DDoS Attack Detection in IoT-Based Networks Using Machine Learning Models: A Survey and Research Directions
Abstract
1. Introduction
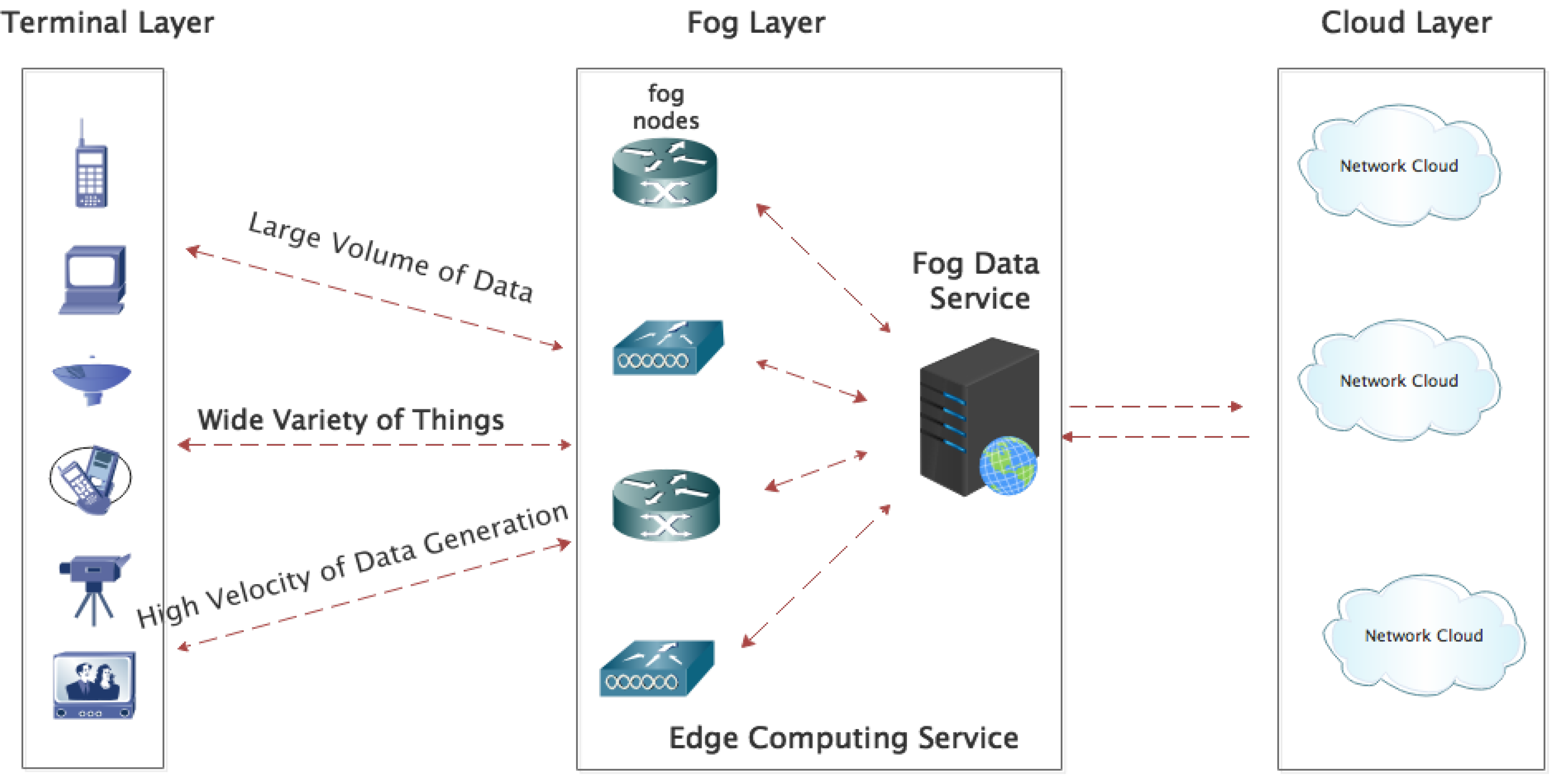
1.1. Internet of Things and Fog Layer
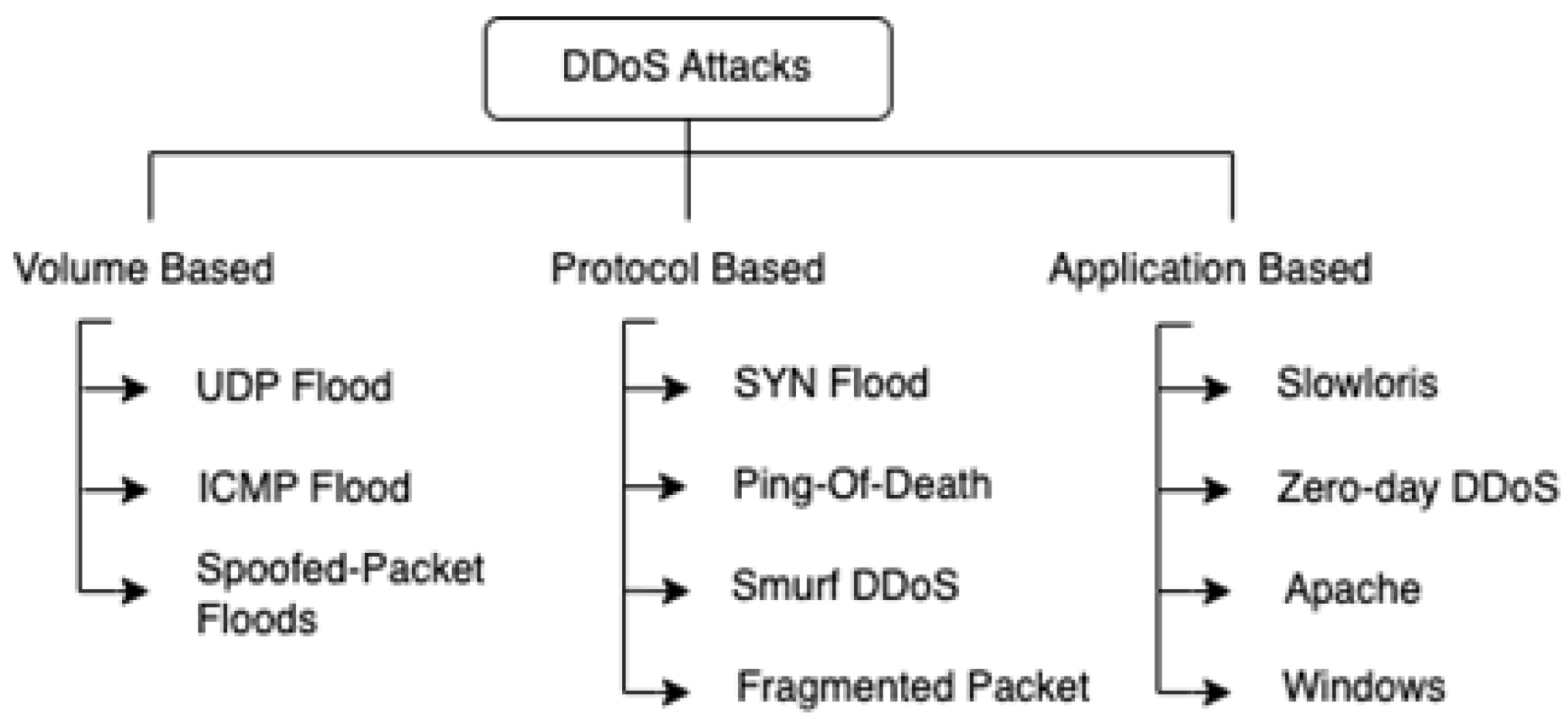
1.2. Distributed Denial of Service Attacks
1.2.1. Volume-Based Distributed Denial of Service Attacks
1.2.2. Protocol-Based Distributed Denial of Services Attacks
1.2.3. Application-Based Distributed Denial of Service Attacks
1.3. Machine Learning Models and Techniques
- Supervised learning is the commonly used type of ML in which a model is developed using a training dataset with predefined outputs. Once the model has been trained, it can predict the decision when new data are provided.
- Unsupervised learning utilizes the entered data solely without having an output corresponding to it. The objective of unsupervised learning is to identify possible hidden patterns or clusters in the data from unlabeled data.
Machine Learning Classifiers
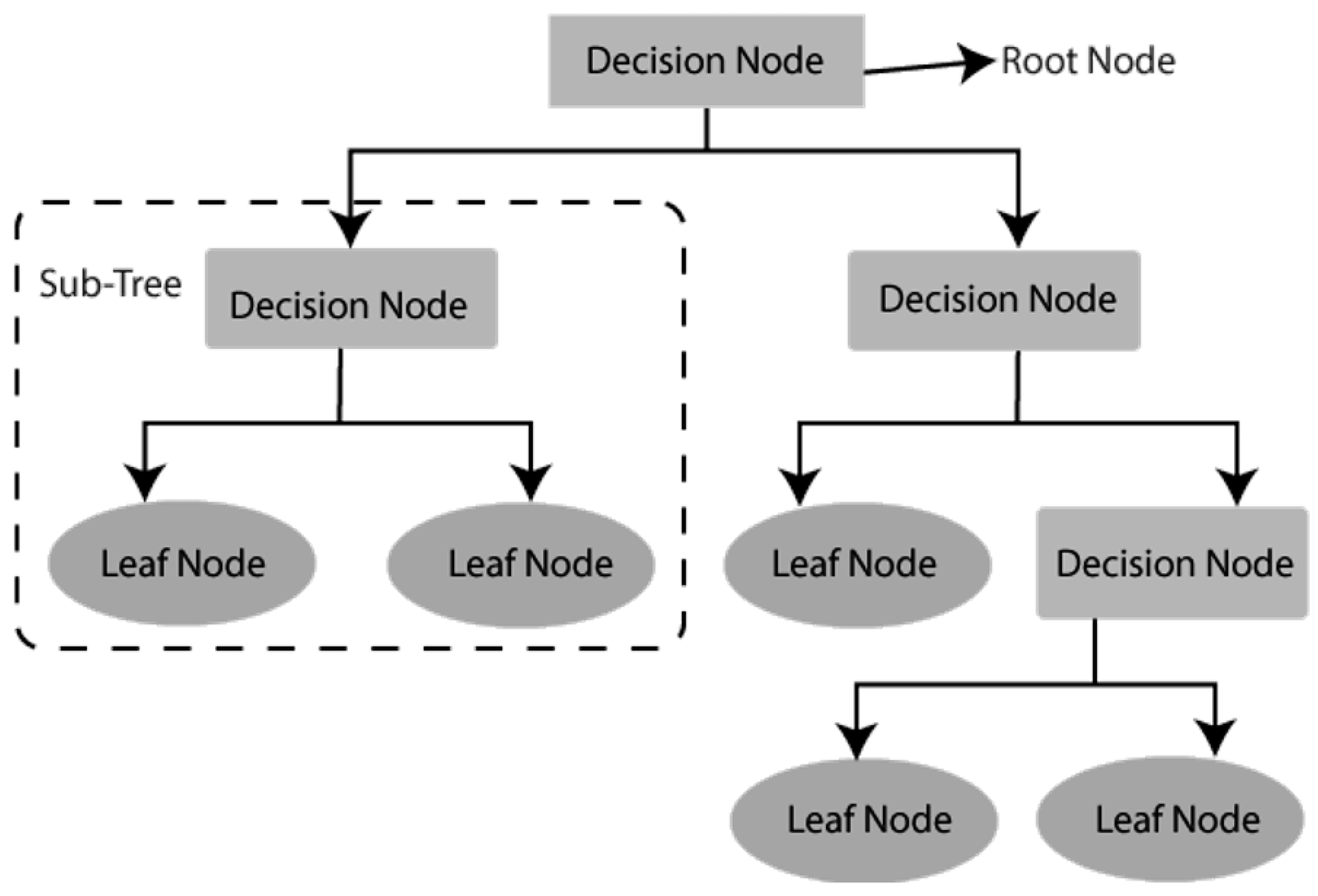
Decision Tree (DT)
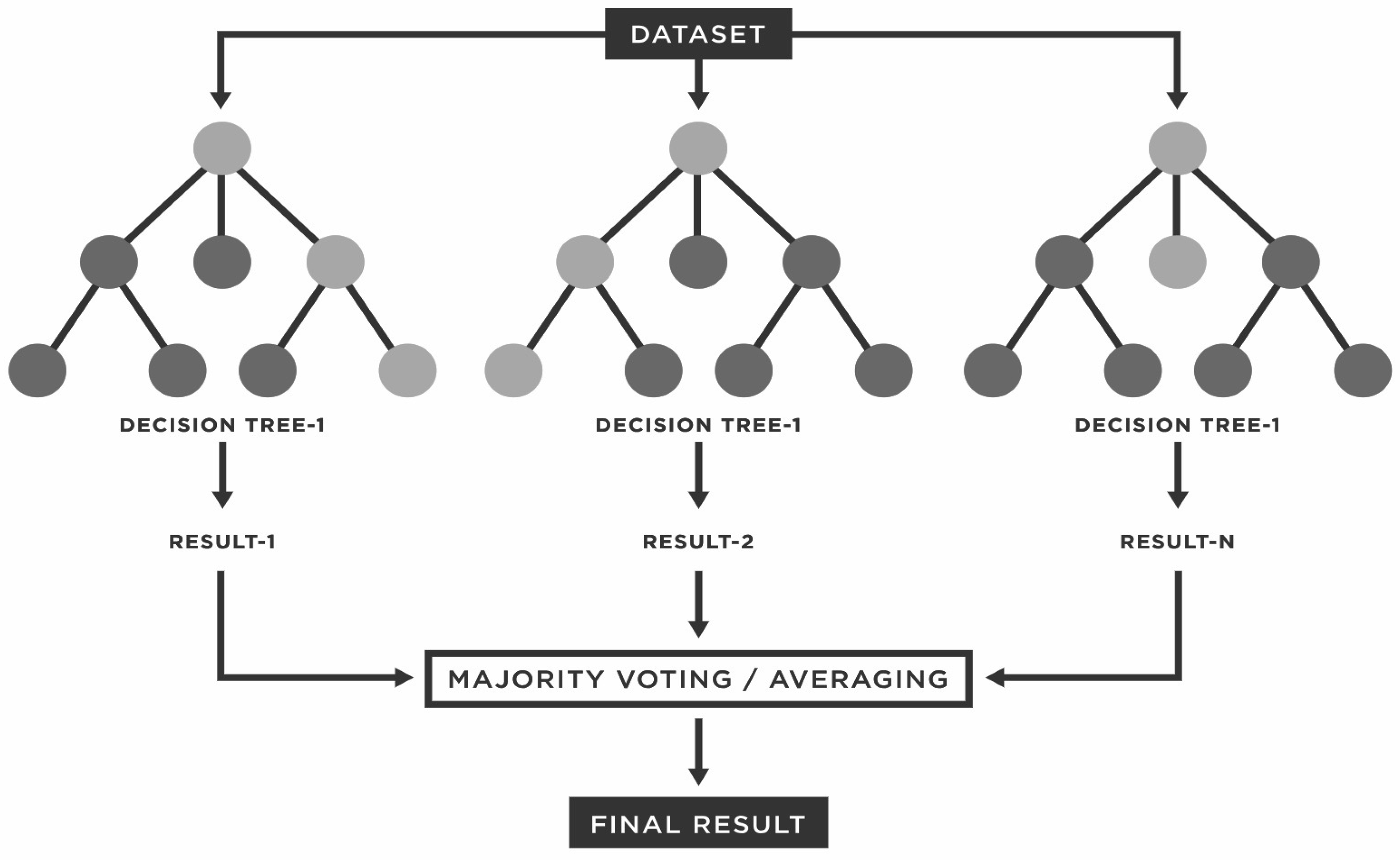
Random Forest (RF)
K-Nearest Neighbors (KNN)
XGBoost (eXtreme Gradient Boosting)
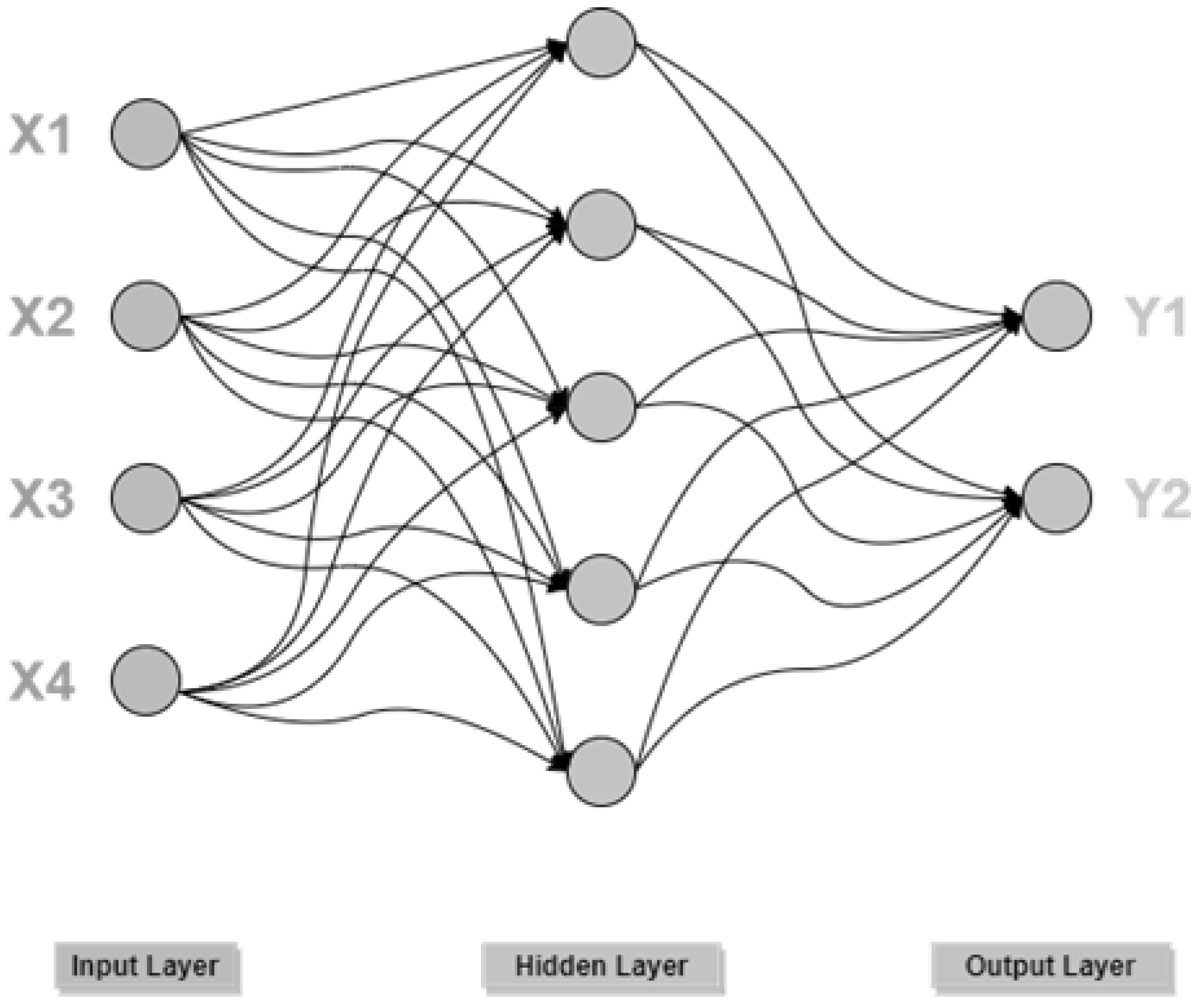
Artificial Neural Network (ANN)
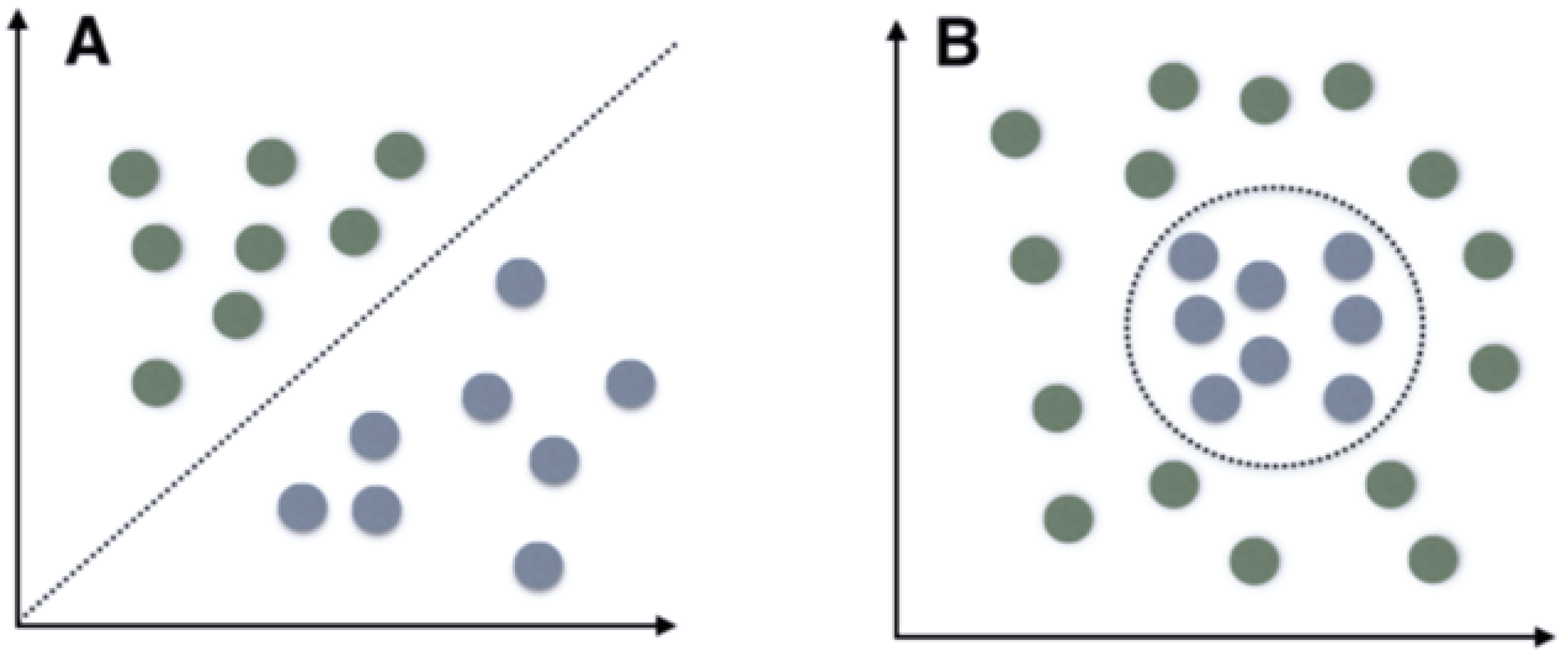
Support Vector Machine (SVM)
- (A)
- Linear SVM: This is utilized for linearly separable data, which implies that if a dataset using a single straight line can be classified into two classes that are linearly separable, the classifier employed is called a linear SVM.
- (B)
- Non-linear SVM: This is utilized for non-linearly separable data, which implies that if a dataset utilizing one straight line cannot be categorized, it is called non-linear data, while the classifier employed is called a non-linear SVM.
Adaptive Boosting (AdaBoost)
1.4. Machine Learning Performance Evaluation
- Accuracy: Accuracy is a widely used metric that measures the overall correctness of the model’s predictions. It represents the proportion of correctly classified instances (i.e., both true positives and true negatives) to the total number of instances. A high accuracy indicates a reliable model, but it may not provide a comprehensive view of the model’s performance due to class imbalance or other factors.
- Precision: Precision is a metric that quantifies the proportion of correctly predicted positive instances (true positives) out of all instances predicted as positive (both true positives and false positives). It measures the model’s ability to avoid false positives. A higher precision indicates a lower rate of false alarms.
- Recall: Recall, also known as sensitivity or the true-positive rate, measures the proportion of correctly predicted positive instances (true positives) out of all actual positive instances (true positives and false negatives). It quantifies the model’s ability to identify all positive instances. A higher recall indicates a lower rate of false negatives.
- F1-Score: The F1-score is a harmonic mean of precision and recall and provides a balanced measure of a model’s performance. It considers both the precision and recall values and is useful when the data has a class imbalance. A higher F1-Score indicates a better trade-off between precision and recall.
- Confusion Matrix: The confusion matrix provides a detailed breakdown of the model’s predictions by showing the number of true positives, true negatives, false positives, and false negatives. It provides insights into the types and frequency of misclassifications, enabling a deeper analysis of model performance.
- Computational Resources: Apart from traditional performance metrics, it is essential to consider the computational resources required by the model. Assessing factors such as training time, memory usage, and inference speed can help determine the practicality and scalability of the model in real-world deployment scenarios.
2. Research Contribution
- What are the current approaches for detecting DDoS attacks in IoT-based networks using machine learning models?
- What are the limitations of existing approaches?
- What are the research directions for improving DDoS attack detection in IoT-based networks using machine learning models?
- Keyword search: The initial search was conducted using keywords such as “DDoS attack”, “Internet of Things”, “IoT-based networks”, “machine learning”, and “DDoS detection” to identify relevant papers in the literature.
- Time frame: Studies published between 2016 and 2022 were considered to ensure the inclusion of recent research and advancements in the field.
- Research objective: The selected studies were required to focus on DDoS attack detection in IoT-based networks using machine learning models. Only papers directly addressing this topic were included.
- Investigation of machine learning models: The studies needed to investigate the effectiveness of machine learning models for DDoS attack detection in IoT-based networks. Papers exploring other detection methods or not employing machine learning were excluded.
- Dataset analysis: Papers related to datasets generated for DDoS attack detection in IoT-based networks were included to explore their characteristics and shortcomings. Studies that discussed dataset properties, size, diversity, and relevance to real-world scenarios were given priority.
2.1. Generated Distributed Denial of Service Attacks on Traffic Datasets
2.2. Machine Learning Methods for Distributed Denial of Service Detection
- Fast detection mode (FDM): This mode classified network traffic when the server was under attack.
- Defensive fast detection mode (DFDM): This mode was an extensive version of FDM that tightened the detection technique to enhance the detection of malicious network traffic.
- High-accuracy mode (HAM): This mode was activated when the server was stable.
2.3. Fog Layer Distributed Denial of Services Detection for an Internet-of-Things-Based Network
3. Discussion and Gap Analysis
- There is a lack of state-of-the-art datasets that are constantly updated to tackle current DDoS complexity and advancement.
- Multiple benchmark datasets suffer from severe class imbalance issues.
- There is a need to investigate a novel set of machine learning models in a comparative analysis study to assess their effectiveness.
- The persistence of DDoS attacks conducted by IoT devices is apparent with the continuity of lack of security measures on IoT devices and the rapid distribution of botnet viruses that continue to evolve each year.
- DDoS attacks in general are going to become even more frequent, more complicated, and relatively inexpensive to perform.
- The use of obscure IoT devices, such as smart refrigerators, thermostats, and CCTV cameras, was previously uncommon. Yet, such devices currently pose a dominant threat that can be utilized as botnets to perform DDoS attacks and take down a target’s services or disrupt them.
4. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Wang, J.; Liu, Y.; Feng, H. IFACNN: Efficient DDoS attack detection based on improved firefly algorithm to optimize convolutional neural networks. Math. Biosci. Eng. 2021, 19, 1280–1303. [Google Scholar] [CrossRef]
- Hasan, M. State of IOT 2022: Number of Connected IOT Devices Growing 18% to 14.4 Billion Globally. IoT Analytics. 2022. Available online: https://iot-analytics.com/number-connected-iot-devices/ (accessed on 14 May 2023).
- Kim, H.S. Fog Computing and the Internet of Things: Extend the Cloud to Where the Things Are. 2015. Available online: https://www.researchgate.net/profile/Mohamed-Mourad-Lafifi/post/Is_there_any_simulation_tool_for_fog_computing/attachment/59d638c079197b8077995f4c/AS%3A398883160117248%401472112564706/download/Fog+Computing+and+the+Internet+of+Things++Extend+the+Cloud+to+Where+the+Things+Are.pdf (accessed on 28 August 2022).
- Ma, K.; Bagula, A.; Nyirenda, C.; Ajayi, O. An IoT-Based Fog Computing Model. Sensors 2019, 19, 2783. [Google Scholar] [CrossRef]
- Džaferović, E.; Sokol, A.; Abd Almisreb, A.; Norzeli, S.M. DoS and DDoS vulnerability of IoT: A review. Sustain. Eng. Innov. 2019, 1, 43–48. [Google Scholar] [CrossRef]
- Mansfield-Devine, S. The evolution of DDoS. Comput. Fraud Secur. 2014, 2014, 15–20. [Google Scholar] [CrossRef]
- Sieklik, B.; Macfarlane, R.; Buchanan, W. Evaluation of TFTP DDoS amplification attack. Comput. Secur. 2016, 57, 67–92. [Google Scholar] [CrossRef]
- Lukaseder, T.; Stölzle, K.; Kleber, S.; Erb, B.; Kargl, F. An SDN-based Approach for Defending against Reflective DDoS Attacks. In Proceedings of the 2018 IEEE 43rd Conference on Local Computer Networks (LCN), Chicago, IL, USA, 1–4 October 2018. [Google Scholar]
- Neelam, D.; Prasenjit, M.; Shashank, S.; Rahamatullah, K. Research Trends in Security and DDoS in SDN. Secur. Commun. Netw. 2016, 9, 6386–6411. [Google Scholar]
- Ehrenkranz, T.; Li, J. On the State of IP Spoofing Defense. ACM Trans. Internet Technol. 2009, 9, 1–29. [Google Scholar] [CrossRef]
- Vishwakarma, R.; Jain, A.K. A survey of DDoS attacking techniques and defence mechanisms in the IoT network. Telecommun. Syst. 2019, 73, 3–25. [Google Scholar] [CrossRef]
- McGregory, S. Preparing for the next DDoS attack. Netw. Secur. 2013, 2013, 5–6. [Google Scholar] [CrossRef]
- Dantas, Y.G.; Nigam, V.; Fonseca, I.E. A selective defense for application layer ddos attacks. In Proceedings of the 2014 IEEE Joint Intelligence and Security Informatics Conference, The Hague, The Netherlands, 24–26 September 2014. [Google Scholar]
- Decision Tree Classification Algorithm. JavaTpoint. Available online: https://www.javatpoint.com/machine-learning-decision-tree-classification-algorithm (accessed on 26 September 2022).
- Random Forest Algorithm. JavaTpoint. Available online: https://www.javatpoint.com/machine-learning-random-forest-algorithm (accessed on 29 September 2022).
- Yiu, T. Understanding Random Forest. Towardsdatascience. 2019. Available online: https://towardsdatascience.com/understanding-random-forest-58381e0602d2 (accessed on 10 October 2022).
- What Is a Random Forest? Available online: https://www.tibco.com/reference-center/what-is-a-random-forest (accessed on 26 September 2022).
- K-Nearest Neighbor(KNN) Algorithm for Machine Learning. Javatpoint. Available online: https://www.javatpoint.com/k-nearest-neighbor-algorithm-for-machine-learning (accessed on 10 October 2022).
- What Is XGBoost? NVIDIA Data Science Glossary. Available online: https://www.nvidia.com/en-us/glossary/data-science/xgboost/ (accessed on 10 October 2022).
- XGBoost. Geeksforgeeks. 2022. Available online: https://www.geeksforgeeks.org/xgboost/ (accessed on 29 September 2022).
- Ghatak, K. XGBoost Algorithm in Machine Learning. Naukri Learning. 2022. Available online: https://www.shiksha.com/online-courses/articles/xgboost-algorithm-in-machine-learning/ (accessed on 9 January 2023).
- Artificial Neural Network Tutorial. Javatpoint. Available online: https://www.javatpoint.com/artificial-neural-network (accessed on 10 October 2022).
- Recurrent Neural Network Algorithms Overview. BUSINESS & AI: Artificial Intelligence for Better Decision Making. Available online: https://www.business-and-ai.com/recurrent-neural-network-algorithms-overview/ (accessed on 26 September 2022).
- Support Vector Machine Algorithm. Javatpoint. Available online: https://www.javatpoint.com/machine-learning-support-vector-machine-algorithm (accessed on 10 October 2022).
- Introduction to Support Vector Machines (SVM). Geeksforgeeks. 2022. Available online: https://www.geeksforgeeks.org/introduction-to-support-vector-machines-svm/ (accessed on 29 September 2022).
- The Ultimate Guide to AdaBoost Algorithm|What Is AdaBoost Algorithm? Great Learning. 2022. Available online: https://www.mygreatlearning.com/blog/adaboost-algorithm/ (accessed on 29 September 2022).
- Boosting in Machine Learning|Boosting and AdaBoost. Geeksforgeeks. 2022. Available online: https://www.geeksforgeeks.org/boosting-in-machine-learning-boosting-and-adaboost/ (accessed on 29 September 2022).
- Saini, A. AdaBoost Algorithm—A Complete Guide for Beginners. Analytics Vidhya. 2021. Available online: https://www.analyticsvidhya.com/blog/2021/09/adaboost-algorithm-a-complete-guide-for-beginners/ (accessed on 29 September 2022).
- Almaraz-Rivera, J.G.; Perez-Diaz, J.A.; Cantoral-Ceballos, J.A. Transport and Application Layer DDoS Attacks Detection to IoT Devices by Using Machine Learning and Deep Learning Models. Sensors 2022, 22, 3367. [Google Scholar] [CrossRef]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B.P. Towards the Development of Realistic Botnet Dataset in the Internet of Things for Network Forensic Analytics: Bot-IoT Dataset. Future Gener. Comput. Syst. 2019, 100, 779–796. [Google Scholar] [CrossRef]
- Liu, Z.; Thapa, N.; Shaver, A.; Roy, K.; Siddula, M.; Yuan, X.; Yu, A. Using Embedded Feature Selection and CNN for Classification on CCD-INID-V1—A New IoT Dataset. Sensors 2021, 21, 4834. [Google Scholar] [CrossRef]
- Ullah, I.; Mahmoud, Q.H. A Scheme for Generating a Dataset for Anomalous Activity Detection in IoT Networks. In Advances in Artificial Intelligence; Springer: Cham, Switzerland, 2020. [Google Scholar]
- Alsaed, A.; Moustafa, N.; Tari, Z.; Mahmood, A.; Anwar, A. TON_IoT Telemetry Dataset: A NewGeneration Dataset of IoT and IIoT forDatadriven Intrusion Detection Systems. IEEE Access 2020, 8, 165130–165150. [Google Scholar] [CrossRef]
- Panigrahi, R.; Borah, S. A detailed analysis of CICIDS2017 dataset for designing Intrusion Detection Systems. Int. J. Eng. Technol. 2018, 7, 479–482. [Google Scholar]
- Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization. In Proceedings of the International Conference on Information Systems Security And Privacy (ICISSP), Funchal, Portugal, 22–24 January 2018; Volume 7, pp. 479–482. [Google Scholar]
- Gopi, R.; Sathiyamoorthi, V.; Selvakumar, S.; Manikandan, R.; Chatterjee, P.; Jhanjhi, N.Z.; Luhach, A.K. Enhanced method of ANN based model for detection of DDoS attacks on multimedia internet of things. Multimed. Tools Appl. 2021, 24, 26739–26757. [Google Scholar] [CrossRef]
- Amrish, R.; Bavapriyan, K.; Gopinaath, V.; Jawahar, A.; Vinoth, C.K. DDoS Detection using Machine Learning Techniques. J. IoT Soc. Mob. Anal. Cloud 2022, 4, 24–32. [Google Scholar] [CrossRef]
- Gaur, V.; Kumar, R. Analysis of Machine Learning Classifiers for Early Detection of DDoS Attacks on IoT Devices. Arab. J. Sci. Eng. 2022, 47, 1353–1374. [Google Scholar] [CrossRef]
- Ismail, M.I.; Mohmand, H.; Hussain, A.A.; Khan, U.; Ullah, M.; Zakarya, A.; Ahmed, M.; Raza, I.; Rahman, U.; Haleem, M. A Machine Learning-Based Classification and Prediction Technique for DDoS Attacks. IEEE Access 2022, 10, 21443–21454. [Google Scholar] [CrossRef]
- Seifousadati, A.; Ghasemshirazi, S.; Fathian, M. A Machine Learning Approach for DDoS Detection on IoT Devices. arXiv 2021, arXiv:2110.14911. [Google Scholar]
- Aysa, M.H.; Ibrahim, A.A.; Mohammed, A.H. IoT Ddos Attack Detection Using Machine Learning. In Proceedings of the 2020 4th International Symposium on Multidisciplinary Studies and Innovative Technologies (ISMSIT), Istanbul, Turkey, 22–24 October 2020; pp. 1–7. [Google Scholar]
- Saini, P.S.; Behal, S.; Bhatia, S. Detection of DDoS Attacks using Machine Learning Algorithms. In Proceedings of the 2020 7th International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 12–14 March 2020; Volume 78, pp. 16–21. [Google Scholar]
- Alkasassbeh, M.; Al-Naymat, G.; Hassanat, A.B.; Almseidin, M. Detecting Distributed Denial of Service Attacks Using Data Mining Techniques. Int. J. Adv. Comput. Sci. Appl. (IJACSA) 2016, 7, 436–445. [Google Scholar] [CrossRef]
- Pande, S.; Khamparia, A.; Gupta, D.; Thanh, D.N.H. DDOS Detection Using Machine Learning Technique. In Recent Studies on Computational Intelligence; Studies in Computational Intelligence; Springer: Singapore, 2021; Volume 921. [Google Scholar]
- Gupta, B.B.; Chaudhary, P.; Chang, X.; Nedjah, N. Smart defense against distributed Denial of service attack in IoT networks using supervised learning classifiers. Comput. Electr. Eng. 2022, 98, 107726. [Google Scholar] [CrossRef]
- Mihoub, A.; Fredj, O.B.; Cheikhrouhou, O.; Derhab, A.; Krichen, M. Denial of service attack detection and mitigation for internet of things using looking-back-enabled machine learning techniques. Comput. Electr. Eng. 2022, 98, 107716. [Google Scholar] [CrossRef]
- Pokhrel, S.; Abbas, R.; Aryal, B. IoT Security: Botnet detection in IoT using Machine learning. arXiv 2021, arXiv:2104.02231. [Google Scholar]
- Doshi, R.; Apthorpe, N.; Feamster, N. Machine Learning DDoS Detection for Consumer Internet of Things Devices. In Proceedings of the 2018 IEEE Security and Privacy Workshops (SPW), San Francisco, CA, USA, 24 May 2018; pp. 29–35. [Google Scholar]
- Islam, U.; Muhammad, A.; Mansoor, R.; Hossain, M.S.; Ahmad, I.; Tageldin, E.; Khan, J.A.; Rehman, A.U.; Shafiq, M. Detection of Distributed Denial of Service (DDoS) Attacks in IOT Based Monitoring System of Banking Sector Using Machine Learning Models. Sustainability 2022, 14, 8374. [Google Scholar] [CrossRef]
- Roopak, M.; Tian, G.Y.; Chambers, J. An Intrusion Detection System Against DDoS Attacks in IoT Networks. In Proceedings of the 10th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 6–8 January 2020; pp. 562–567. [Google Scholar]
- Prasad, A.; Chandra, S. VMFCVD: An Optimized Framework to Combat Volumetric DDoS Attacks using Machine Learning. Arab. J. Sci. Eng. 2022, 47, 9965–9983. [Google Scholar] [CrossRef]
- Sharma, D.K.; Dhankha, T.; Agrawal, G.; Singh, S.K.; Gupta, D.; Nebhen, J.; Razzak, I. Anomaly detection framework to prevent DDoS attack in fog empowered IoT networks. Ad Hoc Netw. 2021, 121, 102603. [Google Scholar] [CrossRef]
- Hassan, K.F.; Manna, M.E. Detection and mitigation of DDoS attacks in the Internet of things using a fog computing hybrid approach. Bull. Electr. Eng. Inform. 2022, 11, 1604–1613. [Google Scholar] [CrossRef]
| Ref. No. | Year | Dataset | No. of Features | ML/DL Models | Highest ML/DL Model Accuracy | Performance Rate |
|---|---|---|---|---|---|---|
| [37] | 2022 | CICDDoS2019 | Best 15 features selected by ExtraTreesClassifier from among 88 features | KNN, DT, RF, ANN | ANN | Accuracy (99.95%), precision (99.95%), recall (100%), F1-Score (99.97%) |
| [39] | 2022 | UNWS-NB15 | - | RF and XGBoost | XGBoost | Average accuracy (AC = 90%), precision (90%), recall (90), F1-Score (90%) |
| [49] | 2022 | Kaggle banking dataset | Homogeneity measure (k-means clustering) for choosing important features | SVM, KNN, RF | SVM | Accuracy (99.8%), precision (99.07%), recall (98.32%), F1-Score (98.5%) |
| [29] | 2022 | BoT-IoT | Three different feature sets from 35 variables ranged from 15 and 18 each | ML = SVM, DT, RF DL = RNN, LSTM, GRU, MLP | DT (robust) and RF outperforms the DL models | Average accuracy (99%) and (100%) accuracy, precision, recall, and F1-Score |
| [51] | 2022 | CICIDS2017,CSE-CIC-IDS2018, CICDDoS2019, DoHBrw2020, NBaIoT2018,UNSW2018 BoTIoT, and UNSW NB15. | Two | AdaBoost, Bagging, GB, KNN, RF, VMFCVD (HAM, FDM, and DFDM modes). | VMFCVD (HAM mode) | Average accuracy (99%), precision (99.99%), and F1-Score (99.99%). |
| [36] | 2022 | KDD Cup99 | 60 | Only ANN | - | - |
| [46] | 2022 | BoT-IoT | 10 best features | DT, RF, KNN, MLP, RNN, LSTM | KNN, RF | KNN Accuracy (99.93) when not applying looking-back approach; RF Accuracy (99.81%) when applying looking-back approach |
| [38] | 2021 | CICDDoS2019 | ANOVA, chi-squared test, and extra tree used to select the best features from among 79 features | RF, DT, KNN, XGBoost | XGBoost + ANOVA = 15 features | XGBoosta + ANOVA: accuracy (98.347%), precision (99%), recall (99%), F1-Score (99%); XGBoost + chi-squared: accuracy (92.67%); XGBoost + extra tree: accuracy (92.78%) |
| [31] | 2021 | CCD-INID-V1 | 83 | XGBoost, RF | XGBoost coupled with RF | - |
| [40] | 2021 | CICDDoS2019 | 10 best features | Naïve Bayes, SVM, AdaBoost, XGBoost, KNN, RF | AdaBoost and XGBoost | Accuracy (100%), F1-Score (1.0) |
| [47] | 2021 | BoT-IoT | Top eight features were selected based on the Chi-Square | KNN, Gaussian Naïve Bayes, MLP ANN | KNN | Accuracy (92.1%), ROC AUC (92.2%) on highly imbalanced real-time data |
| [44] | 2021 | NSL-KDD | - | RF | RF | Accuracy (99.76%) |
| [41] | 2020 | Generated | 40 out of 115 were selected | LSVM, NN, DT, RF | RF coupled with DT | TPR (99.7%), FPR (0.3%), precision (99.7%), recall (99.7%), F1-Score (99.7%), error MAE (DT = 0.31%, RF = 0.37%) |
| [42] | 2020 | Generated | 27 | RF, MLP, J48, naïve Bayes | J48 decision tree | Accuracy (98.64%) |
| [50] | 2020 | Modified CICIDS2017 | 15 out of 85 features | NSGA-II-aJG IDS, MLP, SVM, Bayes, RF | SVM | Accuracy (94.50%) |
| [48] | 2018 | Generated | Three stateless features, three stateful features | RF, KNN, LSVM, DT, NN | All five algorithms | Accuracy, precision, recall, F1-Score higher than (99.0%.) |
| [34] | 2017 | CIC-IDS2017 | 80 | KNN, RF, ID3, Adaboost, MLP, naive Bayes, QDA | KNN, RF, and ID3 | - |
| [45] | 2022 | Generated | 26 features symbolize IoT network behavior and depend on the network flow information | SVM, RF, DT, KNN, NB, LR | RF | Accuracy (99.2%), precision (96.7%), recall ( 98.9%), F-Score (97.8%) |
| Dataset | Year | Publicly Available | Hardware Utilized | Software Utilized | Limitations | Contains IoT Traffic | Setup (Real, Synthetic) |
|---|---|---|---|---|---|---|---|
| CCD-INID-V1 | 2021 | - | Raspberry Pi, Rainbow HAT, smart sensors | Wireshark | Made in consideration with IDS. Does not contain DDoS traffic, only DoS. The dataset did not contain diverse internet usage cases, such as a person surfing the internet. | Yes | Real |
| TON_IoT | 2020 | Yes | Telemetry sensors, smart fridges, thermostats | Nmap, Nessus, Python Scapy NSX-VMware platform & Network audit logs | Imbalanced data, and does not provide intrusion assessment using different machine learning techniques with the proposed dataset to validate it. | Yes | Real |
| CIC-IDS2017 | 2017 | Yes | Modems, routers, switches, firewalls | Ncrack, Metasploit modules, Nmap NSE, CICFlowMeter, Pcap Analyzer, CSV Generator | High-class imbalance, a huge volume of data, and missing values. Focus on multiple attacks including DDoS. Not focused on IoT context. | No | Real |
| BOT-IoT | 2019 | Yes | Four Kali attacking machines targeting Ubuntu server, Ubuntu mobile, Windows 7, and Metasploitable VMs. The firewall was used to ensure the validity of the dataset-labeling process | GoldenEye + hping3, Argus tool, and Ostinato tool | Severe class imbalance. Does not cover all types of DDoS attacks. | Yes | Real |
| IoTID20 | 2020 | Yes | Smart home devices, WiFi cameras, laptops, tablets, smartphones | - | Suffers from class imbalance. Does not cover all types of DDoS attacks (only Mirai DDoS). | Yes | Real |
| CSE-CIC-IDS2018 | 2018 | Yes | Windows and Linux-based workstations | CICFlowMeter, Slowloris, LOIC, HOIC, DVWA, Patator, Hulk, GoldenEye, Slowhttptest, Selenium Framework, Dropbox, Nmap, portscan, Ares, Low Orbit Ion Canon (LOIC), AWS computing platform, OpenSSL, Adobe Acrobat Reader 9. | Seven different attack scenarios: brute-force, Heartbleed, Botnet, DoS, DDoS, Web attacks, and infiltration of the network from inside. | No | Real |
| CIC-DDoS-2019 | 2019 | Yes | Servers, firewalls, switches, PCs | CICFlowMeter, scikit-learn | Not focused on IoT context. | No | Real |
| CIRA-CIC-DoHBrw-2020 | 2020 | Yes | Servers, switches, routers. | Google Chrome, Mozilla Firefox, dns2tcp, DNSCat2, Iodine, AdGuard, Cloudflare, Google DNS, Quad9, DoHLyzer, GeckoDriver, DoH Data Collector, DoHMeter | Implementing DoH protocol within an application using five different browsers and tools and four servers to capture Benign DoH, Malicious DoH, and non-DoH traffic. | No | Synthetic |
| N-BaIoT2018 | 2018 | Yes | Servers, switches, wires, routers, commercial IoT devices, scanners, and loaders | Wireshark, Keras | Focused on Mirai and Bashlite DDoS attack types only. | No | Real |
| UNSW NB15 | 2015 | Yes | Servers, routers, firewalls. | IXIA, tcpdump, Argus, Bro-IDS | DDoS attacks are not taken into consideration. Not focused on IoT context. | No | Synthetic |
| KDD Cup99 | 1999 | Yes | Servers, PCs | MATLAB, DARPA’98 IDS Evaluation Program | Outdated dataset. Redundant records. Not focused on IoT context. | No | Synthetic |
| NSL-KDD | 2009 | Yes | KDD Cup99 setup | KDD Cup99 setup | All types of DDoS attacks are not considered in this dataset. Not focused on IoT context. | No | Synthetic |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alahmadi, A.A.; Aljabri, M.; Alhaidari, F.; Alharthi, D.J.; Rayani, G.E.; Marghalani, L.A.; Alotaibi, O.B.; Bajandouh, S.A. DDoS Attack Detection in IoT-Based Networks Using Machine Learning Models: A Survey and Research Directions. Electronics 2023, 12, 3103. https://doi.org/10.3390/electronics12143103
Alahmadi AA, Aljabri M, Alhaidari F, Alharthi DJ, Rayani GE, Marghalani LA, Alotaibi OB, Bajandouh SA. DDoS Attack Detection in IoT-Based Networks Using Machine Learning Models: A Survey and Research Directions. Electronics. 2023; 12(14):3103. https://doi.org/10.3390/electronics12143103
Chicago/Turabian StyleAlahmadi, Amal A., Malak Aljabri, Fahd Alhaidari, Danyah J. Alharthi, Ghadi E. Rayani, Leena A. Marghalani, Ohoud B. Alotaibi, and Shurooq A. Bajandouh. 2023. "DDoS Attack Detection in IoT-Based Networks Using Machine Learning Models: A Survey and Research Directions" Electronics 12, no. 14: 3103. https://doi.org/10.3390/electronics12143103
APA StyleAlahmadi, A. A., Aljabri, M., Alhaidari, F., Alharthi, D. J., Rayani, G. E., Marghalani, L. A., Alotaibi, O. B., & Bajandouh, S. A. (2023). DDoS Attack Detection in IoT-Based Networks Using Machine Learning Models: A Survey and Research Directions. Electronics, 12(14), 3103. https://doi.org/10.3390/electronics12143103










