Abstract
Mobile sensors enjoy the advantages of easy installation and low consumption, which have been widely adopted in many information systems. In those systems where data are generated rapidly, the throughput of the sensors is one of the most fundamental factors that determine the system functionality. For example, to guarantee data integrity, digital signature techniques can be applied. In many practical scenarios, such as the smart grid system, data are generated rapidly and, hence, the signature together with the data must also be transmitted and verified in time. This requires the mobile sensors to support a high-throughput data processing ability. In this setting, how to achieve efficient signature schemes supporting batch verification must be considered. Many signatures, such as the original national cryptographic standard, namely, the SM2 algorithm, do not support batch verification and are in a public-key infrastructure setting. In this paper, we propose a SM2-based certificateless signature scheme with batch verification, which is suitable for the aforementioned environment. The scheme extends the Chinese cryptographic standard SM2 algorithm to the certificateless setting and multiple signatures can be verified simultaneously. Another advantage of this scheme is that its signing phase does not involve any pairing operation. The verification phase only requires a constant pairing operation, which is not related to the number of signatures to be verified. The construction is generic and can be instantiated using any traditional signature scheme.
1. Introduction
A smart grid is a new type of network based on multiple power devices, which integrates a power data transmission function and power transmission function. These terminal devices often have limited hardware resources while generating mass data. How to increase throughput while ensuring data validation with limited hardware resources is an urgent problem that smart grids face. The validation of power data ensures, on the one hand, the integrity of data. Integrity directly affects the statistical, regulatory, and distribution of the electricity resources. In addition, considering the uncertain work environment of these devices, it is inevitable that sensor equipment malfunctions lead to data anomalies. At this point, it is necessary to quickly locate the device sending the abnormal data. Therefore, tracing the source of the error data is also a function that needs to be implemented. Digital signature technology can protect data from tampering and repudiation, which is sufficient for the data requirements of smart grids.
The earliest digital signature schemes mostly relied on the public-key infrastructure (PKI) setting, which bound user identity and public key information through the issuance of certificates by a CA (a certificate authority). However, this certificate can bring complex certificate management issues to the system and have high requirements for communication bandwidth and storage resources for devices so that it is unsuitable for grid devices. To address this issue, cryptography researchers have proposed identity-based cryptosystems (IBCs) [1,2] that directly use some identifiable information as public keys, such as phone numbers and email addresses. However, the private key comes entirely from the private key generator (PKG) in IBCs. This centralized trust dependency brings serious key escrow problems. Once the PKG center is attacked, it brings security issues to all subordinate devices. The certificateless public-key cryptosystem (CLPKC) inherits the advantages of the previous systems. In the CLPKC, there is neither certificates nor the problem of key escrow. Therefore, the CLPKC is more suitable for smart grid equipment in resource constrained scenarios.
In detail, many smart grid sensors are embedded with sequential numbers in the equipment. The sequential numbers can be treated as identities of the users in the systems and can be used to verify signatures or trace the origin of the message. On the other hand, the identity-based setting is not enough for the smart grid environment since there are large numbers of nodes in the system and it is not easy to select a widely adopted and fully trusted third party as the PKG. Therefore, certificateless cryptography is a prominent candidate for such a system. As is known to all, the pairing operations are comparatively complex and take much more time for computation than other group structures like the elliptic curve setting. However, many certificateless cryptographic schemes share similar algebraic structures to the identity-based constructions and are built upon pairing-friendly groups. Pairing-free certificateless signature schemes have not been widely developed, especially the scheme derived from the national cryptographic standard. To sum up, signature schemes that satisfy the pairing-free, certificateless setting, based on the published standard have many applications in smart grid system. Unfortunately, few constructions have been studied in the literature.
In addition, due to the high real-time requirements of data in the power system, the signature algorithm used must be able to calculate quickly [3]. The terminal node may generate electricity data at any time, and the server will receive multiple data streams from multiple nodes at the same time. The server must be able to quickly process signature verification, which requires the signature algorithm to preferably support batch verification. In these systems, both efficiency [4] and privacy-preserving properties [5] need to be taken into consideration. Signatures that support batch verification can solve this problem. Namely, the signatures on the data collected from various sensors and other equipment can be aggregated in a certain node before being transmitted to the center and can later be verified together. The framework is shown in Figure 1.
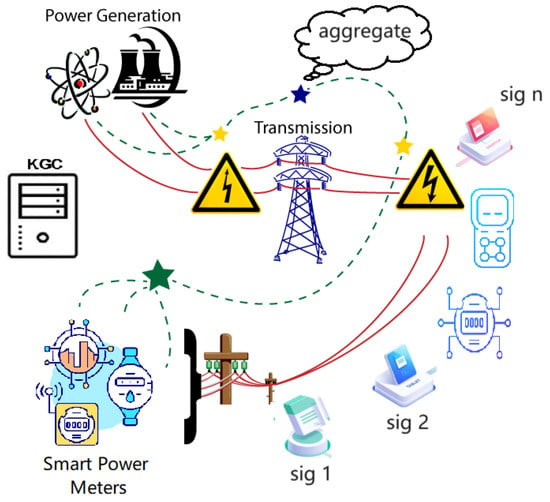
Figure 1.
Framework of certificateless signature with batch verification.
1.1. Related Work
The CLPKC was first proposed by Al-Riyami and Paterson [6] to deal with the key escrow problem in the identity-based encryption (IBE) system [2]. They provided the construction of three schemes including encryption, signature, and key agreement. In addition, two basic adversary models in the certificateless cryptosystem were identified, namely, Type I adversary and Type II adversary. Due to the excellent properties of no-certificate, many researchers were attracted and many follow-up work was proposed. Yum and Lee summarized a general secure construction method of the certificateless signature (CLS) scheme [7] and certificateless encryption (CLE) scheme [8]. However, later these constructions were proved to be unsafe by Hu et al. [9] and Libert et al. [10]. In 2005, Huang et al. [11] proved that there was a security risk in the original Al-Riyami and Paterson scheme [6]. Au et al. [12] re-examined the security model of CLPKC and proposed the concept of a new adversary model called the malicious key generation center (KGC). Huang et al. [13] further subdivided each type opponent into three levels based on their attack capabilities and provided a super secure certificateless signature scheme. Among the known models, security against the super-type adversary achieves the most secure level. Nevertheless, the signature length was slightly long and contained three group elements. In recent years, many new shorter certificateless signature schemes and certificateless aggregate signatures [14,15] were proposed. There are also some schemes that have been proven to be insecure. For example, Shim [16] analyzed five recent articles and found that they can all be forged by adversaries. Therefore, how to construct secure certificateless signatures still requires a very rigorous approach. For a comparative survey of certificateless signature, ref. [17] is a good reference for the related studies until 2022. Two other related but earlier surveys can be found in [18,19].
In addition to solving the key escrow problem, compared to IBCs, another major advantage of certificateless cryptosystem is that they can be implemented without pairing. Baek et al. [20] explored the first certificateless encryption scheme without pairing using the Schnorr signature. However, Sun et al. [21] showed that the scheme in [20] did not consider public key attacks. They fixed the problem using a new scheme with a more stringent security model. The certificateless signature scheme without pairing was finished by He et al. [22] in 2010. For the IoT scenario, Gong et al. [23] and Yang et al. [24] designed a certificateless aggregation signature without pairing and Dai et al. [25] proposed a certificateless aggregation signcryption without pairing. Moreover, many certificateless schemes based on other PKI signatures have been studied. Using the RSA signature, Zhang et al. [26] also constructed a CLS scheme. Another study point is constructing CLS schemes based on already-published cryptographic standards. In 2022, Tang et al. [27] proposed a CLS scheme (in Chinese) based on the Chinese national cryptographic standard. The scheme is built upon the identity-based standard, namely, the SM9 (SM stands for the Chinese pinyi “shangmi”, which means a commercial cryptography application) algorithm. As a result, it must rely on the pairing operation. Recently, He et al. [28] proposed a new CLS scheme using the SM2 algorithm without pairing. But their scheme requires zero-knowledge proof to verify the user public keys and how to support batch verification remains unknown. For batch verification, the certificateless aggregate signature (CLAS) [15,29] technique can be considered.
1.2. Motivation and Contributions
From the above analysis, we can see the enormous advantages of the certificateless cryptosystem and the feasibility of constructing a certificateless scheme based on the traditional signature scheme. However, current research is mostly limited to the implementation of the most basic signature schemes, while some signature algorithms with special functions have not yet emerged. For example, in systems with high throughput and low latency requirements, batch verification of signatures is also a crucial attribute that directly affects the availability of the entire system. Currently, there is no batch verifiable certificateless signature algorithm based on the national security algorithm. The primary contributions of this study include:
- We propose a certificateless signature algorithm with batch verification based on the Chinese national cryptographic standards, in particular with the SM2 algorithm;
- Our scheme supports batch verification of multiple signatures, thereby accelerating the algorithm in high throughput scenarios.
1.3. Technical Overview
From the above analysis, we can see that current studies on certificateless signature (CLS) schemes encounter the limitations of either relying on pairing operations like the scheme [27] built on the SM9 algorithm, or the underlying scheme not being selected as the cryptographic standard. The scheme proposed by He et al. [28] is extended from the SM2 algorithm and does not involve any pairing operation. However, it does not support batch verification. We first review the basic idea of He et al.’s construction. The core technical transformation from a traditional signature scheme to a certificate-based signature scheme is show in Figure 2.
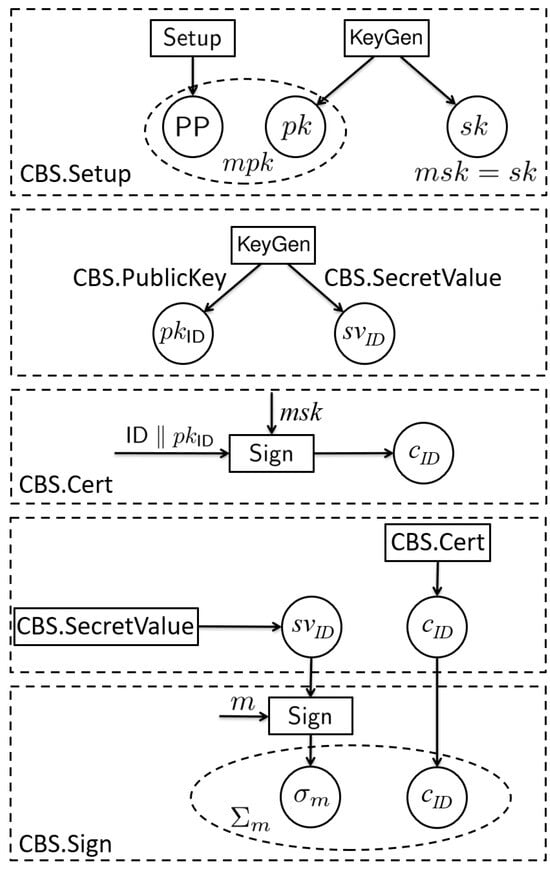
Figure 2.
Transformation from traditional signature to certificate-based signature.
A certificateless signature is similar to a certificate-based signature. The main difference is the secret value setting phase. In the CLS scheme, it is not necessary for the user to select a secret value and compute the public key first, before transmitting the public key to the key generation center (KGC) to obtain the partial private key. This means that the user can apply the partial private key from the KGC first; then, generate the secret value and compute the public key later. During the key extraction phase, the user’s public key may not yet be generated and, hence, cannot directly use the above transformation. To solve this issue, the user’s public key contain two parts: one part is from the key extraction phase, which is similar to the certificate-based setting; the other part is generated by the user itself. These two parts are independently generated but must be used together to sign a message. This paves the way for transforming a traditional signature scheme into a CLS scheme.
As for the zero-knowledge proof part, we use the property of bilinear pairing to replace the complex proof process. Even though this brings the pairing operation into the scheme, it only appears in the verification phase and the signing phase does not involve any pairing operation. For verification, since our scheme supports batch verification, multiple signatures can be verified simultaneously and the number of pairing operations is constant. This means that the additional time cost caused by the pairing operations is a fixed value and, hence, it will not incur too much computational cost during batch verification. The details of batch verification are depicted in Section 4.2.
1.4. Organization
The structure of this article is organized as follows. In Section 2, two preliminaries will be briefly introduced, including CLS and bilinear pairing, and a SM2-based CLS scheme will be reviewed. In Section 3, a new signature scheme with batch verification will be proposed, and in Section 4, the performance of these schemes will be evaluated through simulation experiments. Finally, a conclusion of the entire article is provided in Section 5.
2. Preliminaries
We will describe the definition of two preliminaries, including bilinear pairing and the certificateless signature. We will also review a SM2-based CLS scheme.
2.1. Bilinear Pairing
For three cyclic groups of a prime order q, a map is a bilinear pairing if and only if three properties hold:
- Computable: given any , calculating is efficient;
- Bilinear: for , the equation always holds;
- Nondegenerate: if g is a generator of and h is a generator of , will also be a generator of .
2.2. Certificateless Signature
The CLS scheme usually includes six algorithms:
- Setup : The Setup algorithm is usually operated by the KGC to initialize the scheme, which receives a security parameter . The system master public and secret key pair will be generated;
- KeyExt : The KeyExt algorithm is usually operated by the KGC, which receives the master key pair and a user identity . Finally, a partial private key is generated and transmitted to the user;
- SecretValue : The SecretValue algorithm is usually completed by a user, which receives the master public key and a user identity . Finally, a secret value is generated and returned to the user;
- PublicKey : The PublicKey algorithm is usually completed by a user, which receives the master public key , a user identity , and a secret value . A user public key will be output;
- Sign : The Sign algorithm is usually completed by a user signing it. They receive the master public key , a partial private key , a secret value , and a message m. A signature on the message m will be output;
- Verify : The Verify algorithm is usually completed by a user verifying it. They receive the master public key , a user identity , a public key , a message m, and a signature . If the output is “1”, it means the signature is legal; otherwise, the signature is illegal.
2.3. Review a CLS Scheme Based on SM2
The SM2-based CLS scheme designed by He et al. [28] is made up of six algorithms.
- Setup : The Setup algorithm receives the security parameter as input and uses the SM2 setup algorithm. It chooses an elliptic curve group with parameters and coordinates . Then, it randomly picks and computes . It also selects a hash function H, such as the SM3 algorithm. Finally, the algorithm returns the master public and secret key pair as
- KeyExt : The KeyExt algorithm receives the master key pair and an identity as inputs. Firstly, it randomly selects and computes . Then, it concatenates the identity and the partial public key . Finally, it runs the SM2 signature algorithm to produce the partial private key.
- Compute ;
- Pick randomly and calculate ;
- Compute .
The partial private key is ; - ScretValue : The ScretValue algorithm receives the master public key and an identity . Then, it runs the SM2 key generation algorithm. It randomly selects a and sets with the random value x received from the KGC. Next, it outputs the secret value ;
- PublicKey : The PublicKey algorithm receives the master public key , an identity , and a secret value . Then, it computes and generates a noninteractive zero-knowledge proof (NIZKP) of holding the unique y with respect to . Next, it sets and outputs as the public key;
- Sign : The Sign algorithm receives the master public key , a partial private key , a secret value , and a message m. It first concatenates the identity and message m. Then, it computes and runs the SM2 signing algorithm with to generate the part signature. In detail,
- Compute ;
- Pick randomly and compute ;
- Compute .
Next, it outputs the signature ; - Verify : The Verify algorithm receives the master public key , an identity , a public key , a message m, and a signature . Then, it runs the SM2 algorithm to verify and and checks whether is valid. In detail,
- Compute ;
- Compute ;
- Compute ;
- Compute .
If the proof is valid and the equations hold, it outputs “1”. Otherwise, it outputs “0”.
3. A Certificateless Signature Scheme Supporting Batch Verification
3.1. Zero-Knowledge Proof with Pairing
In the above scheme, we need to provide a NIZKP of y in the user public key to avoid adversaries bypassing by setting . However, zero-knowledge proof requires additional overhead and increases the length of the user public key. We provide an extension scheme that uses bilinear pairing tools to verify the binding relationship between and . A user who verifies the signature can ensure that the signer knows the y corresponding to Y by calculating . The extension scheme is depicted in the following.
3.2. Construction
Next, we describe our new certificateless signature scheme with batch verification based on SM2. Our scheme also consists of six algorithms.
- Setup : The Setup algorithm receives a security parameter . It generates an elliptic curve group with parameters and coordinates . Then, it picks randomly and sets . Next, it chooses a hash function H, such as the SM3 algorithm. Finally, it outputs the master key pair as
- KeyExt : The KeyExt algorithm receives the master key pair and an identity as inputs. It first picks randomly and calculates . Then, it concatenates with . Next, it runs the SM2 algorithm to generate a partial private key.
- Compute ;
- Pick randomly and compute ;
- Compute .
It transmits the partial private key to the user safely; - ScretValue : The ScretValue algorithm receives the master public key and an identity as inputs. Then, it runs the SM2 key generation algorithm. It selects randomly and sets with the random value x received from KGC. Next, it outputs the secret value ;
- PublicKey : The PublicKey algorithm receives the master public key , a user identity , and a secret value of the user as inputs. Then, it computes and . Next, it sets and produces the public key ;
- Sign : The Sign algorithm inputs the master public key , a user partial private key , a secret value , and a message m. It first concatenates the identity and the message m. Then, it computes and runs the SM2 signing algorithm with to generate the part signature. In detail,
- Compute ;
- Pick randomly and compute ;
- Compute .
Next, it outputs the signature ; - Verify : The Verify algorithm receives the master public key , an identity , public key , a message m, and a signature . It first checks if holds. Then, it runs the SM2 verification algorithm to check the validity of and . In detail,
- Compute . Then check if the equations holds;
- Compute .Then check if the equations holds;
- Check if the equations holds
If all three equations hold, it outputs “1”. Otherwise, it outputs “0”.
4. Performance Analyses
4.1. Computational Costs
The efficiency performance of the scheme was evaluated by comparing it with Huang’s CLS [13] through simulation experiments. We use to represent the time of a point addition, a pairing operation, a scalar multiplication in the elliptic curve group, and an exponential operation in the group. G and represent the elliptic curve group and the group of integers that are modular to a prime number p without an explicit statement. The experimental environment and the results are shown as Table 1 and Table 2, respectively:

Table 1.
Experimental environment.

Table 2.
Efficiency comparison of the CLS schemes.
4.2. Batch Verification
This scheme requires the pairing operations in the verification algorithm, which consumes a lot of resources. To accelerate the algorithm, we can batch process a large number of signatures from the same user. For example, when multiple signatures from the same user are received consecutively, the received must all be consistent. Therefore, the verification equations can be performed once. The following is a simplified validation algorithm:
Batch-Verify : The verification algorithm inputs the master public key , a user’s identity , a public key , n messages , and n signatures . The is denoted as and the is denoted as .
- Compute , , , . Then, check if the equations holds. For n signatures coming from the same user, the are the same so that this step only needs to be calculated once for n signatures;
- Compute , , , . Then, check if the equation holds. This step must to be executed for each signature;
- Check if the equation holds. This step only needs to be calculated once for n signatures.
If all three equations hold, it outputs “1”. Otherwise, it outputs “0”.
In this way, when verifying n signatures from the same user, step 1 and 3 only need to be performed once and step 2 needs to be performed n times. Thus, the expensive pairing operation only needs to be performed twice.
Multi-User-Batch-Verify (, , , , ): The verification algorithm inputs the master public key , m identities , and m public keys . The and denote the j-th message and signature for i-th user, respectively. The is denoted as and the is denoted as .
- Compute , , , . Then, check if the equation holds. This step needs to be calculated once for each user;
- Compute , , , . Then, check if the equation holds. This step must to be calculated for each signature;
- For all m public keys, calculate = =. This calculation can be completed by a third-party assistant and the results can be sent to the user. Then, the user calculates and . Finally, check if the equation holds.
If all equations in the three steps hold, it outputs “1”. Otherwise, it outputs “0”.
In this way, when verifying the signatures from m users, the pairing operation can be completed twice locally rather than increasing with the number of users.
5. Conclusions and Future Work
To accelerate the verification algorithm, we extended the CLS scheme proposed by He et al. [28] and accelerated the algorithm execution through batch verification. The proposed scheme is still based on the Chinese national cryptographic standard (SM2) algorithm and no pairing operation is required during the signing process. This guarantees both efficiency and the requirement of using the standard cryptographic algorithm. In addition, the noninteractive zero-knowledge proof (NIZKP) of the signature is replaced by verifying an equation. This improvement provides efficient batch verification for multiple signatures. The number of pairing operations is constant regardless of the amount of signatures.
In this paper, we propose a basic certificateless signature scheme derived from the SM2 algorithm without resorting to the use of pairing operations. Signing or verifying a single signature does not involve any pairing operation. In addition, we further show how to improve the scheme to support batch verification. Nevertheless, the verification of multiple signatures requires a constant number of pairing operations. Despite the fact that the number is constant and is independent from the number of signatures in a batch verification, how to achieve a fully pairing-free SM2-based certificateless signature scheme that supports batch verification is worth studying. In addition, the security analysis is based on the random oracle model, which treats the hash function as an oracle. How to construct schemes without random oracles would also improve the security to a greater extent.
Author Contributions
Conceptualization, C.H.; formal analysis, B.Z.; methodology, C.H.; software, Z.X.; Writing—original draft, Y.W.; Writing—review and editing, L.Z. and Y.F. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the science and technology project of State Grid Corporation of China “Research on lightweight cryptographic technology for power IOT terminal” (Grand No. 5700-202255186A-1-1-ZN).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
All the related research data are available upon authors request.
Acknowledgments
We would like to thank the anonymous reviewers of this paper for their valuable comments and suggestions.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Shamir, A. Identity-Based Cryptosystems and Signature Schemes. In Advances in Cryptology: Proceedings of CRYPTO 84 4; Lecture Notes in Computer Science; Blakley, G.R., Chaum, D., Eds.; Springer: Berlin/Heidelberg, Germany, 1984; Volume 196, pp. 47–53. [Google Scholar] [CrossRef]
- Boneh, D.; Franklin, M.K. Identity-Based Encryption from the Weil Pairing. In Proceedings of the Advances in Cryptology—CRYPTO 2001, 21st Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2001; Proceedings; Lecture Notes in Computer Science. Kilian, J., Ed.; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2139, pp. 213–229. [Google Scholar] [CrossRef]
- Zhang, C.; Zhao, M.; Zhu, L.; Zhang, W.; Wu, T.; Ni, J. FRUIT: A Blockchain-Based Efficient and Privacy-Preserving Quality-Aware Incentive Scheme. IEEE J. Sel. Areas Commun. 2022, 40, 3343–3357. [Google Scholar] [CrossRef]
- Zhang, C.; Hu, C.; Wu, T.; Zhu, L.; Liu, X. Achieving Efficient and Privacy-Preserving Neural Network Training and Prediction in Cloud Environments. IEEE Trans. Dependable Secur. Comput. 2022. early access. [Google Scholar] [CrossRef]
- Hu, C.; Zhang, C.; Lei, D.; Wu, T.; Liu, X.; Zhu, L. Achieving Privacy-Preserving and Verifiable Support Vector Machine Training in the Cloud. IEEE Trans. Inf. Forensics Secur. 2023, 18, 3476–3491. [Google Scholar] [CrossRef]
- Al-Riyami, S.S.; Paterson, K.G. Certificateless Public Key Cryptography. In Proceedings of the Advances in Cryptology—ASIACRYPT 2003, 9th International Conference on the Theory and Application of Cryptology and Information Security, Taipei, Taiwan, 30 November–4 December 2003; Lecture Notes in Computer Science. Laih, C., Ed.; Springer: Berlin/Heidelberg, Germany, 2003; Volume 2894, pp. 452–473. [Google Scholar] [CrossRef]
- Yum, D.H.; Lee, P.J. Generic Construction of Certificateless Signature. In Proceedings of the Information Security and Privacy: 9th Australasian Conference, ACISP 2004, Sydney, Australia, 13–15 July 2004; Lecture Notes in Computer Science. Wang, H., Pieprzyk, J., Varadharajan, V., Eds.; Springer: Berlin/Heidelberg, Germany, 2004; Volume 3108, pp. 200–211. [Google Scholar] [CrossRef]
- Yum, D.H.; Lee, P.J. Generic Construction of Certificateless Encryption. In Proceedings of the Computational Science and Its Applications—ICCSA 2004, International Conference, Assisi, Italy, 14–17 May 2004; Lecture Notes in Computer Science. Laganà, A., Gavrilova, M.L., Kumar, V., Mun, Y., Tan, C.J.K., Gervasi, O., Eds.; Springer: Berlin/Heidelberg, Germany, 2004; Volume 3043, pp. 802–811. [Google Scholar] [CrossRef]
- Hu, B.C.; Wong, D.S.; Zhang, Z.; Deng, X. Key Replacement Attack Against a Generic Construction of Certificateless Signature. In Proceedings of the Information Security and Privacy, 11th Australasian Conference, ACISP 2006, Melbourne, Australia, 3–5 July 2006; Lecture Notes in Computer Science. Batten, L.M., Safavi-Naini, R., Eds.; Springer: Berlin/Heidelberg, Germany, 2006; Volume 4058, pp. 235–246. [Google Scholar] [CrossRef]
- Libert, B.; Quisquater, J. On Constructing Certificateless Cryptosystems from Identity Based Encryption. In Proceedings of the Public Key Cryptography—PKC 2006, 9th International Conference on Theory and Practice of Public-Key Cryptography, New York, NY, USA, 24–26 April 2006; Lecture Notes in Computer Science. Yung, M., Dodis, Y., Kiayias, A., Malkin, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2006; Volume 3958, pp. 474–490. [Google Scholar] [CrossRef]
- Huang, X.; Susilo, W.; Mu, Y.; Zhang, F. On the Security of Certificateless Signature Schemes from Asiacrypt 2003. In Proceedings of the Cryptology and Network Security, 4th International Conference, CANS 2005, Xiamen, China, 14–16 December 2005; Lecture Notes in Computer Science. Desmedt, Y., Wang, H., Mu, Y., Li, Y., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3810, pp. 13–25. [Google Scholar] [CrossRef]
- Au, M.H.; Chen, J.; Liu, J.K.; Mu, Y.; Wong, D.S.; Yang, G. Malicious KGC Attacks in Certificateless Cryptography. IACR Cryptol. ePrint Arch. 2006, 255. [Google Scholar]
- Huang, X.; Mu, Y.; Susilo, W.; Wong, D.S.; Wu, W. Certificateless Signatures: New Schemes and Security Models. Comput. J. 2012, 55, 457–474. [Google Scholar] [CrossRef]
- Zhang, F.; Shen, L.; Wu, G. Notes on the security of certificateless aggregate signature schemes. Inf. Sci. 2014, 287, 32–37. [Google Scholar] [CrossRef]
- Wu, G.; Zhang, F.; Shen, L.; Guo, F.; Susilo, W. Certificateless aggregate signature scheme secure against fully chosen-key attacks. Inf. Sci. 2020, 514, 288–301. [Google Scholar] [CrossRef]
- Shim, K. Design Principles of Secure Certificateless Signature and Aggregate Signature Schemes for IoT Environments. IEEE Access 2022, 10, 124848–124857. [Google Scholar] [CrossRef]
- Hussain, S.; Ullah, S.S.; Ali, I.; Xie, J.; Inukollu, V.N. Certificateless signature schemes in Industrial Internet of Things: A comparative survey. Comput. Commun. 2022, 181, 116–131. [Google Scholar] [CrossRef]
- Housani, H.A.; Baek, J.; Yeun, C.Y. Survey on certificateless public key cryptography. In Proceedings of the 6th International Conference for Internet Technology and Secured Transactions, ICITST 2011, Abu Dhabi, United Arab Emirates, 11–14 December 2011; IEEE: Piscataway, NJ, USA, 2011; pp. 53–58. [Google Scholar]
- Chen, Y.; Tso, R. A survey on security of certificateless signature schemes. IETE Tech. Rev. 2016, 33, 115–121. [Google Scholar] [CrossRef]
- Baek, J.; Safavi-Naini, R.; Susilo, W. Certificateless Public Key Encryption without Pairing. In Proceedings of the Information Security, 8th International Conference, ISC 2005, Singapore, 20–23 September 2005; Lecture Notes in Computer Science. Zhou, J., López, J., Deng, R.H., Bao, F., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3650, pp. 134–148. [Google Scholar] [CrossRef]
- Sun, Y.; Zhang, F.; Baek, J. Strongly Secure Certificateless Public Key Encryption without Pairing. In Proceedings of the Cryptology and Network Security, 6th International Conference, CANS 2007, Singapore, 8–10 December 2007; Lecture Notes in Computer Science. Bao, F., Ling, S., Okamoto, T., Wang, H., Xing, C., Eds.; Springer: Berlin/Heidelberg, Germany, 2007; Volume 4856, pp. 194–208. [Google Scholar] [CrossRef]
- He, D.; Chen, J.; Zhang, R. Efficient and provably-secure certificateless signature scheme without bilinear pairings. IACR Cryptol. ePrint Arch. 2010, 632. [Google Scholar] [CrossRef]
- Gong, Z.; Gao, T.; Guo, N. PCAS: Cryptanalysis and improvement of pairing-free certificateless aggregate signature scheme with conditional privacy-preserving for VANETs. Ad. Hoc. Netw. 2023, 144, 103134. [Google Scholar] [CrossRef]
- Yang, X.; Wen, H.; Diao, R.; Du, X.; Wang, C. Improved Security of a Pairing-Free Certificateless Aggregate Signature in Healthcare Wireless Medical Sensor Networks. IEEE Internet Things J. 2023, 10, 10881–10892. [Google Scholar] [CrossRef]
- Dai, C.; Xu, Z. Pairing-Free Certificateless Aggregate Signcryption Scheme for Vehicular Sensor Networks. IEEE Internet Things J. 2023, 10, 5063–5072. [Google Scholar] [CrossRef]
- Zhang, J.; Mao, J. An efficient RSA-based certificateless signature scheme. J. Syst. Softw. 2012, 85, 638–642. [Google Scholar] [CrossRef]
- Tang, F.; Gan, N.; Yang, X.; Wang, J. Anti malicious KGC certificateless signature scheme based on blockchain and domestic cryptographic SM9. Chin. J. Netw. Inf. Secur. 2022, 8, 9–19. [Google Scholar]
- He, C.; Zhang, B.; Zhang, L.; Xi, Z.; Fang, Y.; Wang, Y. Pairing-Free Certificateless Signature Scheme based on SM2 Algorithm. In Proceedings of the 2nd International Conference on Network Simulation and Evaluation, NSE 2023, Shenzhen, China, 22–24 November 2023; Springer: Berlin/Heidelberg, Germany, 2023. [Google Scholar]
- Gong, Z.; Long, Y.; Hong, X.; Chen, K. Two Certificateless Aggregate Signatures from Bilinear Maps. In Proceedings of the 8th ACIS International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing, SNPD 2007, Qingdao, China, 30 July–1 August 2007; Feng, W., Gao, F., Eds.; IEEE Computer Society: Washington, DC, USA; pp. 188–193. [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).