Abstract
The Internet of Things (IoT) is a transformative technology with significant potential across various applications. IoT enables everyday devices to become smarter, processes to become more intelligent, and communication to be more informative. As the fastest-growing field in Information Technology, IoT integrates objects into a virtual infrastructure that keeps us informed about their states. IoT devices include IT appliances such as PCs, mobile phones, laptops, smartwatches, and other wearable devices, which communicate through sensor-based embedded systems that transmit data. However, as the number of connected devices increases, so do the risks of connectivity and security breaches. These systems are often used in machine-to-machine communication, sharing vast amounts of data, which heightens the risk of intrusions. This survey systematically reviewed and analyzed 82 peer-reviewed studies published between 2010 and 2024, covering IoT security architecture, threats, and defense mechanisms. The review identifies key trends, common challenges, and security threats specific to IoT-based architecture across different domains. Additionally, it proposes solutions to enhance IoT security. The findings contribute to a deeper understanding of the current state of IoT security and offer insights into future research and the practical implementation of protective measures.
1. Introduction
The Internet of Things, usually known as IoT, is a new paradigm that intends to interconnect all smart physical items, with the end goal of the gadgets being able to offer consumers intelligent services when working together. The Internet of Things (IoT) is a system interrelated with digital technology, with a growth in predominant objects such as smart devices, robotic machines, sensors, etc. It has a strong connection with people, objects, and machines, with the ability to transform the world, the way business is performed, the way people communicate, the way robotic processes without human intervention, autonomous transportation, the way people live, play, and work in a smart city, smart retail, etc. IoT is the fastest-growing field in society. Most IoTs’ simple components are connectivity, data processing, user interface, and sensor. Connectivity for data transmission over the internet and the wireless network for data sharing and processing makes the data useful for the next action. The user interface performs data processing, e.g., the security system detects malware and the result, and the alert is sent to forensic analysis. Sensors for the automation of robotic processes, e.g., use the IoT device with a sensor as the security fender for building.
Apart from IoT’s facilities and services, some key issues are directly associated with it. One crucial issue is the security of all the devices, nodes, and networks in IoT. IoT devices are generally observed to be old and have unpatched security holes due to outdated software running on them, which can impose several security challenges on the IoT infrastructure. In this study, IoTs refer to RFID readers (ISO/IEC 18000-6C, UHF Gen2), MuleSoft Anypoint Platform (Mule Runtime version 4.x, SOA-based API integration), and smart appliances/devices/sensors used in manufacturing machinery/warehouse processes.
Different service providers like Microsoft, AWS, and Google are the key players in IoT. IoT applications rely on servers that, in today’s time, are mostly rented from third parties such as cloud platforms to store their data, retrieve data from anywhere through the internet, market their products, collaborate among users, vendors, and business partners, and many more [,,,,,,,,,]. As the IoT domain grows exponentially, the security threats attached to this field also increase. One possible measure to protect our systems and data from being compromised is restricting network access to potentially risky systems and devices, continuously monitoring them for anonymous traffic and malicious activities, and taking appropriate steps and measures accordingly [,,,,,,,,,].
A potential new technology called IoT may be used to enhance the workings of many industrial systems. It is possible for aquaculture farmers to easily monitor water parameters, such as pH, temperature, and more, using IoT-based intelligent systems. The farmer may use it to make informed assumptions about what must be achieved to guarantee the fish’s healthy growth. A network may now be established for all present systems, thanks to the IoT. Systems may communicate with one another and their environment through this network, allowing some action to be conducted. To link all the devices to a network, each one needs a unique identification known as an IP address. An IP address may be used to find and identify a device on a network, and it can also be used to route data. The most often accepted definition of the Internet of Things is “A network of physical objects or ‘things’ that may interact with each other to exchange information and take action.” Alternatively, “the IoT is the connection of individually identifiable embedded computer devices inside the present Internet infrastructure” [,,,,,,,,,].
Earlier IoT deployments often relied on IEEE 802.11n for wireless connectivity, which was a common standard in home and office environments. However, current implementations increasingly adopt more recent standards such as 802.11ac (Wi-Fi 5), 802.11ax (Wi-Fi 6/6E), and 802.11be (Wi-Fi 7). These newer generations offer significantly higher throughput, lower latency, and enhanced reliability, which are critical for supporting large-scale IoT applications. While our discussion retains references to earlier standards to illustrate the historical evolution of IoT connectivity, our focus remains on how these wireless technologies interact with IoT security architectures and threat models.
Compared to existing surveys, the contribution of this work is threefold. First, it consolidates IoT security research from both architecture-centric and threat-centric perspectives, providing a holistic view that connects technical layers to corresponding vulnerabilities and defenses. Second, it integrates the three-layer IoT reference model with the expanded five-layer architecture, offering readers a clear mapping between different conceptual frameworks. Third, it highlights not only established security mechanisms but also emerging challenges and future directions, thereby serving as both a reference for current knowledge and a roadmap for ongoing research. This broader scope distinguishes our survey from prior reviews that often focus on only a single layer, a specific class of attacks, or narrow technological domains.
The remainder of this paper is structured as follows. Section 2 presents the research methodology and explains the systematic review process. Section 3 provides background on IoT architecture and related concepts, while Section 4 discusses the layered models, mapping the three-layer and five-layer perspectives. Section 5 reviews IoT protocols and standards that underpin communication and interoperability. Section 6 examines major IoT security threats across different layers. Section 7 outlines the key technical challenges that continue to hinder secure IoT deployments. Section 8 highlights security best practices and countermeasures recommended in the literature. Finally, Section 9 concludes the paper and discusses future research directions.
2. Research Methodology
2.1. Research Methods
This research uses Software Engineering Criteria from a Systematic Literature Review (SLR). This systematic review was conducted in accordance with the PRISMA 2020 (Preferred Reporting Items for Systematic Reviews and Meta-Analyses) guidelines. A PRISMA flow diagram is provided in Figure 1, illustrating the process of identification, screening, eligibility, and inclusion of studies.
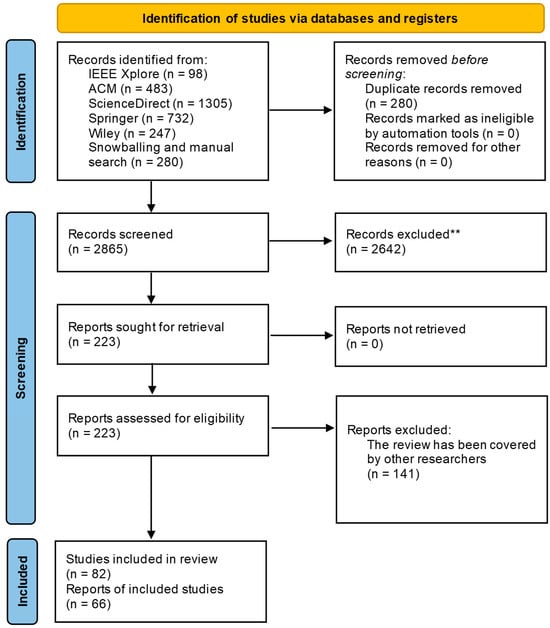
Figure 1.
PRISMA flow diagram. ** Records excluded after title and abstract screening due to duplication, irrelevance to IoT architecture or security, non-English language, or non-peer-reviewed sources.
To ensure transparency and reproducibility, we employed specific search strings and keywords such as “IoT”, “IoT security”, “IoT architectures”, “IoT threats”, “IoT defenses”, “IoT cloud”, and “machine learning for IoT”. Searches were conducted across the following digital libraries: IEEE Xplore, ACM Digital Library, ScienceDirect, SpringerLink, and Wiley Online Library. The inclusion period was set from 2010 to 2024, with the justification that while the majority of sources fall within the last five years (2020–2024) to capture the latest developments, earlier works have also been retained where they represent seminal contributions that remain foundational in the IoT security literature. This balance ensures both historical context and contemporary coverage.
To ensure the quality and relevance of the reviewed literature, we applied specific inclusion and exclusion criteria during the screening process. The inclusion criteria were as follows: (i) peer-reviewed journal and conference papers, (ii) studies published between 2010 and 2024, (iii) publications written in English, and (iv) works directly addressing IoT architectures, security threats, or defense mechanisms. The exclusion criteria were as follows: (i) non-peer-reviewed sources such as blogs, white papers, or technical reports, (ii) duplicate records across databases, (iii) studies limited to abstracts or posters without sufficient methodological details, and (iv) works not primarily focused on IoT security (e.g., general networking or unrelated application domains).
In addition to applying inclusion and exclusion criteria, we conducted a quality assessment of the selected papers to ensure their methodological rigor and relevance. Each paper was evaluated based on the following criteria: (i) clarity of research objectives and scope, (ii) appropriateness of methodology, (iii) contribution to IoT security in terms of architecture, threats, or defenses, and (iv) publication venue quality (peer-reviewed journal or reputable conference). Papers that did not meet a minimum threshold across these dimensions were excluded from the final set. This process ensured that only high-quality and relevant studies were included in the survey.
2.2. Research Questions (RQ)
We prepared several research questions (RQ) before searching for and choosing publications related to the topic. The research questions provide a basis for the subsequent steps in the review process, which include extracting data, establishing inclusion and exclusion criteria, and constructing search strings.
The following are the problems that have been articulated in the research:
- RQ 1: What is the Internet of Things (IoT), and what are the fundamental IoT architectures proposed in the literature?
- RQ 2: What are the advantages and limitations of different IoT architectures across the technical layers?
- RQ 3: How are different IoT architectural models (e.g., three-layer and five-layer) related, and how can they be mapped to each other?
- RQ 4: What are the main security threats, challenges, and opportunities associated with IoT architectures, and how have researchers proposed to address them?
Articles related to research were discovered in the following libraries:
- IEEE Xplore, http://ieeexplore.ieee.org, offers a specialized and comprehensive collection of high-quality scientific and technical literature relevant to the IoT field.
- The ACM digital library, https://dl.acm.org, provides a rich repository of peer-reviewed articles and conference proceedings in computer science and related fields, offering a comprehensive source of recent, credible research on IoT topics.
- ScienceDirect, http://www.sciencedirect.com, has an extensive collection of peer-reviewed articles and journals in various scientific disciplines, particularly computer science and engineering. It provides a valuable resource for accessing recent and credible research relevant to IoT topics.
- SpringerLink, https://link.springer.com, has many articles and books on scientific and technical disciplines, notably computer science and engineering.
- Wiley, https://onlinelibrary.wiley.com/ is a digital platform that provides access to various scholarly journals, books, reference works, and databases across various disciplines, including science, engineering, technology, and more.
To ensure clarity between surveyed content and the contributions of this paper, we structured the review around the following research questions, as shown in Table 1:

Table 1.
Research questions (RQs) guiding this survey, with their focus and corresponding sections in the manuscript.
In addition to addressing these research questions through a systematic survey of the literature, this paper introduces several new contributions that go beyond existing reviews:
- Integration of perspectives—consolidating IoT research from both an architecture-centric and a threat-centric view.
- Explicit mapping of models—providing a one-to-one correspondence between the three-layer and five-layer IoT architectures, which is rarely addressed in earlier surveys.
- Updated coverage—including recent literature up to 2025, ensuring contemporary relevance in a fast-evolving field.
- Emerging directions—identifying future challenges such as lightweight cryptography, blockchain-based trust, and post-quantum security, offering a roadmap for future research.
2.3. Data Extraction
Our research questions are based on the current state-of-the-art IoT-based architectures, different security threats, and the selected articles about possible solutions or measurements.
2.4. Inclusion and Exclusion Criteria
We looked for publications based on their abstracts, keywords, and titles. In the second phase, we added articles on state-of-the-art IoT-based architectures, different security threats, and selected articles about possible solutions or measures.
In addition, we did not include papers that other researchers had not reviewed, were published in a language other than English, were repeats of previous articles, or were of poor quality in other languages.
3. Terminologies
3.1. IoT Architecture
As so many devices are involved in the Internet of Things, no architecture has been devised. The Internet of Things [,,,,,,,,,,,,,,,,,,,] has been proposed with various topologies in mind. Depending on the kind of application, a certain architecture may be more suited for implementation.
3.2. Three-Layer Architecture of IoT
The architecture of IoT is generally conceptualized as comprising three interrelated layers, with each layer dedicated to a particular aspect of data flow and network functionality [,,]:
- Physical layer: The physical layer, also called the perceptual layer, incorporates vital components such as RFID tags and sensors into its construction. It is responsible for sensing and collecting the required data from the linked devices.
- Network layer: The network layer provides a gateway. It handles routing protocols, information connected to servers, and data transfer. Logical network pathways transport data.
- Application layer: The application layer is the top layer. It is accountable for transmitting data to the specified location as necessary. The Internet of Things has three layers, as shown in Figure 2.
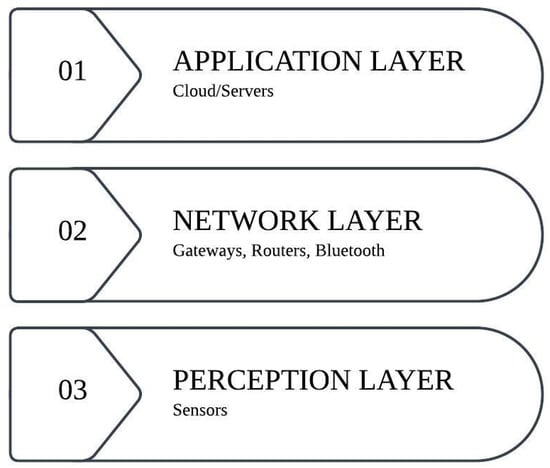
Figure 2.
Three-layer model of IoT.
The most significant drawback of this design is that more tasks will be assigned to a single layer, which makes changing a single layer or numerous layers challenging [,].
3.3. Cloud-Based Architecture
As described in Figure 3, the cloud-based architecture of IoT mainly contains the physical layer, process layer, gateway layer, and cloud services [].
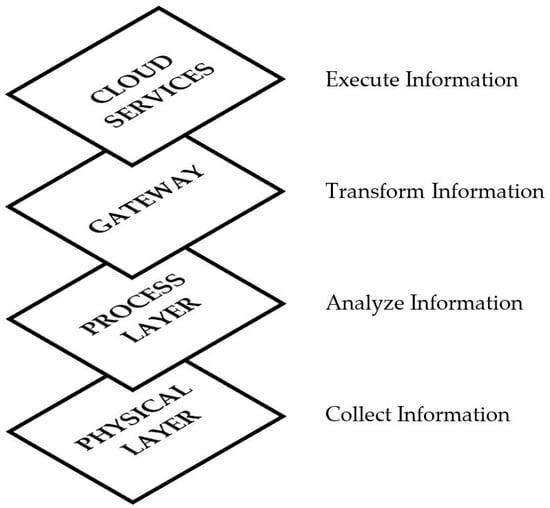
Figure 3.
Cloud-based architecture of IoT information in a database.
Furthermore, Figure 4 shows cloud services below. Using a server gives you easier access to the data and reports, makes it easier for the user to understand the information, and provides some advice. A fire alarm is an example of a high-priority interruption. In a crisis, it prompts the implementation of specified actions.
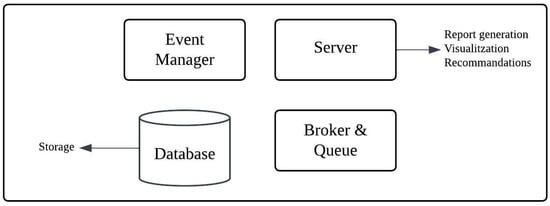
Figure 4.
Cloud services.
3.4. Fog-Based Architecture
Cloud computing is the most cutting-edge technology, and its capabilities have skyrocketed []. Fog computing provides data processing, storage management, and network information exchange between clients and cloud service providers. It uses a decentralized approach to computing and data processing. By collaborating this way, clients may delegate computing, storage, and resource management tasks to the cloud. Figure 5 depicts the fog-based architecture.
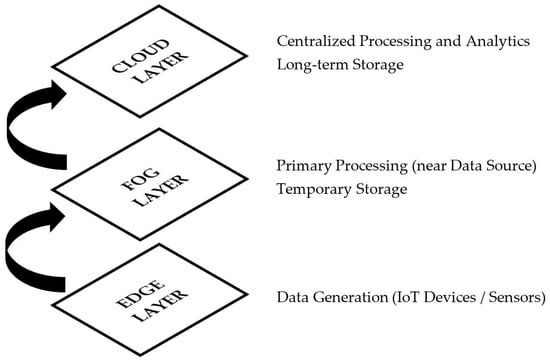
Figure 5.
Fog-based architecture.
Cloud computing architecture and fog computing architecture are essentially the same. Processing occurs on discrete devices at the network’s edge to differentiate this system from others []. Fog computing is also known as computing at the periphery or edge. As previously stated, this system is more scalable than cloud-based designs [,,,,].
3.5. Service-Oriented Architecture of IoT
In most commercial applications, this reference model is used in some capacities. IoT’s service-oriented architecture (SOA) [] is shown in Figure 6.
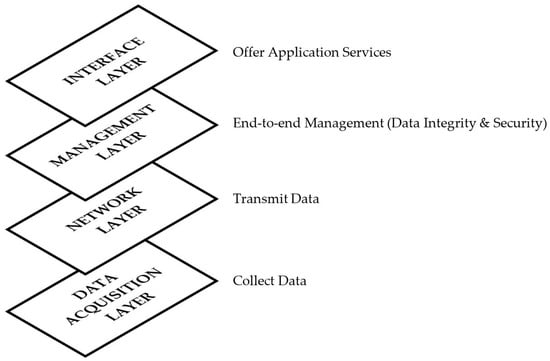
Figure 6.
SOA for IoT.
Similarly, the data collection layer is like the perception layer in terms of its function. It tries to identify the data and transfers it to the network layer by using an IP address. It is also responsible for data processing (via data processing techniques). The network layer handles communication protocols. It might be a wired or wireless network. Protocols such as Z-wave, Zigbee, etc., are often used [,,,,,]. The management layer is responsible for ensuring the integrity of the whole system. It checks whether the data was correctly sent to the other end. Additionally, it helps to ensure the integrity and security of the information that is being stored. It ensures that the information is sent to the appropriate person. Alternatively, the phrase “Business layer” is used to describe this layer of code. It is often referred to as the application layer. Additionally, it handles data formatting and display. It provides users and other applications with information about interaction strategies.
An Internet of Things system’s network and protocol layer includes components including Wi-Fi, Zigbee, Ethernet, Bluetooth, LTE, and 5G, as well as a range of additional wireless and wired network protocols. The transport layer includes protocols such as TCP/IP, UDP/IP, Transport Layer Security (TLS), and Secure Sockets Layer (SSL). Various application protocols have been created to suit the IoT criteria of low power consumption and tiny device capacity, such as AMQP, CoAP, and Message Queuing Telemetry Transport (MQTT). AMQP, which stands for Advanced Message Queuing Protocol, is what we use for the application layer [,,]. Constrained Application Protocol (CoAP) is its full name (MQTT). The data and cloud services layer presents the key cloud-based Internet of Things framework. The IoT architecture is shown in Figure 7 [,,,,,,].
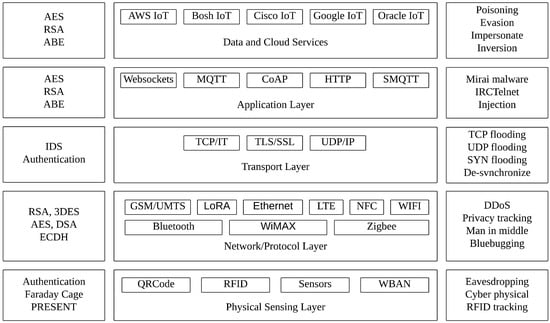
Figure 7.
IoT Architecture and IoT security architecture.
From the reviewed architectures, it is clear that there is no single universal design for IoT. Instead, architectures vary depending on application domains and system requirements. The three-layer model remains the simplest and most widely referenced framework, but its limitations such as overloading certain layers have led to the adoption of more complex designs, including cloud-based and fog-based architectures. Cloud-centric approaches provide scalability and centralized data management, while fog and edge architectures address latency and bandwidth issues by enabling distributed processing closer to devices. This diversity shows that IoT systems must adopt context-specific architectures, where the choice of model is influenced by trade-offs between scalability, latency, energy consumption, and security.
4. IoT and Its Layers
In earlier sections, IoT architecture was introduced using a three-layer model (perception, network, and application). For greater granularity, this section expands this into a five-layer model:
- Perception layer (equivalent to Perception layer in three-layer model): Responsible for sensing and collecting data (e.g., RFID, sensors, QR codes). Security controls: secure boot, device authentication, physical tamper resistance, and lightweight encryption for sensor data.
- Network layer (equivalent to Network layer in three-layer model): Handles data transmission via protocols such as Wi-Fi, Zigbee, LTE, and 5G. Security controls: end-to-end encryption (TLS/DTLS), intrusion detection, secure routing, and traffic filtering.
- Middleware layer: Provides data aggregation, processing, and service management. Security controls: access control, API security, secure cloud interfaces, and anomaly detection for service requests.
- Application layer (equivalent to Application layer in three-layer model): Manages end-user applications (e.g., smart homes, healthcare, transport). Security controls: role-based access, strong authentication (e.g., MFA, biometrics), and secure APIs.
- Business layer: Aligns IoT systems with organizational objectives, compliance, and governance. Security controls: policy enforcement, regulatory compliance (e.g., PDPA, HIPAA, GDPR), auditing, and SLA monitoring.
Figure 8 shows a generic IoT architecture based on application, network, and perception layers with interface components. Security elements are highlighted in the network and perception layers, as these layers are most critical for safeguarding device authentication, data transmission, and integrity. Bluetooth is shown under the LAN and Access Network categories to reflect its role in short-range connectivity within broader IoT communication pathways, though it is also commonly classified as part of the Personal Area Network (PAN). This figure is intended to provide a simplified, conceptual overview rather than an exhaustive taxonomy of all networking protocols.
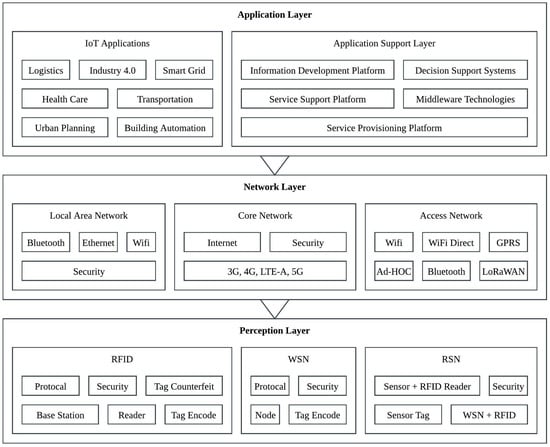
Figure 8.
A generic IoT architecture based on application, network, perceptions layers, and interface components.
4.1. Perception Layer
This layer is the OSI model’s physical layer. In this case, it includes various material instruments and objects, such as QR codes, RFID tags, infrared cameras, etc. There is a chance that other ecosystem components might also make an appearance []. Internet and communication networks meet at this level, earning the nickname “the nexus.” Detecting and identifying an additional intelligent object in the immediate surroundings is the job of this layer. For example, this layer collects and identifies the data and information acquired by sensor nodes, including position, speed, vibration, humidity, and air quality. This layer is often related to design management. After obtaining this data, it is securely communicated to the central system through the network layer. This layer facilitates communication across devices in the same physical space. Ethernet, a low-cost solution for consistent device connectivity, near field communication (NFC), which permits contactless payment between two devices, and Bluetooth are some instances of this communication. Wireless 802.11 allows homes and offices to communicate with each other within a specific range and consumes energy continuously throughout the day. In contrast, Long-Term Evolution (LTE) allows mobile devices to transfer high-speed data, supports wireless connectivity, and broadcast streams. Allowing many devices to share an internet connection over Wi-Fi is possible with Wi-Fi hotspots. These signals are sent using certain frequencies, such as 2.4 GHz or 5 GHz [,,].
4.2. Network Layer
At the network layer, there is a layer of object abstraction. The routing and encapsulation layers transport data packets from their point of origin to their eventual destination. Additionally, it must guarantee that the information that has been acquired is delivered securely and that it is safeguarded from other sensor nodes during the whole transmission process utilizing any sort of network, such as WCDMA, LTE, and UMTS. Consequently, data transmission between the perceptual and middleware levels is mostly the responsibility of the network layer. Many contemporary networks use IPv4 for device connectivity and network traffic routing. IoT data connection frames are becoming lighter and shorter, and IPv6 datagrams are being encapsulated in several short data link frames. It is possible to identify and locate devices on the network using IPv6 and routing internet traffic [].
4.3. Middleware Layer
The administration and storage of data from the lower levels are two of the most important duties of the middleware layer. Many IoT devices contribute to creating services as part of the network or system [,]. As a bonus, the middleware [,] may use the data obtained to extract, computerize, and analyze relevant information to draw appropriate conclusions.
4.4. Application Layer
The application layer is located between the business management layer and the application and service management levels []. This layer handles the administration of end-user applications, and the information it receives from the middleware is used to make this decision. E-Systems based on the Internet of Things, such as smart health, smart eyewear, smart automobiles, smart transportation, and smart homes, may be used in various applications. Provided interfaces and protocols may be found in this layer, including the Data Distribution Service (DDS), Advanced Message Queuing Protocols (AMQP), and Constrained Application Protocols (CAP) []. DDS streamlines the procedures necessary to connect a device to a high-speed network, making it simpler and more dependable. To exchange messages across computer systems, software applications, and hardware, AMQP provides interoperability between middlewares. A primary goal of CoAP was to limit the capabilities of both the device and the network. The secure connection between the CoAP endpoints is made possible by the use of UDP in the HTTP architecture. CoAP’s Quality of Service (QoS) is a resource discovery and content negotiation component []. It is used to keep track of all the communications being sent out.
4.5. Business Layer
This layer represents the topmost level of the IoT architecture and is responsible for translating data insights and system outputs into strategic decisions, policies, and actions []. Unlike the technical layers beneath it, which focus on sensing, transmission, and processing, the Business Layer ensures that IoT deployments align with organizational objectives, regulatory frameworks, and end-user requirements. This includes defining security and privacy policies, enforcing compliance with standards (e.g., GDPR, HIPAA, PDPA), managing service-level agreements (SLAs), and setting rules for data governance. Furthermore, the Business Layer provides feedback to the lower layers by determining priorities such as which data streams require stricter protection, what level of reliability is acceptable, and how resources should be allocated. In this way, the Business Layer connects technical functions to business value and societal impact, ensuring that IoT systems are not only operationally secure but also ethically and economically sustainable.
The transition from the three-layer to the five-layer IoT architecture provides greater granularity and clarity in understanding how IoT systems function and where vulnerabilities may arise. By explicitly introducing the middleware and business layers, the five-layer model highlights critical functions often overlooked in simpler frameworks, such as data aggregation, semantic processing, policy enforcement, and compliance management. This layered separation not only aids in mapping technical functions to business objectives but also clarifies where security controls such as encryption, access management, and data governance must be applied. Overall, the five-layer view offers a more comprehensive framework for aligning IoT’s technical complexity with organizational and societal requirements.
5. IoT Protocols and Standards
Electronic gadgets can communicate with one another thanks to the Internet of Things protocols. Multiple protocols have been created to satisfy the vast range of applications. In addition to IEEE and W3C, several associations and organizations have given standardization and support for protocols for the IoT []. These groups and organizations support applications, infrastructure protocols, technological services, and other important protocols. The following are just a few of the many specifications that support IoT protocols and standards: WiFi 802.11n protocols, which today are used by many developers for higher throughput in the range of a hundred megabits per second and a standard in home and office settings []; IPv6 low-power PAN for header compression and encapsulation; Bluetooth version 4.2, which combines low energy core and basic data rate for radio frequency transceivers (RF transceiver) [,,]. IoT protocols must be in place for communication devices, including rules for data exchange transmission and reception via the internet and other networks. Contrarily, fragmentation in IoT led to its heterogeneity, which derives from the diversity of IoT technologies and the standard it strives to fulfill. In the IoT, numerous IoT devices apply unique protocols and functionality in connectivity, data transmission, and device management [,,,,,,].
Artificial Intelligence and IoT
IoT gathers large amounts of data to be sorted and analyzed by AI interfaces to detect patterns and predict the needs for processing []. AI continues to shine when it has to innovate new ways that offer additional benefits to individuals or enterprises. Most organizations and Fintech have adopted AI-power self-help functions to reduce call center workloads. Introducing AI-enabled functions in applications for most of us to manage transactions, balances, and payments over smartphones became a high-frequency finance activity in our daily lives. Intelligence applications with security integration, such as two-factor authentications and fingerprint access, further strengthen financial validation. It has a secure peer-to-peer connection with the user and the financial institutions with two-factor authentication, safely using smartphones for service and app transactions.
In the application layer, vulnerable websites and IoT architectures have limitations that can be a threat target in an IoT framework [,,,,,,,,]. Therefore, to prohibit malicious users from changing settings, IoT gateways need to be configured with security protocols. In the application layer, adding biometrics and multi-level authorization of accessibility control might be a successful approach. Based on the changing patterns of safety threats, emerging layer-based safety problems and potential defensive measures have been proposed [,,,,,,,,]. The table presents some of the existing threats and potential prevention methods. As illustrated in Table 2, the perception level faces many safety problems. It could be due to various factors like simple physical access to endpoint nodes, internet applications with insecure devices, and non-secured networking infrastructure. Therefore, it can be inferred which key threat layer for the opponents is physical devices or endpoint nodes for IoT systems, as shown in Table 3.

Table 2.
Possible threats of WSN and RFID.

Table 3.
Problems in IoT protection and the countermeasures.
IoT relies on a wide range of communication protocols and standards, each tailored to different connectivity, energy, and application requirements. While this diversity enables flexibility, it also introduces heterogeneity and fragmentation, making interoperability and unified security approaches a continuing challenge. The emergence of AI-integrated IoT demonstrates how intelligent systems can enhance data processing and security, particularly in applications such as financial services and multi-factor authentication. However, the coexistence of multiple protocols and device types means that IoT security must be applied consistently across heterogeneous environments, with future work focusing on interoperable standards and AI-driven adaptive defenses.
6. IoT Security Threats
6.1. IoT and Security
IoT manages protocols and standards in hardware and software platforms and offers security and authentication within the user interface []. Zero-downtime deployment for containers like AWS containers and Microsoft Kubernetes for DevOps and IoT projects can scale elastically without impacting production and ease IoT deployment. The cloud service provider provides computation resources automatically in the provision, scalability, manageability, and dynamic ability of the applications and infrastructure requirements, whether for coding, serverless, auto-billing service, etc. Testing the DevOps with multiple IoT devices to be performed seamlessly integrates data from other sources to offer a visualization when interacting with devices and people. Mixed reality displays important IoT graphical data in real-world objects or workspaces and show centers. Virtual reality has inspired technological advancements in services, transportation, and manufacturing. IoT produces a large volume of data; specialized processes and tools are required to turn the data into actional insight. Not limited by predictive maintenance or real-time decisions, it has included the challenge of data storage, processing, and IoT security, safety, and privacy. Security in data stores and processes is a serious consideration in IoT platforms before IoT can be transformed into business operations. IoT security such as AWS IAM, Azure Sphere, and Azure Digital Twins threat modeling offer security measures for attack detection and prevention from different attacks. End-to-end security approaches protect data, devices, and connections, from device security to connectivity between devices, the cloud, and the internet, as well as data on the internet and cloud during processing and storage []. IoT threats like spoofing, DoS, the elevation of privilege, tampering, and information disclosure are common attacks in IoT infrastructure. Organizations can take measures by learning how likely threats are, examining threats to OS, IoT apps, cloud, and data storage, selecting evaluation strategies based on the unique threat patterns that can be identified, understanding the risks and consequences of the threats, and considering the advice from the experts are great ways to build support to move forward with the comprehensive IoT security roadmap. Monitoring of all connected devices for security analytics and remediation quickly is also important. By tracking all connected devices and data storage that work within IoT infrastructure, the security manager can make sure IoT apps are protected and the security of IoT is effective [].
6.2. Design Principles for IoT
Universally applicable design principles for IoT are generally best practices across all IoT deployments. These principles include the following:
- Security must be an integral part of the IoT system from design to deployments, e.g., use secure authentication for smart homes, industrial IoT, healthcare IoT, etc.
- Scalable for systems to handle growing numbers of devices and increased data volume without additional sensors or devices, e.g., uses scalable protocol like MQTT protocol for smart cities, connected vehicles, agricultural IoT.
- IoT devices and systems interoperability where they work seamlessly with other devices, platforms, and protocols. Uses standardized communication like RESTful APIs for IoT systems requiring cross platform interaction [,].
- IoT systems operate reliably with minimal downtime by adhering redundancy and failover mechanisms, able to handle robust errors handling in critical healthcare systems, industrial automation systems, and connected infrastructure.
- Able to optimize power consumption, especially battery-operated devices such as wearables that use Zigbee protocol with low-power communication; it has idle mode, such as remote monitoring system with sleep mode for idle devices.
- Privacy by design ensures user data is collected and processed with privacy protection in mind. Consumer IoT, healthcare IoT, and financial IoT are examples of how IoTs anonymize personal data and limit data collection to what is strictly necessary.
Whereas, on the other hand, industry-specific design principles for IoT, addressing the unique needs of individual industries, specifically include the following:
- Healthcare IoT—Remote patient monitoring of adherence to regulations like HIPAA and GDPR for patient data which is designed for audit trails and compliance verification []. Monitoring in a real-time manner prioritizes ultra-low-latency communications for life-critical systems. It uses fail-safe mechanisms to handle device malfunctions so the ability handling fault tolerance for the system can continue to operate correctly in the event of hardware or software failure.
- Industrial IoT—Smart manufacturing with operational technology integration ensure compatibility with legacy operational systems like SCADA. It uses protocols like TSN for time-sensitive manufacturing processes, providing design for harsh environments such as extreme-temperature environments, vibrations.
- Connected vehicle—Autonomous driving that uses 5G for rapid data exchange between vehicles and infrastructure; it uses ultra-reliable low-latency communication (URLLC) that ensure systems can operate safely during communication failures or hardware malfunctions. 5G-based Telematics autonomous driving with millimeter wave communications method and automatic obstacle avoidance to simulate the experiment for vehicle synchronization rate responses [].
- Smart agriculture—Precision farming often requires wide-area coverage supported by long-range communication protocols such as LoRaWAN. LoRaWAN builds on LoRa, a chirp spread spectrum (CSS)-based modulation technique at the physical layer that enables low-power transmission over long distances. The LoRaWAN protocol stack adds medium access control, device authentication, and secure data exchange, making it well suited for energy-constrained devices deployed across large and remote agricultural fields. In practice, LoRaWAN is often combined with solar-powered monitoring stations to reduce battery dependence and sustain operations. By enabling robust, low-cost, and energy-efficient connectivity in rural environments, LoRaWAN plays a key role in precision agriculture, a transformative approach that integrates IoT with farming practices to optimize irrigation, crop monitoring, and yield prediction []. Moreover, while LoRaWAN has been widely adopted due to its balance of long-range coverage and low power consumption, recent research has proposed enhanced modulation techniques, such as dual-mode chirp spread spectrum (CSS) and dual-mode time-domain multiplexed CSS, which aim to further improve spectral efficiency, interference resilience, and overall performance in large-scale IoT deployments [].
- Smart cities—Traffic management for massive scalability which handle millions of connected sensor and devices in dense urban areas. Inter-agency data sharing and supporting interoperability between municipal systems such as traffic lights. Resilience to attacks mitigates risks of cyber-attacks that could disrupt essential services like electricity.
To summarize both of their differences, the applied universal and industry-specific principles are tabulated in Table 4. Table 4 provides a comparative overview of universally applicable vs. industry-specific IoT security principles. The examples given are illustrative rather than exhaustive, intended to highlight how general design considerations (e.g., encryption, scalability, interoperability) are adapted to meet the unique requirements of specific domains such as healthcare, smart cities, industry, and agriculture.

Table 4.
Comparison table between universal vs. industrial-specific principles.
6.3. Security Challenge of IoT
IoT is associated with connected devices and networks in the ecosystems, with common security threats listed below:
- Many IoT devices have default usernames and passwords, and people often neglect to change them. Or, default settings are being used. Attackers can exploit this by gaining unauthorized access to devices or networks [].
- IoT devices are not regularly updated and patched, leaving them vulnerable to known exploits. Manufacturers and users must ensure that devices are promptly updated to address security vulnerabilities.
- IoT devices often transmit data over networks without encryption or weak encryption, leading to data interception and unauthorized access to sensitive data.
- Authentication and authorization are absent. A weak or absent authentication mechanism allows unauthorized individuals to access devices, compromising security and potentially affecting the entire network or IoT networks.
- Physical access to IoT devices can be a significant security risk. Attackers with physical access can tamper with the devices or extract sensitive information directly.
- IoT becomes targeted in DoS or DDoS attacks, in which the attacker overwhelms the device or network with excessive traffic, rendering it unresponsive or unavailable.
- Compromised IoT devices can be recruited into botnets and used for malicious purposes, such as launching DDoS attacks or mining cryptocurrencies. IoT malware can exploit vulnerabilities to gain control over devices.
- Poor device management, such as not decommissioning or updating devices, can create security risks, as outdated devices may have known vulnerabilities to exploit.
- Privacy concern: IoT devices often collect and transmit sensitive user data. Inadequate privacy protection can lead to unauthorized access, data breaches, or abuse of personal information.
IoT’s rapid growth and spread have caused several security vulnerabilities and threats. Since the Internet of Things is based on the internet, security threats and challenges related to the internet can also be observed. From the internet point of view, IoT architecture has three main layers, the perception layer, the transportation or network layer, and the application layer, which faces challenges in each layer [,,,,,,,,,].
IoT challenges not only its associated risks but also some common IoT weaknesses that leave them vulnerable to large-scale, coordinated attacks. The vulnerability in device weaknesses’ limited processing power or memory makes traditional security measures impractical. Default passwords and unpatched firmware create entry points. Network-level weaknesses with a lack of encryption or weak encryption in communication protocols like MQTT are vulnerable due to no built-in security as it relies on external TLS/SSL; CoAP is vulnerable due to limited encryption options; and Bluetooth Low Energy is vulnerable during weak paring probes, susceptible to eavesdropping and unauthorized device connection. Application-level weaknesses with insecure APIs expose sensitive data and weak access control and privilege management. IoT limitations in current security protocols are a large-scale question. Is there a scalability issue in handling the exponential growth of IoT devices? Resource constraints are resource-intensive for low-power devices. There are interoperability gaps in different devices and protocol communication security across diverse platforms. Latency concerns whether the encryption process impacts real-time performance. Supply chain vulnerabilities when firmware backdoors or insecure 3rd party components are evaluated. The paper discussed the proposed actionable insight for mitigation by including threat modeling, mitigation framework, multi-layer security approach, protocol enhancement with mandatory encryption and authentication mechanisms, and best practices highlighting practices like regular firmware uprate, secure key, and intrusion detection.
The IoT’s layout is focused on a three-tier/layer structure consisting of a network/communication layer, a perception/hardware layer, and a layer of interfaces/services. Devices, connectivity protocols, and user interfaces are the components that comprise an IoT structure.
6.4. Security Risk in the Perception Layer
This layer is similar to the physical layer of the OSI network model. It gathers information from the outside world through various devices and sensors such as temperature, ultrasonic, RFID, pressure, and barcodes. Since IoT networks are mostly composed of wireless devices and wireless networks, the perception layer could be susceptible to an attacker’s interception of sensor nodes in the IoT network. Similarly, the IoT-based sensor nodes generally operate in the external environment, leading to physical attacks on these nodes, as the attacker can tamper with the device’s hardware components. Moreover, these devices collect data, gather information, and censor data through many terminals. These terminals collect the data for an onward presentation to the user. The fundamental issues associated with these terminals are tempering, terminal viruses, leakage of restricted and confidential data, etc. [].
Another security issue associated with the Internet of Things is the dynamic topology of these networks because of their moving nature. The IoT networks often consist of low-power devices, such as RFID and other sensors, with lower storage, computation power, and power consumption. Because of lower computation power and other characteristics, these devices are susceptible to several security attacks and threats. An attacker can easily transmit malicious data and information, threatening data integrity by adding another node into the system. An example could be a DoS attack, which can cause considerable energy consumption by making them always work in harsh conditions and preventing them from going into sleep mode. Eventually, the devices can die and be switched off in extreme conditions.
We can overcome these issues through security measures such as encryption, access control, confidentiality, etc., which will be discussed in the preventive measure section.
6.5. Security Risk in the Transportation/Network Layer
This layer transfers information from the perception layer to some processing system through the network. The type of network does not matter; it can be the internet, mobile data, WIFI, Bluetooth, or any other kind of network. Since the data transmission is carried out using computers, wired/wireless networks, and other networking components, this layer comprises these components and computers, which can cause the system to face various security issues, e.g., hacker intrusion, unauthorized access, and network security. The openness of the Internet of Things also makes the IoT systems susceptible to several identity authentication issues.
Another issue at the network or transport layer is the vast amount of data flowing through the network. As the sensor devices collect and gather the perceived data, these devices unavoidably produce a vast amount of redundant data, which can produce network congestion while the transmission results in DoS attacks. This issue is controlled by incorporating the interaction between the application and the transmission layer through cross-layer security techniques []. For example, security can be strengthened by enabling the application layer to influence transmission-layer parameters such as adaptive Quality of Service (QoS), secure session initiation, and traffic prioritization. This cross-layer approach helps ensure that data flows are both efficient and resistant to attacks such as packet flooding or unauthorized access. There are issues about the network layer. The following lines briefly discuss some important security issues associated with the network layer []:
- Sybil attack: A Sybil attack occurs when a malicious node falsely asserts multiple identities, posing as distinct entities within a network. This type of attack is recognized as a significant security threat within the IoT system [,].
- Sinkhole attack: In this type of attack, the attacker takes control of a node and manipulates it so that it begins to look attractive to other nearby nodes. The data transmitted from those nodes is diverted to the compromised node, resulting in data loss through packet dropping. Sometimes, the infected node tries to convince the other nodes that the destination node has transmitted and received the data.
- Sleep deprivation attack: The Internet of Things generally contains constraint-based devices. Sensor nodes’ capacity to transition into a low-power sleep mode is incredibly valuable for prolonging the network’s lifespan. This attack exploits network protocol weaknesses to prevent sensor nodes from entering low-power sleep modes. The node’s energy reserves are rapidly depleted, leading to a shortened network lifespan and potentially disrupting its operations [,].
- Denial of service (DoS) attack: In this type of attack, an attacker generally floods the network with useless traffic or raw data, which results in excessive utilization of system resources and makes the network unavailable to users. In this attack, an attacker compromises a node and uses it to inject malicious code into the system and other nodes. Depending upon the type and nature of the injection, this can lead to disastrous conditions. In bad conditions, the network might also become unavailable to its users [].
- Man-in-the-middle attack: In this type of attack, the attacker generally takes advantage of a compromised communication channel among different entities to obtain unauthorized access to watch, monitor, and control all private communication. In this case, the attacker can even fake the victim’s identity and gain more information through communication.
- Selective forwarding attack: This occurs when a compromised or malicious node in the network deliberately forwards only a subset of the packets it receives, while silently discarding others. Unlike a blackhole attack, where all packets are dropped, selective forwarding is more difficult to detect because some traffic still flows through the node. For example, in an IoT sensor network, an attacker may allow routine status messages to pass but drop critical packets such as alarm signals, thereby degrading system reliability and potentially causing significant harm.
6.6. Security Risk in the Application Layer
This layer is mainly responsible for analyzing the information obtained from lower layers for intelligent processing and guarantees data confidentiality, authenticity, and integrity. Real-time information is also obtained at this layer by being presented to the user. Similarly, some securities are related to the application layer; some of the important security issues associated with the application layer are briefly discussed in the following lines:
- Malicious Code Injection: In this attack, the attacker injects malicious code into the system to perform illegal activities and obtain unauthorized access and control. Apart from the network layer, an attacker can also perform this type of attack through the application layer using a hacking technique to inject malicious code.
- Spear-Phishing Attack: It is a kind of spoofing attack. In this attack, the victim, who in most cases is a high-profile person, is tempted to open the emails, which causes the attacker to gain access to the victim’s credentials, which can be used to steal more personal and sensitive information about the victim.
- Sniffing Attack: In this attack, the attacker introduces a type of sniffer application, mostly in the form of cracks and patches, into the victim’s system to force an attack on his system. These sniffer applications are mostly used to collect, monitor, and transmit personal and network information related to the victim.
Radiofrequency identification (RFID) and wireless sensor networks (WSN) are named as components of an IoT system. Therefore, potential threats from these two components are listed in Table 5. We also provide recommendations for security controls to help reduce the damage that these attacks may cause to devices connected to the Internet of Things. The primary emphasis of the article is on performing an in-depth analysis of the security flaws left behind by each layer’s components, as well as outlining the many security measures and methods implemented to defend against prevalent attacks.

Table 5.
Common attacks against IoT devices according to the new architecture [].
Even if the architectures discussed in the previous part make the notion of the Internet of Things realistically possible, a significant amount of research still needs to be performed in this area. This part will discuss the technological issues currently linked to IoT designs. Later, an innovative approach is offered to fulfill the important aspects lacking in the currently used architectures.
IoT security cannot be addressed through a single mechanism but must instead be viewed as a multi-layered challenge, with each layer, from perception to application, facing distinct risks such as physical tampering, network-based intrusions, or application-level exploits. The analysis also shows that while universally applicable principles such as encryption, scalability, and privacy-by-design provide a foundation, industry-specific adaptations are essential to meet the demands of domains such as healthcare, industrial IoT, smart agriculture, and connected vehicles. Furthermore, the effectiveness of IoT defense increasingly depends on cross-layer approaches, where higher-level applications influence transport and network behaviors to improve resilience. However, IoT remains constrained by limited device resources, fragmented standards, and evolving attack vectors, highlighting the need for lightweight, interoperable, and adaptive security mechanisms that balance robustness with efficiency.
7. Technical Challenges
It is generally agreed that the technology and applications related to the Internet of Things are still in their infancy. Many research obstacles remain for industrial usage, such as technology, standards, safety, and privacy []. One major technical challenge in IoT is the sheer scale and diversity of devices connected to the IoT ecosystem.
Device heterogeneity is caused by devices from different hardware capabilities, operating systems, software stacks, and security measures on one device not being compatible or effective on others. Many IoT devices have limited computational power, memory, and energy resources, which constrain the implementation of robust security mechanisms. Traditional security solutions may be too resource-intensive for IoT devices, requiring development processes or lightweight security protocols. IoT devices often communicate over wireless networks, making them susceptible to eavesdropping, tampering, and replay attacks. Ensuring secure communication for data transmission is crucial. Challenging regarding updating updates on many devices may be complex, and remote or inaccessible devices may be disrupted or cannot be controlled by the operation team. Device identification and access management are critical; secure provisioning, authentication, and access control must be implemented to prevent unauthorized access and protect against device spoofing and impersonation. Managing device lifecycle management is challenging; managing the security patches, firmware updates, secure disposal, or repurposing requires careful planning and coordination. The complex interplay between the IoT ecosystem, edge devices, gateways, cloud interconnectivity, and network introduces additional attack vectors and requires comprehensive security measures. Security of the entire IoT system end-to-end is a significant technical challenge.
Future efforts are required to solve these problems and investigate the features of various businesses to guarantee that Internet of Things devices are a suitable match in settings focused on the human experience. Before the Internet of Things becomes broadly adopted and implemented across all industries and domains, there must first be sufficient awareness of the features of those industries as well as the expectations placed on aspects such as cost, security, privacy, and risk [,].
The design of service-based objects on the Internet of Things provides a major challenge for SOA since these objects may have performance and cost-related considerations. Managing many devices in SOA might cause scalability issues. Data transit, processing, and administration are now burdens that service providers must take on [,].
The IoT is a complicated, multi-tiered network platform. A network’s disagreeable behavior is revealed as misleading, delayed, and non-standardized when this raises the complexity among the many various types of devices through the many communication protocols. After addressing, identifying, and optimizing at the architectural and protocol levels, [] showed that the administration of linked objects is a substantial research problem. Numerous objects, such as hardware and software services, are created to facilitate collaboration. There is little doubt that managing linked things is an important research problem.
In the context of network services, it is clear that Service Description Language (SDL) resources are in limited supply. Increased product distribution time would decrease market share, making designing, launching, and integrating resource-intensive services more difficult. Therefore, a strong method for service discovery and an object naming service should be built following the creation of a well-recognized and widely used SDL. After validating the SDL-specific design, a new SDL may be built to handle product distribution.
A traditional network-oriented ICT infrastructure now backs the Internet of Things, and everything connected to it will always impact it. A unified information infrastructure is needed in this environment. Real-time data flow from many connected devices will need a channel with a wide bandwidth. Due to the need for standardization, an architectural framework that can intelligently address infrastructure needs must be designed.
Because of its large size, this database management system may be unable to process the produced data in real time. It is necessary to create ideal solutions. The amount of data generated by the Internet of Things will increase exponentially. The existing RAID technology cannot store the data received at the receiver’s end. In this situation, a data service-centric architecture based on the IoT must be changed to overcome this problem.
The devices linked to the Internet of Things will generate various data kinds, sizes, and formats. For optimal impact, these alterations must be made in conjunction with future technology, which may involve a variety of architectural designs. Researchers must develop new architectures to meet the demands of Big IoT., as well as data that is capable of successfully managing data.
Data is often incompatible with useless handouts due to the nature of the information presented. Using data from the IoT to make decisions is a crucial factor in the process. The value of the data cannot be assessed until the whole pool of data has been filtered. One may obtain it only by mining, analyzing, and comprehending this information. The problem may be solved using huge amounts of data and performing similar regressions. Data mining, analytics, and decision-making services may be facilitated by an appropriate architectural framework found in the data. This might be used to build a strategy based on Big Data.
The issues of combining hardware and software in the context of the Internet of Things must also be investigated by enterprises. Web services will be accessible through a wide variety of middleware solutions, and a wide variety of devices will be able to operate them []. To facilitate the facilitation of several protocols, a special architecture must be developed. More than one billion devices will soon be part of the Internet of Things. All linked data and equipment must be retrievable to build an efficient point-to-point network. Having a unique identity is thus an imperative must. Using a 4-byte IPv4 address, each network node may be uniquely identified on the network. Because it is generally known that the number of IPv4 addresses that are accessible is gradually dwindling and will approach zero over the next several years, new laws addressing this will need to be devised to compete with IPv6, which is a formidable opponent. Pursuing device naming and identification capabilities is an area in which the utmost attention must be paid, and the appropriateness of architectural competence is essential.
The development of the Internet of Things may benefit from adopting standardization as a tool. Improving interoperability across different applications and systems and fostering more competition among those products or services provided at an application level are all examples of what “standardization“ means in the Internet of Things. The spread of the Internet of Things’ technologies involves establishing new security, communication, and identity standards while concurrently producing emergent technologies with a horizontal equivalence. Other academics in the same area must produce industry-specific guidelines and specify critical architectural standards to incorporate IoT properly.
From the standpoint of delivering services, the lack of a language commonly accepted for expressing services makes it difficult to construct new services and combine the resources of physical objects into services that bring extra value. The constructed services will probably be incompatible with diverse communication and implementation settings [,,,,,]. In addition, effective strategies for service discovery and object naming services must be devised to enable the diffusion of the Internet of Things technology [,,]. Scientists must come up with new architectural ways to deal with these issues.
The degree to which the Internet of Things and associated technologies are widely adopted will be largely determined by the network’s security and privacy protection level. The Internet of Things’ inherent complexity and diversity constantly threaten users’ privacy and security. Deployment, mobility, and complexity are the main issues prohibiting the Internet of Things from being safe []. In an IoT context, privacy protection is more susceptible than in a conventional network because of the vast number of attack vectors present in IoT entities, according to [,,]. This is because an IoT ecosystem has a greater number of interconnected devices. Let us say a healthcare monitoring system based on the IoT collects patient data (such as heart rate and pulse, body temperature, and breathing) and sends it to a doctor’s office or hospital via a network in the future. Loss or theft of patient data while it is being delivered over the network poses a serious risk to the user’s life. As a disadvantage, most architectural designs do not include privacy and security issues in their plans. Such a design fault has been spotted in this situation, as well. Even though existing network security solutions allow IoT to be protected against such assaults, much work still needs to be done. Security for the Internet of Things is paramount; it must be reliable, efficient, and powerful. Additional work is needed in the following areas:
- Social, legal, and cultural definition of security and privacy; the management of trust and reputation.
- The use of end-to-end encryption for sensitive data to remain encrypted [].
- The protection of the privacy of communications and user data.
- The implementation of security on services and apps. Even though present network security solutions provide a basis for privacy and security in IoT, it is also understood that more work has to be done. As a result, there is still a lot of work to be done.
For the Internet of Things to be secure, it is necessary to research the following topics. This includes the concept of security and privacy from the standpoint of society and law, the mechanisms for establishing trust and reputation, the security of communication, the privacy of user data and the security of service and application implementations, various privacy-preserving techniques, encryption methods, access control mechanisms, and authentication protocols to mitigate privacy and security risks in IoT [].
7.1. Direction Towards IoT
Common application-specific approaches are provided in this section, many of which are not included in the previous review work or have not been addressed in any manner by the scientific community. IoT refers to the Internet of Any architecture, where “*” is often interpreted as “anything” in the computer industry. The Internet of Things will soon be based on architectures, which are becoming increasingly important in IoT. An architect or developer’s first and most important task is creating a model illustrating the layered components and their relation. Before implementing the design, this step should be completed. New frameworks based on things, such as those found in mining, sports, tourism, governance, social, robotics, automation, and defense, should be developed via research. This can only be made possible if enough financing is made available. If we want to utilize the IoT, we must force ourselves to do so since any design is acceptable. Healthcare, domestic, transportation, the environment, and agriculture are some areas where people search for smart IoT solutions. To meet these issues in the not-too-distant future, academics must strive to adapt to the proper frameworks. We shall enter a new age of perceiving things by combining freshly discovered regions with those gathered through time via the Internet of Things. Maintaining a horizontal, vertical, and diagonal crossing between all the IoT’s core components and the general applications is critical here. A thorough examination of the Internet of Things must be conducted before it can become a reality. Analog, digital, and hybrid goods are all included under the umbrella term “things” in this phrase. Many other kinds of materials, in addition to solids, liquids, semi-liquids, and crystals, may be included in this concept. Integrated chips (ICs), system-on-a-chip (SOC), field-programmable gate arrays (FPGAs), application-specific integrated circuits (ASICs), and flexible electronic components will help close the gap between digital and pure digital mechanisms. The traditional OSI network model will be re-examined to accommodate enhanced layer-based Io. The network’s protocols must be used appropriately on each layer. Scripted web-based pages would communicate with the <* component of the system using NoSQL, SPARQL, graph database, parallel database, Hadoop, Hbase, RDF, and OWL-oriented set-ups for the *> portion of the system. This integration is a result of this collaboration.
On top of that, we will implement data analytics, risk analysis, visualization, resource management, service coordination, task management, APP-based plug-in enabler, API moderator, storage monitor, and predictive analysis to improve IoT-as-a-Service. User experience will be elevated to a new level thanks to the layer being roofed over with infinite applications. People must place a high value on the development of new technologies such as autonomous vehicles and logistics systems; mobile ticketing; environmental monitoring; augmented maps; health tracking; data collection; identification and sensing; smart homes; smart plants; intelligent museums; social networking; theft monitoring; loss apprehension; historical queries; autonomous vehicles and logistics systems; autonomous vehicles and logistics systems; and enhanced gaming environments, among other things.
Mining locations will be hidden via the Internet of Things, and it will also be utilized to connect sports, travel, and tourism, as well as protective systems. The AES, 3-DES, RSA, and SHA-3 algorithms must be modified to fit the constrained resources. Including multimedia in the IoT via streaming algorithms is possible, with individual messages linked to the packet payloads. For the pre- and post-measurement modification of data, it is suggested that “Sensor Model Language” (SensorML) be re-examined to offer a reliable and semantically connected manner of expressing processes and processing components (Open geospatial). SensorML’s major objective of enabling interoperability will be achieved via ontologies and semantic mediation.
Syntactic and semantic aspects of this may be addressed before moving on to linguistics. Consequently, sensors and processes will be more easily understood, utilized, and shared by machines in complex workflows and among intelligent sensor network nodes. “Operating Systems (OS)” are now standard on most digital and hybrid devices that comprise traditional networks OS. There are just a few operating systems available for the IoT invasion. Many IoT operating systems are now available, including Contiki-OS and RIOT-OS.
Although they lack hardware interoperability and semantic techniques, these versions are the most widely used. From this perspective, new kinds of universal IoT-OS need to be developed. Until now, no one has brought up the possibility of an actuator layer in the Internet of Things literature as a potentially significant part of this emerging technology. The number of available actuators is expected to grow exponentially compared to the sensor. Without a centrally monitored and controlled environment, IoT will fill the gap.
7.2. Challenges of IoT
The Internet of Things continues to face several pressing challenges that must be addressed to ensure secure, reliable, and large-scale deployment. One fundamental issue is the lack of standardization across platforms, protocols, and vendors. Without unified standards, interoperability between heterogeneous devices remains limited, increasing integration costs and leaving gaps in security and privacy enforcement. Standardization efforts are therefore essential to establish common frameworks that guarantee compatibility and consistent protection [].
Another major challenge lies in addressing technical limitations related to efficiency and scalability. For example, accurate delay and latency analysis is required before data transmission to maintain the performance of time-sensitive applications such as healthcare monitoring and industrial automation. IoT networks must also adapt to energy constraints, as many devices rely on low-power batteries or energy-harvesting technologies. Ensuring efficiency while maintaining strong security protocols is a difficult balance.
Security and privacy represent perhaps the most critical challenges. Since IoT applications frequently involve the exchange of sensitive personal and organizational data, any breach can lead to significant harm. Protecting users from threats such as unauthorized data access, identity spoofing, and surveillance requires the adoption of strong encryption, continuous authentication, and privacy-preserving data sharing techniques [].
Beyond these existing issues, IoT also faces emerging challenges. These include the need for lightweight cryptography tailored to resource-constrained devices, the integration of AI/ML-based intrusion detection for dynamic threat detection, and the use of blockchain and distributed ledgers to build decentralized trust mechanisms. At the same time, regulatory and ethical considerations, particularly around data ownership and accountability, are becoming increasingly important.
Together, these challenges highlight the complexity of securing IoT systems and highlighting the need for ongoing interdisciplinary research combining cryptography, networking, machine learning, and governance frameworks.
7.3. Possible Countermeasures
To what extent are we at risk of losing our security? Due to TLS protocol vulnerabilities, the IoT’s transport layer is vulnerable to attacks like resource exhaustion and flooding. Replay and amplification attacks are also possible. As long as an intruder manipulates a message stream and rearranges the data packets, they have successfully attempted a replay attack [].
As an effective security precaution, changing the message’s timeliness may prevent the Internet of Things’ devices from being targeted by a replay attack. Assaults on the network and application layers may be called a DDoS attack. DDoS attacks on the transport layer may fall into four categories: TCP flooding, UDP flooding, TCP SYN flooding, and TCP desynchronization. TCP flooding or UDP flooding sends many packets through the TCP or UDP protocols to disrupt or slow the protocol’s operation.
Thanks to TCP SYN flooding, a connection may be established even when the TCP handshake procedure has not been followed. When a packet sequence is disrupted by introducing an erroneous sequence number, it is called TCP hijacking. Transmission control protocol (TCP/IP) attacks are the technical term for what you have just performed. Two separate techniques have been proposed as viable solutions to the TLS challenge. DTLS and an end-to-end tunnel may help protect a network with low power and high loss rates against eavesdropping [].
Machine learning (ML)-based techniques for detecting DDoS and DoS have recently been presented in the literature. Unsupervised clustering, Artificial Neural Network’s (ANN) Linear Vector Quantization (LVQ) model, and ANN’s Back-Propagation (BP) model are all instances of these solutions. A Support Vector Machine-based classifier outperforms K-nearest, naive Bayes, and multilayer perceptrons regarding performance (SVM). This classifier may identify and mitigate DDoS TCP flooding attacks []. Using attribute-based encryption with elliptic curve implementation to secure the MQTT protocol is a strong way to reduce the impacts of the MQTT attack [].
For IoT attacks that target the application layer, injection, IRCTelnet, and the Mirai malware are most common. A Mirai malware attack happens when a hacker tries to access a device linked to the IoT using the device’s default Telnet or SSH account.
Consequently, the default Telnet and SSH accounts should either be deactivated or updated to stop these attacks. An IoT device is coerced into opening a Telnet port using IRCTelnet, which infects the device’s LINUX operating system. In an IRCTelnet attack, turning off the Telnet port number is possible. Security flaws identified in the 2017 OWASP application security flaws review include injections, broken authentications, sensitive data exposures, XML external entities (ExXEs), faulty access controls, security configuration errors, cross-site scripting (XSS), insecure deserialization, and using components with known vulnerabilities.
Delivering untrusted data to an interpreter as part of a command or query to take down the program that utilizes the data in question is also known as “injection.” Using input validation controls, hackers and end users cannot abuse application systems. The use of lightweight encryption by SMQTT may improve its security features. Various research studies have proposed different MQTT variations to enhance the protocol’s already strong security by integrating encryption algorithms like AES and Rivest–Shamir–Adleman (RSA). Communication security for SMQTT is provided via SSL and TLS protocols, both of which are extensively used today. Many iterations of TLS, such as wireless Transport Layer Security (WTLS) and Datagram Transport Layer Security (DTLS), are implemented in mobile communications and UDP-based applications, respectively, to protect users’ privacy and maintain the reliability of their data in today’s technological landscape. Confidential data may be protected by using encryption methods.
In addition, the data is cleaned, and the user’s privacy is safeguarded. On the Internet of Things, symmetric and asymmetric encryption techniques, key sizes, average execution durations for 1000 iterations, and examples of applications are summarized in Table 6. Symmetric cipher algorithm implementations provide message integrity checks, encryption, and entity authentication. Non-repudiation and key management are additional advantages of asymmetric encryption techniques [,,,].

Table 6.
Lightweight encryption algorithms for IoT.
7.4. Thread Modeling Approaches for IoT Architecture
The threat-modeling approach has been briefly discussed in section A “IoT and Security”. Further discussion on adopting a threat-modeling approach for IoT architectures helps systematically identify and mitigate potential vulnerabilities. The proactive approach and strategy ensure that security is integrated into the architecture from the design phase and maintained throughput the IoT system’s lifecycle.
Steps to perform threat modeling for IoT architecture consists of understanding the IoT architecture by gaining a clear view of all components, their functions, and interconnections of IoT such as the following:
- Identify IoT sensors, actuators, controllers, etc.
- Map communication pathway, e.g., Wi-Fi, Bluetooth, Zigbee, Cellular.
- Highlight data flows, storage points, and access methods. Some common practices in countermeasures are shown in Table 7.
- Prioritize risks by focusing on the most critical vulnerabilities first and assess threats based on likelihood and impact using a model like DREAD (Damage, Reproductivity, Exploitability, Affected Users, Discoverability) by creating a risk matrix to classify threats as high, medium, or low risks [,,].
- Specify requirements for data confidentiality, integrity, and availability (CIA triad) for the security of systems, applications, and services to control and offset possible threats to ensure CIA and Safety (CIAS) [].
- Address authentication, authorization, and accountability for devices and users.
- Identify compliance requirements.
- Follow the STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) framework by categorizing threats based on device types, communication channels, and external factors, e.g., hackers, insider threats [].
- Pinpoint entry points that adversaries could exploit by analyzing devices, examining networks, evaluating application vulnerabilities, and reviewing supply chain risks that could tamper with hardware or insecure software updates.
- Adopt a combination of layered countermeasures. Secure device authentication can be enforced through certificate posture checks, where the validity, configuration, and cryptographic strength of device certificates are verified before allowing network access, thereby preventing unauthorized or compromised devices from joining the system. In parallel, end-to-end encryption (E2EE) should be applied to protect data during transmission, ensuring that information is encrypted at the source and decrypted only at the intended destination. This can be achieved using protocols such as TLS 1.3, DTLS, or lightweight cryptographic frameworks designed for constrained devices. Complementary measures include regularly patching and updating devices and systems to address vulnerabilities, applying network segmentation to isolate IoT devices from critical systems, and deploying intrusion detection systems (IDS) to monitor traffic patterns and generate alerts for abnormal behavior. Finally, cloud interfaces must be secured by enforcing strict access controls, applying strong authentication policies, and encrypting sensitive data at rest. Together, these practices create a robust, multi-layered defense strategy for IoT security.
- Verify the effectiveness or implementation of security measures by performing penetration testing to identify exploitable weaknesses, simulate attack scenarios, and evaluate system resilience and audit configurations and policies for compliance and effectiveness.
- Monitor and update threat models by adapting to evolving threats and changes in the IoT ecosystem. This can be achieved by continuously monitoring IoT devices and infrastructure anomalies, updating threat models to reflect new devices, features, or threats, and reviewing logs and incident reports to improve future threat modeling.

Table 7.
Examples of common IoT threats and countermeasures in IoT.
The challenges of IoT are rooted in its heterogeneity, scale, and constrained resources, which make the direct application of traditional ICT and security solutions ineffective. Device limitations, fragmented standards, and interoperability issues continue to hinder secure and seamless integration, while the exponential growth of IoT data introduces storage, latency, and real-time analytics concerns. To address these complexities, lightweight and adaptive architectures are required, supported by global standardization and cross-domain guidelines that align with diverse industrial requirements. At the same time, IoT security must shift from reactive patching to proactive design, where threat modeling and multi-layered defenses are embedded throughout the system’s lifecycle. Key takeaways from this section highlight that only through a combination of standardized frameworks, privacy-aware design, and scalable security controls can IoT evolve from an experimental ecosystem into a resilient and trustworthy infrastructure for critical applications.
8. Security and Best Practices
Further discussion is warranted on the security and best practices other than adhering to threat-modeling approaches when IoT poses potential security risks that threaten individuals, whether from the Internet or personal devices. The following best practices protect good practices in digital IoT.
- Only install reputable and tested software on your computer and smart mobile devices.
- Secure boots ensure devices only run firmware from trusted sources [].
- Never leave personal laptops, handheld, or smartphones unattended; always turn off Bluetooth whenever not necessary; a disabled remote access function, especially for some IoT, comes with the remote access function by default [].
- Always update security patches against bugs and vulnerabilities. Always keep your app software up to date.
- Use complex passwords for device accounts, wireless passwords, or network and internet-connected devices.
- Adhere to the apps’ security policies. When installing the apps, know what data they are to access and abort the permission if they are accessing personal data that you deem unnecessary. Choose only the features you require for the installed apps. Remove a legacy app if it is no longer needed.
- Verify what data is to be stored in your device, especially a smart handheld or smart mobile device, always collect personal data, and understand the risk of data sharing by understanding the security policy and protection [].
- Always use a trusted wireless hotspot, a virtual private network, to secure data transmission between devices.
- Employ secure communication protocols, such as HTTPS, MQTT with TLS, or CoAP with DTLS, to protect data transmission and prevent eavesdropping, replay attacks, and man-in-the-middle attacks.
- Regularly update and patch the firmware and software of IoT devices to address security vulnerabilities. This can be achieved through over-the-air (OTA) updates or secure update mechanisms that verify the updates’ authenticity and integrity.
- Configure firewalls to allow only necessary communication.
- Use an IDS to monitor network traffic for suspicious activity.
8.1. Prevention
Backdoor, Trojan, Botnets, Malware, Middleman, DoS and DDoS attacks, and many other threats have become more dangerous for IoTs. Prevention is a mandate to maintain and protect the security of IoT devices. It is a must for people to protect their IoT devices with the best practices. Security prevention becomes the standard set of policy frameworks for IoT best practices—security frameworks like Microsoft Security Framework 2019 and NIST are based on prevention detection. The agenda of these frameworks highlighted the precautionary and preventive measures in safeguarding connected devices and networks in IoTs.
8.2. Detection
Security damage can be direct or indirect, and it causes bad damage or financial loss due to the damage. Detection of threats and vulnerabilities can be drastically reduced via security detection and analytics to eliminate these damages. It is imperative to protect the IoT from detection. Detection helps identify and nip threats in the bud []. Anomaly detection technology, high-sensitivity intrusion detection technology, etc., effectively detect information on IoT-driven devices. The techniques with zero-day attack detection for known and unknown threats, signature-based, pattern-based, and machine learning detection, are effective ways to attack the risk to IoT devices.
8.3. Encryption
Encryption is used to maintain integrity and confidentiality and avoid the tampering of data. In this technique, the data is encrypted using a cryptographic algorithm with a decryption key and transformed into ciphertext before being transmitted to the destination. The ciphertext is the encrypted form of the actual text. As a result, if an intruder captures the transmitted message, the confidentiality and integrity of the data would remain intact because he will be unaware of the decryption algorithm and keys to decrypt the message and will be presented with a text that would be useless to him. It is a vital means of data security []. Encryption techniques include end-to-end encryption, quantum-resistant encryption for future-proof IoT security, homomorphic encryption when data is being processed while remaining encrypted in edge computing, and attribute-based encryption (ABE) for fine-grained access control []. The key takeaway is to use a strong encryption method, e.g., WPA2 for wireless networks, to secure communication between the network and connected devices. Third-party encryption like wolfSSL [], which has strong embedded security encryption, supports the latest SSL/TLS/DTLS, providing secure communication for IoTs. It has progressive support for ciphers for securing devices. TLS 1.3 and DTLS 1.2 support device communication with a small runtime memory when storing the key algorithm, even with the highest hash and key length []. Security by design uses Hardware Security Modules (HSMs) for secure key storage and cryptographic operations [,].
8.4. Confidentiality
An important factor in security is access to data. The data should always be accessible to authorized users only. A user can be anything. It can be a human, an IoT-based device, or any external device not even part of the network. Data is always only readable by the intended user. Along with encryption-enabled data, confidentiality ensures that only the proposed destination can decrypt the encrypted data so any unauthorized person is unable to access the data. Another important point is that the sensor or device collecting data should not allow its neighboring devices to read and access its collected data and information.
8.5. Authentication
One other key factor in security is the authenticity of the data. It states that the receiver of the data must be able to notice whether an authenticated user transmitted it. Data authenticity is of prime importance in each layer of the IoT architecture. For example, the authenticity of sensor nodes at the perception layer is essential for preventing DoS attacks. There are multiple authentications for IoTs, e.g., 2FA, multi-factor authentication, digital token, one-time password (OTP), and biometric technology with a sensor ensure no one else has access to your devices other than yourself. The reason for hacking is always through personal data; hence, authentication protection is always the front-end layer of security options. Users’ authentication via Zero Trust architecture mandates that users must prove their identity through multiple factors before gaining access to IoT systems. This might include passwords, biometrics, or tokens. By treating every user as untrusted until verified, Zero Trust significantly reduces the risk of credential-based attacks.
8.6. Authorization
It is used to control access to a device throughout the network. It states that the authorized user must always access the data. The relationship among IoT-based devices for exchanging information is established through authentication and authorization. Policy-based and authenticated identity can be used for authorization. It gives authorized control to a user or device without restrictions. Proper authorization is always only granted when the policy-based authorization is executed or the credential and identity are authenticated. An example of an IoT-based policy is the AWS IoT core policy. It has a core function with a control panel API that allows tasks like signing certification rules and data plane API for sending and receiving data from AWS IoT core when authorization is granted via the policy attached to the IAM accounts or groups []. Users are given access or denied access to any topic or application based on authorization. AWS IoT policy has caches; changes to the policy can be made instantly or within minutes, whether to authorize or revoke access.
8.7. Certification
With the rapid rise of IoT, security certificates are used to confirm the identification of both parties participating in the communication process. It becomes a basis for trust in the communication entities []; the certification uses the Public Key Infrastructure (PKI) to provide two-way public key certificates to keep the IoT systems confidential and authentic. The PKI handles all aspects of certificate security, from high integrity, data sharing, messaging, communications, and scale to internet collaboration []. Certification with digital signs guarantees the integrity of data documents and identifies the signer. Once the user has produced or installed the signed certificate, the signed certification can be verified, and the access is secure and may no longer be repudiated [,,,].
8.8. Access Control
Access control provides security to the IoT systems by blocking unauthorized access to nodes and objects to prevent the resources from being compromised. Access control is the most challenging part of IoTs. IoT devices like smartphones let the user obtain instant confirmation of the access request []. It provides easy interaction with others without any physical identification for secure access control, meaning the accessibility of mobile devices can be seen easily from the indoor wayfinding feature that comes with the device [].
Access control manages security by enabling role-based access control to restrict access based on user roles and responsibilities, using MFA for device management interfaces, and maintaining an audit log of device and user activities for monitoring and forensic analysis as part of prevention measures. Effective access control can be ensured by using correct entity identification with certification technology, encryption solutions, authentication mechanisms, and detection solutions. Extending the review made by [,], another method worth mentioning is browser fingerprinting [,], which leverages unique device and browser characteristics to create a distinct profile for each user. Unlike traditional authentication methods, browser fingerprinting does not rely on cookies or explicit user interaction, making it a passive yet powerful tool for enhancing security. By integrating browser fingerprinting with other access control measures, IoT systems can achieve more robust protection against unauthorized access, particularly in environments where physical identification is impractical.
8.9. Compliance and Standards
IoT has revolutionized the way we interact with technology, creating a network of connected devices that communicate and share data. However, with this convenience comes the critical need for robust security measures to protect sensitive information and ensure the integrity of the network. Adhering to established IoT security standards is paramount in achieving this goal. This document explores the key standards that guide IoT security compliance, including the following:
- IoTSF (IoT Security Foundation) best practices to help organizations identify and mitigate security risks in IoT deployments []. The practices emphasize a holistic approach to security, covering aspects such as design and development along with secure coding, threat modeling, and vulnerability assessment; endpoint security ensures an IoT device has built-in security features such as secure boot, encryption, and authentication mechanism; data privacy ensures that data collected by IoT devices is handled in compliance with privacy regulations and protected from breaches; lifecycle management establishes processes for secure firmware updates, patch management; and decommissioning of devices to maintain security throughout its lifecycle.
- NIST IoT cyber security guidelines for strengthening security posture. The key components include maintaining inventory and implementing measures to protect IoT assets from security threats; securing communications to prevent eavesdropping and data manipulation; data checks to prevent unauthorized access and tampering; ensuring device security to prevent unauthorized modification and access; and monitoring and responding to incidents in a prompt manner.
- ISO/IEC 27001 for information security management by managing and protecting sensitive information. Organizations implementing ISO/IEC 27001 can ensure that their IoT deployments align with best practices for information security. Key aspects of ISO/IEC 27001 include risk assessment, security policy, and procedures that govern the use, management, and protection of IoT devices, and data, access control, and incident management, not only detecting, reporting, and responding to the incident but also performing regular drills and reviews to ensure preparedness in the event of incidents.
8.10. Secure Communication
In today’s interconnected world, the proliferation of IoT devices necessitates stringent security measures to protect against unauthorized access and data breaches. Ensuring secure communication within IoT networks is paramount. The following guidelines outline essential practices for securing communication in IoT networks:
- Protocol selection and choosing the right protocols for secure communication are critical. Protocols like HTTPS and MQTT with TLS provide robust security features that safeguard data transmission.
- Network segmentation by isolating IoT devices on separate network segments is a crucial step in limiting their exposure to potential threats. Network segmentation involves dividing a network into smaller, isolated segments, each with its security control. This approach minimizes the attack’s surface and contains potential breaches, preventing them from spreading across the entire network.
- Firewall rules block all traffic by default and allow only selected traffic. Enable state-wide inspection to track the state of active connections and make decisions based on the context of the traffic. Apply least privilege permission for accessing rights of devices and users. Regularly review and update rules to ensure firewalls remain effective against evolving threats.
8.11. Emerging Technologies for IoT Security
As IoT devices proliferate, ensuring their security has become paramount. Emerging technologies are addressing these challenges with innovative solutions, paving the way for a safer and more secure IoT landscape.
AI-based threat detection with real-time identification of unusual patterns in IoT networks is one of the most promising technologies in IoT security. AI-based threat detection systems leverage machine learning algorithms to monitor IoT networks in real-time, identifying unusual patterns and potential threats. These systems can analyze vast amounts of data quickly and accurately, allowing them to detect and respond to anomalies that might indicate security breaches. Traditional security measures often rely on predefined rules and signatures, which sophisticated attackers can bypass. In contrast, AI-based systems can learn and adapt, recognizing new and unknown threats. This adaptability is vital in an environment where new IoT devices and vulnerabilities are constantly emerging. AI excels in pattern recognition, making it an ideal tool for identifying unusual activity in IoT networks. An AI system can distinguish between normal and abnormal behavior by continuously learning from the data it processes. For example, if an IoT device that typically communicates with a specific server suddenly starts sending data to an unknown location, the AI system can flag this as suspicious and initiate an investigation.
Blockchain with decentralized solutions for security device authentication and communication. Its decentralized nature and inherent transparency make it an excellent solution for securing device authentication and communication. Blockchain’s decentralized architecture eliminates the need for a central authority, reducing the risk of a single point of failure. This is particularly important in IoT networks, where thousands of devices might be interconnected. Each device in a blockchain network is authenticated and authorized through a consensus mechanism, ensuring that no unauthorized devices can gain access. Blockchain can also enhance the security of communication between IoT devices. By encrypting data and distributing it across a network of nodes, blockchain ensures that information cannot be altered or intercepted without detection. This makes it significantly harder for attackers to tamper with the data being exchanged between devices.
Zero Trust architecture operates by treating every device and user as untrusted until verified. In a Zero Trust framework, or secure access service edge (SASE), every device must be authenticated and continuously verified before it can access network resources to control authorized and secure access to IoT systems []. The approach minimizes the risk of unauthorized access, as even devices already within the network are not exempt from scrutiny. Continuous verification ensures that compromised devices can be detected and isolated promptly.
8.12. Monitoring and Maintenance
Effective monitoring and maintenance are critical in safeguarding against threats, ensuring compliance, and promoting the longevity of technological assets []. Continuous monitoring involves using advanced tools and technologies to detect and respond to real-time anomalies. This proactive approach enables organizations to identify potential threats and address them before they escalate into significant issues. Modern continuous monitoring tools leverage artificial intelligence (AI) and ML to analyze vast amounts of data and identify patterns that may indicate security breaches or performance issues. These tools provide real-time alerts, detailed reports, and actionable insights, allowing IT teams to respond swiftly and effectively. Early Detection of Threats: By continuously analyzing network traffic, system logs, and user behavior, organizations can detect anomalies that may signify cyberattacks or other malicious activities.
Improved Incident Response with real-time alerts and detailed reports enables IT teams to respond quickly to potential threats, minimizing damage and reducing downtime. Compliance Assurance by continuous monitoring helps organizations meet regulatory requirements by providing evidence of ongoing security measures and incident response activities. Enhanced Performance with monitoring tools can identify performance bottlenecks and other issues, allowing for timely maintenance and optimization of systems and devices. An effective incident response plan should encompass the following key phases:
- Preparation: Establish a dedicated incident response team, define roles and responsibilities, and provide training on incident response procedures.
- Detection and Analysis: Implement monitoring tools to identify potential incidents and establish procedures for analyzing and prioritizing threats.
- Containment, Eradication, and Recovery: Develop strategies for containing and eradicating threats, and outline steps for recovering affected systems and data.
- Post-Incident Activities: Conduct a thorough review of the incident, document lessons learned, and update the incident response plan accordingly.
- Implement an incident response plan by preparing and practicing a plan for handling security breaches.
- Regularly test devices and systems for vulnerabilities.
Regularly practicing the incident response plan through simulations and tabletop exercises is essential for ensuring that all team members are familiar with their roles and responsibilities. These exercises can help identify gaps in the plan and provide opportunities for improvement.
There are several types of vulnerability testing, each with a specific focus:
- Penetration Testing: Simulates real-world attacks on systems and networks to identify vulnerabilities and test the effectiveness of security measures.
- Network Scanning: Scans networks for open ports, insecure configurations, and other vulnerabilities that attackers could exploit.
- Application Security Testing: Analyzes web and mobile applications for security flaws, such as SQL injection, XSS, and insecure authentication mechanisms.
- Configuration Audits: Reviews system and network configurations to ensure they adhere to security best practices and organizational policies.
A comprehensive vulnerability management program involves the following steps:
- Asset Inventory: Maintain an up-to-date inventory of all devices, systems, and applications within the organization.
- Vulnerability Assessment: Regularly conduct vulnerability assessments to identify potential security weaknesses.
- Prioritization: Prioritize vulnerabilities based on their severity, potential impact, and the likelihood of exploitation.
- Remediation: Implement remediation measures to address identified vulnerabilities, such as applying patches, updating configurations, or enhancing security controls.
- Verification: Verify that remediation measures have been successfully implemented and that vulnerabilities have been addressed.
- Reporting and Documentation: Document all vulnerability assessments, remediation activities, and verification results for future reference and compliance purposes.
The review of IoT security best practices shows that effective protection requires a comprehensive and layered strategy that integrates both traditional measures such as secure authentication, encryption, and access control with advanced approaches like AI-driven threat detection, blockchain-based trust models, and Zero Trust architectures. Importantly, security cannot be treated as a one-time implementation but must extend across the entire lifecycle of IoT devices, from secure boot and patch management to monitoring, incident response, and decommissioning. Compliance with global standards (e.g., IoTSF, NIST, ISO/IEC 27001) provides an essential baseline, while industry-specific adaptations ensure contextual relevance. Ultimately, the lesson is that IoT security depends not only on technical safeguards but also on the continuous interplay of prevention, detection, compliance, and maintenance, ensuring resilience in an environment where new devices and threats emerge daily.
9. Conclusions and Future Challenges
In this article, we have extended the reviews made by [] on IoT architecture and [] on IoT sensing. We focused on the IoT security threats and summarized key findings from a systematic literature review, implications of the findings for industry and policymakers, recommendations for improving IoT security and mitigating existing threats, examined IoT architectural types, applications, breakthroughs, and limitations, and highlighted IoT security threats in different areas and preventative measures and solutions. The findings highlight the following improvements:
- Susceptibility to hacking and unauthorized access, data interception, and DoS attacks, with threats emerging from various areas in technology.
- Several preventive measures have been recommended, e.g., threat-modeling approaches to ensure that IoT security countermeasures are in place, threats to attack surface can be mitigated, data transmission can be secured and encrypted, and so on.
- Robust authentication mechanisms to verify identities.
- Constant updates for users on IDs, IPs, and vulnerability patches.
- Improvements in industries and daily life, such as process enhancement, predictive management, and faster tracking.
- Securing communication in IoT networks which includes selecting secure protocols, implementing network segmentation, and configuring robust firewall rules. By following these best practices, you can protect your IoT devices and the sensitive data they handle from potential threats.
- Continuous innovation and breakthroughs in edge computing, resulting in lower data processing latency, reliable communication, accurate data analytics, and decision-making processes, thereby improving security and transparency in IoT and data exchanges.
- Adhering to established IoT security standards for protecting the integrity, confidentiality, and availability of data in IoT deployments. Organizations can mitigate security risks, ensure compliance with regulations, and build trust with their stakeholders in the rapidly evolving IoT landscape.
- By combining universally applicable design principles with industry-specific considerations, IoT architects can create systems that are secure, efficient, and tailored to operational environments. The key is balancing broad best practices with the nuances of specific applications to maximize effectiveness.
- By systematically applying a threat-modeling approach, organizations can better secure their IoT architectures, protect sensitive data, and ensure the reliable operation of their IoT systems.
- Effective monitoring and maintenance, ensuring the security performance and longevity of technology assets, preparing and practicing an incident response plan, and regular testing to proactively address potential threats and maintain a robust security posture, ultimately supporting the organization’s system efficiency and reliability of systems and devices.
To conclude, IoT security, with its immense benefits, resolves security challenges in applications and introduces breakthroughs and proactive measures essential for protecting the integrity and functionality of systems, reduces costs associated with post-deployment fixes, and ensures compliance with regulatory and industry standards. Resilience by strengthening the architecture against both known and emerging threats improves awareness and stakeholder understanding of IoT risks and mitigation strategies. The rapid expansion of IoT technology necessitates robust security measures to protect against the growing array of threats. Emerging technologies offer powerful tools to enhance IoT security and can safeguard IoT networks, ensuring that the benefits of connectivity are not overshadowed by security vulnerabilities. As the IoT landscape continues to evolve, staying ahead of potential threats with innovative security solutions will be crucial for maintaining the integrity and reliability of connected devices.
With ongoing evolution, innovation, and vigilant security practices, IoT will be key to sustainable developments in systems and technology. Emerging developments such as post-quantum cryptography (PQC) [] also present promising directions for securing IoT and IoE systems. PQC algorithms, including lattice-based [] and hash-based schemes [], are being actively tested for their ability to withstand quantum adversaries while remaining lightweight enough for constrained IoT devices. Although a comprehensive review of PQC is beyond the scope of this paper, acknowledging its potential highlights the importance of preparing IoT security architectures for the quantum era. Future studies may therefore focus specifically on the integration of PQC within IoT/IoE infrastructures as a dedicated line of research.
Another important area for future investigation is the energy consumption behavior of IoT nodes under attack conditions. In normal duty cycling, nodes alternate between active and sleep states to conserve energy. However, during certain attacks, such as flooding or denial-of-service, nodes are forced to process excessive requests, leading to abnormal current draw and accelerated battery depletion. Profiling this behavior using node energy tracing can provide valuable insights into attack detection and mitigation strategies. Although a detailed simulation study is beyond the scope of this survey, future research should incorporate such an analysis to better understand the resilience of IoT systems against energy-draining threats.
While this survey has primarily focused on IoT security architectures, threats, and defenses, it is important to note that the Internet of Everything (IoE) is increasingly being discussed as a broader paradigm that extends beyond device interconnectivity to encompass people, data, and processes. Several recent studies [,,] have begun to explore the security implications of IoE, including large-scale trust management, cross-domain interoperability, and post-quantum secure communication frameworks. Although IoE was not the main focus of this work, its overlap with IoT indicates a valuable avenue for future surveys and comparative analyses.
Author Contributions
Conceptualization, S.Y.O.; Methodology, K.S.L. and S.Y.O.; Formal Analysis, K.S.L. and S.Y.O.; Investigation, K.S.L.; Visualization, K.S.L.; Writing—Original Draft, K.S.L.; Project Administration, S.Y.O., M.S.S. and N.M.A.; Supervision, S.Y.O., M.S.S. and N.M.A.; Writing—Review and Editing, S.Y.O. and Y.J.C. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Not applicable (no new data were created).
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| ABE | Attribute-Based Encryption |
| AI | Artificial Intelligence |
| AMQP | Advanced Message Queuing Protocols |
| ANN | Artificial Neural Network |
| ASICs | Application-specific Integrated Circuits |
| CAP | Constrained Application Protocols |
| CIAS | CIA and Safety |
| CoAP | Constrained Application Protocol |
| DDS | Data Distribution Service |
| DoS | Denial of service |
| DP | Differential Privacy |
| DREAD | Damage, Reproductivity, Exploitability, Affected Users, Discoverability |
| DTLS | Datagram Transport Layer Security |
| FPGA | Field-programmable Gate Arrays |
| HSMs | Hardware Security Modules |
| IC | Integrated Chips |
| IDS | Intrusion-detection System |
| IoT | Internet of Things |
| IoTSF | IoT Security Foundation |
| LTE | Long-Term Evolution |
| LVQ | Linear Vector Quantization |
| ML | Machine Learning |
| MQTT | Message Queuing Telemetry Transport |
| NFC | Near Field Communication |
| OTA | Over-the-air |
| OTP | One-time Password |
| PKI | Public Key Infrastructure |
| QoS | Quality of Service |
| RFID | Radiofrequency Identification |
| RQ | Research Questions |
| RSA | Rivest–Shamir–Adleman |
| SASE | Secure Access Service Edge |
| SDL | Service Description Language |
| SLR | Systematic Literature Review |
| SOA | Service-oriented Architecture |
| SOC | System-on-a-chip |
| SSL | Secure Sockets Layer |
| STRIDE | Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege |
| TLS | Transport Layer Security |
| TSN | Time-Sensitive |
| URLLC | Ultra-reliable Low-latency Communication |
| VPN | Virtual Private Network |
| WSN | Wireless Sensor Networks |
| WTLS | Wireless Transport Layer Security |
| XSS | Cross-site Scripting |
References
- Mandal, S. Internet of Things (Part 1). Introduction. Available online: http://www.csharpcorner.com/uploadfile/f88748/internet-of-things-iot-an-introduction/ (accessed on 31 May 2025).
- Whitmore, A.; Agarwal, A.; Da Xu, L. The Internet of Things—A survey of topics and trends. Inf. Syst. Front. 2015, 17, 261–274. [Google Scholar] [CrossRef]
- Jia, X.; Feng, O.; Fan, T.; Lei, Q. RFID technology and its applications in Internet of Things (IoT). In Proceedings of the 2nd IEEE International Conference on Consumer Electronics, Communications and Networks (CECNet), Yichang, China, 21–23 April 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 1282–1285. [Google Scholar]
- Singh, K.J. A survey of IoT platforms: Create your own internet of things. IEEE Consum. Electron. Mag. 2017, 6, 57–68. [Google Scholar] [CrossRef]
- Bandyopadhyay, D.; Sen, J. Internet of things: Applications and challenges in technology and standardization. Wirel. Pers. Commun. 2011, 58, 49–69. [Google Scholar] [CrossRef]
- ITU NGN-GSI Rapporteur Group. Requirements for Support of USN Applications and Services in NGN Environment; ITU: Geneva, Switzerland, 2010. [Google Scholar]
- Miorandi, D.; Sicari, S.; De Pellegrini, F.; Chlamtac, I. Internet of things: Vision, applications and research challenges. Ad Hoc Networks 2012, 10, 1497–1516. [Google Scholar] [CrossRef]
- Bhatia, R. Top 5 Internet of Things (IoT) Initiatives by Government of India. IoT India Mag. Available online: https://analyticsindiamag.com/ai-trends/top-5-internet-things-initiatives-government-india/ (accessed on 31 December 2024).
- Ministry of Electronics and Information Technology (MeitY). Internet of Things (IoT) Policy Framework; Government of India: New Delhi, India. Available online: https://icrier.org/policy_bank/internet-of-things-iot/ (accessed on 18 June 2025).
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- da Silva, A.F.; Ohta, R.L.; dos Santos, M.N.; Binotto, A.P.D. A Cloud-Based Architecture for the Internet of Things Targeting Industrial Devices Remote Monitoring and Control. IFAC-PapersOnLine 2016, 49, 108–113. [Google Scholar] [CrossRef]
- Sethi, P.; Sarangi, S.R. Review article: Internet of Things: Architectures, protocols, and applications. J. Electr. Comput. Eng. 2017, 2017, 1–25. [Google Scholar] [CrossRef]
- Bhattacharyya, N.; Bandhopadhyay, R. Electronic nose and electronic tongue. In Nondestructive Evaluation of Food Quality; Springer: Berlin/Heidelberg, Germany, 2010; pp. 73–100. [Google Scholar]
- Brewster, C.; Roussaki, I.; Kalatzis, N.; Doolin, K.; Ellis, K. IoT in agriculture: Designing a Europe-wide large-scale pilot. IEEE Commun. Mag. 2017, 55, 26–33. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Karakostas, B. A DNS architecture for the Internet of Things: A case study in transport logistics. Procedia Comput. Sci. 2013, 19, 594–601. [Google Scholar] [CrossRef]
- Wang, F.; Ge, B.; Zhang, L.; Chen, Y.; Xin, Y.; Li, X. A system framework of security management in enterprise systems. Syst. Res. Behav. Sci. 2013, 30, 287–299. [Google Scholar] [CrossRef]
- Roman, R.; Najera, P.; Lopez, J. Securing the Internet of Things. Computer 2011, 44, 51–58. [Google Scholar] [CrossRef]
- Hossain, M.M.; Fotouhi, M.; Hasan, R. Towards an Analysis of Security Issues, Challenges, and Open Problems in the Internet of Things. In Proceedings of the 2015 IEEE World Congress on Services (SERVICES), New York, NY, USA, 27 June–2 July 2015; pp. 21–28. [Google Scholar] [CrossRef]
- Kotha, H.D.; Gupta, V.M. IoT application, a survey. Int. J. Eng. Technol. 2018, 7, 636–640. [Google Scholar] [CrossRef]
- Kasmi, M.; Bahloul, F.; Tkitek, H. Smart home based on Internet of Things and cloud computing. In Proceedings of the SETIT 2016, Hammamet, Tunisia, 18–20 December 2016; IEEE: Hammamet, Tunisia, 2016; pp. 82–86. [Google Scholar]
- Kotey, S.D.; Tchao, E.T.; Gadze, J.D. On distributed denial of service current defense schemes. Technologies 2019, 7, 19. [Google Scholar] [CrossRef]
- Singh, M.; Rajan, M.; Shivraj, V.; Balamuralidhar, P. Secure MQTT for Internet of Things (IoT). In Proceedings of the ICCSNT 2015, Gwalior, India, 4–6 April 2015; IEEE: Gwalior, India, 2015; pp. 746–751. [Google Scholar]
- Granjal, J.; Monteiro, E.; Silva, J.S. Security for the Internet of Things: A survey of existing protocols and open research issues. IEEE Commun. Surv. Tutor. 2015, 17, 1294–1312. [Google Scholar] [CrossRef]
- Rizvi, S.; Kurtz, A.; Pfeffer, J.; Rizvi, M. Securing the Internet of Things (IoT): A security taxonomy for IoT. In Proceedings of the TrustCom/BigDataSE 2018, New York, NY, USA, 1–3 August 2018; IEEE: New York, NY, USA, 2018; pp. 163–168. [Google Scholar]
- Greene, S.S. Security Program and Policies: Principles and Practices; Pearson Education: London, UK, 2014. [Google Scholar]
- Iova, O.; Picco, G.P.; Istomin, T.; Kiraly, C. RPL: The routing standard for the Internet of Things… or is it? IEEE Commun. Mag. 2016, 54, 16–22. [Google Scholar] [CrossRef]
- Tiwari, S.; Trivedi, M.C.; Mishra, K.K.; Misra, A.; Kumar, K.K. Smart innovations in communication and computational sciences. In Proceedings of the ICSICCS 2018, Punjab, India, 15–16 June 2017; Springer: Berlin/Heidelberg, Germany, 2018; Volume 851. [Google Scholar]
- Alaba, F.A.; Othman, M.; Hashem, I.A.T.; Alotaibi, F. Internet of Things security: A survey. J. Netw. Comput. Appl. 2017, 88, 10–28. [Google Scholar] [CrossRef]
- Rakić, K. Internet of Things (IoT) in education: Opportunities and challenges. In Digital Transformation in Education and Artificial Intelligence Application. MoStart 2023; Vasić, D., Kundid Vasić, M., Eds.; Communications in Computer and Information Science; Springer: Cham, Switzerland, 2023; Volume 1827, pp. 91–104. [Google Scholar] [CrossRef]
- Atmani, A.; Kandrouch, I.; Hmina, N.; Chaoui, H. Big data for Internet of Things: A survey on IoT frameworks and platforms. In Proceedings of the International Conference on Artificial Intelligence and Symbolic Computation, Marrakech, Morocco, 8–11 July 2019; Springer: Cham, Switzerland, 2019; pp. 59–67. [Google Scholar] [CrossRef]
- Azure. Azure: IoT Technologies and Protocols: A Guide to IoT Technologies and Protocols. Microsoft Azure Documentation. Available online: https://azure.microsoft.com/en-us/solutions/iot/iot-technology-protocols (accessed on 13 June 2021).
- AVSystem. IoT Standards and Protocols Guide—Protocols of the Internet of Things. White Paper, 24 May 2019, Updated 4 March 2020. Available online: https://avsystem.com/blog/iot/iot-protocols-and-standards (accessed on 28 May 2025).
- AWS. AWS IoT Core—Authorization. Amazon Web Services Documentation. 2020. Available online: https://docs.aws.amazon.com/iot/latest/developerguide/iot-authorization.html (accessed on 30 June 2025).
- Bhoyar, P.; Sahare, P.; Dhok, S.B.; Deshmukh, R.B. Communication technologies and security challenges for Internet of Things: A comprehensive review. AEU–Int. J. Electron. Commun. 2019, 99, 81–99. [Google Scholar] [CrossRef]
- Gregersen, C. A Complete Guide to IoT Protocols and Standards in 2021. Blog, 18 December 2020. Available online: https://www.nabto.com/guide-iot-protocols-standards/ (accessed on 30 June 2025).
- Chakrabarty, S.; Engels, D.W. A secure IoT architecture for smart cities. In Proceedings of the 13th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2016; IEEE: Las Vegas, NV, USA, 2016; pp. 812–813. [Google Scholar] [CrossRef]
- Chanal, P.M.; Kakkasageri, M.S. Security and privacy in IoT: A survey. Wirel. Pers. Commun. 2020, 115, 1667–1693. [Google Scholar] [CrossRef]
- Deogirikar, J.; Vidhate, A. Security attacks in IoT: A survey. In Proceedings of the I-SMAC 2017, Palladam, India, 10–11 February 2017; IEEE: Palladam, India, 2017; pp. 32–37. [Google Scholar] [CrossRef]
- Di Martino, B.; Rak, M.; Ficco, M.; Esposito, A.; Maisto, S.A.; Nacchia, S. Internet of things reference architectures, security and interoperability: A survey. Internet Things 2018, 1, 99–112. [Google Scholar] [CrossRef]
- Almubark, H.; Masmali, O. The awareness of Internet of Things (IoT) privacy risk: A survey study. In Proceedings of the Future Technologies Conference (FTC) 2022, Volume 2, Vancouver, BC, Canada, 20–21 October 2022; Arai, K., Ed.; Lecture Notes in Networks and Systems. Springer: Cham, Switzerland, 2023; Volume 560, pp. 202–220. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A survey on IoT security: Application areas, security threats, and solution architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Fobe, J.L.A.O.; Nogueira, M.; Batista, D.M. A new defensive technique against sleep deprivation attacks driven by battery usage. In Proceedings of the XXI Brazilian Symposium on Information and Computational System Security (SBSeg 2022), Santa Maria, Brazil, 12–15 September 2022; SBC: São Paulo, Brazil, 2022. [Google Scholar] [CrossRef]
- Jeyanthi, N.; Thandeeswaran, R. (Eds.) Security Breaches and Threat Prevention on the Internet of Things; IGI Global: Hershey, PA, USA, 2017. [Google Scholar] [CrossRef]
- Joshitta, R.S.M.; Arockiam, L. Security in IoT environment: A survey. Int. J. Inf. Technol. Mech. Eng. 2016, 2, 1–8. Available online: https://www.researchgate.net/publication/308648065_Security_in_IoT_Environment_A_Survey (accessed on 31 March 2025).
- Harisaiprasad, K. The Features and Challenges of IoT-Based Access Control. ISACA Now Blog, 8 May 2019. Available online: https://www.isaca.org/resources/news-and-trends/isaca-now-blog/2019/the-features-and-challenges-of-iot-based-access-control (accessed on 15 January 2025).
- Hassan, A.; Nizam-Uddin, N.; Quddus, A.; Hassan, S.R.; Rehman, A.U.; Bharany, S. Navigating IoT Security: Insights into Architecture, Key Security Features, Attacks, Current Challenges and AI-Driven Solutions Shaping the Future of Connectivity. CMC 2024, 81, 3499–3559. [Google Scholar] [CrossRef]
- Khattak, H.A.; Shah, M.A.; Khan, S.; Ali, I.; Imran, M. Perception layer security in Internet of Things. Future Gener. Comput. Syst. 2019, 100, 144–164. [Google Scholar] [CrossRef]
- Kumar, R.; Kumar, S.; Arjariya, P. A comprehensive survey of security challenges and threats in Internet of Things. In Proceedings of the 2021 5th International Conference on Information Systems and Computer Networks (ISCON), Mathura, India, 22–23 October 2021; IEEE: Mathura, India, 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Chulerttiyawong, D.; Jamalipour, A. Sybil attack detection in Internet of Flying Things-IoFT: A machine learning approach. IEEE Internet Things J. 2023, 10, 12854–12866. [Google Scholar] [CrossRef]
- Kumar, V.; Jha, R.K.; Jain, S. NB-IoT security: A survey. Wireless Pers. Commun. 2020, 113, 2661–2708. [Google Scholar] [CrossRef]
- Buttyan, L. 9 important security requirements to consider for IoT systems. Blog, 25 February 2021. Available online: https://iotac.eu/9-important-security-requirements-to-consider-for-iot-systems/ (accessed on 1 December 2024).
- Mena, D.M.; Papapanagiotou, I.; Yang, B. Internet of things: Survey on security. Inf. Secure. J. A Glob. Perspect. 2018, 27, 162–182. [Google Scholar] [CrossRef]
- Achir, M.; Abdelli, A.; Mokdad, L. Service discovery and selection in IoT: A survey and a taxonomy. J. Netw. Comput. Appl. 2022, 200, 103331. [Google Scholar] [CrossRef]
- Mervin, M. Top Network Access Control Challenges and How to Tackle Them. Blog, 17 January 2024. Available online: https://www.portnox.com/blog/network-access-control/top-network-access-control-challenges-and-how-to-tackle-them/ (accessed on 30 November 2024).
- Nawir, M.; Amir, A.; Yaakob, N.; Lynn, O.B. Internet of Things (IoT): Taxonomy of security attacks. In Proceedings of the ICED 2016, Phuket, Thailand, 11–12 August 2016; IEEE: Kuala Lumpur, Malaysia, 2016; pp. 321–326. [Google Scholar] [CrossRef]
- Ngu, A.H.; Gutierrez, M.; Metsis, V.; Nepal, S.; Sheng, Q.Z. IoT middleware: A survey on issues and enabling technologies. IEEE Internet Things J. 2016, 4, 1–20. [Google Scholar] [CrossRef]
- Norton. IoT: Internet of Things (IoT) Security: 9 Ways to Help Protect Yourself. Norton Blog. 2020. Available online: https://us.norton.com/blog/iot/securing-the-internet-of-things (accessed on 18 April 2021).
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A survey on Internet of Things: Architecture, enabling technologies, security and privacy, and applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Panchiwala, S.; Shah, M. A comprehensive study on critical security issues and challenges of the IoT world. J. Data Inf. Manag. 2020, 2, 257–278. [Google Scholar] [CrossRef]
- Ippolito, P.P. An introduction to the Internet of Things. Blog, 26 August 2019. Available online: https://www.freecodecamp.org/news/introduction-to-iot-internet-of-things/ (accessed on 31 August 2019).
- Sain, M.; Kang, Y.J.; Lee, H.J. Survey on security in Internet of Things: State of the art and challenges. In Proceedings of the ICACT 2017, PyeongChang, Republic of Korea, 19–22 February 2017; IEEE: PyeongChang, Republic of Korea, 2017; pp. 699–704. [Google Scholar] [CrossRef]
- Amyx, S. Managed PKI Certificates: One Step at a Time Toward Securing the IoT. Blog. 2016. Available online: https://medium.com/@ScottAmyx/managed-pki-certificates-one-step-at-a-time-toward-securing-the-iot-8b4c539c8ec (accessed on 28 December 2020).
- Tanaka, S.; Mimura, N.; Tanaka, M.; Fujishima, K.; Ohashi, T. IoT system security issues and solution approaches. IoT Secur.—Hitachi Rev. 2016, 65, 359. Available online: https://www.hitachihyoron.com/rev/archive/2016/r2016_08/111/index.html (accessed on 18 December 2024).
- Salman, T.; Jain, R. A survey of protocols and standards for Internet of Things. arXiv 2019, arXiv:1903.11549. Available online: https://arxiv.org/abs/1903.11549 (accessed on 20 December 2024). [CrossRef]
- Nwazor, T. IoT Security Challenges and 5 Effective Ways to Handle Them. IoT Zone Blog, 15 November 2018. Available online: https://dzone.com/articles/iot-security-challenges-and-5-effective-ways-to-ha-1 (accessed on 31 January 2020).
- Vashi, S.; Ram, J.; Modi, J.; Verma, S.; Prakash, C. Internet of Things (IoT): A vision, architectural elements, and security issues. In Proceedings of the I-SMAC 2017, Palladam, India, 10–11 February 2017; IEEE: Palladam, India, 2017; pp. 492–496. [Google Scholar] [CrossRef]
- WolfSSL Inc. WolfSSL Embedded SSL/TLS Library. Available online: https://www.wolfssl.com/ (accessed on 31 July 2025).
- Zhang, C.; Green, R. Communication security in Internet of Things: Preventive measure and avoid DDoS attack over IoT network. In Proceedings of the 18th Symposium on Communications & Networking (CNS ‘15), Alexandria, VA, USA, 12–15 April 2015; Society for Computer Simulation International: Alexandria, VA, USA, 2015; pp. 8–15. [Google Scholar]
- Zhang, F.Z.; Yang, D.K.; Zhi, C. Introduction of IoT. Lecture Slides. 2010. Available online: https://jhzhang.cn/resources/A050801G/Ch1.pdf (accessed on 1 December 2023).
- Ali, R.F.; Muneer, A.; Dominic, P.D.D.; Taib, S.M.; Ghaleb, E.A.A. Internet of Things (IoT) security challenges and solutions: A systematic literature review. In Advances in Cyber Security. ACeS 2021; Abdullah, N., Manickam, S., Anbar, M., Eds.; Communications in Computer and Information Science; Springer: Singapore, 2021; Volume 1487, pp. 123–140. [Google Scholar] [CrossRef]
- Rejeb, A.; Rejeb, K.; Treiblmaier, H.; Applloni, A.; Alghamdi, S.; Alhasawi, Y.; Iranmanesh, M. The Internet of Things (IoT) in healthcare: Taking stock and moving forward. Internet Things 2023, 22, 100721. [Google Scholar] [CrossRef]
- Tay, Y.H.; Ooi, S.Y.; Pang, Y.H.; Gan, Y.H.; Lew, S.L. Ensuring privacy and security on banking websites in Malaysia: A cookies scanner solution. J. Inform. Web Eng. 2023, 2, 153–167. [Google Scholar] [CrossRef]
- Lai, J.-F.; Heng, S.-H. Secure file storage on cloud using hybrid cryptography. J. Inform. Web Eng. 2022, 1, 1–18. [Google Scholar] [CrossRef]
- Chuah, W.-H.; Chong, S.-C.; Chong, L.-Y. The assistance of eye blink detection for two-factor authentication. J. Inform. Web Eng. 2023, 2, 111–121. [Google Scholar] [CrossRef]
- Ray, P.P. A survey on Internet of Things architectures. J. King Saud Univ.–Comput. Inf. Sci. 2018, 30, 291–319. [Google Scholar] [CrossRef]
- Mrabet, H.; Belguith, S.; Alhomoud, A.; Jemai, A. A survey of IoT security based on a layered architecture of sensing and data analysis. Sensors 2020, 20, 3625. [Google Scholar] [CrossRef]
- Pau, K.N.; Lee, V.W.Q.; Ooi, S.Y.; Pang, Y.H. The development of a data collection and browser fingerprinting system. Sensors 2023, 23, 3087. [Google Scholar] [CrossRef]
- Lee, V.W.Q.; Ooi, S.Y.; Pang, Y.H. Assessing the Importance of Browser Fingerprint Attributes towards User Profiling through Clustering Algorithms. In Proceedings of the ISCAIE 2023, Penang, Malaysia, 20–21 May 2023; IEEE: Penang, Malaysia, 2023; pp. 326–331. [Google Scholar] [CrossRef]
- ISO/IEC 30141:2024; Internet of Things (IoT)—Reference Architecture (Edition 2). International Organization for Standardization: Geneva, Switzerland, 2024.
- The Government of the Hong Kong Special Administrative Region. Practice Guide for Internet of Things Security, Version 1.2; The Government of the HKSAR: Hong Kong, China, 2024; pp. 12–17.
- Mislaw, H.; Dora, K.; Mrio, K.; Ivana, P.Z. Efficient data management in agricultural IoT: Compression, security and MQTT protocol analysis. Sensors 2024, 24, 3517. [Google Scholar] [CrossRef] [PubMed]
- Agali, K.; Masrom, M.; Abdul Rahim, F.; Yahya, Y. IoT-based remote monitoring system: A new era for patient engagement. Healthc. Technol. Lett. 2024, 11, 437–446. [Google Scholar] [CrossRef] [PubMed]
- Kong. The Critical Role of API Security in the Internet of Things (IoT). Blog, 2 August 2024. Available online: https://konghq.com/blog/enterprise/iot-api-security-guide (accessed on 31 December 2024).
- Khaled, A.E.; Helal, S. Interoperable communication framework for bridging RESTful and topic-based communication in IoT. Future Gener. Comput. Syst. 2019, 92, 628–643. [Google Scholar] [CrossRef]
- Benomar, Z.; Garofalo, M.; Georgantas, N.; Longo, F.; Merlino, G.; Puliafito, A. Bridging IoT protocols with the Web of Things: A path to enhanced interoperability. In Proceedings of the 2024 IEEE International Conferences on Internet of Things (iThings), Green Computing & Communications (GreenCom), Cyber, Physical & Social Computing (CPSCom), Smart Data (SmartData), and Congress on Cybermatics, Copenhagen, Denmark, 19–22 August 2024; IEEE: Copenhagen, Denmark, 2024; pp. 44–51. [Google Scholar] [CrossRef]
- Zhou, J.; Liu, J. Research on Key Technologies for Connected Vehicle Autonomous Driving Based on 5G Big Data. Appl. Math. Nonlinear Sci. 2024, 9, 1–14. [Google Scholar] [CrossRef]
- Azim, A.W.; Bazzi, A.; Fatima, M.; Shubair, R.; Chafii, M. Dual-Mode Time Domain Multiplexed Chirp Spread Spectrum. IEEE Trans. Veh. Technol. 2023, 72, 16086–16097. [Google Scholar] [CrossRef]
- Yuga. DREAD Threat Modelling Methodology. Practical DevSecOps, 9 March 2023. Available online: https://www.practical-devsecops.com/dread-threat-modeling/ (accessed on 20 December 2023).
- SECNORA. What is Threat Model STRIDE and DREAD? SECNORA Blog, 22 May 2022. Available online: https://secnora.com/blog/what-is-threat-model-stride-and-dread/ (accessed on 31 December 2022).
- Cornelius, T. The CIA Triad is Insufficient in the Age of AI/OT/IoT. Blog, 6 March 2023. Available online: https://www.linkedin.com/pulse/cia-triad-insufficient-age-aiotiot-tom-cornelius (accessed on 31 December 2023).
- Microsoft. Secure Boot and Trust Boot. Microsoft Documentation, 7 October 2024. Available online: https://learn.microsoft.com/en-us/windows/security/operating-system-security/system-security/trusted-boot (accessed on 30 November 2024).
- Thales. Hardware Security Modules (HSMs). Thales Technical Brief, 14 July 2020. Available online: https://cpl.thalesgroup.com/encryption/hardware-security-modules (accessed on 31 August 2020).
- What Is Hardware Security Module (HSM)? Available online: https://www.fortinet.com/resources/cyberglossary/hardware-security-module (accessed on 7 October 2025).
- Spektor, H. Understanding IoT Security: Threats, Standards & Best Practices. Sternum IoT Blog, 21 February 2024. Available online: https://sternumiot.com/iot-blog/understanding-iot-security-challenges-standards-and-best-practices/ (accessed on 30 October 2024).
- Soori, M.; Arezoo, B.; Dastres, R. Internet of Things for smart factories in Industry 4.0: A review. IoT Pract. 2023, 3, 192–204. [Google Scholar] [CrossRef]
- Chawla, D.; Mehra, P.S. A Roadmap from Classical Cryptography to Post-Quantum Resistant Cryptography for 5G-Enabled IoT: Challenges, Opportunities and Solutions. Internet Things 2023, 24, 100950. [Google Scholar] [CrossRef]
- Ahmadunnisa, S.; Mathe, S.E. A Comprehensive Review on Hardware Implementations of Lattice-Based Cryptographic Schemes. J. Syst. Archit. 2025, 167, 103486. [Google Scholar] [CrossRef]
- Sedghighadikolaei, K.; Yavuz, A.A.; Nouma, S.E. Signer-Optimal Multiple-Time Post-Quantum Hash-Based Signature for Heterogeneous IoT Systems. Internet Things 2025, 33, 101694. [Google Scholar] [CrossRef]
- Banaeian Far, S.; Imani Rad, A.; Hosseini Bamakan, S.M.; Rajabzadeh Asaar, M. Toward Metaverse of Everything: Opportunities, Challenges, and Future Directions of the next Generation of Visual/Virtual Communications. J. Netw. Comput. Appl. 2023, 217, 103675. [Google Scholar] [CrossRef]
- Wijaksana, S.N.; Putra, S.A. Internet of Everything for Monitoring Exhaust Gas Emissions on Green Campuses: A Survey. Procedia Comput. Sci. 2024, 245, 1057–1064. [Google Scholar] [CrossRef]
- Zhang, K.; Li, M.; Zhang, B.; Chu, P.; Che, G. High-Accurate Range Acquisition for LFMCW Radar with Optimized Maximum Likelihood Estimation towards Internet of Everything. Phys. Commun. 2025, 70, 102646. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).