Abstract
The problem analyzed in this paper deals with the classification of Internet traffic. During the last years, this problem has experienced a new hype, as classification of Internet traffic has become essential to perform advanced network management. As a result, many different methods based on classical Machine Learning and Deep Learning have been proposed. Despite the success achieved by these techniques, existing methods are lacking because they provide a classification output that does not help practitioners with any information regarding the criteria that have been taken to the given classification or what information in the input data makes them arrive at their decisions. To overcome these limitations, in this paper we focus on an “explainable” method for traffic classification able to provide the practitioners with information about the classification output. More specifically, our proposed solution is based on a multi-objective evolutionary fuzzy classifier (MOEFC), which offers a good trade-off between accuracy and explainability of the generated classification models. The experimental results, obtained over two well-known publicly available data sets, namely, UniBS and UPC, demonstrate the effectiveness of our method.
1. Introduction
Network traffic classification represents one of the main challenges in network management nowadays. Indeed, Internet Service Providers (ISPs) devote most of their efforts to Internet traffic classification and management. Historically, the Internet traffic classification task was performed primarily for security reasons, as it permits the detection and identification of intrusions and malicious behavior. However, over recent years, the identification of Internet traffic type and workload has become necessary not only for security purposes, but also to perform traffic engineering and to make decisions on policing, traffic shaping, billing, dynamic Quality of Service, and so on. Most of the management techniques are built on top of classification results: as an example, consider billing and accounting, which are only possible if the traffic is first correctly classified. Moreover, attack detection techniques are usually built on top of a traffic classifier. Nonetheless, despite many years of research on the topic, an ultimate solution able to provide “good enough” performance is still under study.
In the literature, several approaches have been proposed to classify IP traffic flows according to the application that generated the traffic. Historically, the most commonly used method is to associate the observed traffic (using flow level data or a packet sniffer) with an application, on the basis of TCP or UDP port numbers [1]. However, port-based classification is inadequate [2], as mapping between ports and applications is not always well defined. As a consequence, in the last decade, research efforts have moved towards classification tools based on Machine Learning (ML) and Artificial Intelligence (AI) algorithms, which rely on statistical features [3].
Among these, Support Vector Machine (SVM) [4] and deep learning techniques [5] have emerged as powerful tools for traffic classification and other network application, such as intrusion detection [6] and other cyber security application [7,8]. Indeed, these techniques, and especially SVM, represent an almost de facto standard in the field. Such methods are able to provide very high accuracy values, often just observing a few traffic statistics computed over the first packets of each flow.
Nonetheless, all of the methods based on machine learning algorithms present a common drawback, as the generated models are seen as black boxes characterized by a low “explainability” level. Indeed, the classification result does not provide the practitioners with any information regarding the criteria that have taken to the given classification, or what information in the input data makes them arrive at their decisions. This is usually justified by the fact that the main goal traditionally pursued is to make the model matching reality (i.e., accurate models), without actually caring for explainable models.
Nowadays, several new requirements have emerged related to fairness or unbiasedness, privacy, reliability, robustness, causality, and/or trust posing the need of deploying systems that must provide explanations for the taken decisions, where necessary [9]. Therefore, traffic classifiers, as well as other traffic analysis systems, must be optimized not only for accuracy but also for the other criteria previously listed.
In such a context, a lot of research efforts are nowadays focusing on “explainable” methods (e.g., explainable artificial intelligence), where explainability “encompasses ML/AI systems for opening black box models, for improving the understanding of what the models have learned and/or for explaining individual predictions” [9]. In this specific area, a recent work in [10] clearly indicates that exploiting the synergy between Fuzzy Rule-Based Systems (FRBSs) and Evolutionary Algorithms is one of the most straightforward ways of combining accuracy and interpretability/explainability in machine learning-based tools.
For such a reason, in this work, which significantly extends the preliminary results presented in [11], we propose a traffic classification approach based on multi-objective evolutionary fuzzy classifiers (MOEFCs) [12,13]. Specifically, MOEFCs deal with the application of Multi-Objective Evolutionary Algorithms (MOEAs) [14] for generating a collection of Fuzzy Rule-Based Classifiers (FRBCs) characterized by different trade-offs between their accuracy and their explainability level [15]. We recall that FRBCs adopt (i) a rule base composed of linguistic IF-THEN rules and (ii) a database which contains the description of the linguistic terms adopted for the fuzzy discretization of each input variable. A specific inference mechanism is adopted for taking a decision whenever a new input is presented to the system.
In this contribution, we exploit the PAES-RCS algorithm, in which the accuracy is calculated in terms of percentage of correctly classified flows of internet traffic. As regards the explainability level, it is calculated in terms of total rule length (TRL), namely, the total number of conditions taken into consideration in the whole rule base. Low values of TRL are associated with rule bases which contain a reduced number of simple rules (i.e., rules in which a low number of conditions are adopted in their antecedent). Note that PAES-RCS has been successfully exploited in a number of recent contributions on real-world applications [15,16].
To evaluate and validate the proposed approach, we have used two publicly available data sets, namely, UniBS and UPC, showing that our system can achieve nearly optimal performance, while simultaneously guaranteeing the explainability of the classification results. We also compared the results achieved by MOEFCs with the ones achieved by two classical ML-based classification algorithms, namely, SVM and Decision Trees. SVM algorithms have been chosen as they represent the de facto standard among machine learning algorithms commonly adopted for solving the internet traffic classification problem. However, SVM models are characterized by a very low explainability level. Regarding decision trees, as from the trees it is possible to extract a set of decision rules, they represent a category of interpretable models among classical machine learning classifiers. However, their rules are not linguistic and the final models are often described by a large number of parameters, namely, the number of nodes and leaves. Thus, also the explainability level of decision trees is often compromised. As a counterpart, the proposed approach, based on MOEFCs, generates models characterized by good trade-offs between their accuracy and their explainability.
The remainder of the paper is organized as follows. In Section 2, we discuss some notable related works, while in Section 3.1 we describe the used data sets. Then, in Section 3.2 we introduce the experimented explainable traffic classification approach. The achieved results are shown in Section 4. Finally, Section 5 concludes the paper with some final remarks and future work.
2. Related Work
Research on traffic classification has been quite prolific in the years and, as a consequence, many works have been written on the topic. Therefore, the aim of this section is not to provide the reader with a comprehensive review of the related works (for which we refer the reader to the surveys on the topic), but just to point out some works significant for our specific proposal.
Machine Learning techniques have been first applied to network traffic classification in 1994 [17] and since then many different methods have been proposed, as detailed in some recent surveys [3,18].
Among the many proposals, particular interest has been raised by classifiers based on Support Vector Machine (SVM). One of the first significant work on the application of SVM to traffic classification is [19], where the authors apply one of the approaches to solving multi-class problems with SVMs and describe a simple optimization algorithm that allows the classifier to perform correctly with as little training as a few hundred samples. Since then, many other works have proposed SVM-based methods [4,20,21,22,23] and, as a result, SVM is nowadays considered as a de facto standard in the field. Nonetheless, as already discussed, all of these works propose methods based on black-box models that do not provide any information about the classification criteria.
As far as Fuzzy Rule-Based Classifiers (FRBCs) are concerned, given their ability to deal with vague and noisy data and to explain how the classification task is performed, they have been widely exploited in several contexts, such as medical diagnosis applications [24], industrial applications [25], and Internet of Things [26]. In the years, several techniques to generate and optimize the structure of FRBCs have been proposed, often without taking into consideration how this maximization affects the FRBC explainability, but only in the last decade, researchers have also focused their attention on the explainability aspects of FRBCs [27]. As accuracy and explainability are conflicting objectives, the generation of the FRBS structure has been modeled as a multi-objective optimization problem. Multi-objective evolutionary algorithms (MOEAs) have been successfully employed to tackle this optimization problem and the term multi-objective evolutionary fuzzy systems (MOEFSs) has been coined [12,28] to identify FRBSs generated by MOEAs. Since then, many papers have proposed the use of MOEFSs in classification problems [16,29,30,31,32,33].
In the specific context of traffic classification, there are some works [34,35] that propose the use of fuzzy models. The work in [34] discusses the application of hybrid models in which fuzzy theory elements are included into a neural network architecture. As regards the contribution discussed in [35], the authors propose an approach which combines a decision trees and fuzzy membership functions for dealing with noisy and vague data. Note that both works include in their experimental analysis a comparison with the traffic classification methods based on SVM. Nonetheless, to the best of our knowledge, our work is the first to propose and evaluate in a systematic way, the application of MOEFCs to generate explainable models for network traffic classification.
3. Materials and Methods
In this section, we first describe the data sets used to evaluate and validate our study, and then we detail the proposed Traffic Classification System.
3.1. Data Sets
We have used two distinct well-known and publicly available data sets: UniBS and UPC.
3.1.1. UniBS Data Set
The UniBS data set [36] is made of traffic collected in the University of Brescia campus network during three consecutive days (from 30 September 2009 to 1 October 2009), anonymized with the Crypto-PAn tool [37]. The dataset has been employed recently in the contributions discussed in [38,39].
The data set is coupled with a log file, containing for each flow, the information
<timestamp> : <IP src> : <IP dst> :
<transport port src> : <transport port dst> :
<DPI verdict(s)> : <application name> :
<transport protocol>
In this work, we have considered the classes corresponding to the following applications: Mail, Skype, Firefox, Safari, BitTorrent, and Amule. Table 1 reports the number of instances per class, considering flows made of at least three, five, and ten packets.

Table 1.
UniBS data set: number of instances per each class.
3.1.2. UPC Data-Set
The UPC data set [40] is made from a subset (about 5.23 GB) of the full-payload traffic traces used in [41] and collected in the Universitat Politecnica de Catalunia during 66 days (from 25 February 2013 to 1 May 2013). Furthermore, these data have been recently used in the experiments on internet traffic classification carried out in [42,43].
As for the UniBS data-set, a log file accompanying the data set contains, for each flow, the information:
flow_id#start_time#end_time#local_ip
#remote_ip#local_port#remote_port
#transport_protocol#operating_system
#process_name#urls#referers#
content_types#
where process_name corresponds to the application that generated the flow.
Table 2 reports the number of instances per class, considering flows made of at least three, five, and ten packets.

Table 2.
UPC data set: number of instances per each class.
3.2. The Proposed Traffic Classification System
In the following, we detail the proposed approach for generating explainable traffic classification models. The diagram depicted in Figure 1 represents the schema of the proposed internet traffic classification system. The data (both the Training Internet Flow () and the Real-Time Internet Flow ()) are preprocessed through a Feature Extraction strategy (discussed in Section 3.2.2), which generates a representation of the data by means of the chosen features. Note that while is composed of historical data collected for training the classification model, the , in a real-world application, is continuously extracted from a network. The representation of the training data ( representation) is used by the PAES-RCS algorithm to build a collection of FRBCs, namely, a collection of XAI classification models. Each model is characterized by a specific trade-off between accuracy and explainability, therefore the final user can select the one that best satisfies her/his requirements. This model (Selected XAI Model in the figure) is then applied on the representation of the Real-Time Internet Flow ( representation) to classify it. In the following, we first focus on the description of adopted multi-objective evolutionary learning scheme for generating FRBCs. Then, we describe two different feature extraction strategies, that we have experimented as preprocessing stage of the overall traffic classification task.
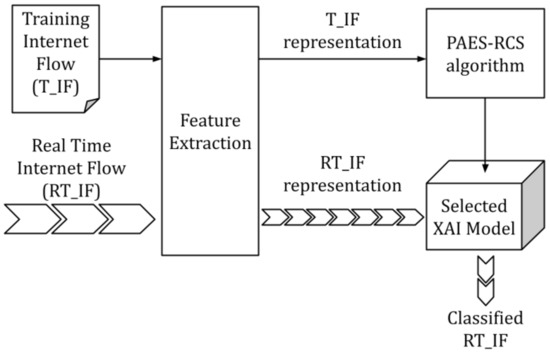
Figure 1.
Block diagram of the proposed Traffic Classification System.
3.2.1. PAES-RCS Method
Evolutionary fuzzy systems, which consist of evolutionary algorithms applied to the design of fuzzy systems, are one of the greatest advances within the area of computational intelligence.
Among these, multi-objective evolutionary fuzzy classifiers (MOEFCs) are characterized by a good trade-off between accuracy and explainability level [12,16]. Therefore, these models have been widely used for approaching classification problems. Indeed, MOEFCs deal with the design of fuzzy rule based classifiers (FRBCs) by means of multi-objective evolutionary algorithms: during the evolutionary design process, both the accuracy and the explainability level of the models are concurrently optimized. At the end of the design process, a set of classification models, characterized by different trade-offs between accuracy and interpretability (Pareto front approximation), are available for the final user that will select the most suitable solution for its problem domain. The final models are usually characterized by compact fuzzy rules, namely, linguistic IF-THEN rules, which can describe the classification process in an explainable way.
An FBRC basically includes a rule base (RB), a database (DB) containing the definition of the fuzzy sets used in the RB, and an inference engine. RB and DB comprise the knowledge base of the rule-based system.
Let be the set of input variables and be the output variable of the classifier. Let , with , being the universe of the input variable . Let be a partition of variable consisting of fuzzy sets. The output variable is a categorical variable assuming values in the set of K possible classes . Let be a training set composed of N input–output pairs, with , and .
With the aim of determining the class of a given input vector, we adopt an RB composed of M rules expressed as
where is the class label associated with the rule, and is the rule weight, i.e., a certainty degree of the classification in the class for a pattern belonging to the subspace delimited by the antecedent of rule .
Usually, a purposely defined fuzzy set () is considered for all the F input variables. This fuzzy set, which represents the “do not care” condition, is defined by a membership function equal to 1 on the overall universe. The term allows generating rules that contain only a subset of the input variables.
A specific reasoning method employs the information it receives from the RB to determine the class label for a given input pattern. We adopt the maximum matching as reasoning method (see [16] for details).
Concerning the DB, we adopted triangular fuzzy sets: each fuzzy set is identified by the tuples , where and correspond to the left and right extremes of the support, and to the core. In particular, in the experiments, we use strong fuzzy partitions, where and, for , and . In Figure 2, we show an example of a strong fuzzy partition composed by three triangular fuzzy sets.
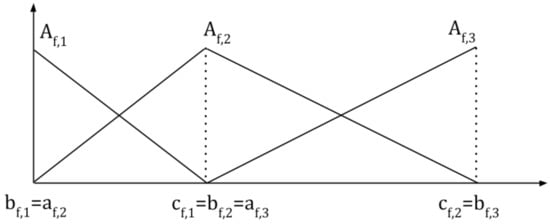
Figure 2.
An example of a strong fuzzy partition.
In order to concurrently design the RB and tune the parameters of the fuzzy sets, we adopt the PAES-RCS algorithm introduced in [44]. The multi-objective evolutionary learning scheme is based on the (2 + 2)M-PAES, which is an MOEA successfully employed in the context of MOEFSs during the last years. We concurrently optimize two objectives: the first objective considers the interpretability of the RB, calculated as the total rule length (TRL), that is, the number of propositions used in the antecedents of the rules contained in the RB; the second objective takes into account the accuracy, assessed in terms of classification rate.
In the learning scheme, we first generated an initial RB and then selected, during the evolutionary process, the most relevant rules and their conditions. Moreover, we concurrently tune the parameters of the fuzzy sets by using a mapping strategy based on a piecewise linear transformation [44]. Once we had defined an initial strong fuzzy partition for each input variable, we extracted the initial set of candidate fuzzy rules from a decision tree: in particular, in this work, we use a recent algorithm, discussed in [45], for generating multi-way fuzzy decision trees. One rule is then created for each path from the root to a leaf node.
In PAES-RCS, each solution is codified by a chromosome C composed of two parts , which define, respectively, the RB and the positions of the representatives of the fuzzy sets, namely, the cores, in the transformed space.
Let and be the initial set of candidate rules generated by the decision tree and the number of rules of this RB, respectively. In order to generate compact and interpretable RBs, we allow that the RB of a solution contains at most rules. The part, which codifies the RB, is a vector of pairs , where identifies the selected rule of and is a binary vector which indicates, for each variable , if the condition is present or not. In particular, if the rule is not included in the RB. Thus, we can generate RBs with a lower number of rules than . Further if the condition of the rule can be replaced by a “don’t care” condition.
is a vector containing F vectors of real numbers: the vector determines the positions of the fuzzy set representatives in the specific variable .
In order to generate the offspring populations, we exploit both crossover and mutation. We apply separately the one-point crossover to and the BLX--crossover, with = 0.5, to . As regards the mutation, we apply two distinct operators for and an operator for . More details regarding the mating operators and the steps of PAES-RCS can be found in [16,44].
3.2.2. Feature Extraction
The feature extraction phase has been designed and implemented so as to process real-time traffic captured by means of the pcap libraries. First of all, the traffic is reconstructed to identify the flows, defined by the 5-uple: source and destination IP addresses, source and destination ports, and protocol (note that, in this work, we consider bidirectional flows). Then, each 5-uple is transformed in a vector of features to be used as input of the FRBC, which is in charge of estimating the type of traffic.
In this work, we have experimented two distinct typologies of traffic features:
- Statistical features: the flow is described by a set of statistical values (namely 21), reported in Table 3.
 Table 3. Statistical features.It is important to highlight that in this work, such features have only been computed for flows made of five or more packets.
Table 3. Statistical features.It is important to highlight that in this work, such features have only been computed for flows made of five or more packets. - Composite features: the flow is described by an array , where H is the number of analyzed flow packets, of higher granularity (i.e., packet level) features [34]:where
- -
- with is the direction of the packet
- -
- with is the dimension in Byte of the packet, normalized with respect to
- -
- with is the time in seconds between packet i and packet
Clearly, such features depend on the parameter H and can only be computed for those flows made of at least H packets. In the experimental results, we will consider .
4. Experimental Results
In this section, we present the results of the experimental tests, carried out to validate and evaluate our proposal. The performance have been measured in terms of the following metrics (defined per class):
- True Positive Rate
- False Positive Rate
- Accuracy
In the previous formulas, , , , and , respectively, represent the number of true positives, of true negatives, of false positives, and of false negatives. Moreover, for some significant cases (for sake of brevity not for all the cases), the confusion matrix is also reported.
Note that in all the tests, we have adopted a k-fold cross-validation approach, with .
In the following, to allow a proper comparison of our system against state-of-the-art classifiers, we present, at first, the performance achieved by SVM and C4.5 decision tree, used as benchmarks, and then the results obtained by our system.
4.1. SVM Classifier
As far as the SVM classifier is concerned, we have used the implementation available in WEKA Toolkit (https://www.cs.waikato.ac.nz/ml/weka/ accessed on 20 May 2021) based on the Sequential Minimal Optimization training algorithm [46]. The parameters of the algorithm have been set as
In Table 4, we show the achieved accuracy on both datasets and for each feature extraction method. Moreover, Table 5 and Table 6 show the results in terms of and for each class of the UniBS and UPC data sets, respectively.

Table 4.
Accuracy achieved by the support vector machine (SVM) classifier.

Table 5.
SVM: TPR and FPR over UniBS data set.

Table 6.
SVM: TPR and FPR over UPC data set.
Regarding the accuracy, the best performance is achieved, for both datasets, adopting composite features and ( over the UPC data set and over the UniBS data set). In both cases, adopting statistical features, the SVM classifier achieves better performances rather than adopting composite features with , and even with in the case of UniBS data set.
Finally, for a deeper analysis, Table 7 reports the confusion matrix for the UniBS case with composite features and (note that for sake of brevity we do not show the confusion matrix for all the cases, as they would not add any significant insight). Note that, for the considered case, the worst results are obtained for Skype, which is often classified as Amule. Such a result can be justified by the fact that the two applications have a similar architecture.

Table 7.
SVM: confusion matrix (UniBS, composite—).
4.2. C4.5 Decision Tree
The C4.5 decision tree has been taken into consideration because of the partly explainability of the results. Indeed, depending on the dimension of the tree and on the number of leaves, the classification results can be accompanied by an analysis of the criteria that take to a given decision. In this work, we have used the J48 classifier available in WEKA toolkit. As regards the parameters of the decision tree, we used the default parameters suggested in WEKA. In particular, the pruning of the decision tree is activated with a confidence parameter value of 0.25. In addition, the minimum number of instances per leaf is set equal to 2.
Similarly to the UniBS case, Table 8 shows the achieved overall performance, while Table 9 and Table 10 report the results in terms of and for each class of the UniBS and UPC data sets, respectively.

Table 8.
Performance achieved by the C4.5 classifier.

Table 9.
C4.5: Performance over UniBS data set.

Table 10.
C4.5: Performance over UPC data set.
Note that in this case, the best accuracy is obtained in both cases with the statistical features ( over the UPC data set and over the UniBS data set). Furthermore, differently from the SVM case, we can notice that the C4.5 does not present any critical result in terms of almost always unrecognized classes.
For allowing a deeper analysis of the achieved results, in Table 11 we report the confusion matrix for the UPC data set and statistical features. Note that the C4.5 offers almost optimal results over all the classes in this case. Indeed, the only misclassifications occur with the most similar classes, that is when considering Chrome and Firefox.

Table 11.
C45: confusion matrix (UPC, statistical).
4.3. PAES-RCS
As for the previous cases, and also for the proposed method, we have run a 5-fold cross-validation, and for each fold we have run three trials (each with a different seed of the random number generator). The algorithm has been run with the parameters indicated in Table 12, and for each fold and each trial we have generated an approximation of the optimal Pareto front. In the following, we report the average results of three representative solutions ordered according to decreasing accuracy. Specifically, as discussed in [44], we sorted the FRBCs in each Pareto front approximation in ascending order of accuracy. Then, we extracted the First (the most accurate and the less explainable), the Median, and the Last solution (the less accurate and the most explainable).

Table 12.
Values of the parameters for PAES-RCS used in the experiments.
Similarly to what done so far, in Table 13 and Table 14 we present the overall performance over the UniBS and the UPC data-set, respectively, in terms of accuracy, number of rules , and total rule length . From the tables we can see that out system is able to achieve nearly optimal results, with an accuracy close to in both the cases.

Table 13.
Performance achieved by the proposed classifier over the UniBS data set.

Table 14.
Performance achieved by the proposed classifier over the UPC data set.
Then, in Table 15 and Table 16, we present the results in terms of and for each class on the UniBS and UPC data sets, respectively. Note that, apart with composite feature and , there is not any class that is mostly unrecognized (as for the SVM classifier). Moreover, it is also interesting to see that, differently from the C4.5 classifier, the proposed method is able to correctly classify Chrome, while it presents some issues in the classification of Firefox.

Table 15.
Proposed method: Performance over UniBS data set.

Table 16.
Proposed method: Performance over UPC data set.
For a deeper analysis, Table 17 and Table 18 report the confusion matrix for the UniBS and UPC case with statistical features, respectively. As expected, these results highlight that, in the UPC case, the most critical case is represented by Firefox, which is often classified as Chrome.

Table 17.
Proposed method: confusion matrix (UniBS, statistical).

Table 18.
Proposed method: confusion matrix (UPC, statistical).
4.4. Comparison among the Different Classification Models
To easily compare the achieved results, Table 19 reports the best results, in terms of accuracy, per each classifier on the two considered data sets, both for the training set and the test set, respectively.

Table 19.
Performance comparison: Accuracy (for the PAES-RCS algorithm the First solution has been considered).
Starting by comparing the performance of our method with those of SVM on the test set, it is easy to see that our method achieves more or less the same accuracy than SVM, with a maximum accuracy of 0.875 (against 0.874) on the UniBS data set, and 0.886 (against 0.896) over the UPC data set. On the contrary, considering again the test set, our method is outperformed, in terms of accuracy, by C4.5 over both the data sets.
Similar results are obtained on the training set. Nevertheless, in this case, note that the overfitting is very high for the SVM algorithm. Furthermore, the decision tree and the proposed PAES-RCS algorithms suffer from this problem, but in this case the phenomenon is less evident.
Nonetheless, as already discussed, our method is characterized by a high level of explainability. To quantify such an aspect, in Table 20 we report the complexity of our method (in terms of number of rules and TRL) and of the C4.5 algorithm (in terms of number of leaves and tree dimension). Note that we do not take into consideration SVM in this analysis, as it is well known that SVM must be considered as a “black box”.

Table 20.
Performance comparison: Complexity (for the PAES-RCS algorithm the First solution has been considered).
As it can be observed from the table, the higher accuracy of C4.5 is paid with a much higher complexity, which directly results in a lower explainability. Note that as far as complexity is concerned, that for our proposed method we have considered the “First” case, which has a much higher complexity, but an only slightly better accuracy, with respect to the “Median” case. Therefore, out method results even more convenient, considering the “Median” case.
To further clarify the level of explainability of the proposed method, we finally analyze some examples of classification rules (created for the UniBS data-set). In Figure 3, we show a generic strong fuzzy partition that has been used for each variable in the experiment. The fuzzy partition consists of seven fuzzy sets, labeled with linguistic values ranging from Very Low (VL) to Very High (VH).
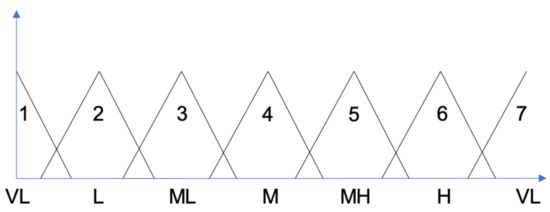
Figure 3.
The fuzzy partition adopted in the experiments.
Given such fuzzy sets, the following are a few examples of classification rules:
- R1: IF f_Sµ is VL THEN Y is Skype
- R2: IF f_N is L THEN Y is Amule
- R3: IF r_SM is H AND r_TM is M THEN Y is Mail
- R4: IF f_N is H AND f_V is VH AND r_V is H AND r_Sm is L AND f_SM is F ML AND r_SM is H AND r_Sµ is H AND f_Sσ is VH AND r_Sσ is VH AND f_TM is H THEN Y is Mail
It is clear, that such rules, being linguistic rules, can be easily read and understood by an operator.
For the sake of completeness, we highlight that both UniBS and UPC are data sets that exhibit some level of imbalance. Therefore, we have applied a set of re-balancing techniques, but the obtained results did not show appreciable improvements. This is probably due to the fact that the level of unbalancing is not very high. Indeed, as can be seen from the tables and the confusion matrices discussed above, we have verified that poor results on specific classes are not due to the imbalance level but rather to the adopted feature extraction procedure and/or to classification model selected. Due to space reasons and to their scarce relevance, we have not reported all the results achieved adopting a re-balancing step of the training set.
5. Conclusions and Future Work
The development of “explainable” classification methods is attracting a lot of research efforts in several fields, such as network monitoring. This is highly justified by the newly emerged requirements in terms of fairness or unbiasedness, privacy, reliability, robustness, causality, and/or trust, which make the standard methods inadequate. For this reason, in this paper, we have proposed a traffic classification tool based on multi-objective evolutionary fuzzy classifiers.
Our proposal has been validated and evaluated over two well-known publicly available traffic data-sets (namely, UniBS and UPC) and has demonstrated optimal performance both in term of accuracy end explainability. Indeed, the achieved results show that our method is able to outperform the de facto standard method (i.e., SVM) both in terms of accuracy and explainability. Moreover, the proposed method is also able to offer a better accuracy–explainability trade-off than C4.5 classifier, in which a very high accuracy is paid in terms of very low level of explainability.
The main limitation of the proposed approach, based on XAI models for internet traffic classification, regards the fact that it may suffer from the “concept drift issue”. Indeed, if a new set of internet applications appears in the monitored network, the system will not be able to identify it. This is due to the fact that the traffic flows associated with the new applications have never been seen by the XAI models during the training stage. This means that the models should be retrained or an incremental learning algorithm should be adopted for updating in real time the parameters of the models (i.e., the rules). This issue, not trivial at all, represents a hot research topic that will be considered in future works.
Author Contributions
Authors contributed equally to this work. All authors have read and agreed to the published version of the manuscript.
Funding
The contribution of Pietro Ducange to this work is supported by the Italian Ministry of Education and Research (MIUR), in the framework of the CrossLab project (Departments of Excellence).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data available in a publicly accessible repository, see Section 3.1.
Acknowledgments
The authors would like to thank Gianluca Alfonzo for having supported the work presented in this paper with the activities carried out in the framework of his internship in the SMARTEST Research Centre of the eCampus University, leaded by Ducange till May 2019.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Moore, D.; Keys, K.; Koga, R.; Lagache, E.; Claffy, K. CoralReef software suite as a tool for system and network administrators. In Usenix LISA; Usenix: San Diego, CA, USA, 2001; pp. 4–7. [Google Scholar]
- Roughan, M.; Sen, S.; Spatscheck, O.; Duffield, N. Class-of-service Mapping for QoS: A Statistical Signature-based Approach to IP Traffic Classification. In Proceedings of the 4th ACM SIGCOMM Conference on Internet Measurement, IMC ’04, Taormina Sicily, Italy, 25–27 October 2004; pp. 135–148. [Google Scholar]
- Salman, O.; Elhajj, I.H.; Kayssi, A.; Chehab, A. A review on machine learning—Based approaches for internet traffic classification. Ann. Telecommun. 2020, 75, 673–710. [Google Scholar] [CrossRef]
- Cao, J.; Wang, D.; Qu, Z.; Sun, H.; Li, B.; Chen, C.L. An improved network traffic classification model based on a support vector machine. Symmetry 2020, 12, 301. [Google Scholar] [CrossRef]
- Rezaei, S.; Liu, X. Deep Learning for Encrypted Traffic Classification: An Overview. IEEE Commun. Mag. 2019, 57, 76–81. [Google Scholar] [CrossRef]
- Muhammad Ashfaq Khan, Y.K. Deep Learning-Based Hybrid Intelligent Intrusion Detection System. Comput. Mater. Contin. 2021, 68, 671–687. [Google Scholar] [CrossRef]
- Alqahtani, H.; Sarker, I.H.; Kalim, A.; Hossain, S.M.M.; Ikhlaq, S.; Hossain, S. Cyber Intrusion Detection Using Machine Learning Classification Techniques. In International Conference on Computing Science, Communication and Security; Springer: Berlin/Heidelberg, Germany, 2020; pp. 121–131. [Google Scholar]
- Salloum, S.A.; Alshurideh, M.; Elnagar, A.; Shaalan, K. Machine learning and deep learning techniques for cybersecurity: A review. In Joint European-US Workshop on Applications of Invariance in Computer Vision; Springer: Berlin/Heidelberg, Germany, 2020; pp. 50–57. [Google Scholar]
- Arrieta, A.B.; Díaz-Rodríguez, N.; Del Ser, J.; Bennetot, A.; Tabik, S.; Barbado, A.; García, S.; Gil-López, S.; Molina, D.; Benjamins, R.; et al. Explainable Artificial Intelligence (XAI): Concepts, taxonomies, opportunities and challenges toward responsible AI. Inf. Fusion 2020, 58, 82–115. [Google Scholar] [CrossRef]
- Fernandez, A.; Herrera, F.; Cordon, O.; Jose del Jesus, M.; Marcelloni, F. Evolutionary Fuzzy Systems for Explainable Artificial Intelligence: Why, When, What for, and Where to? IEEE Comput. Intell. Mag. 2019, 14, 69–81. [Google Scholar] [CrossRef]
- Ducange, P.; Mannara, G.; Marcelloni, F.; Pecori, R.; Vecchio, M. A novel approach for internet traffic classification based on multi-objective evolutionary fuzzy classifiers. In Proceedings of the 2017 IEEE International Conference on Fuzzy Systems, FUZZ-IEEE 2017, Naples, Italy, 9–12 July 2017; pp. 1–6. [Google Scholar]
- Fazzolari, M.; Alcalá, R.; Nojima, Y.; Ishibuchi, H.; Herrera, F. A review of the application of multiobjective evolutionary fuzzy systems: Current status and further directions. IEEE Trans. Fuzzy Syst. 2013, 21, 45–65. [Google Scholar] [CrossRef]
- Antonelli, M.; Ducange, P.; Marcelloni, F. Multi-Objective Evolutionary Design of Fuzzy Rule-Based Systems. In Handbook on Computational Intelligence: Volume 2: Evolutionary Computation, Hybrid Systems, and Applications; World Scientific: Singapore, 2016; pp. 635–670. [Google Scholar]
- Coello, C.A.C.; Brambila, S.G.; Gamboa, J.F.; Tapia, M.G.C.; Gómez, R.H. Evolutionary multiobjective optimization: Open research areas and some challenges lying ahead. Complex Intell. Syst. 2020, 6, 221–236. [Google Scholar] [CrossRef]
- Barsacchi, M.; Bechini, A.; Ducange, P.; Marcelloni, F. Optimizing partition granularity, membership function parameters, and rule bases of fuzzy classifiers for big data by a multi-objective evolutionary approach. Cogn. Comput. 2019, 11, 367–387. [Google Scholar] [CrossRef]
- Gallo, G.; Bernardi, M.L.; Cimitile, M.; Ducange, P. An Explainable Approach for Car Driver Identification. In Proceedings of the 2021 IEEE International Conference on Fuzzy Systems, FUZZ-IEEE 2021, Luxemburg, 11–14 July 2021; in press. [Google Scholar]
- Frank, J.; Mda-c, N.U. Artificial Intelligence and Intrusion Detection: Current and Future Directions. In Proceedings of the 17th National Computer Security Conference, Baltimore, Maryland, 11–14 October 1994. [Google Scholar]
- Pacheco, F.; Exposito, E.; Gineste, M.; Baudoin, C.; Aguilar, J. Towards the deployment of machine learning solutions in network traffic classification: A systematic survey. IEEE Commun. Surv. Tutor. 2018, 21, 1988–2014. [Google Scholar] [CrossRef]
- Este, A.; Gringoli, F.; Salgarelli, L. Support Vector Machines for TCP traffic classification. Comput. Netw. 2009, 53, 2476–2490. [Google Scholar] [CrossRef]
- Sun, G.; Chen, T.; Su, Y.; Li, C. Internet traffic classification based on incremental support vector machines. Mob. Netw. Appl. 2018, 23, 789–796. [Google Scholar] [CrossRef]
- Qu, H.; Jiang, J.; Zhao, J.; Zhang, Y.; Yang, J. A novel method for network traffic classification based on robust support vector machine. Trans. Emerg. Telecommun. Technol. 2020, 31, e4092. [Google Scholar] [CrossRef]
- Dong, S. Multi class SVM algorithm with active learning for network traffic classification. Expert Syst. Appl. 2021, 176, 114885. [Google Scholar] [CrossRef]
- Zhongsheng, W.; Jianguo, W.; Sen, Y.; Jiaqiong, G. Traffic identification and traffic analysis based on support vector machine. Concurr. Comput. Pract. Exp. 2020, 32, e5292. [Google Scholar] [CrossRef]
- Mousavi, S.M.; Abdullah, S.; Niaki, S.T.A.; Banihashemi, S. An intelligent hybrid classification algorithm integrating fuzzy rule-based extraction and harmony search optimization: Medical diagnosis applications. Knowl. Based Syst. 2021, 220, 106943. [Google Scholar] [CrossRef]
- Joshuva, A.; Vishnuvardhan, R.; Deenadayalan, G.; Sathishkumar, R.; Sivakumar, S. Implementation of rule based classifiers for wind turbine blade fault diagnosis using vibration signals. Int. J. Recent Technol. Eng. 2019, 8, 320–331. [Google Scholar]
- Li, G.; Wu, H.; Jiang, G.; Xu, S.; Liu, H. Dynamic gesture recognition in the internet of things. IEEE Access 2018, 7, 23713–23724. [Google Scholar] [CrossRef]
- Alonso, J.M.; Castiello, C.; Magdalena, L.; Mencar, C. Explainable Fuzzy Systems: Paving the way from Interpretable Fuzzy Systems to Explainable AI Systems. In Studies in Computational Intelligence; Springer Nature: Cham, Switzerland, 2021. [Google Scholar]
- Dwivedi, P.K.; Tripathi, S.P. A Review of Multi-Objective Evolutionary Based Fuzzy Classifiers. Recent Adv. Comput. Sci. Commun. 2020, 13, 77–85. [Google Scholar] [CrossRef]
- Trawiński, K.; Cordón, O.; Quirin, A. A Study on the Use of Multiobjective Genetic Algorithms for Classifier Selection in FURIA-based Fuzzy Multiclassifiers. Int. J. Comput. Intell. Syst. 2017, 5, 231–253. [Google Scholar] [CrossRef]
- Alcalá, R.; Nojima, Y.; Herrera, F.; Ishibuchi, H. Multiobjective genetic fuzzy rule selection of single granularity-based fuzzy classification rules and its interaction with the lateral tuning of membership functions. Soft Comput. 2011, 15, 2303–2318. [Google Scholar] [CrossRef]
- Elhag, S.; Fernández, A.; Altalhi, A.; Alshomrani, S.; Herrera, F. A multi-objective evolutionary fuzzy system to obtain a broad and accurate set of solutions in intrusion detection systems. Soft Comput. 2019, 23, 1321–1336. [Google Scholar] [CrossRef]
- Zheng, J.; Wang, L.; Wang, J.J. A cooperative coevolution algorithm for multi-objective fuzzy distributed hybrid flow shop. Knowl. Based Syst. 2020, 194, 105536. [Google Scholar] [CrossRef]
- Ducange, P.; Fazzolari, M.; Marcelloni, F. An overview of recent distributed algorithms for learning fuzzy models in Big Data classification. J. Big Data 2020, 7, 1–29. [Google Scholar] [CrossRef]
- Rizzi, A.; Iacovazzi, A.; Baiocchi, A.; Colabrese, S. A low complexity real-time Internet traffic flows neuro-fuzzy classifier. Comput. Netw. 2015, 91, 752–771. [Google Scholar] [CrossRef]
- Al-Obeidat, F.; El-Alfy, E.S. Hybrid multicriteria fuzzy classification of network traffic patterns, anomalies, and protocols. Pers. Ubiquitous Comput. 2019, 23, 777–791. [Google Scholar] [CrossRef]
- Dusi, M.; Gringoli, F.; Salgarelli, L. Quantifying the accuracy of the ground truth associated with Internet traffic traces. Comput. Netw. 2011, 55, 1158–1167. [Google Scholar] [CrossRef]
- Mohammady, M.; Wang, L.; Hong, Y.; Louafi, H.; Pourzandi, M.; Debbabi, M. Preserving Both Privacy and Utility in Network Trace Anonymization. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, CCS ’18, Toronto, ON, Canada, 15–19 October 2018; pp. 459–474. [Google Scholar]
- Elnawawy, M.; Sagahyroon, A.; Shanableh, T. FPGA-Based Network Traffic Classification Using Machine Learning. IEEE Access 2020, 8, 175637–175650. [Google Scholar] [CrossRef]
- Saber, M.A.S.; Ghorbani, M.; Bayati, A.; Nguyen, K.K.; Cheriet, M. Online data center traffic classification based on inter-flow correlations. IEEE Access 2020, 8, 60401–60416. [Google Scholar] [CrossRef]
- Bujlow, T.; Carela-Español, V.; Barlet-Ros, P. Independent Comparison of Popular DPI Tools for Traffic Classification. Comput. Netw. 2015, 76, 75–89. [Google Scholar] [CrossRef]
- Carela-Español, V.; Bujlow, T.; Barlet-Ros, P. Is Our Ground-Truth for Traffic Classification Reliable? In Proceedings of the 15th International Conference on Passive and Active Measurement, Los Angeles, CA, USA, 10–11 March 2014; Volume 8362, pp. 98–108. [Google Scholar]
- Gómez, S.E.; Hernández-Callejo, L.; Martínez, B.C.; Sánchez-Esguevillas, A.J. Exploratory study on class imbalance and solutions for network traffic classification. Neurocomputing 2019, 343, 100–119. [Google Scholar] [CrossRef]
- Nascimento, Z.; Sadok, D. MODC: A pareto-optimal optimization approach for network traffic classification based on the divide and conquer strategy. Information 2018, 9, 233. [Google Scholar] [CrossRef]
- Antonelli, M.; Ducange, P.; Marcelloni, F. A fast and efficient multi-objective evolutionary learning scheme for fuzzy rule-based classifiers. Inf. Sci. 2014, 283, 36–54. [Google Scholar] [CrossRef]
- Segatori, A.; Marcelloni, F.; Pedrycz, W. On Distributed Fuzzy Decision Trees for Big Data. IEEE Trans. Fuzzy Syst. 2017, 26, 174–192. [Google Scholar] [CrossRef]
- Platt, J. Fast Training of Support Vector Machines Using Sequential Minimal Optimization. In Advances in Kernel Methods: Support Vector Learning; MIT Press: Cambridge, MA, USA, 1999; pp. 185–208. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).