UERANSIM, and PPPoE/L2TP tunneling, as described in Section 4.
The evaluation focused on performance gains in round-trip time (RTT), handover latency, packet loss ratio, jitter, throughput, and CPU utilization. Wireshark traces and system counters were used to collect data under controlled bitrate variations (5–50 Mbps). The results are presented as numerical tables and graphical visualizations.
Overall, the proposed Z-AGF consistently outperforms the baseline W-AGF/UPF configuration. By enabling Local Breakout (LBO) and direct coordination with a Centralized Unit (CU), Z-AGF minimizes core traversal, reduces signaling overhead, and achieves lower latency with improved reliability. The following subsections analyze the handover, reliability, LBO efficiency, and resource utilization in detail.
As in Figure 23, Z-AGF minimizes Path C traversal through 5GC by enabling local breakout and inter-zone routing, resulting in shorter data paths and reduced latency.
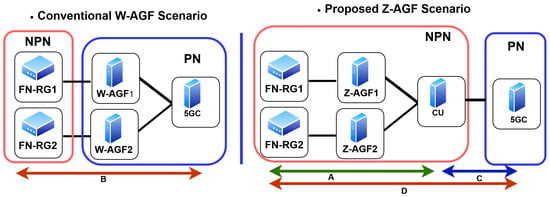
Figure 23.
Experimental setup and traffic flow comparison between baseline W-AGF and proposed Z-AGF architectures.
5.1. Evaluation Methodology
Experiments were executed under three primary configurations using both TCP and UDP traffic profiles:
- Scenario 1: Standard W-AGF(baseline), mobility and session management handled solely by W-AGF/I-UPF.
- Scenario 2: Z-AGF Enabled, Mobility jointly managed by the Z-AGF and CU using cached session contexts.
- Scenario 3: Z-AGF combined with LBO, mobility and localized data routing for intra-campus communication.
Each scenario was repeated to ensure statistical consistency. The reported results corresponded to the average values from these runs.
5.2. Handover Latency Analysis
Figure 24 shows the measured handover latencies across configurations. Z-AGF demonstrates a smoother latency profile compared to the W-AGF baseline, validating the CU-assisted coordination and optimized control-plane signaling.
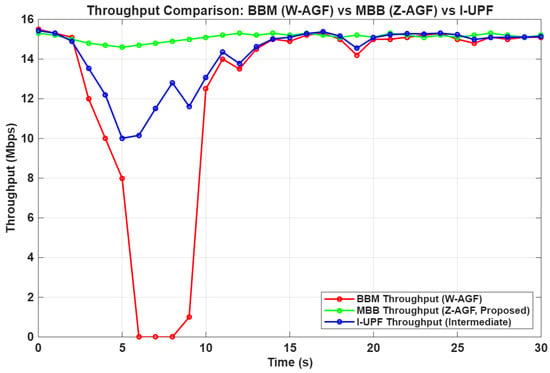
Figure 24.
Measured handover latency comparison between W-AGF baseline, I-UPF and Z-AGF setups. The Z-AGF with LBO achieves the lowest through CU-assisted coordination.
As shown in Table 2, the proposed Z-AGF achieves 45.6% reduction in the average handover latency relative to the baseline. This improvement arises from the pre-cached session contexts in the Session Persistence Engine (SPE) and reduced control signaling during inter-domain mobility. The LBO mechanism further eliminates redundant packet redirection, enabling sub-250 ms mobility crucial for URLLC and interactive streaming.

Table 2.
Comparison of Handover Latency Across Test Scenarios.
5.3. Packet Loss and Session Continuity
The Packet Loss Ratio (PLR) and Session Continuity Rate (SCR) were evaluated during mobility across the departmental gateways.
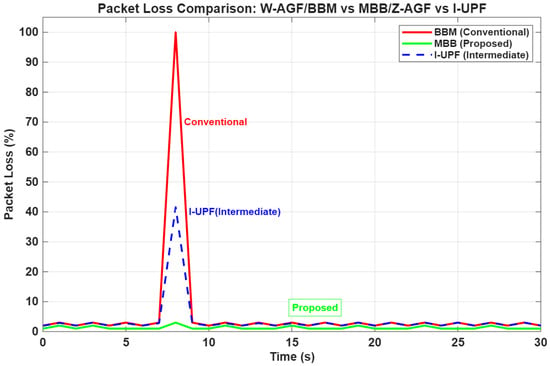
Figure 25.
Packet Loss Ratio and Session Continuity Rate comparison across configurations. Z-AGF maintains perfect session stability.

Table 3.
PLR and SCR Performance under Mobility Scenarios.
Z-AGF yields up to 69% packet loss reduction compared with the baseline and ensures 98.1% session continuity. This improvement results from the MBB handover procedures coordinated by the Z-CU and persistent NAS context caching. This mechanism ensures uninterrupted connectivity for latency-critical applications such as smart classrooms, telepresence, and industrial robotics.
5.4. Local Breakout and QoS Performance
The introduction of the Local Breakout Handler (LBH) within the proposed Z-AGF framework enables local traffic offloading to the campus domain, effectively bypassing the core UPF. This design significantly shortens the data path and enhances the Quality of Service (QoS) for Non-5G-Capable (N5GC) devices. Figure 26, Figure 27, Figure 28 and Figure 29 presents a comparative performance analysis across RTT, jitter, packet loss, and throughput metrics for the UPF/W-AGF and Z-AGF configurations.
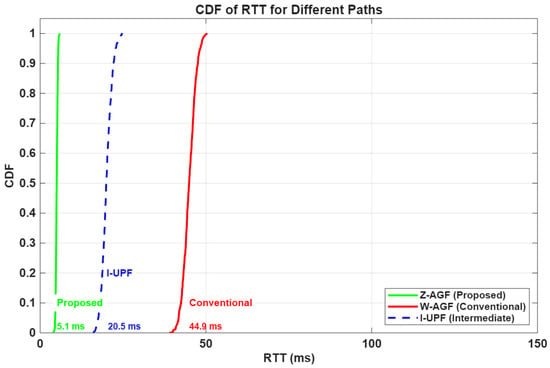
Figure 26.
CDF of RTT for different paths under W-AGF, I-UPF and Z-AGF configurations.
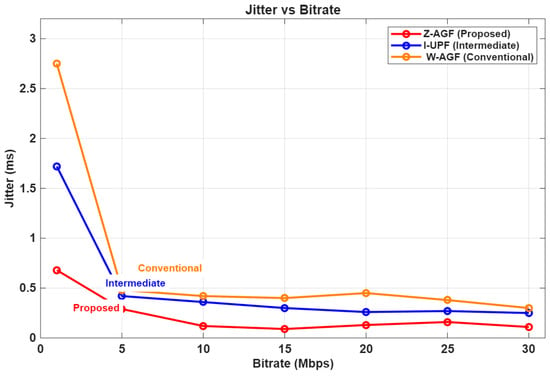
Figure 27.
Jitter versus bitrate comparison across W-AGF, I-UPF and Z-AGF.
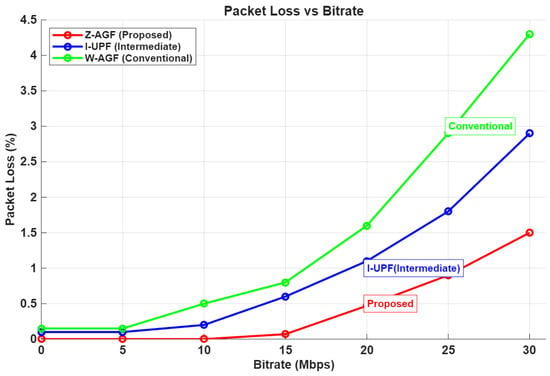
Figure 28.
Packet loss versus bitrate for W-AGF, I-UPF and Z-AGF architectures.
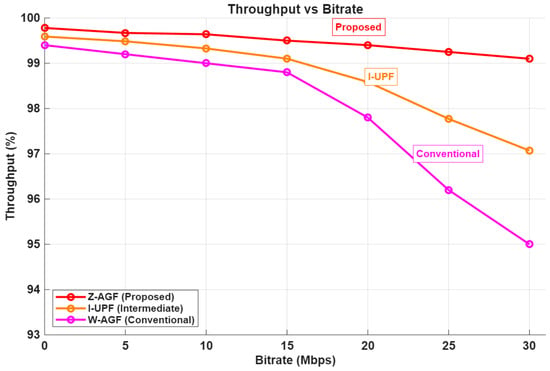
Figure 29.
Throughput versus bitrate for W-AGF, I-UPF and Z-AGF configurations.
As shown in Figure 26, the CDF curves indicate that the proposed Z-AGF achieves the lowest latency distribution, with a mean RTT of approximately 5.1 ms, compared to 44.9 ms for the conventional W-AGF. This demonstrates a latency reduction, highlighting the efficiency of the local breakout and direct CU coordination.
Figure 27 shows that jitter remains minimal and highly stable under Z-AGF operation, remaining below 0.8 ms across all tested bitrates. In contrast, W-AGF exhibits higher jitter (up to 3 ms at low bitrates) owing to extended routing through the CU and core interfaces. This stability underlines the effectiveness of the QoS Policy Control Unit (QPCU) in enforcing URLLC-grade traffic prioritization.
As illustrated in Figure 28, packet loss increases with bitrate for all cases, but the Z-AGF maintains the lowest loss ratio of only 0.13% at 20 Mbps and 2.7% at 30 Mbps compared to 4.4% for W-AGF. This reduction confirms that Z-AGF’s superior link stability and optimized flow control under high-load conditions.
Figure 29 demonstrates that Z-AGF sustains throughput above 99% efficiency across most bitrates, whereas W-AGF degrade to below 96% at higher loads. This highlights the improved bandwidth utilization achieved through local routing and the reduced signaling overhead. Overall, the combined results verify that the proposed Z-AGF with Local Breakout consistently enhances QoS by minimizing delay, loss, and jitter, while maintaining higher throughput stability. These improvements confirm its suitability for delay-sensitive and mission-critical applications within smart-campuses and industrial-IoT networks.
5.5. Functional and Resource Efficiency
Beyond latency and packet loss, Z-AGF significantly optimizes the resource usage. Figure 30 illustrates UPF CPU utilization across the architectures.
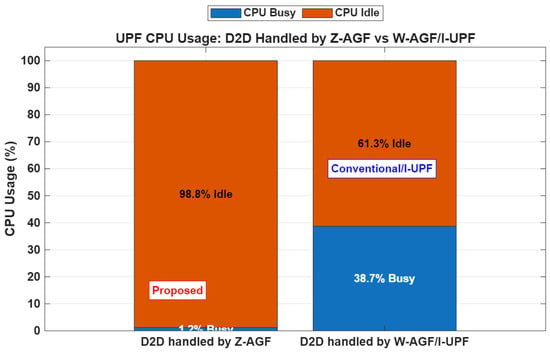
Figure 30.
UPF CPU utilization across architectures. Z-AGF offloading keeps UPF nearly idle during local traffic handling.
The UPF CPU load decreased from 38.7% at the baseline to less than 1.2% under Z-AGF offloading. This demonstrates the efficiency of the edge processing through the User-Plane Enhancement Function (UPEF). Table 4 summarizes the comparative functional capabilities.

Table 4.
Feature Comparison of W-AGF, I-UPF, and Z-AGF Architectures.
5.6. Security, Trust, and Policy Governance in LBO
The Z-AGF strengthens security by performing local authentication, tunnel validation, and CU-supervised session management, reducing exposure to core-network threats. Persistent NAS context caching prevents spoofing and hijacking during mobility, while the UPEF and LDN enforce data isolation and a zero-trust posture across departments.
To prevent rogue access or forged mobility signaling, FN-RG identity, L2TP tunnel parameters, and inter-Z-AGF mobility updates are cryptographically bound to the 5GC/NAS-authenticated context and transported over secure channels (e.g., IPSec/TLS), ensuring that unauthenticated devices, hijacked tunnels, or spoofed mobility events are rejected at the Z-AGF boundary. To maintain policy and charging integrity, Z-AGF integrates with PCF and CHF for localized enforcement equivalent to core processing. NEF/AF coordination ensures lawful exposure of network services and controlled application access. Overall, this LBO design combines low-latency routing with secure, trusted, and standards-aligned governance for N5GC devices in private 5G O-RAN environments.
5.7. Key Findings
The results confirm that Z-AGF substantially enhances the overall system performance while reducing network load and latency. The key observed improvements include the following:
- Up to 45.6% latency reduction during handovers.
- 69% packet loss reduction and 98.1% session continuity.
- 85.6% reduction of RTT for local communications under LBO.
- 98.8% UPF idle rate, validating the effective local offloading.
Overall, the proposed Z-AGF demonstrates robust, scalable, and low-latency connectivity for Non-5G-Capable (N5GC) devices. The synergy between CU coordination, MBB mobility, and localized breakout provides an adaptable foundation for URLLC-driven smart campus and industrial IoT applications.
6. Conclusions and Future Work
This study presents the design, implementation, and evaluation of the Zone Access Gateway Function (Z-AGF),which is a CU-coordinated framework designed to enable seamless mobility, session persistence, and localized data processing for Non-5G-Capable devices within private 5G networks. By combining mobility management, QoS control, and Local Breakout functionality, Z-AGF bridges the wireless and wireline domains while preserving O-RAN and 3GPP compliance. Experimental results verified that Z-AGF substantially improved handover responsiveness, reduced packet loss, and enhanced throughput stability, confirming its suitability for latency-sensitive and mission-critical applications in smart-campus environments.
Future work will enhance Z-AGF with AI-based mobility prediction, RIC/xApp integration, and decentralized authentication to improve intelligence and security. Further exploration will target 6G and multi-RAT integration, including Wi-Fi 7 and LiFi, along with edge computing support for latency-sensitive applications. The Z-AGF framework thus paves the way toward intelligent, autonomous, and latency-optimized Non-Public Networks.
Author Contributions
Conceptualization, A.H. and S.Z.D.; methodology, A.H.; software, A.H. and S.Z.D.; validation, J.-T.W., A.H. and S.Z.D.; formal analysis, A.H.; investigation, S.Z.D.; resources, J.-T.W.; data curation, A.H. and S.Z.D.; writing—original draft preparation, A.H.; writing—review and editing, A.H.; visualization, S.Z.D.; supervision, J.-T.W.; project administration, J.-T.W.; funding acquisition, J.-T.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Science and Technology Council (NSTC), Taiwan, under Grant No. NSTC-113-2221-E-011-067. The support of the NSTC is gratefully acknowledged.
Data Availability Statement
The dataset used in this study is publicly available in onedrive in hackmd at [42].
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| 3GPP | Third Generation Partnership Project |
| 5GC|5GS | 5th Generation Core|5th Generation System |
| 5G-RG | 5th Generation Residential Gateway |
| AGF|AF | Access Gateway Function|Application Function |
| AS|AMF | Access Stratum|Access and Mobility Management Function |
| ATSSS | Access Traffic Steering, Switching and Splitting |
| AUN3 | Authenticable Non-3GPP Device |
| AUSF | Authentication Server Function |
| BBF | Broadband Forum |
| BBM | Break-Before-Make |
| CDF | Cumulative Distribution Function |
| CHAP | Challenge-Handshake Authentication Protocol |
| CP | Control Plane |
| CPE | Customer Premises Equipment |
| CU | Centralized Unit |
| D2D | Device-to-Device |
| DHCP | Dynamic Host Configuration Protocol |
| DL | Down Link |
| DU | Distributed Unit |
| DN | Data Network |
| DOCSIS | Data Over Cable Systems Interface Specifications |
| DSL | Digital Subscriber Line |
| F1AP | F1 Application Protocol |
| FN-RG | Fixed Network Residential Gateway |
| FMC | Fixed-Mobile Convergence |
| FWA | Fixed Wireless Access |
| GPON | Gigabit Passive Optical Network |
| GTP-U | GPRS Tunneling Protocol - User Plane |
| GLI | Global Line Identifier |
| gNB | Next-Generation Node B |
| IoT | Internet of Things |
| IP/IPCP | Internet Protocol/IP Control Protocol |
| IPV6CP | IPV6 Control Protocol |
| IPoE | Internet Protocol over Ethernet |
| I-UPF | Intermediate-UPF |
| ISP | Internet Service Provider |
| MAC | Media Access Control |
| MBB | Make-Before-Break |
| N5GC | Non-5G Capable |
| NAS | Non-Access Stratum |
| NAUN3 | Non-Authenticable Non-3GPP Device |
| NEF | Network Exposure Function |
| NF | Network Function |
| NGAP | Next-Generation Application Protocol |
| NG-RAN | Next-Generation Radio Access Network |
| NIC | Network Interface Card |
| NPN | Non-Public Network |
| NR | New Radio |
| NRF | Network Slice Selection Function |
| NSSF | Network Exposure Function |
| L2TP | Layer 2 Tunneling Protocol |
| LAC | L2TP Access Concentrator |
| LBO | Local Breakout |
| LCP | Link Control Protocol |
| LDN | Local Data Network |
| LNS | L2TP Network Server |
| L-W-CP/UP | Legacy Wireline Access Control/User Plane Protocol |
| PCF | Policy Control Function |
| PDU | Packet Data Unit |
| PN | Public Network |
| PNI-NPN | Public Network Integrated NPN |
| PPP | Point-to-Point Protocol |
| PPPoE | Point-to-Point Protocol over Ethernet |
| PDCP-C | Packet Data Convergence Protocol - Control |
| PDCP-U | Packet Data Convergence Protocol - User |
| PHY | Physical |
| PSA-UPF | PDU Session Anchor - UPF |
| QoS | Quality of Service |
| RAN | Radio Access Network |
| RG | Residential Gateway |
| RLC | Radio Link Control |
| RRC | Radio Resource Control |
| RTT | Round-Trip Time |
| RU | Radio Unit |
| SUPI | Subscription Permanent Identifier |
| SCCRQ | Start-Control-Connection-Request |
| SCTP | Stream Control Transmission Protocol |
| SDAP | Service Data Adaptation Protocol |
| SMF | Session Management Function |
| SNPN | Standalone Non-Public Network |
| UDM | Unified Data Management |
| UDP | User Datagram Protocol |
| UE | User Equipment |
| UP/UL | User Plane/Up Link |
| UPF/UPEF | User Plane Function/User Plane Extension Function |
| W-5GAN | Wireline 5G Access Network |
| W-AGF | Wireline Access Gateway Function |
| W-CP/UP | Wireline Access Control/User Plane Protocol |
| WWC | Wireless Wireline Convergence |
| XGS-PON | 10-Gigabit Symmetric Passive Optical Network |
| Z-AGF | Zone-Access Gateway Function |
| Z-CU | Zone-Centralized Unit |
References
- Trick, U. 5G: An Introduction to the 5th Generation Mobile Networks; Springer: Berlin/Heidelberg, Germany, 2021. [Google Scholar]
- 3GPP TS 23.501 v17.9.0; System Architecture for the 5G System (5GS). 3GPP: Valbonne, France, 2024.
- Recommendation Y.3101; Framework of IMT-2020 Network Requirements. ITU-T: Paris, France, 2022.
- Broadband Forum. Access Gateway Function Functional Requirements for 5G; BBF TR-456 Issue 2; Broadband Forum: Fremont, CA, USA, 2023. [Google Scholar]
- 3GPP TS 23.316 v17.6.0; Access to the 5G Core via Fixed Access Networks. 3GPP: Valbonne, France, 2023.
- Broadband Forum. Functional Requirements for Hybrid Wireline-Wireless Networks; BBF TR-456 Corrigendum 1; Broadband Forum: Fremont, CA, USA, 2024. [Google Scholar]
- O-RAN.WG1.Architecture-v10.00; O-RAN Architecture Description. O-RAN Alliance: Alfter, Germany, 2023.
- 3GPP TS 23.502 v17.7.0; Procedures for the 5G System (5GS). 3GPP: Valbonne, France, 2024.
- 3GPP TS 29.502 v17.4.0; Session Management Services for the 5G System (SMF). 3GPP: Valbonne, France, 2023.
- Wu, J.; Zhang, L. MEC-Enabled Local Breakout for Low-Latency Services in 5G Networks. IEEE Access 2023, 11, 45678–45689. [Google Scholar]
- Sharma, A.; Choi, S. Low-Latency Path Optimization in Distributed UPF Architectures. IEEE Trans. Netw. Serv. Manag. 2023, 20, 1001–1012. [Google Scholar]
- Zhao, M.; Lee, Y.; Lin, P. Performance Analysis of MEC-Based Local Breakout in Edge 5G. IEEE Commun. Mag. 2023, 61, 70–77. [Google Scholar]
- Chen, Y.; Liu, J. O-RAN-Based Latency Benchmarking for 5G Private Networks. IEEE Access 2024, 12, 99901–99912. [Google Scholar]
- Broadband Forum. WWC Scenarios and Deployment Guidelines; BBF Report; Broadband Forum: Fremont, CA, USA, 2024. [Google Scholar]
- Li, R.; Peng, M.; Wang, C. Enhancing Mobility Management in O-RAN through CU Coordination. IEEE Commun. Mag. 2023, 61, 88–95. [Google Scholar]
- 3GPP TS 38.401 v17.4.0; NG-RAN Architecture and Functional Split. 3GPP: Valbonne, France, 2023.
- 3GPP TS 38.471 v17.5.0; F1 Application Protocol (F1AP). 3GPP: Valbonne, France, 2023.
- 3GPP TS 38.472 v17.3.0; Signaling Procedures for F1AP. 3GPP: Valbonne, France, 2023.
- 3GPP TS 38.413 v17.7.0; NGAP Protocol for 5GS. 3GPP: Valbonne, France, 2024.
- IETF. 5WE Encapsulation for Fixed Access Integration; RFC 8822; IETF: Vienna, Austria, 2021. [Google Scholar]
- Khan, R.; Kumar, P.; Jayakody, D.N.K.; Liyanage, M. A Survey on Security and Privacy of 5G Technologies: Potential Solutions, Recent Advancements, and Future Directions. IEEE Commun. Surv. Tutor. 2020, 22, 196–248. [Google Scholar] [CrossRef]
- Open5GS Project. Open Source 5G Core Network. Available online: https://open5gs.org (accessed on 25 October 2025).
- 3GPP TS 22.261 v17.2.0; Service Requirements for the 5G System (Stage 1). 3GPP: Valbonne, France, 2023.
- Broadband Forum. WWC Progress Report; BBF Technical Update; Broadband Forum: Fremont, CA, USA, 2024. [Google Scholar]
- CableLabs. 5G WWC Core Architecture Overview. Technical Report. 2023. Available online: https://www.cablelabs.com/ (accessed on 25 October 2025).
- Ren, L.; Xu, K. AI-Driven RIC/xApp Integration for Intelligent 6G Networks. IEEE Netw. 2024, 38, 55–62. [Google Scholar]
- Broadband Forum. WT-456: AGF Requirements for 5G RG/FN-RG; BBF Working Text; Broadband Forum: Fremont, CA, USA, 2023. [Google Scholar]
- 3GPP TS 24.502 v17.5.0; Non-Access Stratum (NAS) Protocol for 5GS. 3GPP: Valbonne, France, 2024.
- SCTE–ISBE. Authentication and Key Management for WWC Access. Technical Report. 2023. Available online: https://www.scte.org/ (accessed on 25 October 2025).
- 3GPP. 5G System Architecture Update; Release 17 Summary; 3GPP: Valbonne, France, 2024. [Google Scholar]
- Foukas, X.; Marina, M.K. 3GPP Core Network Evolution Toward Access-Agnostic 5G Systems. IEEE J. Sel. Areas Commun. 2022, 40, 1182–1196. [Google Scholar]
- Yousaf, F.; Fontanelli, P.; Iovanna, P.; Costa-Requena, J. A Survey on Converged Fixed-Mobile Access in 5G. IEEE Commun. Surv. Tutor. 2021, 23, 1954–1985. [Google Scholar]
- Ruffini, M.; Kaminski, N.; Marchetti, N.; Doyle, L.; Marquez-Barja, J.M. Optical and wireless network convergence in 5G systems—An experimental approach. J. Light. Technol. 2017, 35, 535–548. [Google Scholar] [CrossRef]
- Park, S.; Kim, Y. Experimental Evaluation of OAI and Open5GS Integration in Private 5G Networks. IEEE Access 2024, 12, 90900–90911. [Google Scholar]
- Nguyen, T.; Huang, P. Optimizing Distributed User Plane in Private 5G Networks. IEEE Access 2024, 12, 120340–120351. [Google Scholar]
- UERANSIM Team. 5G UE and RAN Simulator. Available online: https://github.com/aligungr/UERANSIM (accessed on 25 October 2025).
- Roaring Penguin. RP-PPPoE: PPP Over Ethernet. Available online: http://www.roaringpenguin.com/products/pppoe (accessed on 25 October 2025).
- OpenAirInterface Software Alliance. 5G RAN & Core Platforms. Available online: https://openairinterface.org (accessed on 25 October 2025).
- Internet Systems Consortium (ISC). ISC DHCP Server. Available online: https://www.isc.org/dhcp/ (accessed on 25 October 2025).
- Xelerance. xl2tpd: L2TP Daemon. Available online: https://github.com/xelerance/xl2tpd (accessed on 25 October 2025).
- MongoDB Inc. MongoDB Community Server. Available online: https://www.mongodb.com/try/download/community (accessed on 25 October 2025).
- Hitayezu, A. Zone-Access Gateway Function Data. Available online: https://hackmd.io/@rkT12RG1TWOl4CBfOlDE4w/BJ4nWnNcA (accessed on 9 November 2025).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).