Identifying Similar Users Between Dark Web and Surface Web Using BERTopic and Authorship Attribution
Abstract
1. Introduction
- BERTopic was applied to the surface and dark webs to extract the topics from each web, and identical or similar topics between the two webs were extracted utilizing similarity measurements;
- Information about the users creating content on the surface and dark webs was collected, and the unique characteristics of the authors were extracted using authorship attribution;
- Malicious users actively engaged on the surface and dark webs can be identified based on the unique characteristics of the authors;
- Malicious authors engaged in simultaneous activities on the surface and dark webs can be identified using BERTopic and authorship attribution.
2. Related Work
2.1. Dark Web Analysis
2.2. Topic Modeling
2.3. Authorship Attribution
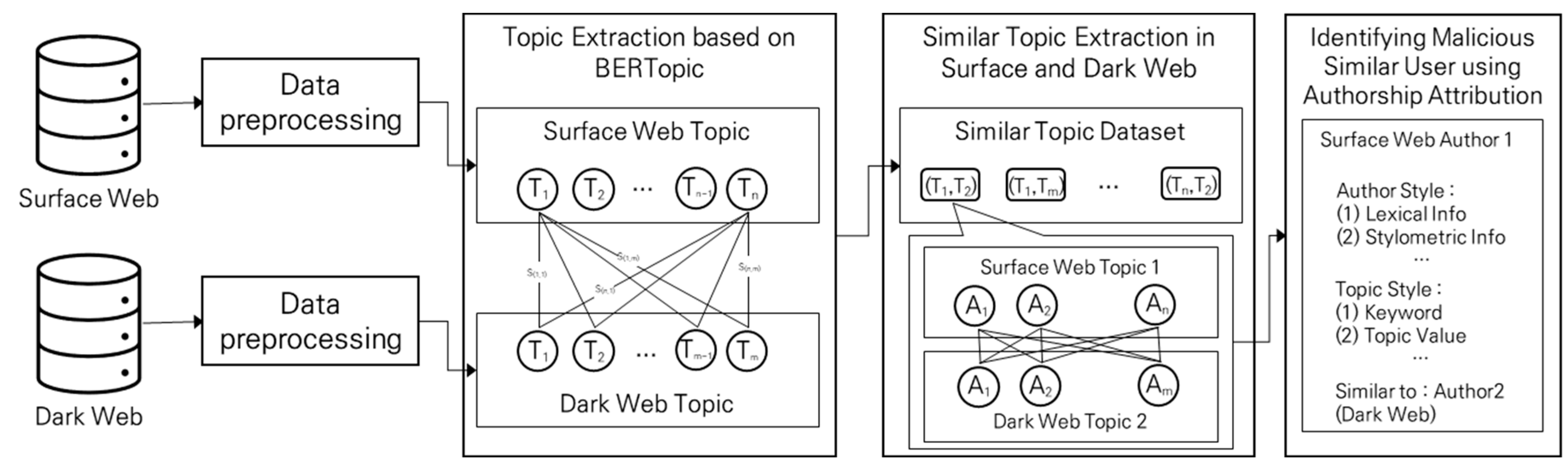
3. Proposed Method
3.1. Data Collection
3.2. Data Preprocessing
3.3. Topic Extraction
3.4. Similar Topic Extraction
3.5. Identifying Malicious Similar Users
4. Experiment and Results
4.1. Dataset
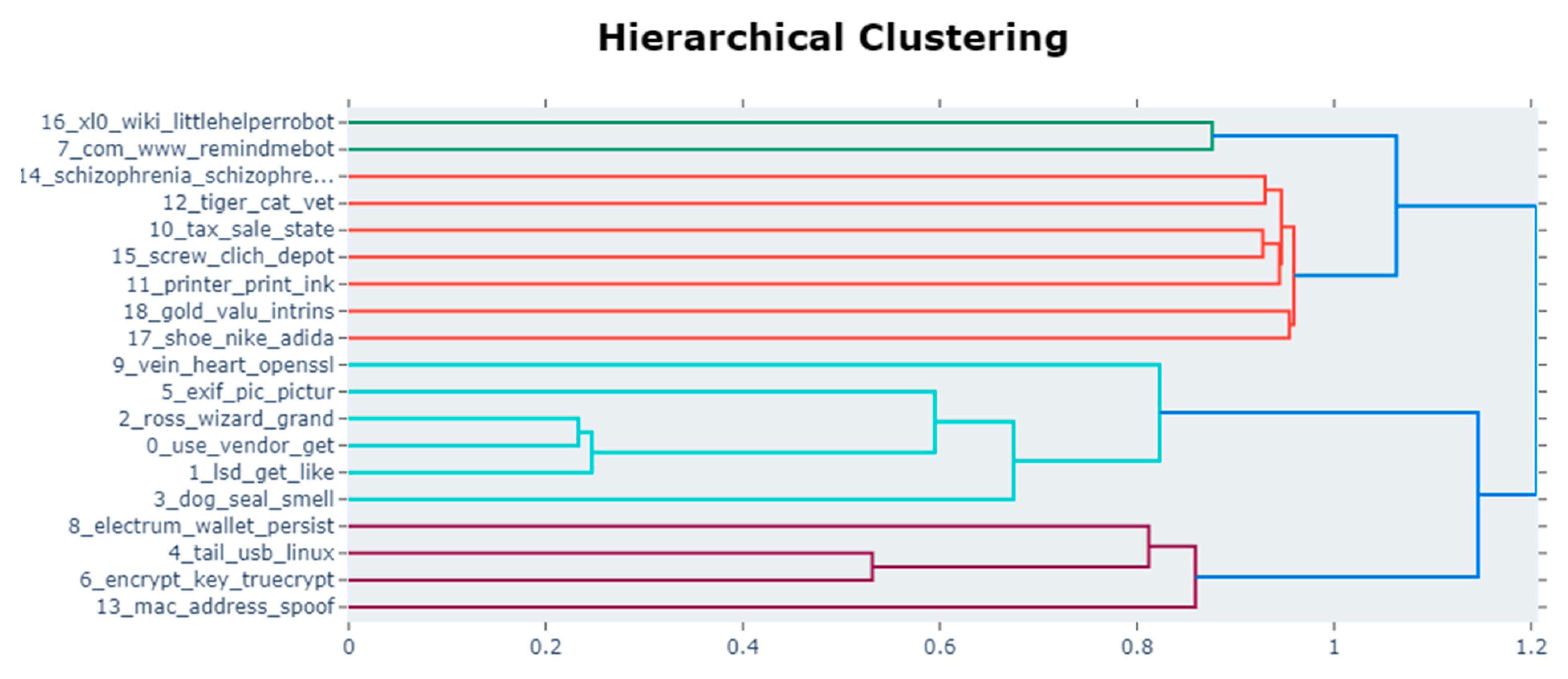
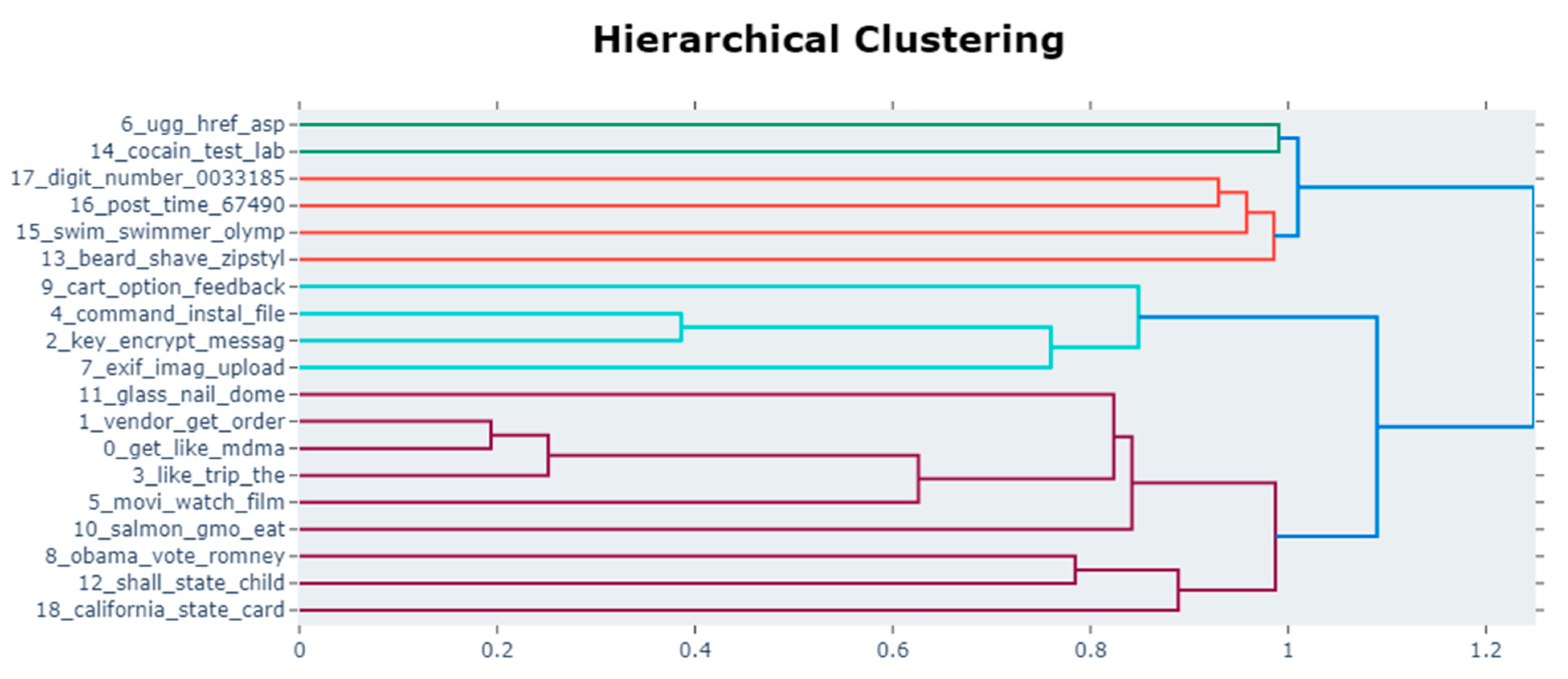
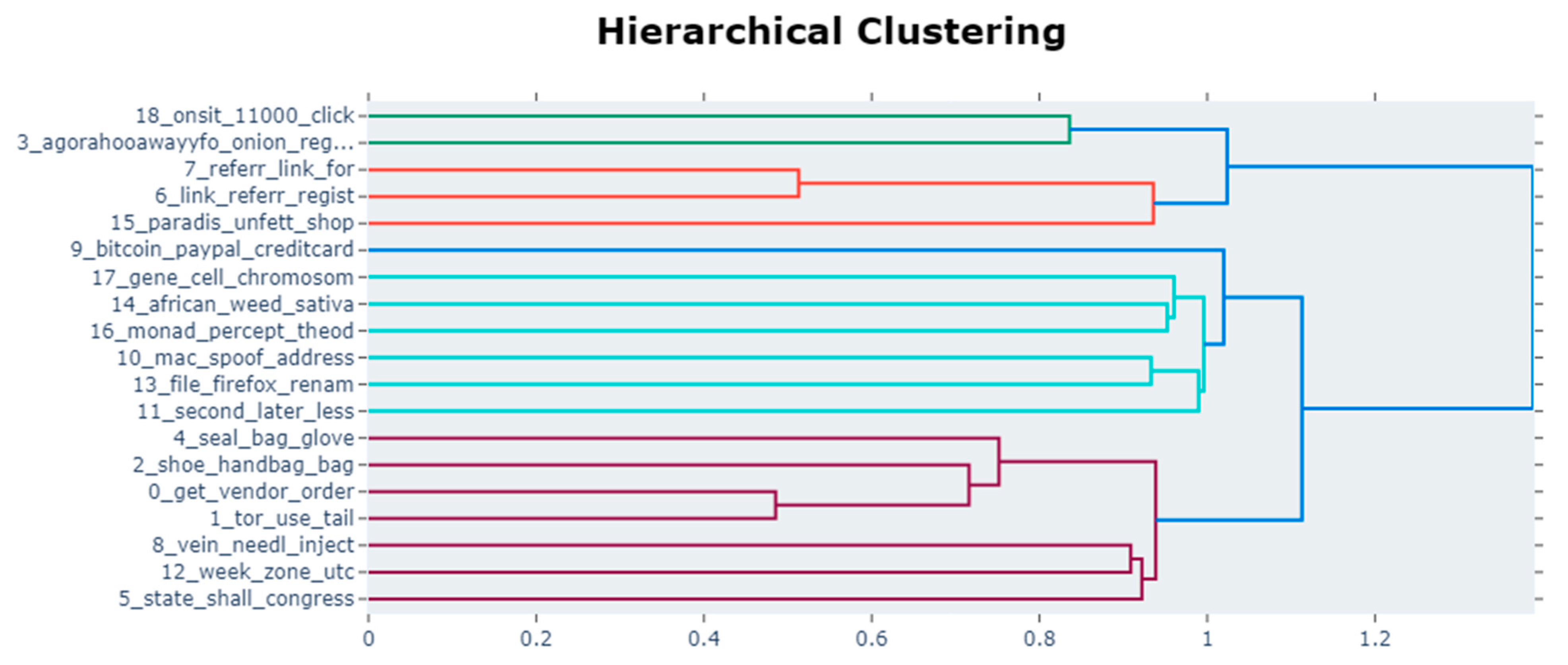
4.2. Topic Similarity Analysis Using BERTopic
4.3. Author Similarity Analysis Using Authorship Attribution
5. Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Al Nabki, M.W.; Fidalgo, E.; Alegre, E.; de Paz, I. Classifying illegal activities on Tor network based on web textual contents. In Proceedings of the 15th Conference of the European Chapter of the Association for Computational Linguistics, Valencia, Spain, 3–7 April 2017; Volume 1, pp. 35–43. [Google Scholar] [CrossRef]
- Beshiri, A.; Susuri, A. Dark web and its impact in online anonymity and privacy: A critical analysis and review. J. Comput. Commun. 2019, 7, 30–43. [Google Scholar] [CrossRef]
- Finklea, K.M. Dark Web; Rep. R44101; Congressional Research Service: Washington, DC, USA, 2017. [Google Scholar]
- Patel, P.B.; Thakor, H.P.; Iyer, S. A comparative study on cyber crime mitigation models. In Proceedings of the 6th International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 13–15 March 2019; pp. 466–470. [Google Scholar]
- Cascavilla, G.; Tamburri, D.A.; Van Den Heuvel, W.-J. Cybercrime threat intelligence: A systematic multi-vocal literature review. Comput. Secur. 2021, 105, 102258. [Google Scholar] [CrossRef]
- Gupta, A.; Maynard, S.B.; Ahmad, A. The dark web phenomenon: A review and research agenda. arXiv 2021, arXiv:2104.07138. [Google Scholar] [CrossRef]
- Minnaar, A. Online ‘underground’ marketplaces for illicit drugs: The prototype case of the dark web website ‘Silk Road. Acta Criminol. Afr. J. Criminol. Vict. 2017, 30, 23–47. [Google Scholar]
- Catakoglu, O.; Balduzzi, M.; Balzarotti, D. Attacks landscape in the dark side of the web. In Proceedings of the Symposium on Applied Computing, Marrakech, Morocco, 3–7 April 2017; pp. 1739–1746. [Google Scholar] [CrossRef]
- Parkar, A.; Sharma, S.; Yadav, S. Introduction to deep web. Int. Res. J. Eng. Technol. 2017, 4, 229–234. [Google Scholar] [CrossRef]
- Basheer, R.; Alkhatib, B. Threats from the dark: A review over dark web investigation research for cyber threat intelligence. J. Comput. Netw. Commun. 2021, 2021, 1302999. [Google Scholar] [CrossRef]
- Lee, S.; Yoon, C.; Kang, H.; Kim, Y.; Kim, Y.; Han, D.; Son, S.; Shin, S. Cybercriminal minds: An investigative study of cryptocurrency abuses in the dark web. In Proceedings of the 26th Annual Network and Distributed System Security Symposium, NDSS 2019, San Diego, CA, USA, 24–27 February 2019. [Google Scholar]
- Ruiz Ródenas, J.M.; Pastor-Galindo, J.; Gómez Mármol, F. A general and modular framework for dark web analysis. Clust. Comput. 2024, 27, 4687–4703. [Google Scholar] [CrossRef]
- Pete, I.; Hughes, J.; Chua, Y.T.; Bada, M. A social network analysis and comparison of six dark web forums. In Proceedings of the 2020 IEEE European symposium on security and privacy workshops (EuroS&PW), Genoa, Italy, 7–11 September 2020; pp. 484–493. [Google Scholar]
- Sabbah, T.; Selamat, A.; Selamat, M.H.; Ibrahim, R.; Fujita, H. Hybridized term-weighting method for dark web classification. Neurocomputing 2016, 173, 1908–1926. [Google Scholar] [CrossRef]
- He, S.; He, Y.; Li, M. Classification of illegal activities on the dark web. In Proceedings of the 2nd International Conference on Information Science and Systems, Tokyo, Japan, 16–19 March 2019; pp. 73–78. [Google Scholar] [CrossRef]
- Cascavilla, G.; Catolino, G.; Ebert, F.; Tamburri, D.A.; van den Heuvel, W.J. “When the code becomes a crime scene” Towards dark web threat intelligence with software quality metrics. In Proceedings of the 2022 IEEE ICSME, Limassol, Cyprus, 3–7 October 2022; pp. 439–443. [Google Scholar] [CrossRef]
- Ball, M.; Broadhurst, R. Data capture and analysis of darknet markets. SSRN 2021, 3344936. [Google Scholar] [CrossRef]
- Ursani, Z.; Peersman, C.; Edwards, M.; Chen, C.; Rashid, A. The impact of adverse events in darknet markets: An anomaly detection approach. In Proceedings of the 2021 IEEE EuroS&PW, Vienna, Austria, 6–10 September 2021; pp. 227–238. [Google Scholar] [CrossRef]
- Alnabulsi, H.; Islam, R. Identification of illegal forum activities inside the dark net. In Proceedings of the 2018 iCMLDE, Sydney, NSW, Australia, 3–7 December 2018; pp. 22–29. [Google Scholar] [CrossRef]
- Jin, Y.; Jang, E.; Cui, J.; Chung, J.-W.; Lee, Y.; Shin, S. DarkBERT: A language model for the dark side of the internet. arXiv 2023, arXiv:2305.08596. [Google Scholar] [CrossRef]
- Dos Reis, E.F.; Teytelboym, A.; ElBahrawy, A.; De Loizaga, I.; Baronchelli, A. Identifying key players in dark web marketplaces through Bitcoin transaction networks. Sci. Rep. 2024, 14, 2385. [Google Scholar] [CrossRef] [PubMed]
- Tavabi, N.; Bartley, N.; Abeliuk, A.; Soni, S.; Ferrara, E.; Lerman, K. Characterizing activity on the deep and dark web. In Proceedings of the 2019 World Wide Web Conference, San Francisco, CA, USA, 13–17 May 2019; pp. 206–213. [Google Scholar] [CrossRef]
- Yang, C.C.; Tang, X.; Thuraisingham, B.M. An analysis of user influence ranking algorithms on Dark Web forums. In Proceedings of the ACM SIGKDD Workshop on Intelligence and Security Informatics, Washington, DC, USA, 25–28 July 2010; pp. 1–7, Article 10. [Google Scholar] [CrossRef]
- Tang, X.; Yang, C.C.; Zhang, M. Who will be participating next? Predicting the participation of Dark Web community. In Proceedings of the ACM SIGKDD Workshop on Intelligence and Security Informatics, Beijing, China, 12 August 2012; Article 1. pp. 1–7. [Google Scholar] [CrossRef]
- Anwar, T.; Abulaish, M. Identifying cliques in dark web forums—An agglomerative clustering approach. In Proceedings of the 2012 IEEE International Conference on Intelligence and Security Informatics, Washington, DC, USA, 11–14 June 2012. [Google Scholar] [CrossRef]
- Alkhatib, B.; Basheer, R.S. Mining the dark web: A novel approach for placing a dark website under investigation. Int. J. Mod. Educat. Comput. Sci. 2019, 11, 1–13. [Google Scholar] [CrossRef][Green Version]
- Chen, H.; Chung, W.; Qin, J.; Reid, E.; Sageman, M.; Weimann, G. Uncovering the dark web: A case study of jihad on the web. J. Am. Soc. Inf. Sci. Technol. 2008, 59, 1347–1359. [Google Scholar] [CrossRef]
- Iliou, C.; Kalpakis, G.; Tsikrika, T.; Vrochidis, S.; Kompatsiaris, I. Hybrid focused crawling on the Surface and the Dark Web. EURASIP J. Inf. Sec. 2017, 2017, 11. [Google Scholar] [CrossRef]
- Sangher, K.S.; Singh, A.; Pandey, H.M. LSTM and BERT based transformers models for cyber threat intelligence for intent identification of social media platforms exploitation from darknet forums. Int. J. Inf. Technol. 2024, 16, 5277–5292. [Google Scholar] [CrossRef]
- Blei, D.M.; Ng, A.Y.; Jordan, M.I. Latent Dirichlet allocation. J. Mach. Learn. Res. 2003, 3, 993–1022. [Google Scholar]
- Ramage, D.; Hall, D.; Nallapati, R.; Manning, C.D. Labeled LDA: A supervised topic model for credit attribution in multi-labeled corpora. In Proceedings of the 2009 Conference on Empirical Methods in Natural Language Processing, Singapore, 6–7 August 2009; pp. 248–256. [Google Scholar]
- Grootendorst, M. BERTopic: Neural topic modeling with a class-based TF-IDF procedure. arXiv 2022, arXiv:2203.05794v1. [Google Scholar] [CrossRef]
- Ríos, S.A.; Muñoz, R. Dark web portal overlapping community detection based on topic models. In Proceedings of the ACM SIGKDD Workshop on Intelligence and Security Informatics, Beijing, China, 12 August 2012; Article 2. pp. 1–7. [Google Scholar]
- Porter, K. Analyzing the DarkNetMarkets subreddit for evolutions of tools and trends using LDA topic modeling. Digit. Investig. 2018, 26, S87–S97. [Google Scholar] [CrossRef]
- Faizan, M.; Khan, R.A. A two-step dimensionality reduction scheme for dark web text classification. In Proceedings of the Ambient Communications and Computer Systems: RACCCS 2019, Ajmer, India, 29–30 May 2019; Hu, Y.C., Tiwari, S., Trivedi, M., Mishra, K., Eds.; Springer: Singapore, 2019; pp. 303–312. [Google Scholar] [CrossRef]
- Bahamazava, K.; Nanda, R. The shift of DarkNet illegal drug trade preferences in cryptocurrency: The question of traceability and deterrence. Forens. Sci. Int. Digit. Investig. 2022, 40, 301377. [Google Scholar] [CrossRef]
- Shin, G.-Y.; Jang, Y.; Kim, D.-W.; Park, S.; Park, A.-R.; Kim, Y.; Han, M.-M. Dark side of the web: Dark web classification based on TextCNN and topic modeling weight. IEEE Access 2024, 12, 36361–36371. [Google Scholar] [CrossRef]
- Pastor-Galindo, J.; Sandlin, H.-Â.; Mármol, F.G.; Bovet, G.; Pérez, G.M. A Big Data architecture for early identification and categorization of dark web sites. Future Gener. Comput. Syst. 2024, 157, 67–81. [Google Scholar] [CrossRef]
- Al-Rowaily, K.; Abulaish, M.; Haldar, N.A.-H.; Al-Rubaian, M. BiSAL—A bilingual sentiment analysis lexicon to analyze Dark Web forums for cyber security. Digit. Investig. 2015, 14, 53–62. [Google Scholar] [CrossRef]
- Dalvi, A.; Bhoir, S.; Naik, N.; Kitkaru, A.; Siddavatam, I.; Bhirud, S. A hybrid TF-IDF and RNN model for multi-label classification of the deep and dark web. Int. J. Adv. Comp. Sci. Appl. 2023, 14. [Google Scholar] [CrossRef]
- Alghamdi, H.; Selamat, A. Techniques to detect terrorists/extremists on the dark web: A review. Data Technol. Appl. 2022, 56, 461–482. [Google Scholar] [CrossRef]
- Ranaldi, L.; Nourbakhsh, A.; Patrizi, A.; Ruzzetti, E.S.; Onorati, D.; Fallucchi, F.; Zanzotto, F.M. The dark side of the language: Pre-trained transformers in the DarkNet. arXiv 2022, arXiv:2201.05613v3. [Google Scholar] [CrossRef]
- Tavabi, N.; Goyal, P.; Almukaynizi, M.; Shakarian, P.; Lerman, K. DarkEmbed: Exploit prediction with neural language models. In Proceedings of the AAAI Conference Artificial Intelligence, New Orleans, LA, USA, 2–7 February 2018; Volume 32. no. 1. [Google Scholar] [CrossRef]
- Murty, C.A.; Rughani, P.H. Sentiment & pattern analysis for identifying nature of the content hosted in the dark web. Indian J. Comput. Sci. Eng. 2021, 12, 1822–1836. [Google Scholar] [CrossRef]
- Deguara, N.; Arshad, J.; Paracha, A.; Azad, M.A. Threat Miner—A text analysis engine for threat identification using dark web data. In Proceedings of the 2022 IEEE International Conference on Big Data, Osaka, Japan, 17–20 December 2022. [Google Scholar] [CrossRef]
- Ranaldi, L.; Ranaldi, F.; Fallucchi, F.; Zanzotto, F.M. Shedding light on the dark web: Authorship attribution in radical forums. Information 2022, 13, 435. [Google Scholar] [CrossRef]
- Litvinova, T.; Litvinova, O.; Panicheva, P. Authorship attribution of Russian forum posts with different types of N-gram features. In Proceedings of the 2019 3rd International Conference on Natural Language Processing and Information Retrieval, Tokushima, Japan, 28–30 June 2019; pp. 9–14. [Google Scholar] [CrossRef]
- Manolache, A.; Brad, F.; Barbalau, A.; Ionescu, R.T.; Popescu, M. VeriDark: A large-scale benchmark for authorship verification on the dark web. Adv. Neural Inf. Process. Syst. 2022, 35, 15574–15588. [Google Scholar]
- Arabnezhad, E.; La Morgia, M.; Mei, A.; Nemmi, E.N.; Stefa, J. A light in the dark web: Linking dark web aliases to real internet identities. In Proceedings of the 2020 IEEE 40th International Conference on Distributed Computing Systems (ICDCS), Singapore, Singapore, 29 November–1 December 2020; pp. 311–321. [Google Scholar] [CrossRef]
- Nazah, S.; Huda, S.; Abawajy, J.H.; Hassan, M.M. An unsupervised model for identifying and characterizing dark web forums. IEEE Access 2021, 9, 112871–112892. [Google Scholar] [CrossRef]
- Nazah, S.; Huda, S.; Abawajy, J.; Hassan, M.M. Evolution of dark web threat analysis and detection: A systematic approach. IEEE Access 2020, 8, 171796–171819. [Google Scholar] [CrossRef]
- Spitters, M.; Klaver, F.; Koot, G.; Van Staalduinen, M. Authorship analysis on dark marketplace forums. In Proceedings of the 2015 European Intelligence and Security Informatics Conference, Manchester, UK, 7–9 September 2015; pp. 1–8. [Google Scholar]
- Klaver, F. Authorship Attribution of Forum Posts. Thesis, Vrije Universiteit Amsterdam, Amsterdam, The Netherlands, 2014. [Google Scholar]
- Sennewald, B. Authorship Attribution in the Dark Web. Master’s Thesis, University of New Brunswick, Fredericton, NB, Canada, 2020. [Google Scholar]
- Benjamin, V.; Chung, W.; Abbasi, A.; Chuang, J.; Larson, C.A.; Chen, H. Evaluating text visualization for authorship analysis. Secur. Inform. 2014, 3, 10. [Google Scholar] [CrossRef]

| Feature Name | Description |
|---|---|
| Average Word Length | The average length of words in the entire document |
| Total Number of Words | The number of words used in the entire document |
| Ratio of Numbers | The ratio of numbers used per sentence |
| Number of Special Characters | The total number of special characters |
| Number of Function Words | The total number of function words |
| Ratio of Sentences Beginning with a Capital Letter | The ratio of sentences that begin with a capital letter in the entire document |
| Ratio of Contractions Used | The ratio of actual contractions among the words that can be formed into contractions |
| Number of Short Words | The number of short words used that are of four letters or fewer |
| Average Number of Words per Sentence | The average number of words used per sentence |
| Number of Words Used | The number of non-duplicate words used in the entire document |
| Number of Punctuation Marks | The number of punctuation marks used |
| Average Number of Punctuation Marks per Sentence | The average number of punctuation marks used per sentence |
| Use of Quotation Marks | Whether quotation marks are used in the entire document |
| Use of Emojis | Whether emojis are used in the entire document |
| Use of URLs | Whether URLs are used in the entire document |
| Dataset | Size | Author | Average Number of Words | Source |
|---|---|---|---|---|
| Agora | 4,195,381 | 12,159 | 143 | Dark Web |
| Silk Road | 614,656 | 30,206 | 119 | Dark Web |
| 106,252 | 17,879 | 84 | Surface Web |
| Name | Keywords |
|---|---|
| Surface Web | ‘lsd’, ‘get’, ‘like’, ‘meth’, ‘drug’, ‘mdma’, ‘take’, ‘good’, ‘would’, ‘know’ ‘exif’, ‘pic’, ‘pictur’, ‘data’, ‘imag’, ‘upload’, ‘photo’, ‘jpg’, ‘camera’, ‘imgur’ ‘encrypt’, ‘key’, ‘truecrypt’, ‘password’, ‘use’, ‘disk’, ‘brute’, ‘drive’, ‘comput’, ‘ae’ ‘schizophrenia’, ‘schizophren’, ‘psychosi’, ‘voic’, ‘hear’, ‘brain’, ‘ndma’, ‘bing’, ‘disord’, ‘xl0’, ‘wiki’, ‘littlehelperrobot’, ‘wut’, ‘github’, ‘mobil’, ‘wikipedia’, ‘http’, ‘judg’, ‘org’ |
| Dark Web (Silk Road) | ‘vendor’, ‘get’, ‘order’, ‘would’, ‘bitcoin’, ‘btc’, ‘like’, ‘make’, ‘use’, ‘account’ ‘key’, ‘encrypt’, ‘messag’, ‘use’, ‘tor’, ‘onion’, ‘pgp’, ‘http’, ‘public’, ‘file’ ‘like’, ‘trip’, ‘the’, ‘think’, ‘get’, ‘karma’, ‘peopl’, ‘one’, ‘gun’, ‘say’ ‘shall’, ‘state’, ‘child’, ‘debt’, ‘bank’, ‘committe’, ‘govern’, ‘unit’, ‘the’, ‘parti’ ‘cocain’, ‘test’, ‘lab’, ‘result’, ‘convert’, ‘maximum’, ‘levamisol’, ‘puriti’, ‘analyz’, ‘level’ |
| Dark Web (Agora) | ‘vein’, ‘needl’, ‘inject’, ‘shoot’, ‘arm’, ‘elbow’, ‘arteri’, ‘bruis’, ‘blood’, ‘use’ ‘week’, ‘zone’, ‘utc’, ‘end’, ‘time’, ‘gmt’, ‘sunday’, ‘monday’, ‘midnight’, ‘friday’ ‘mac’, ‘spoof’, ‘address’, ‘router’, ‘network’, ‘chang’, ‘tail’, ‘wireless’, ‘connect’, ‘macchang’ ‘second’, ‘later’, ‘less’, ‘ago’, ‘pleas’, ‘last’, ‘post’, ‘bmr’, ‘tri’, ‘the’ ‘bitcoin’, ‘paypal’, ‘creditcard’, ‘accept’, ‘anonym’, ‘shop’, ‘minut’, ‘729’, ‘519’, ‘1,099’ |
| Surface Web | Dark Web | Similarity Score |
|---|---|---|
| 0 | 1 | 70.00 |
| 0 | 3 | 70.00 |
| 1 | 5 | 80.00 |
| 1 | 11 | 80.00 |
| 5 | 14 | 60.00 |
| 7 | 18 | 66.67 |
| 8 | 13 | 60.00 |
| 10 | 4 | 55.33 |
| Surface Web | Dark Web | Similarity Score |
|---|---|---|
| 0 | 3 | 66.67 |
| 0 | 4 | 66.67 |
| 2 | 7 | 70.00 |
| 3 | 5 | 70.00 |
| 8 | 15 | 80.00 |
| 9 | 14 | 60.00 |
| 10 | 14 | 55.33 |
| 12 | 17 | 80.00 |
| 16 | 17 | 80.00 |
| Surface Web | Dark Web (Agora) | Similarity Score | Surface Web | Dark Web (Silk Road) | Similarity Score |
|---|---|---|---|---|---|
| user2666 | user4618 | 57.8 | user15376 | user10238 | 68.86 |
| user7287 | user9865 | 26.87 | user2364 | user4978 | 16.83 |
| user1847 | User20 | 63.58 | user748 | user8723 | 21.75 |
| user6405 | User265 | 19.26 | user5546 | user1474 | 10.22 |
| user1470 | user452 | 26.1 | user6600 | User1369 | 63.39 |
| Author | High-Frequency Words |
|---|---|
| User15376 | lsd, day, drug, take, week, good, send, messag, know, wait |
| User10238 | ship, lsd, messag, week, agora, good, btc, mdma, send, know |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shin, G.-Y.; Kim, D.-W.; Park, S.; Park, A.-r.; Kim, Y.; Han, M.-M. Identifying Similar Users Between Dark Web and Surface Web Using BERTopic and Authorship Attribution. Electronics 2025, 14, 148. https://doi.org/10.3390/electronics14010148
Shin G-Y, Kim D-W, Park S, Park A-r, Kim Y, Han M-M. Identifying Similar Users Between Dark Web and Surface Web Using BERTopic and Authorship Attribution. Electronics. 2025; 14(1):148. https://doi.org/10.3390/electronics14010148
Chicago/Turabian StyleShin, Gun-Yoon, Dong-Wook Kim, SungJin Park, A-ran Park, Younghwan Kim, and Myung-Mook Han. 2025. "Identifying Similar Users Between Dark Web and Surface Web Using BERTopic and Authorship Attribution" Electronics 14, no. 1: 148. https://doi.org/10.3390/electronics14010148
APA StyleShin, G.-Y., Kim, D.-W., Park, S., Park, A.-r., Kim, Y., & Han, M.-M. (2025). Identifying Similar Users Between Dark Web and Surface Web Using BERTopic and Authorship Attribution. Electronics, 14(1), 148. https://doi.org/10.3390/electronics14010148






