Abstract
In the last decade, E-voting has received great attention due to its advantages in efficiency and accuracy. Fan et al. presented a novel E-voting system named HSE-Voting by utilizing homomorphic signcryption. The HSE-Voting system was claimed to gain a provable security goal under the standard proof. In this paper, we illustrate that their scheme may suffer from some potential security issues. On the one hand, the voting information could be recovered by the authentication center (AC). On the other hand, any malicious voter could disrupt the voting system undetected by locally modifying his ballot. In order to increase the resilience of the voting system to risks, an improvement of the HSE-Voting system is developed. Our improved system fixes the above security weaknesses but increases the computation cost on the AC side by a small amount. In addition, the proposed scheme satisfies voter anonymity, ballot privacy, and verifiability of election results.
1. Introduction
E-voting refers to voting that allows voters to cast their votes through the internet. Compared with traditional elections, E-voting not only saves a lot of ballot printing, transportation, and manual counting costs but also improves voting efficiency and convenience. For example, the 2020 US presidential election coincides with the national public health security problem. If the traditional voting method is adopted, it will inevitably cause a large number of people to gather, while electronic voting can solve this problem well. Many countries, including India and Brazil, have used electronic voting technology in many different electoral fields [1].
In 2020, Fan et al. [2] proposed a homomorphic signcryption scheme to construct an E-voting system named HSE-Voting in order to improve the efficiency of E-voting. Due to the integrated design of signcryption, its efficiency has been greatly optimized compared with Yang et al.’s system [3] on the agency side. Furthermore, it gives a comparative security analysis. However, there are some security issues in Fan et al.’s system, such as voter privacy being leaked, and the E-voting system may not properly being completed.
In this paper, we propose two cryptanalytic attacks on Fan et al.’s system [2]. In the first attack algorithm, we show that an honest-but-curious authentication center (AC) can recover the voter’s voting information from the corresponding ballot. In the second attack algorithm, we reveal that malicious voters can disrupt the election process by sending special incorrect ballots. Moreover, in order to enhance the security of the HSE-Voting system, we propose an improved HSE-Voting system by combining the signature and the proof of partial-knowledge protocol (PPK). While avoiding the above security risks, our system also reduces the computation cost on the agency-side compared to the existing work.
1.1. Related Work
Electronic voting [4,5,6] has been one of the key areas of focus for researchers. Over the past decade, many E-voting schemes have been proposed [7,8,9,10]. Most efficient E-voting protocols can be categorized by their approaches into the following types: blind signature [11,12,13], mix-nets [14], and homomorphic encryption [3,11,12,14,15,16,17]. In this subsection, we focus on the homomorphic encryption-based E-voting system.
Homomorphic encryption has been utilized in E-voting systems. The benefit of its homomorphic property is that ballots can be tallied without accessing the content of any ballot [18]. The ElGamal scheme [19] is one of the most widely used homomorphic encryption schemes in electronic voting. For instance, Refs. [3,11,12,14,15,16] exploit ElGamal to encrypt the ballots, thereby constructing an E-voting system with some existing cryptography tools, such as the proof of zero-knowledge [20] and the proof of partial knowledge [21].
In [14], Adida proposed a web-based E-voting system named Helios, which achieved open-audit voting using ElGamal encryption. Helios has strong security. Assuming that there are enough auditors, even if all the authorities collaborate to corrupt the system, there is a high probability of being exposed. Nevertheless, the security of Helios is closely related to the shuffling mechanism. It follows that if the Helios server is corrupted, then the submitted votes may be shuffled incorrectly, or the encrypted votes may be decrypted incorrectly. Furthermore, the performance results reported in [14] demonstrate that there is a large time overhead in the actual application. In an election with only two options in each vote and 500 voters, the Helios program takes more than 8 h.
In [12], the Helios system made several dramatic improvements to form the Helios 2.0 program, which was applied to support a real-world election. Specifically, Helios 2.0 updated the open audit mechanism. However, the key generation and decryption codes of Helios 2.0 are required to be completed by several trusted election committees. In fact, it is difficult to guarantee that the trustees are trusted in real environments. In addition, Helios 2.0 does not optimize its efficiency.
In [3], Yang et al. proposed a ranked choice E-voting system based on homomorphic encryption. Compared with the similar previous work, this system greatly improves the computation efficiency on the voter side. However, in this system, signature and encryption exist independently; the computation cost of the election agency increases rapidly as the number of voters grows. In addition, it also lacks the standardized proof of security.
Yuan et al. proposed an E-Voting scheme [7] based on Paillier homomorphic encryption and decentralization. The scheme utilizes signatures and double-encrypted technologies to secure the ballot information during transmission. In addition, the decentralization character avoids the risks associated with the corruption of a single institution and increases the openness and transparency of the system.
Qu et al. proposed an electronic voting protocol [8] based on the homomorphic signcryption. This protocol utilizes blockchain to make the election procedure public. Benefiting from the decentralized nature of blockchain, their protocol eliminates the requirement for trusted institutions.
In addition, Sheela et al. [9] and Saproo et al. [10] developed E-voting software based on homomorphic encryption, which further promotes the application of E-voting technology in practice.
E-voting represents a complex practical application scenario that necessitates the comprehensive consideration of multiple factors. Beyond safeguarding the privacy of voters’ ballot information as a fundamental requirement, it is imperative to ensure eligibility, accuracy, non-repeatability, reliability, verifiability and so on. Consequently, existing schemes enrich the functionality of the voting system to align with practical demands. On the other hand, there is a need to strike a balance between functionality and efficiency to ensure the practicality of the voting system.
1.2. Organization
Section 2 and Section 3 describe cryptographic tools and Fan et al.’s HSE-Voting system, respectively. Section 4 presents the cryptanalytic algorithm, and Section 5 proposes our improved HSE-Voting system. Section 6 provides the characteristic analysis of our system. The performance analysis is shown in Section 7. Section 8 concludes this paper.
2. Preliminaries
In this section, we introduce the notations and the basics of cryptography used in this paper. In the content described, the Diffie–Hellman problem is the intractability problem on which the security of the improvement scheme is based. We use the ElGamal scheme to protect ballot privacy and use its additive homomorphism to count ballot information. The proof of partial knowledge and proof of zero-knowledge (PZK) are adopted to provide the verifiability of election results. These concepts are important in enhancing the security of the HSE-Voting system.
2.1. Diffie–Hellman Problem
The Diffie–Hellman problem is a difficult problem of cryptography proposed by Whitfield Diffie and Martin Hellman in [22].
Definition 1
(Computational Diffie–Hellman Assumption, CDH). Considering is a cyclic group of order q, g is a generator of and two elements . Given and , it is computationally intractable to compute the value .
Definition 2
(Decisional Diffie–Hellman Assumption, DDH). Considering is a cyclic group of order q, g is a generator of , three elements . The DDH tuple and random tuple are computationally indistinguishable.
2.2. Elgamal Cryptography
ElGamal cryptography [19] is a well-known homomorphic encryption scheme. We select a safe-prime p of the form , where q is also a prime. In the remainder of this paper, we consider is a cyclic group of quadratic residues modulo p. The ElGamal scheme consists of the following three algorithms.
KeyGen: Let g be a generator of . Randomly choose , then compute . Output the key pair as follows.
Enc: Given a message , randomly choose element , and encrypt m as follows.
Dec: Given the ciphertext c, decrypt the ciphertext as follows.
where m can be revealed by computing a discrete algorithm.
Homomorphism: We show that the multiplication of and is a ciphertext corresponding to . Note that
2.3. Proof of Partial Knowledge
In an ElGamal cryptography system, there is a cyclic group of quadratic residues of order q with a generator g, the public key , and the secret key is x. Randomly select two plaintexts , compute . Then, we describe the process of proof of partial knowledge based on the ElGamal scheme [21], in which the prover P can prove to the verifier V that the provided ciphertext is one of and , but the verifier V cannot determine which plaintext corresponds to the ciphertext.
Firstly, the prover P generates the PPK parameters as Algorithm 1.
| Algorithm 1 Generating the PPK verification parameters |
|
Then, the prover P sends to the verifier V. After that, the verifier V verifies the correctness of the PPK parameters as Algorithm 2.
If Algorithm 2 outputs true, verifier V believes that the ciphertext is either or , but the exact value of the plaintext cannot be determined. If the is chosen to be encrypted, let step 6 in Algorithm 1 be , and set for Algorithm 2. More details can be seen in [21].
| Algorithm 2 Verifying the PPK parameters |
|
2.4. Proof of Zero-Knowledge
This subsection introduces the preliminary knowledge related to proof of zero-knowledge [20]. As in the previous subsection, this part is still based on the ElGamal cryptography system definition. The process of PZK [20] is described as follows in which the prover P can prove to the verifier V that the return value t and the prover’s public key have the same exponentiation, i.e., x. However, the verifier V cannot obtain any information about the prover’s secret key .
Firstly, the verifier V generates and discloses a random parameter . Then, the prover P generates the PZK parameters as Algorithm 3.
| Algorithm 3 Generating the verification parameters |
|
After that, the prover P sends PZK parameters to the verifier V. Then, the verifier V verifies the correctness of the PZK protocol with the parameters.
If Algorithm 4 outputs true, the verifier V trusts the statement of the prover P.
| Algorithm 4 Verifying the PZK parameters |
|
3. HSE-Voting System Overview
In this section, we briefly introduce the entities and election processes included in the HSE-Voting system [2].
3.1. Entities in the HSE-Voting System
Here, we list all entities involved in the HSE-Voting system.
- Voters: People who are authorized to vote.
- Authentication Center: AC takes responsibility for verifying the identification of voters, tallying and other related work in an election. Especially, AC is honest-but-curious.
- Bulletin Board (B Board): An insert-only bulletin board, which displays all information about the election.
- Auditors: Auditors are responsible for supervising the voting process and verifying the election result. Furthermore, the auditors are credible.
3.2. Initialization and Registration
In the initialization phase, AC applies the safe parameter to generate the parameters and a key pair , where , , then publishes and on the B Board.
In order to register with the HSE-Voting system, every voter has to provide valid identification. Once a voter’s identity has been verified, AC sends a random number to them through a secure channel. In the subsequent election process, the HSE-Voting system requires voters to identify themselves using an number. Obviously, AC can easily determine the voter identity corresponding to the allocated number.
3.3. Ballot Generation
The voter generates plaintext votes for each candidate, where , (1 means support the candidate, 0 means do not support the candidate). The voter computes the signcryption of plaintext vote , the corresponding PPK parameters and their public key as Algorithm 5, and sends , , as well as to AC.
| Algorithm 5 Computing Signcrypt and PPK |
|
3.4. Vote Tallying
AC performs the verifications as follows.
- Verifying the legitimacy of each .
- Verifying the eligibility of each ballot through .
AC tallies all eligibility ballots (i.e., ) as follows.
Then, AC decrypts the tallied ballot and computes the voters’ joint public key as follows.
After that, AC verifies whether the following equation holds.
If the above equation holds, AC publishes the election results , where is the total number of votes received by the j-candidate.
3.5. Vote Audit
The auditor firstly asks the AC for secret key and then verifies
- ,
- .
If both equations hold, the auditor believes that the election result is fair, impartial, and credible.
4. Cryptanalysis of the HSE-Voting System
In this section, we describe our attack algorithms about recovering electoral preference from the ballot and sabotaging the election with the wrong signcryption in detail.
4.1. Recovering Electoral Preference from the Ballot
Theorem 1.
In the HSE-Voting system, the AC can recover every voter’s electoral preference from his ballot.
Proof.
As shown in the Section 3.1, the AC generates , and the voters send their ballots to the AC. Through the components of the ballots, the AC can resume the electoral preference in two ways. The first method is as follows.
- The AC computes .
- With the voter’s ballot , the AC computes .
- If , the plaintext vote is 0; otherwise, the plaintext vote is 1.
In the second method, since all ballots are posted on the B Board, the adversary can obtain the signcryption and corresponding PPK of the voter . According to the generation method of , the parameters and are two random elements in . Therefore, the probability of the following equation is .
According to the verification equations in Algorithm 6, there is
As a consequence, the adversary can easily distinguish between and . Obviously, the vote satisfies the following equation.
Because of , we can retrieve the voting preference easily.
As voters register with the AC, the AC can confirm the real identity of the voter by . In summary, the AC can recover every voter’s electoral preference from his ballot. The reason for this security risk is that the AC has all the private keys . One potential solution is to encrypt the ballot using a collaborative public key approach, thereby circumventing the issue where the AC could decrypt a single ballot. □
| Algorithm 6 Verifying PPK |
|
4.2. Sabotaging the Election with the Wrong Signcryption
Theorem 2.
Malicious voters can disrupt the election process by sending the wrong signcryption.
Proof.
In the phase of ballot generation, the adversary can choose a random element and generate a partially incorrect signcryption for ballot .
After that, the adversary generates a corresponding to and sends the signcryption , the PPK parameters , the identity number , and to the AC. According to the validation rules in the phase of vote tallying, the adversary’s identity number is legitimate, and the verification of does not involve R. Therefore, the erroneous ballot can pass the verification.
Therefore, the tallied ballot is
The AC computes the voters’ joint public key and the election result as follows.
At this point, it is clear that the following inequality holds.
In this case, even if the election process is restarted, the adversary can still cause the election process to fail in the same way. This means that the adversary can achieve the purpose of disrupting the election process through the above steps. This occurred because the voting system was unable to precisely identify the questionable ballots, necessitating a re-initiation of the election. Furthermore, the verification procedure omits the involvement of the third component from the ciphertext. To address this limitation, it would be advisable to enhance the system’s verifiability. □
5. Improved HSE-Voting System
This section describes the details of our improved HSE-Voting system, which applies the same entities as in [2] but makes some minor changes to their specific functions. While retaining the advantages of the HSE-Voting system, we solve the security problem described in Section 4.
5.1. Entities of Our System
In our system, we modify the functions of entities AC and auditor as follows and leave the definitions of the other unchanged entities.
- Authentication Center: As a voting institution, the AC is still responsible for verifying the identification of voters, tallying, and other related work. However, voters no longer only use the AC’s public key to encrypt their ballots. Similarly, we assume that the AC is honest-but-curious.
- Auditor: As a voting institution, the auditor is added with a new function to generate a part of the election public key. In our system, the auditor is no longer credible.
5.2. Initialization of Election
At the beginning of an election, the AC generates the election public parameters and its public key . Then, the AC posts the and on the B Board. Then, the auditor creates its own key pair and uploads its public key on the B Board.
- The AC generates public .
- The AC uses to generate its key pair , where , .
- The auditor generates its own key pair, where , .
- The AC and auditor calculate the joint public key and make it public.
5.3. Registration of Voters
In the registration phase, each voter should generate an ElGamal key pair . Then, every voter provides the AC with his real valid identification (e.g., identification card) and public key . Once a voter’s identity has been verified, its corresponding voter public key will be added to the registration list, which will be posted on the B Board.
5.4. Generate Ballot
The voter generates the binary plaintext votes (where 0 or 1) for all candidates. Then, computes his own encrypted vote as Algorithm 7.
| Algorithm 7 Generating an encrypted vote |
|
After obtaining the encrypted vote , generates the PPK parameters corresponding to the using his secret key , the random parameters , the AC’s public key , and the auditor’s public key . The details are described in Algorithm 8.
| Algorithm 8 Generating a PPK of an encrypted vote |
|
The voter posts , , and on the B Board as their ballot.
5.5. Verifications of Each Submission
As shown in the previous subsection, the contents of all ballots are posted on the B Board, including the encrypted votes, the PPK parameters, and the public key of voters. However, in order to avoid tallying any illegal ballots to the final result, the verification of each submission is an essential and crucial part of the election process. It contains the following three verification steps.
- Verifying whether the sender is authorized: in order to prevent unauthorized people from illegally voting, each voter is required to send a ballot with their public key . The of each authorized voter is added to the registration list once they successfully register, and the AC posts a registration list on the B Board. Thus, anyone can verify whether a subsequent submission is sent by an authorized voter or not. For example, if belongs to the registration list, the sender is an authorized person. Otherwise, the submission will be discarded.
- Verifying whether the public key has not been accepted: in order to prevent unauthorized people from using authorized voters’ information posted on the B Board and prevent authorized voters from repeating voting, the AC is required to check whether it has accepted another submission that contains the same public key. If not, this submission is legal. Otherwise, the submission will be discarded.
- Verifying the eligibility of the encrypted ballot: our system stipulates that each vote of a valid submitted encrypted ballot must be either or . The proof of each voter’s submission is based on the well-known PPK protocol [21]. Specific details are described in Algorithm 9.
| Algorithm 9 Verifying the eligibility of encrypted ballot |
|
If , the ballot meets the eligibility criteria. Otherwise, the submission is discarded. The submissions that pass all the verification processes will be posted on the B Board. Then, the AC accepts these ballots as valid ballots.
5.6. Tallying All Valid Ballots and Decryption
After the voting process, the AC counts all valid ballots , which is described in Algorithm 10.
| Algorithm 10 Tallying all valid ballots |
|
Then, the AC announces the valid ballot-ciphertext and the secret key on the B Board. After that, every entity can verify the legitimacy of each ballot.
Afterward, the auditor generates the intermediate parameter and its corresponding PZK parameters as Algorithm 11.
| Algorithm 11 Generating intermediate parameter and PZK |
|
AC verifies the correctness of intermediate parameter through the PZK parameters as Algorithm 12.
| Algorithm 12 Verifying the of |
|
After that, AC decrypts the valid ballot-ciphertext using its secret key and intermediate parameter as Algorithm 13. Finally, the AC publishes the election results on the B Board.
| Algorithm 13 Decrypting the valid ballot-ciphertext |
|
5.7. Results Auditing
During the results auditing phase, the auditor (or any voter) verifies the correctness of the final result as follows.
- The AC computes and publishes and its corresponding PZK parameters.
- The auditor verifies the PZK parameters (the details are omitted here since the procedure is similar to Algorithm 12) and verifies the following equation.
If the verifications pass, the election result is believed to be credible. The auditor accepts the result and posts it on the B Board.
6. Characteristic Analysis
This section is devoted to giving a detailed security analysis of our improved HSE-Voting system, including the privacy of voters, the correctness of the final election result, and the voting verifiability.
6.1. Privacy of Voters
It is very necessary to protect the voters’ voting preferences. We argue for voter privacy from the following two points: (i) any probabilistic polynomial time adversary cannot distinguish whether a ballot is encrypted by 0 or 1 based on the information on the B Board; (ii) when using the PPK protocol, voters’ voting preferences of ballots will not be revealed during ballot verification.
Theorem 3.
If the ElGamal cryptosystem is semantically secure, any probabilistic polynomial time adversary cannot obtain the voters’ voting preferences from the B Board.
Proof.
Every cast ballot has been encrypted using the ElGamal cryptosystem (cf. Section 2.2) before submitting. ElGamal has homomorphic properties and semantic security. Thus, in our system, there is no probabilistic polynomial time adversary that can distinguish whether a ballot-ciphertext is or from the information published on the B Board. As mentioned above, the voting preferences of ballots remain secure. □
Theorem 4.
When using the PPK protocol and PZK protocol, the voting preferences and the information of the auditor’s secret key will not be revealed during verification.
Proof.
The PPK parameters are generated by using the PPK protocol, which consists of , , , , , , and , where and are random integers, , , , are computed by using random numbers , , , and , are computes by , , as well as . The parameter is the Diffie–Hellman signature between the AC and the voter . The PPK protocol is given in [21], which shows the details of proof that PPK will not reveal the original message. By using the PPK protocol, the verifier can verify all the elements without decryption. The verifier could only know whether an element is encrypted by 0 or 1, but cannot determine the exact value of plaintext.
The PZK parameters are computed by the PZK protocol, which consists of , , , and , where is a random number, , are computed by random number , and is computed by random numbers as well as . The PZK protocol is given in [20], which shows the PZK protocol has zero-knowledge and will not reveal any additional information.
Based on the security of the PPK and PZK protocols, the relevant parameters are not considered to readily reveal private information about voters’ electoral preferences. □
6.2. Correctness of the Election Result
In this subsection, we analyze the correctness of the election results from two aspects: the correctness of ballot delivery and the correctness of ballot integration and decryption.
Theorem 5.
Only authorized voters can vote, and no one can vote repeatedly.
Proof.
Suppose an unauthorized adversary attempts to use the i-th voter’s public key to participate in the election. For the PPK parameter in , due to Definition 1, the difficulty of the CDH problem shows the probability of the adversary successfully forging when they only know g, and is negligible. Therefore, the probability of the adversary successfully forging a valid PPK parameter that satisfies is negligible. In addition, our system ensures that each voter can vote only once by verifying whether their public key is included in other accepted ballots. □
Theorem 6.
The election process during ballot tallying and valid ballot-ciphertext decrypting is correct.
Proof.
In Section 2.2, we introduced the additive homomorphism of the ElGamal scheme. Therefore, the AC can count all the ballots on the B Board according to the correct steps.
Then, the AC uploads all accepted ballots to the B Board. At this time, everyone can check if their ballot is lost. In the end, the AC and auditors jointly decrypt valid ballot-ciphertext to obtain the election result.
Auditors compute
Then, the AC computes
Since , is small in practice. It is feasible to compute the discrete logarithm . Therefore, the election process of ballot tallying and valid ballot-ciphertext decryption is correct. □
Theorem 7.
The AC can check and in order to ensure the legality of the contents.
Proof.
According to the properties of PPK outlined in Section 2.3, the AC can utilize the voter’s public key to ascertain whether the plaintext corresponding to an encrypted ballot represents 0 or 1, thereby confirming the legitimacy and validity of this ballot. Similarly, in accordance with the PZK properties delineated in Section 2.4, the AC can confirm that the auditor has provided the correct decryption information , thus ensuring the accurate decryption of the election results. □
6.3. Voting Verifiability
In this section, we divide the verifiability requirements into two parts: universal verifiability and individual verifiability.
Universal verifiability: the B Board in our E-voting system is public, so everyone can check the accepted ballots and the election result on the B Board. In addition, since all accepted ballots are disclosed, voters can check the correctness of their ballots and prevent their ballots from being forged or tampered with.
Individual verifiability: the auditor (as well as each voter) can verify the final result of the election. The legality of verification is proved in Theorem 8.
Theorem 8.
The auditor (or each voter) can correctly verify the final election result.
Proof.
The auditor first verifies the to prove that the correctness of . Then, he checks the correctness of the final election result by verifying the equation. The correctness of the verification equation is as follows.
□
6.4. Comparison of Characteristics with Related Work
In order to provide a clearer indication of the contribution of the proposed scheme, we compared the characteristics of the proposed scheme with related work, and the results are shown in Table 1. In Yuan et al.’s scheme [7], the RSA signature scheme is employed to guarantee the integrity of ballots. However, there is no consideration of validating the legality of the ballot, i.e., the ciphertext is or . In Qu et al.’s scheme [8], the smart contract with the decryption key is able to decrypt the ciphertext of each ballot and verify its legality. Therefore, this scheme lacks the public verifiability. In Fan et al.’s HSE-Voting system [2], only the trusted auditor can verify the election results.

Table 1.
Characteristic comparison.
7. Performance Analysis
This section presents the performance analysis of our improved HSE-Voting system. We use to denote the computation time of one exponentiation. Meanwhile, we separately analyze the computation cost on the voter side and the AC side. Due to the small computation cost and little use of the auditor side, no detailed analysis is performed here. Furthermore, the comparison of our improved HSE-Voting system with the HSE-Voting system [2] and Yang et al.’s system [3] is given below.
7.1. Performance of the Voter Side
On the voter side, every voter should generate their ballot and submit it to AC. According to Section 5.4, the total computation cost for a voter can be present as the sum of the time of computing the encrypted vote and the corresponding s, which can be expressed as follows.
See Table 2 for a detailed comparison.

Table 2.
Performance comparison.
7.2. Performance of the AC Side
The performance of the AC side can be summarized in three parts: verifying the s of ballots, checking the s of intermediate parameters, and decrypting the valid ballot-ciphertext. The total computation time of the AC side is as follows; see Table 2 for a detailed comparison.
7.3. Experimental Simulation
In this subsection, all tests were performed on a laptop with the following specifications: 2.4 GHz quad-core Intel Core i7 with 16 GB of 1600 MHz DDR3L onboard memory. We used a high-performance implementation from libgmp via the gmpy2 Python module (https://gmpy2.readthedocs.io/en/latest/ (accessed on 4 January 2024)).
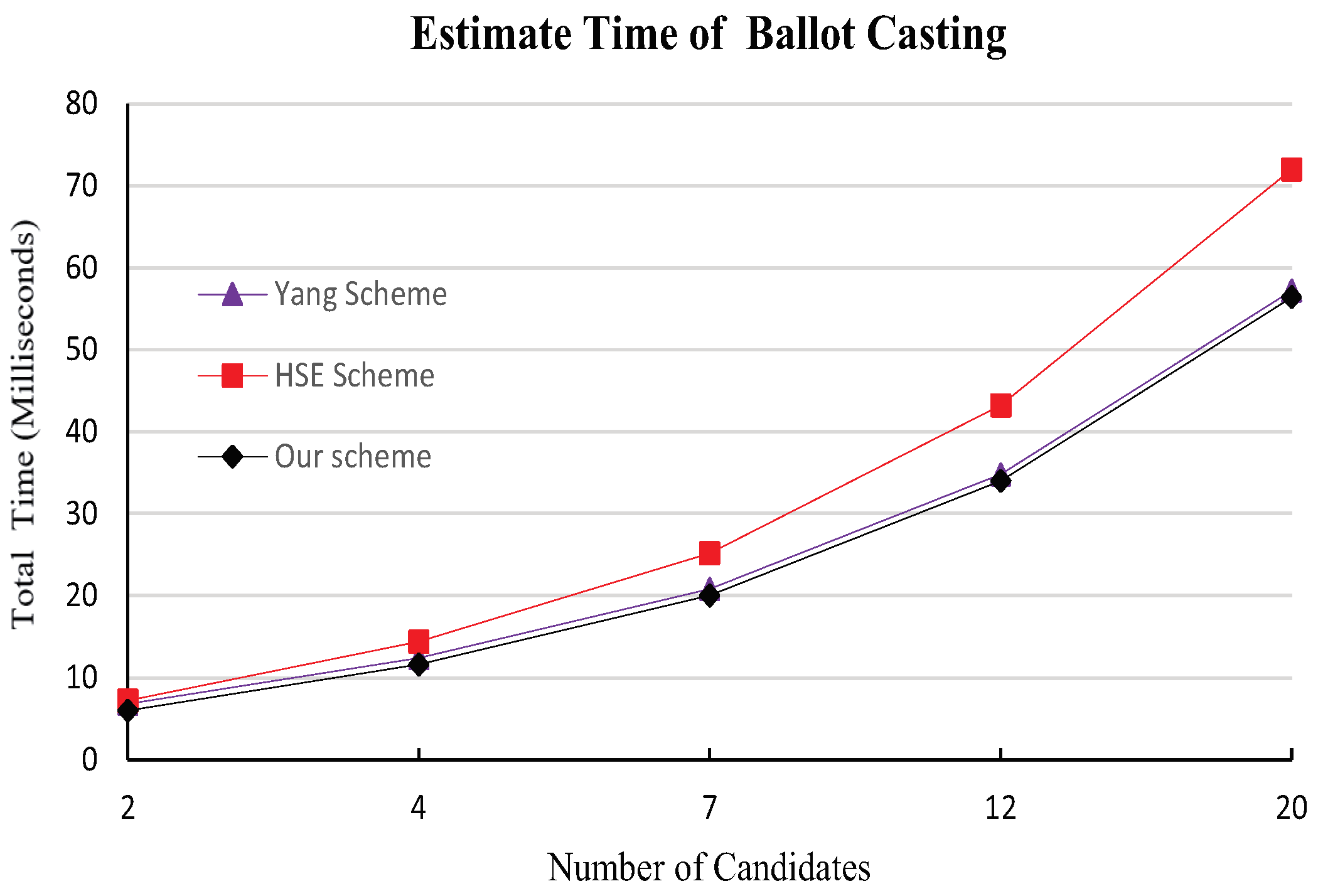
As depicted in Figure 1 and based on our experimental findings, it appears that our scheme may exhibit some efficiency benefits over the HSE-Voting system [2] in ballot casting, while the computational overhead seems to align closely with that of Yang et al.’s scheme [3].
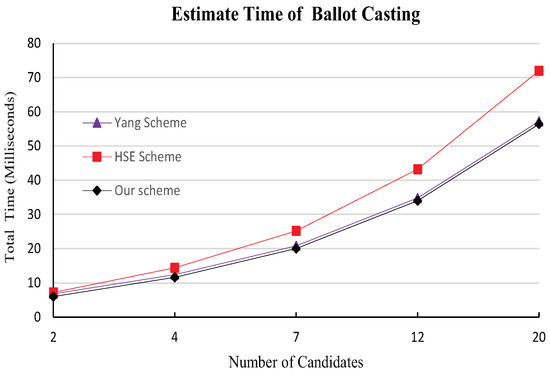
Figure 1.
Estimate total time comparison for a voter of the three systems.
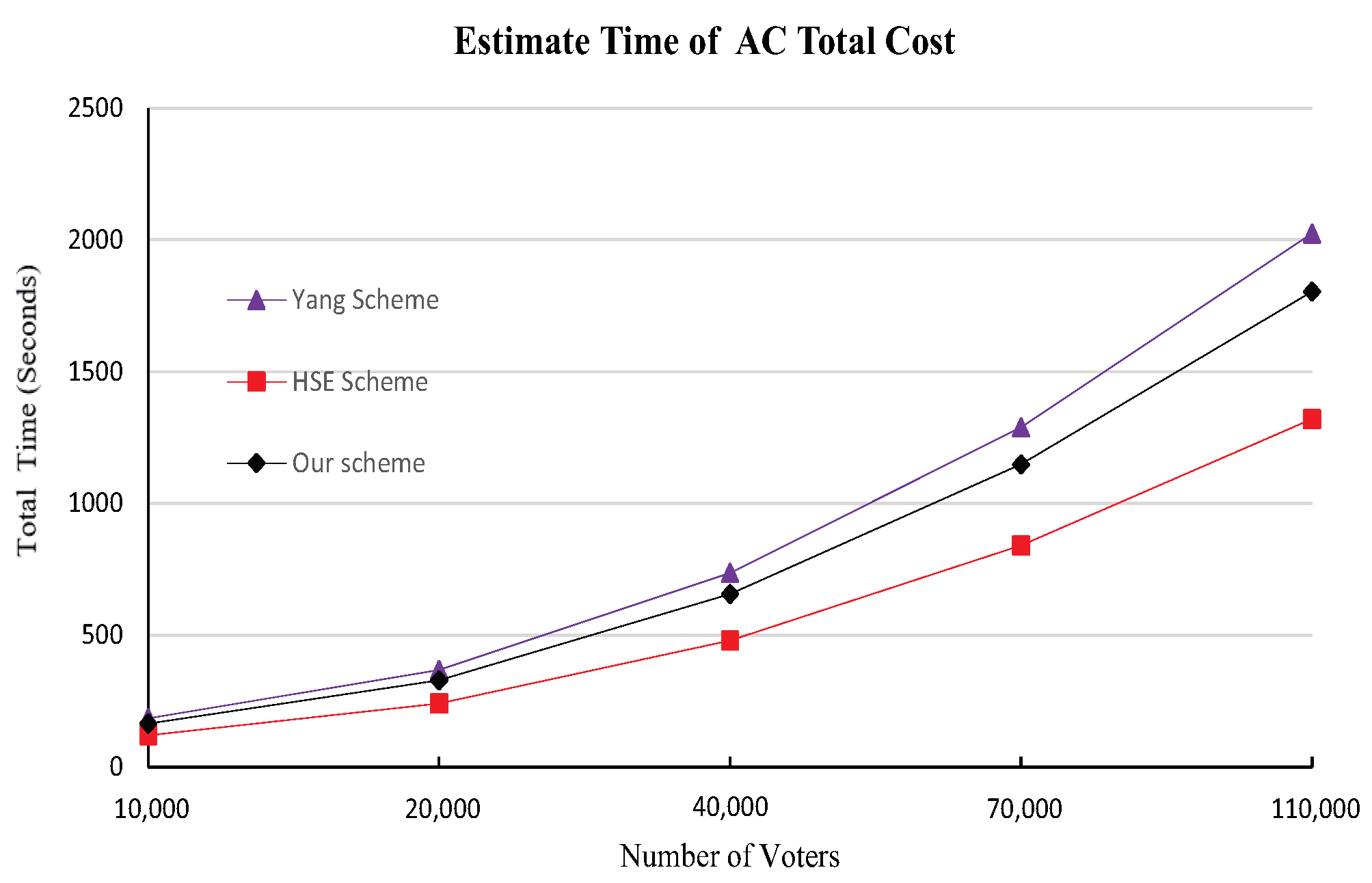
As shown in Figure 2, the computational overhead for the AC side in our enhanced scheme is slightly higher than that of the HSE-Voting system [2]. This increase can be attributed to the integration of additional computational components aimed at bolstering security. In addition, the computational overhead of our AC side is slightly smaller than Yang et al.’s scheme [3], which is one of the design goals of the HSE system.
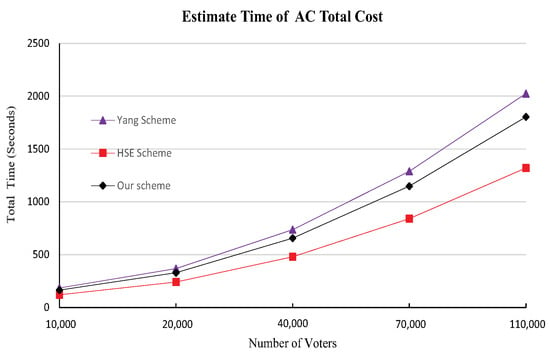
Figure 2.
Estimate total time comparison for AC of 5 candidates.
Combining the comparison results of characteristics and efficiency, the contribution of our scheme is to support the public verification of the ballot legality as well as the validity of election results, and the overall efficiency is slightly higher than Yang et al.’s scheme [3].
8. Conclusions
In this paper, we indicated two potential security threats to the HSE-Voting system and proposed a security-enhanced system based on Fan et al.’s scheme. Firstly, we pointed out that the content of each voter’s ballot could be obtained by the AC. Then, we discovered that malicious voters could create illegitimate ballots to disrupt the election process without being detected. Further, we proposed an improved scheme to avoid the above security risks. In addition, we showed a detailed analysis and demonstration of the characteristics of the improved HSE-Voting system. Comparison results of theoretical analyses and experimental tests suggest that our proposed scheme might offer some insights or benefits when compared to related schemes.
Author Contributions
Conceptualization, Y.Z. and N.Y.; methodology, Y.Z., Z.Z. and N.Y.; validation, C.Z. and W.Z.; writing—original draft preparation, Y.Z. and N.Y.; supervision, W.Z. and B.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Key R&D Program of China No. 2023YFB3106100,
the National Natural Science Foundation of China under Grant 62202363, 62272362, U19B2021,62102299,
and the Youth Innovation Team of Shaanxi Universities, Science and Technology on Communication
Security Laboratory Foundation (61421030202012103), the Henan Key Laboratory of Network
Cryptography Technology under No. LNCT2022-A05.
Data Availability Statement
The data can be shared up on request.
Conflicts of Interest
The authors declare no conflicts of interest.
Notations
| Notations used in the rest of this paper: | |
| The integer ring | |
| ← | Uniform and random select |
| Hash function | |
| ⊕ | XOR |
| The parameters of proof of partial knowledge | |
| The parameters of proof of zero-knowledge | |
| The number of voters | |
| i-th Voter, where | |
| The number of candidates | |
| j-th candidate, where | |
| The ballot belonging to for | |
| The ballot belonging to | |
| The Diffie–Hellman signature | |
| The public key | |
| The secret key | |
| The public key of | |
| The secret key of | |
| A ballot-ciphertext of | |
| A ballot-ciphertext of | |
| A valid ballot-ciphertext of | |
| Intermediate parameter for | |
| B | The final result of election |
References
- Scott, P. US Election 2016: Voter turnout fell to 58 per cent this year, estimates show. Telegraph 2016, 14. Available online: https://www.telegraph.co.uk/news/2016/11/14/us-election-2016-voter-turnout-fell-to-58-per-cent-this-year-est/ (accessed on 4 January 2024).
- Fan, X.; Wu, T.; Zheng, Q.; Chen, Y.; Alam, M.; Xiao, X. HSE-Voting: A secure high-efficiency electronic voting scheme based on homomorphic signcryption. Future Gener. Comput. Syst. 2020, 111, 754–762. [Google Scholar] [CrossRef]
- Yang, X.; Yi, X.; Nepal, S.; Kelarev, A.; Han, F. A secure verifiable ranked choice online voting system based on homomorphic encryption. IEEE Access 2018, 6, 20506–20519. [Google Scholar] [CrossRef]
- Saracevic, M.; Selimi, A. Convex polygon triangulation based on planted trivalent binary tree and ballot problem. Turk. J. Electr. Eng. Comput. Sci. 2019, 27, 346–361. [Google Scholar] [CrossRef]
- Fujioka, A.; Okamoto, T.; Ohta, K. A Practical Secret Voting Scheme for Large Scale Elections. In Advances in Cryptology—AUSCRYPT’92; Springer: Berlin/Heidelberg, Germany, 1992; Volume 718, pp. 244–251. [Google Scholar]
- Shahzad, B.; Crowcroft, J. Trustworthy Electronic Voting Using Adjusted Blockchain Technology. IEEE Access 2019, 7, 24477–24488. [Google Scholar] [CrossRef]
- Yuan, K.; Sang, P.; Zhang, S.; Chen, X.; Yang, W.; Jia, C. An electronic voting scheme based on homomorphic encryption and decentralization. PeerJ Comput. Sci. 2023, 9, e1649. [Google Scholar] [CrossRef] [PubMed]
- Qu, W.; Wu, L.; Wang, W.; Liu, Z.; Wang, H. A electronic voting protocol based on blockchain and homomorphic signcryption. Concurr. Comput. Pract. Exp. 2022, 34, e5817. [Google Scholar] [CrossRef]
- Sheela, A.S.; Franklin, R.G. E-Voting System Using Homomorphic Encryption Technique. J. Phys. Conf. Ser. 2021, 1770, 012011. [Google Scholar] [CrossRef]
- Saproo, S.; Warke, V.; Pote, S.; Dhumal, R. Online voting system using homomorphic encryption. In Proceedings of the ITM Web of Conferences, Navi Mumbai, India, 27–28 June 2020; EDP Sciences: Les Ulis, France, 2020; Volume 32, p. 03023. [Google Scholar]
- Kiayias, A.; Zacharias, T.; Zhang, B. An Efficient E2E Verifiable E-voting System without Setup Assumptions. IEEE Secur. Priv. 2017, 15, 14–23. [Google Scholar] [CrossRef]
- de Marneffe, O.; Pereira, O.; Quisquater, J. Electing a University President Using Open-Audit Voting: Analysis of Real-World Use of Helios. In Proceedings of the 2009 Electronic Voting Technology Workshop/Workshop on Trustworthy Elections, EVT/WOTE’09, Montreal, QC, Canada, 10–11 August 2009; Jefferson, D., Hall, J.L., Moran, T., Eds.; USENIX Association: Berkeley, CA, USA, 2009. [Google Scholar]
- Kumar, M.; Katti, C.P.; Saxena, P.C. A Secure Anonymous E-Voting System Using Identity-Based Blind Signature Scheme. In Proceedings of the Information Systems Security—13th International Conference, ICISS 2017, Mumbai, India, 16–20 December 2017; Lecture Notes in Computer Science. Springer: Cham, Switzerland, 2017; Volume 10717, pp. 29–49. [Google Scholar] [CrossRef]
- Adida, B. Helios: Web-based Open-Audit Voting. In Proceedings of the 17th USENIX Security Symposium, San Jose, CA, USA, 28 July–1 August 2008; van Oorschot, P.C., Ed.; USENIX Association: Berkeley, CA, USA, 2008; pp. 335–348. [Google Scholar]
- Mateu, V.; Miret, J.M.; Sebé, F. A hybrid approach to vector-based homomorphic tallying remote voting. Int. J. Inf. Sec. 2016, 15, 211–221. [Google Scholar] [CrossRef]
- Huszti, A. A homomorphic encryption-based secure electronic voting scheme. Publ. Math. Debr. 2011, 79, 479–496. [Google Scholar] [CrossRef]
- Hirt, M.; Sako, K. Efficient Receipt-Free Voting Based on Homomorphic Encryption. In Proceedings of the Advances in Cryptology—EUROCRYPT 2000, Bruges, Belgium, 14–18 May 2000; Springer: Berlin/Heidelberg, Germany, 2000; Volume 1807, pp. 539–556. [Google Scholar]
- Yi, X.; Paulet, R.; Bertino, E. Homomorphic Encryption and Applications; Springer Briefs in Computer Science; Springer: Cham, Switzerland, 2014. [Google Scholar] [CrossRef]
- ElGamal, T. A Public Key Cryptosystem and a Signature Scheme Based on Discrete Logarithms. In Advances in Cryptology, Proceedings of the CRYPTO’84, Santa Barbara, CA, USA, 19–22 August 1984; Lecture Notes in Computer Science; Blakley, G.R., Chaum, D., Eds.; Springer: Berlin/Heidelberg, Germany, 1984; Volume 196, pp. 10–18. [Google Scholar] [CrossRef]
- Chaum, D.; Pedersen, T.P. Wallet Databases with Observers. In Advances in Cryptology, Proceedings of the CRYPTO’92, 12th Annual International Cryptology Conference, Santa Barbara, CA, USA, 16–20 August 1992; Lecture Notes in Computer Science; Brickell, E.F., Ed.; Springer: Berlin/Heidelberg, Germany, 1992; Volume 740, pp. 89–105. [Google Scholar] [CrossRef]
- Cramer, R.; Damgård, I.; Schoenmakers, B. Proofs of Partial Knowledge and Simplified Design of Witness Hiding Protocols. In Advances in Cryptology, Proceedings of the CRYPTO’94, 14th Annual International Cryptology Conference, Santa Barbara, CA, USA, 21–25 August 1994; Lecture Notes in Computer Science; Desmedt, Y., Ed.; Springer: Berlin/Heidelberg, Germany, 1994; Volume 839, pp. 174–187. [Google Scholar] [CrossRef]
- Diffie, W.; Hellman, M.E. New directions in cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–654. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).