Abstract
Most applications looking for XSS vulnerabilities have a variety of weaknesses related to the nature of constructing internet applications. Existing XSS vulnerability packages solely scan public net resources, which negatively influences the safety of internet resources. Threats may be in non-public sections of internet resources that can only be accessed by approved users. The aim of this work is to improve available internet functions for preventing XSS assaults by creating a programme that detects XSS vulnerabilities by completely mapping internet applications. The innovation of this work lies in its use of environment-friendly algorithms for locating extraordinary XSS vulnerabilities in addition to encompassing pre-approved XSS vulnerability scanning in examined internet functions to generate a complete internet resource map. Using the developed programme to discover XSS vulnerabilities increases the effectiveness of internet utility protection. This programme also simplifies the use of internet applications. Even customers unfamiliar with the fundamentals of internet security can use this programme due to its capability to generate a document with suggestions for rectifying detected XSS vulnerabilities.
1. Introduction
Ensuring information security (IS) in computing systems is a priority for organisations that use algorithms to collect, process, store and transmit information. However, with the widespread use of the internet, many threats to IS have emerged. Most web applications used over the previous decade were static and lacked interactive user interfaces and thereby had no exploitable vulnerabilities [1,2]. As a result, many developers ignored web application security issues at the time. Whilst a large number of dynamic websites that utilise modern technologies to connect users to web applications and enhance their interactions with web resources (e.g., bulletin boards and feedback forms) have been introduced in recent years, these innovations have vulnerabilities that allow intruders to perform computer attacks, such as SQL-injection and cross-site scripting (XSS) [3]. With the help of injected code, an intruder can gain unauthorised access to user data, which could allow them to impersonate these users, perform illegal actions on the local computers of users and the network equipment of their companies or change the configurations of their network and software. The lack of proper measures for ensuring IS has resulted in the emergence of computer attacks linked to malicious code execution [4].
According to the Open Web Application Security Project (OWASP), cross-site programming is one of the most common types of computer attacks [5]. Around 65% of websites are exposed to XSS vulnerabilities detected in current web applications [6], as shown in Figure 1.
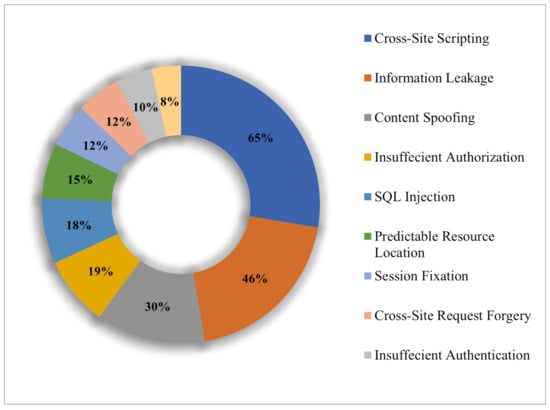
Figure 1.
Percentage of websites exposed to various cyber vulnerabilities.
As shown in Figure 1, it is clear that information leakage is the second biggest threat, with 46% of websites exposed to this type of cyber vulnerability.
Recently, poorly developed software programs have been identified as safety threats. The number of viruses to which a system is potentially exposed is directly associated with the size and complexity of the established net packages and servers. Most multifaceted applications have both extensive loopholes and a few already identified weaknesses. In addition, net servers are intrinsically multifaceted applications. Websites are also multifaceted and even intentionally request extra data from users. Cross-site web page scripting (XSS) is one of the riskiest and most-exploited assaults in current times. Almost 65% of websites have been identified to have one or more of the XSS vulnerabilities listed in current net packages.
Cross-site attacks, where users inject payloads (malicious code) in the customer section of a website, are the most common network attacks via the web. Weak spots found in poorly encrypted websites are exploited by attackers, using the victim’s browser to send malicious text from vulnerable sites. The types of attacks exploiting XSS vulnerabilities are presented in the next section, followed by examples of XSS vulnerability detection software in Section 3. Then, the evaluation results are discussed in Section 4. Finally the conclusion is presented in Section 5.
2. Types of Attacks Exploiting XSS Vulnerabilities
XSS is a computer attack that involves injecting malicious code into the webpage parameters sent to a web browser. This computer attack is similar to SQL-injection [7] and can be used in various ways [8]. XSS attacks can be classified according to the vector and the method of influence, as shown in Figure 2.
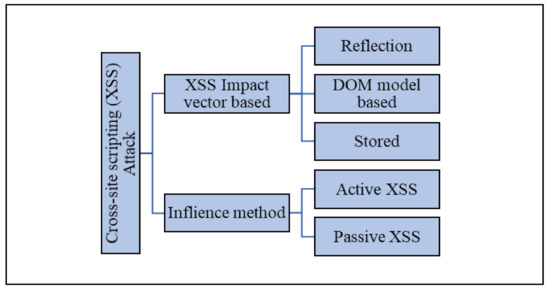
Figure 2.
Classification of XSS attacks.
Based on the XSS impact vector, an XSS attack can be classified as follows:
- Active XSS, which does not require additional actions on part of the user in terms of the functionality of web applications.
- Passive XSS, which is triggered when a user performs a certain action, such as clicking or hovering the cursor.
- Reflected XSS.
- Stored XSS.
- XSS based on the document object model (DOM).
2.1. Reflected XSS
Reflected XSS attacks are the most common type of XSS attack, and the vulnerability exploited by this attack is easy to detect. In a reflected XSS attack, the code is sent to the server and returned to the user within a single HTTP request. The XSS using a reflected XSS vulnerability follows a complex process wherein the malicious code is injected into a URL, this URL is sent to the user, and the user must click on this URL to run the malicious code.
However, such complexity does not present an obstacle for attackers. A basic reflected XSS attack does not aim to steal confidential information. When a user visits a website with a reflected XSS vulnerability, a warning window is displayed after executing the script code. A link to a webpage with a basic reflected XSS vulnerability resembles the following: alert(%E2%80%9CXSScompletedsuccessfully%E2%80%9D))" target="_blank">http://site.com/<script>alert(“XSScompletedsuccessfully”)</script>). An advanced internet user would find this link strange and would refuse to proceed to the directed webpage. One method for hiding such a malicious link is RFC 1738 encoding [9]. In the following code snippet, after encoding a malicious URL, the script code becomes unrecognisable: