Abstract
In the supply chain management literature, various mobile radio frequency identification (RFID) protocols have been proposed for minimizing cargo theft during transport while ensuring the integrity of the entire cargo load or transferring ownership of a tagged item to another owner. These protocols are generally called grouping proof protocols and ownership transfer protocols, respectively. However, no protocol has been proposed that can achieve both requirements. In this paper, we propose a novel designated ownership transfer with grouping proof protocol that simultaneously generates grouping proofs and authenticates the consistency between the receipt proof and pick proof while ensuring that ownership of the cargo is transferred to the new designated owner in one attempt. In addition, the proposed scheme is robust against attacks (such as replay, denial-of-service, and denial-of-proof attacks) and has security features, such as forward/backward secrecy and message integrity.
1. Introduction
In supply chain management (SCM), mobile radio frequency identification (RFID) has recently been widely and rapidly adopted for tracking and identifying objects. An RFID system consists of mobile readers, a back-end server that acts as a trusted third party (TTP), and tags that can be further classified into two types: active and passive. An active tag usually contains an internal power source (typically a battery) to continuously power it, thus giving it a long reading range, whereas a passive tag relies on the radio frequency energy transmitted from the reader as its power source, resulting in a shorter reading range. In SCM, passive tags are more widely used than active tags because of their lower implementation cost. In the early stages of SCM, tags were employed to store information about cargo and facilitate automated stocktaking. However, with this setup, in the later stages of SCM, increasing challenges led to a rise in cargo theft [1]. The key task under such circumstances is to identify the suspect among the supplier, transporter, and recipient based on evidence. To solve this problem, a protocol is needed to generate an undeniable proof of cargo. In 2004, Juels [2] introduced the yoking-proof protocol that proves the existence of two tags within the range of an RFID reader. However, Saito and Sakurai [3] proved that this protocol is insecure, and they extended the concept into the grouping proof. Saito and Sakurai’s proposed protocol allows a single RFID reader to simultaneously prove the existence of a group of tags. The generated proof is later sent to a TTP for further verification. Based on Elliptic Curve Cryptography (ECC), Batina et al. [4] proposed a privacy-preserving multiparty grouping-proof protocol in the setting of a narrow-strong attacker. Batina et al.’s proposed protocol allows generating a proof that is verifiable by a trusted verifier in an offline setting, even though readers or tags are potentially untrusted. However, Hermes and Peeters [5] demonstrated that an adversary can generate a valid grouping proof in Batina et al.’s protocol [4]. In addition, Hermes and Peeters introduced two formal models for yoking proofs. Based on the proposed models, they further proposed two protocols to generate sound yoking proofs. Shen et al. [6] proposed a lightweight RFID grouping authentication protocol, in which one object to be authenticated is attached with a group of RFID tags. If only some of the tags are successfully authenticated, the generated proof can be used to guarantee that the object is here and trace the identities of the disabled tags. In 2016, Abughazalah et al. [7] proposed an offline two-round grouping-proof protocol. Abughazalah et al.’s proposed protocol improves tag’s memory and computing performance. Burmester and Munilla [8] presented an anonymous grouping-proof with untrusted readers, in which the generated proof can be checked by the trusted verifier and the untrusted reader can recover the identifiers for missing tags, but the untrusted reader cannot generate a proof if tags are missing. In the same year, Burmester and Munilla [9] extended earlier work on grouping proofs and group codes to capture resilient group scanning with untrusted readers. Rostampour et al. [10] adopted authenticated encryption to design a scalable grouping proof protocol with message authentication code, which provides both confidentiality and message integrity simultaneously. Each tag individually computes authenticated message, and the reader is responsible for gathering the response messages of all tags in the authentication phase. That is, Rostampour et al.’s protocol eliminates the dependency among the tags’ responses. Based on parallel mode and dynamic host configuration protocol, Shi et al. [11] proposed a lightweight RFID grouping-proof protocol that adopts parallel communication mode between reader and tags. It achieves grouping-proof efficiency.
When cargo is delivered to a new party, the ownership of that cargo should be transferred simultaneously. Most ownership transfer protocols operate based on the following assumptions. After the ownership transfer is complete, the former owner can no longer access the RFID tags, and the new owner can prove ownership of cargo by means of mutual authentication with the RFID tags [12,13,14,15,16,17]. Yang and Xie [17] proposed a RFID protocol for group ownership transfer, in which a group of tags’ ownership can be transferred in one attempt. Later, Li et al. [13] presented a physical-unclonable-function-based RFID ownership transfer protocol in an open environment. A physical unclonable function is used to to prevent that the tag is cloned, and a reader does not need to store the response values in Li et al.’s protocol. According to the EPC Class-1 Generation-2 Version 2 standard, Niu et al. [15] proposed an ultra-lightweight authentication and ownership management protocol, which reduces the storage and the computational costs of the tags. In 2015, Li et al. [14] presented lightweight authentication and delegation protocol for RFID tags, which also adopts physically unclonable function to enhance the security of the tags. Li et al.’s protocol can achieve the security requirement of privacy for the original owner and the new owner. Based on the XOR operation and a 128-bit pseudo-random number generator, Sundaresan et al. [16] proposed a ownership transfer protocol for a multi-tag multi-owner RFID environment, in which it protects privacy for individual-owner and prevents tracking attacks. However, Munilla et al. [18] mounted some attacks on Sundaresan et al.’s protocol [16]. In the demonstrated attacks, an adversary can trace a tag, and the previous owner can obtain the private information shared among the tag and the new owner. By using the ownership transfer protocol, both parties can trade tagged objects more easily. A few researchers have worked to reduce security threats in ownership transfer, including replay [3] and denial-of-service (DoS) attacks [19].
A ownership handover process between a supplier or retailer and a recipient requires two protocols, namely, a grouping proof protocol to ensure all cargo is in place and an ownership transfer protocol to transfer ownership of cargo to the designated party. This process is inefficient and time consuming. Owing to an increasing number of security threats in SCM, there should be a complete RFID protocol that preserves message integrity and privacy. Consider two scenarios in which a malicious party might intercept messages transmitted between tags and mobile readers. In the first scenario, the malicious party might retransmit the messages to execute unauthorized operations, such as by generating bogus proofs or achieving fake authentication. In the second scenario, the malicious new owner might attempt to gain access to the previous transactions of the former owner or the former owner might try to access the future transactions of the new owner. To solve these problems, the grouping proof and ownership transfer protocols must be combined. A different scenario would involve certain products needing to be shipped in groups—for example, safety regulations that require medication to be shipped along with the corresponding information leaflets [20]. Ownership transfer guarantees that the medication and the leaflets originate from the respective owners within a drug manufacturer, and grouping proof ensures that each of the medications is imported along with the correct leaflets. Scenarios in which medication is delivered without the correct leaflets or the leaflets are delivered with counterfeit medication are unacceptable, because they might cause a patient’s death due to medication-related errors [21]. To prevent such a scenario from occurring, grouping proof is required for a valid group ownership transfer. To that end, in 2010, Zuo [22] proposed a protocol based on ownership transfer with the capability to integrate any grouping proof protocols. Although Zuo’s protocol can ensure the simultaneous presence of a group of tags during ownership transfer, it suffers from performance problems. For example, it requires mutual authentication to be performed twice.
In this paper, we propose a novel designated ownership transfer protocol with grouping proof that can ensure message integrity and privacy. Although the ownership transfer and grouping proof protocols are designed for different purposes, they have similarities, such as requiring authentication before information is exchanged and generating random numbers to derive fresh messages. By combining the similarities between the protocols, the proposed protocol not only retains the main security and privacy features of the grouping proof and the ownership transfer protocols but also reduces the number of message or responses needed, because ownership transfer and proof generation are performed in one attempt.
2. Proposed Protocol
The proposed protocol is centered on the hierarchical-management-framework-based grouping proof protocol proposed by Yang et al. [23], which allows several readers to simultaneously scan a group of tags to generate pieces of proof that will later be combined into a final grouping proof by an authorized reader. The protocol consists of three phases: initialization, integrity verification, and ownership transfer. The notations used in the proposed protocol are listed in Table 1.

Table 1.
Symbol notations.
2.1. Initialization Phase
When a cargo shipment with a tag collection is delivered to the recipient , the reader requests the verifier to establish a secure multicast connection to ensure that the generated grouping proofs are in accordance with those on the recipient’s reader and that the message can be transmitted to tags in . Accordingly, the verifier generates a k-ary group key with a subtree height difference of ≤ 1() by using the secret key , where is shared between the verifier and the tags . In summary, the group keys that can transmit messages to q tags in are defined as . Figure 1 shows an example of a 3-ary group key ( is the starting node) generated for a set of 23 tags; the group key is employed to encrypt the multicast messages transmitted to the tags numbered from to , and tags , , and can decrypt the multicast messages encrypted with the group key by using their own shared keys , , and , respectively. The! details of group key generation can be found in Yang and Xie’s proposed methods [17].
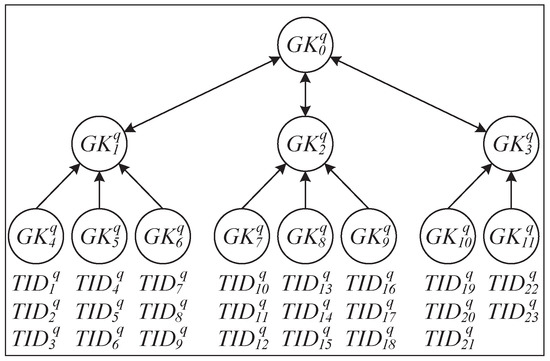
Figure 1.
The 3-ary key tree for a group of tags.
Moreover, a verification code is generated for tags in according to Equation (1).
After the verifier has generated the verification codes , group key , and timestamp , they are then transmitted to the transporter’s reader to be forwarded to the n recipients’ readers.
2.2. Integrity Verification Phase
After the transporter delivers the cargo to the recipient and simultaneously generates grouping proofs by using a reader with a maximum reading capacity of r, the group keys are distributed to several mobile readers from the transporters’ reader to securely multicast messages to tags via the recipients’ readers , thus enabling each reader to receive the maximum number of tags by performing only one multicast. In other words, the grouping proof is generated using the minimum number of group keys.
In this phase, the reader uses the distributed keys to encrypt the recipient’s identification code , ownership transfer request , timestamp , group key set for the child node reader , and tag verification code set , and then transmits the ciphertext until all leaf nodes are reached. For example, as shown in Figure 2, the reader first uses the key to encrypt , , , = , , , , and , and then transmits them to the reader , which will use the session key to decrypt the message, split and and, accordingly, encrypt , , , , , , , , , , and into separate messages by using the session keys and , and send them to the leaf node readers and .
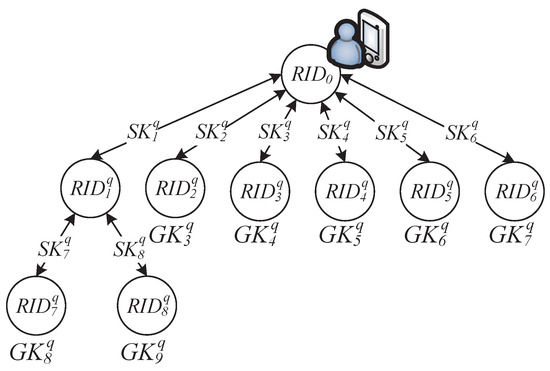
Figure 2.
One group key.
Subsequently, the encrypted messages will be distributed to the corresponding tags. The leaf reader will then collect pieces of proof from the tags, which will be transmitted back to the upper levels and then to reader to generate a grouping proof, as shown in Figure 3.
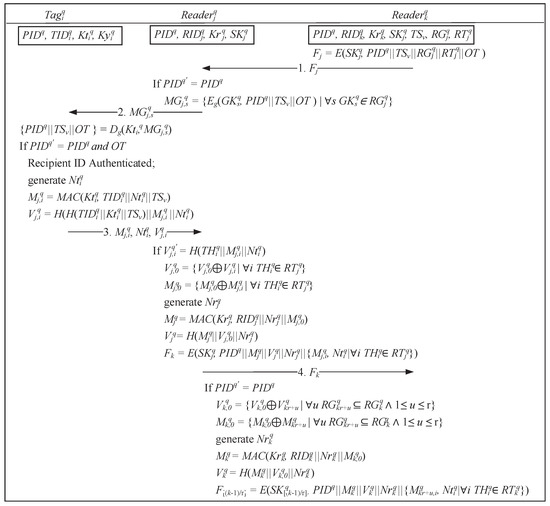
Figure 3.
Generating grouping proofs by using a multilayered reader.
[Message 1] After receiving the encrypted message from , the reader proceeds to decrypt the message using the session key . Then, depending on the child node, splits , and . Furthermore, encrypts and by using the child node session key as message then transmits to .
[Message 2] Upon receiving the encrypted message from , the leaf node reader uses its session key to decrypt the message. The multicast message is constructed, encrypted using the group key along with and , and then transmitted to the corresponding tags to generate pieces of proof.
[Message 3] When any tag receives a multicast message , the tag will proceed to decrypt the message by using the shared key , and then verify whether the decrypted message contains the correct and ownership transfer request . When the verification is correct, the shared key is then employed to compute the pieces of proof along with the tag , a randomly generated number , and a timestamp (if offline then else ). Subsequently, a message verification code is computed for the reader to verify the tag by using the hashing value , the shared key , the timestamp , pieces of proof , and a random number .
[Message 4] To verify the message integrity, a leaf node reader receives a response messages from the tags, the obtained , and tag verification value transmitted from previously, and further, the reader computes . Through comparison with the message verification code transmitted by the tags, the reader can block and prevent proof that is not associated with this delivery. Subsequently, the reader employs the XOR operation to combine all pieces of proof and the verification code into pieces of proof and message verification code . The pieces of proof generated by the reader are then computed using the shared key along with the reader identification code , and randomly generated numbers and . Moreover, a message verification code is also computed by hashing and . The session key is used to encrypt , and for all group member tags, and the encrypted messages are transmitted back to parent node reader . After the parent node reader receives the response message transmitted by child node reader , the encrypted message is decrypted by using the session key to verify whether the message contains the same recipient . Once the recipient is authenticated, the reader uses the same method as the reader to generate the required message, then transmit the message to the reader at the upper level, and finally back to the reader .
As shown in Figure 4, the reader receives a response message from the recipient .
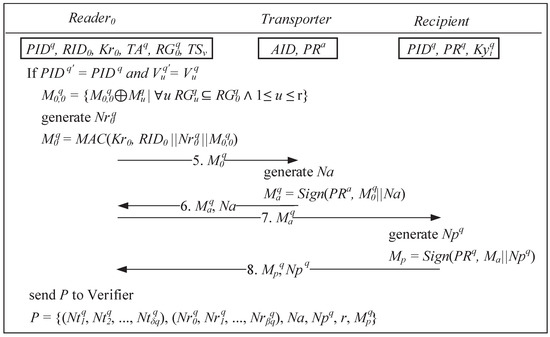
Figure 4.
Affirming tags and proofs signed by both sides and verifying time constraint.
[Message 5] Once all messages transmitted by the child node reader are verified by matching the message verification code to reconfirm message integrity, the reader combines all pieces of proof received from into a combined proof . The shared key is employed to generate the grouping proof by using the identification code , a random number generated by reader , and the combined proof . The grouping proof is then transmitted to the transporter’s tags to be signed.
[Message 6] When the transporter’s tags receive a request message from the reader to sign the grouping proof , a random number is generated to be used along with the transporter’s private key to sign the grouping proof and change it into a signed proof . The signed proof and the random number are then transmitted back to the reader .
[Message 7] After the reader receives the signed proof from the transporter’s tag, the signed proof is transmitted to the recipient’s tag for signing. Using the random numbers generated by the recipient’s tag and the private key , the recipient uses the signing function to sign into the signed proof . The signed proof and a random number are then transmitted back to the reader .
[Message 8] After the reader receives the signed proof from both the transporter’s tag and the recipient’s tag, the final grouping proof P is then transmitted to the verifier. When the verifier receives the final grouping proof P from the reader , the verifier first computes the time difference between the current system time and the timestamp to check whether it was completed within the time threshold. Subsequently, the proof is decrypted using the recipient’s public key and a random number to obtain the signed proof , which is then decrypted using the transporter’s public key and a random number to obtain the grouping proof ’. The verifier computes to determine whether the received grouping proof is identical, thus completing the grouping proof protocol.
2.3. Ownership Transfer Phase
Once the verifier confirms that there are no problems with the proof received from reader , it generates new ownership by shared key for the recipient’s tag, as shown in Figure 5.
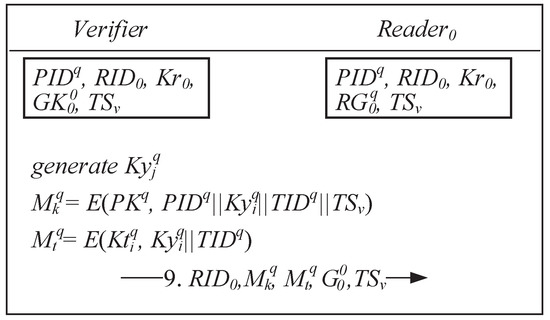
Figure 5.
Acquiring the new ownership of shared keys from the verifier.
[Message 9] The verifier uses the tag’s current shared key and the random number previously generated by the tag to compute the new ownership by shared key . Subsequently, two encrypted messages are generated using the recipient’s public key and the tag’s shared key . The encrypted message consists of the recipient identification code , new ownership by shared key , tag’s identification code , and the new timestamp , whereas consists of the new ownership by shared key and the tag’s identification code . Moreover, a new set of group keys is generated and transmitted to the reader along with , , and .
After receiving the transmitted message from the verifier, the reader proceeds to encrypt the message by using the session key along with and the group key as the encrypted message . Both encrypted messages and are simultaneously transmitted to the recipient’s tags and reader .
[Message 10] Once the recipient’s tag receives the encrypted messages from reader , the recipient’s tag decrypts the message to verify whether is correct. If the verification is successful, the recipient’s tag updates the current ownership by shared key with the new ownership by shared key , as shown in Figure 6.
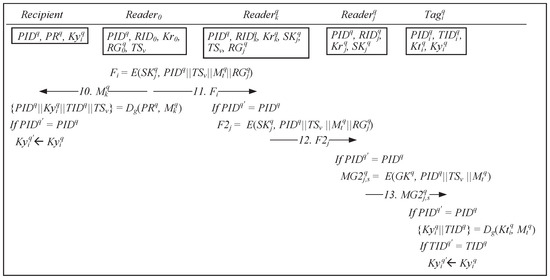
Figure 6.
Updating ownership by shared keys.
[Message 11] After receiving the encrypted message from , the reader proceeds to decrypt the message by using the session key . Depending on the child node, splits (refer to Figure 2) accordingly and then encrypts , , , and by using the child node session key as message and then transmits it to the reader .
[Message 12] Upon receiving the encrypted message from , the leaf node reader uses its session key to decrypt the encrypted message. All group keys in are extracted, and the multicast message is encrypted by using the group keys along with , , and and then transmitted to each tag.
[Message 13] When any tag receives a multicast message , the tag will proceed to decrypt the message by using the shared key and then determine whether the decrypted message contains the correct . If is correct, the message is decrypted to retrieve the tag for further confirmation. When the message is successfully authenticated, the tag updates its current ownership by shared key with the new ownership by shared key , thus effectively completing the ownership transfer protocol.
3. Security Analysis
Table 2 presents a comparison of the security features. denotes that a method listed in the comparison is capable of a feature; denotes that a method fails to achieve the feature; and Δ means that the method can achieve the feature when certain circumstances are satisfied. In addition, we use as an abbreviation for ownership transfer and for grouping proof to indicate which vulnerabilities are present in these two protocols. For example, the replay attack can take place in both protocols, whereas the denial of proof vulnerability is unique to grouping proof protocols.

Table 2.
Comparison of security features of different protocols.
In the method proposed by Saito and Sakurai. [3], the messages are transmitted without random numbers or any counters to prevent old messages from being replayed.
In addition to the legitimacy of the generated proof, the previously proposed protocols [3,5,24] do not authenticate the responses received from the tags. Therefore, if the response messages are generated by tags that do not belong to the current tag group, the verifier will reject and discard the proof, leading to denial of proof. Concurrent attacks can occur when several readers simultaneously attempt to generate grouping proofs for the same tag, which prevents the proofs from being generated because the contents of the previous tags are overwritten by subsequent readers. The protocol proposed by Saito and Sakurai [3] requires the tags and readers to be written multiple times to generate the grouping proof, which can cause a problem in a scenario in which previously written information can be overwritten by other readers. In Hermes and Peeters’s protocol [5], the reader must read the tags more than twice to generate a proof. Although Sun et al.’s protocol [24] does not overwrite proofs when the tags are read by different readers during inspection, the random numbers are not subject to the same security check and might therefore be overwritten.
Jannati and Falahati [26] proved that Zuo’s protocol [22] is vulnerable to the desynchronization attack, which causes a tag to lose synchronization with the new owner, resulting in DoS. In Section 3.1, Section 3.2, Section 3.3, Section 3.4, Section 3.5, Section 3.6 and Section 3.7, we analyze our proposed protocol, which prevents all the aforementioned threats.
3.1. Replay Attack
Assume an attacker can intercept all previous generated grouping proof messages transmitted between all communicating parties and resend them later to bypass authentication or to generate a bogus proof.
However, because each piece of proof contains a different random number or a timestamp for every session, the reader can detect and ignore replayed messages by verifying the timestamps or the random numbers to check whether it has been used before.
3.2. Denial of Proof
Suppose a malicious attacker intercepts all previously generated grouping proof messages transmitted between all communicating parties and attempts to generate a bogus proof by using fake information, causing the verifier to reject and discard the proofs, resulting in denial of proof.
However, in our protocol, each piece of proof computes a verification code . The reader can use the tag verification code provided by the verifier to check whether this piece of proof belongs to this delivery. To generate a valid proof, the hacker must obtain the secret , which is shared only between the tags and the verifier. The secret are not transmitted during protocol execution, and, therefore, the attacker will have no way to acquire them, avoiding the occurrence of denial of proof.
3.3. Denial of Service
When a malicious attacker interrupts the interaction between the reader and the tags by intercepting or blocking the shared key update message, the tag might lose synchronization with the verifier, resulting in DoS.
In our proposed protocol, the verifier stores the old ownership by shared key and the new ownership by shared key . In the case of a DoS attack that blocks these shared key update messages, the verifier can still authenticate the tags.
3.4. Forward Secrecy
Assume an attacker can intercept all previously transmitted messages between all communicating parties during the ownership transfer phase. However, without knowing the previous ownership by shared key , the new owner (recipient ) cannot decrypt the message transmitted between the tags and its former owner (supplier).
3.5. Backward Secrecy
Assume an attacker can intercept all forward messages transmitted between all communicating parties after ownership transfer.
However, in our protocol, new ownership by shared key is computed by the verifier by encrypting the old ownership by shared key and a random number generated by the tags (Figure 3). Therefore, without the new ownership by the shared key, the former owner (supplier) cannot further track messages transmitted between the new owner and the tags.
3.6. Concurrent Attacks
When two readers simultaneously use the same tags, specific parameters may be overwritten. An adversary can use a reader to crisscross specific tags, thereby blocking generation of the grouping proof.
In our proposed protocol, there is no temporary parameter, and the reader needs to communicate with the tag only once to generate the pieces of proof . Hence, no adversary can mount a concurrent attack.
3.7. Message Integrity
Assume an attacker can intercept all previously generated grouping proof messages transmitted between all communicating parties, and then attempts to modify the message to generate a bogus proof to fool the reader or verifier.
In our protocol, each legitimate tag generates a different random number in each session to compute the pieces of proof . Moreover, a verification code is included in the response message to ensure the integrity of that message. The attacker might attempt to retrieve the shared key from the verification code , but, owing to the assumption of OHF, no useful information will be obtained.
4. Performance Analysis
This section analyzes the combination of Zuo’s protocol [22] with grouping proof protocols that do not require a predetermined sequence [5,24,25] and compares the computation capacity loads against our proposed protocol. To ensure unbiased comparison, the analysis was conducted at scan rate of 3.55 M clock cycles per second according to Yang et al.’s effectiveness analysis [23]. Additionally, asymmetric encryption and error-correcting code were employed using the same security strength of bits. The computation time for XOR logic operation was minimal (compared to the crypto-algorithm) and was therefore neglected and not included in the comparison. The reader adopted for this comparison was assumed to have powerful arithmetic capability.
Table 3 lists the notations used for the computation comparison. Table 4 presents the computation costs of the compared protocols. Each of the readers in our proposed protocol can manage a maximum of r tags, and therefore sends only one multicast message to all the tags. The grouping proof protocols in [24,25] can also send multicast messages to all tags, but, when , the reader must transmit the message multiple times, thus requiring a computation time of times. Our protocol adopts a multilayered grouping proof structure. Although a similar message is broadcast, readers are required to communicate with each other. Therefore, our computation time would require times.

Table 3.
Computational capacity symbol notations.

Table 4.
Computational capacity.
According to the method proposed by Yen et al. [25], the computational cost of the reader would increase depending on the number of m tags because the reader would need to verify the identification code of each tag. Hermes and Peeters [5] and Sun et al. [24] employed methods in which identical messages are broadcast to all tags, ensuring the constant computational capacity required by the reader to generate grouping proofs.
We use “OP” as an abbreviation for our proposed protocol; “ZY” represents the combination of Zuo [22] and Yen et al. [25]; “ZS” represents the combination of Zuo [22] and Sun et al. [24]; and “ZH” represents the combination of Zuo [22] and Hermes and Peeters [5]. Figures 8 and 9 show the readers with the maximum reading capacity of 200 tags employed to determine the computing times required by various methods. The number of tags starts from 100 and is doubled until it reaches 12,800.
According to Figure 7, OP involves fewer than 800 tags, and a longer computation time is required because the group key must be decrypted. As the number of tags increases, the computation time increases because computing time and tag number are linearly related. When the number of tags exceeds 800, OP is more efficient compared to the other methods. The computation times of ZY and ZS differ by only 1%.
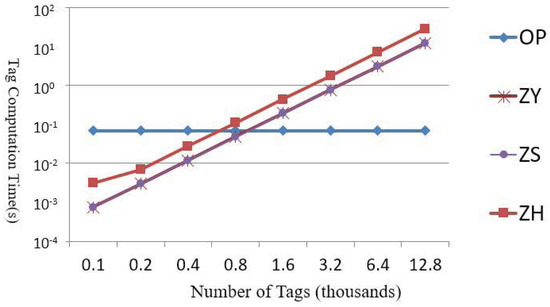
Figure 7.
Comparisons of computation loads of tags.
In addition, Figure 8 shows that, when processing fewer than 3200 tags, OP needs more computing time because the group message must be encrypted and transmitted between the readers. Later, the proof requires signatures from both the transporter and the recipient. However, when the number of the tags exceeds 3200, OP is more efficient compared to the other methods. This advantage shows that OP is a favorable choice in an environment (e.g., SCM) where large numbers of tags must be scanned concurrently to generate proofs and transfer cargo ownership.
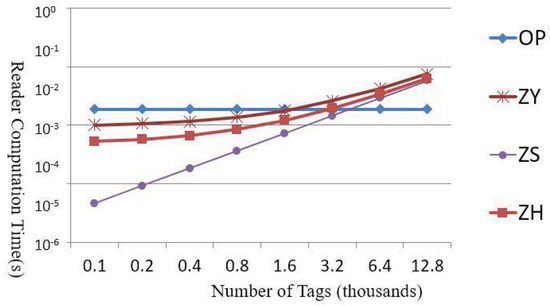
Figure 8.
Comparisons of computation loads of readers.
According to EPC Class-1 Generation-2 standard, the highest transmission rate from a reader to a tag is 160 kbps and that from a tag to a reader is 640 kbps. We used the transmission rate and the message lengths stated in Table 5 to compute the required transmission time from a reader to their tags and from the tags to their reader.

Table 5.
Transmission capacity, symbol notation, and estimated length.
Table 6 presents a comparison of the transmission time of OP with those of the other methods. In OP, we adopted a multilayered grouping proof structure, and a maximum of r tags were distributed to each reader. Thus, compared to other methods, an increase in the number of tags did not lead to an increase in transmission from the tags to the reader. Furthermore, the transmission time from the reader to the tags increased by times because a read-tree was employed. ZY, ZS, and ZH could not manage m tags simultaneously; therefore, the transmission was repeated times when those methods were used.

Table 6.
Transmission capacity.
Figure 9 and Figure 10 show the required transmission times for the tags and readers. According to Figure 9, OP requires slightly more transmission time when fewer than 100 tags are involved. However, when the number of tags is more than 100, OP is more efficient compared to the other protocols, because the other protocols would need to divide the tags and transmit them over several cycles, thereby increasing the transmission time. Figure 10 shows that OP has the shortest transmission time from readers to tags because OP requires only one multicast to broadcast the messages to all tags, as opposed to the other methods, which require the messages to be transmitted multiple times.
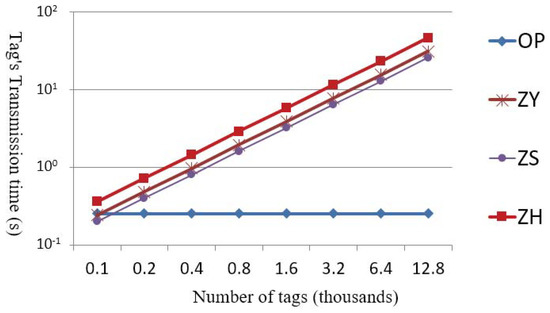
Figure 9.
Comparisons of transmission load of tags.
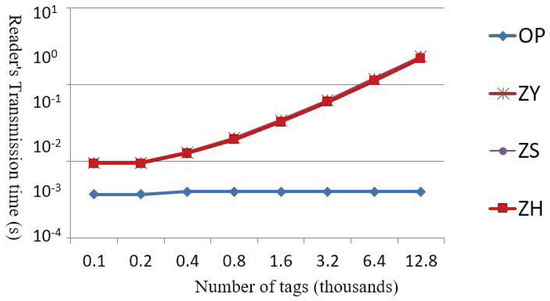
Figure 10.
Comparisons of transmission load of the readers.
5. GNY Logic Proof
In this section, we apply GNY [27] logic to prove the security of our proposed protocol. Our analysis includes four parts:
Please refer to the GNY reasoning studies [27] for the rules (e.g., P1, T1, and F1). The proof process of our proposed protocol is shown as in Table 10.

Table 10.
Proof process.
6. Conclusions
The emerging development of RFID technology has created the potential of massive deployment using the low cost and highly convenient RFID Tags. In a multi-party environment such as SCM, global trading is no longer just about delivering cargo quickly and efficiently, it is also about moving goods securely to the designated recipient [28]. This paper proposes an interesting approach in which a grouping proof protocol (to prove the existence of a group of tags) and ownership transfer protocol (to transfer the ownership of the tags) can be employed simultaneously without hindering mechanism of the original protocol [23]. In addition, once the verifier has confirmed the validity of generated proof provided by the transporter, the ownership transfer will be executed immediately, thus preventing anyone from tampering with the cargo goods (swapping legitimate goods with the counterfeit items, etc.). Furthermore, in terms of security and privacy, we found that the proposed protocol can prevent most known attacks such as replay attack, denial of service, etc. that aim to exploit the message being transmitted between the readers and the tags.
Author Contributions
The four authors have made equal substantial contributions to this work.
Funding
This research was funded by Ministry of Science and Technology (MOST) grant numbers MOST 107-2218-E-011-012, MOST 107-2221-E-033-010, MOST 107-2221-E-130-001, and MOST 106-2221-E-034-002 in Taiwan.
Acknowledgments
The authors gratefully acknowledge the support from Taiwan Information Security Center (TWISC) and Ministry of Science and Technology (MOST) under the grants MOST 107-2218-E-011-012, MOST 107-2221-E-033-010, MOST 107-2221-E-130-001, and MOST 106-2221-E-034-002 in Taiwan.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Leong, C.E. A Research on Supply Chain Security in Malaysia. Int. J. Supply Chain Manag. 2014, 3, 85–93. [Google Scholar]
- Juels, A. Yoking Proof for RFID Tags. In Proceedings of the 2nd Annual International Conference on Pervasive Computing and Communications, Orlando, FL, USA, 14–17 March 2004; pp. 138–143. [Google Scholar] [CrossRef]
- Saito, J.; Sakurai, K. Grouping Proof for RFID Tags. In Proceedings of the International Conference on Advanced Information Networking and Applications, Taipei County, Taiwan, 25–30 March 2005; pp. 621–624. [Google Scholar]
- Batina, L.; Lee, Y.K.; Seys, S.; Singelée, D.; Verbauwhede, E. Extending ECC-based RFID Authentication Protocols to Privacy-preserving Multi-party Grouping Proofs. Pers. Ubiquitous Comput. 2012, 16, 323–335. [Google Scholar] [CrossRef]
- Hermes, J.; Peeters, R. Private Yoking Proofs: Attacks, Models and New Provable Constructions. In Proceedings of the 8th International Conference on RFIDSec, Nijmegen, The Netherlands, 2–3 July 2012; pp. 96–108. [Google Scholar]
- Shen, J.; Tan, H.W.; Chang, S.H.; Ren, Y.J.; Liu, Q. A Lightweight and Practical RFID Grouping Authentication Protocol in Multiple-Tag Arrangements. In Proceedings of the International Conference on Advanced Communication Technology, Ho Chi Minh, Vietnam, 1–3 July 2015; pp. 681–686. [Google Scholar]
- Abughazalah, S.; Markantonakis, K.; Mayes, K. Two Rounds RFID Grouping Proof Protocol. In Proceedings of the IEEE International Conference on RFID, Orlando, FL, USA, 3–5 May 2016; pp. 1–14. [Google Scholar]
- Burmester, M.; Munilla, J. An Anonymous RFID Grouping Proof with Missing Tag Identification. In Proceedings of the IEEE International Conference on RFID, Orlando, FL, USA, 3–5 May 2016; pp. 1–7. [Google Scholar] [CrossRef]
- Burmester, M.; Munilla, J. Resilient Grouping Proof with Missing Tag Identification. In Proceedings of the International Conference on Ubiquitous Computing and Ambient Intelligence, Las Palmas de Gran Canaria, Spain, 29 November–2 December 2016; pp. 544–555. [Google Scholar]
- Rostampour, S.; Bagheri, N.; Hosseinzadeh, M.; Khademzadeh, A. An Authenticated Encryption Based Grouping Proof Protocol for RFID Systems. J. Secur. Commun. Netw. 2017, 9, 5581–5590. [Google Scholar] [CrossRef]
- Shi, Z.; Zhang, X.; Wang, Y. A Lightweight RFID Grouping-Proof Protocol Based on Parallel Mode and DHCP Mechanism. Information 2017, 8, 85. [Google Scholar]
- Huang, H.H.; Yeh, L.Y.; Tsaur, W.J. Ultra-Lightweight Mutual Authentication and Ownership Transfer Protocol with PUF for Gen2v2 RFID Systems. In Proceedings of the International MultiConference of Engineers and Computer Scientists, Hong Kong, China, 16–18 March 2016; Volume 2, pp. 655–658. [Google Scholar]
- Li, Q.S.; Xu, X.L.; Chen, Z. PUF-based RFID Ownership Transfer Protocol in an Open Environment. In Proceedings of the International Conference on Parallel and Distributed Computing, Applications and Technologies, Hong Kong, China, 9–11 December 2014; pp. 131–137. [Google Scholar]
- Li, G.C.; Xu, X.L.; Li, Q.S. LADP: A Lightweight Authentication and Delegation Protocol for RFID Tags. In Proceedings of the International Conference on Ubiquitous and Future Networks, Sapporo, Japan, 7–10 July 2015; pp. 860–865. [Google Scholar]
- Niu, H.F.; Jagannathan, S.; Taqieddin, E.S. A Gen2v2 Compliant RFID Authentication and Ownership Management Protocol. In Proceedings of the IEEE Conference on Local Computer Networks, Edmonton, AB, Canada, 8–11 September 2014; pp. 331–336. [Google Scholar]
- Sundaresan, S.; Doss, R.; Zhou, W.L.; Piramuthu, S. Secure Ownership Transfer for Multi-tag Multi-owner Passive RFID Environment with Individual-owner-privacy. Int. J. Comput. Telecommun. Ind. 2015, 55, 112–124. [Google Scholar] [CrossRef]
- Yang, M.H.; Xie, K.P. TTP-Based Group Ownership Transfer in A Mobile RFID Environment. Int. J. Digit. Content Technol. Its Appl. 2013, 7, 51–69. [Google Scholar]
- Munilla, J.; Burmester, M.; Peinado, A. Attacks on Ownership Transfer Scheme for Multi-tag Multi-owner Passive RFID Environments. Comput. Commun. 2016, 88, 84–88. [Google Scholar] [CrossRef]
- Kapoor, G.; Piramuthu, S. Vulnerabilities in Some Recently Proposed RFID Ownership Transfer Protocols. IEEE Commun. Lett. 2010, 14, 260–262. [Google Scholar] [CrossRef]
- Burmester, M.; Medeiros, B.; Motta, R. Provably Secure Grouping-proofs for RFID Tags. In Proceedings of the 8th Smart Card Research and Advanced Application Conference, London, UK, 8–11 September 2008. [Google Scholar] [CrossRef]
- Yu, Y.C.; Hou, T.W.; Chiang, T.C. Low Cost RFID Real Lightweight Binding Proof Protocol for Medication Errors and Patient Safety. J. Med. Syst. 2012, 36, 823–828. [Google Scholar] [CrossRef] [PubMed]
- Zuo, Y.J. Changing Hands Together: A Secure Group Ownership Transfer Protocol for RFID Tags. In Proceedings of the Hawaii International Conference on System Sciences, Washington, DC, USA, 5–8 January 2010; pp. 1–10. [Google Scholar]
- Yang, M.H.; Luo, J.N.; Lu, S.Y. A Novel Multilayered RFID Tagged Cargo Integrity Assurance Scheme. Sensors 2015, 15, 27087–27115. [Google Scholar] [CrossRef] [PubMed]
- Sun, H.M.; Ting, W.C.; Chang, S.Y. Offlined Simultaneous Grouping Proof Protocol for RFID EPC C1G2 Tags. In Proceedings of the 2nd International Conference on Computer Science and its Applications, Jeju, Korea, 7–9 October 2013; pp. 1–6. [Google Scholar]
- Yen, Y.C.; Lo, N.W.; Wu, T.C. Two RFID-Based Solutions for Secure Inpatient Medeciation Administration. J. Med. Syst. 2012, 36, 2769–2778. [Google Scholar] [CrossRef] [PubMed]
- Jannati, H.; Falahati, A. Cryptanaylsis and Enhancement of a Secure Group Ownership Transfer Protocol for RFID Tags. In Proceedings of the International Conference on Global Security, Safety and Sustainability, Thessaloniki, Greece, 24–26 August 2012; pp. 186–193. [Google Scholar]
- Gong, L.; Needham, R.; Yahalom, R. Reasoning about belief in cryptographic protocols. In Proceedings of the IEEE Computer Society Symposium on Research in Security and Privacy, Oakland, FL, USA, 14–16 April 1990; pp. 234–248. [Google Scholar]
- Russell, D.M.; Saldanha, J.P. Five Tenents of Security-Aware Logistics and Supply Chain Operation. Transp. J. 2003, 44, 44–54. [Google Scholar]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).