Abstract
In this letter, we study turbo product codes with quadratic residue codes (called QR-TPCs) as the component codes. We propose an efficient decoder based on Chase-II algorithm with two convergence conditions for the iterative decoding of QR-TPCs. For each row and column, the Chase-II decoder will stop immediately when one of the conditions is met. The simulation results show that the proposed algorithm has a lower computational complexity compared with existing decoding methods. Moreover, a comparison with 5G low-density parity-check codes shows that the proposed turbo product codes have better performance for short code lengths.
1. Introduction
Combining the ideas of product codes [1] and turbo codes [2], a new iterative decoding algorithm for product codes was proposed by Pyndiah [3,4]. Since this concept is very similar to the iterative decoding of turbo codes built on convolutional component codes, it is known as block turbo code (BTC) and turbo product code (TPC). With its good error correction capability, which is close to the Shannon limit, TPC has great research value and application potential.
(Extended) Bose-Chaudhuri-Hocquenghem (BCH) codes, (extended) Hamming codes and Reed-Solomon (RS) codes are the common types of linear block codes selected as the component codes of TPCs. In this letter, we choose quadratic residue (QR) codes [5] as the component code. As one class of BCH codes, QR codes do not have an error floor at high signal-to-noise ratio (SNR) and most of the known QR codes usually have large minimum distances with code rates greater than or equal to 1/2 so that the code rates of TPCs with QR component codes are around 1/4. Since QR codes usually have larger minimum distances than traditional BCH codes with approximately equal code lengths, they are typically highly prospected in the fields of error correction for reliable data transmission over communication channels with noise. Considering the complexity, the QR codes of lengths less than 100 may have more considerable application potential, especially for short packet transmission with low latency. Take the case of the (24, 12, 8) extended QR code: it has been used in high frequency radio systems [6].
In general, the decoding of TPCs is based on several soft-input/soft-output (SISO) decoders. The iterative operation of the algorithm results in increased computational complexity. In order to reduce the calculation time without noticeable performance loss many efficient decoding algorithms have been investigated to date. In [7], an efficient Chase decoder used for TPC decoding was proposed for one-error-correcting extended BCH codes with substantial complexity reduction and no performance degradation. In [8], Al-Dweik et al. proposed a novel hybrid decoder, which is composed of a standard SISO decoder with a small number of iterations followed by a hard-input/hard-output (HIHO) decoder. In [9], Lu et al. further modified the hybrid decoder developed in [8] and derived a simple formula for estimating the extrinsic information. Simulations showed that the proposed hybrid decoder gained almost the same error correction performance compared to the algorithm in [8] with complexity reduction. However, the hybrid decoders in [8,9] always required a predetermined number of SISO and HIHO modes and did not take into account that the number of error bits would vary according to the SNR or the number of iterations throughout the decoding process. To overcome this deficiency, in [10], Ahn et al. presented a low complexity syndrome-based decoding algorithm based on the syndrome characteristics of extended Hamming codes. When a single error was detected, the decoder was possible to determine the codeword by using only a single hard decision decoding (HDD) operation. Nevertheless, the SISO decoders had to be used if a double-error syndrome was identified. In [11], Yoon et al. proposed an advanced syndrome-based decoder for TPCs with extended Hamming codes as the component codes and introduced an early termination technique. The advanced syndrome-based decoder applied a HDD operation in the proposed hard-input/soft-output (HISO) conditionally for a double-error syndrome, which reduced the overall complexity but remained slight decoding performance gaps in comparison with that of conventional methods. In addition, a number of test sequences that might result in the same codewords or decoding failures had been avoided in [12], and the computation of the extrinsic information was optimized when there was no competing codeword. In [13], Wang et al. introduced a low-complexity decoder based on the Fast Chase algorithm with a new method of calculating the extrinsic information using only two candidate codewords. And in [14], the authors further introduced a high-speed TPC decoder based on the algorithm in [13] with a fully parallel SISO module.
It is worth noting that the research on algorithms for TPC based on QR component codes is relatively small. Moreover, many of the previously studied algorithms cannot be directly used for the decoding of QR-TPCs. In [15], an iterative soft permutation decoding algorithm (ISPDA) used for QR-TPCs is proposed. Its key idea is to move the errors out of the information bits by permutations and then compute the extrinsic information according to the distance-based decoding (DBD) algorithm [16]. However, a large number of permutations need to be performed to obtain good error performance.
In order to tackle the high computational complexity of decoding QR-TPCs, in this letter, We present an efficient decoder for QR-TPCs with two terminating criteria [17,18] based on Chase-II algorithm [19]. Specifically, we apply this approach to decoding QR-TPCs and give a new way of evaluating the extrinsic information. The difference of syndromes (DS) algorithm [20] is employed for the HDD needed in the Chase-II algorithm, which can be utilized to decode any binary systematic QR code and is one of the most effective look-up table methods for decoding QR codes. Note that Duan et al. proposed an improved difference-of-syndromes (IDS) decoding algorithm [21] for decoding QR codes up to the minimum distance to speed up the computations. However, if the error-correction capability , the IDS algorithm is no longer necessary, as its computational complexity is higher than that of the DS algorithm. The proposed decoder avoids a number of unnecessary HDD operations and calculates the extrinsic information in an easy way. With a more efficient decoding process and an excellent error performance, QR-TPCs may have potential applications in modern communication systems for short-blocklength and high-reliability requirements.
The rest of this paper is organized as follow. Section 2 describes the background of QR codes, the sufficient optimality convergence conditions and TPCs. Section 3 provides a description of QR-TPC and the method of calculating the extrinsic information under different conditions. Section 4 presents the simulation results and complexity analysis. Finally, a brief summary is given in Section 5.
2. Background
2.1. Generator Polynomial of QR Codes
Let l be a positive integer and n be a prime number of the form . Denote Q as the set of quadratic residues modulo n, i.e.,
Let be the smallest positive integer such that n divides and be a generator of the multiplicative group consisting of all nonzero elements in GF(). Then the element is a primitive n-th root of unity in GF() where . The generator polynomial of a binary QR code [5] which has the code length n is given by
2.2. Decoding of QR Codes
We first consider the decoding of a single QR code. For a QR code, let be a transmitted codeword and be the corresponding transmitted binary phase-shift keying (BPSK) signal where . Assuming an additive white Gaussian noise (AWGN) channel with zero mean and variance , we denote the received signal by and the hard decoding vector of by where
Supposing is a codeword of the QR code, we define the set of indices where by and define the set of indices where by , i.e.,
Moreover, the correlation discrepancy between and is defined as
We arrange the elements in into a vector such that the corresponding magnitudes is increasing, i.e.,
with for where represents the cardinality of the set . We also denote the first elements of by , where for and for . Assuming the received signal is decoded by the Chase-II decoding algorithm, the following two theorems can be applied to find the maximum likelihood (ML) codeword.
Theorem 1.
Supposing is the first valid codeword found by the Chase-II decoder, we define and . If
then is the ML codeword corresponding to the received signal .
Proof of Theorem 1.
For detailed proof, see [17]. □
Theorem 2.
Let and be two valid codewords and the correlation discrepancy between and is smaller than that between and . Define , , , . Without loss of generality, assume , define (for , ) and . If
then is the ML codeword of .
Proof of Theorem 2.
For detailed proof, see [18]. □
The Chase-II algorithm with two terminating criteria can be summarized as Algorithm 1. Note that Theorem 1 applies only to the first valid codeword found by the Chase-II decoder while Theorem 2 is applicable whenever a valid codeword is found subsequently. If the first valid codeword satisfies Theorem 1, the Chase-II decoder will stop immediately and output the codeword. If not, the decoder will continue decoding and Theorem 2 will be considered whenever a valid codeword is found. The two theorems are applied to help determining the ML codeword, terminating the Chase-II decoder earlier and hence improving its convergence rate. The same ML codeword, however, will be decoded with or without the use of the two theorems.
| Algorithm 1: Chase-II algorithm with two terminating criteria |
 |
In the following section, we apply the aforementioned decoding algorithm in the iterative decoding of TPC codes formed by QR component codes.
2.3. 2-D TPC
We denote two systematic linear block codes by and , where , and denote, respectively, the code length, the information length and the minimum Hamming distance of the i-th code (). Using these two block codes as component codes, a 2-D TPC can be constructed as follows.
- 1.
- Place information bits in an array having rows and columns.
- 2.
- Encode the rows using Code .
- 3.
- Encode the columns using Code .
The structure of the 2-D TPC is shown in Figure 1 and the TPC can be represented by . Moreover, the 2-D TPC is characterized by and has a code rate of . Usually, the same block code is chosen as the component code, i.e., , so as to reduce the complexity of encoder and decoder. In the following, we assume , , and .
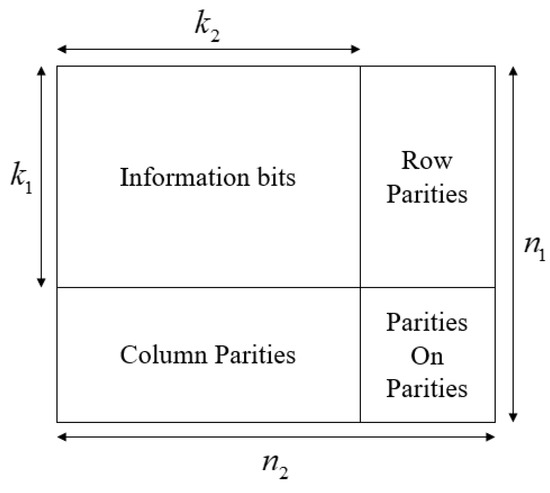
Figure 1.
A 2-D TPC consisting of rows and columns. The overall codeword is represented by .
From this point onwards, unless specified otherwise, we use the following notations. We represent a vector by a bold font small letter or symbol, e.g., and ; and its i-th element by the same small letter or symbol with subscript “i”, e.g., and . We represent a two dimensional array by a bold font capital letter, e.g., ; its i-th row (or j-column) by the same bold font capital letter with subscript “” (and “”), e.g., (and ); and its -th element by the same capital letter with subscript “”, e.g., .
2.4. Pyndiah-Chase-II Algorithm
One of the most common iterative decoding algorithms of TPC is the Pyndiah-Chase-II algorithm [4]. It operates in a SISO mode consisting of several half-iterations. A half-iteration in a row-wise manner and another one in a column-wise manner form one complete iteration. Figure 2 illustrates the operation of a half-iteration. Here, denotes the received signal vector corresponding to one particular (row-wise or column-wise) component code; m denotes the half-iteration number; denotes the extrinsic information vector generated at the m-th half-iteration with being a zero vector; and are predefined scaling factors; is the software information input to the Chase-II decoder; is an output codeword from the decoder having the minimum squared Euclidean distance to ; and is a set containing all other valid codewords found by the decoder. For example, the values of and for the 8 half-iterations in [4] are given by
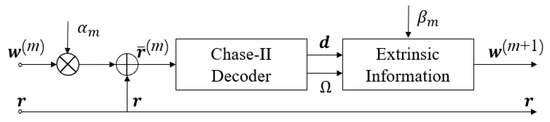
Figure 2.
Block diagram of a half-iteration decoder.
In fact, can be computed dynamically (see (20) in [4]).
In the m-th half-iteration, the i-th element of extrinsic information vector , i.e., , is calculated as follows.
- 1.
- If (i) is an empty set or (ii) all codewords in have their i-th elements the same as , i.e., , thenwhere .
- 2.
- If one or more codewords in have their i-th elements different from , i.e., , we compute the squared Euclidean distance between each of these codewords and . In other words, we compute where . Then we select the codeword that is closest to in terms of squared Euclidean distance. Subsequently, is calculated usingwhere .
3. Proposed QR-TPC and Decoders
3.1. Proposed Scaling Vector
We use the same QR code as the component codes in the 2-D TPC shown in Figure 1. We call the resultant TPC as QR-TPC and denote its codeword by . Assuming BPSK modulation is used and the transmitted signal is passed through an AWGN channel, we denote the received signal by an array in which each row/column corresponds to one QR code.
We first apply the Pyndiah-Chase-II algorithm described in Section 2.4 [4] to decode different QR-TPCs. We assume 8 half-iterations are performed. Moreover, the extrinsic information magnitudes that are derived using (13) have been recorded during the simulations. For each of QR-TPC, QR-TPC and QR-TPC, we plot the average value of that are derived using (13) in Figure 3. The average is plotted against the half-iteration number m for different values. Furthermore, for each half-iteration number m, we evaluate the mean of all the curves and denote this value by (see the thick blue curve in Figure 3). Finally, we obtain the vector
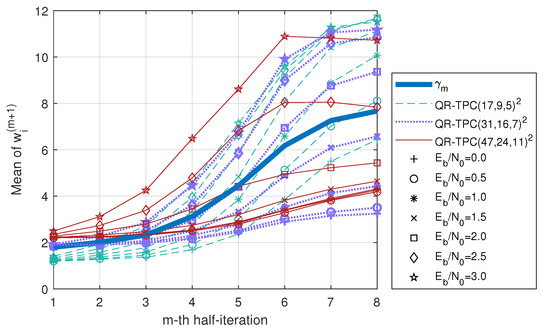
Figure 3.
Average extrinsic information magnitudes derived using (13) versus half-iteration number m. The thick blue curve shows the mean of the averaged values at each m.
3.2. Proposed QR-TPC Decoder
We propose modifying the Chase-II decoder in the Pyndiah-Chase-II algorithm to make the algorithm more efficient. Details of the proposed QR-TPC decoding algorithm with a modified Chase-II decoder are shown in Algorithm 2.
| Algorithm 2: Proposed QR-TPC Decoding Algorithm |
 |
In the modified Chase-II decoder, we apply both Theorems 1 and 2 (described in Section 2.2) as the terminating criteria to complete a half-iteration earlier. Depending on the theorem that has been satisfied, the extrinsic information is calculated as follows.
- 1.
- When Theorem 1 is satisfied, is the only output codeword from the decoder and is an empty set in Figure 2. One simple way to compute the extrinsic information is to apply (12) because is an empty set. However, as will be shown in Section 4, the error performance will be degraded quite significantly (particularly for short codes) compared with that of the original algorithm. We conjecture that the weights used in (12), i.e., ’s, are not large enough to correct the sign of an incorrect bit. Thus, we propose to use in (14) to replace in computing . In other words, when Theorem 1 is applied and is satisfied, we compute usingMoreover, we set a threshold half-iteration number , which defines the occasion that Theorem 1 starts being applied to the Chase-II decoder. The rationale of setting such a threshold is as follows. During the first few half-iterations, the inputs to the Chase-II decoder, i.e., , may not have very high reliabilities. Thus, the ML codeword output is not likely to be the transmitted component codeword. If we apply Theorem 1 and (15) to compute the extrinsic information now, the extrinsic information may not be accurate. But after a number of half-iterations, should become much more reliable and the ML codeword output is more likely to be the transmitted component codeword. Using Theorem 1 and (15) to compute the extrinsic information therefore becomes more accurate. Based on the above rationale, Theorem 1 will be applied when (refer to Line 12 to Line 14 of in Algorithm 2). Moreover, the first entries in will not be used in the Chase-II decoder when .
- 2.
4. Simulation Results
In this section, we consider the QR-TPC shown in Table 1. In our algorithm, all coded bits are modulated by BPSK and transmitted over the AWGN channel. The algorithm will stop when the decoder gathers 100 incorrect codewords. The number of least-reliable-bit (LRB) positions p is set to 4 for the QR-TPC, QR-TPC, QR-TPC and 5 for the QR-TPC. The DS algorithm [20] is employed for the HDD.

Table 1.
Parameters of QR-TPCs.
4.1. BER Performance Comparison
Figure 4 shows the bit error rate (BER) performance of the proposed algorithm. The number of half-iterations is set to 8, and the threshold is set to 1 and 4 separately. We plot three BER simulation results for each QR-TPC when the proposed algorithm is used. In the same figure, we also plot the BER simulation results when the algorithm in [4] (i.e., the one described in Section 2.4) is used. From the result of Figure 4, we can conclude the followings:
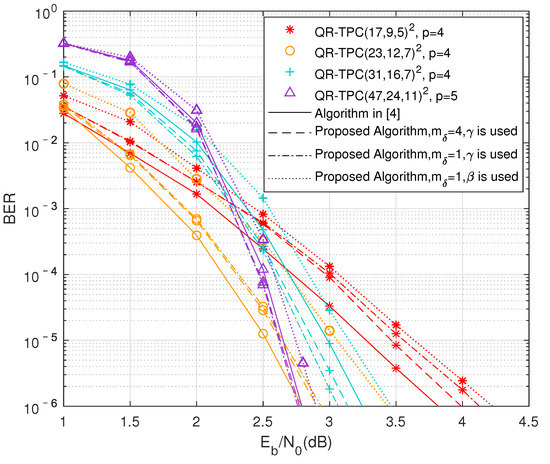
Figure 4.
BER performance of QR-TPCs under different decoder settings.
- Threshold : For certain QR-TPCs, the threshold provides a trade-off between BER performance and computational complexity. It can be seen that increasing from 1 to 4 can further improve the BER performance of our proposed algorithm for the QR-TPC.
- Overall BER performance: We can see that no significant BER deviation between the proposed algorithm and the algorithm in [4]. To be more specific, Figure 4 shows that there are slight BER performance gaps compared with that of the algorithm in [4] for the QR-TPC and QR-TPC. Nonetheless, the BER performance loss is tolerable. Furthermore, the proposed algorithm provides better performance with significant computational complexity reduction for the QR-TPC and QR-TPC. As a result, the proposed algorithm has a similar BER performance as the algorithm in [4].
- Comparison with other non-chase algorithm: When is larger than dB, the decoding performance of the proposed algorithm for the QR-TPC is similar to that reported in [15] (see the curve for 4 iterations in Figure 6 given in [15]).
4.2. Complexity Comparison
In Figure 5, we plot the average number of HDD operations required for decoding each QR-TPC codeword at different for our proposed algorithm and the algorithm in [4]. Since the algorithm in [4] will exhaust all the test patterns, the average number of HDD operations required is fixed for each QR-TPC code and equals . For our proposed algorithm, the modified Chase-II decoder will stop testing any remaining patterns when Theorem 1 or Theorem 2 is satisfied. As a result, the average number of HDD operations required is reduced when our proposed algorithm is used. Figure 5 also shows that:
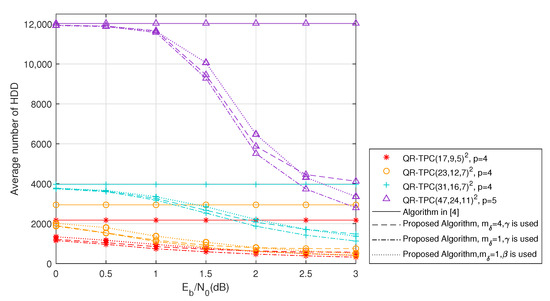
Figure 5.
Average number of HDD operations performed to decode one codeword.
- Proposed scaling vector: When , we can observe that our proposed algorithm can always avoid more HDD operations when using (15) instead of (12) to compute the extrinsic information. For instance, when dB, the average number of HDD operations for the QR-TPC, QR-TPC, QR-TPC and QR-TPC are reduced more by approximately , , and , respectively, using (15) instead of (12).
- Threshold : Using compared with using further reduces the average number of HDD operations because Theorems 1 and 2 are applied earlier (i.e., starting the first half-iteration) in the modified Chase-II decoder.
- The reduction in the average number of HDD operations increases as : In the low region, the number of error bits that occur in each codeword is more likely to exceed the error-correction capability t of the QR code. Thus a valid codeword that satisfies Theorem 1 or Theorem 2 cannot be found easily. As increases, the ML codeword can be obtained more readily found using Theorem 1 or Theorem 2 and hence the modified Chase-II decoder can terminate earlier. We take and dB as an example. For the QR-TPC, QR-TPC, QR-TPC and QR-TPC, the average numbers of HDD operations used in our proposed algorithm are reduced by , , and , respectively, compared with those used in the algorithm in [4]; when is increased to dB, the numbers of HDD operations are reduced by , , and , respectively.
The complexity of SISO QR-TPC decoders depends mainly on the number of operations of HDD. Generally, it takes GF(+), GF(≪) and R(+) for a QR code to run the DS algorithm once, where GF(+) and GF(≪) means the addition and shift operation in the Galois field, and R(+) means the addition operation in the real field. To calculate (8) and (9), the proposed algorithm also requires R(+). But it increases only a minimal computational complexity due to the small number of operations. It is worth pointing out that when Theorem 1 is satisfied, the proposed algorithm calculates the by (15) directly and therefore no longer needs to compute the squared Euclidean distance to . Thus it requires much fewer R(+) and the multiplication operations over the real field (i.e., R(*)).
The complexity comparison of our proposed algorithm and the algorithm in [15] is shown in Table 2, where L represents the average number of HDD operations shown in Figure 5 and P represents the number of the permutations used in [15]. The error performance of the algorithm in [15] depends on P and . In Table 2, when , dB, and , for the QR-TPC, we observe that the proposed algorithm has a much smaller number of GF(+), GF(≪) and R(*) performed to decode one codeword than the algorithm in [15]. In fact, our proposed algorithm may not require such a large number of GF(+), GF(≪), and R(+). In the best case, if the weight of the syndrome of the test pattern is smaller or equal to t, the DS algorithm can directly obtain the candidate codeword. For this reason, the DS algorithm requires only GF(+) and R(+) when decoding a QR code. This situation occurs especially in the high region.

Table 2.
Complexity comparison of the algorithms and relative number of the operations performed to decode one codeword.
In [22], the authors introduce an efficient decoding algorithm for TPCs based on Kaneko’s algorithm [23], which provides similar BER performance to the algorithm in [4]. It is interesting to note that Lemma 1 in Kaneko’s algorithm is identical to Theorem 1 when , where is an arbitrary codeword such that . Figure 2a given in [23] shows that Kaneko’s algorithm reduces the average number of HDD operations by about % compared to the conventional Chase-II algorithm when dB for QR () code. However, in the range under dB, Kaneko’s algorithm requires more complexity than that of the Chase-II decoder. To avoid this drawback, the maximum number of test patterns for each row and column in the algorithm in [22] is made equal to that of the Chase-II decoder. Figure 5 shows that our proposed algorithm can reduced by % HDD operations for QR-TPC in the same . Given that the procedure used for the extrinsic information calculations in [22] is the same as the algorithm in [4], our proposed algorithm uses fewer HDD operations and therefore provides lower computational complexity.
4.3. Comparison with 5G LPDC Codes
QR-TPCs have potential applications in modern communication systems for short-blocklength and high-reliability requirements. We compare the BER performance of QR-TPCs and 5G low-density parity-check (LDPC) codes [24] having similar code parameters. For these LDPC codes, we take the first rows and columns of base graph (BG) 2 as the base matrices (parameters are given in Table 3), and use the sum-product decoding algorithm with a maximum of 50 iterations. It is well known that LDPC codes perform better as codelength increases. As shown in Figure 6, when the codes are short, QR-TPCs have better performance than 5G LDPC codes. Specifically, QR-TPC achieves a dB gain over 5G LDPC (288, 80) at a BER of , and QR-TPC outperforms 5G LDPC (518, 140) by about dB. However, when the codelength becomes long, the 5G LDPC (962,260) outperforms QR-TPC by about dB at a BER of .

Table 3.
Parameters of 5G LDPC Codes.
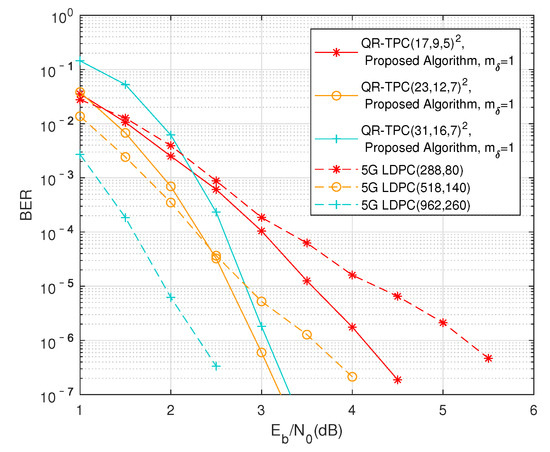
Figure 6.
Comparison of BER performance between QR-TPCs and 5G LDPC codes.
5. Conclusions
This letter presents an efficient decoding algorithm for TPCs with QR component codes. By introducing two convergence conditions and a new scaling vector , the proposed algorithm significantly improves the decoding efficiency with almost the same BER performance compared to the Pyndiah-Chase-II decoding algorithm and the ISPDA. Simulation results also reveal that QR-TPCs outperform 5G LDPC codes with similar parameters when the block lengths are below 500.
Author Contributions
All the authors contributed to various degrees to ensure the quality of this work (Conceptualization, Y.L.; methodology, J.D.; software, J.D.; validation, J.D. and Y.L.; formal analysis, J.D.; investigation, J.D. and R.L.; resources, Y.L., R.L. and T.G.; data curation, J.D.; writing—original draft preparation, J.D.; writing—review and editing, F.C.M.L.; visualization, J.D.; supervision, Y.L.; project administration, T.G.; funding acquisition, Y.L. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by China Natural Science Foundation (NSF) under Grant 61771081, the Fundamental Research Funds for the Central Universities (China) under Grant cstc2019jcyjmsxmX0110.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Elias, P. Error-free coding. Trans. IRE Prof. Group Inf. Theory 1954, 4, 29–37. [Google Scholar] [CrossRef]
- Berrou, C.; Glavieux, A. Near optimum error correcting coding and decoding: Turbo-codes. IEEE Trans. Commun. 1996, 44, 1261–1271. [Google Scholar] [CrossRef]
- Pyndiah, R.; Glavieux, A.; Picart, A.; Jacq, S. Near optimum decoding of product codes. In Proceedings of the 1994 IEEE GLOBECOM. Communications: The Global Bridge, San Francisco, CA, USA, 28 Novermber–2 December 1994; Volume 1, pp. 339–343. [Google Scholar] [CrossRef]
- Pyndiah, R. Near-optimum decoding of product codes: Block turbo codes. IEEE Trans. Commun. 1998, 46, 1003–1010. [Google Scholar] [CrossRef]
- Prange, E. Some Cyclic Error-Correcting Codes with Simple Decoding Algorithms; Technical Report TN-58-156; Air Force Cambridge Res. Center: Cambridge, MA, USA, 1958. [Google Scholar]
- Honary, B.; Hunt, B.; Maundrell, M. Improving automatic link establishment through a new soft decision trellis decoder for the (24,12) Golay code. In Proceedings of the Sixth International Conference on HF Radio Systems and Techniques, York, UK, 4–7 July 1994; pp. 182–185. [Google Scholar] [CrossRef]
- Argon, C.; McLaughlin, S.W. An efficient chase decoder for turbo product codes. IEEE Trans. Commun. 2004, 52, 896–898. [Google Scholar] [CrossRef]
- Al-Dweik, A.; Goff, S.; Sharif, B. A Hybrid Decoder for Block Turbo Codes. IEEE Trans. Commun. 2009, 57, 1229–1232. [Google Scholar] [CrossRef]
- Lu, P.; Lu, E.; Chen, T. An efficient hybrid decoder for block turbo codes. IEEE Commun. Lett. 2014, 18, 2077–2080. [Google Scholar] [CrossRef]
- Ahn, B.; Yoon, S.; Heo, J. Low Complexity Syndrome-Based Decoding Algorithm Applied to Block Turbo Codes. IEEE Access 2018, 6, 26693–26706. [Google Scholar] [CrossRef]
- Yoon, S.; Ahn, B.; Heo, J. An advanced low-complexity decoding algorithm for turbo product codes based on the syndrome. Eurasip J. Wirel. Commun. Netw. 2020, 2020, 1–31. [Google Scholar] [CrossRef]
- Son, J.; Kong, J.J.; Yang, K. Efficient decoding of block turbo codes. J. Commun. Netw. 2018, 20, 345–353. [Google Scholar] [CrossRef]
- Wang, Y.; Lin, J.; Wang, Z. A low-complexity decoder for turbo product codes based on extended hamming codes. In Proceedings of the 2018 IEEE 18th International Conference on Communication Technology (ICCT), Chongqing, China, 8–11 October 2018; pp. 99–103. [Google Scholar] [CrossRef]
- Kishore, J.H.; Yamuna, B.; Balasubramanian, K. Design of a Fast Chase Algorithm based High Speed Turbo Product Code Decoder. In Proceedings of the 2021 International Conference on Advances in Computing and Communications (ICACC), Kochi, India, 21–23 October 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Askali, M.; Ayoub, F.; Chana, I.; Belkasmi, M. Iterative soft permutation decoding of product codes. Comput. Inf. Sci. 2016, 9, 128–135. [Google Scholar] [CrossRef]
- Le, N.; Soleymani, A.R.; Shayan, Y.R. Distance-based-decoding of block turbo codes. IEEE Commun. Lett. 2005, 9, 1006–1008. [Google Scholar] [CrossRef]
- Taipale, D.J.; Pursley, M.B. An improvement to generalized-minimum-distance decoding. IEEE Trans. Inf. Theory 1991, 37, 167–172. [Google Scholar] [CrossRef]
- Wang, L.; Li, Y.; Truong, T.K.; Lin, T. On decoding of the (89, 45, 17) quadratic residue code. IEEE Trans. Commun. 2013, 61, 832–841. [Google Scholar] [CrossRef]
- Chase, D. A class of algorithms for decoding block codes with channel measurement information. IEEE Trans. Inf. Theory 1972, 18, 170–182. [Google Scholar] [CrossRef]
- Li, Y.; Duan, Y.; Chang, H.C.; Liu, H.; Truong, T.K. Using the difference of syndromes to decode quadratic residue codes. IEEE Trans. Inf. Theory 2018, 64, 5179–5190. [Google Scholar] [CrossRef]
- Duan, Y.; Li, Y. An Improved Decoding Algorithm to Decode Quadratic Residue Codes Based on the Difference of Syndromes. IEEE Trans. Inf. Theory 2020, 66, 5995–6000. [Google Scholar] [CrossRef]
- Dave, S.; Kim, J.; Kwatra, S.C. An efficient decoding algorithm for block turbo codes. IEEE Trans. Commun. 2001, 49, 41–46. [Google Scholar] [CrossRef]
- Kaneko, T.; Nishijima, T.; Inazumi, H.; Hirasawa, S. An efficient maximum-likelihood-decoding algorithm for linear block codes with algebraic decoder. IEEE Trans. Inf. Theory 1994, 40, 320–327. [Google Scholar] [CrossRef]
- Chairman, S. Chairman’s Notes of Agenda Item 7.1.5 Channel Coding and Modulation. In Proceedings of the TSG RAN WGI Meeting 87, R1-1613710, 3GPP Session Chairman (Nokia), Reno, Nevada, USA, 14–18 November 2016. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).