Abstract
The increasing proliferation of GPS-enabled mobile devices, including Unmanned Aerial Vehicles (UAVs), smartphones, and laptops, has resulted in a significant upsurge in the outsourcing of spatial data to cloud servers for storage and computation purposes, such as task allocation and location-based services. However, the reliance on untrusted cloud servers introduces the risk of privacy breaches, as these servers possess the ability to deduce and access users’ private information based on task content and query requirements. Existing privacy-preserving task-allocation schemes offer only coarse-grained and non-temporal access control, which restricts their applicability in scenarios involving multiple users and time-series data, such as trajectory and time-related routes. To overcome these challenges, this paper proposes an Efficient and Privacy-Preserving Task Allocation with Temporal Access Control (EPTA-T) scheme for mobile crowdsensing. By leveraging the techniques of Gray code and randomizable matrix multiplication, EPTA-T achieves efficient and privacy-preserving task allocation in mobile crowdsensing. Specifically, EPTA-T supports fine-grained and temporal access control through the utilization of an attribute-based access tree and function integration. The formal security analysis demonstrated that EPTA-T effectively guarantees data privacy and query privacy throughout the task allocation process. Extensive experiments conducted using a real-world dataset indicated that the EPTA-T scheme surpassed the performance of the state-of-the-art scheme.
1. Introduction
Recently, with the increasing proliferation of task allocation in mobile crowdsensing, it notably enhances the crowdsensing paradigm capability of helping requesters find workers to complete location-aware tasks. This enables requesters to specify task requirements that can be matched with workers based on their respective locations. However, in the mobile crowdsensing environment, the crowdsensing paradigm is inherently untrusted, creating the potential for the capture or inference of task information and workers’ locations [1,2]. A prevailing method is to encrypt the spatial data and task content before outsourcing to the crowdsensing paradigm [3], which alleviates the privacy concerns, but incurs limited query functionality and query performance. In addition, the presence of time-related spatial data necessitates the implementation of Temporal Access Control (TAC) in task allocation. For instance, in a Didi Chuxing-based task allocation scenario, if a driver is situated near a requester between the hours of 9:00 and 10:00, the requester can find the driver at any time within that time range, such as 9:30; otherwise, he/she cannot match the driver. Theoretically speaking, a worker’s spatial data can only be accessed at the current time if and only if falls within the worker’s time constraint interval . Unfortunately, existing task-allocation schemes do not support temporal access control.
Challenge 1: How to design an Efficient and Privacy-Preserving Task Allocation (EPTA) scheme that supports Temporal Access Control (TAC). In mobile crowdsensing, workers’ spatial data are typically associated with time-series objects, while requesters’ attributes also contain timestamps. To achieve effective and accurate task allocation, TAC needs to be considered and integrated into the mobile crowdsensing system. However, directly combining existing EPTA schemes [1,2,4] with TAC schemes [5,6] may result in privacy breaches and an excessive burden of key management. EPTA and TAC are performed separately. To this end, the cloud server knows which worker meets the task requirements regardless of whether he/she can be accessed, which reveals the worker’s timestamp and the worker’s location. Moreover, the crowdsensing paradigm can deduce which workers satisfy the task requirements by observing the accessed spatial data, thereby leaking the access pattern. Unfortunately, access pattern leakage can lead to significant privacy issues, such as the disclosure of home addresses, preferences, and behaviors. Additionally, existing approaches have employed attribute-based encryption to enable fine-grained data sharing with access control [7]. However, this introduces computational overhead in terms of data encryption and task allocation. To improve search performance, some symmetric-encryption-based task-allocation schemes [1,8] have been designed. Nevertheless, in multi-user task allocation models, clients are required to share the same secret key, which may lead to key privacy leakage and key management concerns.
Challenge 2: How to provide an arbitrary geometric range query while achieving a fast search. In task allocation, requesters often submit irregular geometric query ranges to find suitable workers located within specific areas for task assignments. However, existing schemes [9,10] only support single or limited geometric ranges, such as circular, rectangular, or triangular ranges. While homomorphic encryption offers a viable approach for secure geometric range queries [11], the computational overhead associated with it is often unacceptable in practical scenarios. To achieve a fast search, Searchable Symmetric Encryption (SSE) [12,13,14] is commonly employed to enable secure and efficient retrieval of ciphertexts. Unfortunately, SSE fails to support complex query functions such as geometric range queries and lacks flexible key management for multi-user task allocation scenarios. In particular, some works have explored schemes for k-Nearest Neighbor (kNN) queries [15] and skyline queries [16] with privacy guarantees. However, these schemes cannot be directly applied to geometric range queries.
In this paper, we aimed to address the above challenging issues. Specifically, we propose an Efficient and Privacy-Preserving Task Allocation with Temporal Access Control (EPTA-T) scheme for mobile crowdsensing, which efficiently allocates tasks while preserving privacy and incorporating temporal access control. EPTA-T is specifically designed to address the limitations of existing schemes in supporting both task allocation and temporal access control. The main contributions are summarized as follows:
- We utilized Gray code to encode spatial data into vectors. These encoded vectors were then encrypted using randomizable matrix multiplication, enabling us to achieve efficient and privacy-preserving task allocation. This approach significantly reduced the computational overhead associated with data encryption and task allocation, while eliminating the need for key sharing among users.
- To support temporal access control, we leveraged the techniques of function differentiation and function integration. By incorporating these techniques into ciphertext-policy Attribute-Based Encryption (ABE), we constructed an access-tree-based policy. This policy enables precise control over temporal access to the encrypted data. Additionally, the secret involved in the data encryption is treated as the secret of the access policy, ensuring access pattern privacy protection.
- Formal security analysis proves that EPTA-T ensures the confidentiality of data and queries under an Indistinguishability under Selective Chosen-Plaintext Attacks (IND-SCPA) model. The experimental results over a real-world dataset indicated that the running time of EPTA-T outperformed the state-of-the-art scheme in terms of index encryption, trapdoor generation, and task allocation.
The remainder of this paper is organized as follows. Section 2 presents an overview of related works on privacy-preserving task-allocation schemes. In Section 3, we outline the system model, threat model, design goals, and problem definition of EPTA-T. In Section 4, we provide the necessary background knowledge. Then, in Section 5, we present the detailed construction and technical aspects of the proposed scheme. In Section 6, we prove the security of the proposed scheme. In Section 7, we evaluate and analyze the performance of EPTA-T via experiments. Finally, we conclude our work in Section 8.
2. Related Work
In this section, we mainly focus on the related works on secure task allocation for mobile crowdsensing, including privacy-preserving task allocation and privacy-preserving range query.
2.1. Privacy-Preserving Task Allocation
Currently, privacy-preserving task allocation has received great attention in academia and industry [1,2,4,17,18]. To address the problem of privacy preservation in task allocation, Song et al. [1] proposed an efficient and privacy-preserving task-recommendation scheme by utilizing predicate encryption and randomizable matrix multiplication. Different from randomizable-matrix-based task allocation, Wang et al. [18] utilized a planar Laplace distribution to perturb tasks and workers’ locations to protect their location privacy. However, using perturbed locations for task allocation can lead to a decrease in the effectiveness of the task assignments. Thus, Xia et al. [19] presented a probabilistic method to quantify the accessibility between workers and requesters and reduced the effect of the perturbed location on task allocation. To achieve task privacy protection, Zhou et al. [20] designed a tree-based privacy-preserving task-allocation system that addresses the task-allocation problem based on the combinatorial multi-armed slot machine problem. To the balance of user privacy and the usability of task allocation, Wang et al. [18] employed differential privacy to protect location privacy and proposed a multi-task assignment scheme for perturbing the available location information. Xu et al. [21] proposed a privacy-preserving task-allocation scheme using inner-product-based encryption to protect the privacy of task information and workers’ locations. However, the schemes in [18,19,20,21] do not support temporal access control, i.e., deciding whether the requesters’ temporal attributes satisfy a designed time-based access policy.
In summary, how to design an efficient and privacy-preserving task-allocation scheme that supports temporal access control is a crucial issue that needs to be addressed in mobile crowdsensing.
2.2. Privacy-Preserving Range Query
Searchable Symmetric Encryption (SSE) [12,13,14,22,23,24] is an effective cryptographic method for secure range query. Based on SSE, Li et al. [25] proposed a tree-aid indistinguishable index structure, which can only support one-dimensional range query. To achieve multi-dimensional range query, several works [1,8] employed an asymmetric scalar-product-preserving encryption approach. For strong security in range query, homomorphic encryption [11,15,26,27,28,29] is applied to realize the direct operations over ciphertext, but the computational cost is heavy and unacceptable. Furthermore, Several schemes have explored the limitations and weaknesses of SSE, which significantly balances security and efficiency effectively. Moreover, Wang et al. [9,10] proposed SSE-based schemes for geometric range query, but these schemes have some limitations such as a single geometric query type, inefficient search performance, and a low-dimensional space. To address these issues, Wang et al. [30] proposed a DSSE-based spatial keyword query scheme for dynamic updates. It is worth noting that the above schemes failed to support accurate and efficient geometric range query and temporal access control.
In a word, how to design an efficient and privacy-preserving geometric range query scheme that achieves an arbitrary geometric range query with a fast search is a significant problem that needs to be solved in the spatial data query.
Compared with the existing works, our proposed EPTA-T has three strong aspects: (1) our EPTA-T scheme achieves efficient and privacy-preserving task allocation with temporal access control in mobile crowdsensing; (2) our EPTA-T scheme supports an efficient and privacy-preserving geometric range query with a fast search in a multi-user setting; (3) our EPTA-T scheme guarantees the confidentiality of the data and queries under the IND-SCPA model.
3. Problem Formulation
In this section, we introduce the system model, threat model, design goals, and problem definition of EPTA-T.
3.1. System Model
As shown in Figure 1, the architecture of our mobile crowdsensing system consists of four entities, i.e., a trusted authority (), a service provider (), multiple workers (s), and multiple data requesters (s).
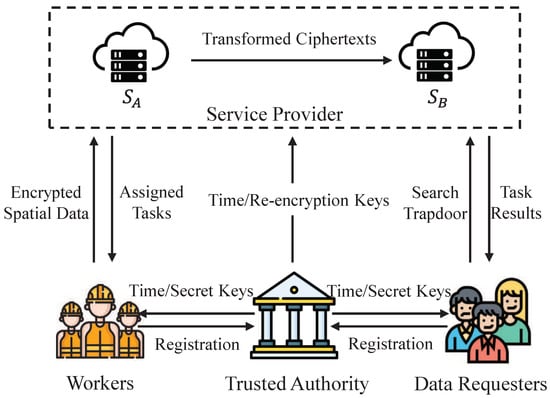
Figure 1.
System model.
- Trusted Authority (): The is responsible for initializing the system and distributing the secret keys. Initially, the sets up the system to provide registration services for both workers and data requesters and generates encryption keys and re-encryption keys for participating entities.
- Service Provider (): The is a crowdsourcing service provider that receives and stores the task content from data requesters. Additionally, the allocates the task requirements to suitable workers. In this model, two non-colluding cloud servers and are introduced to serve as the service provider.
- Workers (): Workers encrypt their locations and send the ciphertexts to the service provider. Based on the locations of the workers, the allocates the task requirements to the proper workers. After that, the workers accomplish the task and return the task results to the service provider.
- Data Requesters (): Before publishing the tasks, data requesters encrypt their task requirements. To find suitable workers who satisfy the query constraints, the generate search trapdoors for their task requirements and submit the search trapdoors along with the encrypted task content to the .
In our task allocation model, the encrypts his/her spatial data according to the designated access policies, constructs encrypted indexes for task allocation, and transmits both the encrypted spatial data and indexes to the . Prior to the releasing a task to the , the generates a search trapdoor based on the task requirements and submits it to the . Upon receiving the search trapdoor from the , the initially converts the ’s privileged time trapdoor into the trapdoor associated with the current time , but only if the falls within the ’s privileged time range. Subsequently, the employs EPTA and TAC for task allocation, concurrently verifying whether the ’s attributes satisfy the access policy and if the search trapdoor corresponds to the appropriate worker index. If these conditions are met, the dispatches the task requirements to the suitable worker. Following the reception of the task results from the selected worker, the returns the results to the .
3.2. Threat Model
In our task recommendation, the is fully trusted in the system, and all communications between the and other entities are secure. The and are considered to be fully trusted, which means they keep their private keys secret. They would not leak or sell their keys to the for profits. The is considered as semi-honest (i.e., honest-but-curious), which means the will honestly perform the designed protocols to provide the task recommendation services, but the may try to derive private information from encrypted locations and search trapdoors. Based on the information that may derive, we considered the following two attacks:
- Ciphertext-only attack: The observes a number of ciphertexts including encrypted locations, encrypted tasks, and search trapdoors, but the cannot obtain their corresponding plaintexts.
- Chosen-plaintext attack: Except knowing the encrypted locations and trapdoors, the can oracle access the task recommendation protocols to obtain some plaintext–ciphertext pairs.
Generally, we assumed that there is no collusion between two cloud servers. This assumption is reasonable, as cloud servers are expected to maintain their reputations and protect their own interests [8]. It is worth noting that the no-collusion assumption has been widely adopted in numerous research works within the security community, particularly in the context of the two-server model [8,15,31].
3.3. Design Goals
The design goals of EPTA-T are summarized as follows:
- Privacy protection: The privacy of workers and data requesters should be protected in our EPTA-T scheme. It is not difficult to see that, in task allocation applications that involve more sensitive user data such as workers’ locations, requesters’ queries, and task results, revealing these data can easily violate user privacy.
- Temporal access control: The EPTA-T scheme should achieve temporal access control for the time-series data (e.g., trajectory data, validity period, and hours of services) in task allocation.
- Efficiency: The computational overhead and communication overhead on the worker and publisher side should be minimized, since the mobile devices are resource-limited. The proposed EPTA-T scheme should achieve efficient data encryption and task allocation.
3.4. Problem Definition
In this paper, our objective was to achieve Efficient and Privacy-Preserving Task Allocation (EPTA) with Temporal Access Control (TAC) for handling massive spatial data comprising temporal and non-temporal attributes. Each spatial datum is encoded as spatial point with a private identity of the worker . The worker’s identity is encrypted using a secret key s under an access policy , which encompasses both temporal and non-temporal access attributes. Specifically, the spatial data can only be accessed within the valid time period defined by . Let IndexEnc be the index encryption algorithm executed by . Based on the IndexEnc algorithm, each spatial datum is encrypted as by using the ’s secret key , i.e., . Let be the index transformation algorithm executed by the . In the IndexTran algorithm, the utilizes the corresponding re-encryption keys and to transform the encrypted ciphertext, i.e., . Let TrapGen be the trapdoor-generation algorithm executed by . When the with an attribute set submits a geometric range of task requirements to the at the current time , the search trapdoor is generated for the geometric range by using the ’s secret key , i.e., . When the receives the search trapdoor from the , using the algorithm, the transforms the ’s privileged time trapdoor into the search trapdoor linked to the current time when the falls within the privileged time range of , i.e., . Upon receiving the transformed trapdoor , the performs the task allocation to search the proper workers who satisfy the access policy and the geometric range query condition simultaneously. Here, means the current time belongs to a valid time period of access policy and the access attribute set, and the ’s attributes satisfy the designed access policy , i.e., . Let be the temporal access control function; we have
where denotes the encrypted secret. Let be the efficient and privacy-preserving task allocation primitive function; we have
Based on the above problem statement, we give the definition of EPTA-T as follows.
Definition 1
(EPTA-T). For a worker with the spatial data encrypted under the access policy , the worker is considered as an accessible and suitable one for a who possesses an attribute set S and submits a geometric range of task requirements at the current time , if and only if both conditions and are met.
4. Preliminaries
In this section, we review some building blocks that are used in our proposed scheme, including Gray code [6], the access tree [22], and polynomial functions [4].
4.1. Gray Code
The process of converting a binary number into its corresponding binary reflected Gray code involves iterating from right to left. Starting with the rightmost digit , if the preceding digit is 1, we replace with . If is 0, we leave unchanged. We then proceed to the next digit and repeat the process until we reach the first digit , which remains the same as was assumed to be 0. The resulting sequence represents the binary reflected Gray code. To convert a binary reflected Gray code back to a binary number, we start with the n-th digit and compute the equation as follows:
If , replace by ; otherwise, leave it unchanged. Next, we compute
By applying the above calculation, we obtain that the binary number corresponds to the initial binary reflected Gray code.
Therefore, the Gray code for bits can be represented as
where || denotes the concatenation operator. For example, , . When using Gray code to encode a grid, the length of each binary code representing a cell is .
4.2. Access Tree
Consider a tree that represents an access policy. In this tree, each non-leaf node represents a threshold gate. The node is defined by its children and a threshold value. The threshold value of a node x is such that , where represents the number of children of node x. On the other hand, each leaf node x in represents an attribute , where the threshold value is set to 1.
Let denote the subtree of rooted at node x. If x is a non-leaf node, if and only if it contains at least children for which . In other words, is true if there are enough child nodes satisfying according to the threshold value .
If x is a leaf node, if and only if the attribute is present in the attribute set S. In other words, is true if the attribute is a member of S.
4.3. Polynomial Function
The polynomial function relates the coefficients of a polynomial to the sums and products of its roots. Let be a polynomial function of degree n, i.e., , where the coefficient of is , and . Based on the property of the polynomial function, we have
where are the roots of . According to the construction of the polynomial function , we can calculate any subproducts of the roots. For any , the -th coefficient is associated with a signed sum of all possible subproducts of the roots, as shown in Equation (5).
5. The Proposed Scheme
In this section, we first introduce the overview of EPTA-T. After that, we give the detailed construction of EPTA-T. In our EPTA-T, it mainly consists of seven algorithms: System Setup (SystSetup), Key Generation (KeyGen), Index Encryption (IndexEnc), Index Transformation (IndexTran), Trapdoor Generation (TrapGen), Trapdoor Transformation (TrapTran), and task allocation (Query). Finally, we analyzed the correctness of EPTA-T.
5.1. Overview
Since EPTA-T supports secure task allocation in multi-worker multi-requester settings without key sharing, the main idea of EPTA-T is to encode and encrypt the index of the spatial data and the search trapdoor of the task requirement into a matrix-trace-based matching operation, such that TAC can be implemented by the same encryption mechanism without involving additional computational overhead.
Transforming the geometric-range-based task allocation into the inner-product-based matching operation. To enable task allocation based on the geometric ranges of the task requirements, the space is divided into uniform cells with dimensions . The task allocation conditions, specifying the spatial data of workers located within the geometric range defined by the data requester, are encoded using Gray code, where 0 and 1 are represented by two positive integers, X and Y, respectively. Each spatial datum is encoded as spatial point by using Gray code and further expanded into a spatial vector by padding it with additional entries, including . The geometric query range is encoded as the aggregated query code , which represents the combination of the codes for the cells encompassed by the geometric range . Subsequently, the aggregated range query vector is generated by padding the query code with additional entries, including the sum of the squares of the code values. Specifically, the aggregated query code is generated by replacing the different entries with 0 to reduce the scale of codes in the query range. Consequently, if the inner product between the spatial vector and the query vector is 0 (i.e., ), this indicates that the spatial data of the worker are located within the geometric query range . Otherwise, if the inner product is non-zero, this signifies that the spatial data are located outside the query range.
As shown in Figure 2, we give an example of the encoding procedure and geometric range query. In Figure 2, the spatial space is uniformly split into cells. The spatial point is encoded as and further extended as spatial vector . In addition, the geometric query range (green domain) is encoded as and . After that, the corresponding query vectors are further extended as and , respectively. Therefore, the inner product between and is 0, which means that the spatial point is located in the geometric query range .
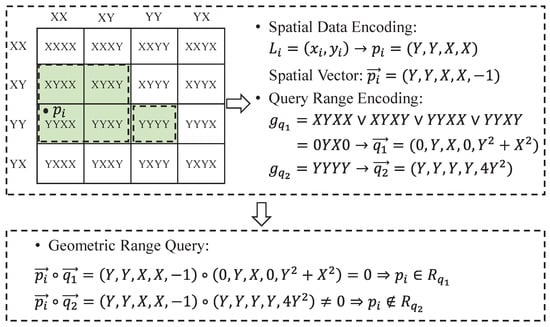
Figure 2.
An Encoding Example of Spatial Data and Query Range and Geometric Range Query.
Secure matrix-trace-based task allocation mechanism. In EPTA-T, we encrypt the spatial data as and transform them as by calling IndexEnc and IndexTran, respectively. In addition, we encrypt the geometric query range of task allocation as and transform it as by calling TrapGen and TrapTran, respectively. After that, we call the Query protocol to calculate the matrix trace (i.e., ) to retrieve proper workers for task allocation. If the worker is the proper one, his/her spatial data are located in the geometric range of the task requirement, i.e., , then .
Secure temporal access control. To achieve EPTA with TAC, the key idea is to perturb the search results of EPTA with the access policy by employing a secret used in IndexEnc as the secret of the access policy to encrypt the corresponding spatial data. To this end, privacy-preserving task allocation is correctly performed only when the spatial data are accessible.
To achieve temporal access control, we add time validity to a secret associated with the spatial data and correlate the encrypted secret with an access time period. Only when a data requester has attributes that satisfy the defined access policy and a secret that corresponds to the accessible time period can the data requester access the spatial data.
For TAC, we constructed a hierarchical temporal access tree and utilized its leaf nodes to denote different time attributes . In addition, when the can access the spatial data, the ’s privileged time period should be satisfied. If the current time satisfies , we utilize the polynomial function property to transform the time-related derivation function associated with and into the original function related to . If , we calculate the original function as shown in Equation (6).
where a represents a unique entry used to differentiate between different data requesters () selected by the , x is a leaf node of the hierarchical temporal access tree, and is the secret share of s for the leaf node x. The entry s is regarded as the secret of the hierarchical temporal access tree ’s root node, which is used to encrypt the private identity of the worker . When the ’s attributes satisfy the defined access policy at the current time , we have .
In our EPTA-T, should first execute TAC by checking whether the ’s attributes satisfy the defined access policy tree at the current time . If the calculates that holds, this indicates that the can access the spatial data. After that, the performs EPTA to calculate . If holds, the accessible spatial data satisfy the geometric query range, and the selects the worker identity as the proper worker and sends the task to this target one.
Remark 1.
To the best of our knowledge, EPTA-T is the first work to support fine-grained and temporal access control in privacy-preserving task allocation, which achieves efficient geometric range query and IND-SCPA security in the multi-worker multi-requester setting without key sharing.
5.2. The Detailed Construction of EPTA-T
Based on the above overview, we describe the detailed construction of EPTA-T:
- (1)
- SystSetup . Given a security parameter , the generates the master key , which consists of two random invertible matrices , a hash function , which hashes any spatial vector and query vector to positive values in and converts the attribute string to a group element, respectively, a random symmetric key K, and a random permutation . In addition, generates a composite order bilinear system of order and generators , . Additionally, the randomly selects an entry and calculates . Namely, the masker secret key can be denoted as , and the public parameters are generated as .
- (2)
- KeyGen . For a worker , the first chooses two random matrices . Then, computes and . For a data requester , the randomly selects two , and then, the computes and . Finally, the sends the secret key to the worker and the secret key to the data requester , and the distributes the re-encryption key to and the re-encryption key to . To distinguish different s, the chooses a unique element for a certain ’s attribute set S.
- (3)
- IndexEnc . Given a worker ’s spatial data , encrypts his/her spatial data and outsources it to as follows:
Step 1: Firstly, the encodes the spatial data as a spatial vector , where is a value of X or Y, and .
Step 2: For the spatial vector , the transforms to a positive integer . After that, the workers have a collection of integers, i.e., , where m denotes the number of workers in the mobile crowdsensing system.
Step 3: To protect the privacy of the transformative integer , the maps the integer with the one-way hash function h and obtains the hash value . Then, the calculates different powers for the hash value to generate an -dimensional vector .
Step 4: Next, the generates a one-time random positive number and embeds it into the vector . That is, the obtains the random vector .
Step 5: After that, the permutes the random vector to another vector by using the permutation , i.e., . Then, the transforms the permuted vector to a corresponding diagonal matrix with the diagonal being .
Step 6: Finally, the generates a random upper triangular matrix , where the main diagonal entries are 1, and the remainder of the non-zero entries are one-time random values. Then, the uses his/her secret key to encrypt as shown in Equation (7). After this operation, the sends the encrypted location to .
Specifically, to protect identity privacy, the worker encrypts the identity as via the standard encryption algorithm (e.g., AES) and encrypts the hierarchical temporal access tree as follows:
- Firstly, the worker selects the entry s as the secret of the root node of the hierarchical temporal access tree .
- Then, the worker calculates the secret shares of s for each leaf node x as .
- Finally, for each leaf node x, if x is represented as a temporal attribute , the splits into , which should guarantee that holds. Thus, encrypts the leaf node x as ; otherwise, encrypts it as .
To achieve secure task allocation, outsources the ciphertexts to .
- (4)
- IndexTran . Upon receiving the encrypted index , uses the corresponding re-encryption key to re-encrypt as shown in Equation (8).
Then, sends to . After receiving converted ciphertext , re-encrypts it with the re-encryption key as shown in Equation (9).
Finally, stores the converted ciphertext , the encrypted identity , and the encrypted access tree :
- (5)
- TrapGen . The data requester designated the geometric range of the task requirement as , where denote left-lower, left-upper, right-lower, and right-upper of the geometric range bound, respectively. Then, the encodes geometric query range into the query vector based on the Gray code. After that, the data requester performs the following operations to generate the search trapdoor:
Step 1: Firstly, encodes the geometric range of the task requirement to query vector as shown in Equation (10) by using the Gray code method.
where is one of X, Y, or 0 and .
Step 2: Secondly, to protect the privacy of the query vector, the transforms the query vector into an n-dimensional vector by using the same transformation as mentioned in IndexEnc, where each entry is a positive integer value.
Step 3: After that, the hashes the integer vector as shown in Equation (11) by using the hash function h.
Step 4: To further protect the privacy of the mapping-based task requirement, the constructs a polynomial function of the task requirement with the degree being n, as shown in Equation (12).
Step 5: Subsequently, the extracts the coefficients of the task function to construct the coefficient vector as . Then, the embeds a one-time random positive number into the coefficient vector Q and generates the random vector .
Step 6: Next, the permutes the random vector as , and then, the transforms into the corresponding diagonal matrix with the diagonal being .
Step 7: Finally, the generates a random upper triangular matrix with the main diagonal being and encrypts the diagonal matrix by using the secret key and the as shown in Equation (13). After that, the sends the encrypted task and search trapdoor to , where denotes symmetric encryption (e.g., AES), and is the plaintext of ’s task.
- (6)
- TrapTran . Upon receiving the search trapdoor , utilizes the corresponding re-encryption key to re-encrypt , as shown in Equation (14).
After that, sends to . Subsequently, finds the requester ’s re-encryption key and re-encrypts to as shown in Equation (15).
- (7)
- Query . Upon receiving the search trapdoor , for each encrypted object , first checks whether the ’s attribute set S satisfies the defined access policy based on Definition 1. If not, outputs ⊥; otherwise, executes the following Query procedure for task allocation.
Step 1: For each leaf node x in hierarchical temporal access tree , if , outputs ⊥. If and , utilizes the ciphertext and time-related derivation function to calculate ; otherwise, outputs . By doing this, we have in the root node of the temporal access tree.
Step 2: Then, checks whether the worker is a suitable one via the corresponding matrix trace between the ’s index and ’s search trapdoor , which is equivalent to checking whether the inner product of spatial vector and query vector is equal to 0. By doing this, can determine whether the spatial data of the are located in the geometric query range of the task requirement by calculating the trace as shown in Equation (16).
If holds, the worker ’s spatial data are located in the geometric query range of the task requirement. Thus, holds, which means the is an accessible and proper worker at the current time and adds to the search result . Otherwise, chooses another re-encrypted spatial datum and performs the above secure task allocation procedure until all encrypted spatial data are searched.
5.3. Correctness Analysis
From linear algebra, we have the following theorem about the correctness of EPTA-T.
Theorem 1
(Correctness of EPTA-T). In EPTA-T, EPTA-T.Query is correct if and only if both and are satisfied.
Proof.
To demonstrate the correctness of EPTA-T, we should prove that both the data requester ’s attribute set S satisfies the temporal access policy at the current time and the worker ’s location is located in the geometric range of the task requirement when are satisfied.
Based on Equations (17) and (18), we can calculate that . Similarly, for the non-leaf node x in , we also can calculate in a recursive way. To this end, we have , which means the ’s attribute set S satisfies the defined access policy at the current time . Therefore, the correctness of TAC is demonstrated.
For the EPTA constraint, note that . According to the similarity transformation in linear algebra, we have . Since and are upper triangular matrices with the main diagonals being , both and are upper triangular matrices with the main diagonals being and . Additionally, by using the same permutation , and are permuted to and , respectively. Therefore, we have
where denotes the inner product between and . In Equation (19), since both and are two one-time positive values, if holds, the equation is satisfied, which means the hash value is the root of the polynomial function constructed by the requester . Since and are derived from the spatial vector and , we have . That is, the ’s spatial data are located in the geometric query range of the task requirement, i.e., . Therefore, the correctness of EPTA-T is demonstrated. □
Discussion: Our EPTA-T achieves secure task allocation and temporal access control simultaneously. By using randomizable matrix multiplication, EPTA-T can resist the IND-SCPA in multi-user setting. In addition, EPTA-T supports temporal access control by leveraging function differentiation and integration, along with CP-ABE, to regulate access to tasks over time. Our EPTA-T considers the locations of the workers, which is not sufficient for accurate task allocation. In practical task allocation scenarios, workers’ keywords are also significant for task matching. To provide a detailed discussion on the advantages and challenges of EPTA-T, we discuss both the functionality and efficiency of EPTA-T as follows:
- Functionality: Our EPTA-T scheme can support task allocation in multi-user settings without key sharing. This is made possible by leveraging proxy re-encryption, which allows the transformation of ciphertexts from an asymmetric key environment to re-encrypted ciphertexts in a symmetric key setting. As a result, even when workers and requesters employ different keys, secure task allocation can still be achieved by utilizing different types of ciphertexts.
- Efficiency: Our EPTA-T scheme provides significant reductions in computational overhead for both the data encryption and task allocation processes. By utilizing randomizable matrix multiplication and matrix decomposition techniques, our EPTA-T scheme avoids heavy cryptographic operations such as fully homomorphic encryption, Paillier encryption, exponential operations, and secure circuits. This design choice leads to a notable improvement in the performance of data encryption and task allocation, as the computational burden is reduced.
6. Security Analysis
Since CPA is stronger than COA, if EPTA-T can resist CPA, it logically follows that it can also provide resistance against COA. Therefore, in this section, we mainly analyzed how EPTA-T can protect the confidentiality of spatial data, workers’ identity, the geometric query of the task requirements, and the task results under an Indistinguishability under Selective Chosen-Plaintext Attacks (IND-SCPA) model. Before demonstrating the security of EPTA-T under the IND-SCPA model, we give the definitions of the secure simulation-based experiment between a computationally bounded adversary and a challenger as follows.
Definition 2
(IND-SCPA data privacy of EPTA-T). Let ∏ be a privacy-preserving task-allocation scheme with temporal access control over a security parameter λ. A security game of data privacy between a challenger and an adversary is defined as follows:
- Initialization: Given a security parameter λ, generates two spatial databases , and , and sends them to .
- Setup: performs the Setup algorithm and the KeyGen algorithm to generate a master key, public parameter, secret key, and re-encryption key and sends the public parameter to
- Phase 1: adaptively submits several encrypted data and trapdoor requests, where each request is one of the following types:
- Encrypted data request: Upon the j-th encrypted data request, outputs a spatial dataset . responds with encrypted spatial data .
- Search trapdoor request: Upon the j-th search trapdoor request, generates a geometric range query and sends it to . After that, responds with a search trapdoor . Here, is subject to , where is a leakage function obtaining all the information leaked during the task allocation process:
- Challenge: With and selected from the initialization, flips a coin , executes IndexEnc to calculate the encrypted spatial data , and sends them to .
- Phase 2: runs Phase 1 again and adaptively selects several spatial data, then issues them to .
- Guess: outputs his/her guess of b. If holds, wins the security game; otherwise, fails.
∏ is secure against IND-SCPA on data privacy if, for any polynomial-time adversary in the above security game, has at most a negligible advantage as follows:
where is a negligible function.
Definition 3
(IND-SCPA query privacy of EPTA-T). Let ∏ be a privacy-preserving task-allocation scheme with temporal access control over a security parameter λ. A security game of query privacy between a challenger and an adversary is defined as follows:
- Initialization: submits two geometric range queries and with the same dimensional space to .
- Setup: runs the KeyGen algorithm to generate a secret key for trapdoor encryption.
- Phase 1: adaptively submits a series of requests to . After that, responds with encrypted spatial data and trapdoor. Each request is one of the following two types:
- Encrypted data request: Upon the j-th encrypted data request, outputs a spatial dataset . Then, responds with encrypted spatial data , where is subject to .
- Search trapdoor request: Upon the j-th trapdoor request, outputs a geometric query request . Then, responds with a search trapdoor :
- Challenge: With and selected in the initialization, flips a coin and calculates . After that, sends it back to .
- Phase 2: adaptively selects a series of trapdoor requests and sends them to , which are still subject to the same restrictions in Phase 1.
- Guess: outputs his/her guess of b. If holds, wins the security game; otherwise, fails.
∏ is secure against IND-SCPA regarding query privacy if, for any polynomial-time adversary in the above security game, has at most a negligible advantage:
6.1. Data Privacy and Identity Privacy
Theorem 2.
Our EPTA-T scheme guarantees IND-SCPA data privacy and identity privacy.
Proof.
To prove the IND-SCPA data privacy of EPTA-T, we should demonstrate that cannot distinguish the ciphertext and based on the security game defined in Definition 2, even though has oracle access to .
Considering that the ’s spatial data are firstly encoded as spatial vector by using Gray code, then transforms into a positive integer and obtains a hash value by using the hash function h. After that, the calculates an -dimensional vector based on the hash value . In addition, the permutes the random vector to with the random permutation . Following this, the permuted vector is transformed into a corresponding diagonal matrix . Finally, the spatial data are encrypted as . Since has no idea about the one-time random value , the random permutation , and the random triangular matrix , it is hard to recover the secret key . Additionally, can obtain several plaintext–ciphertext pairs, but it is difficult for to launch a linear analysis attack.
In Phase 1 and Phase 2 of Definition 2, can adaptively select different spatial data and obtain the corresponding ciphertexts . Unfortunately, both and are a one-time random vector and matrix determined by , and the ciphertexts are random according to . That is, for the given ciphertexts and selected by , cannot distinguish which spatial data are actually encrypted. Therefore, even though has oracle access to IndexEnc, it has a random guess of b with a negligible advantage:
For the identity privacy in EPTA-T, since the worker’s identity is encrypted as by using AES and the secret key of AES is kept private to , the identity privacy can be well protected. □
6.2. Query Privacy and Result Privacy
Theorem 3.
Our EPTA-T scheme guarantees IND-SCPA query privacy and result privacy.
Proof.
Based on Definition 3, to prove the query privacy, we should demonstrate that cannot obtain any sensitive information from the encrypted trapdoor , encrypted attribute set , and matrix trace . Similar to the operation in IndexEnc, can adaptively select different geometric query range and observe the corresponding trapdoor . However, both and are a one-time random vector and matrix determined by , and the encrypted trapdoor is random according to . Therefore, for the given trapdoors and selected by , even though has oracle access to TrapGen, only has a random guess of b for the geometric query range with a negligible advantage:
In addition, can obtain and for temporal access control and task allocation, respectively. However, the privacy of the temporal access tree can be well guaranteed by using Bilinear Diffie–Hellman Assumption (DBDH). Furthermore, the query result only reveals whether is equal to 0 or not, and no more sensitive information of the geometric query can be obtained by . Therefore, our EPTA-T scheme can well guarantee IND-SCPA query privacy and result privacy. □
7. Performance Evaluation
In this section, we provide a thorough experimental evaluation of the EPTA-T scheme. We first depict the configuration of the experimental environment and selection of parameters. Since our EPTA-T scheme is the first work to support fine-grained and temporal access control in privacy-preserving task allocation, we present the comparison of EPTA-T with Privacy-Preserving Boolean Range Query with Temporal Access Control (PBRQ-T) [6] in terms of the computational overhead on IndexEnc, TrapGen, and Query.
7.1. Implementation Settings
Experimental environment. We implemented our EPTA-T scheme and PBRQ-T with JAVA and utilized the JDK library to implement cryptographic primitives such as AES. We conducted experiments on a laptop with a 2.8 GHz, Intel Core i7, 16 GB RAM as and an Android phone with 8G RAM and Octa-core Processors as and . In order to precisely measure the computational cost of the , , and , all experiments were performed on the same devices. Furthermore, all the reported running times were the average of 100 experiments.
Dataset. We randomly selected 10,000 spatial data from the Yelp dataset (https://www.yelp.com/dataset (accessed on 19 May 2023)) as the test dataset, where each spatial datum included the spatial location and attributes. The number of attributes was 44 in the test dataset.
Parameter setting. To compare with PBRQ-T, all primes were set as 60 bits. In addition, we divided the space into cells; the dimension of the spatial vector was 100; the geometric query range was set as a square. In our experimental evaluation, we set the number of the ’s attributes and system attributes as 10, and we assumed that there was only one temporal attribute in the task allocation system.
We compared our EPTA-T scheme with the state-of-the-art PBRQ-T scheme [6]. Note that the PBRQ-T scheme does not support task recommendation in mobile crowdsensing systems. To test the cost domination of our EPTA-T over different database sizes m and dimension vectors n, we mainly evaluated the complexity of index encryption, index transformation, trapdoor generation, trapdoor transformation, and query between , , and , respectively.
7.2. Evaluation and Comparison
Performance evaluation of IndexEnc and IndexTran. The cost of IndexEnc was dominated by the database size m. As shown in Figure 3a, when the database size was 10,000, the index encryption time of EPTA-T was about 3 s, while that of PBRQ-T was more than 2500 s. The reason is that our EPTA-T scheme only executes randomizable matrix multiplication for data privacy protection, while PBRQ-T conducts bilinear mapping and exponentiation operations, which have a more-expensive computational cost than our scheme. Therefore, with the increase of the database’s size, EPTA-T can save more computational costs on the worker side. Since PBRQ-T does not involve the index transformation operation, we only evaluated our EPTA-T on IndexTran with varying vector dimensions (i.e., n). As shown in Figure 3b, we noticed that our proposed EPTA-T increased linearly with the variable vector dimension n. In addition, the IndexTran costs over different database sizes m were almost close in the lower-dimensional setting.
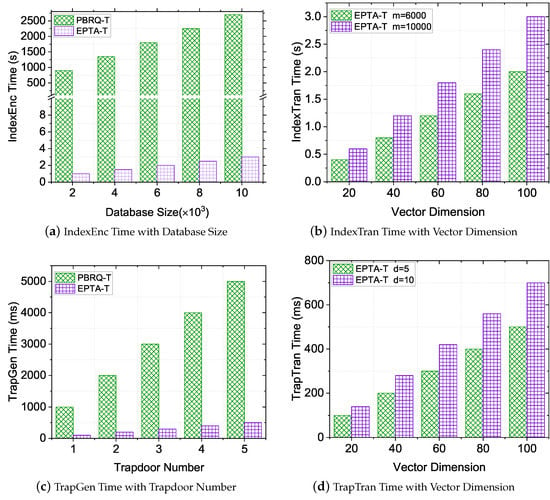
Figure 3.
Performance Evaluation of IndexEnc, IndexTran, TrapGen, and TrapTran.
Performance evaluation of TrapGen and TrapTran. From Figure 3c, we can notice that our EPTA-T had less computational cost for TrapGen and slightly increased with the variable number d of trapdoors, and it was at least faster than PBRQ-T. The underlying reason is that the number of trapdoors had little effect on the calculation of the matrix multiplication. As shown in Figure 3d, we can notice that the TrapTran computational cost of EPTA-T linearly grew with the variable n. Specifically, when the vector dimension achieved 100, the time cost of TrapTran was only 0.7 s, even though the submitted 10 geometric queries at one time.
Performance evaluation of Query. To comprehensively evaluate the query cost, we ran the experiments on the database with different sizes and vectors with different dimensions. As shown in Figure 4, the query overhead was scarcely influenced by the database size and the vector dimension. From Figure 4a, we can notice that the query time of both EPTA-T and PBRQ-T increased linearly with m, and the query performance of EPTA-T outperformed that of PBRQ-T. The query time of EPTA-T was about faster than that of PBRQ-T, which indicates that the calculation operations of matrix trace and functional integration were more efficient than those of exponent arithmetic and bilinear mapping. From Figure 4b, we can notice that a higher vector dimension had a greater query time cost with EPTA-T. The underlying logic is that the increase of the vector dimension d caused the number of matrix dimensions to grow and the computational cost of the matrix-trace-based operation to increase.
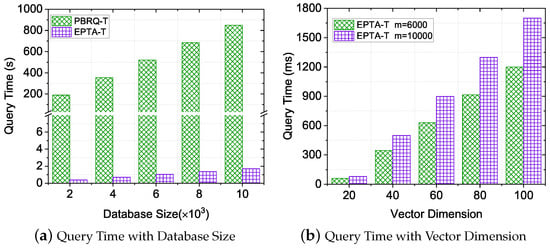
Figure 4.
Performance Evaluation of Query.
8. Conclusions
In this paper, we investigated and studied the problem of privacy-preserving task allocation with temporal access control for mobile crowdsensing. Specifically, we proposed an Efficient and Privacy-Preserving Task Allocation with Temporal Access Control (EPTA-T) scheme that efficiently achieved secure task allocation in multi-user settings by using Gray code and randomizable matrix multiplication. Moreover, EPTA-T incorporates temporal access control by leveraging function differentiation and integration, along with CP-ABE, to regulate access to tasks over time. Furthermore, formal security analysis and experimental evaluations demonstrated that EPTA-T protects data privacy and query privacy and achieves efficient task allocation compared with the state-of-the-art scheme. Regarding open problems, privacy-preserving spatial-keyword-based task allocation is still a challenging issue that needs to be resolved. For future work, we will further consider additional constraints in privacy-preserving task allocation, such as workers’ interests and incentives.
Author Contributions
Conceptualization, F.S. and Y.L.; methodology, F.S.; software, F.S. and S.M.; validation, F.S., Y.L. and Q.J.; writing—original draft preparation, F.S. and Y.L.; writing—review and editing, Q.J., X.Z. and Z.F. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Defense Industrial Technology Development Program (No. JCKY2021602B002), the National Natural Science Foundation of China (Nos. U20A20174, U22B2062, 62202051, 62202234, and 42001247), the National Key R&D Projects (No. 2021YFB00900 and No. 2018YFB0704000), and the China Postdoctoral Science Foundation (No. 2021M700435 and No. 2021TQ0042).
Data Availability Statement
The data presented in this study are available upon request from the corresponding authors. The data are not publicly available due to the privacy requirements of the project.
Conflicts of Interest
The authors declare no conflict of interest. The funders had no role in the design of the study; in the collection, analyses, or interpretation of the data; in the writing of the manuscript; nor in the decision to publish the results.
References
- Song, F.; Qin, Z.; Liu, D.; Zhang, J.; Lin, X.; Shen, X. Privacy-preserving task matching with threshold similarity search via vehicular crowdsourcing. IEEE Trans. Veh. Technol. 2021, 70, 7161–7175. [Google Scholar] [CrossRef]
- Ni, J.; Zhang, K.; Xia, Q.; Lin, X.; Shen, X. Enabling strong privacy preservation and accurate task allocation for mobile crowdsensing. IEEE Trans. Mob. Comput. 2019, 19, 1317–1331. [Google Scholar] [CrossRef]
- Liang, J.; Qin, Z.; Xiao, S.; Ou, L.; Lin, X. Efficient and secure decision tree classification for cloud-assisted online diagnosis services. IEEE Trans. Dependable Secur. Comput. 2019, 18, 1632–1644. [Google Scholar] [CrossRef]
- Shu, J.; Jia, X.; Yang, K.; Wang, H. Privacy-preserving task recommendation services for crowdsourcing. IEEE Trans. Serv. Comput. 2018, 14, 235–247. [Google Scholar] [CrossRef]
- Zhu, Y.; Hu, H.; Ahn, G.J.; Huang, D.; Wang, S. Towards temporal access control in cloud computing. In Proceedings of the INFOCOM, Orlando, FL, USA, 25–30 March 2012; pp. 2576–2580. [Google Scholar]
- Tong, Q.; Li, X.; Miao, Y.; Liu, X.; Weng, J.; Deng, R.H. Privacy-preserving Boolean range query with temporal access control in mobile computing. IEEE Trans. Knowl. Data Eng. 2022, 35, 5159–5172. [Google Scholar] [CrossRef]
- Deng, H.; Qin, Z.; Wu, Q.; Deng, R.H.; Guan, Z.; Hu, Y.; Li, F. Achieving fine-grained data sharing for hierarchical organizations in clouds. IEEE Trans. Dependable Secur. Comput. 2022, 20, 1364–1377. [Google Scholar] [CrossRef]
- Zhang, C.; Zhu, L.; Xu, C.; Ni, J.; Huang, C.; Shen, X. Location privacy-preserving task recommendation with geometric range query in mobile crowdsensing. IEEE Trans. Mob. Comput. 2021, 21, 4410–4425. [Google Scholar] [CrossRef]
- Wang, B.; Li, M.; Wang, H. Geometric range search on encrypted spatial data. IEEE Trans. Inf. Forensics Secur. 2015, 11, 704–719. [Google Scholar] [CrossRef]
- Wang, B.; Li, M.; Xiong, L. FastGeo: Efficient geometric range queries on encrypted spatial data. IEEE Trans. Dependable Secur. Comput. 2017, 16, 245–258. [Google Scholar] [CrossRef]
- Zhang, S.; Ray, S.; Lu, R.; Guan, Y.; Zheng, Y.; Shao, J. Efficient and Privacy-Preserving Spatial Keyword Similarity Query over Encrypted Data. IEEE Trans. Dependable Secur. Comput. 2022; early access. [Google Scholar] [CrossRef]
- Song, F.; Qin, Z.; Xue, L.; Zhang, J.; Lin, X.; Shen, X. Privacy-preserving keyword similarity search over encrypted spatial data in cloud computing. IEEE Internet Things J. 2021, 9, 6184–6198. [Google Scholar] [CrossRef]
- Liang, J.; Qin, Z.; Ni, J.; Lin, X.; Shen, X. Practical and secure SVM classification for cloud-based remote clinical decision services. IEEE Trans. Comput. 2020, 70, 1612–1625. [Google Scholar] [CrossRef]
- Song, F.; Qin, Z.; Zhang, J.; Liu, D.; Liang, J.; Shen, X. Efficient and privacy-preserving outsourced image retrieval in public clouds. In Proceedings of the GLOBECOM, Taipei, Taiwan, 7–11 December 2020; pp. 1–6. [Google Scholar]
- Zheng, Y.; Lu, R.; Zhang, S.; Guan, Y.; Wang, F.; Shao, J.; Zhu, H. PRkNN: Efficient and Privacy-Preserving Reverse kNN Query Over Encrypted Data. IEEE Trans. Dependable Secur. Comput. 2022; early access. [Google Scholar] [CrossRef]
- Zhang, S.; Ray, S.; Lu, R.; Guan, Y.; Zheng, Y.; Shao, J. Toward Privacy-Preserving Aggregate Reverse Skyline Query with Strong Security. IEEE Trans. Inf. Forensics Secur. 2022, 17, 2538–2552. [Google Scholar] [CrossRef]
- Zhang, C.; Hu, C.; Wu, T.; Zhu, L.; Liu, X. Achieving Efficient and Privacy-Preserving Neural Network Training and Prediction in Cloud Environments. IEEE Trans. Dependable Secur. Comput. 2022; early access. [Google Scholar] [CrossRef]
- Wang, H.; Wang, E.; Yang, Y.; Wu, J.; Dressler, F. Privacy-Preserving online task assignment in spatial crowdsourcing: A graph-based approach. In Proceedings of the INFOCOM, Virtual Conference, 2–5 May 2022; pp. 570–579. [Google Scholar]
- Xia, Y.; Zhao, B.; Tang, S.; Wu, H.T. Repot: Real-time and privacy-preserving online task assignment for mobile crowdsensing. Trans. Emerg. Telecommun. Technol. 2021, 32, e4035. [Google Scholar] [CrossRef]
- Zhou, P.; Chen, W.; Ji, S.; Jiang, H.; Yu, L.; Wu, D. Privacy-preserving online task allocation in edge-computing-enabled massive crowdsensing. IEEE Internet Things J. 2019, 6, 7773–7787. [Google Scholar] [CrossRef]
- Xu, Z.; Wu, L.; Qin, C.; Li, S.; Zhang, S.; Lu, R. PPTA: Privacy-Preserving Task Assignment Based on Inner Product Functional Encryption in SAM. IEEE Internet Things J. 2022, 10, 254–267. [Google Scholar] [CrossRef]
- Xue, L.; Liu, D.; Huang, C.; Shen, X.; Zhuang, W.; Sun, R.; Ying, B. Blockchain-Based Data Sharing with Key Update for Future Networks. IEEE J. Sel. Areas Commun. 2022, 40, 3437–3451. [Google Scholar] [CrossRef]
- Huang, C.; Liu, D.; Yang, A.; Lu, R.; Shen, X. Multi-client secure and efficient dpf-based keyword search for cloud storage. IEEE Trans. Dependable Secur. Comput. 2023; early access. [Google Scholar] [CrossRef]
- Song, F.; Qin, Z.; Liang, J.; Lin, X. An efficient and privacy-preserving multi-user multi-keyword search scheme without key sharing. In Proceedings of the ICC, Montreal, QC, Canada, 14–23 June 2021; pp. 1–6. [Google Scholar]
- Li, R.; Liu, A.X.; Wang, A.L.; Bruhadeshwar, B. Fast and scalable range query processing with strong privacy protection for cloud computing. IEEE/ACM Trans. Netw. 2015, 24, 2305–2318. [Google Scholar] [CrossRef]
- Liu, D.; Wu, H.; Huang, C.; Ni, J.; Shen, X. Blockchain-based credential management for anonymous authentication in sagvn. IEEE J. Sel. Areas Commun. 2022, 40, 3104–3116. [Google Scholar] [CrossRef]
- Li, S.; Zhang, Y.; Xu, C.; Cheng, N.; Liu, Z.; Du, Y.; Shen, X. HealthFort: A Cloud-Based Ehealth System with Conditional Forward Transparency and Secure Provenance via Blockchain. IEEE Trans. Mob. Comput. 2022; early access. [Google Scholar] [CrossRef]
- Ren, H.; Li, H.; Liu, D.; Xu, G.; Shen, X. Enabling Secure and Versatile Packet Inspection with Probable Cause Privacy for Outsourced Middlebox. IEEE Trans. Cloud Comput. 2021, 10, 2580–2594. [Google Scholar] [CrossRef]
- Hu, C.; Zhang, C.; Lei, D.; Wu, T.; Liu, X.; Zhu, L. Achieving Privacy-Preserving and Verifiable Support Vector Machine Training in the Cloud. IEEE Trans. Inf. Forensics Secur. 2023; early access. [Google Scholar] [CrossRef]
- Wang, X.; Ma, J.; Liu, X.; Miao, Y.; Liu, Y.; Deng, R.H. Forward/backward and Content Private DSSE for Spatial Keyword Queries. IEEE Trans. Dependable Secur. Comput. 2022; early access. [Google Scholar] [CrossRef]
- Chen, D.; Zhang, N.; Cheng, N.; Zhang, K.; Qin, Z.; Shen, X. Physical layer based message authentication with secure channel codes. IEEE Trans. Dependable Secur. Comput. 2018, 17, 1079–1093. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).