Abstract
Blockchain’s immutability, while enhancing transparency and trust, presents challenges when erroneous or sensitive content must be modified. To address this, we propose a novel cryptographic primitive called Time-Modifiable Chameleon Hash (TMCH), enabling controlled and time-modifiable data redaction in blockchain systems. TMCH enhances traditional chameleon hashes by embedding a time parameter into hash generation and verification, and it supports class-adaptive collision computation via a new Update algorithm. We formally define the security model for TMCH and analyze the relationships among uniqueness, indistinguishability (IND), and collision resistance (CR). This paper presents a concrete construction based on the Boneh–Boyen signature scheme and completes its security analysis and proof. Finally, the efficiency and practicality of the proposed scheme are validated through experimental comparisons with existing algorithms. Our results show that relaxing the uniqueness requirement does not compromise overall security, while enabling traceable and time-aware redactions. The proposed TMCH achieves strong security guarantees and practical efficiency, making it well suited for applications such as compliant data redaction and time-sensitive blockchain transactions.
1. Introduction
Blockchain technology, known for its distributed ledger architecture, is widely adopted for recording cryptocurrency transactions—Bitcoin [1] being a prime example—because of its inherent transparency and openness. As the technology has evolved rapidly, its applications have expanded well beyond digital currencies to areas such as government services, healthcare, and the judiciary. Accordingly, the data recorded on the blockchain have become increasingly rich and sensitive. However, while the immutability of blockchain is designed to ensure data integrity and security, it also presents significant practical challenges: once illegal, malicious, or privacy-infringing content is recorded on-chain, it becomes virtually impossible to delete, potentially leading to long-term harm for individuals and society.
The introduction of the European Union’s General Data Protection Regulation (GDPR), which enshrines the “right to be forgotten”, has intensified this tension. Specifically, the regulation grants individuals the right to request the deletion of their personal data when certain conditions are met. However, this legal entitlement fundamentally conflicts with the immutable nature of blockchain, thereby triggering an inherent conflict between regulatory compliance and blockchain’s design principles. To address this, researchers have started investigating ways to incorporate controlled mutability into blockchains without compromising their fundamental properties. A prominent approach in this direction is the concept of redactable blockchains, which permits the modification of on-chain data under rigorous cryptographic safeguards.
In a seminal work presented at EuroS&P 2017, Ateniese et al. [2] introduced the idea of replacing traditional collision-resistant hash functions (e.g., SHA-256) in blockchain systems with a trapdoor hash function known as the chameleon hash (CH). This approach enables a block initially committed with content m and randomness r to be altered to a new block with content by computing new randomness , such that the chameleon hash output remains unchanged. Fundamentally, when the modifier possesses the corresponding private trapdoor key, they can efficiently generate such collisions, ensuring that the hash value of equals that of . This allows for controlled block modifications while preserving the integrity of the hash links.
When implementing cryptographic primitives like chameleon hashes for redactable blockchains, it is essential to address three fundamental challenges simultaneously: security, scalability, and decentralization. However, as highlighted by the well-known blockchain “Trilemma” [3], achieving all three within a single solution remains highly challenging. From a security standpoint, the redaction mechanism must withstand key exposure threats and provide semantic security comparable to that of public key encryption. At the same time, the redaction operations must be efficient enough to avoid impairing overall system performance. Moreover, in alignment with the decentralization principles of blockchain, the approach should avoid reliance on any single trusted authority. These competing demands lead to a critical question: is it possible to design a practical chameleon hash scheme that effectively balances these conflicting requirements?
To address this challenge, we propose a secure and efficient chameleon hash scheme termed TMCH. TMCH facilitates blockchain redactions with traceability and fine-grained access control, clearly defining who is authorized to modify data and the permissible time frames for such modifications. It introduces time-bound validity for redactions and enforces redaction policies via cryptographic constraints. By embedding temporal and policy conditions within the hash structure, TMCH enables authorized entities to generate valid hash collisions while preserving consistency throughout the blockchain. This design offers a practical and integrated solution that balances security, scalability, and decentralization, providing a strong foundation for the deployment of redactable blockchain systems in real-world scenarios.
Our objective is to explore whether the violation of uniqueness can be rigorously formalized and utilized without compromising overall security and whether TMCH can function as a practical cryptographic primitive for the construction of secure, time-sensitive applications. Specifically, we pose the following question:
Is it possible to construct a provably secure TMCH scheme that deliberately breaks the uniqueness property, satisfies formal IND and CR properties, and supports at least one practical application?
1.1. Contributions
The main contributions of this work are summarized as follows.
- We propose a novel Time-Modifiable Chameleon Hash (TMCH) scheme that integrates time verifiability into its core algorithms. This allows users to incorporate time parameters in hash generation and verification while preserving the ability to compute collisions akin to traditional adaptation algorithms. A key innovation in TMCH is the introduction of a new collision-finding algorithm, Update, which relaxes the conventional uniqueness constraint of chameleon hashes. This supports dynamic collision adjustments with respect to time, forming the fundamental functional extension of the scheme.
- We formalize the security requirements of TMCH and theoretically analyze the relationships among uniqueness, IND, and CR. Our proofs demonstrate how the uniqueness property can be leveraged to establish IND and CR, thereby providing a solid security foundation for the scheme.
- We validate the practicality and effectiveness of the proposed TMCH scheme through comprehensive security proofs and performance evaluations, demonstrating its efficiency and security suitability for real-world applications.
1.2. Structure
This paper is organized as follows. Section 2 provides a comparative analysis of existing research on chameleon hash applications in editable blockchains, summarizing key advancements and limitations of state-of-the-art schemes in balancing redactability and security. Section 3 introduces the necessary preliminaries, including formal definitions of algebraic groups, bilinear maps, the computational Diffie–Hellman (CDH) assumption, and other foundational cryptographic concepts. It reviews the construction of CH schemes, formalizes their required security properties, and illustrates design principles using Pedersen commitments as an example. The section concludes by introducing the construction of the TMCH scheme. Section 4 focuses on a black-box construction of TMCH, detailing its core components and formally defining its security guarantees. Through a series of game-based experiments, it rigorously proves key properties such as correctness, typical indistinguishability, new indistinguishability, typical collision resistance, and new collision resistance. Section 5 describes a concrete white-box instantiation of TMCH based on the Boneh–Boyen signature (BBS) scheme, accompanied by thorough analysis and formal proofs of five critical security properties specific to this instantiation. Section 6 evaluates the proposed scheme’s efficiency and practicality through experiments and comparative tables, demonstrating its performance advantages over existing approaches. Finally, Section 7 concludes the paper and discusses promising avenues for future research.
2. Related Works
CH functions are fundamental cryptographic primitives enabling controlled mutability in blockchain systems. In recent years, a variety of enhanced CH-based schemes have been proposed, targeting key challenges such as fine-grained access control, revocable trapdoor delegation, auditable rewriting, and decentralized trust models. These advancements have significantly improved the practical applicability of redactable blockchain frameworks by seamlessly integrating policy enforcement, accountability, and flexible deployment.
Nevertheless, despite these advances, the majority of existing CH constructions still lack time verifiability—an essential feature in enabling auditability, regulatory compliance, and time-sensitive rewriting policies. Furthermore, current schemes typically lack support for arbitrary or class-adaptive collision computation, thereby restricting their flexibility in adapting to dynamic blockchain environments.
Derler et al. [4] proposed an attribute-based chameleon hash scheme that enables fine-grained rewriting by associating trapdoor capabilities with user attributes. While it strengthens access control, it does not support temporal verifiability or flexible collision logic.
Xu et al. [5] introduced a revocable policy-based chameleon hash, enabling redaction privileges to be revoked dynamically. While improving control and forward security, this scheme still lacks the ability to verify the timing of collisions, and its collision computation remains inflexible.
Xu et al. [6] further enhanced accountability in redactable blockchains by incorporating auditable rewriting logs. This design improves traceability but still does not integrate mechanisms for time-verifiable redactions or support arbitrary, class-adaptive collisions.
Duan et al. [7] proposed a T-times chameleon hash scheme that limits the number of rewrites per trapdoor key. Despite introducing a form of temporal limitation, the number of allowed rewrites is fixed in advance and cannot be cryptographically verified in real time. Furthermore, this approach does not support arbitrary collision computation beyond a preset rewrite count.
Li et al. [8] developed a decentralized chameleon hash framework to eliminate centralized trust assumptions. However, their scheme does not address temporal verifiability or the computation of adaptive collisions, both critical for compliance and auditing in real-world blockchains.
Dong et al. [9] combined chameleon hashing with multi-authority attribute-based encryption to enable access-controlled redactable consortium blockchains. Although this enhances policy enforcement, the scheme suffers from high complexity and lacks mechanisms for time verifiability and arbitrary collision computation.
Chen et al. [10] proposed a time-verifiable policy-based chameleon hash (TPCH) for building traceable redactable blockchains. This scheme supports both private and public redaction modes, enables time traceability of redactions by introducing a time parameter, and incorporates a new Update algorithm to prevent the abuse of redaction powers. Experimental and theoretical analyses have demonstrated its feasibility and practicality. Its advantages include high efficiency in public redaction, support for fine-grained redaction, and time traceability. However, it has drawbacks: the performance of ABE-based private redaction is significantly affected by factors such as the number of attributes, resulting in insufficient efficiency, and the use of numerous cryptographic primitives increases the system complexity.
To better understand the limitations and characteristics of these existing works, we provide a comparative summary in Table 1.

Table 1.
Comparison of chameleon hash schemes for blockchain applications.
As illustrated in the table, most previous works lack support for time verifiability and arbitrary collision computation—two critical features that are essential for modern, auditable, and policy-driven redactable blockchain systems. Although various schemes improve certain aspects like access control or decentralization, none simultaneously offer time-bound hashing, traceable time-shifted redaction, and class-adaptive collision flexibility within a unified, provably secure framework.
To address this gap, we propose a novel TMCH scheme that directly incorporates time verifiability into the hash construction and introduces an Update algorithm supporting class-adaptive, cross-time collision computation. Our proposed TMCH offers a unified solution for controlled, accountable, and time-sensitive data redaction in blockchain systems. We provide a concrete implementation based on the Boneh–Boyen signature scheme and formally analyze its security properties and performance.
3. System Overview and Building Blocks
To facilitate an understanding of the technical details and algorithms, we summarize commonly used symbols in Table 2.

Table 2.
Summary of notations and abbreviations used in this paper.
3.1. System Framework
Our system introduces a secure, time-aware redactable blockchain framework, built upon a novel cryptographic primitive: TMCH. This construction empowers authorized participants to perform verifiable redactions, while embedding time awareness and collision flexibility directly into the hash function itself.
The system involves four primary roles:
- Key Generation Center (KGC): A trusted authority responsible for initializing system parameters and issuing key pairs to users.
- User: Individuals who publish transactions on the blockchain and require hash integrity with time binding.
- Miner: Nodes that verify transaction validity and append them to the blockchain.
- Modifier: Entities granted permission (and trapdoor knowledge) to perform content redaction under predefined policies.
The lifecycle of a TMCH-based blockchain transaction proceeds through several distinct stages.
The KGC runs the Setup algorithm to generate global parameters and a master public key. Each user subsequently generates their personal key pair via the KeyGen algorithm.
To publish a transaction, a user uses the Hash algorithm to compute a chameleon hash bound to a specific time. Given inputs —the public key, message content, and a time label (e.g., block timestamp)—the algorithm outputs a hash value along with randomness . This time binding ensures that any modification to m or t will alter the hash unless the trapdoor is known.
The user submits to the blockchain. The miner, serving as a validator, uses the public key to run the Ver algorithm and checks whether the hash value is consistent with the message m, randomness , and timestamp t. Upon successful verification, the transaction is recorded on the ledger.
If redaction is required due to regulatory compliance, error correction, or content withdrawal, an authorized modifier holding the corresponding trapdoor can invoke the Adapt algorithm to compute a collision, generating a new message and randomness . This process preserves the original hash value, ensuring blockchain consistency while replacing the underlying content.
To enhance auditability, TMCH introduces the Update algorithm, which enables cross-time collision generation. Unlike Adapt, Update keeps the original message m unchanged while generating a new time label and a corresponding randomizer . This functionality allows the system to record when a redaction was performed or authorized and enforce time-based access control policies (e.g., “edits permitted only after 7 days” or “redactions visible only before a specified deadline”).
In summary, our system leverages TMCH to provide the following:
- Time verifiability: Every hash embeds a verifiable time component, enabling audit and delay enforcement.
- Collision flexibility: The trapdoor holder can compute both message collisions (for content updates) and time collisions (for timestamp adjustments), supporting diverse redaction policies (e.g., time-bound edits or content-specific modifications).
- Hash consistency preservation: Hash values remain unchanged across authorized redactions (whether message or time updates), ensuring the integrity of the blockchain’s chain structure.
A graphical summary of this framework and role interactions is provided in Figure 1.
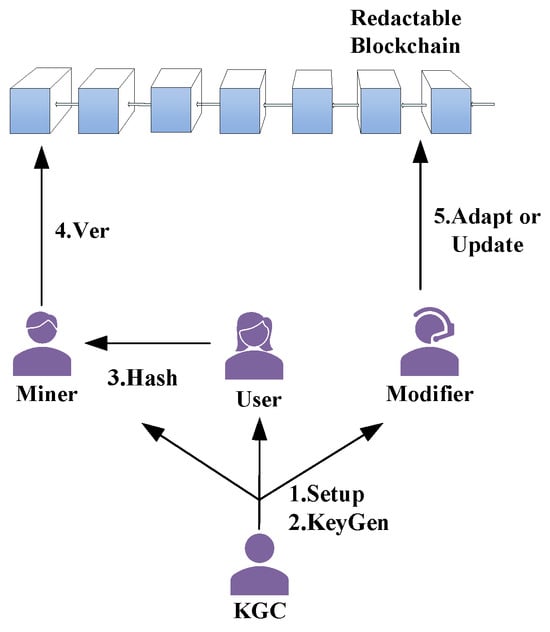
Figure 1.
System framework.
3.2. Groups and Bilinear Maps
Given two multiplicative groups and of the same order p, and a generator g of , a symmetric bilinear pairing is a mapping satisfying the following properties: (1) bilinearity—for all and , it holds that ; (2) non-degeneracy—there exists such that is a generator of ; (3) computability—for every , computing is efficient.
Specifically, this algebraic structure provides a rigorous mathematical framework for TMCH’s hash computation and verification algorithms, ensuring that operations like hash generation and time-shifted collision adjustment are both secure (resistant to forgery) and computationally feasible.
3.3. Intractable Problems
Definition 1. ℓ-SDH Assumption:
Introduced by Boneh and Boyen in [11], the strong Diffie–Hellman assumption states that, given inputs for some , where is a cyclic group of prime order p with generator g, it is computationally infeasible to find a pair for any .
Definition 2. CDH Assumption:
Given a tuple with , where is a cyclic group of prime order p generated by g, it is difficult to compute the element .
Definition 3. Inverse CDH Assumption:
For inputs with , in the context of a cyclic group of prime order p generated by g, it is difficult to calculate .
Definition 4. DDH Assumption:
Given for , where is a cyclic group of prime order p with generator g, deciding whether Z equals is considered computationally infeasible.
These assumptions serve as the theoretical bedrock for TMCH’s security proofs, underpinning the guarantees of indistinguishability and collision resistance and ensuring the scheme’s reliability under standard computational complexity assumptions.
3.4. Chameleon Hash
Definition 5. Chameleon Hash (CH):
Let a CH scheme be CH=Setup,KeyGen,Hash,Ver,Adapt
as follows.
- Setup: On inputting a security parameter λ, output the public parameter . Let be implicit hereafter.
- KeyGen: On inputting a public parameter , output the public and private keys and .
- Hash: On inputting a message m and a public key , output a chameleon hash and randomness .
- Ver: On inputting a public key and a triple , output a decision if is valid. Else, output .
- Adapt: On inputting a private key , a message m, and a triple , this trapdoor collision finding (denoted as typical) algorithm outputs new randomness .
Informally, a secure CH should satisfy the following properties.
Correctness:
Every output produced by properly executed
Hash
and
Adapt
procedures must successfully satisfy
Ver. More precisely, for any security parameter λ, for every , for all key pairs , and for each message (where denotes the message space), if , then the verification algorithm yields
Ver
. Furthermore, for any and any , it holds that
Ver. In addition to these correctness criteria, further security assurances are essential.
Indistinguishability: The randomness output generated by Adapt is computationally indistinguishable from the randomness produced by Hash.
Collision Resistance:
No probabilistic polynomial-time (PPT) adversary with access to the
Adapt
oracle should be able to efficiently produce two distinct tuples and such that VerVer with any non-negligible probability. As noted by Camenisch et al. [12], key exposure freeness is a weaker security than collision resistance as it only requires that one cannot find a collision for some new “tag", while collision resistance requires finding no collision for any “tag".
Useful Property—Trapdoor Collisions:
A user with private key should be able to find two tuples and under a given such that VerVer with an overwhelming probability.
3.5. Design Insights
We exemplify the design of CH with construction based on a Pedersen commitment and show how to build a CH with time verifiability. The Pedersen commitment is a popular cryptographic primitive. In this setting, the public key is a group element in associated with public key , and message m is a group element in . We can easily use a standard (non-trapdoor) collision-resistant hash function (e.g., SHA-256) to map arbitrary-length messages to a group element m. Let be randomness, and the Pedersen commitment-based chameleon hash is as follows:
With private key x, one can compute to find a hash collision for arbitrary . However, according to Ateniese et al. [13], the above results in a key exposure problem. The reason is simple. When given a collision tuple and , anyone can compute
to extract the private key x. Thus, the master secret is lost. Accordingly, Chen et al. [14] proposed a CH based on a gap Diffie–Hellman group (where DDH is easy and CDH is difficult to solve). Let a be a random element over . Their hashing algorithm is as follows:
where , is an implicit parameter over used to limit the key exposure problem according to Ateniese et al. [13]. To generate arbitrary collisions for , compute
where . The above scheme is based on the inverse CDH assumption. If given an inverse CDH instance , one can deduce as
which is a solution to the given inverse CDH instance. Since the inverse CDH assumption is intractable, this scheme is key exposure-free. We exemplify how to break the uniqueness requirement and transform Chen et al.’s [14] CH to TMCH. Let us denote the derived construction as TMCH. Let t be a time parameter over . The hashing algorithm for TMCH is
where . To find arbitrary collisions for , the Adapt algorithm (typical collision-finding algorithm) for TMCH is
where To find arbitrary collisions for , the update algorithm (new collision-finding algorithm) is
where . The above Equations (4)–(6) exemplify the dominant algorithms for TMCH based on Chen et al.’s [14] CH. The correctness of Equations (5) and (6) is clear from inspection. We do not use this scheme directly in our construction. We believe that the reader will be able to complete the proof of the above construction after seeing our two different constructions and relevant security proofs.
4. Definitions of TMCH
We formalize the definition and security requirements for TMCH in this section. We focus on discussing the new collision-finding-related security.
4.1. Syntax of TMCH
Based on the CH introduced in Section 3.4, let a TMCH scheme be TMCH = {Setup, KeyGen, Hash, Ver, Adapt, Update} as follows.
- Setup: On inputting a security parameter , output the public parameter . Let be implicit hereafter.
- KeyGen: On inputting a public parameter , output the public and private keys and .
- Hash: On inputting a message m, a public key , and a time t, output a chameleon hash and randomness .
- Ver: With and , additionally input a time t, and output .
- Adapt: With , , and , additionally input a time t and output new randomness .
- Update: On inputting a private key , a triple , and the original time period and new time period , this new trapdoor collision-finding (denoted as new) algorithm outputs new randomness .
4.2. Useful Properties of TMCH
- Typical Trapdoor Collisions: A user possessing the secret key should be capable of generating two tuples and under a given public key such that VerVer holds with an overwhelming probability.
- New Trapdoor Collisions: A user holding the private key should be able to construct two tuples and under a specific public key such that VerVer with an overwhelming probability.
Definition 6. Correctness:
Every output produced by correctly executed procedures—Hash,
Adapt, and
Update—must successfully pass
Ver. Specifically, for all security parameters λ, for all Setup, for all KeyGen, for all ( as time space), and for all Hash, we have
Ver; additionally, for all , for all Adapt, and for Update, we have
VerVer. Moreover, other security guarantees are needed.
Definition 7. Typical Indistinguishability (T-IND):
T-IND requires that it is computationally difficult to distinguish the distributions of chameleon randomness generated by
Adapt
from that of generated by
Hash, as formalized in experiment depicted below.
- Setup: runs Setup and KeyGen, and it gives to .
- Query Phase: selects a random bit . The adversary then proceeds to submit a series of queries to .
- -
- : issues a query with private key , messages and times t, runs Hash to get and Hash to get , respectively. Additionally, runs Adapt. returns ⊥ if or . Otherwise, if , returns , if , returns .
- Guess: makes a guess a for b.
The advantage of in this game is defined as . A TMCH is considered T-IND-secure if any PPT adversary has at most a negligible advantage in λ.
Definition 8. New Indistinguishability (N-IND)
N-IND requires that it is computationally difficult to distinguish the distributions of generated by Update from that of from Hash, as formalized in experiment , denoted as new IND. is defined through the following interaction protocol between the adversary and the challenger .
- Setup: runs Setup and KeyGen, and it gives to .
- Query Phase: selects a random bit . The adversary then proceeds to submit a series of queries to .
- -
- : issues hash or update query on two time and a private key , runs Hash to get and Hash to get , respectively. Additionally, runs Update to get . returns ⊥ if or . Otherwise, if , returns , if , returns .
- Guess: makes a guess for b.
The advantage of in this game is defined as . A TMCH is considered N-IND-secure if any PPT adversary has at most a negligible advantage in λ.
Definition 9. Typical Collision Resistance: (T-CR)
T-CR requires that no probabilistic polynomial-time (PPT) adversary with access to the Adapt oracle can efficiently generate two distinct tuples and under the same timestamp t such that VerVer with non-negligible probability. This notion of security is formally captured by the experiment presented below:
- Setup: runs Setup and KeyGen and gives to , and keeps secret. initiates an empty list .
- Query Phase: adaptively submits a sequence of the following queries to .:
- -
- : issues update query on two time and a tuple , runs Ver. If Ver, return ⊥. Otherwise, runs to get . If , return ⊥. Otherwise, update and return .
- Output: outputs , and it wins the game if: VerVer, and .
The advantage of in this game is defined as . A TMCH is considered typical collision resistant if any PPT adversary has at most a negligible advantage in λ. As it is similar to the next security, we only elaborate the latter one.
Definition 10. New Collision Resistance (N-CR):
N-CR stipulates that no probabilistic polynomial-time (PPT) adversary with access to the
Update
oracle should be able to efficiently produce a tuple satisfying such that VerVer with a non-negligible probability. This security notion is formally defined by the experiment
, which models the interaction between the adversary and the challenger , as described below.
- Setup: runs Setup and KeyGen and gives to and keeps secret. initiates an empty list .
- Query Phase: adaptively submits a sequence of the following queries to :
- -
- : issues update query at two times and a tuple , runs Ver. If , return ⊥. Otherwise, runs Update and returns . Update .
- Output: outputs and , and it wins the game if VerVer, and .
The advantage of in this game is defined as . A TMCH is considered new-collision-resistant in updates if any PPT adversary has at most a negligible advantage in λ.
Remark 1.
We do not describe uniqueness here as we intend to break the uniqueness requirement [12] to achieve the new collision algorithm
Update
. Uniqueness demands that deriving a collision for the same message and chameleon hash is computationally hard. The existence of the
Update
algorithm, as we previously exemplified in Equation (6), naturally breaks the uniqueness assumption. The correctness of Equation (6) is readily apparent upon inspection. More evidence will be provided in the forthcoming constructions.
5. Constructions for TMCH
In this section, we exemplify two concrete constructions for TMCH and provide a full security analysis.
5.1. Construction: TMCH Based on BBS
We introduce the first construction of TMCH based on Boneh and Boyen’s signature (BBS) [11] scheme.
- Setup: Choose a multiplicative group with order p and generator g. Let be a secure collision-resistant hash function. Return public parameter .
- KeyGen: Choose as the private key and compute as the public key. Return the user’s public key and private key .
- Hash: Give and and implicitly choose a customized identity and randomness to compute and . Then, compute a chameleon hash and chameleon randomness . Let be implicit hereafter.
- Ver: Compute and set . Then, verify whether . If the equation holds, return 1; otherwise, return 0.
- Adapt: First, run Ver to verify the correctness. If the result is 0, output ⊥. Otherwise, compute .
- Update: Begin by executing Ver to confirm the validity. If the verification fails (i.e., returns 0), output ⊥. Otherwise, generate updated randomness as .
5.2. Security Analysis of TMCH
Correctness: The correctness of Adapt is as follows:
The correctness of Update is as follows:
Proof of T-IND for BBS-based TMCH Construction.
Our TMCH is T-IND-secure if the DDH and ℓ-SDH assumptions are intractable. Assume that there exists a PPT adversary against our T-IND security according to Definition 7; we can construct an efficient algorithm to solve the DDH and ℓ-SDH assumptions. We only give a sketch of the proof.
When given a DDH instance , ’s goal is to decide whether is a DH-tuple, i.e., in the form of . When given an ℓ-SDH instance , ’s goal is to find where .
simulates the challenger for . It runs Setup to generate . sets as public key and sends to where is unknown. selects random and and sends to ; flips a random coin . The analysis proceeds differently:
- If , computes and . returns to . As observed, if is a DDH tuple, is computed exactly as in Hash.
- If , selects random and to compute and where . Then, uses to replace , and Z to replace , respectively, in simulating the computing of Adapt. Thus, computes . As observed, if is a DDH tuple and , then is computed exactly as in Adapt. Specifically, if , where and x is some unknown private key, then is an answer to the SDH instance.
Based on the above, we can use a sequence of games to show that we can simulate the view of the adversary without giving out any useful information at all, thus reducing our T-IND security to the intractability of the DDH and ℓ-SDH assumptions. A similar proof methodology can be found in [12]. □
Proof of N-IND for BBS-based TMCH Construction.
Our TMCH is N-IND-secure if the DDH and ℓ-SDH assumptions are intractable. The proof is similar to that of T-IND. When given a DDH instance , we construct an algorithm that simulates the challenger for adversary . runs Setup to generate and sets and sends to . selects random and and sends to ; flips a random coin . The analysis proceeds differently:
- If , computes and . returns to . If is a DDH tuple, is computed exactly as in Hash.
- If , selects random to compute and . Then, use to replace , and Z to replace , respectively, in simulating the computing of Update. Thus, computes . Similarly, if is a DDH tuple and , then are computed exactly as in Update. Accordingly, if , is an answer to the SDH instance.
Similarly, we can use a sequence of games to show that our N-IND security holds as long as the DDH and ℓ-SDH assumptions are intractable to solve. □
Proof of T-CR for BBS-based TMCH Construction.
Our TMCH is T-CR-secure if the ℓ-SDH assumption is intractable. Assume that is an efficient adversary against our T-CR; we outline a method to construct a probabilistic polynomial-time (PPT) algorithm capable of solving the ℓ-SDH problem, as defined in [11]. Given an instance of the ℓ-SDH assumption in the form , we represent it as , where each for , with and . In order to derive () as the solution to SDH, where , simulates the challenger for and interacts with as follows.
During the Query Phase, issues distinct queries under the same public key and . is an implicit parameter for each . Assume that .
To generate a response, for every where , produces the corresponding reply as follows. Let . Set polynomial , where are the coefficients of polynomial . Define
Next, we define polynomial and . Expand and define . Then, computes
Since the above holds for , where , the value represents the valid randomness, ensuring a collision for the customized identity under the given public key. The algorithm responds to the adversary with a collection of fresh randomness values, namely .
Output: Adversary wins by output , where and are collisions, is implicit, and has never been queried during the Query Phase such that
where . We have
Using polynomial long division, the polynomial f can be expressed as , where and . From this representation, we can then deduce
Because and has not been queried previously—that is, —the polynomial does not divide . Consequently, the algorithm computes
The algorithm then outputs the pair , where , as the solution to the given ℓ-SDH instance . To analyze and bound the advantage of in solving the ℓ-SDH problem by leveraging , one can follow the approach presented in [11]; the detailed proof is omitted here. □
Proof of N-CR for BBS-based TMCH Construction.
Our TMCH is N-CR-secure if the ℓ-SDH assumption is intractable. Similarly, assume that is an efficient adversary against our N-CR; we can construct a probabilistic polynomial-time (PPT) to solve the ℓ-SDH assumption. Observe that, to satisfy the winning condition of the N-IND game, we have
By transforming the equation, we get
Use to represent , and to represent . We have
This is exactly in the form of T-CR’s winning condition. Thus, CR is transferable to Upd. and the security analysis of T-CR applies to this part as well. □
6. Performance Evaluation
6.1. Experimental Setup
Our scheme was implemented in Java using the JPBC library and deployed on a desktop equipped with an Intel i5-13600KF processor (3.50 GHz) (manufactured by Intel Corporation, with headquarters in Santa Clara, California, United States) and 32 GB of RAM. For pairing operations, we selected a Type-I curve—specifically, a widely adopted Type-I pairing curve compatible with the PBC framework—to ensure a 96-bit security level, balancing computational efficiency and cryptographic strength [15]. The experimental and parametric environment is summarized in Table 3.

Table 3.
Experimental environment configuration.
6.2. Theoretical Complexity Comparison
Table 4 presents a systematic comparison of the computational complexity of four chameleon hash schemes, focusing on five critical operations at the user side: KeyGen, Hash, Adapt, Revoke or Update, and Verify. Both the DSS+19 and XHY+22 schemes require exponentiation operations in the KeyGen phase, and the Hash and Adapt operations scale linearly as , indicating that their computational overhead grows with attribute set size k and the dimensions of the access control matrix . In contrast, the proposed TMCH scheme maintains constant complexity across all operations, requiring only minimal exponentiation and group insertion steps, demonstrating significant efficiency improvements. While KXY+19 also achieves complexity in the KeyGen and Adapt phases, it requires more computationally expensive pairing operations during the Hash and Verify phases. Notably, TMCH stands out as the only scheme achieving constant complexity in Revoke/Update operations, whereas other schemes either do not support this feature (marked ) or lack explicit complexity specifications. This comprehensive performance advantage makes TMCH particularly suitable for large-scale applications that require frequent update operations.

Table 4.
Complexity comparisons of recent CH works.
6.3. Runtime Performance Evaluation
For single operations of each dominant algorithm, we list the costs in Table 5. It presents the running costs of the key algorithms involved in chameleon hash operations across two schemes: the proposed TMCH and the baseline KXY-19. The operations include Hash generation, Verification, Adapt (collision under the same time), and Update (cross-time collision). TMCH consistently outperforms KXY-19 in all four operations. Specifically, the Hash computation in TMCH takes 99 ms, which is 24.4% faster than in KXY-19 (131 ms). The Verification and Adapt steps show even more pronounced improvements: 121 ms vs. 208 ms (41.8% faster) and 201 ms vs. 289 ms (30.4% faster), respectively. The Update operation—unique to TMCH for time-shifted collisions—is also executed more efficiently (205 ms vs. 273 ms). These results demonstrate that TMCH not only extends the functional capabilities (e.g., time verifiability and arbitrary collision) but also reduces the computational overhead compared to previous constructions, making it more practical for blockchain environments with frequent verification and occasional redactions.

Table 5.
Running costs.
For further quantitative analysis, we evaluated our proposed TMCH scheme in comparison with two representative baselines: the policy-based chameleon hash (PCH) scheme [4] and the KXY+19 scheme [16]. All three schemes were tested under policy set sizes ranging from 1 to 50 and from to , enabling a fair and comprehensive comparison across different levels of operational complexity.
Figure 2 illustrates the relationship between the policy set size and running time for three schemes: our TMCH, KXY+19, and DSS+19. As the policy size increases from 1 to 50, TMCH maintains nearly constant performance (approximately 90–100 ms), demonstrating excellent scalability. In contrast, DSS+19 exhibits a steep increase in running time, exceeding 270 ms at the largest policy size, due to its linear complexity with respect to the policy size. KXY+19 performs better than DSS+19 but worse than TMCH, showing moderate growth with increasing policy sizes. These results confirm that TMCH is more efficient and robust under large and complex policy conditions.
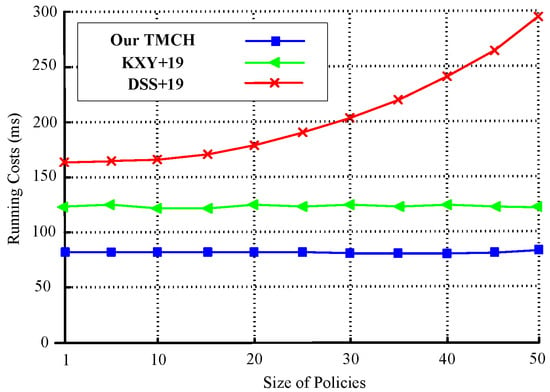
Figure 2.
Hash.
Figure 3 compares the cumulative execution times of TMCH and KXY+19 over 500 runs. TMCH demonstrates significantly better performance, with a total execution time of around 40 s, compared to nearly 90 s for KXY+19. Although both schemes exhibit linear growth, the slope of KXY+19 is much steeper. This highlights TMCH’s efficiency and suitability for environments with frequent hash computations or repeated redactions, such as dynamic blockchain systems or policy auditing frameworks.
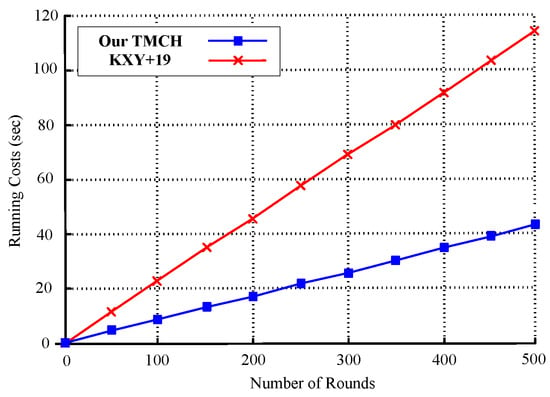
Figure 3.
Ver.
Figure 4 presents the running time under exponentially growing policy sizes, ranging from 2 to 64 for TMCH, KXY+19, and DSS+19. TMCH remains nearly flat, maintaining performance within a narrow band (around 100–110 ms), indicating logarithmic or sub-linear complexity. In contrast, DSS+19 scales poorly, exceeding 450 ms at a policy size of 64. KXY+19 demonstrates moderate scalability but still lags behind TMCH. The superior performance of TMCH under growing complexity validates its design for real-world scenarios with large attribute or policy sets.
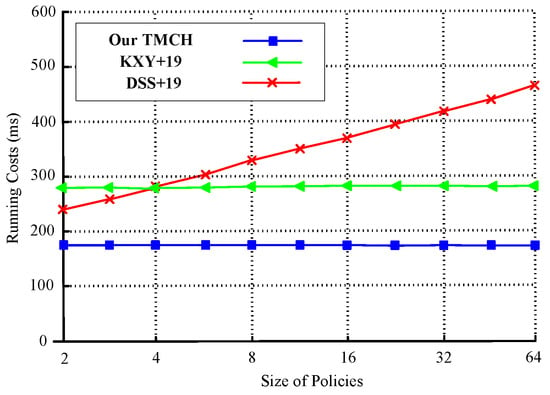
Figure 4.
Adapt.
Figure 5 shows a linear comparison of the cumulative running costs for TMCH and KXY+19 as the number of executions increases from 0 to 500. Both schemes exhibit linear growth, indicating consistent time complexity per operation. TMCH demonstrates better computational efficiency, with the total running time increasing from 0 to approximately 100 s. In contrast, KXY+19 shows a steeper slope, reaching about 130 s at 500 executions. This gap becomes more pronounced as the number of rounds increases, underscoring TMCH’s superior scalability and lower per-operation cost. Such efficiency is particularly advantageous in high-frequency blockchain environments requiring repeated hash generation and verification.
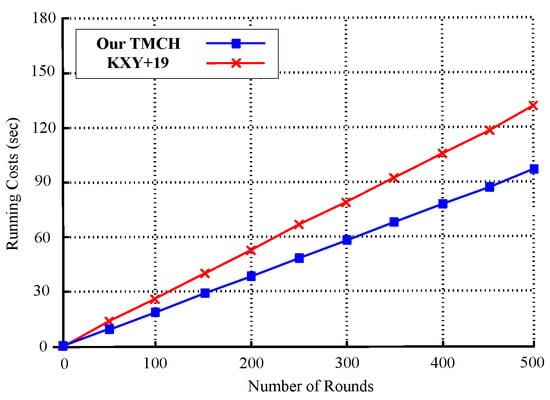
Figure 5.
Update.
7. Conclusions
In this work, we formally address the open problem of non-uniqueness left unresolved by Camenisch et al. [12] and propose a novel Time-Modifiable Chameleon Hash (TMCH) scheme. TMCH introduces a novel trapdoor-based collision-finding algorithm that deliberately breaks the uniqueness property by incorporating time as an explicit parameter into key operations—hashing, verification, and adaptation. Notably, TMCH supports time-dependent arbitrary collision generation while preserving core security properties such as IND and collision resistance (CR). Our scheme achieves security and efficiency comparable to those of existing chameleon hash constructions while enabling temporal control and verifiability.
TMCH is particularly well suited for scenarios requiring time-bound data modification and strong traceability, such as regulatory-compliant blockchain redactions, short-term smart contracts, and tamper-evident log systems. For future work, we plan to explore adding verifiable update mechanisms so that every content change can be transparently audited. Another direction is the design of collaborative redaction protocols, enabling joint authorization and execution by multiple parties, enhancing both trust and security. We also aim to integrate TMCH with privacy-preserving techniques like zero-knowledge proofs, allowing controlled redaction while maintaining data confidentiality.
Author Contributions
Conceptualization, Z.L. and Z.Z.; Methodology, Z.Z.; Software, Z.L.; Validation, Z.L. and Z.Z.; Formal Analysis, Z.L.; Investigation, Z.L.; Resources, Z.Z.; Writing—Original Draft Preparation, Z.L. and Z.Z.; Writing—Review and Editing, Z.L. and Z.Z.; Supervision, Z.Z.; Project Administration, Z.Z.; Funding Acquisition, Z.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the research project on Key Technologies of Quantum-Resistant Cryptographic Algorithms for Network Security Boundary Protection in New Energy Power Stations, Jiangxi Electric Power Company of the State Grid Corporation of China, grant number 521820240017.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: http://bitcoin.org/bitcoin.pdf (accessed on 8 February 2025).
- Ateniese, G.; Magri, B.; Venturi, D.; Andrade, E. Redactable blockchain–or–rewriting history in bitcoin and friends. In Proceedings of the EuroS&P, Paris, France, 26–28 April 2017; pp. 111–126. [Google Scholar]
- Werth, J.; Berenjestanaki, M.; Barzegar, H.; El Ioini, N.; Pahl, C. A Review of Blockchain Platforms Based on the Scalability, Security and Decentralization Trilemma. In Proceedings of the 25th International Conference on Enterprise Information Systems, Prague, Czech Republic, 24–26 April 2023; pp. 146–155. [Google Scholar] [CrossRef]
- Derler, D.; Samelin, K.; Slamanig, D.; Striecks, C. Fine-Grained and Controlled Rewriting in Blockchains: Chameleon-Hashing Gone Attribute-Based. In Proceedings of the NDSS, San Diego, CA, USA, 24–27 February 2019. [Google Scholar]
- Xu, S.; Ning, J.; Ma, J.; Xu, G.; Yuan, J.; Deng, R.H. Revocable policy-based chameleon hash. In Proceedings of the ESORICS, Darmstadt, Germany, 4–8 October 2021; pp. 327–347. [Google Scholar]
- Xu, S.; Huang, X.; Yuan, J.; Li, Y.; Deng, R.H. Accountable and Fine-Grained Controllable Rewriting in Blockchains. IEEE Trans. Inf. Forensics Secur. 2022, 18, 101–116. [Google Scholar] [CrossRef]
- Duan, J.; Wang, W.; Wang, L.; Gu, L. Controlled Redactable Blockchain Based on T-Times Chameleon Hash and Signature. IEEE Trans. Inf. Forensics Secur. 2024, 19, 7560–7572. [Google Scholar] [CrossRef]
- Li, C.; Shen, Q.; Wu, Z. Redactable Blockchain From Decentralized Chameleon Hash Functions, Revisited. IEEE Trans. Comput. 2025, 74, 1911–1920. [Google Scholar] [CrossRef]
- Dong, Y.; Li, Y.; Cheng, Y.; Yu, D. Redactable Consortium Blockchain with Access Control: Leveraging Chameleon Hash and Multi-Authority Attribute-Based Encryption. High-Confid. Comput. 2024, 4, 100168. [Google Scholar] [CrossRef]
- Chen, M.; Xie, G.; Pan, B.; Fang, J.; Xu, Z.; Zhao, Z. Building Traceable Redactable Blockchain with Time-Verifiable Chameleon Hash. Electronics 2025, 14, 846. [Google Scholar] [CrossRef]
- Boneh, D.; Boyen, X. Short signatures without random oracles. In Proceedings of the EUROCRYPT 2004, Interlaken, Switzerland, 2–6 May 2004; Springer: Interlaken, Switzerland, 2004; pp. 56–73. [Google Scholar]
- Camenisch, J.; Derler, D.; Krenn, S.; Pöhls, H.C.; Samelin, K.; Slamanig, D. Chameleon-hashes with ephemeral trapdoors. In Proceedings of the PKC, Amsterdam, The Netherlands, 28–31 March 2017; pp. 152–182. [Google Scholar]
- Ateniese, G.; de Medeiros, B. On the key exposure problem in chameleon hashes. In Proceedings of the ICSCN, Amalfi, Italy, 8–10 September 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 165–179. [Google Scholar]
- Chen, X.; Zhang, F.; Kim, K. Chameleon hashing without key exposure. In Proceedings of the ICIS, Palo Alto, CA, USA, 27–29 September 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 87–98. [Google Scholar]
- Barker, E.B.; Barker, W.C.; Burr, W.E.; Polk, W.T.; Smid, M. Recommendation for Key Management-Part 1: General; National Institute of Standards and Technology, Technology Administration: Gaithersburg, MD, USA, 2006. [Google Scholar]
- Huang, K.; Zhang, X.; Mu, Y.; Rezaeibagha, F.; Du, X.; Guizani, N. Achieving intelligent trust-layer for Internet-of-Things via self-redactable blockchain. IEEE Trans. Ind. Inform. 2019, 16, 2677–2686. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).