A Taxonomy for Threat Actors’ Delivery Techniques
Abstract
:1. Introduction
- To identify and define the key elements that compose the delivery tactic.
- To structure the delivery tactic approaches used in offensive Computer Network Operations (CNE or CNA).
- To provide an accurate taxonomy for techniques into the delivery tactic for these operations, thus allowing defenders to detect novel or uncommon techniques, identify specific countermeasures, and improve global security.
2. Background
2.1. Mitre ATT&CK
2.2. Cyber Kill Chain®
- Reconnaissance. Research, identification, and selection of targets.
- Weaponization. Before attacking a target, the threat actor has to couple a remote access Trojan with an exploit into a deliverable payload.
- Delivery. The transmission of weapons to the targeted environment to launch a particular operation.
- Exploitation. After the weapon is delivered, the exploitation triggers an intruders’ code.
- Installation. The installation of an implant, just as a remote access Trojan, a backdoor, or any kind of malicious software, on the victim system, allowing the adversary to maintain persistence inside the environment.
- Command and Control. The compromised hosts must beacon outbound to an Internet controller server to establish a C2 channel, thus allowing the threat actor to remotely control its target.
- Actions on objectives. After progressing through the first six phases, the intruders can take actions to achieve their original goals, such as information theft, denial, or hop to a third-party infrastructure.
3. Problem Statement
4. Techniques and Limitations
- General models, such as the MITRE ATT&CK or kill-chain models, where delivery is considered as a tactic that can be performed through different approaches.
- Threat actors reports, which analyze specific delivery techniques exploited in real operations.
- Initial classification approaches, which try to propose a classification scheme for delivery techniques but whose focus is not this scheme.
- Malware-focused analysis, which present the mechanisms used to deliver general or particular malware samples to a target.
- General techniques’ description, which provide an analysis for well-known delivery techniques in a general context, typically a whole hostile operation, without delving into the delivery internals.
- Particular techniques analysis, which provide an in-depth dissection of specific techniques such as social engineering or phishing, or of particular elements such as malware.
5. Our Proposal
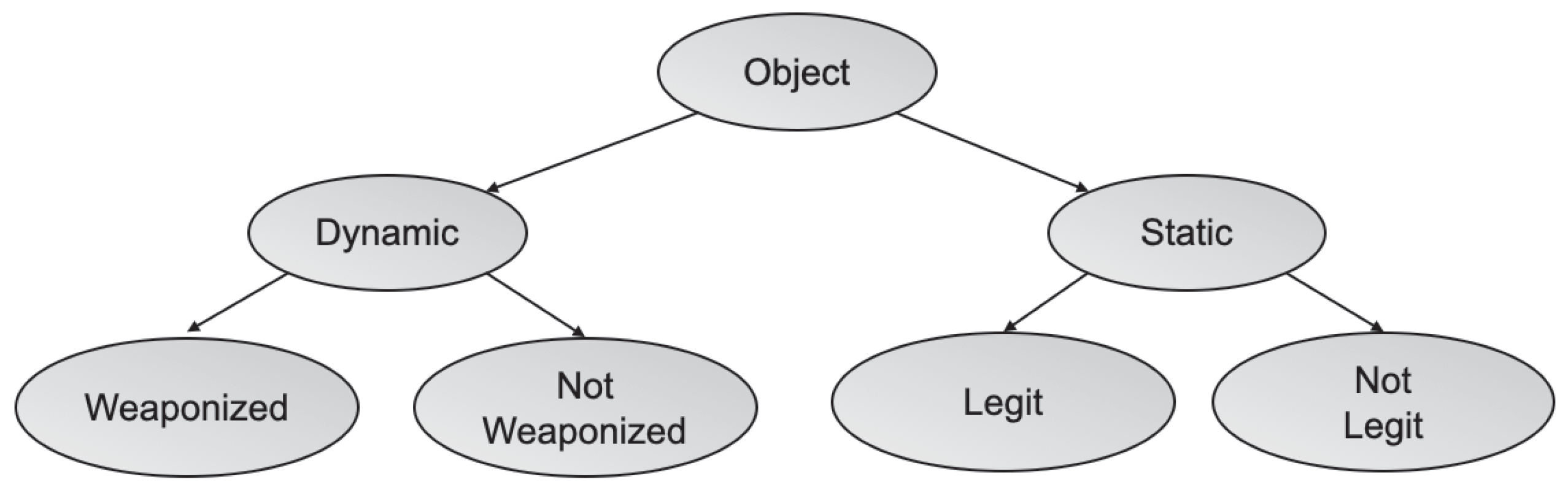
- Delivery Object, is the object used to break the target’s perimeter. This object is usually a deliverable artifact generated by a weaponizer, in which the malicious payload is embedded, typically in the form of an application data file such as Adobe Portable Document Format or Microsoft Office. However, our concept of object includes not only ad hoc, malicious artifacts, such as links or files, but also points out the infrastructure to be abused by hostile actors, such as public facing services.
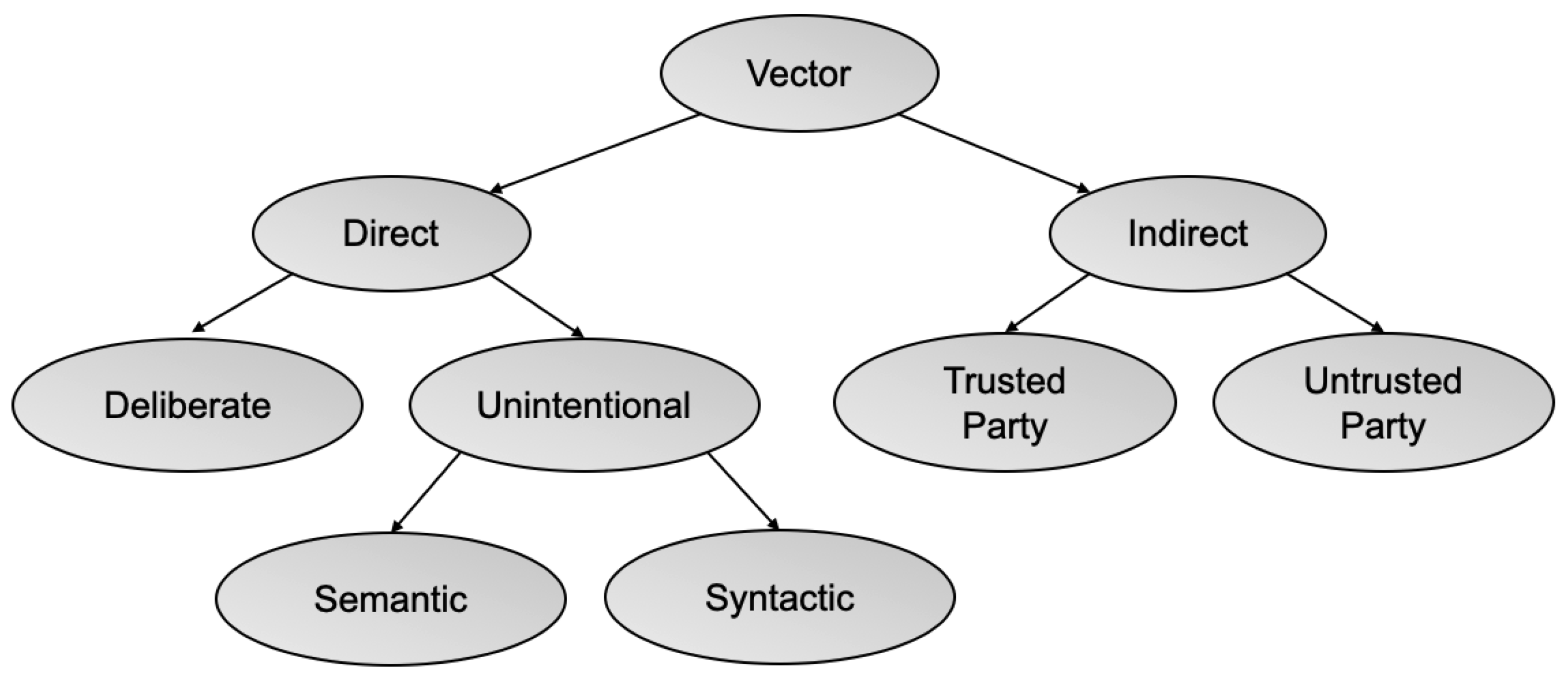
- Delivery Vector, is the transport used to deliver the artifact to its target. Examples of delivery vectors include USB memory drives, mail messages, hardware implants, or supply chains.
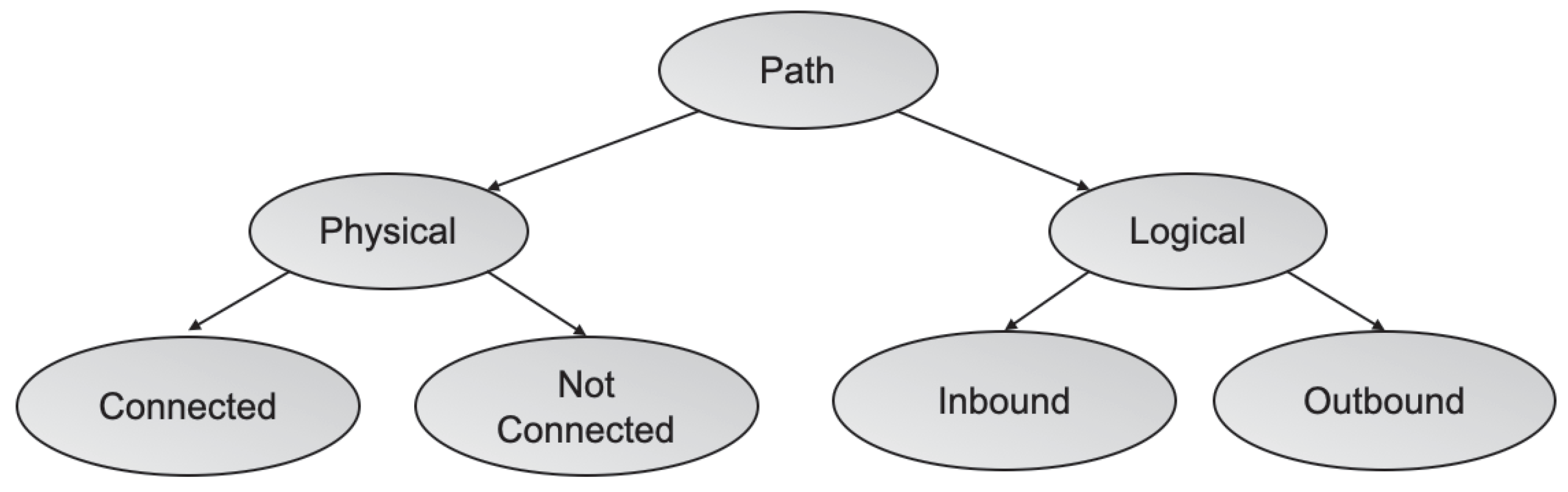
- Delivery Path, is the way the delivery vector breaks the target’s perimeter. Although in some cases this delivery path is directly linked to the delivery vector, in other cases they are independent, as we well analyze later in this work. Examples of delivery paths include both physical and logical routes to the target.
5.1. Mapping to MITRE ATT&CK
5.2. A Practical Example
- The mix of both approaches: the delivery of trojanized software through physical means, for example, through any removable media. This delivery technique is identified in our taxonomy, and it is a key threat to be considered in air-gapped networks, where software is installed or updated through physical media.
- The physical delivery of a trojanized element that is not directly connected to the target infrastructure, for example, a device to remotely listen to a conversation.
6. Discussion
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Monte, M. Network Attacks and Exploitation: A Framework; John Wiley and Sons: Hoboken, NJ, USA, 2015. [Google Scholar]
- Sood, A.K.; Enbody, R.J. Targeted cyberattacks: A superset of advanced persistent threats. IEEE Secur. Priv. 2012, 11, 54–61. [Google Scholar]
- Yadav, T.; Rao, A.M. Technical aspects of cyber kill chain. In Proceedings of the International Symposium on Security in Computing and Communication, Kochi, India, 10–13 August 2015; pp. 438–452. [Google Scholar]
- Strom, B.E.; Battaglia, J.A.; Kemmerer, M.S.; Kupersanin, W.; Miller, D.P.; Wampler, C.; Whitley, S.M.; Wolf, R.D. Finding Cyber Threats with ATT&CK™-Based Analytics; Technical Report; MITRE Technical Report MTR170202; The MITRE Corporation: McLean, VA, USA, 2017. [Google Scholar]
- Xiong, W.; Legrand, E.; Åberg, O.; Lagerström, R. Cyber security threat modeling based on the MITRE Enterprise ATT&CK Matrix. Softw. Syst. Model. 2022, 21, 157–177. [Google Scholar]
- Al-Shaer, R.; Spring, J.M.; Christou, E. Learning the associations of mitre ATT&CK adversarial techniques. In Proceedings of the 2020 IEEE Conference on Communications and Network Security (CNS), Avignon, France, 29 June–1 July 2020; pp. 1–9. [Google Scholar]
- Hutchins, E.M.; Cloppert, M.J.; Amin, R.M. Intelligence-driven computer network defense informed by analysis of adversary campaigns and intrusion kill chains. Lead. Issues Inf. Warf. Secur. Res. 2011, 1, 80. [Google Scholar]
- Garba, F.A.; Junaidu, S.B.; Ahmad, I.; Tekanyi, M. Proposed Framework for Effective Detection and Prediction of Advanced Persistent Threats Based on the Cyber Kill Chain. Sci. Pract. Cyber Secur. J. 2018, 3, 1–11. [Google Scholar]
- Myers, L. The Practicality of the Cyber Kill Chain Approach to Security. CSO Online. 2013. Available online: https://www.computerworld.com/article/2485687/the-practicality-of-the-cyber-kill-chain-approach-to-security.html (accessed on 1 December 2021).
- Zeng, W.; Germanos, V. Modelling Hybrid Cyber Kill Chain. In Proceedings of the International Workshop on Petri Nets and Software Engineering, Aachen, Germany, 23–28 June 2019. [Google Scholar]
- Laliberte, M. A Twist on The Cyber Kill Chain: Defending against a JavaScript Malware Attack. Dark Read. 2017. Available online: https://www.darkreading.com/attacks-breaches/a-twist-on-the-cyber-kill-chain-defending-against-a-javascript-malware-attack (accessed on 4 December 2021).
- Bryant, B.D.; Saiedian, H. A novel kill-chain framework for remote security log analysis with SIEM software. Comput. Secur. 2017, 67, 198–210. [Google Scholar] [CrossRef]
- Pols, P. The Unified Kill Chain: Designing a Unified Kill Chain for Analyzing, Comparing and Defending against Cyber Attacks; Technical Report; Cyber Security Academy: The Hague, The Netherlands, 2017. [Google Scholar]
- Hahn, A.; Thomas, R.K.; Lozano, I.; Cardenas, A. A multi-layered and kill-chain based security analysis framework for cyber-physical systems. Int. J. Crit. Infrastruct. Prot. 2015, 11, 39–50. [Google Scholar] [CrossRef]
- Case, D.U. Analysis of the cyber attack on the Ukrainian power grid. Electr. Inf. Shar. Anal. Cent. (E-ISAC) 2016, 388, 1–23. [Google Scholar]
- Zhou, X.; Xu, Z.; Wang, L.; Chen, K.; Chen, C.; Zhang, W. Kill chain for industrial control system. In Proceedings of the MATEC Web of Conferences, EDP Sciences, Nanjing, China, 24–26 May 2018; Volume 173, p. 01013. [Google Scholar]
- Lu, K.C.; Liu, I.H.; Li, J.S. A Survey of the Offensive and defensive in Industrial Control System. Bull. Netw. Comput. Syst. Softw. 2022, 11, 1–6. [Google Scholar]
- Skormin, V.A.; Summerville, D.H.; Moronski, J.S. Detecting Malicious Codes by the Presence of Their “Gene of Self-replication”. In Proceedings of the International Workshop on Mathematical Methods, Models, and Architectures for Computer Network Security, St. Petersburg, Russia, 21–23 September 2003; pp. 195–205. [Google Scholar]
- Dornhackl, H.; Kadletz, K.; Luh, R.; Tavolato, P. Malicious behavior patterns. In Proceedings of the 2014 IEEE 8th international symposium on service oriented system engineering, Oxford, UK, 7–11 April 2014; pp. 384–389. [Google Scholar]
- Chakkaravarthy, S.S.; Sangeetha, D.; Vaidehi, V. A survey on malware analysis and mitigation techniques. Comput. Sci. Rev. 2019, 32, 1–23. [Google Scholar] [CrossRef]
- Provos, N.; Mavrommatis, P.; Rajab, M.A.; Monrose, F. All Your IFRAMEs Point to Us. In Proceedings of the 17th Conference on Security Symposium (SS’08); USENIX Association: San Jose, CA, USA, 2008; pp. 1–15. [Google Scholar]
- Kwon, B.J.; Srinivas, V.; Deshpande, A.; Dumitraş, T. Catching worms, trojan horses and pups: Unsupervised detection of silent delivery campaigns. arXiv 2016, arXiv:1611.02787. [Google Scholar]
- Takey, Y.S.; Tatikayala, S.G.; Samavedam, S.S.; Eswari, P.L.; Patil, M.U. Real Time early Multi Stage Attack Detection. In Proceedings of the 2021 7th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 19–20 March 2021; Volume 1, pp. 283–290. [Google Scholar]
- Assante, M.J.; Lee, R.M. The industrial control system cyber kill chain. SANS Inst. InfoSec Read. Room 2015, 1. Available online: https://sansorg.egnyte.com/dl/HHa9fCekmc (accessed on 29 November 2021).
- Bahrami, P.N.; Dehghantanha, A.; Dargahi, T.; Parizi, R.M.; Choo, K.K.R.; Javadi, H.H. Cyber kill chain-based taxonomy of advanced persistent threat actors: Analogy of tactics, techniques, and procedures. J. Inf. Process. Syst. 2019, 15, 865–889. [Google Scholar]
- Dargahi, T.; Dehghantanha, A.; Bahrami, P.N.; Conti, M.; Bianchi, G.; Benedetto, L. A Cyber-Kill-Chain based taxonomy of crypto-ransomware features. J. Comput. Virol. Hacking Tech. 2019, 15, 277–305. [Google Scholar] [CrossRef] [Green Version]
- Mirza, Q.K.A.; Brown, M.; Halling, O.; Shand, L.; Alam, A. Ransomware Analysis using Cyber Kill Chain. In Proceedings of the 2021 8th International Conference on Future Internet of Things and Cloud (FiCloud), Rome, Italy, 23–25 August 2021; pp. 58–65. [Google Scholar]
- Bere, M.; Bhunu-Shava, F.; Gamundani, A.; Nhamu, I. How advanced persistent threats exploit humans. Int. J. Comput. Sci. Issues (IJCSI) 2015, 12, 170. [Google Scholar]
- Ussath, M.; Jaeger, D.; Cheng, F.; Meinel, C. Advanced persistent threats: Behind the scenes. In Proceedings of the 2016 Annual Conference on Information Science and Systems (CISS), Princeton, NJ, USA, 16–18 March 2016; pp. 181–186. [Google Scholar]
- Nelson, T.; Kettani, H. Open Source PowerShell-Written Post Exploitation Frameworks Used by Cyber Espionage Groups. In Proceedings of the 2020 3rd International Conference on Information and Computer Technologies (ICICT), San Jose, CA, USA, 9–12 March 2020; pp. 451–456. [Google Scholar]
- Quintero-Bonilla, S.; Martín del Rey, A. A new proposal on the advanced persistent threat: A survey. Appl. Sci. 2020, 10, 3874. [Google Scholar] [CrossRef]
- Chen, P.; Desmet, L.; Huygens, C. A study on advanced persistent threats. In Proceedings of the IFIP International Conference on Communications and Multimedia Security, Aveiro, Portugal, 25–26 September 2014; pp. 63–72. [Google Scholar]
- Siddiqi, M.A.; Ghani, N. Critical analysis on advanced persistent threats. Int. J. Comput. Appl. 2016, 141, 46–50. [Google Scholar]
- Zhu, Z.; Dumitras, T. Chainsmith: Automatically learning the semantics of malicious campaigns by mining threat intelligence reports. In Proceedings of the 2018 IEEE European Symposium on Security and Privacy (EuroS&P), London, UK, 24–26 April 2018; pp. 458–472. [Google Scholar]
- Gangwar, K.; Mohanty, S.; Mohapatra, A. Analysis and detection of ransomware through its delivery methods. In Proceedings of the International Conference on Recent Developments in Science, Engineering and Technology, Gurgaon, India, 13 October 2017; pp. 353–362. [Google Scholar]
- Raunak, P.; Krishnan, P. Network detection of ransomware delivered by exploit kit. ARPN J. Eng. Appl. Sci. 2017, 12, 3885–3889. [Google Scholar]
- Beckers, K.; Krautsevich, L.; Yautsiukhin, A. Analysis of social engineering threats with attack graphs. In Data Privacy Management, Autonomous Spontaneous Security, and Security Assurance; Springer: Berlin/Heidelberg, Germany, 2014; pp. 216–232. [Google Scholar]
- Jakobsson, M. Modeling and preventing phishing attacks. In Proceedings of the Financial Cryptography, Roseau, Dominica, 28 February–3 March 2005; Volume 5. [Google Scholar]
- Foozy, C.F.M.; Ahmad, R.; Abdollah, M.F. Phishing detection taxonomy for mobile device. Int. J. Comput. Sci. Issues (IJCSI) 2013, 10, 338–344. [Google Scholar]
- Lacey, D.; Salmon, P.; Glancy, P. Taking the bait: A systems analysis of phishing attacks. Procedia Manuf. 2015, 3, 1109–1116. [Google Scholar] [CrossRef]
- Särökaari, N. Phishing Attacks and Mitigation Tactics. Ph.D. Thesis, University of Jyväskylä, Jyväskylä, Finland, 2020. [Google Scholar]
- Krithika, N. A Study On WHA (Watering Hole Attack)–The Most Dangerous Threat To The Organisation. Int. J. Innov. Sci. Eng. Res. (IJISER) 2017, 4, 196–198. [Google Scholar]
- Subburaj, T.; Suthendran, K. DigitalWatering Hole Attack Detection Using Sequential Pattern. J. Cyber Secur. Mobil. 2018, 7, 1–12. [Google Scholar] [CrossRef] [Green Version]
- Bowen, B.M.; Hershkop, S.; Keromytis, A.D.; Stolfo, S.J. Baiting inside attackers using decoy documents. In Proceedings of the International Conference on Security and Privacy in Communication Systems, Turin, Italy, 3–5 June 2009; pp. 51–70. [Google Scholar]
- Chetioui, K.; Bah, B.; Alami, A.O.; Bahnasse, A. Overview of Social Engineering Attacks on Social Networks. Procedia Comput. Sci. 2022, 198, 656–661. [Google Scholar] [CrossRef]
- Reed, M.; Miller, J.F.; Popick, P. Supply chain attack patterns: Framework and Catalog; Office of the Deputy Assistant Secretary of Defense for Systems Engineering: Washington, DC, USA, 2014. [Google Scholar]
- Coufalíková, A.; Klaban, I.; Šlajs, T. Complex strategy against supply chain attacks. In Proceedings of the 2021 International Conference on Military Technologies (ICMT), Brno, Czech Republic, 8–11 June 2021; pp. 1–5. [Google Scholar]
- Yeboah-Ofori, A.; Ismail, U.M.; Swidurski, T.; Opoku-Boateng, F. Cyberattack ontology: A knowledge representation for cyber supply chain security. In Proceedings of the 2021 International Conference on Computing, Computational Modelling and Applications (ICCMA), Brest, France, 14–16 July 2021; pp. 65–70. [Google Scholar]
- Ivaturi, K.; Janczewski, L. A taxonomy for social engineering attacks. In Proceedings of the International Conference on Information Resources Management, Centre for Information Technology, Organizations, and People, Shenzhen, China, 26–27 November 2011; pp. 1–12. [Google Scholar]
- Krombholz, K.; Hobel, H.; Huber, M.; Weippl, E. Advanced social engineering attacks. J. Inf. Secur. Appl. 2015, 22, 113–122. [Google Scholar] [CrossRef]
- Heartfield, R.; Loukas, G. A taxonomy of attacks and a survey of defence mechanisms for semantic social engineering attacks. ACM Comput. Surv. (CSUR) 2015, 48, 1–39. [Google Scholar] [CrossRef]
- Aldawood, H.; Skinner, G. An Advanced Taxonomy for Social Engineering Attacks. Int. J. Comput. Appl. 2020, 177, 1–11. [Google Scholar] [CrossRef]
- Fan, W.; Lwakatare, K.; Rong, R. Social engineering: IE based model of human weakness for attack and defense investigations. Int. J. Comput. Netw. Inf. Secur. 2017, 9, 1–11. [Google Scholar] [CrossRef] [Green Version]
- Salahdine, F.; Kaabouch, N. Social engineering attacks: A survey. Future Internet 2019, 11, 89. [Google Scholar] [CrossRef] [Green Version]
- Chaudhry, J.A.; Rittenhouse, R.G. Phishing: Classification and countermeasures. In Proceedings of the 2015 7th International Conference on Multimedia, Computer Graphics and Broadcasting (MulGraB), Jeju, Korea, 25–28 November 2015; pp. 28–31. [Google Scholar]
- Rastenis, J.; Ramanauskaitė, S.; Janulevičius, J.; Čenys, A.; Slotkienė, A.; Pakrijauskas, K. E-mail-based phishing attack taxonomy. Appl. Sci. 2020, 10, 2363. [Google Scholar] [CrossRef] [Green Version]
- Varshney, G.; Misra, M.; Atrey, P.K. A survey and classification of web phishing detection schemes. Secur. Commun. Netw. 2016, 9, 6266–6284. [Google Scholar] [CrossRef]
- Adeka, M.I. Cryptography and Computer Communications Security. Extending the Human Security Perimeter through a Web of Trust. Ph.D. Thesis, University of Bradford, Bradford, UK, 2015. [Google Scholar]
- Colwill, C. Human factors in information security: The insider threat–Who can you trust these days? Inf. Secur. Tech. Rep. 2009, 14, 186–196. [Google Scholar] [CrossRef]
- Ani, U.D.; He, H.; Tiwari, A. Human factor security: Evaluating the cybersecurity capacity of the industrial workforce. J. Syst. Inf. Technol. 2019, 21, 2–35. [Google Scholar] [CrossRef]
- Gozon, F.Z.; Vaczi, D.; Toth-Laufer, E. Fuzzy-based Human Factor Centered Cybersecurity Risk Assessment. In Proceedings of the 2021 IEEE 19th International Symposium on Intelligent Systems and Informatics (SISY), Subotica, Serbia, 16–18 September 2021; pp. 83–88. [Google Scholar]
- Van Vuuren, I.E. IT security trust model-securing the human perimeter. Int. J. Soc. Sci. Humanit. 2016, 6, 852. [Google Scholar] [CrossRef] [Green Version]
- Astakhova, L.; Medvedev, I. An Information Tool for Increasing the Resistance of Employees of an Organization to Social Engineering Attacks. Sci. Tech. Inf. Process. 2021, 48, 15–20. [Google Scholar] [CrossRef]
- Subramanian, R.K.; Kumar Kattumannil, D. ERRM Gap Analysis & Identification. In Event-and Data-Centric Enterprise Risk-Adjusted Return Management; Springer: Berlin/Heidelberg, Germany, 2022; pp. 205–283. [Google Scholar]
- Bullee, J.W.; Montoya, L.; Junger, M.; Hartel, P. Spear phishing in organisations explained. Inf. Comput. Secur. 2017, 25, 593–613. [Google Scholar] [CrossRef]
- Rendall, K.; Nisioti, A.; Mylonas, A. Towards a multi-layered phishing detection. Sensors 2020, 20, 4540. [Google Scholar] [CrossRef]
- Parmar, B. Protecting against spear-phishing. Comput. Fraud Secur. 2012, 2012, 8–11. [Google Scholar] [CrossRef]
- Threat Landscape for Supply Chain Attacks; Technical Report; European Union Agency for Cybersecurity (ENISA): Athens, Greece, 2021.
- Collier, Z.A.; Sarkis, J. The zero trust supply chain: Managing supply chain risk in the absence of trust. Int. J. Prod. Res. 2021, 59, 3430–3445. [Google Scholar] [CrossRef]
- Al-Amin, S.; Sharkar, S.R.; Kaiser, M.S.; Biswas, M. Towards a blockchain-based supply chain management for e-agro business system. In Proceedings of the International Conference on Trends in Computational and Cognitive Engineering, Online, 21–22 October 2021; pp. 329–339. [Google Scholar]
- Latif, M.N.A.; Aziz, N.A.A.; Hussin, N.S.N.; Aziz, Z.A. Cyber security in supply chain management: A systematic review. LogForum 2021, 17, 49–57. [Google Scholar] [CrossRef]
- Novoszel, L.; Wakolbinger, T. Meta-analysis of Supply Chain Disruption Research. In Proceedings of the Operations Research Forum; Springer: Berlin/Heidelberg, Germany; Volume 3, pp. 1–25.
- Peisert, S.; Schneier, B.; Okhravi, H.; Massacci, F.; Benzel, T.; Landwehr, C.; Mannan, M.; Mirkovic, J.; Prakash, A.; Michael, J.B. Perspectives on the SolarWinds incident. IEEE Secur. Priv. 2021, 19, 7–13. [Google Scholar] [CrossRef]
- Ohm, M.; Plate, H.; Sykosch, A.; Meier, M. Backstabber’s knife collection: A review of open source software supply chain attacks. In Proceedings of the International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, Lisbon, Portugal, 24–26 June 2020; pp. 23–43. [Google Scholar]
- Halak, B. Cist: A threat modelling approach for hardware supply chain security. In Hardware Supply Chain Security; Springer: Berlin/Heidelberg, Germany, 2021; pp. 3–65. [Google Scholar]
- Halak, B. Hardware Supply Chain Security: Threat Modelling, Emerging Attacks and Countermeasures; Springer Nature: Berlin/Heidelberg, Germany, 2021. [Google Scholar]
- Harrison, J.; Asadizanjani, N.; Tehranipoor, M. On malicious implants in PCBs throughout the supply chain. Integration 2021, 79, 12–22. [Google Scholar] [CrossRef]
- Arquilla, J.; Guzdial, M. The SolarWinds hack, and a grand challenge for CS education. Commun. ACM 2021, 64, 6–7. [Google Scholar] [CrossRef]
- Analytica, O. Kaseya Ransomware Attack Underlines Supply Chain Risks; Technical Report oxan-es; Oxford Analytica: Oxford, UK, 2021. [Google Scholar]
- Hope, A. North Korean Lazarus Hacking Group Leverages Supply Chain Attacks to Distribute Malware for Cyber Espionage. CPO Magazine, 5 November 2021. [Google Scholar]
- Chinchani, R.; Iyer, A.; Ngo, H.Q.; Upadhyaya, S. Towards a theory of insider threat assessment. In Proceedings of the 2005 International Conference on Dependable Systems and Networks (DSN’05), Yokohama, Japan, 28 June–1 July 2005; pp. 108–117. [Google Scholar]
- Bishop, M.; Gates, C. Defining the insider threat. In Proceedings of the 4th Annual Workshop on Cyber Security and Information Intelligence Research: Developing Strategies to Meet the Cyber Security and Information Intelligence Challenges Ahead, Oak Ridge, TN, USA, 12–14 May 2008; pp. 1–3. [Google Scholar]
- Probst, C.W.; Hunker, J.; Gollmann, D.; Bishop, M. Aspects of insider threats. In Insider Threats in Cyber Security; Springer: Berlin/Heidelberg, Germany, 2010; pp. 1–15. [Google Scholar]
- Hunker, J.; Probst, C.W. Insiders and Insider Threats-An Overview of Definitions and Mitigation Techniques. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2011, 2, 4–27. [Google Scholar]
- Georgiadou, A.; Mouzakitis, S.; Askounis, D. Detecting Insider Threat via a Cyber-Security Culture Framework. J. Comput. Inf. Syst. 2021, 1–11. [Google Scholar] [CrossRef]
- Wei, Y.; Chow, K.P.; Yiu, S.M. Insider threat prediction based on unsupervised anomaly detection scheme for proactive forensic investigation. Forensic Sci. Int. Digit. Investig. 2021, 38, 301126. [Google Scholar] [CrossRef]
- Miller, J.F. Supply Chain Attack Framework and Attack Patterns; Technical Report; MITRE Corp: Mclean, VA, USA, 2013. [Google Scholar]
- Yeboah-Ofori, A.; Islam, S. Cyber security threat modeling for supply chain organizational environments. Future Internet 2019, 11, 63. [Google Scholar] [CrossRef] [Green Version]
- Yeboah-Ofori, A.; Mouratidis, H.; Ismai, U.; Islam, S.; Papastergiou, S. Cyber Supply Chain Threat Analysis and Prediction Using Machine Learning and Ontology. In Proceedings of the IFIP International Conference on Artificial Intelligence Applications and Innovations, Crete, Greece, 25–27 June 2021; pp. 518–530. [Google Scholar]
- Saxena, N.; Hayes, E.; Bertino, E.; Ojo, P.; Choo, K.K.R.; Burnap, P. Impact and key challenges of insider threats on organizations and critical businesses. Electronics 2020, 9, 1460. [Google Scholar] [CrossRef]
- Liu, L.; De Vel, O.; Han, Q.L.; Zhang, J.; Xiang, Y. Detecting and preventing cyber insider threats: A survey. IEEE Commun. Surv. Tutor. 2018, 20, 1397–1417. [Google Scholar] [CrossRef]
- Badhwar, R. Commentary on Insider Threat. In The CISO’s Next Frontier; Springer: Berlin/Heidelberg, Germany, 2021; pp. 345–351. [Google Scholar]
- Wang, J.H.; Tavoosi, J.; Mohammadzadeh, A.; Mobayen, S.; Asad, J.H.; Assawinchaichote, W.; Vu, M.T.; Skruch, P. Non-Singleton Type-3 Fuzzy Approach for Flowmeter Fault Detection: Experimental Study in a Gas Industry. Sensors 2021, 21, 7419. [Google Scholar] [CrossRef]
- Qin, S.; Zhang, C.; Zhao, T.; Tong, W.; Bao, Q.; Mao, Y. Dynamic High-Type Interval Type-2 Fuzzy Logic Control for Photoelectric Tracking System. Processes 2022, 10, 562. [Google Scholar] [CrossRef]
- Amanlou, A.; Suratgar, A.A.; Tavoosi, J.; Mohammadzadeh, A.; Mosavi, A. Single-Image Reflection Removal Using Deep Learning: A Systematic Review. IEEE Access 2022, 10, 29937–29953. [Google Scholar] [CrossRef]
- Inac, H.; Oztemel, E. An assessment framework for the transformation of mobility 4.0 in smart cities. Systems 2021, 10, 1. [Google Scholar] [CrossRef]
- Oladipo, I.D.; AbdulRaheem, M.; Awotunde, J.B.; Bhoi, A.K.; Adeniyi, E.A.; Abiodun, M.K. Machine Learning and Deep Learning Algorithms for Smart Cities: A Start-of-the-Art Review. In IoT IoE Driven Smart Cities; Springer: Cham, Switzerland, 2022; pp. 143–162. [Google Scholar] [CrossRef]
- Wang, L.; Zhang, Y. Linear approximation fuzzy model for fault detection in cyber-physical system for supply chain management. Enterp. Inf. Syst. 2021, 15, 966–983. [Google Scholar] [CrossRef]
- Alshurideh, M.T.; Al Kurdi, B.; Alzoubi, H.M.; Ghazal, T.M.; Said, R.A.; AlHamad, A.Q.; Hamadneh, S.; Sahawneh, N.; Al-kassem, A.H. Fuzzy assisted human resource management for supply chain management issues. Ann. Oper. Res. 2022, 1–19. [Google Scholar] [CrossRef]
- Bukowski, L.; Feliks, J. Fuzzy logic expert system for supply chain resilience modelling and simulation. J. Pol. Saf. Reliab. Assoc. 2015, 6, 31–38. [Google Scholar]
- Kumar, S.; Anbanandam, R. An integrated Delphi–fuzzy logic approach for measuring supply chain resilience: An illustrative case from manufacturing industry. Meas. Bus. Excell. 2019, 23, 350–375. [Google Scholar] [CrossRef]
- Gallab, M.; Bouloiz, H.; Alaoui, Y.L.; Tkiouat, M. Risk assessment of maintenance activities using fuzzy logic. Procedia Comput. Sci. 2019, 148, 226–235. [Google Scholar] [CrossRef]
- Díaz-Curbelo, A.; Espin Andrade, R.A.; Gento Municio, Á.M. The role of fuzzy logic to dealing with epistemic uncertainty in supply chain risk assessment: Review standpoints. Int. J. Fuzzy Syst. 2020, 22, 2769–2791. [Google Scholar] [CrossRef]

| Family | References | Pros | Cons |
|---|---|---|---|
| General models | [13,24,25,26,27] | Industry standards Specifications based on real attacks Useful for the identification of particular techniques in offensive operations | Plain structure Not an in-depth analysis Not designed for the identification of security gaps |
| Threat actors reports | [28,29,30,31] | Real world cases In-depth analysis for each case New delivery techniques are presented | Focus on specific delivery techniques No structure proposal |
| Initial classifications | [32,33] | Initial structure for techniques Real techniques mapping | Not focused on delivery, but general approaches Date of publication |
| Malware-focused | [26,34,35,36] | In-depth analysis for malware delivery Detection oriented Malware as a relevant threat | Focus on specific s: malware and malware related Not designed to identify security gaps outside malware ecosystem |
| General techniques | [37,38,39,40,41,42,43,44,45,46,47,48] | Delivery techniques analyzed with a global operation perspective: completeness Real world cases | No classification proposal Not in-depth analysis |
| Particular techniques | [49,50,51,52,53,54,55,56,57] | In-depth analysis of particular techniques Structure proposals for these techniques | Focus on particular techniques, without considering a global delivery scheme |
| Object | Dynamic | Weaponized | |
| Not Weaponized | |||
| Static | Legit | ||
| Not legit | |||
| Vector | Direct | Deliberate | |
| Unintentional | Syntactic | ||
| Semantic | |||
| Indirect | Trusted Party | ||
| Untrusted Party | |||
| Path | Physical | Connected | |
| Not Connected | |||
| Logical | Inbound | ||
| Outbound | |||
| Technique ID | Name | Sub-Techniques |
|---|---|---|
| T1189 | Drive-by Compromise | N/A |
| T1190 | Exploit Public-Facing Application | N/A |
| T1133 | External Remote Services | N/A |
| T1200 | Hardware Additions | N/A |
| T1566 | Phishing | - Spearphishing Attachment |
| - Spearphishing Link | ||
| - Spearphishing via Service | ||
| T1091 | Replication Through Removable Media | N/A |
| T1195 | Supply Chain Compromise | - Compromise Software Dependencies and Development Tools |
| - Compromise Software Supply Chain | ||
| - Compromise Hardware Supply Chain | ||
| T1199 | Trusted Relationship | N/A |
| T1078 | Valid Accounts | - Default Accounts |
| - Domain Accounts | ||
| - Local Accounts | ||
| - Cloud Accounts |
| Object (T1195) | Dynamic | Weaponized (T1189, T1566, T1091) | |
| Non-Weaponized (T1190) | |||
| Static | Legit (T1078, T1199, T1133) | ||
| Not legit (T1200) | |||
| Vector | Direct | Deliberate | |
| Unintentional | Syntactic (T1190, T1133, T1200, T1091, T1078) | ||
| Semantic (T1566) | |||
| Indirect | Trusted Party (T1195, 1199) | ||
| Untrusted Party (T1189) | |||
| Path | Physical | Connected (T1200, T1091, T1195.003) | |
| Not Connected | |||
| Logical | Inbound (T1190, T1133, T1195.001, T1195.002, T1078) | ||
| Outbound (T1189, T1566, T1199) | |||
| Technique ID | Name | Number of Groups |
|---|---|---|
| T1189 | Drive-by Compromise | 24 |
| T1190 | Exploit Public-Facing Application | 16 |
| T1133 | External Remote Services | 20 |
| T1200 | Hardware Additions | 1 |
| T1566.001 | Spear phishing Attachment | 64 |
| T1566.002 | Spear phishing Link | 34 |
| T1566.003 | Spear phishing via Service | 7 |
| T1091 | Replication Through Removable Media | 4 |
| T1195.001 | Compromise Software Dependencies and Development Tools | 0 |
| T1195.002 | Compromise Software Supply Chain | 6 |
| T1195.003 | Compromise Hardware Supply Chain | 0 |
| T1199 | Trusted Relationship | 5 |
| T1078.001 | Valid Accounts: Default | 0 |
| T1078.002 | Valid Accounts: Domain | 10 |
| T1078.003 | Valid Accounts: Local | 8 |
| T1078.004 | Valid Accounts: Cloud | 2 |
| Object (6) | Dynamic | Weaponized (133) | |
| Non-Weaponized (16) | |||
| Static | Legit (45) | ||
| Not legit (1) | |||
| Vector | Direct | Deliberate | |
| Unintentional | Syntactic (61) | ||
| Semantic (105) | |||
| Indirect | Trusted Party (11) | ||
| Untrusted Party (24) | |||
| Path | Physical | Connected (5) | |
| Not Connected | |||
| Logical | Inbound (62) | ||
| Outbound (134) | |||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Villalón-Huerta, A.; Ripoll-Ripoll, I.; Marco-Gisbert, H. A Taxonomy for Threat Actors’ Delivery Techniques. Appl. Sci. 2022, 12, 3929. https://doi.org/10.3390/app12083929
Villalón-Huerta A, Ripoll-Ripoll I, Marco-Gisbert H. A Taxonomy for Threat Actors’ Delivery Techniques. Applied Sciences. 2022; 12(8):3929. https://doi.org/10.3390/app12083929
Chicago/Turabian StyleVillalón-Huerta, Antonio, Ismael Ripoll-Ripoll, and Hector Marco-Gisbert. 2022. "A Taxonomy for Threat Actors’ Delivery Techniques" Applied Sciences 12, no. 8: 3929. https://doi.org/10.3390/app12083929
APA StyleVillalón-Huerta, A., Ripoll-Ripoll, I., & Marco-Gisbert, H. (2022). A Taxonomy for Threat Actors’ Delivery Techniques. Applied Sciences, 12(8), 3929. https://doi.org/10.3390/app12083929







