Abstract
With quantum computers, the quantum resistance of cryptographic systems has gradually attracted attention. To overcome the shortcoming of existing identity-based encryption (IBE) schemes in resisting quantum attacks, we introduce an IBE scheme based on learning with errors (LWE). In addition, devices with limited computing power are becoming increasingly common in practice, making it increasingly important to improve the efficiency of online computation of encryption algorithms. The classic solution is to directly improve the efficiency of the Gaussian sampling algorithm, thereby increasing the overall efficiency of the scheme. However, our scheme combines the efficient Gaussian sampling algorithm, -trapdoor, with online/offline method to further improve the online encryption efficiency of the encryption algorithm. Our scheme completes partial computation before knowing the message and receiver’s identity, and once the message and receiver’s identity are obtained, the online part encryption can be efficiently completed. We construct an identity-based online/offline encryption (IBOOE) scheme from LWE with -trapdoor, improve the efficiency of online encryption while achieving quantum resistant security. We prove the scheme’s security under the standard model for chosen-plaintext attack (CPA). By comparing with relevant schemes in terms of experiments and analysis, our scheme has improved efficiency by 65% to 80% compared to the classical LWE IBE scheme (increasing with LWE security parameters), and by 60% to 70% compared to the recent IBE scheme from LWE. This greatly improves the efficiency of online computing for low-power encryption devices while ensuring security.
1. Introduction
In IBE schemes, user submits an arbitrary string corresponding to the identity to key generation center (KGC). This user’s private key which is authenticated is generated by the KGC and corresponds to the identity. Encrypting messages only requires knowing the identity of the recipient. This process does not require verifying the correctness of credentials in traditional public key architectures, especially for energy limited devices. With quantum computers’ computing technology, traditional encryption algorithms face the danger of being attacked by quantum computers. However, traditional IBE schemes do not have quantum resistant security.
Lattice-based cryptography system has the characteristics of simple structure and complex mathematics, and is the most prospective type of anti-quantum cryptography technology. The lattice-based IBE schemes deserve further research due to the excellent performance in practical application scenarios and scalability advantages. Gentry, Peikert, and Vaikuntanathan [1] designed an approach for lattice-based signature algorithms and proved the method’s security under the random oracle model; we abbreviate their scheme to GPV scheme. Cash et al. [2] proposed the LWE IBE scheme and proved this anti-quantum IBE scheme’s security under the standard model. Furthermore, Agrawal et al. [3] brought up an anti-quantum IBE scheme based on lattice under the standard model. In line with Agrawal et al.’s [3] work, their scheme has a simpler construct and shorter ciphertext compared to Cash et al.’s [2] scheme. Agrawal et al. treated identity as a chunk, and the lattice in their scheme consists of “left” and “right” lattices. The trapdoor for the left lattice is the true trapdoor for generating secrete keys, while the trapdoor for the right lattice is only used in security proof. Our scheme learns their idea of trapdoor generation and further improves based on it.
However, the current IBE algorithm based on lattice structure still has shortcomings in computational efficiency. The biggest reason is that lattice-based encryption schemes are closely related to Gaussian sampling, and thus, many efficiency improvement schemes focus on improving the efficiency of Gaussian sampling. Since the current implementations of Gaussian sampling are still achieved through extensive simulations to infinitely approximate Gaussian distributions, which still affects the overall computational efficiency. In an effort to carry the efficiency of existing lattice-based IBE schemes to a new and higher level, we apply online/offline method to delegate most of the Gaussian sampling and the parts that do not require identity and message knowledge to powerful devices for offline computation.
1.1. Our Motivation and Contributions
Although existing IBE schemes can protect the confidentiality of data without checking certificates, they cannot resist attacks from quantum computers. To address this issue, an anti-quantum IBE scheme can be achieved by constructing on LWE, the classic hard problem on lattice. However, the current LWE based IBE schemes are less efficient. Thus, we propose an IBOOE scheme based on LWE; the offline phase completes Gaussian sampling before obtaining the message to be encrypted and identity. In this way, our scheme ensures the efficiency of the scheme while achieving anti-quantum security. Our contributions are shown below.
- (1)
- We first investigate the coexistence of anti-quantum security and efficiency in the IBE system, and design an IBOOE scheme from the LWE problem.
- (2)
- We then construct our concrete IBOOE scheme from LWE and prove the CPA secure under the standard model.
- (3)
- Finally, we aim to test the feasibility and effectiveness of our scheme through the contrast of the original scheme [3], our scheme, and the recent anti-quantum IBE scheme [4].
1.2. Paper Organization
The rest of this article is organized as follows. We introduce the relevant work of our paper in Section 2. In Section 3, we introduce some concepts and related definitions, and describe the security model and system architecture. In Section 4, we propose the construction of our efficient IBOOE based on LWE and analyze its correctness and security. In Section 5, we compare our scheme with classical and recent LWE based IBE schemes. In Section 6, we conclude this article.
2. Related Work
The GPV scheme [1] provided the underlying scheme for the lattice-based IBE cryptographic algorithms. Regev [5] presented a typical lattice difficulty problem, the LWE problem. In the research of anti-quantum cryptography schemes, especially for IBE schemes, considering quantum circuits’ aspect, the proof of GPV scheme is conducted solely under the random oracle model, but without considering the security proof under the random oracle model from quantum technology. Zhandry [6] developed a new technology for random oracle model from the quantum technology, and then demonstrated that the GPV scheme is secure under the random oracle model from the quantum technology. Katsumata et al. [7] then provided more rigid proof for GPV scheme under the random oracle model from quantum technology. While Gao et al. [8] first constructed anti-quantum IBE scheme from LWE and a quantum circuit, they proved their quantum IBE scheme’s security under the random oracle model. Moreover, considering the enlargement of anti-quantum cryptography schemes in terms of functionality, Dutta et al. [9] first brought up the specific unidirectional construction of the proxy-re-encryption-based identity from LWE; they then proved under the standard model that the scheme is secure. In addition, for the sake of strengthening the security of proxy-re-encryption-based identity, on this basis, Wu et al. [10] added a function called re-encryption verifiability, which is a proxy re-encryption IBE scheme from basic lattice. Liu et al. [11] then extended the concept of server-aided revocable IBE to hierarchical IBE. In order to withstand side channel attack, Li et al. [12,13,14,15] presented some identity-based encryption schemes with leakage resilience. Furthermore, in terms of extending LWE itself, Abla et al. [16] brought up an IBE scheme based on ring LWE, with shorter main public key and stricter security analysis. Conversely, Fan et al. [17] brought up an adaptively secure scheme under the standard model, which is a fresh anti-quantum IBE scheme for middle product LWE. In addition, Lai et al. [18] promoted two-stage sampling approach of the GPV scheme, and proposed the new lattice two-stage sampling technology, which added noise not only to the ciphertext, but also to the key.
However, most of the current IBE schemes are inefficient, and they take up a lot of storage space. In terms of storage, the main issue is each user’s ID has a parameter matrix, which yields a sharp increase in the scale of the system’s public parameters. Zhang et al. [4] proposed a flexible trade-off mechanism using blocking technology to balance the scale of common parameters and the computational cost involved. They divide the identity into multiple parts and associate each part with a matrix, while slightly increasing the modulus of the lattice to maintain the same level of security. In the Gaussian sampling aspect, Weiden et al. [19] displayed that the running time consumed by Gaussian sampling accounts for half of the Lyubashevsky’s lattice signature scheme [20]. For the sake of improving the efficiency of Gaussian sampling, Micciancio and Peikert [21] brought up a new approach for generating a trapdoor in the lattice, which is more efficient with smaller hidden constants; this trapdoor is called -trapdoor. This method of generating trapdoors is more efficient because it does not involve any expensive Hermite normal form or matrix inversion computations. Next, Micciancio and Walter [22] developed a new Gaussian sampling algorithm and the algorithm is applicable to arbitrary and variable Gaussian distributions. By implementing more efficient Gaussian sampling, lattice-based cryptographic algorithms can be more widely applied. Furthermore, Sun et al. [23] also proposed a secure and efficient exponential Bernoulli sampling algorithm to achieve universal, efficient, and synchronized Gaussian sampling of integers.
Significantly, in the sake of improving the expense of Gaussian sampling in lattice encryption algorithms, the online/offline method is also an effective way. In 2008, Guo et al. [24] first brought up the IBOOE scheme. The principal idea is to complete computing that consume a lot of resources in the offline part through powerful devices. These calculations do not require knowledge of messages and identities. Under this mindset, we propose an online/offline IBE scheme from LWE with -trapdoor, complete Gaussian sampling during the offline phase. The offline part can be completed by powerful devices without the need to know identity and messages.
3. Preliminaries
We take values from the finite set , and let and be random variables. Furthermore, the statistical distance between A and B, two ensembles of distributions indexed by s, is . For an uniform and random variable from , if we have , then we have the random variable is -uniform over . More specifically, we let and be the two sets of random variables. Furthermore, set , if is an ignorable function of , and in this way, we have that and are statistically approaching.
For vectors . norm is the shortest distance to go from one point to another, which is the sum of squared differences between points. indicates the S’s longest vector’s length. indicates the Gram–Schmidt orthogonalization of the ordered vectors as in above sequence.
We let be n linearly independent vectors and . Furthermore, the following additive discrete subgroup is called an n-dimensional lattice which is generated by :
For the three positive integers , and q, where q is a prime number, we define and , and consider two kinds of n-dimensional lattices defined by . The transposed rows of generates the first lattice and the first lattice is defined as:
Those integer vectors are “orthogonal” under the modulus q to the rows of . Furthermore, they constitute the second lattice. The second lattice is defined as:
Moreover, we let for the arbitrary be the coset.
For and , the Gaussian function is defined as . Then, we let for any fixed countably subset . Next, the discrete Gaussian distribution for arbitrary is defined as .
Definition 1.
Let over for an indicates the distribution of the random variable and a prime number q, means , where A is a normal random variable, the mean of A is zero, and the standard deviation of A is .
Definition 2.
For a prime number , a positive integer , and the distribution in , the ()-LWE problem is for the oracle access of samples, to differentiate between the distribution and the uniform distribution over , where , and .
Theorem 1
([5]). There is an efficient algorithm for approaching the SIVP and the GapSVP problems in the worst case, to within factors in the norm, if for resolving the -LWE problem with there exists an effective, probable quantum algorithm.
3.1. Framework and Security of IBOOE
Our IBOOE scheme is made up of the following five probabilistic polynomial-time (PPT) algorithms as below.
: In the setup phase, it takes security parameter as the input, sets plaintext space and ciphertext space, then manufactures the global public parameters for following algorithms and the master secret key for the KGC.
: In the process of extracting secret key, it takes public parameters , the master secret key and the for generating the secret key , and corresponds to the identity .
: During the offline encrypting phase, it takes public parameters as input for generating the offline ciphertext .
: During the online encrypting phase, it takes public parameters , the message , the offline ciphertext , and the as inputs for generating online ciphertext .
: In the decrypting phase, it takes public parameters , the ciphertext and the secret key of the receiver, whose identity is as inputs for decrypting the message .
For the security proof of our construction, we reduce our lattice based IBE scheme to a classical difficult problem on lattices, the LWE problem.
The ()-LWE problem permits repetitive queries to the given challenge oracle . Furthermore, we say that if the following:
is non-ignorable for the random s from , then the algorithm resolves the ()-LWE problem. returns the real LWE sample and is for the random case. The means the probability of guessing correctly when accesses . The same applies to .
In order to ensure strong privacy in our IBOOE scheme, we describe a game that caches a character called “indistinguishable from random”. This implies that the challenge ciphertext from the ciphertext space appears to be a random element, making it difficult to decipher. For the security parameter , we define the scheme’s message space as and the scheme’s ciphertext space as . How the game works is described below.
: In the initial phase, the adversary first outputs its target identity .
: In the setup phase, the challenger then runs the algorithm and gives the adversary public parameters . Furthermore, the challenger keeps the master key to itself.
: In the first phase, the adversary sends private key queries and the query is for . We request that cannot equal to . For private key corresponds to the identity , and the challenger runs algorithm to respond. Then, the challenger sends to . The above queries are all adaptive.
: After adversary judgement of that the first phase is completed, a plaintext will be output. Furthermore, this is the plaintext that intends to be challenged. Then, for the following simulation, the challenger chooses the random bit corresponding to different situation, and the challenger also chooses a random ciphertext .
- (1)
- For , challenger uses algorithm for setting challenge ciphertext as .
- (2)
- For , the challenger directly uses the challenge ciphertext chosen before and setsThe challenger then sends as the ciphertext for challenge to adversary .
: Then, in the second phase, the adversary adaptively sends the supplemental queries from to r, and the query corresponds to the private key extraction query, where cannot be equivalent to . Just like in phase 1, the challenger sends to adversary .
: Lastly, adversary sends the guess as its output for result that the challenger chose before. wins the game when . For the positive of adversary for attacking an IBE scheme, we define it as:
The possibility of the adversary winning depends on the random bits which are used by the challenger and the adversary .
Definition 3.
If for every INDr-sID-CPA PPT adversary we have , which is an ignorable function, then we are able to say that an IBE scheme is selective-identity, indistinguishable from random.
Lastly, we define the corresponding adaptive identity of our aforesaid concept, that is, in the attack game process, the init phase is removed so that the adversary can reveal the that it wants to attack, namely its target identity, until the challenge phase. In the first phase, we permit the adversary to send random private key queries and then the adversary selects the random target identity . Furthermore, the only limitation is that in the phase 1, the adversary will not send the private key query for . Our security concept obtained in this way is defined in Definition 3, which is defined as INDr-ID-CPA.
3.2. Sampling Algorithms
For , q is an odd number, , namely the result of rounding up . We denote the as . Let be a public matrix and ⊗ means tensor product. The -trapdoor for the lattice was proposed in the scheme [21].
Definition 4
([21]). Given a matrix with , q is an odd number. If there pertains some invertible matrix , and we have , then is named a -trapdoor for . We say that the greatest singular value of is denoted as , and the quality of this trapdoor is judged by
Theorem 2
([21]). Let and is invertible matrix. For and , there is a randomized algorithm , and the algorithm’s output is a parity-check matrix with -trapdoor . The distribution of approximately follows uniform distribution.
Moreover, for any and sufficiently large , randomized algorithm , which outputs sampling results from distribution within statistical distance.
Lemma 1
([3]). Suppose that , where and q is a prime number. Let matrix be an uniform matrix from mod q. Let and be two uniform matrices from and separately. Then, for all of the vectors w from , the distribution and the distribution is statistically approaching.
We look back at some sampling algorithms from [3,21]. Let be matrices in , the matrix , and . Set , .
- –
- For matrix and its -trapdoor , matrix , vector and parameter , the algorithm outputs a vector distributed statistically approaching to .
- –
- For matrix and its -trapdoor , matrix , uniformly random matrix from , vector , and parameter , the algorithm outputs a vector distributed statistically close to .
3.3. Encoding Identities as Matrices
The encoding function : is used to map identities in to matrices in . is an explicit full-rank differences (FRD) construction, which means for all different and from , the matrix is full-rank. Furthermore, the method is to build an additive subgroup from of size . All of the non-zero matrices from are full-rank. In this way, for all different , the difference between them is also in , as a consequence, is full-rank.
Although we are primarily interested in the finite field , we represent the structure of a random field . In cases where polynomial of degree less than r, we define the r-vector of coefficients of f as ces(f) and express it as a row vector. However, in cases where f is of degree less than , we add zeroes to the right of the coefficients vector, so it becomes r-vector. The case in point is, for r = 8 we have ces() = (1, 0, 7, 0, 0, 1, 0, 0) . We let p of degree r be some irreducible polynomial from . Think back that the polynomial f from mod p has degree less than r, consequently, the ces(f mod p) is a vector from .
Yet, for an input , the polynomial . We define as:
Because for all of the prime numbers q and the integer , there are irreducible polynomials of degree r from , and the structure can cater for any pair of q and r.
Theorem 3
([25]). Let be a field and the p is a polynomial from . The function is an encoding with FRD, if the p is irreducible from .
Let , and . The function , where , works as below.
Theorem 3 proves that for all prime numbers q, the function is FRD, where is irreducible from .
4. New Lattice-Identity-Based Online/Offline Encryption
The construction of our lattice based IBOOE scheme is on the basis of the following idea. In the offline phase, we generate offline ciphertext with high computational complexity and no need to know identity and messages. During the online phase, we generate online ciphertext by using identity, messages, and offline ciphertext.
4.1. Construction
As shown in Figure 1, in our IBOOE scheme, KGC generates public parameters and master secert key. With the master secret key, KGC generates the private key for the Data User. For performing the offline encryption operation, the Offline Server completes Gaussian sampling and sends offline ciphertext to the Data Owner. Using the offline ciphertext, the Data Owner completes online encryption with the Data User’s and the message . The Data User decrypts ciphertext for the final message . The concrete algorithms are as below.
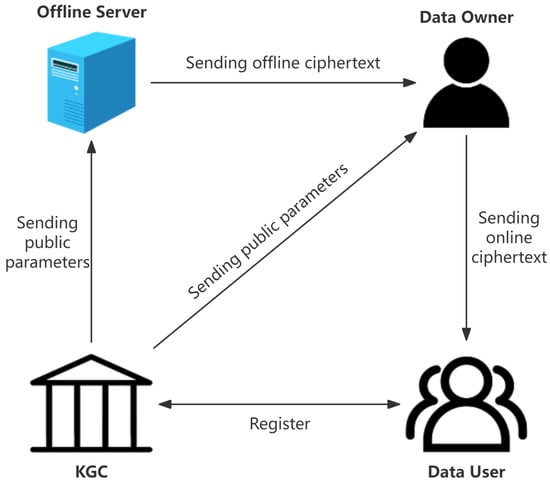
Figure 1.
Our IBOOE scheme’s architecture.
: KGC takes r to be the security parameter, sets , . Then, it rounds up n to next larger integer and rounds up q to next larger prime number. Among above formulas, is for . By using algorithm , it selects a uniform and random -matrix with the -trapdoor as defined in Definition 4. It then selects two uniform and random matrices in . It selects a uniform and random r-vector ∂ in . Lastly, KGC outputs public parameters and the master key :
: KGC takes public parameters , the master key , and an identity as inputs, then KGC samples as:
In the above formula, is the FRD map as described in Section 3.3 and is distributed as . Let , which means . For the chosen , KGC outputs the following secret key:
: The Offline Server takes public parameters as input and completes Gaussian sampling, which does not need the identity and the message that needs to be encrypted in following online algorithm. It also chooses the uniform and random vector and the uniform and random matrix from . It also chooses and for noise vectors, which both follow the distribution of Definition 1, and set . Offline Server computes and and stores the offline ciphertext for the online phase:
: The Data Owner takes , identity , and a message as inputs. Then, it sets as . It also sets and . The Data Owner outputs the online ciphertext:
: The Data User takes public parameters , the private key , and the online ciphertext as inputs, it then computes in . It compares and , the downward rounding of , treat them as integers from . If the two integers are approaching, namely, if from , output 1, otherwise output 0.
In the above encryption, the matrix has significant importance in security proof. The matrix is a tool for a specific distribution required by the simulation, which is used to sample noise vectors ().
4.2. Parameters and Correctness
We define our scheme’s correctness below.
If , the algorithm runs as and ciphertexts generated as , , then outputs “” with an overwhelming probability.
Proof.
When our scheme is operated as specified, during decryption, we have:
For recovering correctly, we can compute the error term as , and it needs to be less than . Since and , we have and . For is sampled by , we have . Let , with the error term as follows:
For a random matrix chosen from , we have . Since ([3]), the error term is then limited by:
In order for the system to function properly, we must make sure that the error term described as above in is lower than . needs and to operate correctly. and need to be large enough, . Furthermore, our security proof needs .
For the sake of meeting the requirements of accuracy and safety, we set the parameters as follows, using r as security parameter:
which round up n to the next greater integer, and round up q to the next greater prime number. Furthermore, is for . □
4.3. Security Proof
We demonstrate that our IBOOE scheme is indistinguishable from randomness under the selective identity attack in Definition 3. Being indistinguishable from randomness implies that, in the ciphertext space, the challenge ciphertext cannot be distinguished from randomly selected elements in the ciphertext space.
Theorem 4.
If the -LWE assumption holds true, the IBOOE scheme is secure for INDr-sID-CPA.
Proof.
Our security proof follows a series of games, where the first one of these games is identical as INDr-sID-CPA game, which is described in Definition 3. Furthermore, the adversary has no positive in the final game. Because when the adversary gets the ciphertext in the last game, it is always a randomly selected element from ciphertext space. We demonstrate that the upside of the PPT adversary winning the rudimentary INDr-sID-CPA game is ignorable by demonstrating that the adversary cannot distinguish the series of games presented below. The proof of indistinguishability between the Game 2 and the Game 3 is reduced to the LWE difficulty problem. □
- : The Game 0 is between the adversary for our scheme and the INDr-sID-CPA challenger, it is just as described in Definition 3, namely the original game.
- :
: In the initial phase, the adversary first outputs its target identity .
: In the setup phase, the challenger then runs algorithm and chooses to construct as:
The challenger provides the system public parameters to the adversary and keeps the master key secrete from .
: In the first phase, the adversary sends the private key queries to the challenger and the query is for . We request that cannot equal to . For private key which corresponds to the identity , the challenger runs algorithm to respond. The challenger sends to . The above queries are all adaptive.
: After the adversary’s judgment of the first phase is completed, a plaintext will be output. Furthermore, this is the plaintext that intends to be challenged. Then, for the following simulation, the challenger selects a random bit corresponding to a different situation, and it also picks a random ciphertext .
- (1)
- For , the challenger uses algorithm for setting the challenge ciphertext as (,,M).
- (2)
- For , the challenger directly uses the ciphertext chosen before and sets
The challenger then sends as the ciphertext for challenge to adversary .
: Then, in the second phase, the adversary adaptively sends supplemental queries from to r, and the query corresponds to the private key extraction query, where cannot be equivalent to . Just like in phase 1, the challenger sends to adversary .
: Lastly, the adversary sends the guess as its output for result that the challenger chose before. wins the game when . For the positive of adversary for attacking an IBE scheme, we define it as:
- :
: In the initial phase, the adversary first outputs its target identity .
: In the setup phase, the challenger then runs algorithm , generates as a random matrix and generates using with -trapdoor , and constructs . The challenger provides the system public parameters to the adversary and keeps the master key secrete from .
: In the first phase, the adversary sends the private key queries to the challenger and the query is for . We request that cannot equal to . For the private key , which corresponds to the identity , the challenger runs to respond. During , the challenger uses to get where:
The challenger then sends to . The above queries are all adaptive.
: After the adversary’s judgement of the first phase is completed, a plaintext will be output. Furthermore, this is the plaintext that wants to be challenged. Then, for the following simulation, the challenger selects a random bit corresponding to different situation, and it also picks a random ciphertext .
- (1)
- For , the challenger uses algorithm for setting challenge ciphertext as (,,M).
- (2)
- For , the challenger directly uses the ciphertext chosen before and sets
The challenger then sends to adversary .
: Then, in the second phase, the adversary adaptively sends the supplemental queries from to r, and the query corresponds to the private key extraction query, where cannot be equivalent to . Just like in phase 1, challenger sends to adversary .
: Lastly, the adversary sends the guess as its output for result that the challenger chose before. wins the game when . For the positive of adversary for attacking the IBE scheme, we define it as
- :
: In the initial phase, the adversary first outputs its target identity .
: The challenger then runs algorithm , generates as a random matrix and generates the matrix using with -trapdoor , and constructs . The challenger provides the system public parameters to the adversary and keeps the master key secrete from .
: In the first phase, the adversary sends the private key queries to the challenger and the query is for . We request that cannot equal to . The private key corresponds to the identity , and the challenger runs to respond. During , the challenger uses to get where is as in Formula (2). The challenger sends to . The above queries are all adaptive.
: After the adversary’s judgement of the first phase is completed, a plaintext will be output. Furthermore, this is the plaintext that wants to be challenged. Then, for the following simulation, the challenger selects a random bit corresponding to different situation, and it also picks a random ciphertext , but always sets the challenge ciphertext as .
The challenger then sends to adversary .
: In the second phase, the adversary adaptively sends the supplemental queries from to r, and the query corresponds to the private key extraction query, where cannot be equivalent to . Just like in phase 1, the challenger responds to adversary .
: Lastly, the adversary sends the guess as its output for the result that challenger chose before. wins the game when . For the positive of adversary for attacking an IBE scheme, we define it as
Theorem 5.
Game 0 and Game 1 are statistically indistinguishable.
Proof.
The challenger uses random matrices to generate public parameters and the trapdoor in Game 0. The challenger generates challenge ciphertext during the challenge phase. We use from to represent a random matrix, which is used to generate .
The challenger chooses and constructs as in Formula (1) in Game 1. Furthermore, identity is the identity which will be attacked by . This means we change a little in how the challenger generates the matrix in public parameters.
Lemma 1 shows that Game 0 is statistically indistinguishable from Game 1. We use martix for constructing and challenge ciphertext in Game 1. We are able to know that the distribution () is statistically approaching to () by Lemma 1. The is a uniform matrix from . In this way, matrix is statistically approaching to the uniform one in ’s view. Therefore, the as defined in Formula (1) is also approaching to the uniform one. As a result, are indistinguishable in the Game 0 and the Game 1. □
Theorem 6.
Game 1 and Game 2 are statistically indistinguishable.
Proof.
We construct matrix as a random matrix in Game 2, and for , we generate it by running algorithm with -trapdoor . Construct as in Game 1. For private key queries, the challenger uses matrix to respond. Furthermore, for , for the sake of answering the private key queries, the challenger uses the short vector from and sets as in Formula (2). According to the structure, the difference between and is non-singular, namely . Now, for private key query, challenger runs algorithm to respond. As in Game 1, algorithm outputs the vector from , which is sampled from distribution statistically approaching to .
In other aspects, Game 2 is as same as Game 1. Because the response to the private key queries is statistically very approaching to the response in the Game 1, ’s positive over the Game 1 and Game 2 has an almost ignorable difference. □
Theorem 7.
Game 2 and Game 3 are statistically indistinguishable.
Proof.
Game 3 is just like Game 2, although it differs in that the challenge ciphertext is always picked as an independent and random element from . Since the challenge ciphertext in the ciphertext space is always a novel random element and adversary has no positive in Game 3, then for a PPT adversary, the second and third games are computationally indistinguishable, and we do this by reducing it to the LWE problem.
Assuming has significant superiority in differentiating between the Game 2 and the Game 3. Then, we apply the adversary for an LWE algorithm .
As described in Definition 2, an LWE problem instance is to differentiate between truly random sample and noisy pseudo-random for some secret s in . In our security game, we set as the truly random sample and the as the LWE sample. makes a distinction between the two with the adversary , and operates as below:
Simulator approaches from and for each , simulator achieves a fresh pair .
The adversary declares to that the object it wants to attack is .
Simulator generates the system’s public parameters as below:
- (a)
- From n of the given LWE samples, it makes the random matrix and for all the i-th column of is the r-vector .
- (b)
- Specify the zeroth LWE sample as a publicly available random r-vector . The zeroth LWE sample has not been used yet.
- (c)
- Use and to create the remaining of public parameters as in Game 2.
- (d)
- Lastly, it sends public parameters to the adversary.
For each of the private key extraction query, simulator answers just as in Game 2.
With the target , when adversary prompts the message bit and the challenge ciphertext, responds as below:
- (a)
- Set as the entries from the LWE instance and set from .
- (b)
- Letting for masking message bit.
- (c)
- Set .
- (d)
- Send to the adversary.
If the LWE oracle is pseudo-random, namely = , will be distributed as in Game 2. Firstly, inspect that the . Secondly, by the definition of we are able to know that for some random noise vector , which is distributed as , . Thus, defined as above in the step (c) satisfies:
and the part in Game 2 is the quantity on the right, namely the efficacious challenge ciphertext. We also notice that , and the x’s distribution is as the . In this way, in step (b) satisfies , just like the part of the challenge ciphertext described in the Game 2.
In the case that = , we have is uniform from and is uniform from . According to the standard left-over-hash-lemma, which describes the hash function defined by the matrix . It makes sure that the two quantities and are uniformly independent. Thus, , which is defined as in step (c) is uniformly independent in . As a result, the challenge ciphertext in is always uniform just as in Game 3. □
After allowing supplemental queries, speculates that this is a challenger of Game 2 or Game 3. The simulator finally outputs the guess of as a solution to the LWE problem for which it is attempting to resolve.
We have mentioned before that in the case of = , the adversary ’s opinion is just like in the Game 2. Furthermore, in the case of = , the adversary ’s opinion is just like in the Game 3. Consequently, the positive of smulator in resolving LWE is equal to the positive of in differentiating between the Game 2 and the Game 3. At this point, we have fully introduce the algorithm and provide corresponding proof.
5. Comparison and Analysis
We compare our scheme with existing schemes [3,4] in terms of storage and computing. In Table 1, the performance of the schemes are analyzed from the aspects of size, size, online ciphertext size, offline ciphertext size, and security. We compare the computation efficiency of schemes in Table 2, from online computation, offline computation, and dimension. In addition, we also demonstrate through experimental simulations that our scheme is more efficient than existing schemes [3,4].

Table 1.
Comparison of storage space.

Table 2.
Comparison of computation efficiency.
5.1. Theoretical Comparison
The schemes in Table 1 and Table 2 are secure against CPA under the standard model, where n is the dimension of the lattice, r is the security parameter, and q is the modulus. Furthermore, the limiting relationship between them is . Table 1 shows the storage cost and security among Agrawal et al.’s anti-quantum IBE scheme [3], our online/offline anti-quantum IBE scheme, and Zhang et al.’s anti-quantum IBE scheme [4]. Our scheme uses the more efficient trapdoor generation method -trapdoor to generate trapdoors in scheme. Moreover, the scheme [4] is a lattice based IBE scheme proposed by Zhang et al. in 2020, which is an efficient IBE scheme with short parameters over lattice. With the same security level, our scheme has a smaller size than scheme [4], and also has a smaller online ciphertext size. This is friendly to low-power encryption devices.
We also compare the efficiency of different schemes in Table 2 in terms of the computational cost of online ciphertext, the computational cost of offline ciphertext, and the dimension of lattice. It is easy to see through a comparison that our scheme has the highest efficiency in online ciphertext calculation compared to the scheme [3,4]. In addition, our scheme not only supports expansion into adaptive security scheme, but also into multi-bit encryption and HIBE, and has been proven to be secure in the standard model.
5.2. Experimental Simulation
Furthermore, we compare the clock cycles for implementing the online part of Agrawal et al.’s anti-quantum IBE scheme, Zhang et al.’s anti-quantum IBE scheme and our online/offline anti-quantum IBE scheme from LWE. In our scheme, the Gaussian sampling parts which do not request and are placed on the Offline Server for operation. Our implementation is carried out on an Intel i7-12700 2.7GHz CPU, which is manufactured by Intel, Shanghai, China, with double precision floating point numbers for non integers in C++. We use the “time.h” to measure clock cycles. The one-dimensional sampler [26] is a modified rejection sampler. We set q and r for different LWE security [27]. In our settings, for 108.7-bit LWE security; for 279.7-bit LWE security; for 454.7-bit LWE security; and for 531.7-bit LWE security.
The scheme in [3] is a classic IBE scheme based on LWE, while the scheme in [4] is a recently published efficient LWE IBE scheme. The scheme in [4] balances efficiency and public parameter size through clever ideas in identity processing, and our scheme focuses on improving the efficiency of online computing while ensuring security. As shown in Figure 2, for the efficiency of the online part, our online/offline scheme has improved by 65% to 80% compared to the initial anti-quantum IBE scheme [3] from LWE, and by 60% to 70% compared to the scheme [4]. The improvement in efficiency increases with the increase of LWE security parameters. Because our scheme not only uses the efficient trapdoor generation method of -trapdoor in generating trapdoors, but also performs offline calculation in advance to enable the online part to only complete necessary operations with lower cost. This is very practical in scenarios where encryption devices have low power consumption, because through online/offline technology, high calculation overhead can be completed in advance, and this part of the calculation does not require message and receiver’s identity. In this way, the efficiency of encryption devices can be maximized during the online phase.
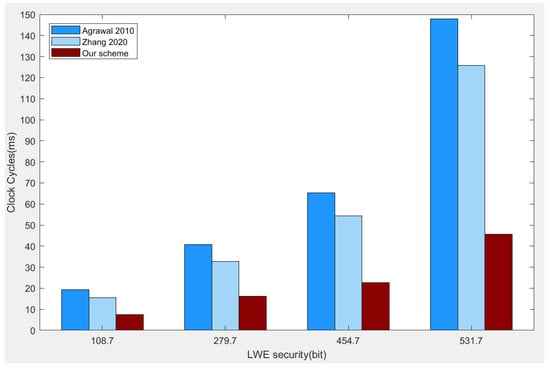
Figure 2.
The comparison of online part between our online/offline scheme and other schemes [3,4] for different LWE security. In the above figure, the LWE security corresponds to different security parameter r: 108.7-bit LWE security corresponds to ; 279.7-bit LWE security corresponds to ; 454.7-bit LWE security corresponds to ; and 531.7-bit LWE security corresponds to .
6. Conclusions
With the rapid development of quantum computing technology, how to design efficient IBE schemes that resist quantum attacks is currently a hot research topic. In this paper, our innovative suggestion is to design an IBOOE scheme by utilizing the difficult problem of lattice-based cryptography, which can efficiently perform online encryption even if the device’s computing power is limited. Furthermore, the offline phase can be achieved without the need of the message to be encrypted and the recipient’s identity. In addition, we use -trapdoor for generating “strong trapdoors” in lattice. Compared to most existing schemes, our scheme is simpler and more efficient, greatly reducing online computing costs. We prove under the standard model that the scheme is CPA secure. Through the performance and security analysis, our scheme improve the performance of the classic LWE IBE scheme [3] by 65% to 80% (increased by LWE security parameters), and by 60% to 70% in comparison with the scheme [4]. This greatly increases the efficiency of online computing for low-power encryption devices while guaranteeing security.
Our online/offline scheme based on IBE from LWE materializes high performance while resisting quantum interference. Although our scheme can be easily expanded into an adaptive security scheme [3], and can also convert to the Hierarchical IBE scheme [2], it lacks practical features in daily life, such as flexible user changes. In the future, we will further design attribute-based encryption schemes [28,29,30,31] from LWE, which has fine-grained access control function.
Author Contributions
Conceptualization, B.Z., J.L. and Y.Z.; Methodology, B.Z. and J.L.; Software, B.Z. and J.L.; Validation, B.Z. and J.L.; Formal analysis, B.Z. and J.L.; Investigation, B.Z. and J.L.; Resources, B.Z., J.L. and Y.Z.; Data curation, B.Z., J.L., J.S. and Y.Z.; Writing—original draft, B.Z. and J.L.; Writing—review & editing, B.Z., J.L., J.S. and Y.Z.; Visualization, B.Z. and J.L.; Supervision, J.L. and Y.Z.; Project administration, J.L., J.S. and Y.Z. All authors have read and agreed to the published version of the manuscript.
Funding
Jiguo Li was supported by the National Natural Science Foundation of China (62072104, U21A20465); Jian Shen was supported by the National Natural Science Foundation of China (U21A20465).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The original contributions presented in the study are included in the article, further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Gentry, C.; Peikert, C.; Vaikuntanathan, V. Trapdoors for Hard Lattices and New Cryptographic Constructions. In Proceedings of the Fortieth Annual ACM Symposium on Theory of Computing, Victoria, BC, Canada, 17–20 May 2008. [Google Scholar]
- Cash, D.; Hofheinz, D.; Kiltz, E.; Peikert, C. Bonsai Trees, or How to Delegate a Lattice Basis. J. Cryptol. 2012, 25, 601–639. [Google Scholar] [CrossRef]
- Agrawal, S.; Boneh, D.; Boyen, X. Efficient Lattice (H)IBE in the Standard Model. In Advances in Cryptology–EUROCRYPT 2010, Proceedings of the 29th Annual International Conference on the Theory and Applications of Cryptographic Techniques, French Riviera, France, 30 May–3 June 2010; Springer: Berlin/Heidelberg, Germany, 2010; Volume 6110, pp. 553–572. [Google Scholar]
- Zhang, Y.; Liu, Y.; Guo, Y.; Zheng, S.; Wang, L. Adaptively Secure Efficient (H)IBE over Ideal Lattice with Short Parameters. Entropy 2020, 22, 1247. [Google Scholar] [CrossRef] [PubMed]
- Regev, O. On Lattices, Learning with Errors, Random Linear Codes, and Cryptography. J. ACM (JACM) 2009, 56, 1–40. [Google Scholar] [CrossRef]
- Zhandry, M. Secure Identity-based Encryption in the Quantum Random Oracle Model. Int. J. Quantum Inf. 2015, 13, 1550014. [Google Scholar] [CrossRef]
- Katsumata, S.; Yamada, S.; Yamakawa, T. Tighter Security Proofs for GPV-IBE in the Quantum Random Oracle Model. J. Cryptol. 2021, 34, 5. [Google Scholar] [CrossRef]
- Gao, W.; Yang, L.; Zhang, D.; Liu, X. Quantum Identity-based Encryption from the Learning with Errors Problem. Cryptography 2022, 6, 9. [Google Scholar] [CrossRef]
- Dutta, P.; Susilo, W.; Duong, D.H.; Baek, J.; Roy, P.S. Lattice-based Unidirectional IBPRE Secure in Standard Model. arXiv 2020, arXiv:2005.06741. [Google Scholar]
- Wu, L.; Yang, X.; Zhang, M.; Wang, X. IB-VPRE: Adaptively Secure Identity-based Proxy Re-encryption Scheme from LWE with Re-encryption Verifiability. J. Ambient. Intell. Humaniz. Comput. 2022, 13, 469–482. [Google Scholar]
- Liu, Y.; Sun, Y. Generic Construction of Server-aided Revocable Hierarchical Identity-based Encryption. Int. Conf. Inf. Secur. Cryptol. 2020, 12612, 73–82. [Google Scholar]
- Li, J.; Teng, M.; Zhang, Y.; Yu, Q. A Leakage-Resilient CCA-Secure Identity-Based Encryption Scheme. Comput. J. 2016, 59, 1066–1075. [Google Scholar] [CrossRef]
- Li, J.; Guo, Y.; Yu, Q.; Lu, Y.; Zhang, Y. Provably Secure Identity-based Encryption Resilient to Post-challenge Continuous Auxiliary Input Leakage. Secur. Commun. Netw. 2016, 9, 1016–1024. [Google Scholar]
- Li, J.; Yu, Q.; Zhang, Y. Identity-based Broadcast Encryption with Continuous Leakage Resilience. Inf. Sci. 2018, 429, 177–193. [Google Scholar] [CrossRef]
- Yu, Q.; Li, J.; Ji, S. Hierarchical Identity-Based Online/Offline Encryption Scheme with Leakage Resilience. Secur. Commun. Netw. 2022, 2022, 6849761. [Google Scholar]
- Abla, P.; Liu, F.H.; Wang, H.; Wang, Z. Ring-based Identity Based Encryption–Asymptotically Shorter MPK and Tighter Security. In Theory of Cryptography: 19th International Conference, TCC, Raleigh, NC, USA, 8–11 November 2021; Springer: Cham, Switzerland, 2021; Volume 13044, pp. 157–187. [Google Scholar]
- Fan, J.; Lu, X.; Au, M.H. Adaptively Secure Identity-Based Encryption from Middle-Product Learning with Errors. In Proceedings of the Australasian Conference on Information Security and Privacy, Brisbane, QLD, Australia, 5–7 July 2023; Volume 13915, pp. 320–340. [Google Scholar]
- Lai, Q.; Liu, F.H.; Wang, Z. New Lattice Two-Stage Sampling Technique and Its Applications to Functional Encryption – Stronger Security and Smaller Ciphertexts. In Advances in Cryptology—EUROCRYPT 2021, Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Zagreb, Croatia, 17–21 October 2021; Springer: Cham, Switzerland, 2021; Volume 12696, pp. 498–527. [Google Scholar]
- Weiden, P.; Hülsing, A.; Cabarcas, D.; Buchmann, J. Instantiating Treeless Signature Schemes. Cryptol. ePrint Arch. 2013, 2013, 65. [Google Scholar]
- Lyubashevsky, V. Lattice Signatures without Trapdoors. In Advances in Cryptology—EUROCRYPT 2012, Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, UK, 15–19 April 2012; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7237, pp. 738–755. [Google Scholar]
- Micciancio, D.; Peikert, C. Trapdoors for Lattices: Simpler, Tighter, Faster, Smaller. In Advances in Cryptology—EUROCRYPT 2012, Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, UK, 15–19 April 2012; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7237, pp. 700–718. [Google Scholar]
- Micciancio, D.; Walter, M. Gaussian Sampling over the Integers: Efficient, Generic, Constant-Time. In Advances in Cryptology–CRYPTO 2017, Proceedings of the 37th Annual International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 2017; Springer: Cham, Switzerland, 2017; Volume 10402, pp. 455–485. [Google Scholar]
- Sun, S.; Zhou, Y.; Ji, Y.; Zhang, R.; Tao, Y. Generic, Efficient and Isochronous Gaussian Sampling over the Integers. Cybersecurity 2022, 5, 10. [Google Scholar]
- Guo, F.; Mu, Y.; Chen, Z. Identity-based Online/Offline Encryption. Financ. Cryptogr. Data Secur. 2008, 5143, 247–261. [Google Scholar]
- Cramer, R.; Damgård, I. On the Amortized Complexity of Zero-Knowledge Protocols. In Advances in Cryptology, Proceedings of the Annual International Cryptology Conference 2009, Santa Barbara, CA, USA, 16–20 August 2009; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5677, p. 177. [Google Scholar]
- Karney, C.F.F. Sampling Exactly from the Normal Distribution. Acm Trans. Math. Softw. (TOMS) 2016, 42, 1–14. [Google Scholar] [CrossRef]
- Chen, Y.; Genise, N.; Mukherjee, P. Approximate Trapdoors for Lattices and Smaller Hash-and-sign Signatures. In Advances in Cryptology–ASIACRYPT 2019, Proceedings of the 25th International Conference on the Theory and Application of Cryptology and Information Security, Kobe, Japan, 8–12 December 2019; Springer: Cham, Switzerland, 2019; Volume 11923, pp. 3–32. [Google Scholar]
- Chen, S.; Li, J.; Zhang, Y.; Han, J. Efficient Revocable Attribute-based Encryption with Verifiable Data Integrity. IEEE Internet Things J. 2024, 11, 10441–10451. [Google Scholar]
- Chen, N.; Li, J.; Zhang, Y.; Guo, Y. Efficient CP-ABE Scheme with Shared Decryption in Cloud Storage. IEEE Trans. Comput. 2022, 71, 175–184. [Google Scholar]
- Li, J.; Zhang, Y.; Ning, J.; Huang, X.; Poh, G.S.; Wang, D. Attribute Based Encryption with Privacy Protection and Accountability for CloudIoT. IEEE Trans. Cloud Comput. 2022, 10, 762–773. [Google Scholar] [CrossRef]
- Zhang, R.; Li, J.; Lu, Y.; Han, J.; Zhang, Y. Key Escrow-free Attribute Based Encryption with User Revocation. Inf. Sci. 2022, 600, 59–72. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).