Abstract
The security of images has gained great interest in modern communication systems. This is due to the massive critical applications that are based on images. Medical imaging is at the top of these applications. However, the rising number of heterogenous attacks push toward the development of securing algorithms and methods for imaging systems. To this end, this work considers developing a novel authentication, intellectual property protection, ownership, and security technique for imaging systems, mainly for medical imaging. The developed algorithm includes two security modules for safeguarding various picture kinds. The first unit is accomplished by applying watermarking authentication in the frequency domain. The singular value decomposition (SVD) is performed for the host image’s discrete cosine transform (DCT) coefficients. The singular values (S) are divided into 64 × 64 non-overlapping blocks, followed by embedding the watermark in each block to be robust to any attack. The second unit is made up of two encryption layers to provide double-layer security to the watermarked image. The double random phase encryption (DRPE) and chaotic encryption have been tested and examined in the encryption unit. The suggested approach is resistant to common image processing attacks, including rotation, cropping, and adding Gaussian noise, according to the findings of the experiments. The encryption of watermarked images in the spatial and DCT domains and fused watermarked images in the DCT domain are all discussed. The transparency and security of the method are assessed using various measurements. The proposed approach achieves high-quality reconstructed watermarks and high security by using encryption to images and achieves robustness against any obstructive attacks. The developed hybrid algorithm recovers the watermark even in the presence of an attack with a correlation near 0.8.
1. Introduction
With the recent advances in image processing, the demands for securing images have been raised. Since digital multimedia works, including video, music, and photographs, became available for transmission, duplication, and publishing through the Internet, there has been a growing demand for security against illicit copying and dissemination [1]. The embedding of information, known as the watermark, is one approach to protect digital multimedia against illicit recording and distribution [2]. Watermarking has been used to secure digital multimedia data; therefore, digital watermarking could be an appealing option [3].
Medical imaging has been used in many applications and provides a path for achieving healthcare 4.0 [4]. Due to the advancement of computer-based communication and e-healthcare over the past decade, the requirement for secure medical images has become critical to preserving patients’ confidential medical data without compromising image quality. Medical imaging extensively uses 3D images and the recent advances in camera-based systems [5]. Medical images must be kept for the benefit of future patients, and a standardized approach must be developed to maintain their content’s accuracy, quality, and dependability [6]. The standard gives medical specialists instructions for achieving three types of telemedicine security: secrecy, authenticity, and integrity [7].
The issues of authenticity, confidentiality, integrity, and security of medical images transmitted through a communication system have been proposed to be resolved using medical image watermarking. Private medical data incorporated into the image should be undetectable, resistant to various attacks, and accessible only to authorized individuals [8]. There are currently just a few studies on watermarking algorithms for medical volume data, despite the fact that volume data are used in a wide range of medical picture applications. Watermarking in healthcare and medical information systems is still being researched [9].
A digital watermark is a type of marking implanted discreetly in a signal that can tolerate noise, such as audio, video, or image data. It is often used to indicate the owner of the signal’s copyright [10]. Digital watermarks may be used to validate the signal’s legitimacy and integrity or to reveal the signal’s owners’ identities. It is widely employed for tracing copyright violations and currency authenticity [11].
Robust watermarking algorithms well protect watermarking information against noise, compression, filtering, rotation, collision assaults, resizing, and cropping [10]. Watermarking techniques are divided into transform domain and spatial domain techniques. The watermarking information in the transform domain is generally more reliable than in the spatial domain. The discrete wavelet transform (DWT), and discrete cosine transform (DCT) are the transforms that are most frequently used for coefficient domain watermarking systems [12,13]. Medical images need to be encrypted in order to protect them from theft and keep the patients’ records safe; thus, we can achieve privacy.
This work provides a novel hybrid watermarking technique for securing medical image encryption. Different photos have been studied to ensure the robustness of the suggested technique. In the developed technique, the image is watermarked using a cascade of two mathematical transforms (DCT and Singular Value Decomposition (SVD)). The two transforms provide varying levels of resistance to watermarking attacks, such as noise, compression, filtering, rotation, collision attacks, resizing, and cropping.
Furthermore, the image is encrypted with DRPE or chaotic encryption to improve watermarking security and make it very hard for an unauthorized individual to recreate the original data. Any information loss during the embedding and extraction processes is completely unacceptable because every small detail contains vital information. The main contributions of the work can be summarized as follows:
- Designing and developing a novel watermarking technique for medical images to achieve copyrights.
- Designing and developing a novel encryption algorithm to secure the watermarked images.
- Developing a fusion process that is based on a fully different image than that to be encrypted.
- Developing three different systems that consider the watermarked images in spatial and DCT domains and the fused watermarked images in DCT. Double random phase encryption (DRPE) and chaotic encryption are used for each system.
- Performance evaluation of the developed technique for heterogeneous images and using various metrics.
The requirements for securing medical images have become critical to preserving patients’ confidential medical data without compromising image quality. So, some techniques were developed to achieve copyrights, as in [4], while the other part of existing techniques were introduced to achieve privacy using encryption, as in [9]. However, the novelty of the developed technique comes from considering both objectives. In our developed work, a hybrid technique of watermarking and encryption is proposed to achieve privacy and copyright.
The rest of the article is organized as follows. The existing related studies and the background of the considered methods are presented in Section 2. Section 3 introduces the developed hybrid scheme, while the performance is introduced in Section 4. Results are discussed in Section 5, and the conclusions and future directions are indicated in Section 6.
2. Background and Related Works
Multimedia files, including videos, songs, and images, can have information embedded into them using a digital watermarking technique, which allows the asset owner to retrieve and utilize the watermark to verify ownership. Watermark embedding and watermark extraction techniques make up a generalized watermark model.
In this section, we consider the common techniques used during watermarking. Furthermore, the related studies to the developed watermarking technique are introduced and discussed to present the novelty of the developed method.
2.1. Discrete Transforms
- A.
- Discrete Cosine Transform (DCT)
The real component of the discrete Fourier transform is used to obtain the discrete cosine transform. The DCT is a widely used transform function for converting a signal from the spatial to the frequency domain. The DCT splits an image into different frequency bands, making watermarking information easier to put in the image’s intermediate frequency bands. The intermediate frequencies are set in such a way that they avoid the most visually essential sections of the image (low frequencies) while avoiding overexposure to noise and compression attacks (high frequencies) [14,15]. Compression, sharpening, filtering, and noising are all attacks that DCT domain watermarking can withstand.
The formal definitions of DCT and Inverse DCT are introduced as follows.
where F(u,v) is the element of the transformed matrix, F(x,y) is the original matrix and α(u) is defined as follows.
- B.
- Discrete Wavelet Transform (DWT)
A DWT is a mathematical technique that performs a multi-resolution decomposition for images or frames [16]. It has been deployed for various applications, including picture watermarking, speech and video compression, and antenna simulation [17].
The DWT uses filters to separate the input into high and low-frequency components. The high-frequency component carries information on the edge parts, whereas the low-frequency component is split into high and low-frequency components once more. High-frequency components are often used for watermarking since the human eye is less sensitive to edge changes. Figure 1 depicts the wavelet transform, where g(n) denotes the low pass filter, h(n) is the high pass filter, and the down arrow denotes the factor two down-sampling of the output coefficients.
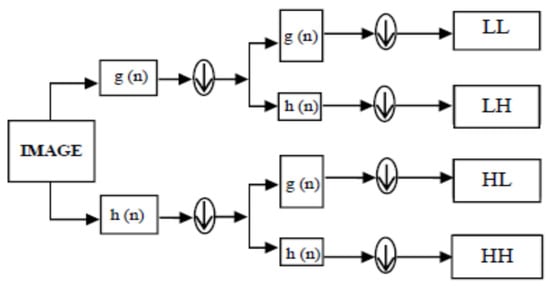
Figure 1.
2-level DWT using filtering approach.
The DWT describes an image as a series of miniature waves called wavelets, each with a different frequency and duration. A picture can be separated into four sub-bands using a wavelet (LL, HL, LH, and HH). This transform can be applied to the sub-bands, resulting in a multiscale perspective. To preserve higher image quality, DWT is used on two levels [17].
2.2. The Double Random Phase Encryption (DRPE)
Encryption is the process of encrypting a message so that only people with the proper authorization can read it and those without cannot. DRPE relies on modifying an image’s spectral distribution [18]. The DRPE is a frequently used optical encryption method because of its ease of use and resistance to numerous attacks. Image decoding is impossible without prior knowledge of the spectrum modification or the target image on the other side.
The idea behind DRPE is to use a coherent 4-f optical system in conjunction with two statistically independent random phase masks to turn an input image into stationary white noise. In order to encrypt data, one key is placed in the input plane (RPM1), while the other is placed in the Fourier plane (RPM2). Figure 2 summarizes the DRPE encryption and decryption processes [19].
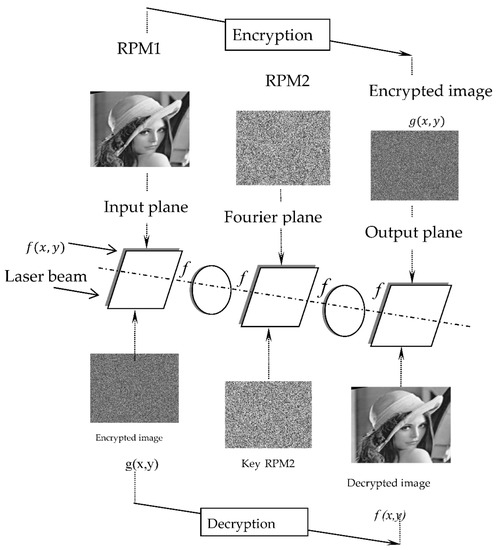
Figure 2.
Optical DRPE encryption process (top) and decryption process (bottom).
2.3. Chaotic Baker Map
In real-time secure image transmission systems, chaotic system is a well-known method deployed for encryption [20]. The starting settings and system parameters are extremely important in these systems. Chaotic systems are deterministic, yet their behavior is pseudorandom. The chaotic Baker map is a permutation-based tool that uses a secret key to randomize a square matrix of size MM by shifting pixel positions [21].
The Baker map is denoted by V (y1, y2, ……, yk), where the sequence of integers (y1, …, yk) represents the secret key. The sequence (y1, …, yk) is chosen so that each integer xi divides M, and the summation of (y1, …, yk) equals M. The pixel at indices (l, s) is moved to new indices as follows.
2.4. Fusion with Wavelet Transform
Image fusion is one of the most advanced, specific, and valuable medical imaging procedures available today. It is a common technique used to merge two or more images into one while keeping each original image’s key qualities. Numerous image fusion methods have been created, including the DCT, DWT, and DT CWT methods [22,23].
The decomposition of the image volume into frequency bands represents the preliminary step in the image fusion process. The specified fusion rules are then used for each image’s frequency bands to identify which can be combined and must be deleted from the final coefficients volume, as presented in Figure 3. The inverse wavelet transform is used to provide the final fussed volume.
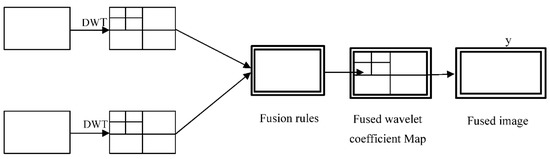
Figure 3.
The image fusion scheme based on DWT.
2.5. Related Works
Watermarking provides several appealing qualities that complement security measures and can provide improved protection for various multimedia applications. Watermarking was used in medical picture applications because of its appealing features, such as security and privacy [24]. Lavanya, in [25], presented a method for watermarking medical photographs that uses a stream cipher to encrypt them. Lavanya used a method for data integrity watermarking medical photos that included data embedding, image encryption, and image recovery phases [25]. Then, many watermarking techniques have been introduced and improved for medical photos [9,26].
In [27], the authors developed a hybrid algorithm based on DCT and DWT to improve the robust performance of encrypted domain watermarking. The authors suggested an encryption-based watermark-embedding algorithm that secures the original images from the third-party embedder. In [28], the authors compared a group of watermarking strategies depending on DWT and SVD. The authors of [29] established a very robust watermarking approach for color photographs by leveraging the advantages of the spatial and frequency domains.
In [30], Parah et al. proposed two secure hiding algorithms for medical images. One approach involved embedding watermark data in the electronic patient record at both the region of interest (RoI) and region of non-interest (RoNI). For remote diagnosis purposes, the second technique hides the watermark and EPR in RONI while preserving the ROI. In [31], the authors proposed a robust fragile watermarking solution for RoI in medical photos based on SVD and DWT.
In [32], Badshah et al. developed a watermarking algorithm for digital ultrasound images depending on the LZW (Lempel–Ziv–Welch) algorithm. Watermark data volume was reduced by using lossless data encoding. The used watermark was a cross between a ROI and a secret key. In recent years, watermarking has been employed to ensure the reliability and integrity of medical photographs. As a result, Eswaraiah and Reddy, in [33], developed a novel watermarking technique depending on integer wavelet transform (IWT). The proposed approach was predicated on incorporating patient RoNI data, hash RoI value, and recovery data. Integrity of RoI was confirmed, altered blocks within RoI were accurately detected, reliable RoNI data were made available, and key RoI data were successfully extracted.
In [34], the authors proposed a novel hybrid reversible medical picture watermarking approach to tackle the challenge of the transform domain. Turuk and Dhande, in [35], presented a novel wavelet-based reversible watermarking technique. They used numerous heterogeneous watermarks for image recovery.
In [36], the authors presented another reversible watermarking approach for medical photos based on the redundant DWT. The suggested system embedded the watermark through the changing of redundant DWT coefficients. This is to maintain the cover image’s excellent perceptional quality, while the sub-sample is employed to enrich the embedding capacity. In [37], the authors proposed a medical picture embedding approach that embed two secret watermarks into the RONI blocks.
Based on SVD, redundant DWT, and homomorphic transform, Khare and Srivastava, in [38], suggested a hybrid method for embedding medical images. In [39], the authors introduced a medical picture HER concealing algorithm that is both secure and efficient. The Pixel Repetition Method (PRM) and the modular arithmetic methodology are used in this method.
In [40], the release of graph data has been seen as a crucial step in the mining and analyzing data. Graph data, which reveal relationships between things, can be created locally and stored by different data owners. Since they may be related to the private lives of their owners and might be used by adversaries to carry out inference attacks, these data are typically private and sensitive. Current approaches either overlook the dispersed overlapping of graphs or treat private graph data as centralized contents. Therefore, a novel paradigm for distributed graph publication is suggested in this study. Differential privacy is used in this architecture to support the publication of secure materials. Graph combination, plan construction sharing, data perturbation, and graph reconstruction are among its four steps.
Protecting user privacy that is buried in the smart city data is becoming essential be-fore these data are combined for additional mining, analysis, and prediction. Since there is a natural trade-off between data privacy and data availability, it is difficult to maintain users’ context privacy after data fusion while ensuring reliable data analysis and prediction outcomes. In [41], the authors developed a privacy-aware data fusion and prediction solution for the industrial smart city environment that considered this difficulty. The developed technique was developed based on the traditional locality-sensitive hashing method.
In [42], the authors proposed an assessment paradigm in which only successfully authenticated users can submit reviews to service vendors under the proposed assessment paradigm. The blockchain network stores all of the reviews for service providers as well as the registration and authentication records of users’ identities. According to the security analysis, this model can guarantee the validity of user reviews for service providers. Other users can access valid user evaluations of service providers via the review publicity module. Additionally, the experimental findings demonstrate that the suggested approach has a shorter review submission time than alternative methods.
In [43], local differential privacy (LDP), which offers high-level privacy protections, has recently been adopted as the de facto norm for data sharing and analysis. The primary goal of LDP-based techniques is to extract statistical data about the entire population from sensitive data. However, authors employed LDP for distance estimates between scattered data to facilitate more intricate data analysis for the first time in the literature. To be more precise, we suggest PrivBV, a locally differentially private bit vector technique with a distance-aware property in the anonymized space. The authors also provide an optimization technique for minimizing privacy leaks in the high-dimensional space.
Due to its global coupling and the synchronization of its neurons’ pulses, the pulse-coupled neural network (PCNN) is frequently employed in picture fusion frameworks. However, the performance of the fusion is hampered by its manual parameter adjustment and inability to handle numerous pictures. To fuse the magnetic resonance imaging and single-photon emission computed tomography images of patients with acquired immunodeficiency syndrome (AIDS) dementia complex and Alzheimer’s disease, the authors, in [44], proposed a novel weighted parameter adaptive dual channel PCNN (WPADCPCNN) based medical fusion approach. Fractal dimension was used to estimate the parameters of the proposed WPADCPCNN model from its input data. While the low-pass sub-bands were combined using a new weighted multi-scale morphological gradients-based method, and the high-pass sub-bands were fused using the WPADCPCNN model.
3. Proposed Fusion-Based Securing Technique
The developed technique merges two main processes: embedding the information and extracting the original image. Figure 4 presents the main steps of the developed watermarking technique. It starts with picture pre-processing, then moves on to DCT transformation, SVD watermarking, and IDCT transformation. The watermarked image has a path throw the security unit to encrypt the image. A double layer of security is applied to achieve higher security of the watermarked image. The security unit comprises two parts: DWT fusion and DRPE. The input image is pre-processed at first and then passed to the DCT algorithm.
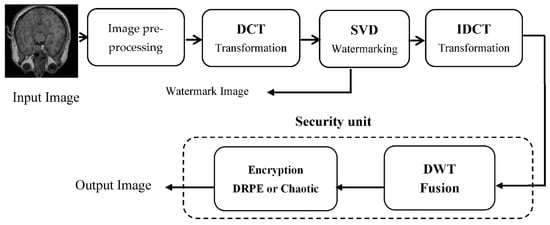
Figure 4.
Block diagram of the proposed technique.
The watermark embedding is carried out for the luminance component of the image. For the input f, 3D medical or color images can be converted into Y-Cb-Cr image as follows.
where Y is considered for luminance for luminance information, Cb is considered for chrominance blue information, and Cr is considered for red information of an image.
Because changes in brightness are less visible than changes in chrominance, the luminance component can be used as a cover for the watermark. Following the pre-processing unit, the DCT is applied to reduce residual intelligibility in the time domain and improve security. The DCT coefficient is embedded with the watermark image using the SVD watermarked approach, as in Figure 5.
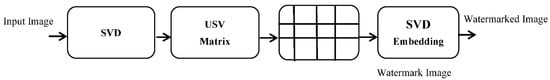
Figure 5.
Block diagram of the SVD embedding.
The SVD is calculated for the Y component to three components. The S component is divided into 64 × 64 blocks. The block number will be (M/64 ΧM/64) for an MxN input image. The watermark image is inserted into each block. Finally, the watermarked image is transformed to spatial using IDCT transformation followed by the encryption unit. This unit is developed to improve the security of the watermarked image; thus, an attacker cannot configure the real watermark without knowing the embedding approach.
The encryption unit is performed into two layers; DWT fusion followed by optical encryption using DRPE or Chaotic backer map to obtain better security. The developed algorithm deploys fusion in novel way compared with the traditional fusion processes.
It is developed with a fully different image than the encrypted image to achieve high-level randomness in the obtained watermarked image. This way is expected to achieve higher encryption efficiency. In order to ensure robustness, we consider three versions of the proposed technique with the specifications introduced in Table 1.

Table 1.
The three different proposed techniques.
4. Experimental Results
This section contains extensive performance evaluation findings for the three suggested approaches. The developed systems were tested over Matlab environment. As shown in Figure 6, the suggested encryption techniques have been tested for color, grayscale, and medical photos, each of which is 256 × 256 pixels in size, with watermarks of 64 × 64 pixels.

Figure 6.
Color, grayscale and medical images and watermarks.
Table 2, Table 3, Table 4, Table 5, Table 6 and Table 7 provide the watermarked images and the corresponding extracted watermarks for the tree proposed techniques based on DRPE and Chaotic.

Table 2.
Results of the third proposed technique based on DRPE.

Table 3.
Results of the third proposed technique based on Chaotic.

Table 4.
Results of the second proposed technique based on DRPE.

Table 5.
Results of the second proposed technique based on Chaotic.

Table 6.
Results of the first proposed technique based on DRPE.

Table 7.
Results of the first proposed technique based on Chaotic.
4.1. Imperceptibility and Robustness Analysis
In this section, we evaluate the quality of the encrypted images obtained at two levels of security after adding a watermark and applying encryption using the proposed encryption method. The peak signal-to-noise ratio (PSNR) is used as the quality metric for both watermarked and encrypted images. The proposed technique (3) produced ultra-high-quality images with high PSNRw from 115 dB to 116 dB for the watermarked image and gave a high degree of encryption after applying DPRE or chaotic by giving low PSNRe from 9 dB to 13 dB. In the case of using fusion in addition to DPRE or chaotic in the transform domain, PSNRf ranged from 14 dB to 16 dB, as presented in Table 2 and Table 3.
Where PSNRw is PSNR after adding watermark, PSNRe is PSNR after encryption, PSNRd is PSNR after decryption, and PSNRf is PSNR after fusion.
In the transform domain, the proposed technique (2) produced ultra-high-quality photos with high PSNRw ranging from 115 dB to 116 dB for the watermarked image and gave a high degree of encryption after applying DPRE or chaotic by giving low PSNRe from 3 dB to 11 dB without fusion as shown in Table 4 and Table 5.
In the case of working in the spatial domain, the proposed technique (1) for the watermarked image achieves images with high-quality and high PSNRw from 53 dB to 75 dB. Table 6 and Table 7 present results for this case. Results indicate that the proposed technique (1) gave low PSNRe from 3 to 11 dB without fusion after applying DPRE or chaotic.
Additionally, watermarks are accurately extracted from the marked photos without errors or mistakes, demonstrating the efficacy of the extraction methods. The findings demonstrate that whether embedding is used on color, grayscale, or medical photos, the proposed strategies always produce better-quality watermarked images.
We introduced a comparison between the PSNR, correlation coefficient (Cr) and structural similarity index (SSIM) for the proposed methods, as shown in Figure 7 using chaotic and in Figure 8 for DRPE encryption. Cr and SSIM are calculated as follows.
where A(i,j) and AW(i,j) are the original and extracted watermarks, respectively, µx and µy are the mean values of the signals x and y, respectively, , and are the variances of signals x and y, respectively, δxy is the cross-covariance between the two signals x and y, (S1 and S2) are small values.
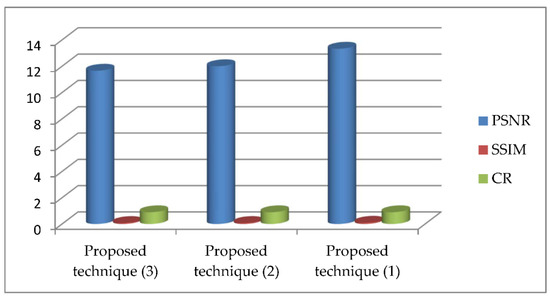
Figure 7.
Comparison of PSNR, SSIM and Cr for color airplane image for the three proposed techniques using chaotic encryption.
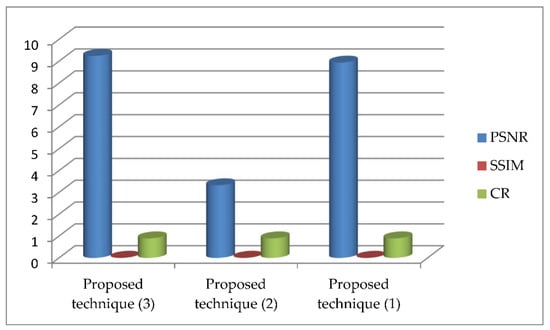
Figure 8.
Comparison of PSNR, SSIM, and Cr for color airplane image for the three proposed techniques using DRPE encryption.
4.2. Robustness Analysis
The watermarking process is considered resilient if a recovered watermark is obtained after using different attacks on the watermarked photos with good quality. Different attacks, including rotation, cropping, and noise addition, are used on the watermarked photos to test the resiliency of our systems. The resilience of the system was estimated through Cr measures.
4.2.1. Rotation Attack Analysis
We made a rotation to the watermarked photos by 30°. The encrypted photos and the corresponding watermarks captured after 30° rotation for the three proposed systems. Some values of the correlation coefficient are between 0.5 and 0.8 as shown in Table 8, Table 9 and Table 10. It is clear from figures that recovered watermarks are obtained from the rotated images. The results clearly state that the correlation between recovered and original watermarks is high, which means robustness is high.

Table 8.
Rotated images and corresponding extracted watermarks for the third proposed technique.

Table 9.
Rotated images and corresponding extracted watermarks for the second proposed technique.

Table 10.
Rotated images and corresponding extracted watermarks for the first proposed technique.
4.2.2. Cropping and Additive Gaussian Noise Analysis
Twenty percent of watermarked photographs are cropped during the watermarking process. The cropped photos yield a clearly discernible watermark as presented in Table 11, Table 12 and Table 13. Between 0.5 and 0.8 are reported for the correlation coefficients. The obtained watermark pictures are of good subjective quality and are easily recognizable, despite the fact that objective analysis reveals their lack of robustness.

Table 11.
Cropped images and corresponding extracted watermarks for the third proposed technique.

Table 12.
Cropped images and corresponding extracted watermarks for the second proposed technique.

Table 13.
Cropped images and corresponding extracted watermarks for the first proposed technique.
In addition, the system’s robustness has been evaluated under a Gaussian noise attack, as demonstrated in Table 14, Table 15 and Table 16. The correlation coefficient was used to evaluate the degree of similarity between the unaltered and watermarked versions of the photograph. The corrupted watermarked image can still be used to recover recognizable watermarks, as indicated in tables.

Table 14.
Gaussian noise images and corresponding extracted watermarks for the third proposed technique.

Table 15.
Gaussian noise images and corresponding extracted watermarks for proposed technique 1.

Table 16.
Gaussian noise images and corresponding extracted watermarks for the second proposed technique 2.
Table 17 shows a comparison of Cr of recovered watermarks from the gray Lena image for the three proposed systems using DRPE and chaotic encryption after applying three types of attacks to watermarked images. Figure 9 summarizes the results of this comparison.

Table 17.
The comparison among the recovered watermark after applying attacks.
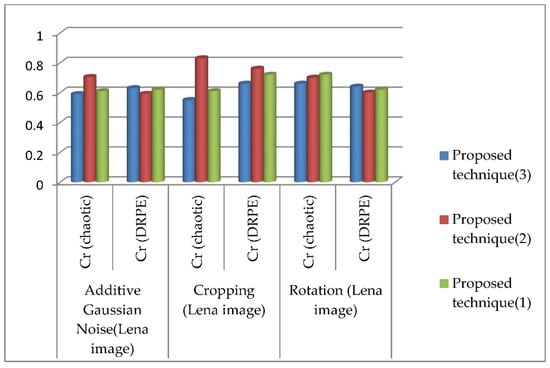
Figure 9.
Comparison of Cr of recovered watermarks from gray Lena image for the three proposed techniques using DRPE and chaotic encryption after applying three types of attacks to watermarked images.
5. Discussion
The developed technique depends on watermarking the image to maintain its quality and then encrypting it using either DPRE or chaotic method. Three techniques of the developed algorithm were considered, each of which implements a domain, as indicated in Table 1. The first technique works in the spatial domain, and the watermarked image is encrypted using DPRE or chaotic method. This is the same for the second technique, which works in the transform domain. The third technique makes a fusion of the watermarked image in addition to DPRE or chaotic encryption in the transform domain. This achieved a higher level of security by introducing a second level of encryption.
The third proposed technique produced ultra-high-quality images with high PSNRw for the watermarked images. It gave a high degree of encryption after applying DPRE or chaotic by giving low PSNRe. When performing fusion besides DPRE or chaotic in the transform domain, PSNRf was increased. This indicates that the introduction of fusion achieves higher privacy.
Moreover, watermarks are accurately extracted from the marked photos without errors or mistakes, demonstrating the efficacy of the extraction methods. The findings demonstrate that whether embedding is used on color, grayscale, or medical photos, the proposed strategies always produce better-quality watermarked images.
The resilience of the system was estimated via Cr. Compared to existing schemes, the proposed technique achieves a high resilience, with an average Cr of 0.8. Three heterogeneous attacks were considered for testing the security of the developed technique. Additive gaussian noise, cropping, and rotation were the primary attacks; however, the developed technique recovered the marked images without errors.
6. Conclusions
The article provided a novel watermarking technique that can be used to secure medical imaging. The use of a blend of graph-based transforms, SVD, fusion and chaotic and DRPE encryption allows for effective watermark embedding. The proposed method was tested on both normal and medical photos. The image’s quality is unaffected by the watermark, and the findings show that the proposed technique performs well. The proposed method is quick and adding an optimization algorithm will boost the utility of quality measurements. Higher quality metric values can still be targeted. Since the proposed method allows for the embedding and extraction of watermarked images without constraints on the host image, we think it would be useful to the field of watermarking for managing digital images. The proposed system may improve and fine-tune stealth and robustness to yield optimal performance against various assaults.
Author Contributions
Conceptualization, H.A.A., A.A.A. and R.A.; methodology, R.A. and A.A.A.; software, A.A.A., R.A. and A.A.A.; validation, R.A., A.A.A. and H.A.A.; formal analysis, R.A.; investigation, H.A.A. and A.A.A.; resources, R.A. and H.A.A.; data curation, A.A.A. and H.A.A.; writing—original draft preparation, R.A., A.A.A. and H.A.A.; writing—review and editing, A.A.A.; visualization, H.A.A.; supervision, R.A.; project administration, A.A.A. and H.A.A.; funding acquisition, R.A. All authors have read and agreed to the published version of the manuscript.
Funding
Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2022R323), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Acknowledgments
Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2022R323), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Dhawan, S.; Gupta, R. Analysis of Various Data Security Techniques of Steganography: A Survey. Inf. Secur. J. Glob. Perspect. 2021, 30, 63–87. [Google Scholar] [CrossRef]
- Mahto, D.K.; Singh, A.K. A Survey of Color Image Watermarking: State-of-the-Art and Research Directions. Comput. Electr. Eng. 2021, 93, 107255. [Google Scholar] [CrossRef]
- Wan, W.; Wang, J.; Zhang, Y.; Li, J.; Yu, H.; Sun, J. A Comprehensive Survey on Robust Image Watermarking. Neurocomputing 2022, 488, 226–247. [Google Scholar] [CrossRef]
- Karatas, M.; Eriskin, L.; Deveci, M.; Pamucar, D.; Garg, H. Big Data for Healthcare Industry 4.0: Applications, Challenges and Future Perspectives. Expert Syst. Appl. 2022, 200, 116912. [Google Scholar] [CrossRef]
- Hussain, S.; Mubeen, I.; Ullah, N.; Shah, S.S.U.D.; Khan, B.A.; Zahoor, M.; Ullah, R.; Khan, F.A.; Sultan, M.A. Modern Diagnostic Imaging Technique Applications and Risk Factors in the Medical Field: A Review. BioMed Res. Int. 2022, 2022, 5164970. [Google Scholar] [CrossRef]
- Salcudean, S.E.; Moradi, H.; Black, D.G.; Navab, N. Robot-Assisted Medical Imaging: A Review. Proc. IEEE 2022, 110, 951–967. [Google Scholar] [CrossRef]
- Kaviani, S.; Han, K.J.; Sohn, I. Adversarial Attacks and Defenses on AI in Medical Imaging Informatics: A Survey. Expert Syst. Appl. 2022, 198, 116815. [Google Scholar] [CrossRef]
- Singh, A.K.; Anand, A.; Lv, Z.; Ko, H.; Mohan, A. A Survey on Healthcare Data: A Security Perspective. ACM Trans. Multimed. Comput. Commun. Appl. 2021, 17, 1–26. [Google Scholar] [CrossRef]
- Nagarajan, S.; Anita, X.; Rajangam, V. Medical Image Watermarking: A Review on Wavelet-Based Methods. In Signal and Image Processing Techniques for the Development of Intelligent Healthcare Systems; Springer Singapore: Singapore, 2021; pp. 203–221. ISBN 9789811561405. [Google Scholar]
- Wadhera, S.; Kamra, D.; Rajpal, A.; Jain, A.; Jain, V. A Comprehensive Review on Digital Image Watermarking. arXiv 2022, arXiv:2207.06909. [Google Scholar]
- Mishra, P.; Ahuja, R. Review of Secured, Robust and Imperceptible Digital Watermarking Scheme. In Proceedings of the 2021 9th International Conference on Reliability, Infocom Technologies and Optimization (Trends and Future Directions) (ICRITO), Nodia, India, 3–4 September 2021; pp. 1–5. [Google Scholar]
- Shamshad, F.; Khan, S.; Zamir, S.W.; Khan, M.H.; Hayat, M.; Khan, F.S.; Fu, H. Transformers in Medical Imaging: A Survey. arXiv 2022, arXiv:2201.09873. [Google Scholar]
- Sahin, A.; Guler, I. A Survey of Digital Image Watermarking Techniques Based on Discrete Cosine Transform. Int. J. Inf. Secur. Sci. 2021, 10, 99–110. [Google Scholar]
- Ochoa-Domínguez, H.; Rao, K.R. Discrete Cosine Transform, 1st ed.; CRC Press: Boca Raton, FL, USA, 2019; ISBN 9780203729854. [Google Scholar]
- Solé-Casals, J.; Anchustegui-Echearte, I.; Marti-Puig, P.; Calvo, P.M.; Bergareche, A.; Sánchez-Méndez, J.I.; Lopez-de-Ipina, K. Discrete Cosine Transform for the Analysis of Essential Tremor. Front. Physiol. 2018, 9, 1947. [Google Scholar] [CrossRef] [PubMed]
- Choudhry, M.S.; Kapoor, R.; Abhishek; Gupta, A.; Bharat, B. A Survey on Different Discrete Wavelet Transforms and Thresholding Techniques for EEG Denoising. In Proceedings of the 2016 International Conference on Computing, Communication and Automation (ICCCA), Noida, India, 29–30 April 2016; pp. 1048–1053. [Google Scholar]
- Othman, G.; Zeebaree, D.Q. The Applications of Discrete Wavelet Transform in Image Processing: A Review. Jscdm 2020, 1, 31–43. [Google Scholar]
- Ghadirli, H.M.; Nodehi, A.; Enayatifar, R. An Overview of Encryption Algorithms in Color Images. Signal Process. 2019, 164, 163–185. [Google Scholar] [CrossRef]
- Zhou, K.; Fan, J.; Fan, H.; Li, M. Secure Image Encryption Scheme Using Double Random-Phase Encoding and Compressed Sensing. Opt. Laser Technol. 2020, 121, 105769. [Google Scholar] [CrossRef]
- Zolfaghari, B.; Koshiba, T. Chaotic Image Encryption: State-of-the-Art, Ecosystem, and Future Roadmap. Appl. Syst. Innov. 2022, 5, 57. [Google Scholar] [CrossRef]
- Vijayakumar, T.; Mohamed Parvees, M.Y. Applications of Chaotic Maps for Image Security. J. Optoelectron. Laser 2022, 41, 559–565. [Google Scholar]
- Azam, M.A.; Khan, K.B.; Salahuddin, S.; Rehman, E.; Khan, S.A.; Khan, M.A.; Kadry, S.; Gandomi, A.H. A Review on Multimodal Medical Image Fusion: Compendious Analysis of Medical Modalities, Multimodal Databases, Fusion Techniques and Quality Metrics. Comput. Biol. Med. 2022, 144, 105253. [Google Scholar] [CrossRef]
- Kaur, H.; Koundal, D.; Kadyan, V. Image Fusion Techniques: A Survey. Arch. Comput. Methods Eng. 2021, 28, 4425–4447. [Google Scholar] [CrossRef]
- Thabit, R. Review of Medical Image Authentication Techniques and Their Recent Trends. Multimed. Tools Appl. 2021, 80, 13439–13473. [Google Scholar] [CrossRef]
- Lavanya, A.; Natarajan, V. Watermarking Patient Data in Encrypted Medical Images. Indian Acad. Sci. 2012, 37, 723–729. [Google Scholar] [CrossRef]
- Anand, A.; Singh, A.K. Watermarking Techniques for Medical Data Authentication: A Survey. Multimed. Tools Appl. 2021, 80, 30165–30197. [Google Scholar] [CrossRef]
- Guo, J.; Zheng, P.; Huang, J. Secure Watermarking Scheme against Watermark Attacks in the Encrypted Domain. J. Vis. Commun. Image Represent. 2015, 30, 125–135. [Google Scholar] [CrossRef]
- Mohananthini, N.; Yamuna, G. Comparison of Multiple Watermarking Techniques Using Genetic Algorithms. J. Electr. Syst. Inf. Technol. 2016, 3, 68–80. [Google Scholar] [CrossRef]
- Prathap, I.; Natarajan, V.; Anitha, R. Hybrid Robust Watermarking for Color Images. Comput. Electr. Eng. 2014, 40, 920–930. [Google Scholar] [CrossRef]
- Parah, S.A.; Sheikh, J.A.; Ahad, F.; Loan, N.A.; Bhat, G.M. Information Hiding in Medical Images: A Robust Medical Image Watermarking System for E-Healthcare. Multimed. Tools Appl. 2017, 76, 10599–10633. [Google Scholar] [CrossRef]
- Thakkar, F.N.; Srivastava, V.K. A Blind Medical Image Watermarking: DWT-SVD Based Robust and Secure Approach for Telemedicine Applications. Multimed. Tools Appl. 2017, 76, 3669–3697. [Google Scholar] [CrossRef]
- Badshah, G.; Liew, S.-C.; Zain, J.M.; Ali, M. Watermark Compression in Medical Image Watermarking Using Lempel-Ziv-Welch (LZW) Lossless Compression Technique. J. Digit. Imaging 2016, 29, 216–225. [Google Scholar] [CrossRef]
- Eswaraiah, R.; Sreenivasa Reddy, E. Robust Medical Image Watermarking Technique for Accurate Detection of Tampers inside Region of Interest and Recovering Original Region of Interest. IET Image Process. 2015, 9, 615–625. [Google Scholar] [CrossRef]
- Selvam, P.; Balachandran, S.; Pitchai Iyer, S.; Jayabal, R. Hybrid Transform Based Reversible Watermarking Technique for Medical Images in Telemedicine Applications. Optik 2017, 145, 655–671. [Google Scholar] [CrossRef]
- Turuk, M.P.; Dhande, A.P. A Novel Reversible Multiple Medical Image Watermarking for Health Information System. J. Med. Syst. 2016, 40, 269. [Google Scholar] [CrossRef]
- Gao, L.; Gao, T.; Zhao, J. Reversible Watermarking in Medical Image Using RDWT and Sub-Sample. In Cryptography; IGI Global: Hershey, PA, USA, 2020; pp. 480–497. [Google Scholar]
- Swaraja, M.; Kora, P. An Optimized Blind Dual Medical Image Watermarking Framework for Tamper Localization and Content Authentication in Secured Telemedicine. Biomed. Signal Process. Control. 2020, 55, 101665. [Google Scholar] [CrossRef]
- Khare, P.; Srivastava, V.K. A Secured and Robust Medical Image Watermarking Approach for Protecting Integrity of Medical Images. Trans. Emerg. Telecommun. Technol. 2021, 32, e3918. [Google Scholar] [CrossRef]
- Parah, S.A.; Sheikh, J.A.; Akhoon, J.A.; Loan, N.A. Electronic Health Record Hiding in Images for Smart City Applications: A Computationally Efficient and Reversible Information Hiding Technique for Secure Communication. Future Gener. Comput. Syst. 2020, 108, 935–949. [Google Scholar] [CrossRef]
- Zheng, X.; Zhang, L.; Li, K.; Zeng, X. Efficient Publication of Distributed and Overlapping Graph Data under Differential Privacy. Tsinghua Sci. Technol. 2022, 27, 235–243. [Google Scholar] [CrossRef]
- Qi, L.; Hu, C.; Zhang, X.; Khosravi, M.R.; Sharma, S.; Pang, S.; Wang, T. Privacy-Aware Data Fusion and Prediction with Spatial-Temporal Context for Smart City Industrial Environment. IEEE Trans. Industr. Inform. 2021, 17, 4159–4167. [Google Scholar] [CrossRef]
- Li, F.; Yu, X.; Ge, R.; Wang, Y.; Cui, Y.; Zhou, H. BCSE: Blockchain-Based Trusted Service Evaluation Model over Big Data. Big Data Min. Anal. 2022, 5, 1–14. [Google Scholar] [CrossRef]
- Sun, L.; Ping, G.; Ye, X. PrivBV: Distance-Aware Encoding for Distributed Data with Local Differential Privacy. Tsinghua Sci. Technol. 2022, 27, 412–421. [Google Scholar] [CrossRef]
- Panigrahy, C.; Seal, A.; Mahato, N.K. MRI and SPECT Image Fusion Using a Weighted Parameter Adaptive Dual Channel PCNN. IEEE Signal Process. Lett. 2020, 27, 690–694. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).























































































































































































































































































































































































































