Abstract
This paper investigates robust -based control for autonomous underwater vehicle (AUV) systems under time-varying delay, model uncertainties, and cyber-attacks. Sensor and actuator cyber-attacks can cause faults in the overall AUV system. In addition, the behavior of the system can be affected by the presence of complexities, such as unknown random uncertainties that occur in system modeling. In this paper, the robustness against unpredictable random uncertainties is investigated by considering unknown but norm-bounded (UBB) random uncertainties. By constructing a proper Lyapunov–Krasovskii functional (LKF) and using linear matrix inequality (LMI) techniques, new stability criteria in the form of LMIs are derived such that the AUV system is stable. Moreover, this work is novel in addressing robust control, which considers time-varying delay, cyber-attacks, and randomly occurring uncertainties for AUV systems. Finally, the effectiveness of the proposed results is demonstrated through two examples and their computer simulations.
1. Introduction
Autonomous underwater vehicles (AUVs) have become indispensable robotic devices for ocean exploration that carry out various military and civilian applications, including ocean floor surveying, oceanographic data gathering, minefield surveying, pipeline inspection, and anti-submarine warfare [1,2,3]. Research in underwater vehicles has been very active in the past few decades with the advancement of control, sensing, communication, and computing technologies. In practice, controlling the stability of AUV is a challenging task during underwater operations and time-varying disturbances [4], i.e., the payload, mass, dynamics, and buoyancy will change when performing different tasks. In addition, AUV suffers from marine environmental external disturbances, i.e., wakes, ocean currents [5,6], and unpredictable uncertainties [7,8,9].
In recent years, the security of autonomous marine vehicles has attracted much attention because attackers can access a set of sensors and actuator devices, modify their software or environment, and carry out coordinated attacks on the system design. In cyber-security, control technology has been widely applied, and it is well known that control performance depends on the quality of control input and sensor measurement signals [10]. Recently, sensor and actuator attacks were presented in adaptive neural dissipative control for Markovian jump cyber-physical systems [11], resilient control of cyber-physical systems [12], and cyber-attacks in industrial control systems [13]. A secure tracking control was developed in [14] to guarantee the prescribed security in systems with sensor and actuator attacks. Actuator saturation and probabilistic cyber-attacks were discussed in uncertain networked control systems [15]. The hybrid-driven-based resilient control for T-S fuzzy systems with time-delay and cyber-attack was investigated in [16].
The behavior of the system can be affected by complexities such as random uncertainties that occur during system modeling. These complexities are subject to random changes in complicated circumstances, exceptional environmental disturbances, random failures, modeling errors, varying geometry and material properties, repairs of system components, and so forth, which may occur in a probabilistic way. The appearance of parameter uncertainties often exhibits a random nature, because of unpredictable changes. As a result, the so-called randomly occurring uncertainty (ROU) is usually controlled by Bernoulli-distributed stochastic variables. In recent years, the concept of randomly occurring uncertainties has been investigated in [17,18].
Time-varying delay frequently occurs in AUV controls, and it may cause undesirable transient system responses, diminish system performance, and even lead to instability. References [19,20] discussed unknown uncertainties and time-varying delays in AUV systems. In recent years, the concept of time-varying delay and delays in vehicle systems has been investigated [21,22,23]. In [19,20], robustness against unpredictable uncertainties was investigated by considering unknown but norm-bounded (UBB) uncertainties. However, note that UBB random uncertainties were not handled in [19,20].
Inspired by [19,20], our paper addresses robustness against unpredictable random uncertainties by considering UBB random uncertainties. Moreover, we handle time-varying delay in AUV controls. However, to the best of our knowledge, cyber-attacks were not handled in the control of AUV systems. To the best of our knowledge, no papers are available on the stabilization of AUV systems with time-varying delay, randomly occurring uncertainties, and cyber-attacks.
In our paper, we design a robust control for autonomous underwater vehicle systems under time-varying delay, uncertain random models, and cyber-attacks. The AUV model and schematic of the AUV system in the presence of cyber-attacks and external disturbances are shown in Figure 1. The effectiveness of the proposed control is demonstrated by two examples and their computer simulations. Using computer simulations, we compare the performance of our robust control with controls in [19,20], and present the outperformance of the proposed control.
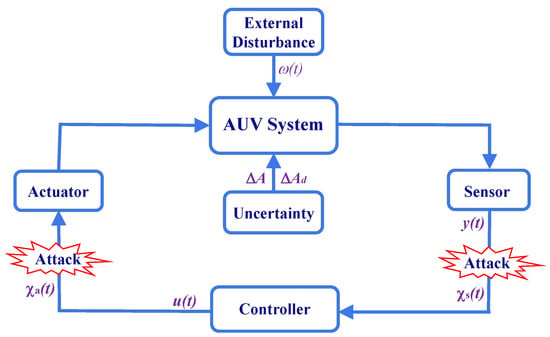
Figure 1.
Schematic diagram of AUV system in the presence of cyber-attacks and external disturbances.
2. Problem Formulation and Preliminaries
In this section, problem formulation, basic assumptions, definition, and lemma are given.
Notations: In this work, and denotes the n-dimensional Euclidean real space, and the set of real matrices; “T” is the superscript for matrix transposition; “(−1)” is the superscript for matrix inverse. In a symmetric matrix, the symmetric term is indicated by the symbol “∗”. The notation P > 0 (<0) indicates that positive definite (negative definite) symmetric matrix and “I” is the identity matrix with the proper dimension.
2.1. AUV System I with Time-Varying Delay
Motivated by [19], we consider the class of continuous-time linear uncertain time-varying delay systems of the form:
where is the state at time t, is the control input, is the external disturbance that belongs to , is the measured output, and is the initial state condition. A, , B, , and C are known matrices of appropriate dimensions. is a nonnegative time-varying delay affecting the system states, assumed to be bounded as and , where . The state feedback controller can be designed and formulated as follows:
where K is the feedback control gain.
According to [19,20], and represent the UBB uncertainties in system (1) satisfying:
where , , , and are known as constant matrices with appropriate dimensions and is an unknown matrix with Lebesgue measurable elements and satisfies .
Note that the behavior of the system can be affected by the presence of complexities, such as random uncertainties that occur during the process of system modeling. The appearance of parameter uncertainties often exhibits a random nature, due to unpredictable changes. As a result, the ROU is usually controlled by Bernoulli-distributed stochastic variables. In recent years, the concept of randomly occurring uncertainties has been investigated [17,18].
In our paper, the randomly occurring UBB uncertainties are assumed to follow a Bernoulli distribution, which is expressed as follows:
where is a known constant. The stochastic variable is introduced to characterize the randomly occurring uncertainties.
Now, considering the randomly occurring uncertainties [17] and the sensor and actuator attacks [24] in system (1), we have the following formulation:
where denotes the state vector affected by the actuator attack , is the measurable output affected by the sensor attack , and nonlinear functions and are used to model the cyber signals inserted by attackers. The probability of the event that the system’s actuator or sensor has been affected by a cyber-attack is denoted by (or ).
According to [25], both and are Markovian stochastic processes with the binary state (0 or 1), which satisfy the following probability:
where an actuator cyber-attack (or a sensor cyber-attack ) happens when event (or ), which indicates that the actuator (or the sensor) of the system is the target of a cyber-attack. On the other hand, event (or ) indicates that there is no cyber-attack on the actuator (or on the sensor). A cyber-attack on the system’s actuator (or sensor) is represented as (or ), which indicates the possibility of the attack.
2.2. AUV System II with Time-Varying Delays
2.3. AUV Auxiliary State Dynamics System
Let us consider a continuous-time reference model described as follows:
where and are the state and the output of the reference model, respectively. We define an auxiliary state vector as follows:
where is a matrix, as defined in [19]. By using outputs (1) and (13), we have an output tracking error:
Definition 1
([26]). System is said to satisfy robust performance if the following conditions are satisfied:
- (1)
- The closed-loop system from with is asymptotically stable for admissible uncertainties satisfying .
- (2)
- Under the zero initial condition, one satisfies:where is a given constant.
Note that the output tracking error depends on the auxiliary state dynamics system ; we define the tracking performance index as follows:
Lemma 1
([27]). (Schur complement) For a given matrix with and , then the following conditions are equivalent:
- (1)
- ;
- (2)
- , .
Lemma 2
([28]). (Jensen’s Inequality) For any symmetric positive definite matrix , scalars and satisfying , vector function , the following integral inequality holds:
3. Main Results
3.1. Stability of AUV System with Time-Varying Delays
Theorem 1.
For given positive scalars , ρ, , the uncertain time-varying delay system (4) under controller (2) is asymptotically stable and satisfies the performance level γ, if there exist symmetric positive definite matrices , , , , , , and for any matrix , with compatible dimensions, one satisfies , such that the following LMI holds:
where
, , , , , , , , , , , , , , , , ,
Proof.
Let us consider the following Lyapunov–Krasovskii functional:
where
It should be noted that the inequalities (17), (19), and (20) come from Jensen’s inequality (Lemma 2), and the inequality (21) comes from Theorem 1 of [29].
By using Definition 1 and combining it with (14), (16) and (21), we have:
where and
, , , , , , , , , , , , .
Pre- and post-multiplying both sides of by diag and matrix variables denoted by , , then, one gets:
It is noted that (23) is not an LMI condition because of the term . In view of the inequality , we have:
Now, separating the measured output and uncertainties from and in , we have:
where
Using Lemma 2 of [20], we have:
Theorem 2.
For given positive scalars , ρ, , the uncertain time-varying delays system (6) under controller (2) is asymptotically stable and satisfies the performance level γ, if there exist symmetric positive definite matrices , , , , , , and for any matrix , with compatible dimensions, one satisfies , such that the following LMI holds:
where
, , , , , , , , , , , , , , , , , , , , and all other parameters are defined in Theorem 1. Furthermore, the controller gain matrix is given by .
3.2. Stability of Auxiliary State Dynamics System
In this subsection, we establish the stability of the auxiliary state dynamics system.
Theorem 3.
For given positive scalars , ρ, , the auxiliary system (10) under controller (2) is asymptotically stable and satisfies the tracking performance level γ, if there exist symmetric positive definite matrices , , , , , , , , and for any matrix , with compatible dimensions, one satisfies , such that the following LMI holds:
where
.
Proof.
Let us consider the following Lyapunov–Krasovskii functional:
where
It should be noted that the positive definite matrices diag {P, , diag {, , and diag {, . From Equation (29)–(31), the solution is similar to that of Equations (17)–(21). Now, consider the condition following index:
Under zero-initial conditions, we have and , which leads to the following result:
Then, combining (29)–(32), we have the expression:
where and is defined as later. Using the Schur complement lemma, the right-hand side of inequality (33) is equivalent to the matrix , resulting in:
where , , , , , , , , , , , , , , , , , , , , ,
Pre- and post-multiplying both sides of by diag {, , , , , I, , , , , I, I} and using similar arguments from Theorem 1 with , we obtain the following result. Separating the uncertainties from and in , we have:
Using Lemma 2 of [20], we have:
Theorem 4.
For given positive scalars , ρ, , the auxiliary system (11) under controller (2) is asymptotically stable and satisfies the tracking performance level γ, if there exist symmetric positive definite matrices , , , , , , , , and for any matrix , with compatible dimensions, one satisfies , such that the following LMI holds:
where
, , , and all other parameters are defined in Theorem 3. Furthermore, the controller gain matrix is given by .
4. Computer Simulation Examples
In this section, to verify the effectiveness of our work, two examples are implemented using the MATLAB R2023b Toolbox. To the best of our knowledge, this paper is novel in addressing robust controls that consider time-varying delays, cyber-attacks, and randomly occurring uncertainties for AUV systems. Using computer simulations, we compare the performance of our robust control with controls in [19,20], and demonstrate the outperformance of the proposed control.
Example 1.

The simulations are conducted on a model of an autonomous underwater vehicle [19]. The system matrices are converted from discrete-time to continuous-time using the MATLAB command “d2c”. The AUV system matrices are listed in Table 1, and the matrices , . The initial states are , external disturbance , and time-varying delay . In order to describe the uncertain measurements:

Table 1.
Continuous-time and discrete-time system matrices.
The first four cases present the simulation results for Theorem 1, and the last case presents the simulation results for Theorem 3.
- Case 1.
- (AUV system I with time-varying delay) For the simulation of Theorem 1, using the following parameter values: time , performance level minimum , lower bound , upper bound , , the probability of an random event occurs , the possibility of an actuator attack , the possibility of a sensor attack , the probability of an actuator attack , the probability of a sensor attack , , , and . We obtained the control gain matrix for the AUV system (4). Thus, the state trajectories simulation result is shown in Figure 2.
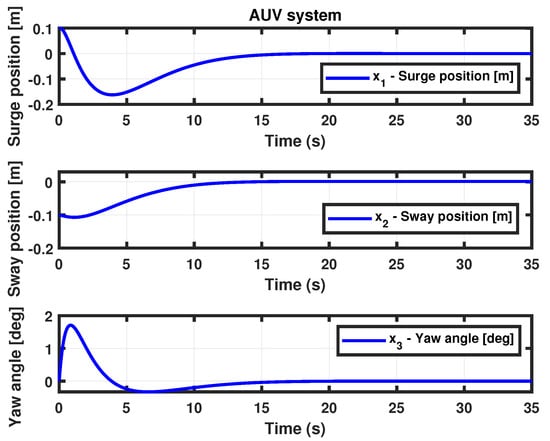 Figure 2. State trajectories of AUV for Theorem 1.
Figure 2. State trajectories of AUV for Theorem 1. - Case 2.
- Case 3.
- Case 4.
- (Sensor attack and measured output) The simulation comparison of the measured output with a sensor attack is shown in Figure 4a. Additionally, the disturbance graph is presented in Figure 4b.
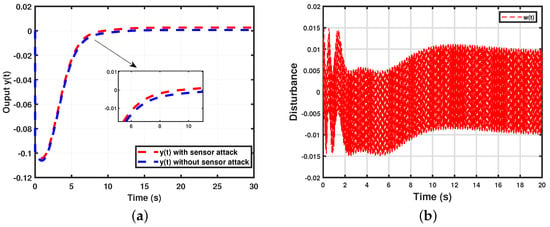 Figure 4. Simulation results for Theorem 1. (a) Comparison of output y(t). (b) Disturbance.
Figure 4. Simulation results for Theorem 1. (a) Comparison of output y(t). (b) Disturbance.
A comparative analysis of the surge and sway positions, as well as the yaw angle, is presented in Table 2.

Table 2.
Comparative analysis of surge, sway positions, and yaw angle.
In Table 3, the lower bound, upper bound, and controller settling time are compared with reference [19].
- Case 5.
Moreover, Theorem 3 obtained the control gain matrix by using the same parameters as Theorem 1. The surge and sway positions, as well as the yaw angle of the auxiliary system state trajectories, are shown in Figure 5.
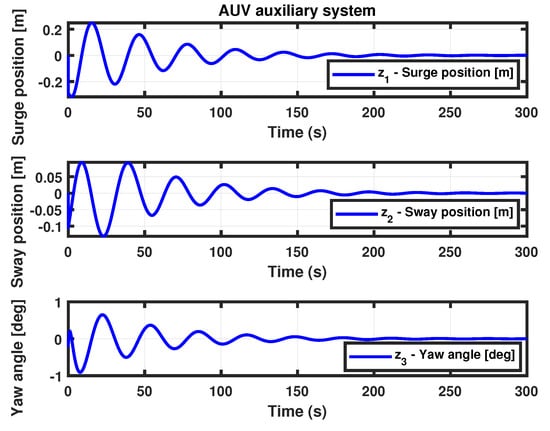
Figure 5.
Simulation results for Theorem 3.
Example 2.
We will adopt the continuous-time system as the one considered in [20], and the system matrices and are defined in Example 1, and uncertain measurements . The initial states are , and time-varying delay is defined as .
The first three cases present the simulation results for Theorem 2, and the last case presents the simulation results for Theorem 4.
- Case 1.
- (AUV system II with time-varying delays) For the simulation of Theorem 2, we used the following parameter values: time , performance level minimum , lower bound , upper bound , , the probability of an random event occurs , the possibility of an actuator attack , the possibility of a sensor attack , the probability of an actuator attack , the probability of a sensor attack , , , and . We obtained the controller gain matrix for the AUV system (6). Thus, the state trajectories simulation result is presented in Figure 6.
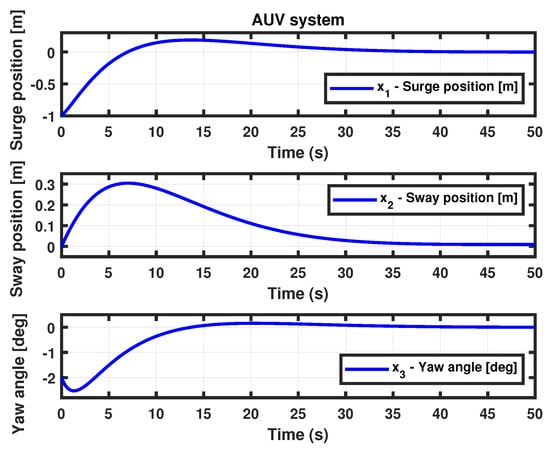 Figure 6. State trajectories of AUV for Theorem 2.
Figure 6. State trajectories of AUV for Theorem 2. - Case 2.
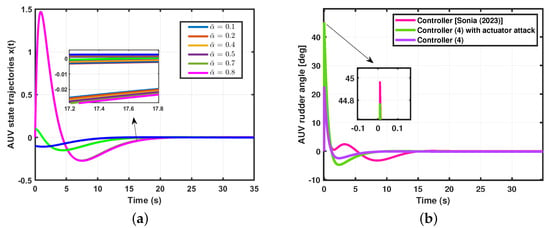
- (Actuator attacks and controller) When actuator attacks occur with in system (6), the simulation results of these different probabilities of actuator attacks are shown in Figure 7a. The performance of the controller , compared with that of the actuator attack, is presented in Figure 7b.
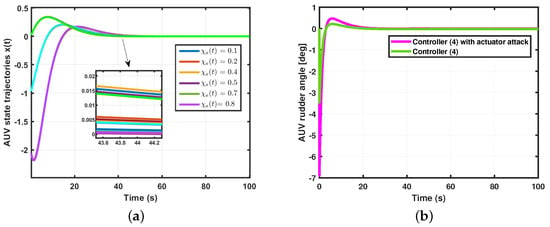 Figure 7. Simulation results for Theorem 2. (a) Comparison of actuator attack . (b) Comparison of controller (2).
Figure 7. Simulation results for Theorem 2. (a) Comparison of actuator attack . (b) Comparison of controller (2). - Case 3.
- (Sensor attacks and measured output) The simulation comparison of the measured output with a sensor attack is shown in Figure 8a. Additionally, the time-varying delay graph is presented in Figure 8b.
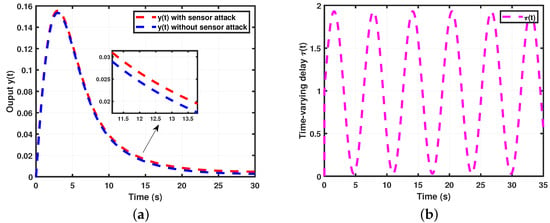 Figure 8. Simulation results for Theorem 2. (a) Comparison of output y(t). (b) Time-varying delay .
Figure 8. Simulation results for Theorem 2. (a) Comparison of output y(t). (b) Time-varying delay . - Case 4.
- (Auxiliary state dynamics system II) Theorem 4 for the AUV auxiliary system yields the controller gain matrix , using the same parameter values as in Theorem 2. The surge and sway positions, along with the yaw angle of the auxiliary system state trajectories, are shown in Figure 9.
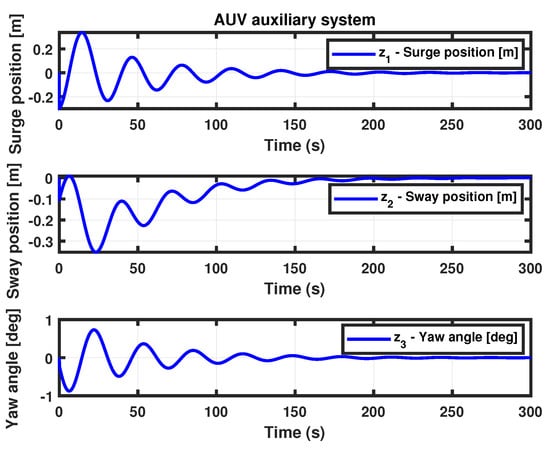 Figure 9. Simulation results for Theorem 4.
Figure 9. Simulation results for Theorem 4.

Table 4.
Comparative analysis of surge, sway, and yaw positions.
5. Conclusions
In this article, we address the robust control problem of AUVs under time-varying delay, model uncertainties, and cyber-attacks. To the best of our knowledge, this paper is novel in addressing robust control, considering time-varying delays, cyber-attacks, and randomly occurring uncertainties in AUV systems.
A continuous-time linear uncertain time-varying delay system is established for the concerned AUVs. Based on the continuous-time time-varying delay system with consideration of randomly occurring uncertainties, a stochastic sensor and actuator attacks are derived. A robust controller is proposed for the established AUV systems under time-varying delay, uncertain random models, and cyber-attacks. It is proven that the resulting closed-loop system is asymptotically stable. In addition, asymptotic stability is discussed in the auxiliary state dynamic system.
Author Contributions
This paper is written by S.V.K. This paper is supervised and revised by J.K. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the National Research Foundation of Korea (NRF) grant funded by the Korea government (MSIT) (Grant Number: 2022R1A2C1091682).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are available on reasonable request.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Thuyen, N.A.; Thanh, P.N.N.; Anh, H.P.H. Adaptive finite-time leader-follower formation control for multiple AUVs regarding uncertain dynamics and disturbances. Ocean Eng. 2023, 269, 113503. [Google Scholar] [CrossRef]
- Li, Y.; He, J.; Shen, H.; Zhang, W.; Li, Y. Adaptive practical prescribed-time fault-tolerant control for autonomous underwater vehicles trajectory tracking. Ocean Eng. 2023, 277, 114263. [Google Scholar] [CrossRef]
- Wang, Y.; Wang, Z.; Chen, M.; Kong, L. Predefined-time sliding mode formation control for multiple autonomous underwater vehicles with uncertainties. Chaos Solitons Fractals 2021, 144, 110680. [Google Scholar] [CrossRef]
- Li, J.; Du, J.; Chang, W.J. Robust time-varying formation control for underactuated autonomous underwater vehicles with disturbances under input saturation. Ocean Eng. 2019, 179, 180–188. [Google Scholar] [CrossRef]
- Li, J.; Du, J.; Hu, X. Robust for dynamic positioning of ships under unknown disturbances and input constraints. Ocean Eng. 2020, 206, 107254. [Google Scholar] [CrossRef]
- Li, X.G.; Wang, J.M. Fuzzy active disturbance rejection control design for autonomous underwater vehicle manipulators system. Adv. Control Appl. 2021, 3, e44. [Google Scholar] [CrossRef]
- Liu, H.; Lyu, Y.; Lewis, F.L.; Wan, Y. Robust time-varying formation control for multiple underwater vehicles subject to nonlinearities and uncertainties. Int. J. Robust Nonlinear Control 2019, 29, 2712–2724. [Google Scholar] [CrossRef]
- Xu, Y.; Wan, L.; Zhang, Z.; Chen, G. Robust adaptive path following control of autonomous underwater vehicle with uncertainties and communication bandwidth limitation. Ocean Eng. 2023, 287, 115895. [Google Scholar] [CrossRef]
- Shojaei, K.; Chatraei, A. Robust platoon control of underactuated autonomous underwater vehicles subjected to nonlinearities, uncertainties and range and angle constraints. Appl. Ocean Res. 2021, 110, 102594. [Google Scholar] [CrossRef]
- Li, T.; Wang, W.; Chen, W. Mixed H∞ and passive event-triggered control for Markovian jump systems with sensor saturation under cyber-attacks. Asian J. Control 2022, 24, 3588–3600. [Google Scholar] [CrossRef]
- Zhang, H.; Chen, Z.; Zhao, N.; Xing, B.; Mathiyalagan, K. Adaptive neural dissipative control for markovian jump cyber-Physical systems against sensor and actuator attacks. J. Frank. Inst. 2023, 360, 7676–7698. [Google Scholar] [CrossRef]
- Nateghi, S.; Shtessel, Y.; Edwards, C. Resilient control of cyber-physical systems under sensor and actuator attacks driven by adaptive sliding mode observer. Int. J. Robust Nonlinear Control 2021, 31, 7425–7443. [Google Scholar] [CrossRef]
- Syfert, M.; Ordys, A.; Kościelny, J.M.; Wnuk, P.; Możaryn, J.; Kukiełka, K. Integrated approach to diagnostics of failures and cyber-attacks in industrial control systems. Energies 2022, 15, 6212. [Google Scholar] [CrossRef]
- Huang, X.; Dong, J. Secure tracking control against sensor and actuator attacks: A robust model-reference adaptive control method. Inf. Sci. 2022, 604, 11–27. [Google Scholar] [CrossRef]
- Huang, X.; Xing, M.; Mo, H.; Hu, S.; Luo, H. Stabilization of uncertain networked control systems with actuator saturation and probabilistic cyberattacks. Asian J. Control 2023, 25, 1407–1419. [Google Scholar] [CrossRef]
- Saravanakumar, T.; Lee, T. Hybrid-driven-based resilient control for networked T-S fuzzy systems with time-delay and cyber-attacks. Int. J. Robust Nonlinear Control 2023, 33, 7869–7891. [Google Scholar] [CrossRef]
- Saravanakumar, T.; Nirmala, V.; Raja, R.; Cao, J.; Lu, G. Finite-time reliable dissipative control of neutral-type switched artificial neural networks with non-linear fault inputs and randomly occurring uncertainties. Asian J. Control 2020, 22, 2487–2499. [Google Scholar] [CrossRef]
- Vimal Kumar, S.; Marshal Anthoni, S.; Raja, R. Dissipative analysis for aircraft flight control systems with randomly occurring uncertainties via non-fragile sampled-data control. Math. Comput. Simul. 2019, 155, 217–226. [Google Scholar] [CrossRef]
- Ghrab, S.; Ahmed Ali, S.; Benamor, A.; Langlois, N.; Messaoud, H. A novel robust discrete-time integral sliding mode tracking control design for time-varying delay MIMO systems with unknown uncertainties. ISA Trans. 2024, 145, 1–18. [Google Scholar] [CrossRef]
- Ghrab, S.; Benamor, A.; Messaoud, H. A new robust discrete-time sliding mode control design for systems with time-varying delays on state and input and unknown unmatched parameter uncertainties. Math. Comput. Simul. 2021, 190, 921–945. [Google Scholar] [CrossRef]
- Hernández-González, O.; Ramírez-Rasgado, F.; Farza, M.; Guerrero-Sánchez, M.-E.; Astorga-Zaragoza, C.-M.; M’Saad, M.; Valencia-Palomo, G. Observer for Nonlinear Systems with Time-Varying Delays: Application to a Two-Degrees-of-Freedom Helicopter. Aerospace 2024, 11, 206. [Google Scholar] [CrossRef]
- Campos-Martínez, S.-N.; Hernández-González, O.; Guerrero-Sánchez, M.-E.; Valencia-Palomo, G.; Targui, B.; López-Estrada, F.-R. Consensus Tracking Control of Multiple Unmanned Aerial Vehicles Subject to Distinct Unknown Delays. Machines 2024, 12, 337. [Google Scholar] [CrossRef]
- Hernández-González, O.; Targui, B.; Valencia-Palomo, G.; Guerrero-Sánchez, M.-E. Robust cascade observer for a disturbance unmanned aerial vehicle carrying a load under multiple time-varying delays and uncertainties. Int. J. Syst. Sci. 2024, 55, 1056–1072. [Google Scholar] [CrossRef]
- Li, Y.; Voos, H. An application of linear algebra theory in networked control systems: Stochastic cyber-attacks detection approach. IMA J. Math. Control Inf. 2015, 1–22. [Google Scholar] [CrossRef]
- Li, Y.; Voos, H.; Rosich, A.; Darouach, M. A Stochastic Cyber-Attack Detection Scheme for Stochastic Control Systems Based on Frequency-Domain Transformation Technique. In Network and System Security. In Proceedings of the 8th International Conference, NSS 2014, Xi’an, China, 15–17 October 2014; Au, M.H., Carminati, B., Kuo, C.-C.J., Eds.; Springer: Cham, Switzerland, 2014; Volume 8792, pp. 209–222. [Google Scholar]
- Zhang, X.; Xu, X.; Li, J.; Luo, Y.; Wang, G.; Brunauer, G.; Dustdar, S. Observer-based H∞ fuzzy fault-tolerant switching control for ship course tracking with steering machine fault detection. ISA Trans. 2023, 140, 32–45. [Google Scholar] [CrossRef] [PubMed]
- Lien, C.H.; Yu, K.W.; Wu, L.C.; Chung, L.Y.; Chen, J.D. Robust H1 switching control and switching signal design for uncertain discrete switched systems with interval time-varying delay. J. Frank. Inst. 2014, 351, 565–578. [Google Scholar] [CrossRef]
- Wu, W.; Wang, X.; Rao, H.; Zhou, B. Delay-dependent Wide-area Damping Controller Synthesis Approach Using Jensen’s Inequality and Evolution Algorithm. CSEE J. Power Energy Syst. 2023, 9, 1774–17785. [Google Scholar]
- Park, P.; Ko, J.W.; Jeong, C. Reciprocally convex approach to stability of systems with time-varying delays. Automatica 2011, 47, 235–238. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).