Abstract
Social economy actors have assisted the recovery from crises by providing innovative solutions that are aimed at strengthening public services to complement government action. Currently, the widespread use of information and communication technologies (ICTs) by both citizens and organizations has changed society’s routine behavior, giving rise to the so-called information society. One of the major burdens of using big data for social problems is the lack of adequate data governance standards. Challenging and critical issues about big data include privacy and security for most of the social economy field of activities. Blockchain technology has attracted the attention of academic researchers and industries, which combines technologies like cryptography, end-to-end communication, and algorithms. Moreover, blockchain technology provides user anonymity to protect the privacy of users. We propose a hierarchical blockchain system for social economy services that can effectively protect the security and privacy of users and transmitted data. The proposed scheme was proven to ensure the legitimacy of all parties in the system and security of data and transactions, and blockchain technology and signcryption mechanisms were applied to achieve integrity, non-repudiation, and traceability. Security and performance analyses are also provided to prove that the proposed scheme achieved the above security concerns with efficiency.
1. Introduction
The social economy has been the focus of attention over the last decade as a sector in economic and social activity, and the influence of the social economy has increased since the COVID-19 crisis [1,2]. The main purpose of the social economy is to strengthen public services to complement government actions and help society recover from crises caused by natural disasters, population change, epidemics, reconstruction, etc. In other words, the social economy provides a chance to rework the post-crisis economy by promoting inclusive and sustainable economic models. The social economy has already been developed in many ways, such as with the labor force, food, supplies, and so on, and some sectors of the social economy have developed bank-like mechanisms to achieve transactions between service providers and receivers. Moreover, the social economy can also play an important role in achieving the sustainable development goals (SDGs) proposed by the United Nations.
Information and communication technologies (ICTs) have been developed rapidly and applied widely to transform the current society into an information society [3,4]. Emerging technologies, such as the Internet of Things (IoT), big data analysis and applications, artificial intelligence, and blockchain technology, are identified as being key technologies in the social economy in the next decades [5,6]. Digitalization using emerging technologies may accelerate improvements in accountability, transparency, and the impact of social economy organizations [6]. However, information in the social economy is non-financial information, which cannot be measured and evaluated easily, and this feature may become a burden for digitalization [6]. Other burdens of social economy digitalization include data privacy and security for data and transactions [6,7]. Transactions happen in the social economy system without a complete mechanism to record and store transaction data, and this situation makes verification and audit activities difficult.
Blockchain technology provides secure transactions using encryption and signature mechanisms that not only allow any user to upload transaction records, but blockchain to be verified through distributed nodes without a trusted third party. Several research institutes and industries have embraced blockchain technology to improve the security and efficiency of transactions, data transmission, and data storage. Moreover, blockchain technology with the IoT environment has been discussed and developed for years [8,9,10,11,12], and the related issues of security in blockchain technology have also been discussed [13]. Researchers have also utilized the features of blockchain technology to develop a system for digital forensics to achieve a chain of custody, which can ensure that evidence has been monitored while transferring without unauthorized access and modification [14,15].
Blockchain technology can transfer conventional paper-based processes which involve manual labor to digitalized and automatic processes while maintaining the features mentioned above. The transmitted information in blockchain networks, which is decentralized and trustless, can be certificated. However, the social economy has not adopted blockchain technology widely because of concerns about potential security problems.
We propose a hierarchical blockchain system for social economy services. The proposed scheme aims to apply blockchain technology to the social economy to strengthen the security and privacy of data and transactions in an efficient way. The proposed scheme also aims to achieve security properties, such as confidentiality, integrity, non-repudiation, and traceability with blockchain technology and the designed cryptographic mechanisms. The remaining organization of this paper is sketched below. The social economy, blockchain technology, signcryption, and short signature mechanism are introduced in Section 2. Section 3 introduces the proposed scheme, and the security analyses are detailed in Section 4. Finally, the conclusion is drawn in Section 5.
2. Related Works
2.1. Social Economy
The social economy is defined as the set of private, formal organizations with autonomy of decision and freedom of membership [16,17]. The social economy provides environments for members to meet market needs by providing goods or services, and members’ profits or surpluses are not directly linked to capital or fees contributed by each member [16,17]. The social economy is often defined by governments which have power in economic decisions, but governments seldom relate the social economy to environmental sustainability as a circular economy [18]. We take time banks and food banks as examples of the social economy.
Time banks, proposed by Cahn, are community-building and reciprocity-based work trading systems, and “time dollars” are tradable as a currency [19,20,21,22]. People can exchange goods and services with the concept of time dollars [1]. Cahn proposed five principles of the time bank system, which are “asset, redefining work, reciprocity, social networks, and respect [19,20,21,22]”. We, human beings, are assets which have the ability to contribute human force [18,19,20,21]. Works in the time bank contributed by assets are rewardable by creating a currency through helping each other [19,20,21,22]. Time banks utilize the original reciprocity in human society, i.e., “give and take”, to build relationships and trust with others and become a social network which can make lives meaningful [19,20,21,22]. Finally, members should respect other individuals [19,20,21,22].
Food banks were founded because of the rise in food insecurity, which means people were worrying, anxious, and uncertain about access to food or the quality and quantity of food [23,24]. Zero hunger is a global challenge to eliminate hunger and achieve food security by a charitable food system providing emergency food relief [25,26]. Food banks have played an important role in mitigating food insecurity across various countries through indirect services [25,26]. Food banks are responsible for sourcing, banking, and distributing surplus food [26]. Food banks collect or raise public donations of surplus or unsaleable food from growers, manufacturers, wholesalers, and retailers and provide food with lower or no charge [26,27].
In a typical system structure of a social economy, which is illustrated in Figure 1, the data preservation and transaction mechanisms in the social economy should be considered along with informatization including the security of transactions. Transactions through trusted third parties like conventional financial transactions may have risks, such as malicious insider attacks, data integrity, non-repudiation, etc. Since the necessity and importance of building mutual assistance within communities have increased, especially since COVID-19 breaking out, the issues mentioned above should be noticed [22]. Achieving goals of the social economy and SDGs have become difficult, and, fortunately, new models of creativity, knowledge, and sustainability based on emerging technologies have been developed quickly and widely, such as blockchain technology [18]. Blockchain technology provides opportunities to solve the problems above. Blockchain-based social economy systems have not been discussed widely. The proposed scheme is expected to be applied to social economies to enhance security properties with efficiency.

Figure 1.
System structure of social economy. A social economy system could be a hierarchical structure including a server with multiple organizations at different physical locations. Users can be service providers (givers) and receivers (takers).
2.2. Blockchain Technology
The original purpose of blockchain technology was recording the transactions of Bitcoin to avoid unusual transactions [13,28]. Blockchain technology has attracted the attention of academic researchers and industries, which combines the technologies of cryptography, end-to-end communication, and algorithms. Blockchain technology is also called distributed ledger technology using hash functions to link with previous blocks, and all nodes in the network verify each block while copies of the blockchain are stored in nodes [9,11,29]. The mechanism described above achieves features like decentralization, freedom from third parties, and collective maintenance. Data are transmitted, stored, and verified by distributed nodes in the network, and all nodes can reach a consensus. Blockchain technology can upload transaction records as a block anytime, anywhere, and each block is linked using encryption, signatures, and hash function mechanisms. Each block stores a copy of the blockchain as data which can be verified and remain unchanged. Moreover, blockchain technology provides user anonymity to protect the privacy of users [12]. Industries, such as financial institutions, governments, medical care institutions, academic institutions, logistics, etc., have started to develop blockchain systems because of their wide applications, for example, in medical records management, data transmission in the IoT, the signing process of official documents, certificate issuing, financial transactions, and so on. Previous research utilizing blockchains with security mechanisms for different applications has been proposed. Wang et al. proposed a blockchain system based on physical unclonable functions in a wireless body sensor network environment, which achieved mutual authentication between sensors, gateways, and medical professionals with a lightweight-designed mechanism [30]. Wang et al. utilized blockchain technology to design an authentication scheme for unmanned aerial vehicles [31].
Transactions happen in social economy systems without a complete mechanism to record and store transaction data, and this situation makes verification and audit activities difficult. Blockchain technology provides opportunities to solve the problems above. The proposed scheme applying blockchain technology is expected to enhance security properties in an efficient way.
2.3. Blockchain Technology in the Social Economy
Since blockchain technology provides transferring and record-keeping in a secure way with a decentralized structure, government management may be the first sector besides finance to consider applying blockchain technology, such as in public health, taxation, voting, etc. [32,33,34]. Property registration and the real estate market are other potential sectors in which blockchains are expected to increase efficiency in these kinds of economy exchange activities [32]. Balbo et al. proposed a wallet application on smart phones for a local economy based on blockchain technology as a co-production of a public service application, and Viano et al. discussed and analyzed blockchain-based co-production processes based on a case study by Balbo et al. [33,35]. As mentioned in Viano et al.’s work, blockchain technology provides a digitalized and automatic process and certificated information in decentralized and trustless networks, and the features above are reasons for government and social economies to apply blockchain technology [33,34]. Although attractive features of blockchain technology have been mentioned for a decade, recent research in blockchain technology in the social economy has focused on the local level because of potential risks in security which become a burden for digitalized social economy development [33,34]. In this research, we designed a hierarchical blockchain system which is flexible and suitable for social economy services.
2.4. Signcryption
Signcryption is a combination of encryption and signature mechanisms which is more effective in both computation and communicational costs than in operating encryption and signature mechanisms separately [36]. Signcryption can complete encryption and signature mechanisms at the same time and generates ciphertext and signatures, and then the receiver obtains a decryption key using a private key and the signature of the receiver, and recovers and verifies the integrity of the decrypted plaintext. By doing so, signcryption can achieve confidentiality, non-repudiation, and authenticity. The proposed scheme applies signcryption for message transmission and verification.
2.5. Short Signature
Boneh et al. [37] proposed a short signature based on Weil pairing which could generate a half-length signature compared to those generated by the elliptic curve digital signature algorithm. Moreover, the short signature has the ability to achieve batch verification, which can verify multiple signatures at one time. The proposed scheme applies short signatures by Boneh et al. [37] for message transmission and verification in social economy services that have a network of multiple nodes.
3. Proposed Scheme
We will introduce the system structure and the whole process in this section.
3.1. System Structure
Six roles are included in the proposed scheme, which are users, organizations, applications (APPs), servers, private blockchains, and public blockchains. Users are service providers (givers) and service receivers (takers) in a social economy system, and organizations are responsible for running and maintaining the social economy system in specific field. The organizations could be nonprofit organizations, non-government organizations, or a dedicated unit in a government. Users and organizations utilize APPs to operate the social economy system. Although functions in APPs will differ according to the roles of the operators and the various services in a social economy, the proposed scheme focuses on security properties of communication, authentication, and message transmission. The server is responsible for key generation and data storage and management. Social economy systems can have private blockchain systems which only allow legitimate members to join as a node, and private blockchains can be traced and checked if conflicts happen. The proposed scheme also provides a public blockchain system for block verification using public nodes. Figure 2 illustrates the system structure of the proposed scheme.
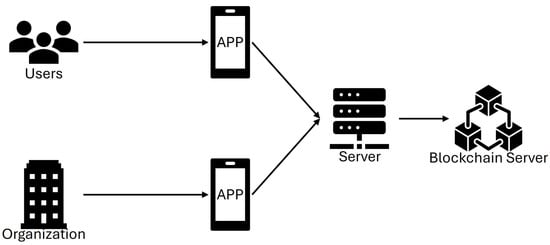
Figure 2.
The system structure of a proposed scheme. Users are service provider receivers. Organizations are responsible for running and maintaining the social economy system. Users and organizations utilize APPs to operate the social economy system. The server is responsible for key generation and data storage and management. The proposed systems have private and public blockchain systems.
The proposed scheme includes twelve phases. Parameters for the whole system are generated preliminarily. Users and organizations must register to servers to become legitimate parties through the registration phase. Users are given a public and private key through the key generation phase, and users and organizations authenticate each other in the mutual authentication phase. When users want to transmit messages to organizations, the client–organization signcryption phase is executed, and organizations need to execute the client–organization unsigncryption phase to recover the message. Similar situations happen between organizations and servers in the organization–server signcryption and organization–server unsigncryption phases. After that, the server generates private and public blocks and sends them to private and public blockchain systems. The private blockchain system only allows legitimate members to join as a node and can be verified by users if conflicts happen. The proposed scheme also provides a public blockchain system for block verification using public nodes. Figure 3 illustrates a high-level overview of the proposed scheme.
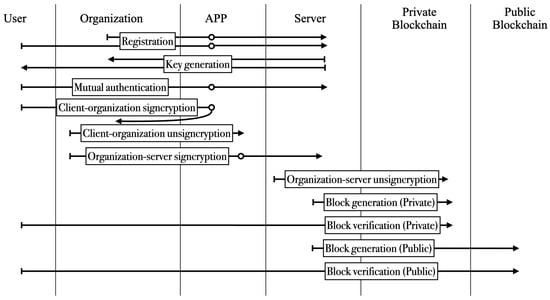
Figure 3.
High-level overview of the proposed scheme.
The proposed scheme includes user , organization , public key generator (PKG), APP used by user , server S, and the blockchain server. User can register to more than one organization, and each organization will generate an identity and the corresponding account information. Organization registers to the system to have functions, such as member management and received message verification. The PKG takes part in public and private key generation. User and organization register to the server to become legal roles, and then user and organization can log in to the system through the APP. The notations used in proposed scheme are listed in Table 1.

Table 1.
Notations used in the proposed scheme.
3.2. Preliminary
The system generates public and private parameters in the preliminary phase through the steps below.
Step 1. The system randomly chooses a big prime q and elliptic curve function E.
Step 2. The system generates addition groups (, ) and multiplicative group , and the bilinear maps e are as follows where () .
Step 3. Let g be the generator of .
Step 4. The system generates one-way hash functions () where , , , and .
Step 5. The system chooses a base point P which is bigger than n, a random number , and a random number and computes y as follows.
Step 6. The system outputs the public parameters and secretes parameters .
3.3. Registration Phase
User and organization input (, ) for registration through a secure channel. The steps in detail are described as below and illustrated in Figure 4.
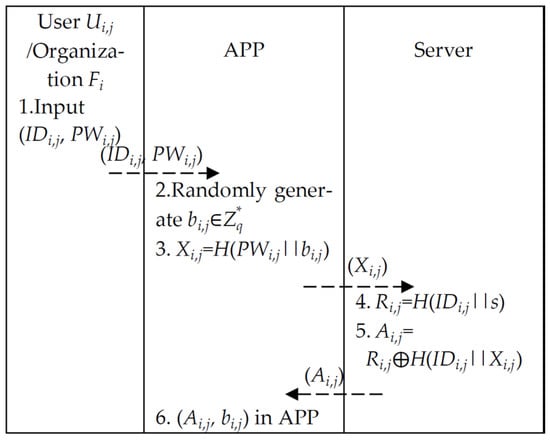
Figure 4.
Registration phase.
Step 1. User and organization input (, ) and send to the APP.
Step 2. User and organization generate randomly.
Step 3. User and organization calculate (, , ) and send (, ) to the system.
3.4. Key Generation Phase
User ’s public and private keys are generated in the key generation phase. The steps in detail are described as follows and are illustrated in Figure 5.

Figure 5.
Key generation phase.
Step 1. User and organization input .
Step 2. The PKG calculates the public key as and the private key and stores (, ) securely.
3.5. Mutual Authentication Phase
After user and organization input (, ) and are authenticated, the session key will be generated. The steps in detail are described as follows and are illustrated in Figure 6.
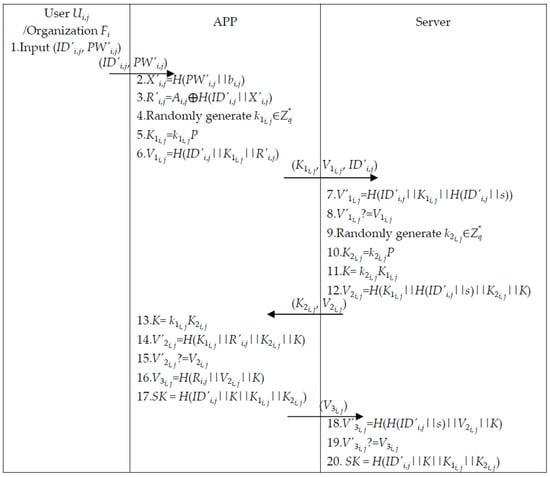
Figure 6.
Mutual authentication phase. The session key will be generated in this phase.
Step 1. User and organization input (, ) and send to the APP.
Step 2. The APP computes (, ) according to the equations below.
Step 3. The APP generates randomly, computes (, ), and sends (, , ) to server S.
Step 4. Server S computes and verifies with the received . If it holds, the identity of user and organization are verified, or the mutual authentication phase will be terminated.
Step 5. Server S generates randomly, computes (, K, ), and sends (, ) to the APP.
Step 6. The APP computes (K, ) and verifies with the received . If it holds, the identity of the system is verified or the mutual authentication phase will be terminated.
Step 7. The APP computes (, SK) and sends to the system.
Step 8. The server S computes and verifies with the received . If it holds, K is verified, and the system computes SK, or the mutual authentication phase will be terminated.
Note that interactions between user and the server from Step 3 to 7 are to ensure the legitimate identity of each other and negotiate a common session key using a key exchange technique, and Steps 7 to 8 are to confirm a session key .
3.6. Client–Organization Signcryption Phase
User signs and encrypts message M and generates and sends to organization through the client–organization signcryption phase. The steps in detail are described as follows and are illustrated in Figure 7.
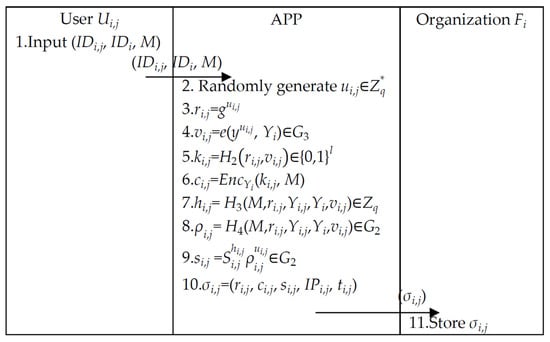
Figure 7.
Client–organization signcryption phase.
Step 1. User sends (, , M) to the APP.
Step 2. The APP generates and computes .
Step 3. The APP uses (, ) to compute (, ) as follows.
Step 4. The APP encrypts (, ) to ciphertext and computes (, ).
Step 5. The APP generates signature using (, ), outputs , and sends to organization .
3.7. Client–Organization Unsigncryption Phase
After receiving , organization decrypts through the client–organization unsigncryption phase. The steps in detail are described as follows and are illustrated in Figure 8.
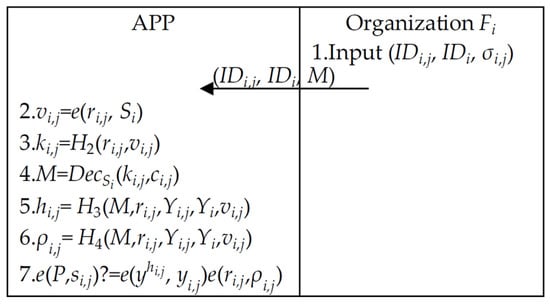
Figure 8.
Client–organization unsigncryption phase.
Step 1. Organization sends (, , ) to the APP.
Step 2. The APP computes (, ) and recovers the ciphertext as follows.
Step 3. The APP computes (, ) and verifies according to Equation (32). If it holds, the APP outputs M or False.
3.8. Organization–Server Signcryption Phase
After completing the previous phase, organization signs and encrypts M and sends ciphertext to the server. The steps in detail are described as follows and are illustrated in Figure 9.
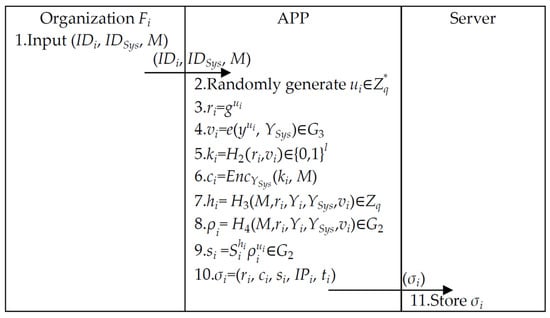
Figure 9.
Organization–server signcryption phase.
Step 1. Organization sends (, , M) to the APP.
Step 2. The APP generates and computes .
Step 3. The APP uses (, ) to compute (, ) as follows.
Step 4. The APP encrypts (, ) to ciphertext and computes (, ).
Step 5. The APP generates signature using (, ), outputs , and sends to the server.
3.9. Organization–Server Unsigncryption Phase
After receiving , the server decrypts through the organization–server unsigncryption phase. The steps in detail are described as follows and are illustrated in Figure 10.
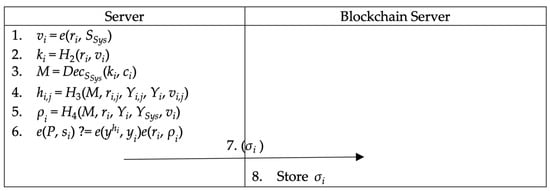
Figure 10.
Organization–server unsigncryption phase.
Step 1. The server calculates (, ) and recovers M.
Step 2. The server calculates (, ) and verifies using (, ). If the verification is successful, the server receives M, or the server outputs False.
Step 3. After successful verification, the server sends to blockchain server, and the blockchain server stores .
3.10. Block Generation of Private Blockchain
The blockchain server generates a private block PriB using and writes to a private blockchain. The steps in detail are described as follows and are illustrated in Figure 11.
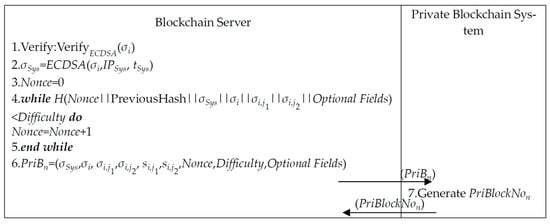
Figure 11.
Block generation of private blockchain.
Step 1. The blockchain server obtains from the private blockchain and verifies .
Step 2. The blockchain server generates signature using (, , ) and defines the initial value of Nonce as 0.
Step 3. The blockchain server S executes loop judgment while satisfying the difficulty level Difficulty. If the conditional judgment is satisfied, Nonce will be added as 1, and the loop judgment will be terminated.
Step 4. The private block is generated and sent to the private blockchain system. After that, the block number is generated and sent to the private blockchain system.
3.11. Block Verification of Private Blockchain
User obtains and verifies ( ). If PriB is verified successfully, user outputs True or False. The steps in detail are described as follows.
Step 1. User obtains from the private blockchain server.
Step 2. User verifies if satisfies Difficulty or not.
Step 3. User verifies ().
Step 4. User verifies signcryption message. If private block is correct, user outputs True or False.
3.12. Block Generation of Public Blockchain
During the block generation phase of the public chain, the blockchain server takes multiple private chain blocks and generates the public chain block which are then written into the public blockchain. The steps in detail are described as follows and are illustrated in Figure 12.
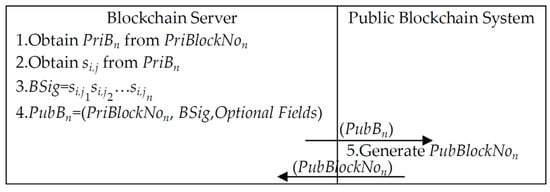
Figure 12.
Block generation of public blockchain.
Step 1. The blockchain server obtains the private chain block corresponding to .
Step 2. The blockchain server extracts from multiple private chain blocks .
Step 3. The blockchain server calculates , generates a public chain block , and transmits to the public blockchain.
Step 4. The blockchain server writes into the public blockchain and generates the corresponding block number .
Step 5. Return to blockchain server.
3.13. Block Verification of Public Blockchain
During the aggregation verification phase, user verifies the public chain block to confirm whether a corresponding private block exists, whether the private block signature is correct, and whether the aggregate signature is correct using public parameters. When multiple public chain blocks pass the verification, it outputs True, indicating that the aggregation verification is successful and valid; otherwise, it outputs False. The steps in detail are described below.
Step 1. User obtains (, ) from the blockchain server.
Step 2. User verifies whether exists in a private chain and obtains the private block .
Step 3. User verifies whether is consistent with the signature in the private block .
Step 4. User uses the hash function with () to generate .
Step 5. User verifies the aggregate signature. If the public chain block is correct, user outputs True, otherwise, False.
4. Security Analysis
This paper applies the random oracle model [38], BAN logic [39], and the automated validation of internet security protocols and applications (AVISPA) [40,41] for formal security proof. The process of the random oracle model proof can refer to other works using the random oracle model, including Li’s work [42] because of a similar process of proof. In addition, the process of BAN logic can refer to other works using BAN logic, including Parameswarath and Sikdar’s work [43] because of a similar process of proof that aims to prove that principles in schemes can believe established session keys. This paper will not describe the random oracle model [38] and the BAN logic [39] proof in detail. Informal security presents theoretical analyses that are present for the proof of fulfillment of the security requirements of the proposed scheme.
4.1. Formal Security Analysis Using AVISPA
The AVISPA tool was utilized for analyzing large-scale internet security-sensitive protocols and applications [40,41]. The AVISPA tool executes simulation protocols specified in the HLPSL language [41]. To validate cryptographic protocols, the AVISPA tool includes four back-ends: the observational finite model checker (OFMC), the constraint logic-based attack searcher (CLAtSe), the SAT-based model checker (SATMC), and the tree automaton-based security protocol analysis with automatic approximation (TA4SP). We utilized the AVISPA tool and security protocol animator (SPAN) to provide security proofs for the proposed scheme. The proposed protocol was verified using the OFMC and CLAtSe back-ends within the AVISPA tool. We have two organizations: user (client/member) U and server S. To validate the proposed scheme, we considered three secrecy goals and two authentication goals, as follows.
- secrecy_of g1: Bij is the private key of user (U).
- secrecy_of g2: PWij is the private key of user (U).
- secrecy_of g3: S’ is the private key of system (S).
- authentication_on k1ij: Server S performs identity authentication on user U based on the k1ij’ received from the message sent by user U.
- authentication_on k2ij: User U performs identity authentication on server S based on the k2ij’ received from the message sent by user U.
After executing the tool, as shown in Figure 13, the analysis results of the proposed protocol using OFMC and CL-AtSe back-ends confirm that specified confidentiality and identity authentication properties were satisfied for a finite number of sessions within the environmental organizations. Therefore, the proposed scheme can withstand both active and passive attacks. The results of the formal security analysis using AVISPA are shown in Figure 13.
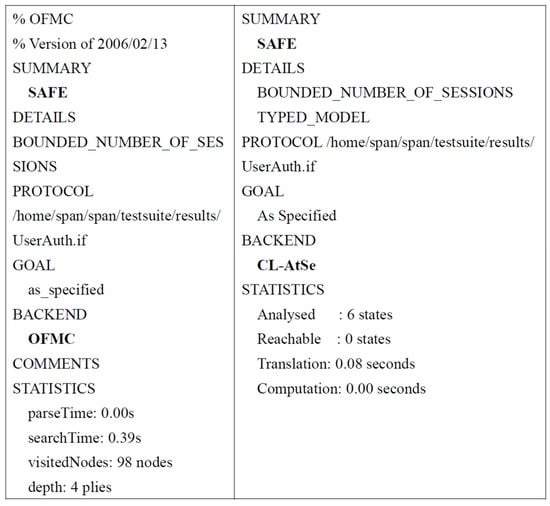
Figure 13.
Results of formal security analysis using AVISPA. The results show that the proposed scheme can withstand both active and passive attacks.
4.2. Mutual Authentication
During the login and authentication phases, both the user and system engage to mutually authenticate each other’s identity. The users send their information to the system, which then verifies the user’s identity and generates a session key K. The system then sends its information and session key K to the user. The user confirms the system’s identity and generates a session key SK based on the session key K, which is then sent back to the system. The system, based on the received session key K, verifies whether it was sent by itself. If so, it generates a corresponding session key SK. It is unlikely for an attacker to forge the user’s identity because any discrepancies in identity verification or session key validation would be detected. Intercepting the conversation is also improbable since it requires the possession of the session key SK.
4.3. Integrity
If an attacker attempts to tamper with transaction points, it would be impractical due to this research placing timestamp points on the blockchain. When an attacker tries to alter information on a block, they would need to change the tampered block and all preceding blocks to succeed. In terms of computational complexity, this is nearly impossible to achieve, and the cost would be prohibitively high. Therefore, blockchain ensures the integrity, authenticity, and security of data.
4.4. Non-Repudiation and Traceability
During the aggregation verification phase, user verifies the public chain block to confirm whether the corresponding private block exists, whether the private block signature is correct, and whether the aggregate signature is correct, using the public parameter PP. When multiple public chain blocks pass the verification, it outputs , indicating that the aggregation verification is successful and valid; otherwise, it outputs . Equation (53) proves the correctness of signature verification.
4.5. User Privacy
The user’s identity will not be transmitted in mutual authentication, client–organization signcryption, or client–organization unsigncryption phases. As a result, user privacy can be protected.
5. Performance Analysis
According to previous research [44], the time of performing a one-way hash function operation () is about 0.0052 milliseconds (ms), an ECC multiplication operation () is about 0.4276 ms, and an encryption operation () is about 0.0215 ms. The time taken for computing XOR operations is ignored because the value is too low to influence the result. The results of the computational complexity and performance time of the proposed scheme are presented and shown in Table 2. In mutual authentication phase (MA), the user will take 0.8864 ms, the organization will take 0.8864 ms, and the server will take 0.876 ms. In the client–organization signcryption phase (CO_S), the user will take 0.9223 ms. In the client–organization unsigncryption phase (CO_U), the organization will take 2.1751 ms. In the organization–server signcryption phase (OS_S), the organization will take 0.9223 ms. In the organization–server unsigncryption phase (OS_U), the server will take 2.1751 ms. The whole execution time is about 10 ms at most. As a result, the proposed scheme proved that it is efficient enough to complete the whole scheme, although there are no requirements or standards about the recommendation of time to perform a cryptographic module. We also compare the mutual authentication phase of the proposed scheme with previous works in Table 3. Although the performance of the proposed scheme is not better than some previous works, such as Shuai et al.’s work [45], the proposed system scenario supposes that the user and organization are using smart phones, which have much more computing and storing resources compared to devices in previous works [45,46,47,48,49,50].

Table 2.
Performance analysis of the proposed scheme. The results show the whole execution time is about 10 ms at most, which proves the proposed scheme is efficient enough to complete the whole scheme.

Table 3.
Performance comparisons of mutual authentication phases.
6. Discussions
The proposed scheme is a blockchain system in a hierarchical structure, which is an approach for social economy services. The security and performance analyses are also provided to prove that the proposed scheme achieved the security properties mentioned with efficiency, as it only needed 10 ms for execution. The proposed scheme not only incorporates the benefits of blockchain technology, such as digitalized and an automatic process, certificated information, decentralized networks, etc., but decreases risks of security by utilizing signcryption and short signature mechanisms to design the proposed scheme.
The limitations of the proposed scheme will be described below. Users have to use applications on mobile devices (APPs) to utilize the proposed system, which means skills and an environment of information technology will be necessary for users. Although the development of information technology has become widespread, we cannot ignore people who do not have such skills or environments. Moreover, APPs should be designed with user-friendly interfaces for which users can spend negligible efforts to learn [32]. For example, institutes or people in rural areas may not have a good wireless communication environment for transferring information, or people may be elderly, who have less motivation, willingness, or abilities to learn about and use APPs. One of the main purposes of the social economy is to help vulnerable groups, but the proposed system cannot maximize effectiveness if the proposed system is not easy to use.
The introduction of the proposed system to the social economy can be planned and evaluated, such as through empirical tests, in the future. Low- earth orbit (LEO) communication networks, like 5G or 6G, can be seen as extensions of wireless communication for rural areas. The development of 5G/6G with LEO communications may be necessary to improve the wireless communication environment. For users, an APP with a user-friendly design is necessary. If a social economy system is executed by an institution or government, the organization should have an adoption strategy including how to help people who are unable or refuse to use the APP, for example, sending caregivers or case managers of the original social economy system to help or act on behalf of them.
We are undergoing the implementation of a real-world social economy system including discussions with the social affairs bureaus of city governments, charity associations, religious groups, etc., which already have social-economy-related services. In the future, the evaluation of the implementation, such as a cost–benefit analysis, user acceptance test, user satisfaction survey, qualitative research with interview activities, etc., will be conducted.
7. Conclusions
The social economy has become more and more important in modern society, and the social economy provides a chance to enhance public services. Information and communication technology interventions provide the informatization of the social economy, which may improve the efficiency and range of applications. Data preservation and transaction mechanisms should be considered in informatized social economies because cybersecurity risks always exist. We designed and evaluated a hierarchical blockchain system for social economy services which applies blockchain technology. The proposed scheme not only incorporates the benefits of blockchain technology, such as a digitalized and automatic process, certificated information, decentralized networks, etc., but decreases risks of security by utilizing signcryption and short signature mechanisms to design the proposed scheme. The proposed scheme was proved to have the security properties to ensure the legitimacy of all parties in the system and security of data and transactions, and blockchain technology and signcryption mechanisms were applied to achieve confidentiality, integrity, non-repudiation, and traceability. The security and performance analysis are also provided to prove that the proposed scheme achieved the above security properties with efficiency. The proposed scheme can be introduced to non-profit organizations, such as social affairs bureaus of city governments, charity associations, religious groups, etc., which already have social-economy-related services, such as the food banks and time banks mentioned in previous sections. By doing so, the efficiency of the social economy can be improved with security mechanisms and a suitable adoption strategy, and the social economy can be expected to be active with digitalization and automation in the future.
Author Contributions
Conceptualization, Y.-C.C. and C.-L.H.; methodology, Y.-C.C. and C.-L.H.; validation, Y.-C.C. and T.-W.L.; formal analysis, Y.-C.C.; writing—original draft preparation, Y.-C.C. and T.-W.L.; writing—review and editing, C.-L.H. and K.-Y.T.; visualization, T.-W.L.; supervision, C.-L.H. and K.-Y.T. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Nation Science & Technology Council NSTC 113-2221-E-182-065-MY3 317 and 113-2634-F-004-001-MBK and 111-2410-H-182-007-MY2 and Chang Gung Memorial Hospital 318 Research Project (CMRP) CARPD3P0011.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Seyfang, G. Harnessing the Potential of the Social Economy? Time Banks and UK Public Policy. Int. J. Sociol. Soc. Policy 2006, 26, 430–443. [Google Scholar] [CrossRef]
- Kawęcki, N. Current and Future Roles in the Social Economy and the COVID-19 Crisis. Nowocz. Syst. Zarządzania 2022, 17, 49–64. [Google Scholar] [CrossRef]
- Ziemba, E. The Contribution of ICT Adoption to the Sustainable Information Society. J. Comput. Inf. Syst. 2019, 59, 116–126. [Google Scholar] [CrossRef]
- Cristobal-Fransi, E.; Daries, N.; Cardona, J.R.; Del Río-Rama, M.D.L.C. Challenges of Digitization in the Social Economy in Times of Pandemic: The Evolution of Online Presence and e-Commerce in Agri-Food Cooperatives. Agric. Food Econ. 2023, 11, 49. [Google Scholar] [CrossRef]
- Gagliardi, D.; Psarra, F.; Wintjes, R.; Trendafili, K.; Pineda Mendoza, J.; Haaland, K.; Turkeli, S.; Giotitsas, C.; Pazaitis, A.; Niglia, F. New Technologies and Digitisation—Opportunities and Challenges for the Social Economy and Social Economy Enterprises; Publications Office: Luxembourg, 2020. [Google Scholar]
- Berardi, L.; Valentinetti, D. Digitalization of Social Impact for Social Economy Organizations. Can. J. Nonprofit Soc. Econ. Res. 2023, 13, 114–120. [Google Scholar] [CrossRef]
- Lin, Y.; Xie, Z.; Chen, T.; Cheng, X.; Wen, H. Image Privacy Protection Scheme Based on High-Quality Reconstruction DCT Compression and Nonlinear Dynamics. Expert. Syst. Appl. 2024, 257, 124891. [Google Scholar] [CrossRef]
- Samaniego, M.; Jamsrandorj, U.; Deters, R. Blockchain as a Service for IoT. In Proceedings of the 2016 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Chengdu, China, 15–18 December 2016; pp. 433–436. [Google Scholar]
- Fernández-Caramés, T.M.; Fraga-Lamas, P. A Review on the Use of Blockchain for the Internet of Things. IEEE Access 2018, 6, 32979–33001. [Google Scholar] [CrossRef]
- Panarello, A.; Tapas, N.; Merlino, G.; Longo, F.; Puliafito, A. Blockchain and IoT Integration: A Systematic Survey. Sensors 2018, 18, 2575. [Google Scholar] [CrossRef]
- Dai, H.-N.; Zheng, Z.; Zhang, Y. Blockchain for Internet of Things: A Survey. IEEE Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef]
- Wang, C.; Cheng, X.; Li, J.; He, Y.; Xiao, K. A Survey: Applications of Blockchain in the Internet of Vehicles. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 77. [Google Scholar] [CrossRef]
- Feng, Q.; He, D.; Zeadally, S.; Khan, M.K.; Kumar, N. A Survey on Privacy Protection in Blockchain System. J. Netw. Comput. Appl. 2019, 126, 45–58. [Google Scholar] [CrossRef]
- Kumar, G.; Saha, R.; Lal, C.; Conti, M. Internet-of-Forensic (IoF): A Blockchain Based Digital Forensics Framework for IoT Applications. Future Gener. Comput. Syst. 2021, 120, 13–25. [Google Scholar] [CrossRef]
- Li, M.; Lal, C.; Conti, M.; Hu, D. LEChain: A Blockchain-Based Lawful Evidence Management Scheme for Digital Forensics. Future Gener. Comput. Syst. 2021, 115, 406–420. [Google Scholar] [CrossRef]
- Monzon, J.L.; Chaves, R. The European Social Economy: Concept and Dimensions of the Third Sector. Ann. Public Coop. Econ. 2008, 79, 549–577. [Google Scholar] [CrossRef]
- González-Morales, O.; Galván-Sánchez, I.; Román-Cervantes, C. Social Responsibility as a Source of Satisfaction for Worker-Members in a Social Economy Transport Company. Res. Transp. Bus. Manag. 2023, 51, 101070. [Google Scholar] [CrossRef]
- Vutsova, A.; Yalamov, T.; Arabadzhieva, M. Promoting Social Economy as an Instrument for Institutional Change: The Case of Bulgaria. Stud. Iurid. Lublinensia 2023, 32, 283–302. [Google Scholar] [CrossRef]
- Cahn, E.S.; Rowe, J. Time Dollars: The New Currency That Enables Americans to Turn Their Hidden Resource-Time-into Personal Security & Community Renewal; Rodale Press: Emmaus, PE, USA, 1992; ISBN 9780878579853. [Google Scholar]
- Cahn, E.S. No More Throw-Away People: The Co-Production Imperative; Essential: London, UK, 2000; ISBN 9781893520028. [Google Scholar]
- Válek, L.; Jašíková, V. Time Bank and Sustainability: The Permaculture Approach. Procedia Soc. Behav. Sci. 2013, 92, 986–991. [Google Scholar] [CrossRef]
- Lee, Y.-T.; Lin, J.-J.; Hsu, J.Y.-J.; Wu, J.-L. A Time Bank System Design on the Basis of Hyperledger Fabric Framework. In Proceedings of the 2020 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Toronto, ON, Canada, 2–6 May 2020; pp. 1–3. [Google Scholar]
- Nord, M.; Cafiero, C.; Viviani, S. Methods for Estimating Comparable Prevalence Rates of Food Insecurity Experienced by Adults in 147 Countries and Areas. J. Phys. Conf. Ser. 2016, 772, 012060. [Google Scholar] [CrossRef]
- Daly, Z.; Black, J.; McAuliffe, C.; Jenkins, E. Food-Related Worry and Food Bank Use during the COVID-19 Pandemic in Canada: Results from a Nationally Representative Multi-Round Study. BMC Public Health 2023, 23, 1723. [Google Scholar] [CrossRef]
- Esmaeilidouki, A.; Rambe, M.; Ardestani-Jaafari, A.; Li, E.; Marcolin, B. Food Bank Operations: Review of Operation Research Methods and Challenges during COVID-19. BMC Public Health 2023, 23, 1783. [Google Scholar] [CrossRef]
- Mossenson, S.; Giglia, R.; Pulker, C.E.; Chester, M.; Pollard, C.M. Dietary Risk of Donated Food at an Australian Food Bank: An Audit Protocol. BMC Nutr. 2023, 9, 67. [Google Scholar] [CrossRef] [PubMed]
- Mossenson, S.; Giglia, R.; Pulker, C.E.; Chester, M.; McStay, C.; Pollard, C.M. Evidence for Initiating Food Safety Policy: An Assessment of the Quality and Safety of Donated Food at an Australian Food Bank. Food Policy 2024, 123, 102589. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 12 July 2024).
- Abulkasim, H.; Mashatan, A.; Ghose, S. Quantum-Based Privacy-Preserving Sealed-Bid Auction on the Blockchain. Optik 2021, 242, 167039. [Google Scholar] [CrossRef]
- Wang, W.; Chen, Q.; Yin, Z.; Srivastava, G.; Gadekallu, T.R.; Alsolami, F.; Su, C. Blockchain and PUF-Based Lightweight Authentication Protocol for Wireless Medical Sensor Networks. IEEE Internet Things J. 2022, 9, 8883–8891. [Google Scholar] [CrossRef]
- Wang, W.; Han, Z.; Gadekallu, T.R.; Raza, S.; Tanveer, J.; Su, C. Lightweight Blockchain-Enhanced Mutual Authentication Protocol for UAVs. IEEE Internet Things J. 2024, 11, 9547–9557. [Google Scholar] [CrossRef]
- Bustamante, P.; Cai, M.; Gomez, M.; Harris, C.; Krishnamurthy, P.; Law, W.; Madison, M.J.; Murtazashvili, I.; Murtazashvili, J.B.; Mylovanov, T.; et al. Government by Code? Blockchain Applications to Public Sector Governance. Front. Blockchain 2022, 5, 869665. [Google Scholar] [CrossRef]
- Viano, C.; Avanzo, S.; Cerutti, M.; Cordero, A.; Schifanella, C.; Boella, G. Blockchain Tools for Socio-Economic Interactions in Local Communities. Policy Soc. 2022, 41, 373–385. [Google Scholar] [CrossRef]
- Viano, C.; Avanzo, S.; Boella, G.; Schifanella, C.; Giorgino, V. Civic Blockchain: Making Blockchains Accessible for Social Collaborative Economies. J. Responsible Technol. 2023, 15, 100066. [Google Scholar] [CrossRef]
- Balbo, S.; Boella, G.; Busacchi, P.; Cordero, A.; De Carne, L.; Di Caro, D.; Guffanti, A.; Mioli, M.; Sanino, A.; Schifanella, C. CommonsHood: A Blockchain-Based Wallet App for Local Communities. In Proceedings of the 2020 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPS), Oxford, UK, 3–6 August 2020; pp. 139–144. [Google Scholar]
- Zheng, Y. Digital Signcryption or How to Achieve Cost(Signature & Encryption) ≪ Cost(Signature) + Cost(Encryption). In Proceedings of the Advances in Cryptology—CRYPTO ’97, 17th Annual International Cryptology Conference, Santa Barbara, CA, USA, 17–21 August 1997; Kaliski, B.S., Ed.; Springer: Berlin/Heidelberg, Germany, 1997; pp. 165–179. [Google Scholar]
- Boneh, D.; Lynn, B.; Shacham, H. Short Signatures from the Weil Pairing. In Proceedings of the Advances in Cryptology—ASIACRYPT 2001, Gold Coast, Australia, 9–13 December 2001; Boyd, C., Ed.; Springer: Berlin/Heidelberg, Germany, 2001; pp. 514–532. [Google Scholar]
- Bellare, M.; Rogaway, P. Random Oracles Are Practical: A Paradigm for Designing Efficient Protocols. In Proceedings of the 1st ACM Conference on Computer and Communications Security, Fairfax, VA, USA, 3–5 November 1993; Association for Computing Machinery: New York, NY, USA, 1993; pp. 62–73. [Google Scholar]
- Burrows, M.; Abadi, M.; Needham, R. A Logic of Authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Armando, A.; Basin, D.; Boichut, Y.; Chevalier, Y.; Compagna, L.; Cuellar, J.; Drielsma, P.H.; Heám, P.C.; Kouchnarenko, O.; Mantovani, J.; et al. The AVISPA Tool for the Automated Validation of Internet Security Protocols and Applications. In Proceedings of the Computer Aided Verification, Scotland, UK, 6–10 July 2005; Kousha, E., Rajamani, S.K., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 281–285. [Google Scholar]
- von Oheimb, D. The High-Level Protocol Specification Language HLPSL Developed in the EU Project AVISPA. In Proceedings of the APPSEM 2005 Workshop, Frauenchiemsee, Germany, 12–15 September 2005. [Google Scholar]
- Li, X.; Zhu, R.; Du, D.; Jiang, C.; Zhou, Z. ECC-Based Certificateless Aggregate Signcryption Scheme in Cyber-Physical Power Systems. IEEE Syst. J. 2024, 18, 893–904. [Google Scholar] [CrossRef]
- Parameswarath, R.P.; Sikdar, B. A Secure PUF-Based Authentication Protocol for Remote Keyless Entry Systems in Cars. IEEE Trans. Veh. Technol. 2024, 73, 9825–9838. [Google Scholar] [CrossRef]
- Yuan, M.; Tan, H.; Zheng, W.; Vijayakumar, P.; Alqahtani, F.; Tolba, A. A Robust ECC-Based Authentication and Key Agreement Protocol for 6G-Based Smart Home Environments. IEEE Internet Things J. 2024, 11, 29615–29627. [Google Scholar] [CrossRef]
- Shuai, M.; Yu, N.; Wang, H.; Xiong, L. Anonymous Authentication Scheme for Smart Home Environment with Provable Security. Comput. Secur. 2019, 86, 132–146. [Google Scholar] [CrossRef]
- Zou, S.; Cao, Q.; Wang, C.; Huang, Z.; Xu, G. A Robust Two-Factor User Authentication Scheme-Based ECC for Smart Home in IoT. IEEE Syst. J. 2022, 16, 4938–4949. [Google Scholar] [CrossRef]
- Li, X.; Peng, J.; Obaidat, M.S.; Wu, F.; Khan, M.K.; Chen, C. A Secure Three-Factor User Authentication Protocol with Forward Secrecy for Wireless Medical Sensor Network Systems. IEEE Syst. J. 2020, 14, 39–50. [Google Scholar] [CrossRef]
- Wang, X.; Teng, Y.; Chi, Y.; Hu, H. A Robust and Anonymous Three-Factor Authentication Scheme Based ECC for Smart Home Environments. Symmetry 2022, 14, 2394. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Bhuiyan, M.Z.A.; Wu, F.; Karuppiah, M.; Kumari, S. A Robust ECC-Based Provable Secure Authentication Protocol with Privacy Preserving for Industrial Internet of Things. IEEE Trans. Ind. Inform. 2018, 14, 3599–3609. [Google Scholar] [CrossRef]
- Khaliq, A.A.; Anjum, A.; Ajmal, A.B.; Webber, J.L.; Mehbodniya, A.; Khan, S. A Secure and Privacy Preserved Parking Recommender System Using Elliptic Curve Cryptography and Local Differential Privacy. IEEE Access 2022, 10, 56410–56426. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).