Abstract
Security is a critical issue for medical and health care systems. Password-based group-authenticated key agreement for wireless sensor networks (WSNs) allows a group of sensor nodes to negotiate a common session key by using password authentication and to establish a secure channel by this session key. Many group key agreement protocols use the public key infrastructure, modular exponential computations on an elliptic curve to provide high security, and thus increase sensor nodes’ overhead and require extra equipment for storing long-term secret keys. This work develops a novel group key agreement protocol using password authentication for WSNs, which is based on extended chaotic maps and does not require time-consuming modular exponential computations or scalar multiplications on an elliptic curve. Additionally, the proposed protocol is suitable for multiple independent groups and ensures that the real identities of group members cannot be revealed. The proposed protocol is not only more secure than related group key agreement protocols but also more efficient.
1. Introduction
A security association which manages security in a network layer is an important matter and it involves the establishment of a shared security key between two end points to support secure associations [1]. Wireless sensor networks (WSNs) consist of a large number of sensor nodes, which cannot support heavy computations, extensive communications or extensive storage and have limited bandwidth. They can be applied in many environments, such as medical monitors, military reconnaissance and communication, and others. WSNs are deployed to allow a legitimated user to login to the network and access data. The sensor node authentication has become one of the important security issues [2]. Group authenticated key agreements for WSNs enable a group of sensor nodes to authenticate each other and to establish a common key for securely communicating over public sensor networks. Group authenticated key agreement protocols typically fall into two categories, which are group key agreement protocols without public keys and group key agreement protocol using public keys. The former realize authentication and negotiates a group key using shared weak passwords or a shared long-term secret key [3,4,5,6], while the latter realize authentication and negotiate a common group key using public key systems [7,8,9]. Most group key agreement protocols that use public keys have higher security than those without. However, they depend on time-consuming modular exponential computations and scalar multiplications on an elliptic curve, and thus are not suitable for sensor networks. Recently, several group-authenticated key agreement approaches have been presented. Unfortunately, most of these protocols were developed for two communication entities (two-party) or three communication entities (three-party), and can only be extended to a group key agreement protocol with difficulty. Thus, most authenticated key agreement protocols are difficult to extend to multi-group authenticated key agreement for WSNs.
A multi-group key agreement protocol for WSNs allows communicating entities (sensor nodes) to belong to multiple groups, and enables each group to establish an independent group session key. A key hypergraph [9,10,11] is a graph where each vertex represents a party and each hyper-edge represents a relation among parties who to share a key. For instance, group members SN1, SN2, SN3, SN4 and SN5 involve groups {SN1, SN2, SN3}, {SN3, SN4, SN5}, and {SN1, SN2, SN3, SN4, SN5} and establish group keys used for secure communication. Then its key hypergraph can be denoted as G = {V, E}, where V = {SN1, SN2, SN3, SN4, SN5} is a finite set of vertices and E = {e1 = {SN1, SN2, SN3}, e2 = {SN3, SN4, SN5}, e3 = {SN1, SN2, SN3, SN4, SN5}} is a set of subsets of V, as presented in Figure 1.
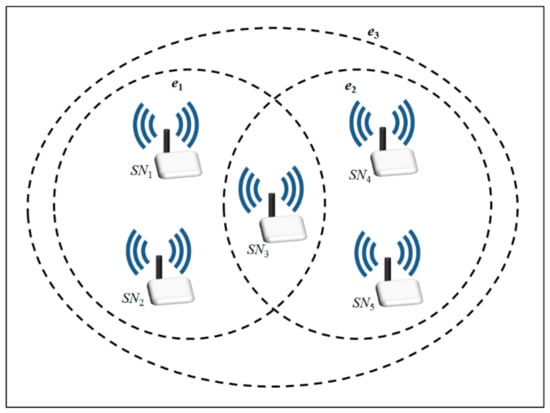
Figure 1.
In a key hypergraph, one sensor node is allowed to belong to multiple independent groups.
Key management issues are also considered to have a major impact on the security scale of WSNs [12]. Recently, several group-authenticated key agreement approaches have been presented for WSNs. For example, in 2007, Jeong and Lee [9] proposed a group-authenticated key agreement protocol that uses a public key system to build a session key; these group key approaches can be extended for hypergraphs and are suitable for use with multiple groups [9,10,11].
Users also need extra storage, such as radio frequency identification (RFID) tags, flash drives, smart cards and so on, to store public/private key pairs. In 2006, Abdalla et al. [3] developed a password-based group-authenticated key exchange that can be executed in a constant number of rounds. In the same year, Dutta and Barua [13] proposed a password-based encrypted group-authenticated key agreement protocol. Although these approaches do not require the maintenance of public key systems, all communicating users share the same password so these protocols do not protect the privacy of users. In 2013, Lee et al. [14] proposed a password-based group-authenticated key agreement protocol for the integrated electronic patient record (EPR) information system, which enabled users to have their own passwords. A multi-server authentication protocol based on dynamic identity is proposed by Sood et al. [15]. Amin et al. [16] demonstrated that Xue et al.’s protocol [17] is not protected against the user anonymity problem and cannot resist user impersonation and session key discloser attack. In 2017, Lin et al. [18] applied an extended chaotic map to present password-less group authentication key agreement which improves the computation efficiency for the simple group password-based authenticated key agreement (SGPAKE) proposed by Lee et al [19]. Although most limitations in the field of security have been overcome, the above protocols require many time-consuming modular exponential computations or scalar multiplications on elliptic curves and so are inefficient and unsuitable for use in many practical scenarios. Moreover, most of them are difficult to extend to multiple groups.
Recently, a number of key agreement protocols based on chaotic maps were proposed, which have improved computational efficiency. Using Chebyshev chaotic maps has been shown to be more efficient than cryptography using modular exponential computations and scalar multiplications on elliptic curves [20,21,22,23,24,25,26,27,28,29]. However, Chebyshev chaotic maps and their enhancement are affected by the discrete logarithm problem and the Diffie–Hellman problem [30,31,32,33]. In addition, most of them were developed for two communication entities (two-party) or three communication entities (three-party), and can only be extend to group key agreement protocol with difficulty.
In our analysis, we present a novel password-based multi-group authenticated key agreement protocol for WSNs that was based on the extended chaotic map-based Diffie–Hellman problem. The main contributions of this paper are:
(1). The proposed protocol enables one sensor node to belong to several mutually independent groups and ensures group key security. Additionally, the real identities of group members cannot be revealed.
(2). Accordingly, the proposed protocol is suitable for multiple groups and ensures users’ anonymity. It overcomes not only the limitations of previously proposed protocols and has a lower computational cost, but also offers greater security and is suitable for WSNs.
The remainder of this paper is organized as follows. The primitives used are described in Section 2. The proposed extended chaotic map-based multi-group authenticated key agreement protocol is illustrated in Section 3. In Section 4, we presented the security analysis and overall comparison. The conclusions are drawn in Section 5.
2. Preliminaries
This section lists notations and describes the underlying primitives used in this paper. The underlying primitives include Chebyshev polynomials, enhanced Chebyshev chaotic maps, the extended chaotic map-based discrete logarithm and Diffie–Hellman problems [30,31,32,33] which are described as follows and Table 1 lists the symbol system applied by the proposed solution.

Table 1.
The symbol system applied by the proposed solution.
2.1. Chebyshev Polynomials
The Chebyshev polynomials of degree n are defined as:
and the first few Chebyshev polynomials are
2.2. Semigroup Property
We have Tr(Ts(x)) = Trs(x) for different r and s, where −1 ≤ x ≤ 1. The core idea of semi-group is similar to the Diffie–Hellman problem. Semi-group implies that there is not a specific order for r and s. This property comes from Chebyshev polynomials. However, −1 ≤ x ≤ 1 is not enough to provide high security in terms of the diversity of x, and Zhang extends the mapping range from (−1,1) to (−∞, ∞) [33]. In other words, the scheme with a semi-group property has similar security to that of the Diffie–Hellman key exchange [34].
2.3. Enhanced Chebyshev Polynomials
In order to enhance the property of the Chebyshev chaotic map, Zhang [19] proved that the semi-group property holds for Chebyshev polynomials defined on interval . This paper uses the following enhanced Chebyshev polynomials:
The enhanced Chebyshev polynomials meet the semi-group property. Then,
2.4. Extended Chaotic Map-based Discrete Logarithm (ECM-DL) Problem
Given x, y, and p, it is not computationally feasible to find the satisfied integer r,
2.5. Extended Chaotic Map-based Diffie-Hellman (ECM-DH) Problem
Given Tu(x) mod p, Tv(x) mod p, T(•), x, and p, where u, v ≥ 2, , and p is a large prime number, the calculations are not feasible.
3. Proposed Multi-Group Authenticated Key Agreement Protocol for WSNs
This section presents a group authenticated key agreement protocol using extended chaotic maps for hypergraphs. The proposed protocol enables one user to belong to several independent groups, ensures group key security, and protects the real identities of group members. The proposed protocol is composed of four phases, which are the initialization phase, registration phase, the authentication and key agreement phase and the password change phase, and it is implemented as follows.
3.1. Initialization Phase
- Step 1:
- The authentication server AS randomly selects mk as its master key.
- Step 2:
- AS computes pks = Tmk(x) mod p, where x is a random number and p is a large prime number.
- Step 3:
- AS publishes parameters (pks, T(.), x, p).
3.2. Registration Phase
Step 1: SNiS:{IDi, pwi}
The sensor node SNi chooses his/her identity IDi and password pwi, and sends {IDi, pwi, Groupi} to AS over a secure channel, where Groupi = (Gi1, Gi2,…,GiN) and Gi1, Gi2,…,GiN are groups that SNi belong to.
Step 2: Upon receiving the register message from SNi, The trusted authentication server (AS) computes HIDi = h(IDi ||mk), Qi = h(IDi || pwi) and stores (HIDi, Qi, Groupi).
3.3. Authentication and Key Agreement Phase
This phase, as shown in Figure 2, enables sensor nodes SNi for i = 1,2,…,n to authenticate each other and to negotiate session keys for each group with the help of AS. First, sensor node SNi sends its password pwi to AS, which is encrypted with a secret key of SNi and AS. After AS successfully authenticates SNi, AS assists these sensor nodes in agreeing a common secret key as their group session key. The details are worked as follows.
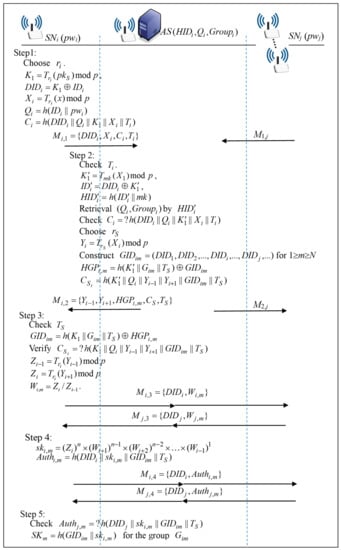
Figure 2.
The proposed multi-group authenticated key agreement protocol for wireless sensor networks (WSNs).
Step 1. SNi→AS : Mi,1 = {DIDi, Xi, Ci, Ti}
Each sensor node SNi chooses a nonce ri, computes K1 = Tri(pkS) mod p, DIDi=K1IDi, Xi = Tri(x) mod p, Qi=h(IDi||pwi), Ci = h(DIDi||Qi||K1||Xi||Ci,||Ti), where Ti is the current timestamp, and sends Mi,1 = {DIDi, Xi, Ci, Ti} to AS.
Step 2. AS→SNi :Mi,2 = {Yi-1, Yi+1, HGPi,m, CS, TS}
After receiving Mi,1, AS checks the validity of Ti. If successful, AS computes K1’ = Tmk(X1) mod p, IDi’ = DIDiK1’, HIDi’ = h(IDi’||mk), retrieves (Qi, Groupi) by HIDi’, and checks Ci = h(DIDi||Qi||K1’||Xi||Ti). If successful, AS chooses a nonce rS, computes Yi = Trs(Xi) mod p, constructs a group identity GIDim = (DID1, DID2,…,DIDi,…,DIDj,…) by using sensor nodes’ temporal identity DIDi and calculates HGPi,m = h(K1’||Gim||TS)⊕GIDim, CSi = h(K1’||Qi||Yi-1||yi+1||GIDim||TS) for i = 1,2,…,n, where TS is the current timestamp and SNi is a group member of Gim for m = 1,2,…,N, and sends Mi,2 = {Yi-1, Yi+1, HGPi,m, CS, TS} to Ui.
Step 3. SNi→* : Mi,3 = {DIDi ,Wi,m}
SNi checks TS, calculates GIDim = h(K1||Gim||TS)⊕ HGPi,m and verifies CSi = h(K1||Qi||Yi-1||yi+1||GIDim||TS). If successful, SNi computes Zi-1 = (Yi-1) mod p, Zi = (Yi+1) mod p and Wi,m = Zi / Zi-1, and broadcasts Mi,3 = {DIDi ,Wi,m}.
Step 4. SNi→* : Mi,4 = {DIDi ,Authi,m}
After receiving Mi,3 for , if SNi computes ski,m = (Zi)n×(Wi+1)n-1×(Wi+2)n-2×…×(Wi-1)1 and key confirmation Authi,m = h(DIDi||ski,m||GIDim||TS), and broadcasts Mi,4 = {DIDi ,Authi,m}.
Step 5. Finally, SNi authenticates SNj by checking Authi,m = h(DIDi||ski,m||GIDim||TS) for ji, and computes skm = h(GIDim||ski,m) for the group Gim.
3.4. Password Change Phase
A legal sensor nodes SNi changes its password by performing the following steps.
Step 1. SNi→AS : Mi,1 = {DIDi, Xi, Ci, Ti}
SNi chooses a nonce ri, computes K1 = Tri(pkS) mod p, DIDi = K1IDi, Xi = Tri(x) mod p, Qi = h(IDi||pwi), Qi_new = h(IDi||pwi_new), Di = h(K1||Ti)Qi_new, Ei = h(DIDi||Qi||Qi_new||K1||Xi||Ti), where Ti is the current timestamp, and sends Mi,1 = {DIDi, Xi ,Di, Ei, Ti} to AS.
Each sensor node SNi chooses a nonce ri, computes K1 = Tri(pkS) mod p, DIDi = K1IDi, Xi = (x) mod p, Qi = h(IDi||pwi), Ci = h(DIDi||Qi||K1||Xi||Ci,||Ti), where Ti is the current timestamp, and sends Mi,1 = {DIDi, Xi, Ci, Ti} to AS.
Step 2. AS→SNi :Mi,2 = {VSi, TS}
After receiving Mi,1, AS checks the validity of Ti. If successful, AS computes K1’ = Tmk(X1) mod p, IDi’ = DIDiK1’, HIDi’ = h(IDi’||mk), retrieves (Qi, Groupi) by HIDi’, computes Q’i_new = Dih(K1||Ti) and checks Ei = h(DIDi||Qi||Q’i_new||K’1||Xi||Ti). If successful, AS replaces Qi with Q’i_new, and calculates VSi = h(K1’||Qi||Q’i_new||K’1||Xi||Ts), where Ts is the current timestamp, and sends Mi,2 = {VSi, TS} to SNi. Finally, SNi makes sure that AS has updated SNi’s verification data in S’s database by validating Ts and checking VSi = h(K1||Qi||Qi_new||K’1||Xi||Ts).
4. Security Analysis
The security analyses on the correctness, session key security, perfect forward security, mutual authentication, and privacy protection are provided; it also resists password guessing, known-key attacks, and sensor node capture attacks.
4.1. Correctness
All legal users have the same secret ski,m since SNi computes
Thus, these sensor nodes can obtain a common session key SKm = h(GIDim||ski,m) for the group Gim.
4.2. Session Key Security
Given (xo) mod p (=
(x) mod p) and
(xo) mod p (= (x) mod p), where x0 denotes Trs(x) mod p, Yi = T = Tr•ri+1(xo) mod p (= Triri+1rs(x) mod p) cannot be determined, because of the ECM-DH problem. The values of r1,r2,…,rn and rs are randomly selected and mutually independent in each protocol execution, so the secret ski,m and the session key SKm fail to be determined without knowledge of rs and ri for 1 ≤ i ≤ n, where and SKm = h(GIDim||ski,m) for the group Gim. Hence, the session key security is based on the ECM-DH problem and is therefore considered not computationally feasible.
4.3. Perfect Forward Security
In the proposed protocol, since r1,r2,…,rn and rs are randomly selected and independent among protocol executions, a compromised password pwi does not yield any previous session keys SKm = h(GIDim||ski,m) for Gim, where . The session key security is based on the ECM-DH problem. Accordingly, the proposed protocol provides perfect forward security.
4.4. Mutual Authentication
In the proposed group key agreement scheme, only legal sensor node SNi who has the correct IDi and pwi can compute Ci = h(DIDi||Qi||K1||Xi||Ci,||Ti), where Qi = h(IDi||pwi). AS then authenticates sensor node by checking Ci = h(DIDi||Qi||K1||Xi||Ci,||Ti). Also, sensor node authenticates AS by checking CSi = h(K1||Qi||Yi-1||Yi+1||GIDim||TS). Additionally, only legal SNi in Gi,m can compute . Then, SNi authenticates SNj by checking Authi,m = h(DIDi||ski,m||GIDim||TS) for ji. Therefore, the participants of the proposed protocol authenticate each other.
4.5. Privacy Protection
In the proposed protocol, DIDi implicitly involves the identity of SNi, IDi, where DIDi = K1IDi. Attackers cannot derive IDi from DIDi because IDi is protected by K1 and the security of K1 (= Trmk mod p) is based on the ECM-DH problem. Additionally, the group identity GIDim = (DID1, DID2,…,DIDi,…,DIDn) is protected by h(K1||Gim||Ts) (or K1). No one can derive GIDim from the revealed message HGPim, where HGPim = h(K1||Gim||Ts)GIDim. Another group member SNi cannot recognize the group members of Gim to which SNi does not belong. Thus, the proposed protocol ensures users’ privacy protection.
4.6. Resistance to Undetectable On-Line Password-Guessing Attacks
In the proposed protocol, an adversary SNi* cannot compute the correct Ci = h(DIDi||h(IDi||pwi)||K1||Xi||Ti) without SNi’s identity IDi, where K1 = Tri(pkS) mod p, DIDi = K1IDi, Xi = Tri(x) mod p and Ti is the timestamp, and so such an adversary fails to send out Mi,1 = {DIDi, Xi, Ci, Ti} in Step 1. Additionally, SNi* who has IDi and is disguised as SNi guesses a password pwi*, computes Ci* = h(DIDi||Qi*||K1||Xi||Ti), where Qi* = h(IDi||pwi*) and sends M*i,1 = {DIDi, Xi, Ci*, Ti} to S in Step 1. After receiving M*i,1, AS will detect this failed password-guessing by checking Ci = h(DIDi||Qi||K1’||Xi||Ti) in Step 2, where K’1 = Tmk(X1) mod p, IDi’ = DIDiK1’, HID’I = h(ID’i||mk), Qi = h(IDi||pwi). Therefore, the proposed protocol is secure against undetectable on-line password-guessing attacks.
4.7. Resistance to Off-Line Password-Guessing Attacks
In the authentication and key agreement phase of the proposed protocol, only messages Ci = h(DIDi||Qi||K1||Xi||Ci||Ti) in Mi,1 and CSi = h(K1||Qi||Yi-1||Yi+1||GIDim||TS) in Mi,2 contain password pwi, where Qi = h(IDi||pwi). However, pwi is protected by K1, and the one-way property of hash functions. Similarly, in the password change phase of the proposed protocol, only messages Di = h(K1||Ti)Qi_new and Ei = h(DIDi||Qi||Qi_new||K1||Xi||Ti) in Mi,1 and CSi = h(K1||Qi||Yi-1||Yi+1||GIDim||TS) in Mi,2 contain password pwi, where K1 = Tri(pkS) mod p, DIDi = K1IDi, Qi = h(IDi||pwi) and Qi_new = h(IDi||pwi_new). However, pwi and pwi_new are protected by K1 and the one-way property of hash functions. No information helps to confirm the correctness of the guessed passwords, so off-line password-guessing attacks are unsuccessful against the proposed protocol.
4.8. Known-Key Security
The session keys SKm = h(GIDim||ski,m), generated in various runs, are mutually independent, where , since r1,r2,…,rn and rS are randomly selected by SN1, SN2,…, SNn and AS, respectively, and are independent across protocol executions. Thus, the proposed group key agreement protocol exhibits known-key security.
4.9. Resistance to Sensor Node Capture Attacks
In the proposed scheme, each sensor node SNi has its secrets (IDi, pwi). An attacker A who has captured SNj and obtained IDj cannot derive other sensor node SNi’s secrets (IDi, pwi), and thus cannot impersonate SNi and AS.
5. Performance Analyses and Comparisons
The performance of the proposed protocol in communication was compared with that of related approaches. Table 2 presents a performance comparison of the group authenticated key agreement (GAKA) protocols of Abdalla et al. [3], Kim et al. [7], Boyd and Nieto [8], and Dutta and Barua [13] and the protocol that was proposed herein, where Tchao denotes the time required to execute a Chebyshev chaotic map operation; Tsym denotes the time required to execute a symmetric encryption/decryption operation; Texp denotes the time required to execute a modular exponential operation, Tsign/veri denotes the time required to execute a signing/verifying operation in the public key system, and Tchao < Tsym < Texp (≈ Tsign/veri) [35,36].

Table 2.
Comparisons of other related protocols and the proposed protocol.
The first comparison concerned computations. These GAKA protocols [3,7,8,13,14] require many time-consuming modular exponential computations or scalar multiplications on elliptic curves to realize authentication and negotiate group keys. Only the proposed GAKA protocol was developed using extended chaotic map operations and did not have a heavy computational burden. Thus, the proposed GAKA protocol was more efficient than the other GAKA protocols.
The second comparison concerned the realization of user authentication in each protocol. The protocols of Kim et al. [7] and Boyd and Nieto [8] realize authentication using users’ public keys. The GAKA protocols of Abdalla et al. [3], Dutta and Barua [13], and Lee et al. [14] as well as the proposed GAKA protocol realize authentication using users’ passwords. However, in the GAKA protocols of Abdalla et al. [3] and Dutta and Barua [13], all users share the same password so their protocols do not ensure users’ privacy.
The third comparison concerned whether the protocol required the maintenance of users’ public keys. The protocols of Kim et al. [7] and Boyd and Nieto [8] employ users’ public keys, and thus require extra equipment to store long-term secret keys and the results of time-consuming exponential computations in clients. The GAKA protocols of Abdalla et al. [3], Dutta and Barua [13], and Lee et al. [14] as well as the proposed GAKA protocol are password-based authentication protocols. Each user remembers only his weak password without the need for any extra equipment to store long-term secret keys.
The fourth comparison involved whether the protocol was suitable for hypergraphs. The GAKA protocols [3,7,8,13] consider only a single group, and are difficult to extend to multiple groups. The protocol of Kim et al. [7] and the proposed GAKA protocol enable communicating entities to belong to multiple groups, and so are effective for hypergraphs.
The final comparison involved whether the protocol provided the anonymity of users. The GAKA protocols [3,7,8,13,14] reveal users’ identities, and fail to protect user privacy. Only the proposed GAKA protocol did not reveal users’ identities, and so protected users’ anonymity.
Table 3 lists the simulation environment, including used hardware/software specifications and algorithms. Figure 3 illustrates simulation results for the response time of related protocols and the proposed one for n = 5, 10, 15,…, 30. Due to the use of extended Chebyshev chaotic map operations, the proposed protocol required less response time than related protocols.

Table 3.
Simulation environment.
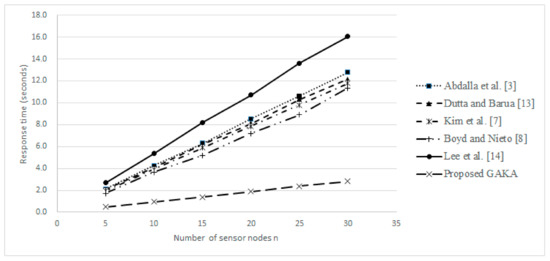
Figure 3.
The response time of related protocols and the proposed one.
6. Conclusions
This work presented an efficient and secure group authenticated key agreement protocol for WSNs, which enabled sensor nodes to belong to multiple independent groups. The proposed protocol used extended chaotic map operations, did not require time-consuming computations, and thus was more computationally efficient than other group-authenticated key agreement protocols. Moreover, it did not require the maintenance of users’ public keys or extra equipment for storing a long-term secret key, and resisted potential attacks and provided more functionality than comparable approaches. The proposed protocol is not only suitable for WSNs, but also can be implemented in the current environment involving database systems, file sharing systems, broadcasting radio/TV systems, and others.
Author Contributions
Conceptualization, M.-S.C., I.-P.C. and T.-K.L.; Methodology, M.-S.C. and I.-P.C.; Writing—Original draft preparation, M.-S.C. and I.-P.C.; Writing—Review and editing, M.-S.C., I.-P.C. and T.-K.L.; Funding acquisition, I.-P.C.
Funding
This study was supported in part by grants from the Ministry of Science and Technology of the Republic of China (Grant No. 104-2221-E-426-001).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Blaze, M. Trust Management and Network Layer Security Protocols. In International Workshop on Security Protocols; Springer: Berlin/Heidelberg, Germany, 1999; pp. 109–118. [Google Scholar]
- Hsieh, W.B.; Leu, J.S. A dynamic identity user authentication scheme in wireless sensor networks. In Proceedings of the 9th International Wireless Communications and Mobile Computing Conference (IWCMC), Sardinia, Italy, 1–5 July 2013; pp. 1132–1137. [Google Scholar]
- Abdalla, M.; Bresson, E.L.; Chevassut, O.; Pointcheval, D. Password-based group key exchange in a constant number of rounds. In Public Key Cryptography—PKC 2006; Springer: Berlin/Heidelberg, Germany, 2006. [Google Scholar]
- Tang, Q.; Choo, K.K.R. Secure password-based authenticated group key agreement for data-sharing peer-to-peer networks. In International Conference on Applied Cryptography and Network Security ACNS 2006; Springer: Berlin/Heidelberg, Germany, 2006; pp. 162–177. [Google Scholar]
- Pecori, R. A comparison analysis of trust-adaptive approaches to deliver signed public keys in P2P systems. In Proceedings of the 7th International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 27–29 July 2015. [Google Scholar]
- Pecori, R.; Veltri, L. 3AKEP: Triple-authenticated key exchange protocol for peer-to-peer VoIP applications. Comput. Commun. 2016, 85, 28–40. [Google Scholar] [CrossRef]
- Kim, H.-J.; Lee, S.-M.; Lee, D.-H. Constant-round authenticated group key exchange for dynamic groups. In Advances in Cryptology—ASIACRYPT 2004 LNCS 3329; Springer: Berlin/Heidelberg, Germany, 2004; pp. 245–259. [Google Scholar]
- Boyd, C.; Nieto, J.M.G. Round-optimal contributory conference key agreement. In Public Key Cryptography—PKC 2003 LNCS 2567; Springer: Berlin/Heidelberg, Germany, 2003; pp. 161–174. [Google Scholar]
- Jeong, I.; Lee, D. Key agreement for key hypergraph. Comput. Secur. 2007, 26, 452–458. [Google Scholar] [CrossRef]
- Voloshin, V.I. Introduction to Graph and Hypergraph Theory; Nova Science Publishers: New York, NY, USA, 2009. [Google Scholar]
- Bretto, A. Hypergraph Theory; Springer: Berlin, Germany, 2013. [Google Scholar]
- Gandino, F.; Celozzi, C.; Rebaudengo, M. A Key Management Scheme for Mobile Wireless Sensor Networks. Appl. Sci. 2017, 7, 490. [Google Scholar] [CrossRef]
- Dutta, R.; Barua, R. Password-based encrypted group key agreement. Int. J. Netw. Secur. 2006, 3, 30–41. [Google Scholar]
- Lee, T.F.; Chang, I.P.; Wang, C.C. Simple group password-based authenticated key agreements for the integrated EPR information system. J. Med. Syst. 2013, 37, 9916. [Google Scholar] [CrossRef]
- Sood, S.K.; Sarje, A.K.; Singh, K. A secure dynamic identity based authentication protocol for multi-server architecture. J. Netw. Comput. Appl. 2011, 34, 609–618. [Google Scholar] [CrossRef]
- Amin, R.; Kumar, N.; Biswas, G.P.; Iqbal, R.; Chang, V. A light weight authentication protocol for IoT-enabled devices in distributed Cloud Computing environment. Future Gener. Comput. Syst. 2018, 78, 1005–1019. [Google Scholar] [CrossRef]
- Xue, K.; Hong, P.; Ma, C. A lightweight dynamic pseudonym identity based authentication and key agreement protocol without verification tables for multi-server architecture. J. Comput. Syst. Sci. 2014, 80, 195–206. [Google Scholar] [CrossRef]
- Lin, T.H.; Tsung, C.K.; Lee, T.F.; Wang, Z.B. A round-efficient authenticated key agreement scheme based on extended chaotic maps for group cloud meeting. Sensors 2017, 17, 2793. [Google Scholar] [CrossRef]
- Lee, T.F.; Wen, H.A.; Hwang, T. A weil pairing-based round-efficient and fault-tolerant group key agreement protocol for sensor networks. In Sensor Network Operations; IEEE Press: Piscataway, NJ, USA, 2006; pp. 571–579. [Google Scholar]
- Xiao, D.; Liao, X.; Deng, S. Using time-stamp to improve the security of a chaotic maps-based key agreement protocol. Inf. Sci. 2008, 178, 1598–11602. [Google Scholar] [CrossRef]
- Han, S.; Chang, E. Chaotic map based key agreement with/out clock synchronization. Chaos Solitons Fractals 2009, 39, 1283–1289. [Google Scholar] [CrossRef]
- Xiao, D.; Liao, X.; Deng, S. A novel key agreement protocol based on chaotic maps. Inf. Sci. 2007, 177, 136–1142. [Google Scholar] [CrossRef]
- Guo, X.; Zhang, J. Secure group key agreement protocol based on chaotic hash. Inf. Sci. 2010, 180, 4069–4074. [Google Scholar] [CrossRef]
- Gong, P.; Li, P.; Shi, W. A secure chaotic maps-based key agreement protocol without using smart cards. Nonlinear Dyn. 2012, 70, 2401–2406. [Google Scholar] [CrossRef]
- Niu, Y.; Wang, X. An anonymous key agreement protocol based on chaotic maps. Commun. Nonlinear. Sci. Numer. Simulat. 2011, 16, 1986–1992. [Google Scholar] [CrossRef]
- Farash, M.S.; Attari, M.A. Cryptanalysis and improvement of a chaotic map-based key agreement protocol using chebyshev sequence membership testing. Nonlinear Dyn. 2014, 76, 1203–1213. [Google Scholar] [CrossRef]
- Lou, D.-C.; Lee, T.-F.; Lin, T.-H. Efficient biometric authenticated key agreements based on extended chaotic maps for telecare medicine information systems. J. Med. Syst. 2015, 39, 58. [Google Scholar] [CrossRef]
- Lee, T.-F. Efficient three-party authenticated key agreements based on Chebyshev chaotic map-based diffie-hellman assumption. Nonlinear Dyn. 2015, 81, 2071–2078. [Google Scholar] [CrossRef]
- Lee, T.-F.; Lin, C.-Y.; Lin, C.-L.; Hwang, T. Provably secure extended chaotic map-based three-party key agreement protocols using password authentication. Nonlinear Dyn. 2015, 82, 29–38. [Google Scholar] [CrossRef]
- Kocarev, L.; Tasev, Z. Public-key encryption based on Chebyshev maps. In Proceedings of the IEEE International Symposium on Circuits and Systems 3, Bangkok, Thailand, 25–28 May 2003. [Google Scholar]
- Mason, J.C.; Handscomb, D.C. Chebyshev Polynomials; Chapman & Hall/CRC: Boca Raton, FL, USA, 2003. [Google Scholar]
- Bergamo, P.; D’Arco, P.; Santis, A.; Kocarev, L. Security of public-key cryptosystems based on Chebyshev polynomials. IEEE Trans. Circuits Syst. I 2005, 52, 1382–1393. [Google Scholar] [CrossRef]
- Zhang, L. Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos Solitons Fractals 2008, 37, 669–674. [Google Scholar] [CrossRef]
- Wang, X.; Zhao, J. An Improved Key Agreement Protocol based on Chaos. Commun. Nonlinear Sci. Numer. Simul. 2010, 15, 4052–4057. [Google Scholar] [CrossRef]
- Wu, S.; Chen, K. An efficient key-management scheme for hierarchical access control in e-medicine system. J. Med. Syst. 2012, 36, 2325–2337. [Google Scholar] [CrossRef] [PubMed]
- Cheng, Z.Y.; Liu, Y.; Chang, C.C.; Chang, S.C. Authenticated RFID security mechanism based on chaotic maps. Secur. Comm. Netw. 2013, 6, 247–256. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).