Abstract
Chaotic systems are vital in designing contemporary cryptographic systems. This study proposes an innovative method for constructing an effective substitution box using a 3-dimensional chaotic map. Moreover, bouyed by the efficiency of the proposed chaos-based substitution boxes’ effectiveness, we introduce a new chaos-based image cryptosystem that combines the adeptness of Gray codes, a non-linear and sensitive hyper-chaotic system, and the proposed S-box. The generated secret key emanating from the cryptosystem is correlated to the input image to produce a unique key for each image. Extensive experimental outcomes demonstrate the utility, effectiveness, and high performance of the resulting cryptosystem.
1. Introduction
In various graphics applications such as military, medicine, homeland security, etc., advanced image encryption techniques are increasingly needed for the safe transfer, storage, and recuperation of digital images. A well-designed image cryptosystem should meet the two principles: diffusion and confusion [1]. Confusion indicates that all possible traces or information related to the plaintext or key are deleted from the ciphertext. Diffusion indicates that any tiny modification in either the plaintext or the key leads to a huge modification in the ciphertext. The substitution-box (S-box) is a nonlinear unit used in many cryptographic applications to guarantee the confusion characteristic [2]. The diffusion feature can be checked with chaotic dynamical maps. In actuality, chaotic maps have numerous ultimate features, such as ergodicity, sensitivity to primary conditions. They show a random behavior that can cause confusion and diffusion in the plaintext to get secure ciphertext [3].
Recently, various researchers have used chaotic maps in constructing S-boxes and designing image encryption mechanisms [4,5,6,7,8,9,10,11,12,13]. Chaotic systems play an important role in designing S-boxes. For example, Tang et al. [14] presented a different scheme for constructing S-box using a 2D discretized chaotic system, and in [7], a four-step strategy to construct S-boxes using a chaotic system is proposed. In [15], Chen et al. developed the scheme presented in [14] by utilizing 3D Backer system. In [16], Fatih et al. introduced a new method for S-box constructions using chaotic Lorenz map. Furthermore, Khan et al. [17] presented a new S-box construction scheme for block cipher using multi-chaotic maps. A popular characteristic of the above approaches is that they construct S-boxes using only the randomness properties of chaotic systems. This is why we need a new chaotic map with good randomness properties to build strong S-boxes. In [18], Tlelo-Cuautle et al. presented a new 3D chaotic map with infinite numbers of equilibrium points and good effective performance. Based on the advantages of the presented map in [18], we design a new chaos-based S-box that utilizes the randomness property of the chaotic map.
Data security performs a vital task in our daily life, in which chaotic systems are popularly utilized in the development of modern encryption mechanisms [19,20,21]. Based on chaos, several image cryptosystems have been introduced. Most of them are dependent on a one-dimensional or multi-dimensional chaotic system to generate pseudorandom numbers for constructing the cipher image. For example, in [22], a skew tent map is employed to design an image encryption approach, and in [8], a 1D chaotic map is obtained through coupling sine and tent maps, which is then adjusted to encrypt the plain image. Hua et al. in [23] employ a 2D Sine Logistic modulation system to produce an image cryptosystem, and Liu et al. [24] suggest a color image cryptosystem by utilizing a hyper-chaotic map and Choquet fuzzy integral. In [9], a chaos-based image block encryption approach is presented using S-box, and Wang et al. [24] suggested an image cryptosystem in the form of block cipher using a chaotic map and dynamic random growth mechanism. In [25], an image cryptosystem based on a 3D cat map is proposed. Although the previous schemes have some good results, they are not enough to raise the effectiveness of potential applications for the image encryption field. Most of them present vulnerabilities [26,27,28].
Based on the presented chaos-based substitution box efficiency, we present a new chaos-based image cryptosystem using Gray code, 3D chaotic map [18], and the proposed substitution box strategy. The provided image cryptosystem can be implemented on both grey-scale and colored images. Experimental outcomes demonstrate that the presented approach posses high performance and security.
To clarify, the main contributions of our study are twofold, as follows:
- Designing a new chaos-based S-box and validating its randomness property as required in efficient chaotic maps [18].
- Utilising the designed S-box as the fulcrum of a new image cryptosystem that also integrates the Gray code and the chaotic mapping [18] to generate unique encryption signatures with high sensitivity for each image.
This work’s organization is as follows: Section 2 gives the preliminary work for the suggested schemes. In Section 3, the new approach of designing the S-box is illustrated, and the criteria for assessing the S-box and the performance evaluation of the suggested S-box are presented and compared with other chaos-based S-boxes. In Section 4, a new chaos-based image cryptosystem is presented, while its performance evaluations are provided in Section 5. Finally, a conclusion is given in Section 6.
2. Preliminary Knowledge
This section presents the preliminary knowledge needed for constructing the S-box and designing the image encryption mechanism. In what follows, we provide the preliminary knowledge regarding the chaotic system [18] and Gray code.
2.1. 3D Chaotic Map
Tlelo-Cuautle et al. [18] introduced a new 3D chaotic map with infinite numbers of equilibrium points and good effective performance, which the following equation can express:
where a is the system parameter, and are state variables. For more information about the chaotic map, refer to Reference [18]. To present the cryptographic applications of the chaotic system provided in Equation (1), we adjust the system as given in Equation (2).
2.2. Gray Code
Gray code is a representation of two consecutive values that should differ in only one bit. This feature has proven useful in many applications. The representation of Gray code can be defined as given in Equation (3).
where ≫ denotes the binary right shift, and ⊕ is the binary XOR operation. Table 1 provides an illustrated example of Gray code operation.

Table 1.
Illustrative example of 3-bit Gray code equivalence.
3. Proposed S-box Approach
In this part, we present the new approach of designing the S-box, its performance evaluation, and compared it with other chaos-based S-boxes.
3.1. S-box Construction
Chaotic systems perform a vital task in constructing S-boxes. Utilizing the powers of the presented chaotic map in [18], we proposed a new chaos-based S-box that utilizes the randomness property of the chaotic map. The proposed algorithm for producing a new S-box is described in Algorithm 1.
| Algorithm 1: S-box construction |
| Parameters: Primary conditions and control parameters for acting the 3D chaotic map () Output: An S-box (SBox) 1 // Operate the chaotic map using primary requirements 256 times 2 // Order the elements in ascending structure 3 // Get the index of every element of the sequence V in the sequence X 4 // Remodeling sequence into structure to generate the S-box |
In this paper, the primary key parameters for acting the chaotic system (2) to generate the stated S-box are given as (, , , and ). The generated S-box by the presented method is shown in Table 2.

Table 2.
S-box by the proposed scheme.
3.2. Performance Analysis
In [29,30,31], the most important criteria for a strong S-box are presented. These criteria include bijectivety, strict avalanche criterion (SAC), differential and linear approximation probability, and the bit independence criterion (BIC).
3.2.1. Bijective Property
An S-box is bijective when it has all distinct outcome integers in the period . From Table 2, our produced S-box has distinct outcome integers in the period . Consequently, the produced S-box fulfills the bijective characteristic.
3.2.2. Nonlinearity Criterion
The non-linearities of the produced S-box and S-boxes displayed in [7,14,15,16,32] are shown in Table 3. We notice that the average non-linearity given by the suggested approach is superior to that of the S-boxes in References [7,14,15,16] and lower than Wang’s S-box [32].

Table 3.
Comparison of the non-linearities.
3.2.3. Strict Avalanche Criterion
The dependence matrix of the created S-box is provided in Table 4. The average value of the proposed S-box’s dependence matrix is 0.4993, which is very near to the optimal value of 0.5. The maximum, minimum, and average values of our S-box and other S-boxes’ dependence matrix are provided in Table 5. The outcomes demonstrate that the generated S-box using our strategy has good SAC features.

Table 4.
Dependence matrix of the proposed S-box.

Table 5.
Comparison of strict avalanche criterion.
3.2.4. Output Bits Independence Criterion (BIC)
The outcomes of BIC for our S-box are provided in Table 6 and Table 7. Table 6 displays the BIC non-linearity, in which the minimum BIC non-linearity is 100, and the average value exceeds 104.2143. Table 7 shows the BIC-SAC, in which the average BIC-SAC is 0.5030, which is very near to the optimal value of 0.5. Consequently, the presented S-box fulfills the BIC criterion. Additionally, the comparison of the nonlinearities BIC and BIC-SAC are given in Table 8. Table 8 proves that the outcomes obtained from our S-box realize a practically acceptable range.

Table 6.
Bits Independence Criterion (BIC) nonlinearity of the proposed S-box.

Table 7.
BIC-SAC criterion of the proposed S-box.

Table 8.
Comparison of BIC.
3.2.5. The Equiprobable Input/Output XOR Distribution
The differential approximation tables for our S-box are listed in Table 9. The differential approximate probability (DP) of the presented S-box is 0.039062, demonstrating that the presented method is secure against differential attacks. The PDs of other S-boxes are provided in Table 10, in which our S-box has an acceptable DP value compared to other S-boxes.

Table 9.
Differential approximate probability (DP) for the proposed S-box.

Table 10.
Differential approximate probability (DP) comparison.
3.2.6. Linear Approximation Probability (LP)
The probability of linear approximation for the compared S-boxes is given in Table 11. Obviously, our S-box has an LP value of 0.1250 and is comparable with the value of other S-boxes. Consequently, the proposed S-box has acceptable LP characteristics.

Table 11.
A comparison of Linear approximation probability (LP).
3.3. Discussion
From the above performance evaluations of our S-box compared with prior S-boxes, we can conclude that:
- Table 2 demonstrates the bijective feature of our proposed S-box.
- From Table 3, we can notice that our S-box have good performance compared to prior S-boxes in References [7,14,15,16].
- The average value of BIC-SAC for the proposed S-box is 0.5030, which is very near the optimal value.
- The maximum DP value, Table 10, is acceptable.
- The LP value of our S-box, Table 11, is acceptable.
4. Proposed Encryption Approach
In this part, we present a new image cryptosystem based on S-box, 3D chaotic system (2), and Gray code. In the substitution phase, the presented S-box in Section 3 is utilized to demonstrate its fitness for various cryptographic applications.
4.1. Encryption Process
The detailed steps of the encryption process for the presented cryptosystem are outlined in Figure 1 and defined in Algorithm 2.
| Algorithm 2: Encryption procedure |
 |
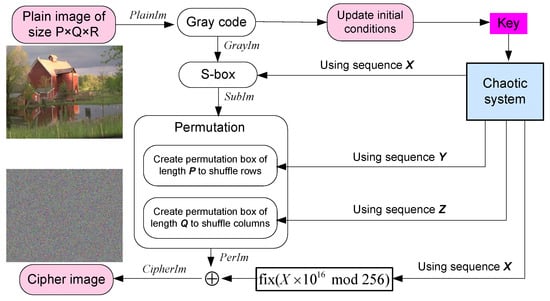
Figure 1.
Block diagram of the proposed encryption algorithm.
4.2. Decryption Process
The decryption process consists of applying the encryption steps in reverse order. The proposed algorithm is symmetric; i.e., the same secret key is used at the reception to decipher the encrypted images correctly. Thus, the secret key of (2) and the parameter must be transferred to the receiver using a secure exchange like the Diffie-Hellman key exchange. The steps of the decryption process are illustrated in Figure 2 and detailed in Algorithm 3.
| Algorithm 3: Decryption procedure |
 |
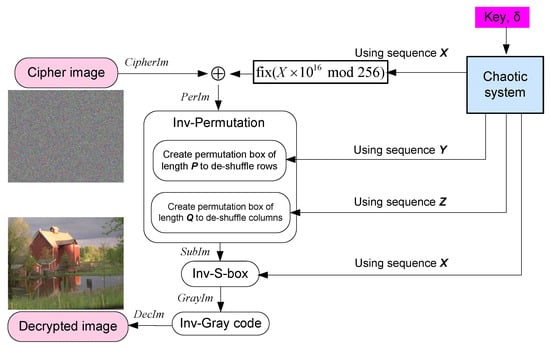
Figure 2.
Block diagram of the proposed decryption algorithm.
5. Performance and Security Analyses
In this part, various analyses are employed to evaluate the security and performance of the suggested encryption scheme. A dataset of images taken from Kodak [33] of dimension were employed to evaluate the proposed cryptosystem (see Figure 3). The primary values and control parameter for acting the 3D chaotic map (2) are given as (, , , and ). These simulation results were obtained using Matlab software, which was performed on an Intel Core i5-2450M 2.5 CPU with 6 GB RAM.
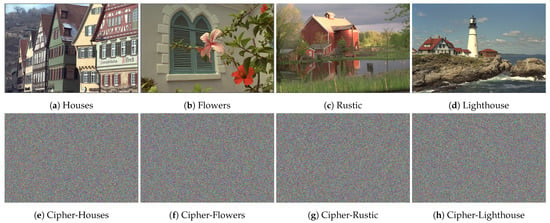
Figure 3.
Image dataset utilized for evaluating the proposed cryptosystem (a–d) and its corresponding ciphered ones (e–h).
5.1. Key Space Analysis
The key space is defined as the whole set of keys employed throughout the encryption process. It must be amply large to make brute-force attacks ineffective. The key space of the proposed cryptosystem consists of the initial conditions of (2). The computational precision of digital computers is assumed to be . The possible values of are , as are the values of , , and a. Therefore, the proposed scheme holds a key space, which is enough to defend against potential brute-force-based attacks.
5.2. Statistical Analysis
In this part, various statistical analyses are utilized to evaluate the performance of the suggested cryptosystem, including correlation analysis, histogram analysis, global entropy, and local entropy.
5.2.1. Correlation Analysis
The correlation of neighboring pixels in the original images and their ciphered ones are displayed in this subsection. It is understood that the values of correlation for original images are very near to 1, whilst encrypted images with a good encryption mechanism are very near to 0. The correlations among each pair of two neighboring pixels can be measured as follows:
where and are gray-scale values of two selected adjacent pixels, and N is the complete number of pairs collected from the image. The correlation coefficients of 10,000 randomly selected pairs of neighboring pixels in the original image and its encrypted ones are provided in Table 12. The correlation coefficients of original images are close to 1, whilst those of ciphered images are approximately equal to 0. Then, the adjacent pixels in the encrypted image are de-correlated in each direction. This feature is displayed graphically in Figure 4, Figure 5 and Figure 6, which contains plots of the correlation distributions in each direction of the original Houses image and the Cipher-Houses image for each color component. Consequently, the presented encryption scheme fulfills zero correlation, and it has a high privilege towards statistical attacks.

Table 12.
Correlation values for combinations of images in the dataset in Figure 3.
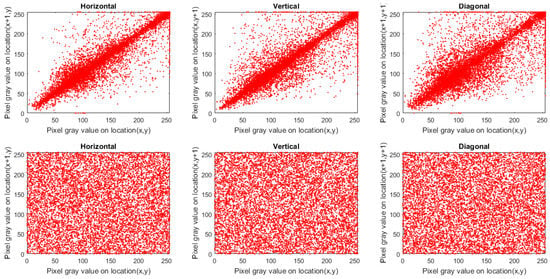
Figure 4.
Correlation distribution of plain and ciphered Houses images for the red channel.
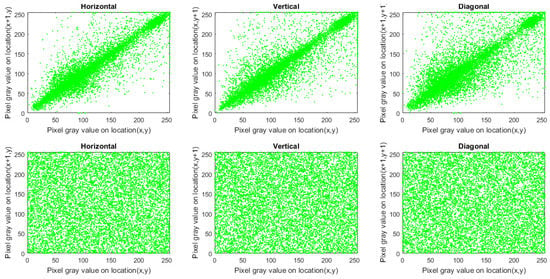
Figure 5.
Correlation distribution of plain and ciphered Houses image for the green channel.
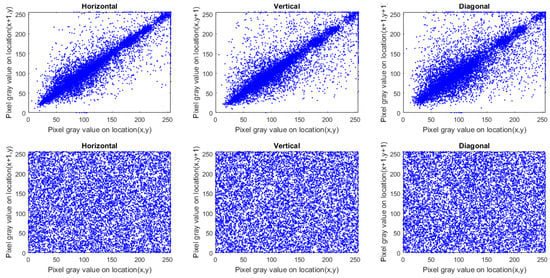
Figure 6.
Correlation distribution of plain and ciphered Houses image for the blue channel.
5.2.2. Histogram Analysis
The histogram exposes the intensity of the grey level of an image. This information can be beneficial in the event of a histogram attack with an uneven distribution. Images created using a well-designed image cryptosystem should have identical histograms to increase resistance to statistical analysis. Histograms of plain images and their ciphered ones are shown in Figure 7. Obviously, the histograms of the ciphered images are somewhat identical and differ significantly from the corresponding plain images. Therefore, we can deduce that the suggested encryption mechanism can withstand histogram attacks.
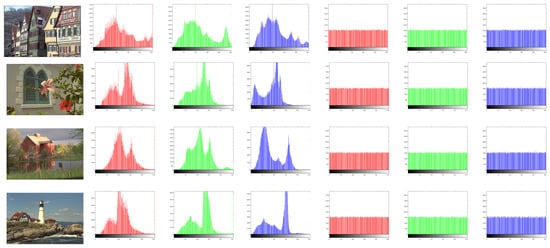
Figure 7.
Histograms of the studied images, which the encrypted images (displayed in the last three columns) have a completely identical distribution.
5.2.3. Global Entropy
Information entropy is a statistical examination of randomness. The entropy value can be measured as given in (5).
where denotes the appearance probability of each symbol . The optimal entropy value (i.e., bits) is achieved if all the pixels appeared with equal probability, which implies that the pixel distribution is identical. The entropy values of experimented images are given in Table 13, in which the entropy values for the presented cryptosystem are approximately equal to 8. Thus, the presented image cryptosystem has the ability to withstand entropy attacks.

Table 13.
Global information entropy for the examined dataset.
5.2.4. Local Entropy
The global entropy is the average amount of information, so it does not reflect the randomness within each region of the image; i.e., the insufficiency of randomness inside some local regions of the image may be hidden. Therefore, it is recommended to apply another entropy analysis that works at the block level, namely, the local entropy [34]. The local entropy computation is conducted following the steps reported in [34]. The local entropy outcomes are listed in Table 14, where the entropies are very close to the optimal empiric value [34].

Table 14.
Local information entropy for the examined dataset.
5.3. Sensitivity Analysis
A well-designed cryptosystem must present a very high sensitivity of the ciphered image to slight modifications in either the key or the plain image. In this part, we present the suggested cryptosystem sensitivity analyses, including key sensitivity and plaintext sensitivity.
5.3.1. Key Sensitivity
A robust encryption scheme always warrants a high sensitivity to the secret key. That is, any slight change in such a key would provide a diametrically different encrypted image. Figure 8 shows the outcomes of key sensitivity for the proposed image cryptosystem, in which it demonstrates a high sensitivity to the secret key. Consequently, the proposed cryptosystem is extremely sensitive to tiny changes in the secret key.
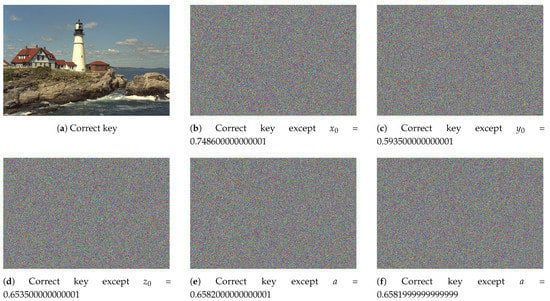
Figure 8.
Outcomes of key sensitivity for the proposed image cryptosystem.
5.3.2. Plaintext Sensitivity
Like the key sensitivity, the plaintext sensitivity measures the rate of changes in the ciphertext when inducing a slight alteration to the plaintext. In this regard, two well-known quantitative tools were used: unified average changing intensity (UACI) and the number of pixel change rate (NPCR). We performed NPCR to calculate the number of different pixels between two ciphered images encrypted with one key and differing only in one bit of the plain image. Whereas the UACI criteria provide the average intensity variation. The NPCR and UACI are represented in (6) and (7), respectively.
where W is the complete number of pixels in the image and is obtained as:
where, and are two ciphered images; the pixel of and are indicated as and , respectively; and n is the number of bits utilized to form a greyscale pixel value. The results of NPCR and UACI values are provided in Table 15. It can be observed from Table 15 that all of the NPCR values are over than , which confirms the high sensitivity of the encryption method, and UACI values for all experimented dataset are very near to , which verifies that the degree of influence is very high. Accordingly, the proposed cryptosystem is immensely sensitive to minor changes in the original image, and no valuable information can be deduced from the algorithm.

Table 15.
NPCR and UACI values for the investigated dataset by changing one bit in the plain image.
5.4. Robustness Analysis
When transmitted over a communication channel, the encrypted images are susceptible to data losses, which causes degradations in the quality of the decrypted images. Furthermore, the transmission channels are noisy, and the encrypted images are susceptible to noise-based attacks. In this part, we present the robustness analyses of the suggested cryptosystem, including occlusion attack and noise attack.
5.4.1. Occlusion Attack
An occlusion attack generally tests an encryption scheme’s ability to retain the original image’s features when the corresponding encrypted image is subjected to a loss of information. Figure 9a–d depict the encrypted images of Lighthouse under data losses of (a) , (b) , (c) , and (d) , respectively. Their decrypted images are displayed in Figure 9e–h, respectively. Although half of the encrypted image information is lost, the corresponding decrypted image reserves enough visual information of the original image. As a result, the proposed cryptosystem can resist occlusion-based attacks.
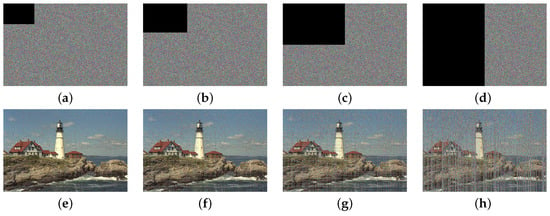
Figure 9.
Occlusion attacks: encrypted images with (a) , (b) , (c) , and (d) data loss; their corresponding decrypted images (e–h).
5.4.2. Noise Attack
A strong encryption scheme should not be concerned with such noises. To check the robustness of the proposed cryptosystem to noise-based attacks, the encrypted image of the Lighthouse is tainted by the salt and pepper noise with several densities. The corresponding decrypted images are displayed in Figure 10. It is shown that the image maintains the original image’s features, although the noise density is set to 0.3. Therefore, the proposed cryptosystem exhibits strong immunity against noise-based attacks.

Figure 10.
Decrypted images undergo the salt and pepper noise with a density of: (a) 0.005, (b) 0.05, (c) 0.100, and (d) 0.300.
5.5. Known-Plaintext and Chosen-Plaintext Attacks
The main task of cryptanalysis is to recover the entire secret key or some parts of it to completely or partially decipher the ciphertexts produced by a given encryption scheme. Moreover, in some attack scenarios, the attacker can retrieve the correct plaintext from a given ciphertext without needing the secret key. Indeed, he/she tries to find any similarities between plaintexts and ciphertexts. According to how the cryptanalyst performed such a search, four different attacks are presented and listed here from the hardest to the easiest attacks: the ciphertext-only attack, the known-plaintext attack, the chosen-plaintext attack, and the chosen-ciphertext attack. Among these attacks, the known-plaintext and chosen-plaintext attacks are considered the powerful ones, and if an encryption scheme can withstand them, it can resist the other attacks as well. In the proposed cryptosystem, the secret key is fully correlated to the input image, which leads to a unique key for each different image. Accordingly, the cryptanalyst cannot establish any link between plaintext/ciphertext pairs. The proposed cryptosystem has the power to hold facing known-plaintext and chosen-plaintext attacks.
5.6. Comparative and Speed Analysis
To appraise our image cryptosystem’s performance, its experimental outcomes are compared to other related encryption schemes. Table 16 provides a comparison analysis, proving our encryption mechanism’s high performance. Apart from performance and security evaluations of the presented approach, a speed performance is also needed. Table 17 provides the speed performance of our cryptosystem and the competitive image cryptosystem for various sizes of grey-scale of images as reported in [35]. Table 16 and Table 17 confirm the supremacy of our cryptosystem alongside those related image cryptosystems.

Table 16.
Comparative study of the average values of information entropy, correlation coefficients, UACI, and NPCR of the suggested cryptosystem image with respect of other similar cryptosystems.

Table 17.
Comparative analysis of encryption speed (ms) for the suggested cryptosystem and other cryptosystems.
6. Conclusions
A new approach to building a strong S-box using a 3D chaotic map was presented in this paper. The performance results show that the presented S-box has better cryptographic features than prior S-box approaches. Furthermore, a new chaotic-based image cryptosystem using the proposed S-Box and Gray code was introduced. It employs a key generation process that relies on the input image and acts as its signature to make high key sensibility. Various numerical and simulation methods were used to analyze the performance of the proposed image encryption approach. We will focus on designing a new video encryption scheme using the presented S-Box, chaotic maps, and Gray code in the near future.
Author Contributions
Conceptualization, A.A.A.E.-L. and B.A.-E.-A.; methodology, A.A.A.E.-L. and B.A.-E.-A.; software, A.A.A.E.-L. and B.A.-E.-A.; validation, A.B. and A.M.I.; formal analysis, A.A.A.E.-L. and B.A.-E.-A.; investigation, B.A.-E.-A. and A.B.; resources, A.M.I.; data curation, A.B., and A.M.I.; writing–original draft preparation, A.A.A.E.-L. and B.A.-E.-A.; writing–review and editing, A.A.A.E.-L., B.A.-E.-A. and A.M.I.; visualization, A.B.; supervision, A.A.A.E.-L. and A.M.I.; project administration, A.B. and A.M.I.; funding acquisition, A.M.I. All authors have read and agreed to the published version of the manuscript.
Funding
This study is sponsored by the Prince Sattam Bin Abdulaziz University, SaudiArabia via the Deanship for Scientific Research funding for the Advanced Computational Intelligence and Intelligent Systems Engineering (ACIISE) Research Group Project Number 2020/01/12173.
Data Availability Statement
Data is available on request to any of the corresponding authors.
Acknowledgments
This study is sponsored by the Prince Sattam Bin Abdulaziz University, Saudi Arabia via the Deanship for Scientific Research funding for the Advanced Computational Intelligence and Intelligent Systems Engineering (ACIISE) Research Group Project Number 2020/01/12173. A. A. Abd El-Latif acknowledge support from the Menoufia University, Egypt.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Alanezi, A.; Abd-El-Atty, B.; Kolivand, H.; El-Latif, A.A.A.; El-Rahiem, B.A.; Sankar, S.; Khalifa, H.S. Securing Digital Images through Simple Permutation-Substitution Mechanism in Cloud-Based Smart City Environment. Secur. Commun. Netw. 2021, 2021, 6615512. [Google Scholar] [CrossRef]
- Abd EL-Latif, A.A.; Abd-El-Atty, B.; Venegas-Andraca, S.E. A novel image steganography technique based on quantum substitution boxes. Opt. Laser Technol. 2019, 116, 92–102. [Google Scholar] [CrossRef]
- Li, H.; Wang, Y.; Zuo, Z. Chaos-based image encryption algorithm with orbit perturbation and dynamic state variable selection mechanisms. Opt. Lasers Eng. 2019, 115, 197–207. [Google Scholar] [CrossRef]
- Ding, L.; Ding, Q. A Novel Image Encryption Scheme Based on 2D Fractional Chaotic Map, DWT and 4D Hyper-chaos. Electronics 2020, 9, 1280. [Google Scholar] [CrossRef]
- Hernández-Díaz, E.; Pérez-Meana, H.; Silva-García, V.; Flores-Carapia, R. JPEG Images Encryption Scheme Using Elliptic Curves and A New S-Box Generated by Chaos. Electronics 2021, 10, 413. [Google Scholar] [CrossRef]
- Batouty, A.S.E.; Farag, H.H.; Mokhtar, A.A.; El-Badawy, E.S.A.; Aly, M.H. Improvement of Radio Frequency Identification Security Using New Hybrid Advanced Encryption Standard Substitution Box by Chaotic Maps. Electronics 2020, 9, 1168. [Google Scholar] [CrossRef]
- Jakimoski, G.; Kocarev, L. Chaos and cryptography: Block encryption ciphers based on chaotic maps. IEEE Trans. Circuits Syst. I Fundam. Theory Appl. 2001, 48, 163–169. [Google Scholar] [CrossRef]
- Zhou, Y.; Bao, L.; Chen, C.P. A new 1D chaotic system for image encryption. Signal Process. 2014, 97, 172–182. [Google Scholar] [CrossRef]
- Liu, H.; Kadir, A.; Niu, Y. Chaos-based color image block encryption scheme using S-box. AEU-Int. J. Electron. Commun. 2014, 68, 676–686. [Google Scholar] [CrossRef]
- Tsafack, N.; Kengne, J.; Abd-El-Atty, B.; Iliyasu, A.M.; Hirota, K.; Abd EL-Latif, A.A. Design and implementation of a simple dynamical 4-D chaotic circuit with applications in image encryption. Inf. Sci. 2020, 515, 191–217. [Google Scholar] [CrossRef]
- Abd-El-Atty, B.; Amin, M.; Abd-El-Latif, A.; Ugail, H.; Mehmood, I. An Efficient Cryptosystem based on the Logistic-Chebyshev Map. In Proceedings of the 2019 13th International Conference on Software, Knowledge, Information Management and Applications (SKIMA), Island of Ulkulhas, Maldives, 26–28 August 2019; pp. 1–6. [Google Scholar]
- Aslam, M.N.; Belazi, A.; Kharbech, S.; Talha, M.; Xiang, W. Fourth order MCA and chaos-based image encryption scheme. IEEE Access 2019, 7, 66395–66409. [Google Scholar]
- Belazi, A.; Rhouma, R.; Belghith, S. A novel approach to construct S-box based on Rossler system. In Proceedings of the 2015 International Wireless Communications and Mobile Computing Conference (IWCMC), Dubrovnik, Croatia, 24–28 August 2015; pp. 611–615. [Google Scholar]
- Tang, G.; Liao, X.; Chen, Y. A novel method for designing S-boxes based on chaotic maps. Chaos Solitons Fractals 2005, 23, 413–419. [Google Scholar] [CrossRef]
- Chen, G.; Chen, Y.; Liao, X. An extended method for obtaining S-boxes based on three-dimensional chaotic Baker maps. Chaos Solitons Fractals 2007, 31, 571–579. [Google Scholar] [CrossRef]
- Özkaynak, F.; Özer, A.B. A method for designing strong S-Boxes based on chaotic Lorenz system. Phys. Lett. A 2010, 374, 3733–3738. [Google Scholar] [CrossRef]
- Khan, M.; Shah, T.; Mahmood, H.; Gondal, M.A. An efficient method for the construction of block cipher with multi-chaotic systems. Nonlinear Dyn. 2013, 71, 489–492. [Google Scholar] [CrossRef]
- Tlelo-Cuautle, E.; de la Fraga, L.G.; Pham, V.T.; Volos, C.; Jafari, S.; de Jesus Quintas-Valles, A. Dynamics, FPGA realization and application of a chaotic system with an infinite number of equilibrium points. Nonlinear Dyn. 2017, 89, 1129–1139. [Google Scholar] [CrossRef]
- Abd el Latif, A.A.; Abd-el Atty, B.; Amin, M.; Iliyasu, A.M. Quantum-inspired cascaded discrete-time quantum walks with induced chaotic dynamics and cryptographic applications. Sci. Rep. 2020, 10, 1–16. [Google Scholar]
- Tsafack, N.; Sankar, S.; Abd-El-Atty, B.; Kengne, J.; Jithin, K.; Belazi, A.; Mehmood, I.; Bashir, A.K.; Song, O.Y.; Abd El-Latif, A.A. A new chaotic map with dynamic analysis and encryption application in internet of health things. IEEE Access 2020, 8, 137731–137744. [Google Scholar] [CrossRef]
- Sambas, A.; Vaidyanathan, S.; Tlelo-Cuautle, E.; Abd-El-Atty, B.; Abd El-Latif, A.A.; Guillén-Fernández, O.; Hidayat, Y.; Gundara, G. A 3-D multi-stable system with a peanut-shaped equilibrium curve: Circuit design, FPGA realization, and an application to image encryption. IEEE Access 2020, 8, 137116–137132. [Google Scholar] [CrossRef]
- Zhou, G.; Zhang, D.; Liu, Y.; Yuan, Y.; Liu, Q. A novel image encryption algorithm based on chaos and Line map. Neurocomputing 2015, 169, 150–157. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y.; Pun, C.M.; Chen, C.P. 2D Sine Logistic modulation map for image encryption. Inf. Sci. 2015, 297, 80–94. [Google Scholar] [CrossRef]
- Liu, H.; Wang, X.; Kadir, A. Color image encryption using Choquet fuzzy integral and hyper chaotic system. Opt. Int. J. Light Electron Opt. 2013, 124, 3527–3533. [Google Scholar] [CrossRef]
- Gu, G.; Ling, J. A fast image encryption method by using chaotic 3D cat maps. Opt. Int. J. Light Electron Opt. 2014, 125, 4700–4705. [Google Scholar] [CrossRef]
- Li, C.; Lo, K.T. Optimal quantitative cryptanalysis of permutation-only multimedia ciphers against plaintext attacks. Signal Process. 2011, 91, 949–954. [Google Scholar] [CrossRef]
- Bechikh, R.; Hermassi, H.; El-Latif, A.A.A.; Rhouma, R.; Belghith, S. Breaking an image encryption scheme based on a spatiotemporal chaotic system. Signal Process. Image Commun. 2015, 39, 151–158. [Google Scholar] [CrossRef]
- Zhang, Y. Comments on “Color image encryption using Choquet fuzzy integral and hyper chaotic system”. Opt. Int. J. Light Electron Opt. 2014, 125, 5560–5565. [Google Scholar] [CrossRef]
- Wang, Y.; Xie, Q.; Wu, Y.; Du, B. A software for S-box performance analysis and test. In Proceedings of the ECBI 2009 International Conference on Electronic Commerce and Business Intelligence, Beijing, China, 6–7 June 2009; pp. 125–128. [Google Scholar]
- Biham, E.; Shamir, A. Differential cryptanalysis of DES-like cryptosystems. J. Cryptol. 1991, 4, 3–72. [Google Scholar] [CrossRef]
- Belazi, A.; Abd El-Latif, A.A. A simple yet efficient S-box method based on chaotic sine map. Opt. Int. J. Light Electron Opt. 2017, 130, 1438–1444. [Google Scholar] [CrossRef]
- Wang, Y.; Wong, K.W.; Li, C.; Li, Y. A novel method to design S-box based on chaotic map and genetic algorithm. Phys. Lett. A 2012, 376, 827–833. [Google Scholar] [CrossRef]
- Kodak Lossless True Color Image Suite. Available online: http://r0k.us/graphics/kodak/ (accessed on 20 June 2020).
- Wu, Y.; Zhou, Y.; Saveriades, G.; Agaian, S.; Noonan, J.P.; Natarajan, P. Local Shannon entropy measure with statistical tests for image randomness. Inf. Sci. 2013, 222, 323–342. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y. Design of image cipher using block-based scrambling and image filtering. Inf. Sci. 2017, 396, 97–113. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y.; Huang, H. Cosine-transform-based chaotic system for image encryption. Inf. Sci. 2019, 480, 403–419. [Google Scholar] [CrossRef]
- Wang, X.; Liu, L.; Zhang, Y. A novel chaotic block image encryption algorithm based on dynamic random growth technique. Opt. Lasers Eng. 2015, 66, 10–18. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).