Abstract
The Internet of Drones (IoD) is greatly developed and promotes many civil applications. However, it can still be prone to several security problems which threaten public safety. The issue of security poses further problems upon linking the IoD to the Internet, as its data stream is exposed to attack. For secure communication between drones, an effective route planning scheme with a major intention of accomplishing security is needed. With this aim, this study develops an enhanced search-and-rescue optimization-enabled secure route planning (ESRO-SRP) scheme for the IoD environment. The presented ESRO-SRP technique mainly aims to derive a set of optimal routes to the destination. In addition, the ESRO-SRP algorithm is derived by the integration of the quasi-oppositional-based learning (QOBL) concept with the conventional SRO algorithm. Moreover, the presented ESRO-SRP technique derived a fitness function encompassing different input parameters such as residual energy, distance, and degree of trust. The experimental validation of the ESRO-SRP technique is carried out under several aspects, and the results demonstrated the enhancements of the ESRO-SRP model over recent approaches. The ESRO-SRP model has provided an increased packet delivery ratio (PDR) of 86%, whereas the BRUe-IoE, ORP-FANET, UAVe-WSN, and TR-UAV Swarm approaches have accomplished a minimal PDR of 79.60%, 73.60%, 67.60%, and 63.20%, respectively.
1. Introduction
The use of unmanned aerial vehicles (UAVs), also termed drones, is anticipated to incline at exceptional rates because of growing curiosity from investors, hobbyists, and researchers; the quantity of drones is quickly rising, and the Internet of Drones (IoD) environment and number of related applications are expanding rapidly, in which an infinite number of multi-sized drones flawlessly communicate with one another via area service providers whose objective it is to understand and align the accessibility of drones to a controlled airspace and operate a navigation service [1]. The economic development of drone industries in the United States, involving military scouting, traffic, wildlife surveillance, urban safety scrutiny of infrastructure, on-demand package supply, aerial photography, etc., is reported to be substantial for industries or business operations [2,3]. Figure 1 depicts the procedure of IoD.
Figure 1.
Application areas of IoD.
Even though the IoD network offers numerous benefits, it also carries numerous susceptibilities which should be handled, the most important criteria of which are privacy and security problems [4]. However, the IoD network system is commonly placed for real-time application zones where end users need to obtain real-time information from UAVs which are connected to a particular area. So, there are high chances of security assaults occurring, leading to the colossal ruin of the data exchange functions inside the network [5,6,7]. An attacker can gain access to the keys and block transmissions. For the accessibility of keys, the intruder can abuse a susceptibility in the IoD network and its application zones. The intruder might alter this information, resulting in the misguidance of the receivers. However, IoD access management is a significant variable, and security problems regarding authorization and accessibilities must be emphasized [8,9]. This applies to the data in transfer, which should be protected for confidentiality, authenticity, and integrity.
Most of the privacy and security methods advanced by authors were intended to ensure security measures on the IoD network [10,11]. The approaches focused on mitigating problems which influence the secure localization of drones or privacy and security necessities linked with the IoD network system. Localization fault assaults impede the reliability position of UAVs, leading to distressing costs for the overall functionality of the IoD network [12]. Additionally, privacy and security necessities are the objectives that decide the functions and capacities of the IoD network attained in justifying certain privacy and security measures [13]. The privacy and security needs of the IoD network involve authenticity, integrity, availability, privacy preservation, and confidentiality [14].
Tian et al. [15] suggested a powerful privacy-preserving validation architecture. With the help of a lightweight online/offline signature model, this architecture guarantees verification effectiveness while placing resource constraints on small-scale UAVs. Considering the high mobility of UAVs, a prediction validation model is explored by using mobile edge computing (MEC) in this architecture for reducing the verification expenses for possible verification activity. Allouch et al. [16] developed an Unmanned Traffic Management (UTM)-Chain, a light-weight blockchain-related security model with hyper ledger fabric for UTM of lower-altitude UAV that fits the storage and computation resource constraints of UAV. Furthermore, UTM-Chain offers secured and unchangeable traffic information among their ground control stations and the UAVs. In [8], a blockchain-related security model for cyber-physical systems is introduced for ensuring secured transmission of datasets amongst drones. In this model, the miner node is chosen by deep learning (DL)-based technique, that is, a deep Boltzmann machine, with features such as flight time of the drone, computation resource, and the available battery power.
The authors in [17] developed a lightweight user verification system where the client in the IoD environments needs to directly access information from a drone to show that the client is authorized for accessing the dataset from that drone. The formal security validation with the generally recognized automatic confirmation of Internet security protocol and application tool alongside informal security investigation shows that the suggested technique is secured against well-known attacks. In [18], the authors developed a Drone-map organizer, viz., a service-related fog-based drone managing scheme that monitors, communicates, and controls with drones through the networks. The suggested technique enables interaction with various drones through the internet that allows drones to be controlled anyplace and anywhere, with no long-distance restrictions. This model offers drones access to fog computational resources for drones to perform heavyweight load computation. Though existing works have focused on the IoD environment, it is still necessary to design energy-efficient and security-based solutions for the IoD environment with the inclusion of multiple input parameters of the drones.
This study develops an enhanced search-and-rescue optimization-enabled secure route planning (ESRO-SRP) scheme for the IoD environment. The presented ESRO-SRP technique mainly aims to derive a set of optimal routes to the destination. In addition, the ESRO-SRP algorithm is derived by the integration of the quasi-oppositional-based learning (QOBL) concept with the conventional SRO algorithm. Moreover, the presented ESRO-SRP technique derived a fitness function encompassing different input parameters such as residual energy (RE), distance, and trust degree. The experimental validation of the ESRO-SRP technique is carried out under several aspects. In short, the major contributions are summarized as follows.
- To the best of our knowledge, the ESRO-SRP technique for the IoD environment does not exist in the literature.
- Develop a new ESRO-SRP technique for a secure route selection process in the IoD environment.
- Derive an ESRO-SRP algorithm using the combination of QOBL with the traditional SRO algorithm and derive a fitness function involving multiple input parameters.
- Simulate the performance of the ESRO-SRP technique under varying levels of energy consumption in the IoD environment.
2. Materials and Methods
In this study, a novel ESRO-SRP technique has been developed for secure communication among drones in the IoD environment. The presented ESRO-SRP technique mainly aims to derive a set of optimal routes to the destination. In addition, the ESRO-SRP algorithm is derived by the integration of the QOBL concept with the conventional SRO algorithm. Moreover, the presented ESRO-SRP technique derived a fitness function encompassing different input parameters such as RE, distance, and trust degree.
2.1. Overview of ESRO-SRO Algorithm
In the SRO approach, the human position is equal to the resolution of the optimization issues, and the clue quantity accomplished in the location characterizes the objective function. The group members gather clue information in the search. Few clues are absent in the event of gaining optimal clues in another position, but the dataset is exploited for optimizing the searching technique [19]. Here, the position of the left clue can be stored in the ( memory matrix), where the position of the human is stored in the ( position matrix). The matrix dimension is the same as . They are matrices, whereas symbolizes problem dimension and embodies human count. The clue matrixes have the attained clue position. The and matrixes are upgraded in all human searching processes [19]:
In Equation (1), and represent the position of human and memory matrixes; correspondingly, embodies the position of initialized dimension for human, and characterizes dimensional position for the preliminary memory. Given the description presented in the previous section, in addition to an arbitrary clue amid accomplished clues, the search path is described as follows:
In Equation (2), , and correspondingly symbolize human location, the clue location, and human searching direction; suggests arbitrary numbers within 1 and and appropriately chosen It is important to emphasize that human usually seeks accordingly, and some repetitious positions could not be searched another time. Henceforth, the search should be generated if the group member is restrained. Therefore, dimension could not be rehabilitated.
For applying this constraint, the binomial crossover operator has been exploited when the clue is larger than that of the clue associated with the present position, an direction and the position of that search clue; next, the searching method undergoes the present location beside the direction [16].
where the following are defined: symbolizes the novel place of parameters of humans; specifies place of parameter for the accomplished clues; and correspondingly imply an objective function for the and solution; and epitomize arbitrary value; symbolizes arbitrary value within 1 and that assures that 1D of is varied from . Equation (3) is applied to accomplish a new place of human in all dimensions.
Next, humans search nearby the current place, and the concept of related discrete clues applied in the social phase is exploited for searching. In conflict with the social phase, dimension is attuned in the separation phase. The novel place of human can be accomplished as follows [16]:
In Equation (4), and characterize arbitrary numbers within 1 and . To evade motion besides another clue, and are designated in this manner, such that symbolizes an arbitrary value between zero and one. In the metaheuristic method, each solution should be positioned in the solution region, and when they are farther from the permitted solution region, they should be altered. If the novel place of a human is farther from the solution region, the succeeding equation is exploited for altering the novel place:
The process involved in the SRO algorithm is given in Algorithm 1.
| Algorithm 1: Pseudo-code of the SRO algorithm |
| Begin rand [−1, 1] do End For do End For do End for End If End for Decide the existing finest place and upgrade Xbest End while Return Xbest End |
Next, in all iterations, the member of the group searched according to the two phases, and after each stage, once the value of the main function is in position, is greater than that of the preceding one ( thus the earlier position would be stored in an arbitrary place of the M memory matrix and it would be adopted as a novel place. If not, the position is left and memory is not improved:
where indicates the location of clue saved in the , and represents arbitrary numbers within 1 and . With that memory, upgrading increases the different kinds of techniques and the ability of methods for detecting a globally optimum solution. Firstly, the unsuccessful search number (USN) is fixed as zero for all human beings. Once the human discovers an optimal clue in the first and second stages of the searching technique, the USN is fixed as zero for that human; if not, it raises it by one point as follows [16]:
The arbitrary place from the search region is represented in the following equation and is fixed as zero for that human:
In Equation (9), designates an arbitrary value and is discrete for each dimension. Tizhoosh proposed the concept of oppositional-based learning (OBL) that includes opposite numbers having the highest possibility of accomplishing a solution compared to arbitrary numbers. The incorporation of OBL with the SRO method leads to an improved convergence rate and effective result of the presented ESRO-SRP algorithm. The QOBL method applies quasi-opposite value efficiently through the opposite number in the global optimal outcome. Assume represents a real number in -dimensional region. The and opposite and quasi-opposite numbers are shown in the following [20]:
In which and ].
Let be a point from the -dimensional region. The opposite point, and quasi-opposite point, are shown in the following.
Here, and
In QOBL is exploited to the SRO algorithm to initialize the population as well as creation jumping. It generates a group of optimum outcomes for population initialization [8]. Algorithm 2 defines the QOBL pseudo-code to the novel population.
| Algorithm 2: Pseudo-code of QOBL |
else end if end for end for |
2.2. Process Involved in ESRO-SRP Technique
To define an optimum group of routes, an offered function was employed to determine the following hop to destination and is represented by:
The drive is to determine an optimum group of routes from the cluster heads (CHs) to the base station (BS), employing a fitness function (FF) comprising 2 parameters such as energy and distance. Primarily, the RE of the next-hop node is determined, and a node with higher energy was provided as a relay node. To transfer data, the source node sends it to the relay node, which is further forwarded to BS utilizing inter CHs. Thus, the node with higher RE is provided as the next-hop node. A primary sub-objective was offered as:
In addition, the Euclidean distance was executed to define the distance from CH to BS. The minimized energy dissipation was frequently dependent on the broadcast distances. With a lesser distance, the energy was retained significantly [21]. Once the distance is improved, a further count of energy is spent. Hence, the node with lesser distances is chosen to relay nodes. So, the next sub-objective using distance is which is formulated as:
The present research work utilized direct trust values (TVs) amongst drones, and their mathematical process was signified as:
Here, and denotes the direct as well as indirect TVs of one node to another node correspondingly. The count of trust nodes from the cluster is attained in the group with maximal TVs, and their state value was provided by the level of confidence values suggested in one node to another node. The TV of BS was computed as:
In the above formula, refers to the trusted value and represents the amount of drones. If the path trust was smaller than the trust requirement value, the path trust alert occurrence was triggered.
The above-mentioned sub-objective was revised as to FF as offered in that and denotes the weight assigned to every sub-objective.
3. Results and Discussion
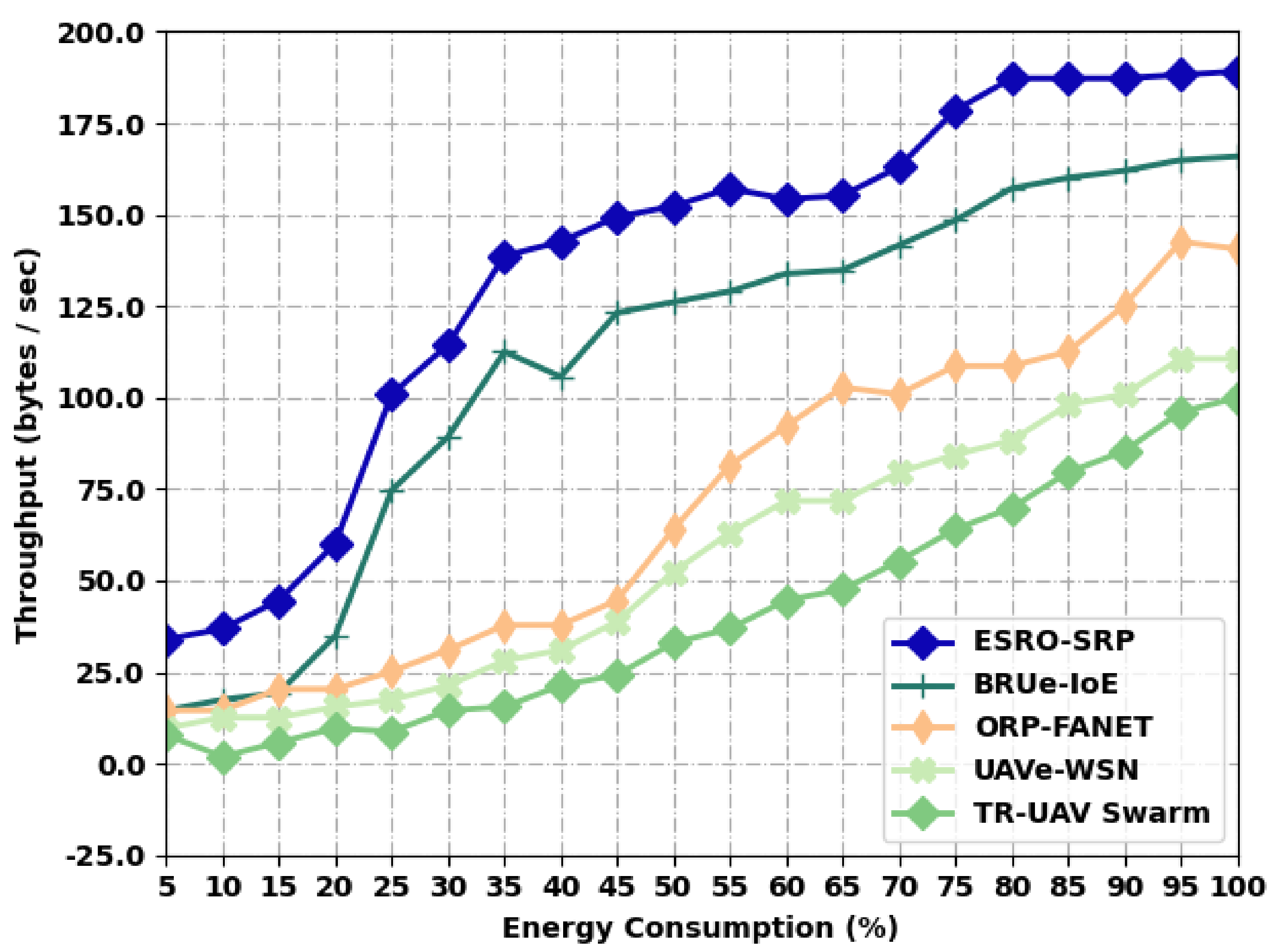
In this section, the performance validation of the ESRO-SRP model is examined under distinct levels of energy consumption (EC). The EC is varied from 5% to 100% with a step size of 5%. Table 1 and Figure 2 report a comparative throughput (THRP) inspection of the ESRO-SRP model with recent models under distinct levels of energy [22,23,24,25]. The results portrayed that the ESRO-SRP model has accomplished maximum values of THRP under all energy levels. For instance, with an EC of 5%, the ESRO-SRP model has provided an increased THRP of 33.95 bytes/s, whereas the BRUe-IoE, ORP-FANET, UAVe-WSN, and TR-UAV Swarm models have accomplished a reduced THRP of 14.54 bytes/s, 14.54 bytes/s, 9.69 bytes/s, and 7.75 bytes/s, respectively. Moreover, with an EC of 100%, the ESRO-SRP system has offered a maximal THRP of 189.20 bytes/s, whereas the BRUe-IoE, ORP-FANET, UAVe-WSN, and TR-UAV Swarm techniques have accomplished a lower THRP of 165.91 bytes/s, 140.68 bytes/s, 110.60 bytes/s, and 99.93 bytes/s, respectively.

Table 1.
Throughput analysis of ESRO-SRP technique with existing algorithms under distinct levels of energy.
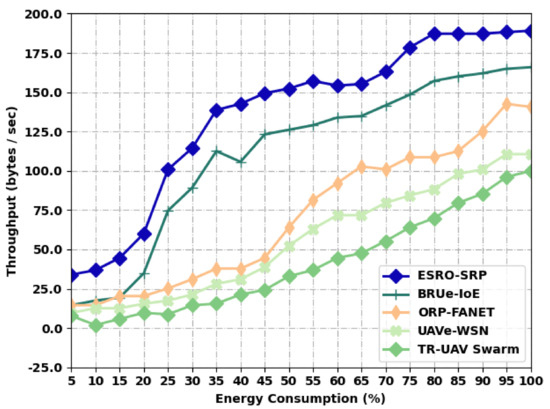
Figure 2.
Throughput analysis of ESRO-SRP technique under distinct levels of energy.
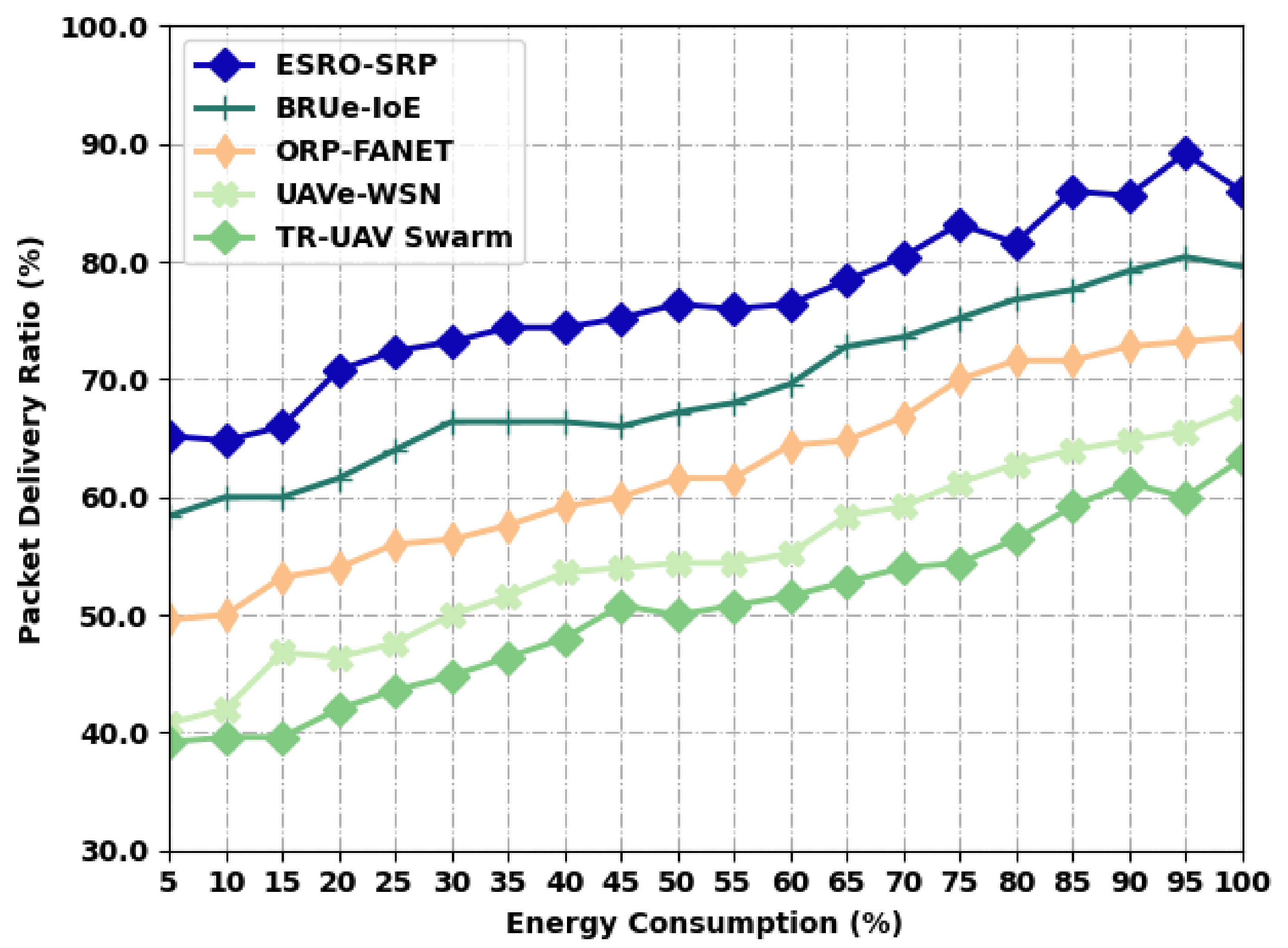
Table 2 and Figure 3 define a comparative PDR examination of the ESRO-SRP approach with recent models under distinct levels of energy. The results exposed that the ESRO-SRP model has accomplished maximal values of PDR under all energy levels. For example, with an EC of 5%, the ESRO-SRP model has provided an increased PDR of 65.20%, whereas the BRUe-IoE, ORP-FANET, UAVe-WSN, and TR-UAV Swarm systems have accomplished a decreased PDR of 58.40%, 49.60%, 40.80%, and 39.20%, respectively. Additionally, with an EC of 100%, the ESRO-SRP model has provided an increased PDR of 86%, whereas the BRUe-IoE, ORP-FANET, UAVe-WSN, and TR-UAV Swarm approaches have accomplished a minimal PDR of 79.60%, 73.60%, 67.60%, and 63.20%, respectively.

Table 2.
PDR analysis of ESRO-SRP technique with existing algorithms under distinct levels of energy.
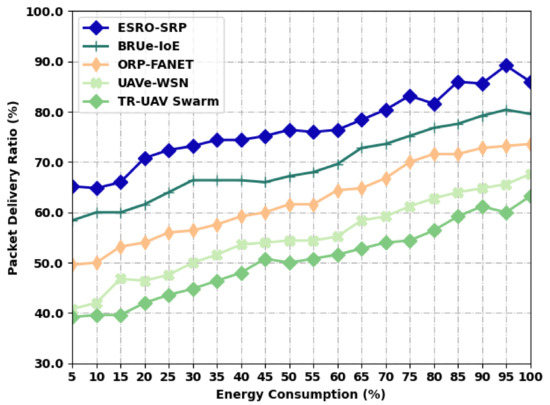
Figure 3.
PDR analysis of ESRO-SRP technique under distinct levels of energy.
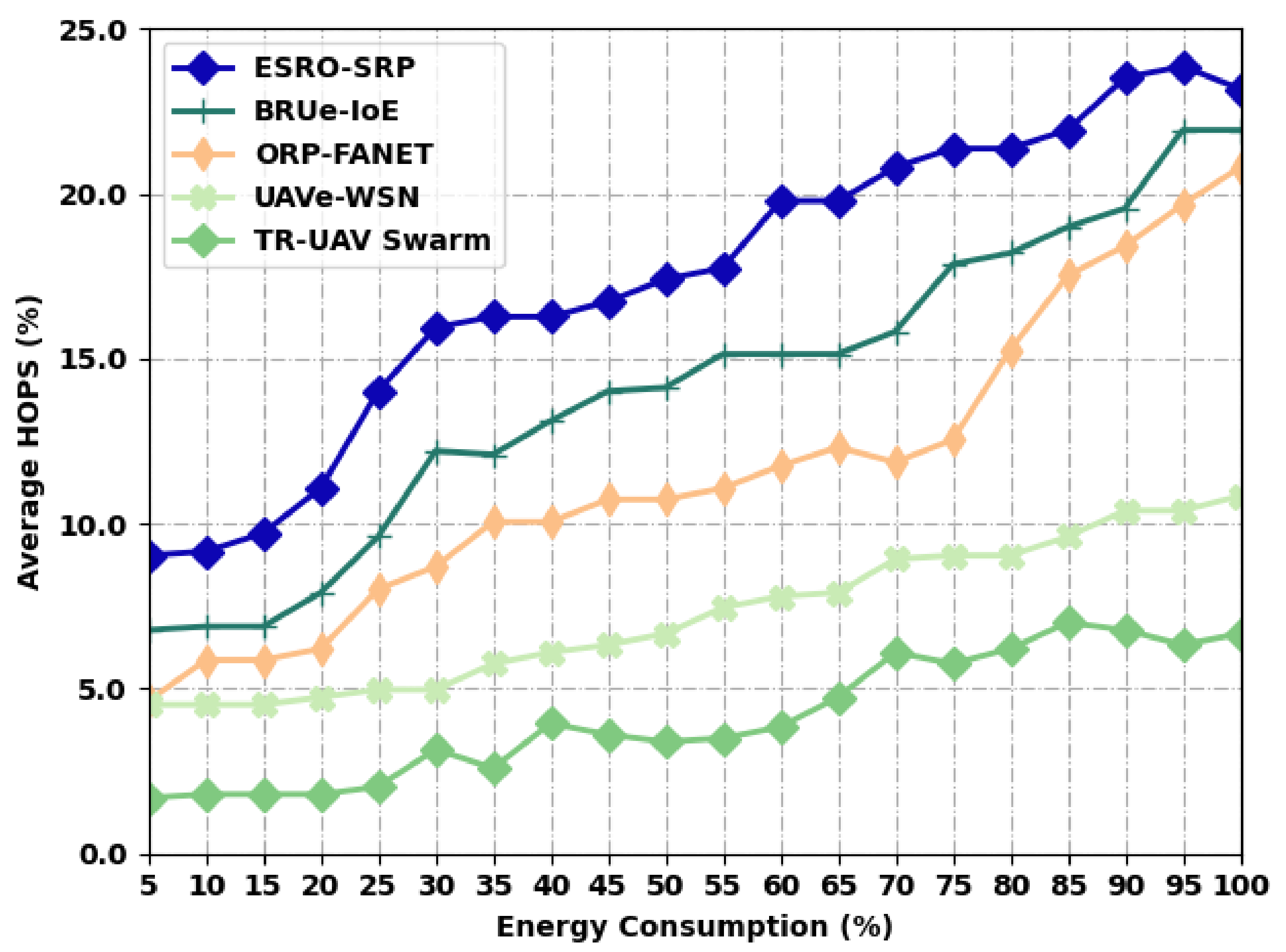
Table 3 and Figure 4 demonstrate a comparative average HOPS (AHOPS) analysis of the ESRO-SRP system with recent models under distinct levels of energy. The results depicted that the ESRO-SRP approach has accomplished higher AHOPS values under all energy levels. For instance, with an EC of 5%, the ESRO-SRP model has provided an increased AHOPS of 9%, whereas the BRUe-IoE, ORP-FANET, UAVe-WSN, and TR-UAV Swarm algorithms have accomplished a minimal AHOPS of 7%, 5%, 5%, and 2%, respectively. Finally, with an EC of 100%, the ESRO-SRP model has offered superior AHOPS of 23%, whereas the BRUe-IoE, ORP-FANET, UAVe-WSN, and TR-UAV Swarm methodologies have accomplished a lower AHOPS of 22%, 21%, 11%, and 7% correspondingly.

Table 3.
Average HOPS analysis of ESRO-SRP technique with existing algorithms under distinct levels of energy.
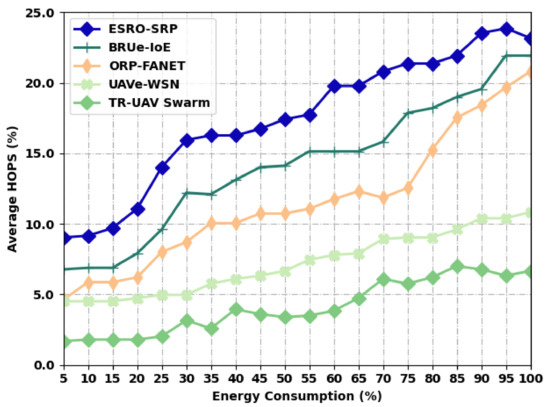
Figure 4.
AHOPS analysis of ESRO-SRP technique under distinct levels of energy.
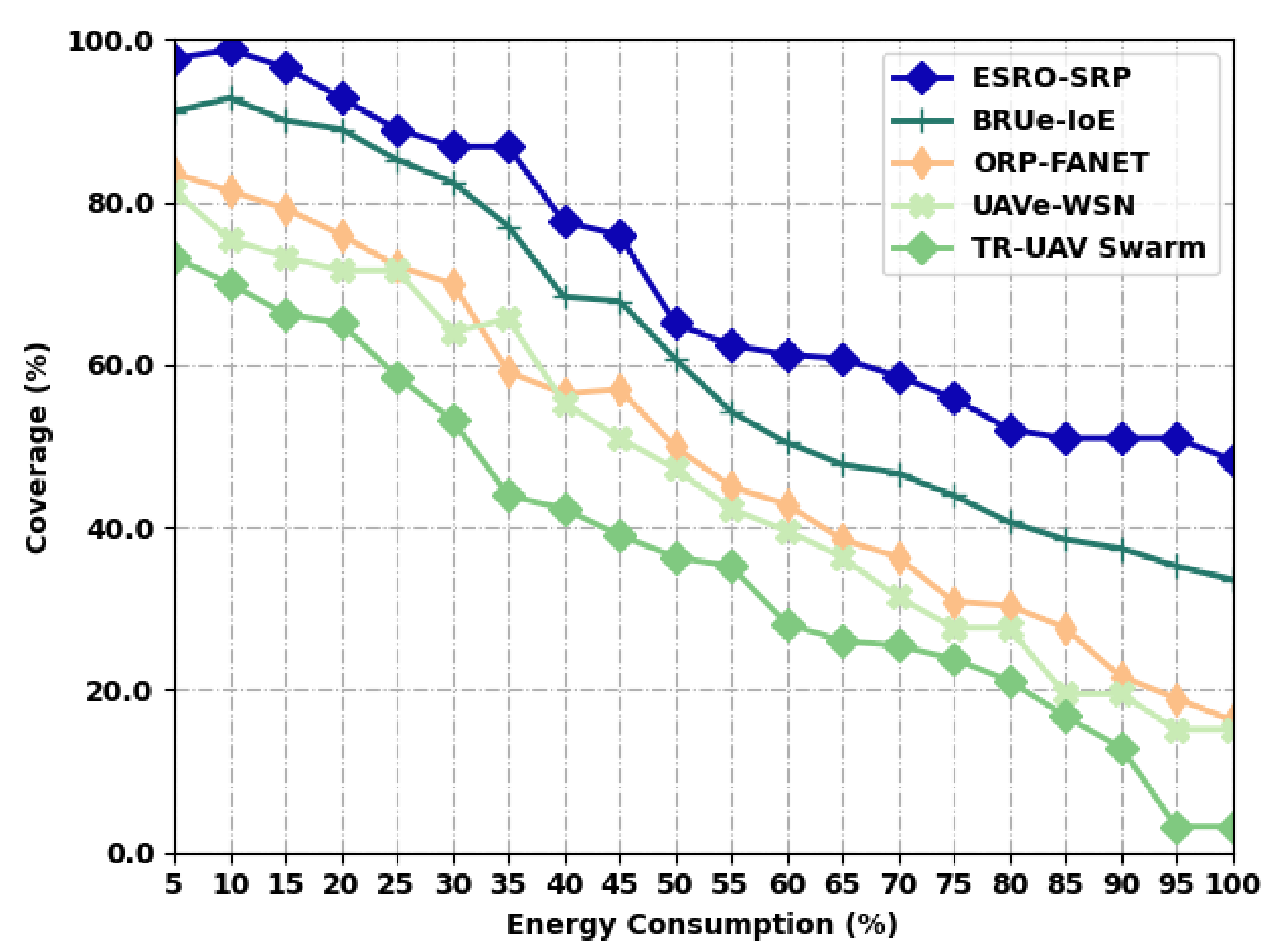
Table 4 and Figure 5 illustrate a comparative coverage inspection of the ESRO-SRP approach with recent models under distinct levels of energy. The outcomes represented that the ESRO-SRP model has accomplished improved values of coverage under all energy levels. For instance, with an EC of 5%, the ESRO-SRP model has provided a maximal coverage of 97.69%, whereas the BRUe-IoE, ORP-FANET, UAVe-WSN, and TR-UAV Swarm methods have accomplished a decreased coverage of 91.18%, 83.58%, 81.41%, and 73.26%, respectively. Finally, with an EC of 100%, the ESRO-SRP model has provided an enhanced coverage of 48.29%, whereas the BRUe-IoE, ORP-FANET, UAVe-WSN, and TR-UAV Swarm models have accomplished minimal coverage of 33.63%, 16.26%, 15.18%, and 3.24%, respectively.

Table 4.
Coverage analysis of ESRO-SRP technique with existing algorithms under distinct levels of energy.
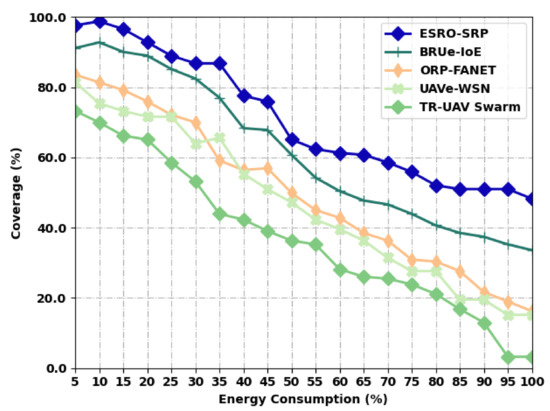
Figure 5.
Coverage analysis of ESRO-SRP technique under distinct levels of energy.
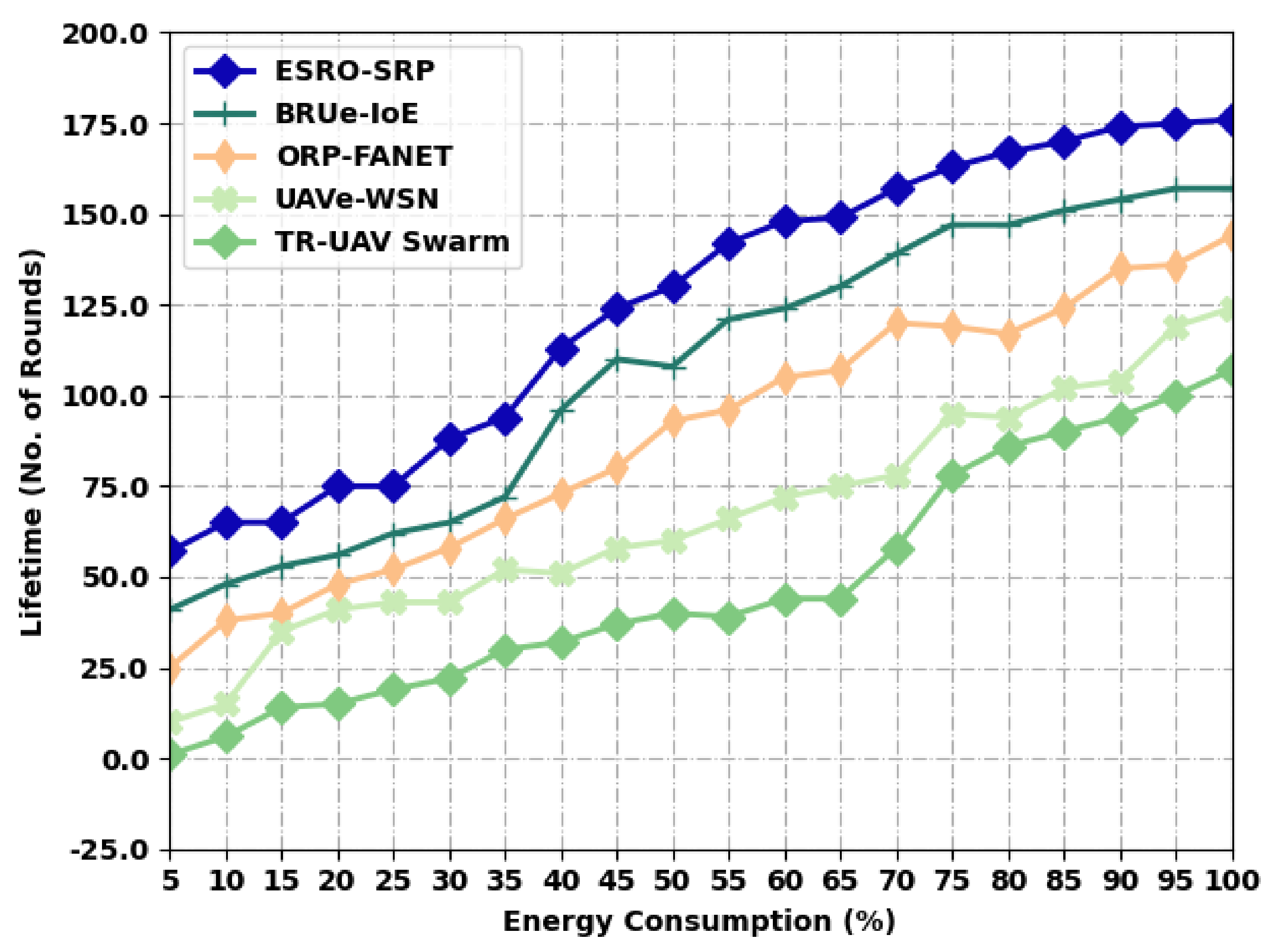
Table 5 and Figure 6 depict a comparative lifetime analysis of the ESRO-SRP algorithm with recent methodologies under distinct levels of energy. The results outperformed in that the ESRO-SRP model has accomplished maximum values of a lifetime under all energy levels. For instance, with an EC of 5, the ESRO-SRP system has provided a higher lifetime of 57 rounds, whereas the BRUe-IoE, ORP-FANET, UAVe-WSN, and TR-UAV Swarm algorithms have accomplished a minimal lifetime of 41, 25, 10, and 1 round, respectively. Moreover, with an EC of 100, the ESRO-SRP model has an obtainable increased lifetime of 176 rounds, whereas the BRUe-IoE, ORP-FANET, UAVe-WSN, and TR-UAV Swarm approaches have accomplished a decreased lifetime of 157, 144, 124, and 107 rounds, respectively.

Table 5.
Lifetime analysis of ESRO-SRP technique with existing algorithms under distinct levels of energy.
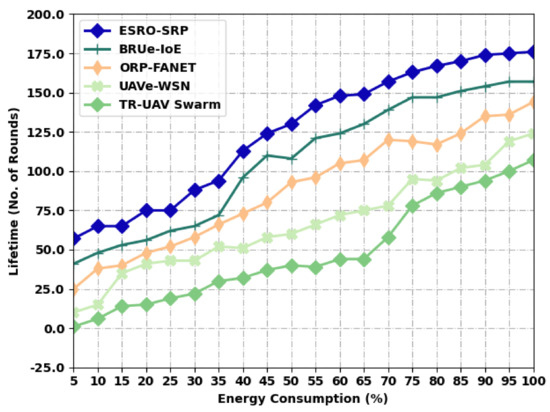
Figure 6.
Lifetime analysis of ESRO-SRP technique under distinct levels of energy.
The experimental results ensured the superior outcomes of the proposed model over other models in the IoD environment.
4. Conclusions
In this study, a novel ESRO-SRP technique was established for secure communication among the drones in the IoD environment. The presented ESRO-SRP technique mainly aims to derive a set of optimal routes to the destination. In addition, the ESRO-SRP algorithm is derived by the integration of the QOBL concept with the conventional SRO algorithm. Moreover, the presented ESRO-SRP technique derived a fitness function encompassing different input parameters such as RE, distance, and trust degree. The experimental validation of the ESRO-SRP technique is carried out under several aspects, and the results demonstrated the enhancements of the ESRO-SRP model over recent approaches. The ESRO-SRP model has provided an increased PDR of 86%, whereas the BRUe-IoE, ORP-FANET, UAVe-WSN, and TR-UAV Swarm approaches have accomplished a minimal PDR of 79.60%, 73.60%, 67.60%, and 63.20%, respectively. Therefore, the ESRO-SRP technique can be exploited as an effective tool to improve security and network efficiency. In the future, the performance of the ESRO-SRP algorithm will be extended to the integration of lightweight cryptographic techniques.
Author Contributions
Conceptualization, S.D. and F.S.A.; methodology, J.S.A.; software, I.Y.; validation, F.S.A., J.S.A. and A.M.; formal analysis, A.S.M.; investigation, A.A.A.; resources, M.A.D.; data curation, A.M.; writing—original draft preparation, F.S.A., J.S.A. and M.A.D.; writing—review and editing, S.D. and A.S.M.; visualization, I.Y.; supervision, J.S.A.; project administration, M.A.D.; funding acquisition, F.S.A. All authors have read and agreed to the published version of the manuscript.
Funding
The authors extend their appreciation to the Deanship of Scientific Research at King Khalid University for funding this work through the Large Groups Project under grant number (142/43). Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2022R319), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia. The authors would like to thank the Deanship of Scientific Research at Umm Al-Qura University for supporting this work by Grant Code: (22UQU4340237DSR31).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data sharing is not applicable to this article as no datasets were generated during the current study.
Conflicts of Interest
The authors declare that they have no conflict of interest. The manuscript was written through contributions of all authors. All authors have given approval to the final version of the manuscript.
References
- Singh, M.; Aujla, G.S.; Bali, R.S. A Deep Learning-Based Blockchain Mechanism for Secure Internet of Drones Environment. IEEE Trans. Intell. Transport. Syst. 2021, 22, 4404–4413. [Google Scholar] [CrossRef]
- Lin, C.; He, D.; Kumar, N.; Choo, K.-K.R.; Vinel, A.; Huang, X. Security and Privacy for the Internet of Drones: Challenges and Solutions. IEEE Commun. Mag. 2018, 56, 64–69. [Google Scholar] [CrossRef]
- Alsamhi, S.H.; Ma, O.; Ansari, M.S.; Almalki, F.A. Survey on Collaborative Smart Drones and Internet of Things for Improving Smartness of Smart Cities. IEEE Access 2019, 7, 128125–128152. [Google Scholar] [CrossRef]
- Chatterjee, S.; Perumalla, S.; Siva Kumar, A.P. Design and Implementation of Novel Secure User Authentication System over Internet of Drones. Int. J. Syst. Syst. Eng. 2021, 11, 105–120. [Google Scholar] [CrossRef]
- Putranto, D.S.C.; Aji, A.K.; Wahyudono, B. Design and Implementation of Secure Transmission on Internet of Drones. In Proceedings of the 2019 IEEE 6th Asian Conference on Defence Technology (ACDT), Bali, Indonesia, 13–15 November 2019; pp. 128–135. [Google Scholar] [CrossRef]
- Al-Wesabi, F.N.; Obayya, M.; Hamza, M.A.; Alzahrani, J.S.; Gupta, D.; Kumar, S. Energy Aware Resource Optimization using Unified Metaheuristic Optimization Algorithm Allocation for Cloud Computing Environment. Sustain. Comput. Informatics Syst. 2022, 35, 100686. [Google Scholar] [CrossRef]
- Fitwi, H.; Nagothu, D.; Chen, Y.; Blasch, E. A Distributed Agent-Based Framework for a Constellation of Drones in a Military Operation. In Proceedings of the 2019 Winter Simulation Conference (WSC), National Harbor, MD, USA, 8–11 December 2019; pp. 2548–2559. [Google Scholar] [CrossRef]
- Abunadi, I.; Althobaiti, M.M.; Al-Wesabi, F.N.; Hilal, A.M.; Medani, M.; Hamza, M.A.; Rizwanullah, M.; Zamani, A.S. Federated Learning with Blockchain Assisted Image Classification for Clustered UAV Networks. Comput. Mater. Contin. 2022, 72, 1195–1212. [Google Scholar] [CrossRef]
- Sirohi, P.; Al-Wesabi, F.N.; Alshahrani, H.M.; Maheshwari, P.; Agarwal, A.; Dewangan, B.K.; Hilal, A.M.; Choudhury, T. Energy-Efficient Cloud Service Selection and Recommendation Based on QoS for Sustainable Smart Cities. Appl. Sci. 2021, 11, 9394. [Google Scholar] [CrossRef]
- Alrowais, F.; Almasoud, A.S.; Marzouk, R.; Al-Wesabi, F.N.; Hilal, A.M.; Rizwanullah, M.; Motwakel, A.; Yaseen, I. Artificial Intelligence Based Data Offloading Technique for Secure MEC Systems. Comput. Mater. Contin. 2022, 72, 2783–2795. [Google Scholar] [CrossRef]
- Singh, M.; Aujla, G.S.; Bali, R.S. ODOB: One Drone One Block-based Lightweight Blockchain Architecture for Internet of Drones. In Proceedings of the IEEE INFOCOM 2020—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 6–9 July 2020; pp. 249–254. [Google Scholar] [CrossRef]
- Guerber, C.; Royer, M.; Larrieu, N. Machine Learning and Software Defined Network to secure communications in a swarm of drones. J. Inf. Secur. Appl. 2021, 61, 102940. [Google Scholar] [CrossRef]
- Kuzmin, A.; Znak, E. Blockchain-base structures for a secure and operate network of semi-autonomous Unmanned Aerial Vehicles. In Proceedings of the 2018 IEEE International Conference on Service Operations and Logistics, and Informatics (SOLI), Singapore, 31 July–2 August 2018; pp. 32–37. [Google Scholar] [CrossRef]
- Ravi, N.; Chitanvis, R.; El-Sharkawy, M. Applications of Drones using Wireless Sensor Networks. In Proceedings of the 2019 IEEE National Aerospace and Electronics Conference (NAECON), Dayton, OH, USA, 15–19 July 2019; pp. 513–518. [Google Scholar] [CrossRef]
- Tian, Y.; Yuan, J.; Song, H. Efficient privacy-preserving authentication framework for edge-assisted Internet of Drones. J. Inf. Secur. Appl. 2019, 48, 102354. [Google Scholar] [CrossRef]
- Allouch, A.; Cheikhrouhou, O.; Koubâa, A.; Toumi, K.; Khalgui, M.; Gia, T.N. UTM-Chain: Blockchain-Based Secure Unmanned Traffic Management for Internet of Drones. Sensors 2021, 21, 3049. [Google Scholar] [CrossRef] [PubMed]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V.; Rodrigues, J.J.P.C. Design and Analysis of Secure Lightweight Remote User Authentication and Key Agreement Scheme in Internet of Drones Deployment. IEEE Internet Things J. 2018, 6, 3572–3584. [Google Scholar] [CrossRef]
- Gorrepati, R.R.; Guntur, S.R. DroneMap: An IoT Network Security in Internet of Drones. In Development and Future of Internet of Drones (IoD): Insights, Trends and Road Ahead; Springer: Cham, Switzerland, 2021; pp. 251–268. [Google Scholar] [CrossRef]
- Jain, D.K.; Tyagi, S.K.S.; Neelakandan, S.; Prakash, M.; Natrayan, L. Metaheuristic Optimization-Based Resource Allocation Technique for Cybertwin-Driven 6G on IoE Environment. IEEE Trans. Ind. Inform. 2021, 18, 4884–4892. [Google Scholar] [CrossRef]
- Goswami, P.; Mukherjee, A.; Maiti, M.; Tyagi, S.K.S.; Yang, L. A Neural-Network-Based Optimal Resource Allocation Method for Secure IIoT Network. IEEE Internet Things J. 2021, 9, 2538–2544. [Google Scholar] [CrossRef]
- Padmaa, M.; Jayasankar, T.; Venkatraman, S.; Dutta, A.K.; Gupta, D.; Shamshirband, S.; Rodrigues, J.J. Oppositional chaos game optimization based clustering with trust based data transmission protocol for intelligent IoT edge systems. J. Parallel Distrib. Comput. 2022, 164, 142–151. [Google Scholar] [CrossRef]
- Ahmad, M.; Ullah, F.; Wahid, I.; Khan, A.; Uddin, M.I.; Alharbi, A.; Alosaimi, W. A Bio-inspired Routing Optimization in UAV-enabled Internet of Everything. Comput. Mater. Contin. 2021, 67, 321–336. [Google Scholar] [CrossRef]
- Liu, B.; Zhang, W.; Chen, W.; Huang, H.; Guo, S. Online computation ofoading and trafc routing for UAV swarms in edge-cloud computing. IEEE Trans. Veh. Technol. 2020, 69, 8777–8791. [Google Scholar] [CrossRef]
- Baek, J.; Han, S.I.; Han, Y. Energy-efficient UAV routing for wireless sensor networks. IEEE Trans. Veh. Technol. 2020, 69, 1741–1750. [Google Scholar] [CrossRef]
- Yang, H.; Liu, Z. An optimization routing Protocol for FANETs. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 2–8. [Google Scholar] [CrossRef] [Green Version]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).