Abstract
Cyber–physical systems (CPSs) is a manufacturing infrastructure that requires high reliability real-time automatic control characteristics. It is widely used in industrial fields such as production and transportation. An example is a future transportation network system that controls information such as sensors and actuators based on a network. However, CPSs are susceptible to cyberattacks as network-based interconnections increase. Data handled between a car and a fog server can put personal privacy at risk, so it is essential to introduce security technologies such as encryption. A login/password method is required to satisfy the demand for secure sharing and utilization by service users. Based on the attributes of these target service users, the authority to decrypt data is delegated to legitimate users, and a pull-in encryption method is required. In this paper, we propose a method to safely protect the system from attacks through the method of managing attribute-based delegation of authority. Using a semantic security model, the proposed system is proven safe against public attacks by malicious users, and it can be used to protect against attacks on a smart car.
1. Introduction
The rapid development of sensing, activating, control, and networking technologies has enabled close fusion between various individuals that make up the physical world, such as machinery, electronic equipment, infrastructure, energy supply and consumption facilities, medical devices, and automobiles. Complex systems in systems technology, which fundamentally differentiate themselves from existing individual electronic devices by collecting and analyzing necessary information from physical objects through various sensors and sharing processed information with various controllers and actuators, have been proposed and developed. In this way, a cognitive control system in which cyber world information processing functions and the physical world respond closely to each other and cooperate is called cyber–Physical Systems (CPSs). Cyber–Physical systems are expected to be applied to most information processing and control computing fields, contributing dramatically to the improvement of efficiency, safety, and security. In particular, on the basis of intelligent cyber information collection and optimal control technologies, it is expected to be applied to various fields such as city intelligent traffic control, building group energy-consumption analysis and optimal control, and smart space service. The Internet of Things (IoT), combined with the main social infrastructure of real life, reveals dangers that exist in cyberspace, such as the theft of personal information by hacking home appliances and spreading malware infections in the real world.
However, as the IoT combines major social infrastructures with our real-life things, the number of security threats is skyrocketing. For example, the dangers in cyberspace, such as theft of personal information by hacking home appliances and malware infections, are appearing. It is also possible to hack passwords to open the doors of smart cars, illegally exercise authority that only the owner of the smart car has, force the smart car itself to move, or steal it. Not only that, it is also possible to track the locations of smart cars and remotely attack their hardware to prevent them from working properly [1,2,3,4].
Big data environments are combined with the IoT infrastructure and cloud environments to provide platforms and services, but security solutions that remain in individual units are missing consistent security policies, slowing down decision-making, etc., and are becoming a problem. Therefore, new customized security services are needed in the various network environments (e.g., the IoT, the CPSs, the cloud, big data, etc.).
New combined environmental urban transport systems will continue to be important for safety and will be combined with new IoT infrastructure for technologies that detect and avoid risks. In addition, the importance of safety will not change in future urban transportation systems, and the demand for technologies to detect and avoid the risks of movement will increase. In transportation networks, a huge amount of data is exchanged, such as the number of automobiles, the movements of millions of people, and the transfer of personal information, which are all bound together by external environmental information.
Modern mobile communication systems are mechanisms that process information that is collected on a central server and sent to each mobile unit. At present, the time available for judgment is insufficient because of problems such as network latency. In other words, moving a large amount of data requires individual real-time processing. In addition, it is possible to obtain necessary information, such as nearby accident information and traffic jam information, by exchanging information on geographically close movement or movement in previous similar situations. However, it is very difficult to collect information from many mobile units on a central server and make it searchable. In such a case, it is necessary to extract only important data, reduce the total storage, and transfer only important information. In order to collect only important information, various data volumes, such as car camera images and driver movement, are immediately analyzed; risk is calculated, and avoidance behavior is supported or automated [5].
Software-defined network (SDN) technology refers to network structures and devices that allow distributed network equipment to be easily managed by software. This technology enables network operators to manage network resources in an active and automated manner. It is possible to reduce the management costs of the network and respond quickly to sudden situations. This technology flexibly controls networks through programs such as network virtualization and network function virtualization. For this reason, SDN separates the data plane and control plane of the network, providing a standardized interface between them, allowing network operators to program the control plane for different situations. Therefore, it is possible to control the communication function performed on the data side in various ways. The term SDN has spread throughout the world and is being researched by many institutions and companies. Under the SDN concept, various network control structures and implementations have been proposed. Although the number of cases where SDN is introduced into actual network systems is increasing, the environment in which SDN is applied is limited, and various types of SDNs have not become widespread. Among the security vulnerabilities of SDN technology, the privileged elevation attack causes a big problem in the control function by allowing the authority to be arbitrarily not authenticated.
The information collected needs to be shared only by legitimate users, and the authority to access data needs to be controlled, depending on the situation. A login/password method is required to satisfy the demand for secure sharing and utilization by service users. Based on the attributes of these target service users, the authority to decrypt data is delegated to legitimate users, and a pull-in encryption method is required.
In this paper, as a technical countermeasure for these problems, we study how to encrypt data so that only users with legitimate attributes can access them. Property delegation in a fog computing environment and Ciphertext Policy Attribute-Based Threshold Decryption (CP-ABTD), a retractable encryption method, can be applied to provide a monitoring service for vehicles.
The structure of this paper is as follows: Section 2 is a study of the underlying technologies and threats for the proposed system. Section 3 explains the detailed operational processes of the system and the scenarios in which attribute-based delegation of authority and the retractable encryption method are applied. In Section 4, the proposed system is shown to be tamper-proof and publicly offered, demonstrating its security compared to existing attribute-based encryption-only or delegation-of-authority encryption algorithms. Finally, Section 5 offers conclusions [6,7].
2. Related Research
2.1. Intelligent Transportation System
Cyber–physical system technology will be applied to road traffic systems to improve safety, efficiency, and security, accelerating the realization of intelligent transportation systems for future smart cities [8].
Connected vehicle technology (CV) is an important cyber–physical system technology that can bring about a breakthrough improvement in the safety and efficiency of road traffic systems. In fact, it is possible to develop efficient intersection control algorithms by applying CV technology and contribute to reducing traffic congestion [9,10]
One of the representative research topics using cyber–physical systems is the development of intersection communication protocols [11]. In particular, the development of an intersection communication protocol that efficiently controls the flow of vehicles in complex traffic situations where autonomous vehicles and existing vehicles coexist can be said to be very important. In light of this importance, various studies have been conducted to develop intersection control protocols. Another example is the development of a traffic congestion mitigation protocol that focuses on the problem of traffic congestion on highways and develops a protocol to reduce traffic congestion by utilizing communication functions between vehicles.
The efficiency and safety of the road traffic system can be improved by utilizing cyber–physical system technology, but research on security technology is also active. Since external security attack elements are steadily increasing to the extent that affects the function of vehicle operating devices, various cyber physics system studies are being conducted to increase the security of vehicles. Of course, various internal intrusion detection systems (IDS) have been developed, but most of them have not successfully responded to some security attacks because of the probabilistic characteristics of such systems.
2.1.1. Traffic Forecasting Information Based on Big Data
The Ministry of Land, Infrastructure, Transport, and Tourism of Korea and the Korea Road Corporation have constructed and are operating a traffic management system for national roads to provide traffic information on national expressways and general national highways. Road traffic and special situation information are provided to drivers in real time through road signs, the Internet, smartphones, Twitter, and automatic response systems. The traffic information center provided by the Seoul Regional Land Management Agency, Korea Expressway Corporation, the National Police Agency, and local governments distributes traffic information through various media, such as homepages, Internet portals, smartphones, navigation systems, Twitter, and ARS (automatic response system). Road traffic information is provided and utilized through various media and technologies, such as carriers and broadcasters providing main road traffic information via smartphones, DMB (digital multimedia broadcasting), navigation systems, etc.
In Germany, as the population density of the area around the autobahn increases, online traffic simulation (OLSIM), supported by the German government, was developed to solve traffic congestion problems on the autobahn caused by the increase in traffic volume. It collects data from about 4000 loop detectors and provides users with real-time traffic conditions and 30 min hourly traffic condition forecast information via the Web. Figure 1 shows the traffic situation forecast information system in Germany.
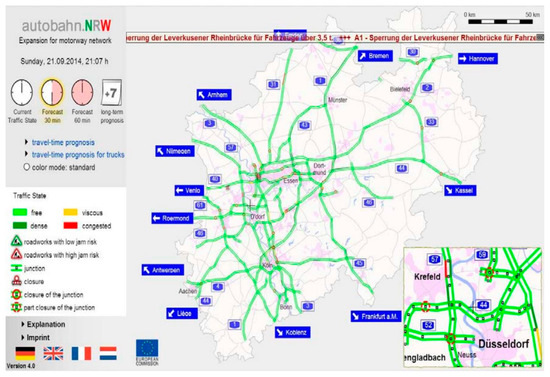
Figure 1.
German traffic forecast information system.
Big data traffic forecasting technology collects, stores, and analyzes a wide variety of information and provides it as a variety of application services, including intelligent home networks, universal healthcare, smart environment management, and mobile sensor-based personalization. Information provision in various fields, such as services and ubiquitous sensor network (USN) virtual world applications, can be applied to the service system industry and markets and can promote their development. In addition, it is a technology that matches the trends in power generation technology, such as driverless self-driving vehicles and smart roads. It can be applied technically on the roads, and the safety of drivers is improved by providing predicted driving information, which is effective in reducing traffic accidents.
2.1.2. V2X Communication Environments
Based on the edge computing environment, it is possible to control traffic flow via communication with vehicles traveling on the road and all surrounding infrastructure. In particular, future vehicles will only be able to maintain a fast, safe, and comfortable operating environment through communication with everything in the vicinity. In this way, in order to ensure mutual compatibility between cars and surrounding infrastructure devices in smart transportation networks, the 3GPP standards body for mobile communications proposed in 2016 a V2X standard that utilizes mobile communications networks.
Figure 2 shows the communication environment of the smart transportation network proposed by the 3GPP.
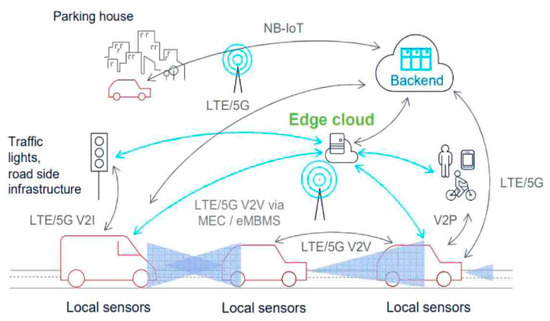
Figure 2.
V2X (Vehicle-to-Everything) environment.
It was designed so that the surrounding infrastructure can actively communicate with smart cars and other cars in the vicinity using V2X based on IEEE802.11P in the Internet of Things, and even autonomous driving is possible. This protocol allows the infrastructure facilities, smart vehicles, and infrastructure equipment in the vicinity to autonomously control traffic conditions via periodic communication using Wi-Fi.
However, even in the above V2X communication environment, there are still many risks, such as forgery of the identity of the smart car itself, attacks via illegal remote connections, and tampering with surrounding cars and infrastructure.
2.1.3. Security Threats
Distinguishing security threats requires security policy management and control and interlocking networks to identify cyber breaches inside the control networks, detect forgery/alteration of control commands and monitoring information, and defend against vulnerabilities in control systems, vulnerable authentication systems, and denial of service attacks. To distinguish vulnerabilities, first (in terms of security policy management), there are many points of contact for cooperation between internal business networks and external organizations, for communications between systems in the control network, and for system security policy formulation and management deficiencies. Second, by interlocking control networks, many control systems are physically connected to an internal business network and external organizations in order to send and receive data and operate information protection systems in linked sections of the networks. Even if a network is secure, unauthorized access is possible because of the careless setup of the information protection system. Third, there are cyber breaches inside the control network. In many cases, the transitional aspect is not a single net but a large number of subnets and a central network. Failures and breaches that occur in the systems inside the control network affect the overall control system owing to the risk of metastasis. Fourth, there is the risk of forgery and alteration of control commands and monitoring information. It is possible for hackers and malicious insiders who have invaded the control network to forge or alter control commands and monitor information of the control system. Fifth, it is possible to invade cyberspace by using the vulnerabilities in control systems, as well as remote access services in network devices, systems, and applications. Sixth, weak authentication systems often do not use authentication procedures in an emergency; they might use passwords that are hardcoded in the control software or use simple passwords. Finally, control systems with limited resources, including embedded devices, are vulnerable to denial-of-service attacks.
Not properly protecting components in next-generation intelligent transportation systems poses a serious security threat. The purpose of building a next-generation intelligent transportation system is to ensure safety, prevent serious threats to people’s lives and property, and ensure road traffic efficiency. It can be said that dependence in cyberspace is higher than in the conventional transportation system in that the characteristics of the intelligent transportation system are for V2X communication; that is, all vehicles are connected by this communication. This means that an attacker can use a vulnerability to execute a cyberattack via an exposed network, causing direct physical damage and risks to human life, which can be a serious problem.
In addition, autonomous vehicles in the C-ITS environment collect a huge amount of information through communications, sensing, video technology, etc., and they process this information via deep learning algorithms. When autonomous vehicles process vast amounts of information via deep learning, attackers can inject abnormal data or cause some of the data to be modified, causing unforeseen consequences. Owing to these issues, it is necessary to ensure a reliable level of safety and security in order for autonomous vehicles to be commercialized and popularized, which requires thorough hardware and software verification.
In this way, direct communication vehicle-to-vehicle (V2V) and vehicle-to-infrastructure (V2I) and back, to defend against cyberattacks, is an issue that must be decided first. It is also necessary to protect each type of communication between vehicle-to-network (V2N) end servers and deal with assets and threats separately.
In the V2V system, the vehicle is treated as a major asset based on physical factors, and it is necessary to protect the vehicle’s position and authentication information as an asset, which is personal information that needs to be protected by V2V communication. Attacks on these assets can be carried out in the following ways.
V2I attacks can be seen as direct attacks on infrastructure systems. Therefore, the V2I assets that need to be protected intensively include not only vehicles but also ITS firefighter base stations, backend servers, etc., and personal information such as vehicle location and authentication information must be protected.
V2N communication needs security in mobile devices, aftermarket devices, etc., inside vehicles and connected to the OBD-2 adapter for in-vehicle infotainment systems. There is a threat because apparently, V2N has more types of connected devices than V2V and V2I, which makes it possible to diversify attack patterns that exploit vulnerabilities. As a typical example of various security vulnerabilities and attack methods against V2N-connected vehicles, the internal CAN communication attack and the remote ECU hacking method against the Jeep Cherokee were released at Defcon in 2015. Also, in 2016, at George Mason University, an attacker hijacked the software control flow of MirrorLink, an automobile platform that works with smartphones, and discovered that a forced control attack on the vehicle’s ECU was possible. In addition, by modifying the car diagnostic application (known as a representative service of V2N) via reverse engineering and changing it so that unauthorized attacks were possible and newly deploying it, the attacker intended to remotely control the ECU of the vehicle. Recently, various services and types of content have been used in conjunction with cloud services. Therefore, inadequate security operations in the cloud service itself can lead to security threats in the V2N environment. In particular, the vehicle cloud, unlike the general Internet cloud, is highly mobile, has a large number of nodes, exposes location information for location-based services, and provides different devices and services for each vehicle. It has all the characteristics that make it prone to security vulnerabilities.
Integrity and Availability Violation
Security threats that violate integrity, which is one of the typical types of threats, are represented by attacks such as message forgery and tampering. Attacks such as forging or altering a message sent from a vehicle, or disseminating false information, are possible. Such attacks can also interfere with normal message forwarding through DoS in a way that compromises availability, which is one of the other key security factors. DoS attacks can take forms such as ineffective major flooding attacks or deleting valid messages. In addition, since a DoS attack on the external network may occur in conjunction with a DoS attack on the internal network, there is concern about additional damage. Furthermore, signals that induce interference in the communication channel can be used to compromise the availability of V2V communication through signal jamming.
V2I is vulnerable to attacks such as message forgery and tampering that violate integrity, just as V2V attacks. In addition, DoS and signal jamming can be used to compromise the availability of V2I communication environments.
In V2N communication, there is the risk of integrity being compromised by message forgery or alteration, as with V2V or V2I. This is because a backend server and car messages can be subjected to man-in-the-middle attacks. In addition, consistency can be violated because of software malfunctions. Multiple services using V2N communication can have software bugs in applications installed on mobile devices (such as smartphones and tablets) and in vehicle devices (such as vehicle infotainment systems, OBD-2 adapters, and telematics head units). This can corrupt data and compromise the integrity of the software. In addition, when connecting a vehicle’s device, a malware-infected mobile device can interfere with the vehicle’s normal V2N service. The bigger problem is that V2N is also closely related to the connection between the vehicle and the cloud. That is not a problem for the vehicle’s internal system, but the data stored in the cloud server could be damaged or lost because of poor cloud management. The point is that the integrity of the data can be compromised. The infringement can be an attack such as DoS or signal jamming and can create problems such as software bugs, malfunctions due to malware, and reduced service availability due to cloud server problems.
Infringement of Confidentiality
Confidentiality breaches can occur, such as the code of various services through V2N being leaked through attack methods such as eavesdropping, and these threats are introduced earlier, not just breach of confidentiality. Modifying and distributing the application through reverse engineering can result in infringement of both integrity and availability, such as enabling remote forced control of the vehicle ECU as the attacker intended.
Threats to Authentication
If a private key is obtained through physical access to a vehicle, authentication can be bypassed, and the attacker can impersonate a legitimate vehicle user.
In the V2I environment, communication entities such as onboard units (OBUs) and roadside units (RSUs) go through an entity authentication process that must determine that the ID is for a legitimate owner. Therefore, if a private key is obtained through physical access to an RSU or an OBU, one concern is that authentication will be bypassed.
In order to receive various services using V2N, it is necessary to go through the authentication process, but if the authentication information is stolen, the service can be used without permission by pretending to be the legitimate authority. In addition, if an appropriate authentication procedure is not in place between the vehicle and the mobile device in a service implementation, an attacker can take advantage of this vulnerability and take control of the vehicle through a mobile device or the like.
Repudiation Vulnerability
Nonrepudiation threats can include extracting private keys and message forgery/alteration. When a hacker manipulates traffic to impersonate or disguise a specific vehicle or extracts a private key to create and distribute a fake message, it becomes impossible to deny transmission of messages to/from the spoofed vehicle. Conversely, a threat may occur when the fact of message transmission to/from a vehicle is denied. If a message can be forged or altered, it may not be possible to deny that the message was ever sent or received; it may not be possible to grasp a clear meaning when deciding where responsibility lies.
In the V2V method, if an attacker manipulates traffic to spoof a specific vehicle, V2I can spoof not only the vehicle but also an RSU, or the attacker can create a false message through the extraction of the private key.
A user could arbitrarily change or modify software or hardware in order to use a service through V2N as he/she likes. If an accident occurs, however, that user could deny any operational fact that might be available before the change was made. After restoring the default state, problems such as blaming the manufacturer or the service provider for an accident can occur. In such cases, the manufacturer or service provider must be held liable for the accident, even without negligence, if the user is unable to prove that the system was arbitrarily modified or forged. This can be seen as belonging to the nonrepudiation threat. In addition, there may be a problem with a user not updating software properly. Generally, to repair various bugs and vulnerabilities, service providers send security updates on a regular basis, but users might continue to use systems without updating them. By delaying the update, in the event of damage, the user could hold the service provider responsible for an accident. Even then, if it is not possible to prove the update was not properly carried out at the time of the accident, the manufacturer or service provider could be held liable, and damages due to nonrepudiation may occur. Additionally, such nonrepudiation can apply the other way around. A manufacturer might deceive the consumer and avoid liability for a problem that occurred when a software update was not provided, claiming that the problem occurred because the consumer did not perform an update. When utilizing the cloud with a V2N service, an attacker can forge or alter a message sent between nodes in the vehicle cloud and transfer it to another node. Later, when the fact becomes apparent, an attacker can deny it and is vulnerable to the repudiation of a cloud-based attack.
Privacy Invasion
In a typical attack, personal information can be collected or leaked through session sniffing, traffic analysis, etc. In particular, a vehicle terminal used for vehicle-to-vehicle communication, including vehicle speed and position information, will broadcast the vehicle position to other terminals in the vicinity in a basic safety message (BSM). By continuously tracking geolocation records, it can locate the vehicle.
Similar to the V2V method, personal information can be collected and leaked through session sniffing, traffic analysis, etc. In particular, probe vehicle data (PVD) messages discussed in ISO TC204 include vehicle status information (engine status, ABS resin functioning, etc.) and vehicle position information (latitude, longitude, altitude), and vehicle operation information (route, heading, etc.). Therefore, the interception of these PVD messages can lead to privacy breaches.
V2V and V2I privacy breaches can occur because of the variety of services provided and the implementation of personalized services if the main problem is the capture of location information. Personal information can be collected or leaked through general session sniffing, traffic analysis, etc., and the information stored on the cloud server can be stolen because of mismanagement of the cloud service connected via V2N. There is also the possibility that personal information will be leaked after bypassing other services or from threats such as an attacker stealing the personal information of a service user because of a bug or vulnerability in software related to the V2N service or from the installation of malware.
2.2. IoT Security Threats
2.2.1. Threats from the Device Perspective
Security threats from devices include information leakage from a hacked device, data forgery/alteration, device access by unauthenticated users, and device loss or theft.
First, unauthorized access to a person’s device means that an unauthorized person can access it. When using a wireless network, if an ID, password, etc., are not in a router or in the IoT device itself, anyone will be able to access it. If an attacker with a malicious purpose accesses it, the damage is increased. An attacker could inject malicious code over a wireless network, turning a smart device into an infected device. Distributed denial of service (DDoS) attacks can be generated by gathering infected IoT devices in this way.
Second, information leaks through hacked devices can allow communication with smart devices over wireless networks to use corporate IoT services. At this time, if a device becomes vulnerable, an attacker can access the smart device via a wireless network. For example, as mentioned above, the user may not have set up an ID and password required to use IoT device services. An attacker can access the device without any information. It may lead to secondary damage such as leaking information stored inside the device or requesting a ransom by taking the data
Third, the security threat of data forgery and alteration has one prerequisite: the attacker must be able to access smart devices via a wireless network. After that, administrator authority to use the device can be obtained, and data can be forged or altered. These types of forgery and alteration of data may pose threats such as sending malicious data for communication and preventing a service from performing normally. Accidents caused by sensor malfunctions and erroneous information transmission caused by modulation of documents are possible. When using a smart sensor in a company, it is possible to detect the movement of people inside the building, change the temperature in the office, add humidity, smoke, carbon dioxide, etc., and analyze where electricity is used a lot. Modulating these values causes a variety of damages, such as cutting off power due to overload detection, paralyzing the business by activating the fire alarm due to a malfunction in a smoke sensor, and triggering the sprinkler system by raising the temperature in a sensor.
Fourth, device loss or theft is a security threat that can occur when a user with a smartphone, etc., loses the device or if anyone steals the device. By losing a smart device, allowing other users to acquire it, allowing them to access it, or sending and receiving sensitive information that should not be accessed, confidentiality may be compromised. Information such as IDs and passwords recorded in a smart device could lead to network infringement that allows access to routers and IoT devices that can be connected to by obtaining access rights.
2.2.2. Security Threats from Network Hacking
To access an IoT device, you must first go through a wireless network. An attacker who uses a normal wireless router or similar can gain control of a smart device by illegally accessing a router and can exploit it to pose a security threat.
First, there is the man-in-the-middle attack. It is possible for users to hack IoT devices and control them by acquiring information during service authentication between IoT devices and smartphones that control the devices. Ken Munro, a researcher at Pen Test Partners (a British security company), demonstrated password theft of wireless LAN through a smart pot kettle. The hack first takes advantage of a bug in the kettle settings to create wireless Internet access with a name such as the wireless Internet and then uses a hotspot with a high signal to make the smart pot automatically connect to it. Then, after locating the user through a directional antenna, breaking into the internal network (the actual Wi-Fi network), and sending a command to the smart pot, the unencrypted Wi-Fi password was confirmed through a demo to be leaked. “With data, directional antennas, and network equipment acquired based on social engineering, it is possible to steal the password of the wireless LAN connected to the smart pot kettle framework,” he explained.
The second threat is IP spoofing, which exploits IP protocol authentication vulnerabilities by faking an IP address, turning it into an IP address of a network host, attempting to attack other IP addresses, and neutralizing IP-based authentication. Attacks using IP spoofing have sufficient resources, such as tools created by attackers, so even small vulnerabilities can be attacked by connecting once and gaining trust.
Finally, there is radio network interference. IoT services communicate mostly over wireless networks. Taking advantage of these access points, we recently targeted interfaces that use various wireless signals, such as mobile communication networks (telephones), a GPS, and radio waves (3G, 4G, LTE) that can be used with mobile phones and tablets. Radio wave blocking devices have appeared. These devices can be used to prevent receiving regular IoT services.
2.3. Fog Computing
Fog computing is a newly proposed platform to more efficiently provide computing, data storage, and network services between IoT devices with cloud computing and geographical high-density distribution characteristics. While this fog computing can be defined as an extension of cloud computing as a model designed to allow fog nodes to play a certain role in the existing cloud, there is a clear difference from existing cloud computing. The differences can be explained by dividing them into edge location, location awareness, and context awareness.
Edge location can provide services (ex-augmented reality, real-time video streaming, etc.) that require real-time processing of large amounts of data that were difficult to provide in existing cloud environments because fog computing exists geographically close to IoT devices. Location awareness has the advantage of supporting the mobility of devices, which is an important element in location-based services because fog computing can roughly know the location information of IoT devices. With context awareness, fog nodes can provide more optimized services because they can utilize context information such as local network status and device status information when communicating with IoT devices. Figure 3 shows an SDN-based VANET. It has the basic structure of fog computing [12].
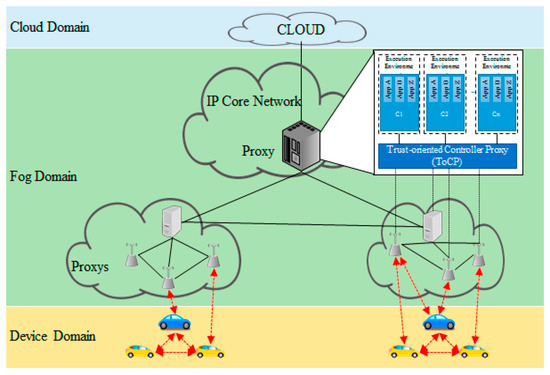
Figure 3.
SDN-based VANET.
2.4. ABE and ABTD
Attribute-based encryption is an extension of the concept of identity-based encryption, which Sahai and others first proposed. Attribute-based encryption refers to a method of decrypting a message when there is an attribute value sufficient to decrypt the message by comparing the attribute value of the user with the attribute value included in the ciphertext.
Attribute-based encryption is classified into key-policy attribute-based encryption (KP-ABE) and ciphertext-policy attribute-based encryption (CP-ABE) according to the encryption policy. KP-ABE is a method in which an access tree is included in a private key issued to each user, and an attribute value is included in a ciphertext. The user who receives the private key decrypts the message when the attribute value included in the ciphertext satisfies the access tree of the private key. CP-ABE includes an attribute value of each user in the user’s private key, and the ciphertext includes an access tree. Users can decrypt the message if their attribute values satisfy the access tree of the ciphertext [13].
In the KP-ABE method, a hierarchical attribute-based encryption method was proposed for scalable access control [14,15,16].
In the initial CP-ABE, the size of the ciphertext increases linearly according to the access policy. Therefore, as an efficiency improvement study, Emura et al. proposed having a constant ciphertext size [17]. In addition, Li et al. proposed outsourced decryption that can be verified with a certain ciphertext length [18].
Lai et al. and Li et al. presented a hidden access policy in the ABE scheme [19,20]. In addition, Li et al. proposed a searchable encryption scheme for the cloud [21,22]. Methods for improving property cancellation and user collusion were also proposed [23]. Rahulamathavan et al. proposed a technique to improve the vulnerability of user collusion [24]. Nign et al. proposed a traceable method to improve the vulnerability of leaking access vigilant proof [25,26].
Multiauthority ABE (MA-ABE) supports multiple attribute authorities and one central authority to improve the vulnerability of the existing ABE to the central authority [27]. MA-ABE has a vulnerability to collusion attacks by collecting user attributes from multiple organizations when obtaining a secret key by submitting the user’s global identifier (GID) to the organization. Accordingly, Chase and Chow proposed the privacy-preserving MA-ABE (PPMA-ABE) by Certificate Authority (CA) [28]. In addition, Han et al. proposed a privacy-preserving decentralized CP-ABE (PPDCP-ABE) that keeps both user identifiers and attributes confidential [29]. This method requires the user’s anonymous certificate, so there is a vulnerability in a collusion attack.
Attribute-based encryption requires a method that prevents users who withdraw attribute values due to withdrawal from services from continuing to receive the services. In attribute-based encryption, techniques for withdrawing attribute values include a list of attribute-value withdrawers in the access tree. Most withdrawal techniques use a list of attribute-value withdrawers in KP-ABE. In CP-ABE, attribute value withdrawal techniques include placing an expiration date on attribute values [30,31].
In this paper, an attribute-enabled encryption algorithm capable of such withdrawal is used. It is intended to propose a model that prevents attacks such as user identity forgery in a smart traffic environment.
3. Proposed System
3.1. Overview
The proposed system is constructed based on the structure of fog computing. At the top, it has the function of a cloud server in cloud computing. This step consists of a data service provider and a proxy manager. The main roles are data storage and data and proxy server management. That is, the data store is performed in the data service provider. In addition, the proxy manager authenticates and manages proxies. In the intermediate stage, proxy servers are located. Proxy servers mainly play the role of data collection, process, and storing. In addition, re-encryption is performed on the data collected at the edge stage. Re-encryption is performed according to the user who requests it by checking the delegation or withdrawal list of stored data. At the bottom edge stage, there are objects that produce or collect data, such as smart cars and smart signals. These individuals are responsible for encrypting data produced or collected. Encryption is performed using the user’s accessible authority structure. The user may access data through a cloud server or a proxy server. Decryption authority is required to access encrypted data.
Figure 4 shows the network model of the proposed system.
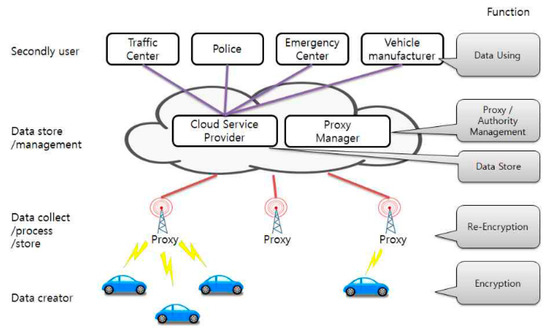
Figure 4.
Network model of the proposed system.
3.2. Attribute-Based Encryption
The system proposed in this paper uses an attribute-based encryption algorithm. It operates more flexibly than the existing attribute-based encryption algorithm. In other words, the delegation and withdrawal of attributes are simultaneously performed. The delegate holding the secret key may delegate the decryption authority of the ciphertext to the secondary user. Here, the delegate and the secondary user must correspond to a set of attributes. In addition, the delegate can decide whether to delegate his or her authority and then withdraw the attribute. This is to revoke the authority to decrypt the delegated ciphertext so that it cannot be accessed.
The encryption algorithm consists of seven steps in total. Each algorithm includes a preparation step, a key generation step, an encryption step, a delegation step, a secondary delegation step, a secondary decoding step, and a decryption step. The preparation step and the key generation step are performed by a central certification authority. The encryption and delegation steps are performed by the delegate. The secondary delegation step and the secondary decryption step are performed by the policy management agency. Finally, the decryption step is performed by the secondary user.
3.2.1. Bilinear Mapping
A bilinear map is a function that combines two vector spaces to create another third vector space. Let , and be cyclic groups of the same order. Given that is a product group, the bilinear map to , the product of and , can be expressed as follows: is the generator of , is a function of the bilinear mapping, and and are elements of and . Bilinear mapping ( being the output space of the bilinear mapping) with respect to the two cyclic groups has the following three characteristics [5]:
- Bilinear: for all and all ;
- Nondegenerate: for the generator of ;
- Computable: There is an efficient algorithm to calculate for all .
3.2.2. Access Structure
The decryption of the ciphertext is performed when the user’s attribute belongs to the attribute set of the secret key.
For example, a medical college is conducting research on a new strain of COVID-19. If another medical university researcher needs access to the data studied, the private key must be that of a university professor and must be created based on the attributes of the research team, the research team leader, or the department head. The structure (university professor ∧ research team) ∨ (research team leader ∨ department dean) must be created as shown in Figure 5 (‘∧’ is an AND gate, and ‘∨’ is an OR gate).
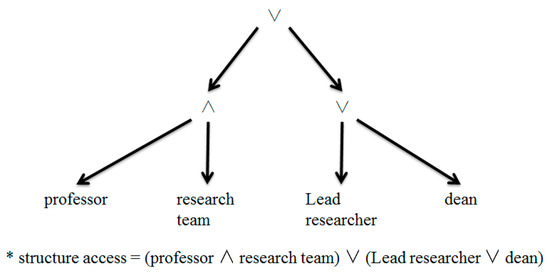
Figure 5.
The Structure Access.
If the researcher is a university professor and dean, the secret key includes the attribute (university professor, dean). When trying to access the data, the researcher did not satisfy the AND gate called the university professor and research team, but the OR gate called the dean so that the researcher could access the data.
3.3. System Operation
The proposed system is capable of controlling secondary users’ access using delegation and withdrawal of access rights based on attribute-based encryption. The proposed system generates data from equipment such as smart cars and smart traffic lights. The generated data are transmitted through the peripheral infrastructure through V2X. The transmitted data include personal information. Encryption is in progress to prevent the leakage of personal information. At this time, the infrastructure does not have enough resources for calculation. Therefore, we try to solve this problem using the structure of fog computing.
The notation for understanding this paper is shown in Table 1.

Table 1.
The notation.
Figure 6 shows the operation of the proposed system based on a virtual scenario. The configured system consists of an authorized certification authority, a data generator, a data collection and authority examiner, and a secondary user of the data.
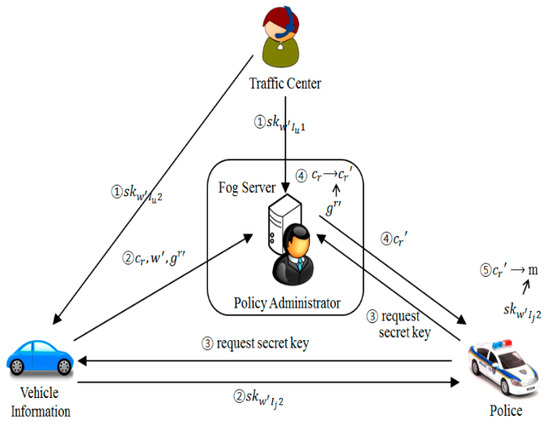
Figure 6.
The configuration of the scenario.
The proposed system will be explained focusing on the scenario of the vehicle monitoring system for violating traffic laws. The procedure of the encryption algorithm capable of delegating and withdrawing attributes consists of seven steps. Detailed methods of each step are described in Section 3.4. The Traffic Control Center, an authorized certification body, proceeds with the preparation stage and the key generation stage. The vehicle, which is a data generator and a delegator of authority, performs an encryption step and a delegation step. In the fog server in charge of collecting and processing data with the policy management agency, a secondary delegation step and a secondary decryption step are performed. The police, who are the data user and the delegator of authority, proceed with the decryption step.
It is assumed that all vehicles have completed the delegate stage at the time of registration of the vehicle. On public roads, police (delegate) find suspicious vehicles. When the police want to view information on a vehicle (delegator), they organize a scenario in which access rights are reviewed and approved by the government.
- When the vehicle is first registered, the transportation center proceeds with an algorithm of the preparation step. In this step, the public key () and the master key () are generated using the system parameter. The algorithm of the key generation step is performed in the following order to generate a distributed key. Two distribution keys are generated using vehicle attribute () and identifier (). The generated distribution keys (, ) are delivered to the Fog server and the vehicle, respectively;
- The vehicle generates a ciphertext () by performing an algorithm of the encryption step. The generated ciphertext is stored in the Fog server database. The vehicle delegates the decoding authority to the police through the algorithm of the delegation step. In this step, the secret distribution key () for the police is generated and transmitted to the police using the attribute set () defined by the vehicle and the identifier () of the police. In addition, the attribute conversion key () is divided and transmitted to the policy management agency;
- Police cars require approval from policy management agencies to view vehicle data. The policy management agency approves or rejects the police’s access after determining the legitimacy. (This scenario is mainly approved);
- When the policy management agency approves the data access to the police, it proceeds with the algorithm of the secondary delegation step to generate a secret distribution key () using the attribute set (). Subsequently, the algorithm of the secondary decryption step is performed to generate the re-ciphertext (). Re-ciphertext are generated using secret distribution keys and police identifiers. This generated re-ciphertext is sent to the police;
- The police decrypt the secret distribution key () received from the vehicle, and the re-ciphertext () received from the policy management agency to view the data.
3.4. Detailed Operation of System
Figure 7 shows the detailed operations of the system.
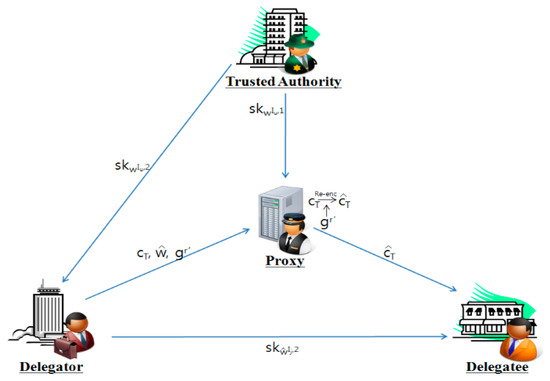
Figure 7.
The concept of CP-ABTD.
First, the certification body executes the preparation step. The certification authority generates security parameter k to support delegation of authority and then follows the key generation steps to communicate with the policy manager and the delegator. The certification body and policy manager can be one administrative body with a trusted third party.
Privilege delegation uses the transmitted security parameters and the session key to provide the policy administrator with settings for encryption. Then, a random value is generated and sent to the authority auditor (the proxy). It then provides the delegate with the value set using the session key.
A permissions examiner generates a random value and a temporary value based on this and goes through the confirmation process with the policy administrator. The policy administrator uses the random value transmitted from the proxy and the information that authenticates the authority delegation to generate the encrypted data to be passed and sends the encrypted data to the delegate.
Finally, the delegate uses a random value as the session key that allows the policy administrator to authenticate the preissued delegator with the data encrypted and sent on behalf of the delegate. It can be decrypted. The detailed operation process has been simplified into seven stages (preparation, key generation, encryption, delegation, secondary delegation, secondary decryption, and decryption) as follows.
3.4.1. Preparation ()
With security parameter as the input, generate the generator, as well as , which is a prime order, .
The bilinear map is , and the system attribute group is (where n is an integer).
selects a random element, .
Use Equation (1) to generate , public key (), and master key (m).
3.4.2. Key generation ()
Performed with the attribute group, as well as the delegator identifier, , as follows:
- Base Component of the Private Key
Create an element for the private key through Equation (2).
- 2.
- Attribute Component of the Private Key
Select attributes , and calculate and .
Send the first private key share, , to the proxy, and send the second private key share, , to the delegator.
3.4.3. Encryption () ()
Randomly select and calculate Equation (3). Equation (4) is the calculation formula of the leaf attribute.
Create ciphertext of the delegator.
3.4.4. Delegation ()
Randomly select , and set with .
Set the attribute switch key, , and calculate with using Equation (5).
Send the private key share , to the delegatee, and send and to the proxy.
3.4.5. Secondary Delegation ()
Check the attribute delegation list; if the target is eligible to be delegated attributes, calculate with and calculate as in Equation (6). Otherwise, do not perform the calculation.
Send private key share to the delegatee.
3.4.6. Secondary decryption ()
Check the attribute revocation list; if the target is not to have attributes revoked, calculate, and calculate as in Equation (7).
Otherwise, do not perform the calculation. The calculation is conducted with all attributes .
3.4.7. Decryption ()
Calculate Equation (8), with all attributes,
Calculate Equation (9).
Calculate Equation (10) and restore .
4. Analysis
4.1. Comparison with Existing System
Attribute-based encryption has been studied, focusing on malicious conspiracy attacks rather than conventional encryption algorithms. In addition, attribute-based encryption capable of attribute withdrawal can be further developed to delegate or revoke attributes. In this study, the safety against attribute withdrawal and modulation attacks is analyzed and compared with previous studies. Attribute withdrawal is to remove or disable the delegated attribute. For example, when the attribute value “a” is withdrawn, the certification authority notifies the proxy not to perform an operation related to “a” and to remove “a” from the system attribute set in which all attributes are integrated. Thereafter, a new secret key is issued and transmitted to all users who have a secret key related to “a”. It also regenerates the re-encryption key.
The function of delegating and withdrawing user attributes is suitable for a cyber–physical system environment. The delegation of authority is the delegation of authority to the proxy to provide their data. The proxy can determine whether the delegate’s access to the delegate’s data is legitimate. In the proposed method, the attribute conversion key was transmitted to the policy management agency to enable justification.
In this study, we propose a safe method for modulating the attacks of attribute-based encryption capable of attribute withdrawal. For authority management and delegation, the proxy determines the legitimacy of access and provides access authority management. Here, justification is determined using the dynamic threshold password. This can solve the problem of modulation attacks. Table 2 shows a comparison between the proposed system and existing frameworks.

Table 2.
Comparisons with the Proposed System.
4.2. Security
The level of security for attribute-based re-encryption is analyzed based on things presented by the cloud [32,33]. These include unidirectionality, data confidentiality, noninteraction, intransitivity, multiple uses, re-encryption control, and master key security.
Unidirectionality means that reverse re-encryption or decryption cannot be performed. Data confidentiality means that data cannot be obtained from an entity without privileges for the ciphertext. Noninteraction means no entity other than the data owner is needed to generate the encryption key; interaction cannot be used to generate the encryption key or the basic data needed for encryption. With intransitivity, two different re-encryptions cannot be combined to obtain a new ciphertext. In other words, different ciphertexts cannot be combined to generate a new ciphertext to be reused, nor can the information needed for decryption be obtained. With multiple uses, re-encrypted data can be re-encrypted again and distributed. This is different from intransitivity, and it is not about generating a new ciphertext by combining re-encrypted ciphertexts. It means that re-encrypted data can be re-encrypted using a proper encryption key for distribution. Re-encryption control, whether or not to perform re-encryption, can be controlled by the data owner. It means that re-encryption for distribution for multiple uses is possible. However, the data owner must be able to decide whether to perform the re-encryption or not. In terms of master key security, a user cannot obtain a master key of an owner by colluding with another entity. In other words, the data user must not be able to obtain the master key of the data owner by any other means.
The proposed model meets the following criteria, which are satisfied in typical proxy re-encryption: unidirectionality, data confidentiality, noninteraction, intransitivity, and master key security. In addition, the model satisfies re-encryption control but does not satisfy multiple uses. In the model that includes re-encryption control, when data generated by a vehicle are sent encrypted by the vehicle, the proxy will re-encrypt them. This is because access attributes for a re-encrypted ciphertext can be delegated or revoked. With respect to multiple uses, the model does not assume there is a case in which re-encrypted ciphertext is re-encrypted and used. Other attacks on the ciphertext include the collusion attack, user/attribute revocation, and man-in-the-middle attack. To prevent a collusion attack, the user must not be able to use encrypted data by colluding with the cloud. That is, a revoked user must not be able to access any encrypted data. User/attribute revocation is an important consideration when using attribute-based encryption. A man-in-the-middle attack is when an attacker comes between two parties that are in communication, eavesdrops on them, and obtains useful data.
The proposed model satisfies user/attribute revocation. However, it may not fully defend against collusion attacks and man-in-the-middle attacks. The user revocation problem is resolved because user attributes can be delegated or revoked. However, for attribute delegation and revocation, because an attribute delegate/revocation list is not kept at the fog server, a revoked user cannot generate attributes by colluding with multiple entities. However, if the fog server joins in the collusion, the system may be vulnerable. With regard to man-in-the-middle attacks and messages that are re-encrypted at the proxy, they will be secure as long as the attacker does not satisfy the access structure. However, if the attacker is disguised as a legitimate user or a proxy, the system may be vulnerable momentarily.
Table 3 shows whether or not the proposed model supports different security and attack items.

Table 3.
The Security Analysis of Proposed Model.
4.3. Safety Consideration
4.3.1. Security against Conspiracy Attacks
A trusted authority, which securely stores the master key in attribute-based authorization encryption, is an institution that is fully trusted. Proxy is an institution that can be semitrusted. In other words, it is necessary to create a secret key share of the delegated person, generate a re-encryption statement, and distribute it honestly to users. However, it is unreliable in that no information about plaintext should be known.
Through a security game between an attacker and a user (challenger), an attribute-based authorization delegation encryption technique may know semantic security. Semantic security means that an attacker cannot acquire any information about plaintext when creating a given ciphertext using a ciphertext and a public key.
Security games have the following requirements. First, it should be possible to prevent conspiracy attacks between users. That is, two or more users should not be able to combine their attribute sets in order to extend their decoding authority. Second, it should be possible to prevent conspiracy attacks by authority reviewers and users. Users and authority reviewers who do not have a secret key satisfying the access policy must not be able to decrypt the ciphertext in malicious cooperation. Finally, the delegated secret key (the secret key created by the delegator for the delegate) should not jeopardize safety. Safety should not be compromised by the delegated secret key, such as deriving the master key of the certification authority using the delegated secret key.
The most important security feature of attribute-based encryption is the safety against conspiracy attacks. A conspiracy attack is a combination of two or more users’ attribute sets to extend their decryption rights.
For example, there is a ciphertext consisting of the access structure “A”. The user A’s secret key consists of the attribute set “B”, and the user B’s secret key consists of the attribute set “C”. A public offering attack is to generate a secret key related to “D” by combining the secret key of user A and user B to view a ciphertext composed of the access structure “E”.
This proposed method is based on the safety of the attribute-based authorization delegation encryption technique against conspiracy attacks. Attribute-based authorization delegation encryption techniques are safe against conspiracy attacks that combine secret keys related to attribute sets. This is because the key generation algorithm generates a unique identifier “F” for each user as an arbitrary random number and is inherent in the secret key (e.g., user’s secret key share). That is, since each user cannot know “A” determined by an arbitrary random number by the certification authority, the secret key cannot be combined for a public offering attack. Therefore, the proposed system is safe from public offering attacks that combine secret keys between users.
Moreover, it is also safe from conspiracy attacks between the authority reviewer and the user. For example, assuming that user B conspires with a malicious authority reviewer to convert user A’s ciphertext into his ciphertext, user A must generate an attribute conversion key “G” that delegates access rights to user B in order for B to convert the ciphertext. If the attribute conversion key is not generated, re-encryption is not performed. Therefore, the proposed system is also safe against conspiracy attacks between the authority reviewer and the user.
4.3.2. Modulation Attack on Attribute Conversion Key
A modulation attack on an attribute conversion key refers to an attack in which the attribute conversion key “A” is lost or modulated so that the original attribute conversion key “B” cannot be recombined. Since the attribute-based authorization delegation encryption technique is the only attribute conversion key, re-encryption cannot be performed if “C” is lost, leaked, or modulated. In contrast, in the proposed system, the attribute conversion key “G” may be configured only when the attribute conversion key “D” is divided into the attribute conversion key “E” and collected by “F” during recombination.
5. Conclusions
A cyber–physical system is an environment in which many sensors and surrounding devices can communicate between themselves. Among them, the field of smart cars is expected to develop rapidly in relation to autonomous vehicles that are combined with artificial intelligence. However, there are also security threats that try maliciously to hack smart cars or disguise the identity of the owner. In addition, access control for secondary users who want to access encrypted data is complicated. To solve this problem, in this paper, we proposed a secure data access control method that combines an encryption method capable of delegating and revoking attribute-based authority in a proxy and a threshold encryption method.
In this paper, we propose a proxy-based data access authority-management method suitable for cyber-physical systems that uses the existing attribute-based encryption method that can delegate and withdraw attributes and dynamic threshold cryptography. In addition, it is designed to determine the restoration possibility according to the amount of shared information required to restore the attribute transformation key by using a dynamic threshold cipher against an attack on the attribute transformation key. Through this, users can grant or revoke data access rights to secondary users. This improves overall computational efficiency as it eliminates the process of updating the user’s secret key and passphrase when the secondary user’s privileges are lost in the existing approach. It also showed safety against collusion attacks by malicious users, and it showed safety against tampering attacks on property conversion key share.
In future research, we want to increase the speed and efficiency of calculations compared with existing studies. As the number of attributes increases, the ciphertext and key computation increase. In addition, each time attribute withdrawal occurs, a re-encryption key is generated, increasing the calculation process. Therefore, it is necessary to study a lightweight technique that reduces computational complexity. In addition, research is needed to protect user attributes by adding anonymity to the attributes presented in this paper.
Author Contributions
Conceptualization and methodology, H.-J.C., H.-K.Y. and Y.-J.S.; validation, Y.-J.S.; formal analysis, H.-J.C. and H.-K.Y.; resources, H.-K.Y.; supervision, Y.-J.S.; writing—original draft preparation, H.-J.C.; writing—review and editing, H.-K.Y. and Y.-J.S. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Maruyama, H. Edge-heavy data and architecture in the big data era. J. Inf. Process. Manag. 2014, 56, 269–275. [Google Scholar] [CrossRef]
- Robinson, P.; Vogt, H.; Wagealla, W. (Eds.) Privacy, Security and Trust within the Context of Pervasive Computing; Springer: Boston, MA, USA, 2005. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP’07), Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar]
- Ibraimi, L.; Petkovic, M.; Nikova, S.; Hartel, P.; Jonker, W. Ciphertext-Policy Attribute-Based Threshold Decryption with Flexible Delegation and Revocation of User Attributes; Centre for Telematics and Information Technology, Internal Report; University of Twente: Enschede, The Netherlands, 2009. [Google Scholar]
- Hong, K.; Lillethun, D.; Ramachandran, U. Mobile fog: A programming model for large-scale applications on the internet of things. In Proceedings of the Second ACM SIGCOMM Workshop on Mobile Cloud Computing, Hong Kong, China, 16 August 2013; pp. 15–20. [Google Scholar]
- Mambo, M.; Okamoto, E. Proxy cryptosystems: Delegation of the power to decrypt ciphertexts. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 1997, 80, 54–63. [Google Scholar]
- Yang, H.-K.; Cha, H.-J.; Song, Y.-J. A Study on Surveillance Service for Vehicles based on Cryptog-raphy using Attributes. J. Hum. Sci. Technol. Innov. 2021, 1, 1–8. [Google Scholar]
- Won, M.-G.; Jung, D.-W.; Kang, J.-H.; Park, T.-J.; Son, S.-H. Smart city technology based on cyber physical system. Inf. Commun. Mag. Korean Inst. Commun. Inf. Sci. 2014, 31, 45–53. [Google Scholar]
- Knorr, F.; Baselt, D.; Schreckenberg, M.; Mauve, M. Reducing traffic jams via VANETs. IEEE Trans. Veh. Technol. 2012, 61, 3490–3498. [Google Scholar] [CrossRef]
- Kerner, B.S.; Klenov, S.L.; Brakemeier, A. Testbed for wireless vehicle communication: A simulation approach based on three-phase traffic theory. In Proceedings of the 2008 IEEE Intelligent Vehicles Symposium, Eindhoven, The Netherlands, 4–6 June 2008; pp. 180–185. [Google Scholar]
- Azimi, R.; Bhatia, G.; Rajkumar, R.R.; Mudalige, P. STIP: Spatio-temporal intersection protocols for autonomous vehicles. In Proceedings of the 2014 ACM/IEEE International Conference on Cyber-Physical Systems (ICCPS), Berlin, Germany, 14–17 April 2014; pp. 1–12. [Google Scholar]
- Han, M. Optimal routing path calculation for SDN using genetic algorithm. Int. J. Hybrid Inf. Technol. 2018, 11, 7–12. [Google Scholar] [CrossRef]
- Kim, S.; Kim, J.; Ha, D.; Ryu, Y. Carnegie Mellon University’s CERT dataset Analysis and suggestions. Int. J. Adv. Res. Big Data Manag. Syst. 2017, 1, 1–6. [Google Scholar] [CrossRef]
- Wan, Z.; Deng, R.H. HASBE: A hierarchical attribute-based solution for flexible and scalable access control in cloud computing. IEEE Trans. Inf. Forensics Secur. 2011, 7, 743–754. [Google Scholar] [CrossRef]
- Deng, H.; Wu, Q.; Qin, B.; Domingo-Ferrer, J.; Zhang, L.; Liu, J.; Shi, W. Ciphertext-policy hierarchical attribute-based encryption with short ciphertexts. Inf. Sci. 2014, 275, 370–384. [Google Scholar] [CrossRef]
- Li, J.; Yu, Q.; Zhang, Y. Hierarchical attribute based encryption with continuous leakage-resilience. Inf. Sci. 2019, 484, 113–134. [Google Scholar] [CrossRef]
- Emura, K.; Miyaji, A.; Nomura, A.; Omote, K.; Soshi, M. A ciphertext-policy attribute-based encryption scheme with constant ciphertext length. Int. J. Appl. Cryptogr. 2010, 2, 46–59. [Google Scholar] [CrossRef]
- Li, J.; Sha, F.; Zhang, Y.; Huang, X.; Shen, J. Verifiable outsourced decryption of attribute-based encryption with constant ciphertext length. Secur. Commun. Netw. 2017, 2017, 3596205. [Google Scholar] [CrossRef] [Green Version]
- Lai, J.; Deng, R.H.; Li, Y. Fully secure cipertext-policy hiding CP-ABE. In Proceedings of the International Conference on Information Security Practice and Experience, Guangzhou, China, 30 May–1 June 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 24–39. [Google Scholar]
- Li, J.; Wang, H.; Zhang, Y.; Shen, J. Ciphertext-policy attribute-based encryption with hidden access policy and testing. KSII Trans. Internet Inf. Syst. (TIIS) 2016, 10, 3339–3352. [Google Scholar]
- Li, J.; Lin, X.; Zhang, Y.; Han, J. KSF-OABE: Outsourced attribute-based encryption with keyword search function for cloud storage. IEEE Trans. Serv. Comput. 2016, 10, 715–725. [Google Scholar] [CrossRef]
- Li, J.; Shi, Y.; Zhang, Y. Searchable ciphertext-policy attribute-based encryption with revocation in cloud storage. Int. J. Commun. Syst. 2017, 30, e2942. [Google Scholar] [CrossRef]
- Li, J.; Yao, W.; Han, J.; Zhang, Y.; Shen, J. User collusion avoidance CP-ABE with efficient attribute revocation for cloud storage. IEEE Syst. J. 2017, 12, 1767–1777. [Google Scholar] [CrossRef]
- Rahulamathavan, Y.; Veluru, S.; Han, J.; Li, F.; Rajarajan, M.; Lu, R. User collusion avoidance scheme for privacy-preserving decentralized key-policy attribute-based encryption. IEEE Trans. Comput. 2015, 65, 2939–2946. [Google Scholar] [CrossRef] [Green Version]
- Ning, J.; Dong, X.; Cao, Z.; Wei, L.; Lin, X. White-box traceable ciphertext-policy attribute-based encryption supporting flexible attributes. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1274–1288. [Google Scholar] [CrossRef]
- Ning, J.; Cao, Z.; Dong, X.; Wei, L. White-box traceable CP-ABE for cloud storage service: How to catch people leaking their access credentials effectively. IEEE Trans. Dependable Secur. Comput. 2016, 15, 883–897. [Google Scholar] [CrossRef]
- Chase, M. Multi-authority attribute based encryption. In Theory of Cryptography Conference; Springer: Berlin/Heidelberg, Germany, 2007; pp. 515–534. [Google Scholar]
- Chase, M.; Chow, S.S. Improving privacy and security in multi-authority attribute-based encryption. In Proceedings of the 16th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 9–13 November 2009; pp. 121–130. [Google Scholar]
- Han, J.; Susilo, W.; Mu, Y.; Zhou, J.; Au, M.H.A. Improving privacy and security in decentralized ciphertext-policy attribute-based encryption. IEEE Trans. Inf. Forensics Secur. 2014, 10, 665–678. [Google Scholar]
- Al-Dahhan, R.R.; Shi, Q.; Lee, G.M.; Kifayat, K. Survey on revocation in ciphertext-policy attribute-based encryption. Sensors 2019, 19, 1695. [Google Scholar] [CrossRef] [Green Version]
- Ali, M.; Sadeghi, M.R.; Liu, X. Lightweight revocable hierarchical attribute-based encryption for internet of things. IEEE Access 2020, 8, 23951–23964. [Google Scholar] [CrossRef]
- Luo, S.; Hu, J.; Chen, Z. Ciphertext policy attribute-based proxy re-encryption. In Proceedings of the International Conference on Information and Communications Security, Barcelona, Spain, 15–17 December 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 401–415. [Google Scholar]
- Koo, W.K.; Hwang, J.Y.; Kim, H.J.; Lee, D.H. ID-Based proxy re-encryption scheme with chosen-ciphertext security. J. Inst. Electron. Eng. Korea CI 2009, 46, 64–77. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).