In the original publication [1], concerns were raised regarding the following references, and they were removed from the reference list:
81. Vijayakumar, K.; Kumar, K.P.M.; Kottilingam, K.; Karthick, T.; Vijayakumar, P.; Ganeshkumar, P. An adaptive neuro-fuzzy logic based jamming detection system in WSN. Soft Comput. 2019, 23, 2655–2667.
109. Sumalatha, M.S.; Nandalal, V. An intelligent cross layer security based fuzzy trust calculation mechanism (CLS-FTCM) for securing wireless sensor network (WSN). J. Ambient Intell. Humaniz. Comput. 2021, 12, 4559–4573.
147. Nigam, G.K.; Dabas, C. ESO-LEACH: PSO based energy efficient clustering in LEACH. J. King Saud Univ.—Comput. Inf. Sci. 2021, 33, 947–954.
Due to the removal of the references, subsequent references and the corresponding citations in the main text have been adjusted to align with the numerical order. The following text has been updated.
In Section 2, “95 publications examined” was updated to “94 publications examined”.
In Section 5, the sentence “A fuzzy based jamming attack detection scheme by incorporating Fuzzy Inference System (FIS) (based on Takagi–Sugeno FL) and adaptive neuro-fuzzy inference system (ANFIS) is proposed in [81]. The two proposed methods make use of RSSI and packet delivery ratio (PDR) for jamming attack detection. The schemes are implemented in CH and BS to determine attacks at CMs and CH. The use of FL helps to optimize the used metrics for better identification of jammer attacks. The results indicate that the ANFIS-based scheme achieves better performance than the FIS-based scheme.” was deleted.
In Section 5, the sentence “A cross layer protection method based on fuzzy logic and trust values is proposed in [109]. It employs several parameters retrieved from cross-layer data to mitigate the impacts of safety threats in WSN. The fault tracking mechanism uses an enhanced CNN model based on trustworthiness to discover malicious nodes in WSN.” was deleted.
In Section 7, the sentence “The proposed technique improves the overall network performance by 10.00%, 23.75%, and 54.54% when compared to ESO [147], GECR [148], and LEACH [140]” was updated to “The proposed technique improves the overall network performance by 23.75% and 54.54% when compared to GECR [145] and LEACH [138].”
In Section 8, “Overall, 28% of papers applied SI followed by Hybrid by 21%, 21% for FL, then 19% for deep learning” was updated to “Overall, 29% of papers applied SI followed by Hybrid by 21%, 19% for FL, then 19% for deep learning”.
In Table 3, the row for reference [81] was removed.
Figure 3 was updated accordingly:
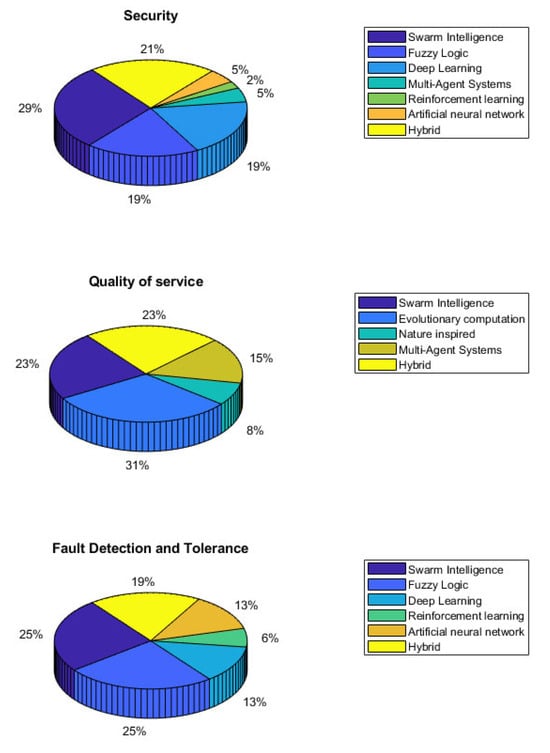
Figure 3.
AI approaches in relation to different WSN challenges.
The authors clarify that the scientific conclusions remain unchanged despite the removal of the references from the manuscript. These corrections have been approved by the Academic Editor. The original publication has also been updated.
Reference
- Osamy, W.; Khedr, A.M.; Salim, A.; El-Sawy, A.A.; Alreshoodi, M.; Alsukayti, I. Recent Advances and Future Prospects of Using AI Solutions for Security, Fault Tolerance, and QoS Challenges in WSNs. Electronics 2022, 11, 4122. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).