Abstract
Cooperative jamming (CJ) combined with single-input multiple-output (SIMO) technology can effectively improve the security and reliability of Internet of Things (IoT) systems. However, imperfect main channel state information (CSI) leads to incomplete CJ cancellation, which degrades the performance after combining. In this paper, by considering channel estimation errors and residual CJ at each receiving antenna, the residual CJ power after jamming suppression is analyzed, and the optimal combining coefficient for maximizing the signal-to-jamming-noise ratio (SJNR) is derived. The output SJNR of optimal diversity combining is given, and the achievable secrecy rate is analyzed on this basis. The theoretical and simulation results verify the combined effect of channel estimation errors and residual CJ on the combining performance. Moreover, it is worth noting that the combining performance is closely related to the spatial correlation of residual CJ.
1. Introduction
In recent years, Internet of Things (IoT) technology has developed rapidly, and various smart devices have gradually entered the public field of vision, widely used in home, medical, manufacturing, and other fields. In particular, the vision of the Internet of Everything (IoE) will be further advanced by the sixth-generation mobile (6G) network, which will be a fully connected world with integrated terrestrial wireless and satellite communications. However, with the number and types of nodes in wireless networks having shown explosive growth, the problem of network security has become increasingly prominent. Due to the broadcast nature of wireless communication, any node can receive the signal sent by the transmitter within the signal-receiving range in free space [1]. In IoT-oriented 6G systems, physical layer security technology can improve the security of information transmission in wireless communication to ensure efficient and reliable system operation.
Unlike the traditional encryption mechanism, physical layer security does not depend on the computing power of the device but makes full use of the inherent randomness and complexity of the wireless channel to achieve secure communication [2]. Cooperative jamming (CJ) is an effective physical layer security technique used to improve the secrecy rate [3]. Different from artificial noise, in CJ, the independent sender adds random signals to the channel, and the licensed and eavesdropping channels simultaneously interfered with the random signals. However, the licensed receiver can utilize the prior information of CJ to separate the desired signal.
1.1. Background Study of CJ Performance
CJ technology has been widely used in security systems [4,5,6,7,8]. Specifically, ref. [4] presents a robust security study for a two-unmanned aerial vehicle scenario with an intelligent reflecting surface, in which one drone is used to transmit CJ to interfere with eavesdroppers. The authors in [5] analyze the feasibility of using an intermittent jamming strategy to achieve physical layer security in IoT security systems, and a matching precision optimization algorithm is designed to achieve the optimal time-slot-free security transmission. A multi-leader single-follower Stackelberg game is proposed in [6] to maximize the benefits of jamming nodes. The authors in [7] investigate the use of CJ to improve transmission confidentiality and provide a secure transmission design to maximize the confidentiality of the secrecy outage probability (SOP) constraints secrecy rate. For scenarios where legitimate and non-legitimate channels are highly correlated, ref. [8] proposes a CJ-aided beamforming design scheme that maximizes the secrecy rate under SOP constraints.
The above papers are based on the assumption that the main channel’s channel state information (CSI) is perfect. In practice, it is difficult to cancel all the CJ due to non-ideal factors, even at the licensed receiver. Further, the residual CJ caused by incomplete jamming cancellation will worsen the licensed receiver’s signal-to-jamming-noise ratio (SJNR), thereby affecting the safety of the systems. For this problem, ref. [9] analyzes the influence of non-ideal factors on CJ suppression performance. Different from the theoretical analysis of the above literature, ref. [10] explicitly proposes a CJ cancellation architecture for point-to-point communication systems, and a test bench is designed to implement the proposed architecture. In the experimental results, the architecture can provide about 51dB CJ cancellation capability, which provides the experimental basis for CJ cancellation in the receiver. Unfortunately, it does not discuss reducing the system deterioration caused by residual CJ.
For the deterioration of security performance caused by these non-ideal factors, most studies optimize the SJNR from the power allocation between CJ and desired signals, e.g., ref. [11] optimizes the transmit power ratio between CJ and desired signals for signal distortion caused by transceiver in-phase and quadrature imbalance. In [12], the secrecy performance is jointly optimized from two perspectives of transmitter power allocation and receiver reconstruction CJ compensation with frequency mismatch. In addition, ref. [13] proposes the use of the frequency offset least mean squares (FO-LMSs) algorithm to improve the influence of carrier and sampling frequency offset on CJ cancellation.
The optimization studies of the above literature are all based on single-input, single-output (SISO) systems. For single-input multi-output (SIMO) systems, N independent branch signals can be obtained at the licensed receiver, and the signal output of each branch can be combined with appropriate combining technology, which can reduce the influence of residual CJ on the systems and achieve diversity gain. The traditional maximum ratio combining (MRC) [14] can achieve the best performance in terms of improvement under the condition that CSI is completely known and the CJ can be perfectly suppressed. However, when CSI is not perfect, the optimal coefficient of MRC cannot be accurately achieved, e.g., the influence of time migration on the MRC coefficient and the output signal-to-noise ratio (SNR) is analyzed in [15]. On the other hand, refs. [16,17] point out that the traditional MRC is not an optimal combining method when the received signal has interference other than Gaussian white noise. Specifically, ref. [16] studies the performance of MRC applied to SIMO systems with Poisson field of interferers. In [17], the SNR of the received signal with pulse noise is derived and compared under different combination schemes.
1.2. Contributions
Although literature [15,16,17] analyze the influence of non-ideal factors on diversity combining schemes, they are all based on communication scenarios, and their purpose is to maximize the communication rate, which is quite different from our research background and objectives; in these studies, the effects of residual CJ on the merging coefficient and security performance are not considered. In this paper, for the CJ-aided single-input multiple-output multiple-eavesdropper (SIMOME) systems, we analyze the influence of channel estimation error on CJ suppression and then derive the optimal combining coefficient and the security performance after combining them. To the best of the authors’ knowledge, we are the first to analyze the effects of incomplete CSI and the resulting residual CJ on diversity combining performance in CJ-aided SIMOME systems. Our key contributions are summarized as follows:
- The CJ-aided physical layer security model for SIMOME systems is presented.
- The effects of licensed receiver’s incomplete CSI and the resulting residual CJ on the signal-to-jamming-plus-noise ratio (SJNR) are analyzed, and the closed-form expression of the combined output SJNR is given.
- The optimal combining coefficient is derived for maximizing the combined output SJNR, and the achievable secrecy rate is analyzed to evaluate the security performance of the systems.
Bold uppercase and lowercase letters are used to represent matrices and vectors, respectively. The notation denotes the auto-covariance matrix of , and denotes the cross-correlation matrix between a and b. Function denotes mathematic expectation.
2. System Model
Consider the system model shown in Figure 1, which includes a desired signal transmitter (Alice), CJ transmitter (Jammer), licensed receiver (Bob), and eavesdropper (Eve). Alice and Jammer each have a single antenna, and Bob and Eve are equipped with N antennas. Assume that the channel matrices of Alice to Bob and Eve are and , and the channel matrices of Jammer to Bob and Eve are and , respectively.
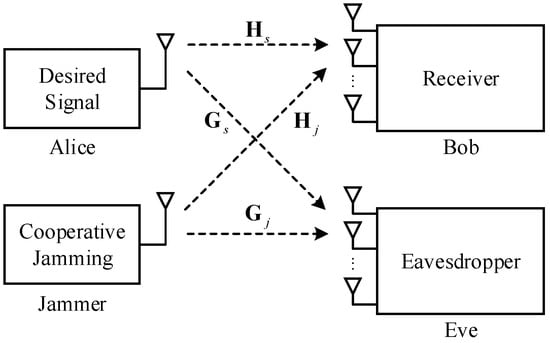
Figure 1.
Model of SIMOME system.
2.1. Signal Transmission
is defined as a complex Gaussian random vector and , where is the auto-covariance matrix of , which is given by
Similarly, is also a complex Gaussian random vector and , where is the auto-covariance matrix of , which is given by
Suppose that the transmitted signal of Alice and Jammer obeys the complex Gaussian distribution, and is uncorrelated with . and are the variances of desired signal and CJ, i.e., and . Bob’s received signal is a mixed signal consisting of desired signal, CJ, and additive Gaussian white noise (AWGN), which can be expressed in vector form as
where denotes AWGN. Assume that the noise power on each branch is , then .
At Bob, the jamming is separated from the mixed signal, and the residual signal is then combined according to a certain weight (see Figure 2). In this paper, CJ cancellation and combining are carried out in Bob. The original jamming is used for CJ reconstruction by using the estimated channel coefficient, and the reconstructed CJ is subtracted from the received signal. After jamming cancellation, the combined coefficient is estimated, and the combined signal is obtained according to the weight of each branch phase.
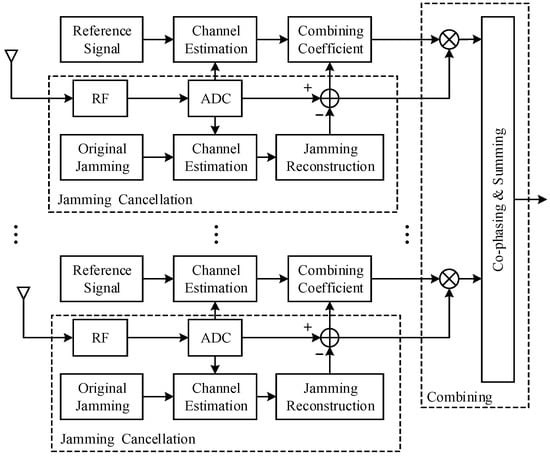
Figure 2.
Combining in CJ-aided SIMOME system (Bob).
2.2. Jamming Cancellation
Since the priori information of CJ is known to Bob, the CJ can be reconstructed and cancellated by utilizing the original jamming. However, even Bob cannot accurately reconstruct CJ due to imperfect CSI, which will result in incomplete jamming cancellation.
is the channel observation for , where the auto-covariance matrix . In this paper, the minimum mean square error (MMSE) algorithm is used to optimize ; thus, the estimated channel value is given by
is the zero-mean complex Gaussian vector with the auto-covariance matrix
The auto-covariance matrix of CJ’s channel estimation error is defined as , and then the channel estimation error is defined as , which is uncorrelated with , and
The reconstructed jamming can be expressed as
Thus, the residual signal after jamming cancellation is the combination of the desired signal, residual CJ, and AWGN, which is given by
2.3. Diversity Combining
Similarly with jamming cancellation, the estimated channel coefficient vector can be obtained by MMSE estimation for , and
where the auto-covariance matrix and denote the channel observation vector for . is also a zero-mean complex Gaussian vector with the auto-covariance matrix
The auto-covariance matrix of the desired signal’s channel estimation error is defined as , and then the channel estimation errors and are given by
To achieve diversity gain, we use the weight vector to combine the signals after jamming cancellation, where is the weight coefficient of the k-th signal branch. By multiplying each signal branch by the complex coefficient and then accumulating all branches, the combined variable can be expresses as
It can be seen from (14) that in addition to noise, the combined signal also contains residual jamming due to channel estimation error, which will worsen the combined SJNR. Selecting the appropriate weight can maximize the output SJNR and reduce the influence of residual jamming on the system safety performance. Thus, the problem of the determination of the weight vector is key and proves difficult for diversity combining.
3. Optimal Combining in SIMOME Systems
Traditional MRC is an optimal method under the assumption that CSI is perfectly known, and the signal does not contain any jamming other than white noise. In this method, the system can achieve the maximum diversity gain when [18].
However, since CSI is always unperfect, cannot be obtained accurately. Besides the desired signal and AWGN, residual CJ is also included in , and residual CJ between each branch is not necessarily independent. Thus, the result of the traditional MRC in [14] cannot be used directly in our system. In this scenario, both residual CJ and the channel estimation error of the desired signal need to be taken into account to achieve the maximum output SJNR. To solve this problem, this section deduces the optimal combining coefficient and combining performance based on residual CJ and the desired signal’s channel estimation error analyzed in Section 2.
3.1. Combining Coefficient
Equation (14) presents the output signal after diversity combining. For block-fading channels [19], the channel statistics change much more slowly than the channel state. Therefore, we do assume that perfect channel statistics can be obtained from the receiver. Moreover, both and are regarded as jamming due to and but are not observable. Equation (14) can be rewritten as
where and . The power of the combined signal is
and the power of is calculated as
Thus, the output SJNR of the combiner is defined as
Proposition 1.
The maximum SJNR can be obtained when
Proof of Proposition 1
. Please see Appendix A.
By substituting (19) to (18), the output SJNR can be expressed as
□
Remark 1.
Consider the ideal scenario, where and , i.e., and . In this case, the special form of output SJNR
can be obtained as
and the optimal combining coefficient can be expressed as
It can be seen that this result is consistent with that of MRC. Thus, the traditional MRC can be regarded as an ideal case for this paper.
Remark 2.
At one extreme, if the channel errors between branches are independent of each other, i.e.,
and are diagonal matrices,
takes on the largest value, which can be expressed as
Remark 3.
At the other extreme, if the channel errors between branches are complete correlated, i.e., , , where e = [1, 1, 1, …]T, takes on the smallest value, which can be expressed as
3.2. Achievable Secrecy Rate
In the system model in Figure 1, Eve is also equipped with multiple antennas. The mixed signal received by Eve can be expressed as
where and are channel coefficient matrices with Alice and Jammer to Eve, respectively. denotes Gaussian white noise and .
Since Eve cannot obtain prior information about CJ, it cannot separate the desired signal from the received mix signal. Assuming that the combining weight vector of Eve is , then the combined signal of Eve is
In order to more conservatively evaluate the security performance of the system, we assume that Eve can perform the ideal MRC and , and then the output SJNR can be expressed as
In this paper, the achievable secrecy rate [2] is used to evaluate the security performance of the SIMOME system. The achievable secrecy rate denotes the difference between the mutual information of Alice–Bob and Alice–Eve, which can be expressed as
where . It can be seen that when , , the system has secrecy capability.
Further, ref. [20] proposes that the thermal noise at Eve can be assumed to be 0 to determine the secrecy rate more conservatively. Under this assumption, can be rewritten as
4. Simulation Results
In this section, we simulate and verify the combining performance under the imperfect CSI analyzed in this paper and compare the proposed scheme with other traditional schemes that do not consider the imperfect CSI and the resulting residual CJ. In simulations, the power of CJ is equal to that of the desired signal, and . The normalized channel estimation error variances of the desired signal and the CJ at the i-th branch are and , respectively. Both and are random values of . The specific simulation parameters are shown in Table 1.

Table 1.
Simulation Conditions.
Firstly, Figure 3 shows the output SJNR under different normalized channel estimation errors, where the errors of each branch are uncorrelated. Let the normalized channel estimation error variance of the desired signal and CJ on each branch be equalized; this applies in the following simulations. When the channel estimation error is small, the output SJNR of the proposed optimal combining scheme and MRC schemes are both close to the ideal MRC. When the channel estimation error is large, the residual jamming is large; thus, the output SJNR of the three schemes deteriorates. Still, the performance of the optimal combining scheme is always better than that of MRC schemes, and the greater the channel estimation error, the more obvious the advantage of the optimal combining scheme over MRC schemes. Among them, the performance of the optimized MRC scheme is better than that of the traditional MRC scheme because the channel estimation error of the communication signal is considered. Moreover, compared with equal-gain combining, the optimal combining scheme can obtain a higher output SJNR, especially when the channel estimation error is small.
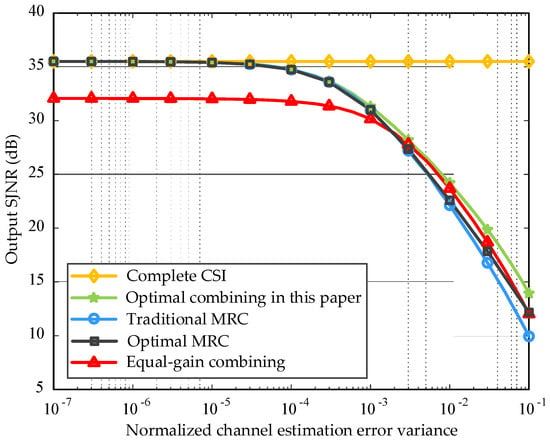
Figure 3.
Comparison of combining performance under different channel estimation errors, where traditional MRC is proposed in [21] and optimal MRC is proposed in [22].
Next, Figure 4 compares the effect of antenna number on the output SJNR when the channel errors of each branch are correlated and not correlated. When the channel estimation errors between branches are not correlated, the growth trend in the SJNR in optimal combining is similar to that of ideal MRC, which increases with the increase in antenna number. In this case, the residual jamming can be regarded as noise, and its influence on performance can be reduced by increasing the number of antennas. On the contrary, when the channel estimation errors among branches are completely correlated, increasing the antenna numbers cannot reduce the influence of residual jamming on the output SJNR. In particular, the larger the normalized channel estimation error, the more limited the optimization of the SJNR by combining. These phenomena are consistent with remark 2 and remark 3.
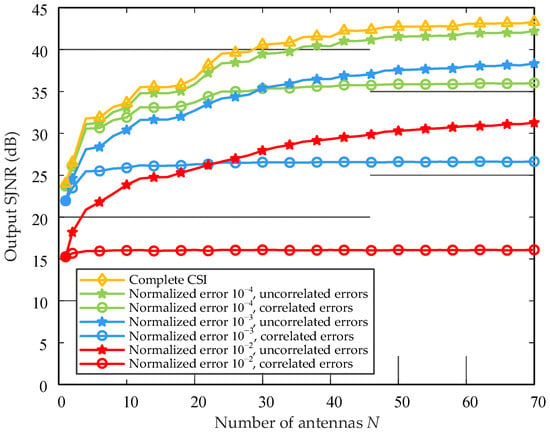
Figure 4.
Comparison of combining performance under different antenna numbers.
Suppose Bob and Eve are close to each other, and , [23]. Figure 5 further proves that the optimization effect of increasing the number of antennas decreases as the error correlation increases. Compared with the curve for the same number of antennas, the achievable secrecy rate decreases with the increase in the normalized channel estimation error, regardless of whether the channel estimation errors are correlated. It is worth noting that for the perfectly correlated channel estimation errors, when the normalized channel estimation errors are large, the achievable secrecy rate cannot be improved, even if the number of antennas is increased.
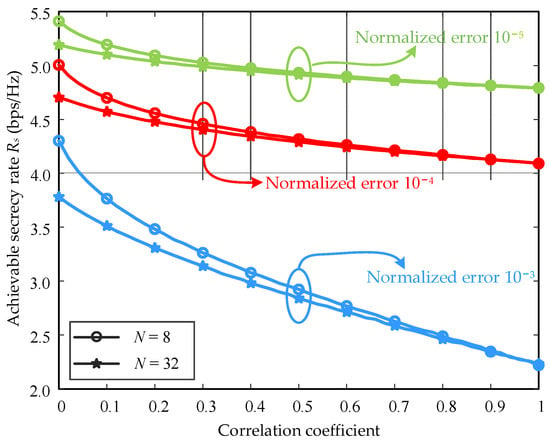
Figure 5.
Effect of channel estimation errors correlation on achievable secrecy rate.
5. Conclusions
This paper investigates the effect of imperfect CSI and the resulting residual CJ on diversity combining and security performance in IoT systems and analyzes the optimal combining scheme considering imperfect CSI. To improve the security of IoT systems, a CJ cancellation model combined with the diversity combining technique at licensed receivers is proposed. Considering the imperfect CSI, the optimal diversity combining coefficient is derived to maximize the output SJNR, and the achievable secrecy rate is given to evaluate the security performance. The theoretical and simulation results show that the proposed scheme is superior to other combining schemes, especially when the channel estimation error is large. In the follow-up study, we will not only focus on the channel estimation error but also consider the influence of non-ideal factors such as phase noise, delay, and frequency offset on jamming cancellation and combining performance.
Author Contributions
Conceptualization, H.Z.; Writing—original draft, Y.M.; Writing—review & editing, W.L. and W.W.; Supervision, S.S. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the National Natural Science Foundation of China under Grant 62071094 and Grant 61901396.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
To facilitate the calculation of , we define
and then (18) can be expanded as
Calculate the derivative of with respect to ; the outcome is shown as
Let the partial derivative be 0, i.e.,
where is a constant and .
References
- Anaya-Lopez, G.J.; Gomez, G.; Lopez-Martinez, F.J. A product channel attack to wireless physical layer security. IEEE Wirel. Commun. Lett. 2021, 3, 154–196. [Google Scholar] [CrossRef]
- Csiszar, I.; Korner, J. Broadcast channels with confidential message. IEEE Trans. Inf. Theory 1978, 24, 339–348. [Google Scholar] [CrossRef]
- Tang, L.; Chen, H.; Li, Q. Social tie based cooperative jamming for physical layer security. IEEE Commun. Lett. 2015, 19, 1790–1793. [Google Scholar] [CrossRef]
- Ye, R.; Peng, Y.; Al-Hazemi, F.; Boutaba, R. A Robust Cooperative Jamming Scheme for Secure UAV Communication via Intelligent Reflecting Surface. IEEE Trans. Commun. 2024, 72, 1005–1019. [Google Scholar] [CrossRef]
- Huo, Y.; Wu, Y.; Li, R.; Gao, Q.; Luo, X. A Learning-Aided Intermittent Cooperative Jamming Scheme for Nonslotted Wireless Transmission in an IoT System. IEEE Internet Things J. 2022, 9, 9354–9366. [Google Scholar] [CrossRef]
- Zhong, Y.; Zhou, F.; Wang, Y.; Deng, X.; Al-Dhahir, N. Cooperative jamming-aided secure wireless powered communication networks: A game theoretical formulation. IEEE Commun. Lett. 2020, 24, 1081–1085. [Google Scholar] [CrossRef]
- Hu, L.; Wen, H.; Wu, B.; Tang, J.; Pan, F.; Liao, R.-F. Cooperative-jamming-aided secrecy enhancement in wireless networks with passive eavesdroppers. IEEE Trans. Veh. Technol. 2018, 67, 2108–2117. [Google Scholar] [CrossRef]
- Xu, S.; Han, S.; Meng, W.; Yan, S.; He, L. Correlation-based cooperative jamming to enhance secrecy with receiver-side correlation. IEEE Trans. Veh. Technol. 2020, 69, 1903–1912. [Google Scholar] [CrossRef]
- Guo, W.; Li, C.; Zhao, H.; Wen, R.; Tang, Y. Comprehensive effects of imperfect synchronization and channel estimation on known interference cancellation. IEEE Trans. Veh. Technol 2020, 69, 457–470. [Google Scholar] [CrossRef]
- Guo, W.; Zhao, H.; Tang, Y. Testbed for Cooperative Jamming Cancellation in Physical Layer Security. IEEE Wirel. Commun. Lett. 2020, 9, 240–243. [Google Scholar] [CrossRef]
- Song, C.; Zhao, H.; Qin, L.; Wen, R.; Shao, S. Analysis and Optimization of Transceiver IQ Imbalances in Artificial Noise Shielded FH Communication. IEEE Trans. Signal Process 2022, 70, 2798–2813. [Google Scholar] [CrossRef]
- Mao, Y.; Zhao, H.; Li, W.; Shao, S. Joint Transceiver Optimization for CJ-Aided Security Communication Systems With Frequency Mismatch. IEEE Wireless Commun. Lett. 2024, 13, 1631–1635. [Google Scholar] [CrossRef]
- Pärlin, K.; Riihonen, T.; Turunen, M.; Nir, V.L.; Adrat, M. Known-Interference Cancellation in Cooperative Jamming: Experimental Evaluation and Benchmark Algorithm Performance. IEEE Wirel. Commun. Lett. 2023, 12, 1598–1602. [Google Scholar] [CrossRef]
- Eng, T.; Kong, N.; Milstein, L. Comparison of diversity combining techniques for rayleigh-fading channels. IEEE Trans. Commun. 1996, 44, 1117–1129. [Google Scholar] [CrossRef]
- Guo, W.; Song, C.; Zhao, H.; Shao, S.; Tang, Y. Outage probability of Performance analysis of MRC with imperfect time alignment in SIMO systems. IEEE Wirel. Commun. Lett. 2020, 9, 1319–1322. [Google Scholar] [CrossRef]
- Wang, Y.; Liu, F.; Wang, C.; Wang, P.; Ji, Y. Performance analysis of SIMO MRC receivers with correlated poisson field of interferers. IEEE Commun. Lett. 2021, 25, 74–78. [Google Scholar] [CrossRef]
- Mei, Z.; Johnston, M.; Le Goff, S.; Chen, L. Performance analysis of ldpc-coded diversity combining on rayleigh fading channels with impulsive noise. IEEE Trans. Commun. 2017, 65, 2345–2356. [Google Scholar] [CrossRef]
- Lo, T. Maximum ratio transmission. IEEE Trans. Commun. 1999, 47, 1458–1461. [Google Scholar] [CrossRef]
- He, B.; Zhou, X. Secure on-off transmission design with channel estimation errors. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1923–1936. [Google Scholar] [CrossRef]
- Yun, S.; Im, S.; Kim, I.-M.; Ha, J. On the secrecy rate and optimal power allocation for artificial noise assisted mimome channels. IEEE Trans. Veh. Technol 2018, 67, 3098–3113. [Google Scholar] [CrossRef]
- Tashman, D.H.; Hamouda, W. Physical-Layer Security on Maximal Ratio Combining for SIMO Cognitive Radio Networks Over Cascaded κ-μ Fading Channels. IEEE Trans. Cogn. Commun. Netw. 2021, 7, 1244–1252. [Google Scholar] [CrossRef]
- Thomas, V.A.; Kumar, S.; Kalyani, S.; El-Hajjar, M.; Giridhar, K.; Hanzo, L. Error Vector Magnitude Analysis of Fading SIMO Channels Relying on MRC Reception. IEEE Trans. Commun. 2016, 64, 1786–1797. [Google Scholar] [CrossRef]
- Guo, W.; Zhao, H.; Du, L.; Shao, S.; Tang, Y. Cooperative jamming power allocation with frequency offset in physical layer security. In Proceedings of the GLOBECOM 2020—2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).