Abstract
This paper studies the secure transmission in the dual-hop cognitive wiretap networks, where the secondary transmitter (Alice) aims to transmit confidential information to the secondary receiver (Bob) in the face of a multi-antenna relay (Relay), while the malicious eavesdropper (Eve) is used to eavesdrop the confidential information from Alice and Relay. To improve security, we design two transmission schemes, namely maximal-ratio combining/maximal-ratio transmission-selection combining (MRC/MRT-SC) with half-duplex (HD) receiver and maximal-ratio combining-zero forcing beamforming/maximal-ratio transmission-selection combining-zero forcing beamforming (MRC-ZFB/MRT-SC-ZFB) with full-duplex (FD) receiver. To evaluate the secrecy performance obtained from the proposed schemes comprehensively, the new closed-form and simple asymptotic expressions for the secrecy outage probability (SOP) and secrecy throughput (ST) of our considered networks with MRC-ZFB/MRT-SC-ZFB and MRC/MRT-SC schemes are derived, respectively. Thus, we explore the effect of various schemes on system secrecy performance in terms of SOP and ST. Analytical results and numerical simulations demonstrate that MRC-ZFB/MRT-SC-ZFB achieves better performance in the two proposed schemes. In particular, we show that the FD receiver plays a crucial role in designing the cognitive wiretap networks for protecting the legitimate link against attack from the malicious eavesdropping.
1. Introduction
The dramatic needs in wireless communications service have resulted in higher requirements for more spectrums. Cognitive radio networks (CRNs) aim to effectively address spectrum scarcity and have attracted much attention from the research communities [1,2,3,4]. In spectrum sharing CRNs, the unlicensed secondary users (SUs) can have access to the licensed primary users’ (PUs) spectrum in the condition that the interference power at the PU does not surpass a certain value [5]. Not only are CRNs expected to increase spectrum reuse, but they are also taken the low complexity of implementation into consideration. Thus, the underlay scheme has attracted growing attention, where the interference of SUs to the PUs should be guaranteed not to exceed a given threshold.
1.1. Background
Due to the open nature of CRNs, they are vulnerable to illegal attacking and malicious eavesdropping, which would result in many challenging issues, especially security. Traditional security policies are not applicable to meet the security requirements of CRNs. Motivated by the problem, physical layer security (PLS) has been conceived as a new paradigm to guarantee secure transmissions while overcoming the vulnerabilities of traditional higher layer cryptography. For enhancing the PLS of wireless transmissions, many works have been explored. The orthogonal frequency-division multiplexing of CRNs as the medium access technique is put forward to show the performance of PLS in [6]. In [7,8], the authors proposed multiuser scheduling-aided energy harvesting to improve PLS in CRNs. The maximizing secrecy capacity of CRNs through zero forcing beamforming (ZFB) was investigated in [9]. There is still a lot of previous work that has been done on PLS of CRNs. In [10], the security strategy deployment for switches on core network is proposed to enhance network’s performance in cognitive internet of vehicles. In [3,11,12], the authors proposed different protocols to enhance the secrecy performance of CRNs. The device-to-device (D2D), the non-orthogonal multiple access (NOMA), buffer-aided technology and millimeter-wave (mmWave) were also used to improve the communication quality of CRNs [13,14,15,16,17].
With the maturity of self-interference cancellation technology, full-duplex (FD) technology is becoming more widely used. It is worth highlighting that lots of scholars are focusing on the full-duplex (FD) and have extensively applied it in many areas. On the one hand, the FD technique is proposed for the sake of enhancing the performance of the traditional cooperative jamming scheme (TCJS). The core part of full-duplex jamming scheme (FDJS) is that the FD user is able to transmit jamming signal and receive the required signal at the same time, and has been widely used in 5G communication systems [18]. In [19,20] , authors have fully demonstrated the application of FD technology in CRNs. Different from TCJS, FDJS is much easier and more reliable to realize. In [12], the authors designed different antenna reception schemes of FD operations, where the secrecy performance of system is enhanced through transmitting jamming signals and receiving legal signal at the same time. In [21], the authors analyzed the different relay selection schemes for the FD heterogeneous networks with multiple cognitive radio eavesdroppers to improve the secrecy performance of system. In [22], the authors analyzed collaboration interference (CI) transmission scheme of the FD wireless wiretap networks for improving PLS in CRNs. In [23], the authors explored that receiving antenna can send jamming signals at the time of receiving information and energy to degrade the eavesdropper’s decoding capacity through FD operation, which was put forward to enhance the PLS. On the other hand, the beamforming with artificial noise (AN) of FD operation can effectively decrease the eavesdropping efficiency of eavesdropping users by sending interfering signals. However, beamforming with AN is different from beamforming in traditional networks because there are following aspects should be considered in CRNs. First, the interference power of PU should be taken into consideration in the process of designing beamforming scheme, that is, the quality of service (QoS) of PUs are ensured. Second, in [24,25,26], the SU transmitter can obtain SU receiver channel state information (CSI) through a pilot signal transmitted by SU receiver. Secure transmission in a multiple-input single-output multi-eavesdropper CRNs was investigated in [26] with the aim of maximizing the ergodic secrecy rate by beamforming and AN. In [27], AN was introduced in D2D to interfere with illegal eavesdropping of eavesdropping nodes, and the closed-form expression of SOP was further obtained to verify the impact on system performance. An artificial-noise-aided CJS was proposed to improve the PLS under the energy harvesting constraints and practical secrecy rate in [28].
1.2. Motivation and Contribution
Motivated by the discussion mentioned above,we investigate secure transmission in the dual-hop cognitive wiretap networks with FD receiver over Rayleigh fading channels under two different scenarios, in which the secondary transmitter (Alice) aims to transmit confidential information to the secondary receiver (Bob) in the presence of a multi-antenna relay (Relay), while the eavesdropper (Eve) is to eavesdrop the confidential information from Alice and Relay. The randomize-and-forward (RaF) transmission protocol has been widely used in different phases of physical layer security in CRNs. Since there is the transmission heterogeneity of the two transmitters, the eavesdropper cannot merge the common information of the two phases [29,30]. Relay is considered the half-duplex (HD) operation and Bob is considered the FD beamforming with AN operation to prevent overheard by the eavesdropper. To be specific, for the HD operation, the Relay utilize maximal-ratio combining (MRC) to pay more attention to the signal detection from Alice and send data to Bob by using maximal-ratio transmit (MRT) scheme, and then Bob receives signals forwarded from the Relay through using the selection combining (SC) scheme. While for the FD operation, MRC-ZFB/MRT-SC-ZFB secure transmission schemes are proposed, Relay first adopts MRC scheme to receive the data forwarded from Alice and at the same time Bob uses the ZFB scheme to transmit AN signals to reduce the illegal wiretapping of users at the first phase. At the second phase, Relay utilizes MRT scheme to send security information to Bob, and then Bob selects the best antenna to receive information from Relay and simultaneously transmits the jamming signal by utilizing the remaining antennas with FD operation. Our principal contributions are highlighted as follows:
- We first derive closed-form and simple asymptotic expressions for the secrecy outage probability (SOP) and the secrecy throughput (ST) of the FD receiver cognitive wiretap networks with MRC-ZFB/MRT-SC-ZFB and MRC/MRT-SC schemes, respectively [31]. Moreover, we also explore the impact of the various system parameters on the SOP and ST, i.e., the number of antennas and the interference threshold at Relay and Bob.
- We further derive the asymptotic closed-form expressions for the SOP and the secrecy diversity order and secrecy coding gain are achieved under two different scenarios, namely Scenario I: and fixed , and Scenario II: and , which reveals that the influence of system performance under the high signal-to-noise ratio (SNR). Two distinct scenarios can achieve the same secrecy diversity () under Scenario I and zero secrecy diversity under Scenario II, where and denote the average SNR of the main channel and the eavesdropping channel, respectively.
- Through the derivation and analysis of the SOP and ST, it has been verified that the MRC-ZFB/MRT-SC-ZFB scheme of FD operation at Bob outperforms MRC/MRT-SC scheme of HD operation in terms of enhancing secrecy performance of CRNs. The attained asymptotic expressions shed lights on the impact of distinct system parameters, i.e., increasing interference threshold of the primary network within a certain range and the number of antennas at the Relay and Bob. The beamforming of AN design can effectively improve the secrecy performance of the considered networks and the secrecy performance of the considered scheme with FD operation is mainly affected by the secrecy coding gain.
The remainder of the paper is organized as follows. In Section 2, the proposed system model is described. The SOPs of the system for the secondary data transmission are analyzed in Section 3. In Section 4, we provide the SOPs of the system under the high SNR analysis and ST. In Section 5, the numerical results and discussions are presented. Finally, we concludes this paper in Section 6.
2. System Model
As shown in Figure 1, Let us consider a secure transmission in cognitive wiretap networks with FD receiver consisting of a secondary user (SU) transmitter (Alice), a legitimate SU receiver (Bob), a relay (Relay), a primary user receiver (PU) and a passive eavesdropper (Eve). A transmitter Alice, an eavesdropper Eve and a primary user receiver only have a single antenna, while a secondary Relay and Bob are equipped with multiple antennas, which are denoted by and , respectively. As in, it is assumed that in this paper the Alice, Relay, Bob and Eve nodes are located in the same cluster far away from the primary user transmitter, and hence there is no direct link from the Alice–Bob and the link security information can only be transmitted through the Relay node. In this paper, we assume that both main and wiretap channels experience quasi-static independent block Rayleigh fading. The malicious eavesdropper has strong eavesdropping ability. The channel coefficient between M and N nodes, termed as , is an distributed random variable (RV) with zero mean and variance as denoted by . As in [20,32,33,34], legitimate channel state information (CSI) is assumed available at the Relay and Bob, namely the CSI of Alice-Relay and Relay–Bob. Recently, with advances on self-interference (SI) cancellation technology, we assume that the SI can be completely suppressed of the relay–relay link [11,20]. For investigating the advantages of FD Bob, we explore two distinct secure transmission schemes, namely MRC/MRT-SC scheme of HD operation and MRC-ZFB/MRT-SC-ZFB scheme of FD operation. For MRC-ZFB/MRT-SC-ZFB scheme, the CSI of the eavesdropping links is available for Bob, i.e., the CSI of Bob-Eve link. According to [12,33,35] and the mutual reciprocity of the channels, the Bob can obtain a reliable feedback CSI from the Eve in the condition of time-division duplex transmission.
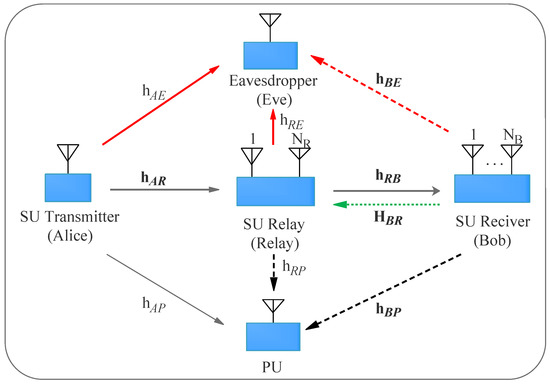
Figure 1.
System Model.
2.1. MRC/MRT-SC with HD Scenario
The secure MRC/MRT-SC protocol employs two phases. For MRC phase, the Alice transfers information to the Relay, and Relay receives a radio signals through MRC scheme based on HD operation. Thus, the instantaneous SNR at Relay can be represented as
where denotes the noise variance at Relay, is an channel link vector Alice-Bob, and the transmit power of Alice is denoted by , which should be varied as [36]
where Q and are the interference temperature constraint and the maximum transmit power constraint at PU and Alice, respectively. is the channel coefficient for the Alice–PU link.
Similarly, define the SNR at node Eve as , and is given by
where denotes the noise variance at Eve, is the channel coefficient for Alice–Eve link.
For MRT-SC phase, the Relay transfers information to the Relay by applying MRT-SC scheme based on HD operation which is similar to analysis of the MRC phase to transmit signal. Therefore, the instantaneous SNR for the Bob can be represented as
where refers to the channel vector between Relay and the i-th receive antenna at Bob, refers to the noise variance at Bob, and the transmit power of Relay is denoted by , which must satisfy . is the Rayleigh channel and obeys the exponential distribution [37].
Similarly, define the SNR at node Eve as , and is given by
in which is the channel coefficient for Relay-Eve link.
2.2. MRC-ZFB/MRT-SC-ZFB with FD Scenario
The secure MRC-ZFB/MRT-SC-ZFB protocol employs two phases and the beamforming vector , are designed for each phase. For MRC-ZFB phase, we put forward an optimal beamforming scheme which maximizes the achievable secrecy rate of MRC-ZFB CRNs based on FD operation. Relay can adopt antennas gain for receiving the signal from the Alice by MRC operation, and Bob uses antennas for transmitting jamming signals to eavesdropper Eve simultaneously by using ZFB operation. ZFB is employed to get rid of malicious jamming signals for meeting the constraints at PU.
Now, defining the channel matrix, i.e., , where , are , channel link matrices Bob-PU and Bob-Relay, respectively, but the number of the antennas at Bob should be more than . It is assumed that Relay employs a linear receiver with = 1 for detecting signal. Additionally, MRC is employed at the Relay, denoted as [38]. The optimal expression of the weight vector is given by
where † and are the conjugate transpose operator and the Frobenius norm, respectively. denotes the channel vector between antennas of Bob and Eve. denotes the channel vector between Relay and Bob. By applying the projection matrix theory [39], weight vector is given by
where is the correlation matrix with rank . Consequently, the instantaneous SNR at the Relay and the instantaneous signal-to-interference-plus-noise ratio (SINR) at the Eve are written as
and
where the interference power of Bob–Eve is denoted by . For the FD mechanism, when researchers investigate the performance limitations of information theory (such as capacity), the assumption that SI is not taken into consideration is widely used [33].
Therefore, for solving the closed-form expressions of SOP of FD operation at Bob, a detailed introduction will be presented in Section 3.
For MRT-SC-ZFB with FD phase, the Relay uses the antennas to transmit information to Bob. Then Bob selects the best i-th antenna to receive information from Relay and the remaining antennas transmit the jamming signal to Eve simultaneously. Therefore, Relay adopts MRT operation to decode and retransmit signal, and Bob adopts SC-ZFB operation to receive signals simultaneously to transmit jamming signals. The aim of SC-ZFB operation is to maximize the received SNR at Bob while avoiding the leakage of security information to the Eve and the interference to PU.
For the MRT-SC-ZFB phase, it requires . Thus, the optimal expression of the optimal weight vector is expressed as
where denote the channel vector between the remaining antennas of Bob and Eve. denote the channel vector between the remaining antennas of Bob and PU. By applying projection matrix theory, weight vector is given by
where is the correlation matrix with rank . Hence, the instantaneous SNR at the Bob and the instantaneous SINR at the Eve are written as
and
As mentioned before, the precoding matrix and are designed for MRC-ZFB and MRT-SC-ZFB schemes so that the AN signal is wholly eliminated at the Bob–Relay and Bob–PU. It is clearly noted that in the MRC-ZFB/MRT-SC-ZFB with FD scenario, jamming signal is transmitted throughout the information transmission process to degrade the eavesdropping channel capacities of Alice–Eve and Relay–Eve links, and it does not interfere with the PU.
However, both , , and are affected by the common variable RV, represent scheme 1 and scheme 2, respectively. and in and . To solve this problem, we should derive the Cumulative Distribution Function (CDF) of and , and Probability Density Function (PDF) of and conditioned on G and .
According to RaF protocol, the SOPs of the two different phases are independent. A fundamental secrecy performance criterion in the complete Alice–Bob process is instantaneous secrecy capacity, which is represented as
where and represent the capacities of the main channel and eavesdropping channel links, respectively, and stands for the first phase and the second phase, respectively. For maximizing the secrecy capacity , the main channel need to maximize and the eavesdropping channel need to minimize through the number of and at the Relay and Bob in two different phases. Two different phases of each scenario have independent transmission processes. , , , , and are defined in this paper for doing simple notational analysis.
3. Secrecy Performance Analysis
In this part, we study the SOP of the secure transmission in the dual-hop cognitive wiretap networks with FD receiver under two different scenarios. The SOP, defined as the probability of the secrecy capacity, , is less than a given threshold, . According to RaF protocol [20,40], we only solve the SOP of each independent phase. Mathematically, given by
where and represent instantaneous secrecy rate and a predetermined threshold, respectively. Furthermore, the outage probability of is expressed as
where and refer to the instantaneous secrecy rate of the first phase and the second phase, respectively, (MRC, MRC-ZFB) in the first phase, (MRT-SC,MRT-SC-ZFB) in the second phase. The instantaneous SOP of and in MRC/MRT-SC scheme are written as
and
The instantaneous SOP of and in MRC-ZFB/MRT-SC-ZFB scheme are formulated as
and
In order to solve (16), needs to use (17), (18), (19) and (20). We have
and
where and are the SOP of the first phase and second phase of each scenario, respectively. Furthermore,
with
and
with
and are CDF of and , respectively. Armed with (15), the expression of will be presented in the following Lemma.
Lemma 1.
The of Alice-Bob link channel is expressed as
Next, we will solve the and of two different scenarios according to Lemma 1.
3.1. MRC/MRT-SC with HD Scenario
For MRC phase, observing from (1), (3) and [11], the conditional CDF of and the conditional PDF of , are respectively written as
and
The random variable obeys the exponential distribution, and the PDF expression of G is given by
Thus, by using (30) and (31), we can write the CDF of for the MRC operation with the HD mechanism in the following theorem.
Theorem 1.
By using MRC scheme we can calculate the CDF of , which can be derived as
where is the incomplete upper gamma function, as defined in (Equation (8.350.2), [41]).
Proof of Theorem 1.
See Appendix A. □
For MRT-SC phase, observing from (4), (5), [12,42], the conditional CDF of and the conditional PDF of , are respectively given by
and
where , with , , and . Then, substituting (33) and (34) into (15), the conditional is written as
The random variable also obeys the exponential distribution, and the PDF expression of can be written as .
Thus, by using (35) and , we can write the CDF of for the MRT-SC scheme with the HD mechanism in the following theorem.
Theorem 2.
By using MRT-SC scheme we can calculate the CDF of , which can be derived as
In this phase, the proof process of for the MRT-SC scheme is similar with Theorem 1, and will not be elaborated here.
3.2. MRC-ZFB/MRT-SC-ZFB with FD Scenario
For MRC-ZFB phase, observing from (8) and (9), and in the presence of [12], the conditional CDF of can be written as
Lemma 2.
The conditional PDF of is given by
Proof of Lemma 2.
See Appendix B. □
Then, we can operate several mathematical manipulations. By making use of (Equation (9.211.4), [41]), and can be rewritten as
and
where being the confluent hypergeometric function of second kind.
Thus, the conditional can be rewritten as
Hence, the can be derived as
Now, substituting (31) into (43), we can write the CDF of for the MRC-ZFB scheme with the FD mechanism in the following theorem.
Theorem 3.
By using MRC-ZFB scheme we can calculate the CDF of , which can be derived as
In this phase, the proof process of for the MRC-ZFB scheme is similar with Theorem 1, and will not be elaborated here.
For MRT-SC-ZFB phase, observing from (12) and (13), and by making use of [12], conditional CDF of and conditional PDF of are respectively presented as and . These processes are similar to (33) and (38). By replacing with , which also satisfies the condition of , , and in (33). In (38), , and .
Then, substituting and into (15), the conditional is written as
Thus, by using (45) and , we can write the CDF of for the MRT-SC-ZFB scheme with the FD mechanism in the following theorem.
Theorem 4.
By using MRT-SC-ZFB scheme we can calculate the CDF of , which can be derived as
In this phase, the proof process of the for the MRT-SC scheme is similar with Theorem 1, and will not be elaborated here.
4. High SNR Analysis and Secrecy Throughput
4.1. High SNR Analysis
Although the derivation of the closed-form expressions of the SOP has been finished above, the analysis of the asymptotic SOP in the high SNR will be conducted in this subsection to obtain more insights. Specifically, consider two different scenarios: (1) and fixed , that a scenario in which the SNR of main link outperforms the SNR of the eavesdropper’s link, also known as the eavesdropper’s channel, suffers from heavy shadowing effect. (2) and , that a scenario where both the receiver and the eavesdropper can be closer to the transmitter, namely both the wiretap channel and main channel are equipped with better SNR. ST is also one of the indicators to verify the secrecy performance of the considered system. Finally, the secrecy performance can be expressed by the high SNR slope, the secrecy diversity gain and coding gain. In the section, for and , represent MRC/MRT-SC, MRC-ZFB/MRT-SC-ZFB, respectively.
4.1.1. Scenario I: and Fixed
In this scenario, is approximated as
and is given by
where and represent the first phase and second phase of the MRC/MRT-SC and MRC-ZFB/MRT-SC-ZFB schemes, respectively.
(1) MRC/MRT-SC scheme:
Corollary 1.
The asymptotic SOP of the different time-slots with MRC/MRT-SC scheme under andfixed is given by
and
Proof of Corollary 1.
See Appendix C. □
(2) MRC-ZFB/MRT-SC-ZFB scheme:
Corollary 2.
The asymptotic SOP of the different phases with MRC-ZFB/MRT-SC-ZFB scheme under andfixed is given by
Then is given by
Proof of Corollary 2.
See Appendix D. □
Remark 1.
The secrecy diversity gain of the MRC/MRT-SC and MRC-ZFB/MRT-SC-ZFB schemes is under Scenario I, which is only determined by the number of and of Relay and Bob, respectively. Additionally, the quality of the main channel and wiretap channel influence the secrecy performance of two scenarios through the coding gain, i.e., , in which (MRC/MRT-SC, MRC-ZFB/MRT-SC-ZFB), respectively. We found that the more multiple antennas of Relay and Bob, the better system performance.
4.1.2. Scenario Ii: and
Now, the approximated SOP of the considered CRNs is analyzed in this section.
(1) MRC/MRT-SC scenario:
Corollary 3.
The asymptotic SOP of the MRC/MRT-SC scenario under and can be expressed as
where and being expressed as
and
Proof.
(2) MRC-ZFB/MRT-SC-ZFB scheme:
Corollary 4.
The asymptotic SOP of the MRC-ZFB/MRT-SC-ZFB scenario under and is given by
where and are respectively expressed as
and
Proof.
Remark 2.
In contrast to Scenario I, when and , two scenarios appear to be the secrecy outage floor that unable to obtain secrecy diversity. Thus, the secrecy performance of the system can only be improved by the secrecy coding gain.
4.2. Secrecy Throughput
On the basis of SOP, the ST more comprehensively measures the reliability and security of the system in a whole way, which is the product of the complementary probability of and the predetermined secrecy rate (Equation (24), [43]), [44]. Thus, the throughput expression of the two schemes can be written as
where (MRC/MRT-SC, MRC-ZFB/MRT-SC-ZFB).
Remark 3.
Given the Equation (59), we numerically find that exist an optimal value in a given range. When is small, of the two scenarios is relatively small. However, when exceeds an optimal value, the would decrease until zero. Therefore, determining the optimal value, , is practically significant to system designers, which can achieve the local optimal ST of system.
5. Numerical Results
In this section, analytical results demonstrate the secrecy performance of the MRC/MRT-SC and MRC-ZFB/MRT-SC-ZFB schemes in terms of the achievable SOP. A detailed investigation on the effect of various system parameters, namely the number of antennas and thresholds, i.e., , and is conducted. Without loss of generality, , , and dB are set, and the transmitted SNR at Alice or Relay can be derived as . In addition, we take path loss attenuation as , where is the distance from M to N node and is normalized to 1, and all simulation results are obtained by averaging over 300,000 independent Monte Carlo trials. The Monte Carlo simulations in all figures thoroughly coincide with the theoretical simulation curves, which verifies that the closed-form expression is derived correctly in this paper. With the high SNR, the asymptotic curve approaches the exact curve. We also verified the secrecy diversity order in the asymptotic analysis expressions by the asymptotic curve.
Figure 2 and Figure 3 illustrate the impact for different numbers of , , and Q on the SOPs of the MRC/MRT-SC and MRC-ZFB/MRT-SC-ZFB schemes, respectively. at different . The exact curves are obtained from and . Due to the strong eavesdropping ability of the eavesdropper, the MRC/MRT-SC scheme does not significantly change the system performance. It is clearly seen that the outage performance of wireless communications is proportional to the number of , and . Obviously, if the is higher, the outage performance of the system will be better. As shown, MRC-ZFB/MRT-SC-ZFB scheme achieves the best performance over the range of and the secrecy rate of the MRC-ZFB/MRT-SC-ZFB scheme gradually increases with before it saturates. And in this section, secrecy outage floor will appear in MRC-ZFB/MRT-SC-ZFB and MRC/MRT-SC schemes when increases, this is because the Q is a crucial factor influencing the secrecy performance of system and is not limited by the of the secondary user transmitter. Additionally, when the number of and Q are fixed in two schemes, MRC-ZFB/MRT-SC-ZFB scheme with FD operation and beamforming with AN obviously attain better performance than MRC/MRT-SC scheme with HD operation from the perspective of enhancing the secrecy performance of wireless communications.
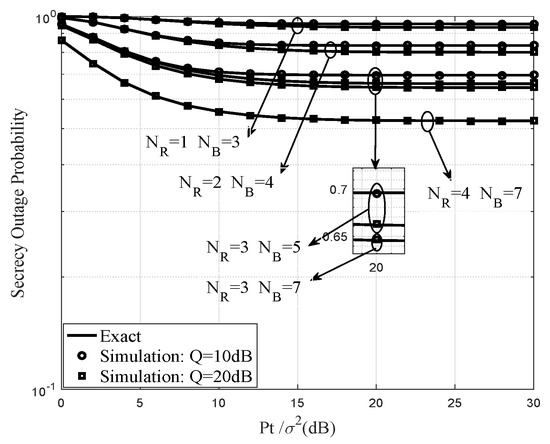
Figure 2.
Secrecy outage probability of MRC/MRT-SC scheme for different number , and Q.
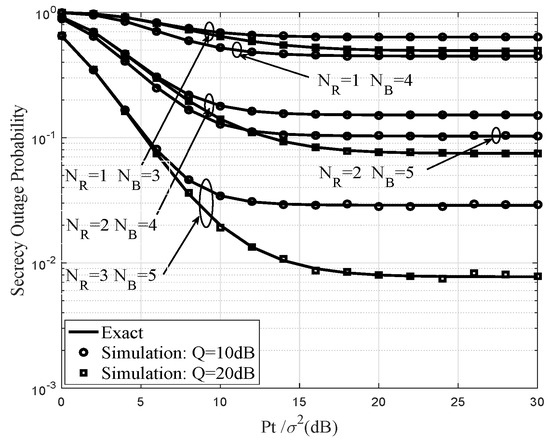
Figure 3.
Secrecy outage probability for the MRC-ZFB/MRT-SC-ZFB scheme when dB and different number , and Q.
Figure 4 shows the effect of increasing and on the SOP and the asymptotic expressions curves of SOP attained from (47) under the and fixed , respectively, where dB and dB. The parallel slope of the asymptote shows that the high SNR slope is independent of . It is worth noting that the curve converges quickly and hence the derived approximation is accurate. Furthermore, when and increase, the SOP will be significantly improved. Moreover, as expected, MRC/MRT-SC scheme has the lowest performance than the MRC-ZFB/MRT-SC-ZFB scheme. Thus, we see that the MRC-ZFB/MRT-SC-ZFB scheme with FD operation and beamforming with AN always outperforms than the MRC/MRT-SC scheme with HD operation, which means that transmitting jamming signals from a FD Bob through the MRC-ZFB/MRT-SC-ZFB scheme would enhance the secrecy array gain of the system compared with the MRC/MRT-SC scheme under Scenario I.
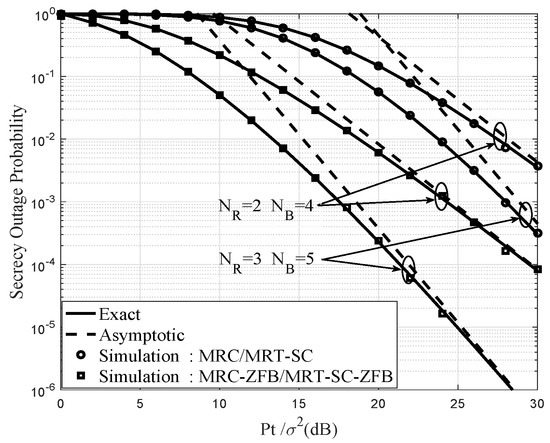
Figure 4.
Exact and asymptotic secrecy outage probability for the MRC/MRT-SC and MRC-ZFB/MRT-SC-ZFB schemes under Scenario I when dB, dB and different values and .
Figure 5 shows the SOP versus of the two schemes when dB, , and . The asymptotic expressions curves of SOP are achieved from (53) and (56) under the and , respectively. The analytical results shows that the MRC-ZFB/MRT-SC-ZFB scheme has better performance than MRC/MRT-SC scheme under different and . It is noted that, for fixed , increasing and lead to a slight decrease in the values of SOP. Additionally, the MRC-ZFB/MRT-SC-ZFB scheme achieves better performance than the MRC/MRT-SC scheme at the low , while the same holds at the high . Therefore, the MRC-ZFB/MRT-SC-ZFB scheme improves the transmission performance of wireless communication under Scenario II.
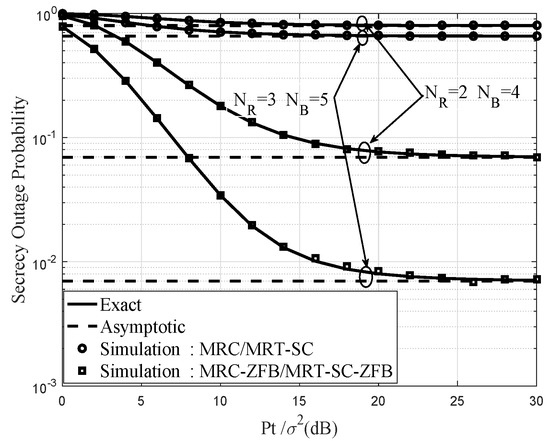
Figure 5.
Exact and asymptotic secrecy outage probabilities for the MRC/MRT-SC and MRC-ZFB/MRT-SC-ZFB schemes under Scenario II when dB and different values and .
Figure 6 shows the SOP of two schemes for different number of and fixed varies with dB and dB. As the Relay is equipped with more antennas, the SOP steadily decreases. It can be seen that the MRC-ZFB/MRT-SC-ZFB scheme always outperforms the MRC/MRT-SC scheme, and MRC/MRT-SC with HD operation scheme has a higher SOP under the same conditions. In particular, the MRC-ZFB/MRT-SC-ZFB scheme has a greater influence on the secrecy performance of the system than the MRC/MRT-SC scheme from the perspective of the value of . The reason is that the MRC-ZFB/MRT-SC-ZFB scheme enhances system secrecy performance based on FD operation at Bob. Thus, it also verifies the exact validity and the rationality of the closed-form expression of our proposed schemes. It is found that the more , the better the system performance, and the secrecy performance of the proposed MRC-ZFB/MRT-SC-ZFB scheme with FD operation is mainly affected by the secrecy coding gain.
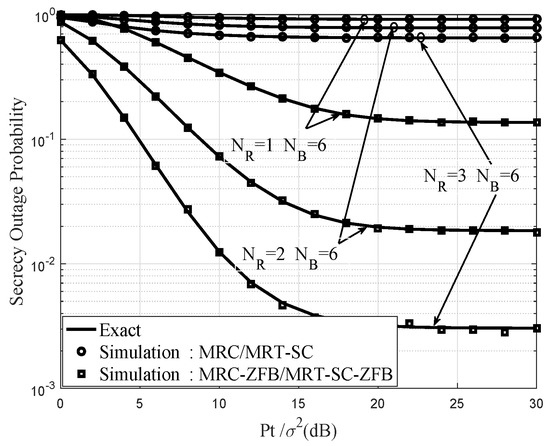
Figure 6.
Secrecy outage probability of two schemes for different number and fixed .
Figure 7 shows the secrecy outage probability vs , and . dB, dB, and are set in two figures. In the first figure, when we set SNR = 20 dB, the simulation results demonstrate that when is relative low, the SOP of two different schemes decreases when increases. The MRC-ZFB/MRT-SC-ZFB of our proposed scheme outperforms MRC/MRT-SC scheme. The main reason is that the main channel is similar with the eavesdropper’s channel. However, when is over 20, the eavesdropper’s eavesdropping ability is relative weak and the noise power is almost zero, so there is no eavesdropping and interference object for MRC-ZFB/MRT-SC-ZFB scheme. Therefore, the two schemes have almost the same effect on system performance.The second figure shows that the SOP of two different schemes decreases when increases. When and 10, the SOP of MRC-ZFB/MRT-SC-ZFB scheme have obvious influence than the MRC/MRT-SC scheme in terms of enhancing the secrecy performance of system.
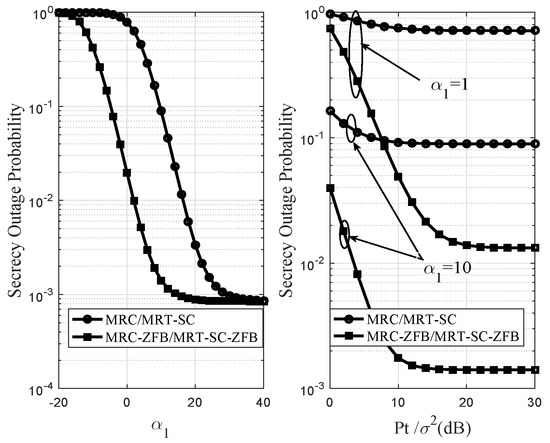
Figure 7.
Secrecy outage probability of two schemes for different .
Figure 8 plots the ST versus with different values of and . In this simulation, the analytical curves were obtained from (59), and it is clearly seen that the throughput of different schemes increases at the beginning and then decreases with the increasing of . It illustrated that there exists an optimal value of MRC/MRT-SC and MRC-ZFB/MRT-SC-ZFB schemes, making the secrecy transmission best. We also find that increasing and can improve ST significantly, which reflects the efficiency of equipping Relay and Bob with multiple antennas. Observe from Figure 8 that the ST of the MRC/MRT-SC scheme does not change significantly as varies from = 4 to 6. This is because the ST is mainly affected by the antenna gain in MRC/MRT-SC scheme. Finally, we observe that MRC-ZFB/MRT-SC-ZFB also outperforms the MRC/MRT-SC scheme over different values of , and .
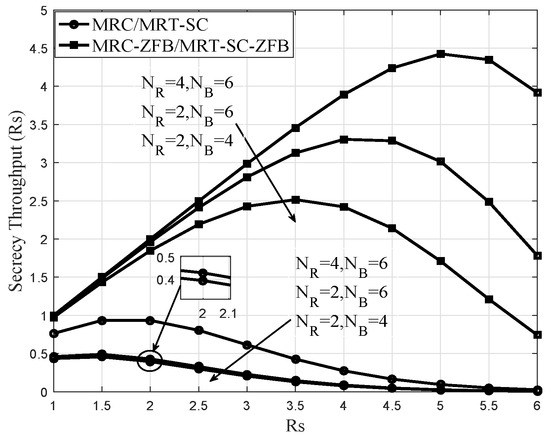
Figure 8.
Throughput of the two schemes vs different with SNR = 20 dB, Q = 20 dB, and different values and .
6. Conclusions
In this paper, we explored the secure transmission in cognitive wiretap networks with FD receiver. To investigate the benefits of FD operation at receiver of the considered CRNs, the MRC-ZFB/MRT-SC-ZFB with FD operation and MRC/MRT-SC of HD operation schemes were proposed, respectively. Also, the new closed-form and simple asymptotic expressions for the SOP and ST of our considered networks with MRC-ZFB/MRT-SC-ZFB and MRC/MRT-SC schemes were derived, respectively. Different transmission parameters, such as the SNR, Q and the number of and are designed to verify the impact on system secrecy performance. The closed-form expressions for the exact and asymptotic SOP concisely characterized the secrecy diversity gain and the secrecy coding gain. Additionally, analytical results and numerical simulations demonstrated that beamforming with AN is an important tool for ensuring secure transmission facing with a malicious eavesdropper in CRNs. Finally, it is also found that the MRC-ZFB/MRT-SC-ZFB scheme outperforms MRC/MRT-SC scheme, which verifies the advantages of the schemes conceived in this paper. Our results provided a unified model to analyse the SOP performance and the ST of the FD receiver cognitive wiretap networks over Rayleigh fading channels and could be easily extended to the scenarios with multiple PUs being faced with multiple eavesdroppers, which is also one of the parts in our further works.
Author Contributions
Z.S. and T.Z. conceived the model; Z.S. performed the simulation results and wrote the paper; and T.Z., Y.C., W.Y., H.W., Y.Z., L.T. provided some suggestions and revised the paper. All authors have read and agree to the published version of the manuscript.
Funding
This work was supported by the National Natural Science Foundation of China under Grant (No. 61801496, No. 61771487 and No. 61801497), the National Postdoctoral Program for Innovative Talents of China (No. BX20180374), the National University of Defense Technology Research Project (No. ZK17-03-25), the Defense Science Foundations of China (No. 2019-JCJQ-JJ-221), and the Joint Foundation Project of Zunyi Science and Technology Bureau and Zunyi Medical University of Guizhou Provincial (No. E-282).
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
Appendix B
We first denote . By using (Equation (12), [45]), the PDF of the index distribution can be expressed as
Noticing that when , is the correct expression. Based on (9), we have
Hence, is represented as
Finally, we obtain the conditional PDF of after derivation.
Appendix C
Based on MRC scheme, when , the conditional CDF of is given by
Also, the conditional PDF of is written as
Now, On the basis of (31), the desired result can be derived as
Based on MRT-SC phase, the MRT-SC scheme is similar with MRC scheme description process of the (A8), and when , the conditional CDF of can be approximated as
is the same as of (A6).
Similarly, the asymptotic conditional is given by
Now, on the basis of , the desired result is written as
Appendix D
On the basis of MRC-ZFB scheme, when , the conditional CDF of is the same as (A5), only with the change of parameter . Also, fixed , we can obtain from (38). The conditional PDF of is represented as
Now, according to (31), the desired result is written as
Since the MRT-SC-ZFB phase is similar with description process of the (A14) at MRC-ZFB phase, so it is simply derived here. When , the approximation of can be obtain by (A9), only with the change of parameters . Similarly, fixed , we can obtain from (38). The conditional PDF of is written as
Based on , the desired result is presented as
References
- Mitola, J. Cognitive Radio: An Integrated Agent Architecture for Software Defined Radio. Ph.D. Thesis, KTH Royal Institute of Technology, Stockholm, Sweden, 2000. [Google Scholar]
- Zhang, T.; Cai, Y.; Huang, Y.; Duong, T.Q.; Yang, W. Secure full-duplex spectrum-sharing wiretap networks with different antenna reception schemes. IEEE Trans. Commun. 2017, 65, 335–346. [Google Scholar] [CrossRef]
- Huang, Y.; Al-Qahtani, F.; Wu, Q.; Zhong, C.; Wang, J.; Alnuweiri, H. Outage analysis of spectrum sharing relay systems with multiple secondary destinations under primary user’s interference. IEEE Trans. Veh. Technol. 2014, 63, 3456–3464. [Google Scholar] [CrossRef]
- Oliveira, G.; Fernandez, E.; Mafra, S.; Montejo-Sánchez, S. Physical layer security in cognitive radio networks using improper gaussian signaling. IEEE Commun. Lett. 2018, 22, 1886–1889. [Google Scholar] [CrossRef]
- Biliary, E.; Goldsmith, A.; Greenstein, L.; Mandayam, N.; Poor, H.V. Principles of Cognitive Radio; Cambridge University Press: Cambridge, UK, 2013. [Google Scholar]
- Shah, H.A.; Koo, I. A novel physical layer security scheme in OFDM-based cognitive radio networks. IEEE Access 2018, 6, 29486–29498. [Google Scholar] [CrossRef]
- Ding, X.; Zou, Y.; Zhang, G.; Chen, X.; Wang, X.; Hanzo, L. The security-reliability tradeoff of multiuser scheduling-aided energy harvesting cognitive radio networks. IEEE Trans. Commun. 2019, 67, 3890–3904. [Google Scholar] [CrossRef]
- Yan, P.; Zou, Y.; Zhu, J. Energy-aware multiuser scheduling for physical-layer security in energy-harvesting underlay cognitive radio systems. IEEE Trans. Veh. Technol. 2018, 67, 2084–2096. [Google Scholar] [CrossRef]
- Nandan, N.; Majhi, S.; Wu, H. Maximizing secrecy capacity of underlay MIMO-CRN through bi-directional zero-forcing beamforming. IEEE Trans. Wirel. Commun. 2018, 17, 5327–5337. [Google Scholar] [CrossRef]
- Qian, Y.; Chen, M.; Chen, J.; Hossain, M.S.; Alamri, A. Secure enforcement in cognitive internet of vehicles. IEEE Internet Things J. 2018, 5, 1242–1250. [Google Scholar] [CrossRef]
- Zhang, T.; Huang, Y.; Cai, Y.; Yang, W. Secure transmission in spectrum sharing relaying networks with multiple antennas. IEEE Commum. Lett. 2016, 20, 824–827. [Google Scholar] [CrossRef]
- Zhang, T.; Huang, Y.; Cai, Y.; Zhong, C.; Yang, W.; Karagiannidis, G.K. Secure multiantenna cognitive wiretap networks. IEEE Trans. Veh. Technol. 2017, 66, 4059–4072. [Google Scholar]
- Sultana, A.; Zhao, L.; Fernando, X. Efficient resource allocation in device-to-device communication using cognitive radio technology. IEEE Trans. Veh. Technol. 2017, 66, 10024–10034. [Google Scholar] [CrossRef]
- Li, M.; Liao, W.; Chen, X.; Sun, J.; Huang, X.; Li, P. Economic-robust transmission opportunity auction for D2D communications in cognitive mesh assisted cellular networks. IEEE Trans. Mob. Comp. 2018, 17, 1806–1819. [Google Scholar] [CrossRef]
- Song, Y.; Yang, W.; Xiang, Z.; Wang, B.; Cai, Y. Secure transmission in mmWave NOMA networks with cognitive power allocation. IEEE Access 2019, 7, 76104–76119. [Google Scholar] [CrossRef]
- Wei, C.; Yang, W.; Cai, Y.; Tang, X.; Yin, T. Secrecy outage performance of buffer-aided underlay cognitive relay networks with outdated CSI. In Proceedings of the 2018 IEEE 7th CIC International Conference on Communications in China (CIC ICCC), Beijing, China, 16–18 August 2018; pp. 168–173. [Google Scholar]
- Xiang, Z.; Yang, W.; Pan, G.; Cai, Y.; Song, Y. Physical layer security in cognitive radio inspired NOMA network. IEEE J. Sel. Top. Signal Process 2019, 13, 700–714. [Google Scholar] [CrossRef]
- Jameel, F.; Wyne, S.; Kaddoum, G.; Duong, T.Q. A comprehensive survey on cooperative relaying and jamming strategies for physical layer security. IEEE Commun. Surv. Tuts. 2019, 21, 2734–2771. [Google Scholar] [CrossRef]
- Amjad, M.; Akhtar, F.; Rehmani, M.H.; Reisslein, M.; Umer, T. Full-duplex communication in cognitive radio networks: A survey. IEEE Commun. Surv. Tuts. 2017, 19, 2158–2191. [Google Scholar] [CrossRef]
- Shang, Z.; Zhang, T.; Cai, Y.; Liu, Y.; Yang, W. Secure Spectrum-Sharing Wiretap Networks With Full-Duplex Relaying. IEEE Access 2019, 7, 181610–181625. [Google Scholar] [CrossRef]
- Nguyen, N.; Kundu, C.; Ngo, H.Q.; Duong, T.Q.; Canberk, B. Secure full-duplex small-cell networks in a spectrum sharing environment. IEEE Access 2016, 4, 3087–3099. [Google Scholar] [CrossRef]
- Li, M.; Huang, Y.; Yin, H.; Wang, Y.; Cai, C. Improving the security and spectrum efficiency in overlay cognitive full-duplex wireless networks. IEEE Access 2019, 7, 68359–68372. [Google Scholar] [CrossRef]
- Zhang, J.; Pan, G.; Wang, H. On physical-layer security in underlay cognitive radio networks with full-duplex wireless-powered secondary system. IEEE Access 2016, 4, 3887–3893. [Google Scholar] [CrossRef]
- Goel, S.; Negi, R. Guaranteeing secrecy using artificial noise. IEEE Trans. Wirel. Commun. 2008, 7, 2180–2189. [Google Scholar] [CrossRef]
- Yang, N.; Elkashlan, M.; Duong, T.Q.; Yuan, J.; Malaney, R. Optimal transmission with artificial noise in MISOME wiretap channels. IEEE Trans. Veh. Technol. 2016, 65, 2170–2181. [Google Scholar] [CrossRef]
- Al-Nahari, A.; Geraci, G.; Al-Jamali, M.; Ahmed, M.H.; Yang, N. Beamforming with artificial noise for secure MISOME cognitive radio transmissions. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1875–1889. [Google Scholar] [CrossRef]
- Tolossa, Y.J.; Vuppala, S.; Kaddoum, G.; Abreu, G. On the uplink secrecy capacity analysis in D2D-enabled cellular network. IEEE Syst. J. 2018, 12, 2297–2307. [Google Scholar] [CrossRef]
- Zhou, F.; Chu, Z.; Sun, H.; Hu, R.Q.; Hanzo, L. Artificial noise aided secure cognitive beamforming for cooperative MISO-NOMA using SWIPT IEEE J. Sel. Areas Commun. 2018, 36, 918–931. [Google Scholar] [CrossRef]
- Koyluoglu, O.O.; Koksal, C.E.; el Gamal, H. On secrecy capacity scaling in wireless networks. IEEE Trans. Inf. Theory 2012, 58, 3000–3015. [Google Scholar] [CrossRef]
- Cai, C.; Cai, Y.; Zhou, X.; Yang, W.; Yang, W. When does relay transmission give a more secure connection in wireless ad hoc networks. IEEE Trans. Inf. Forensics Secur. 2014, 9, 624–632. [Google Scholar] [CrossRef]
- Kong, L.; Vuppala, S.; Kaddoum, G. Secrecy analysis of random MIMO wireless networks 0ver α-μ fading channels. IEEE Trans. Veh. Technol. 2018, 67, 11654–11666. [Google Scholar] [CrossRef]
- Zou, Y.; Wang, X.; Shen, W. Optimal relay selection for physical-layer security in cooperative wireless networks. IEEE J. Sel. Areas Commun. 2013, 31, 2099–2111. [Google Scholar] [CrossRef]
- Li, L.; Chen, Z.; Zhang, D.; Fang, J. A full-duplex Bob in the MIMO gaussian wiretap channel: Scheme and performance. IEEE Signal Process. Lett. 2016, 23, 107–111. [Google Scholar] [CrossRef]
- Hoang, T.M.; Duong, T.Q.; Suraweera, H.A.; Tellambura, C.; Poor, H.V. Cooperative beamforming and user selection for improving the security of relay-aided systems. IEEE Trans. Commun. 2015, 63, 5039–5051. [Google Scholar] [CrossRef]
- Chen, G.; Coon, J.P.; di Renzo, M. Secrecy outage analysis for downlink transmissions in the presence of randomly located eavesdroppers. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1195–1206. [Google Scholar] [CrossRef]
- Elkashlan, M.; Wang, L.; Duong, T.Q.; Karagiannidis, G.K.; Nallanathan, A. On the security of cognitive radio networks. IEEE Trans. Veh. Technol. 2015, 64, 3790–3795. [Google Scholar] [CrossRef]
- Tang, X.; Cai, Y.; Yang, W.; Huang, Y.; Duong, T.Q.; Yang, W. Secrecy outage analysis of buffer-aided multi-antenna relay systems without eavesdropper’s CSI. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar]
- Zhong, C.; Jiang, X.; Qu, F.; Zhang, Z. Multi-Antenna Wireless Legitimate Surveillance Systems: Design and Performance Analysis. IEEE Trans. Wirel. Commun. 2017, 16, 4585–4599. [Google Scholar] [CrossRef]
- Basilevsky, A. Applied Matrix Algebra in the Statistical Sciences; Courier Corporation: North Chelmsford, MA, USA, 2013. [Google Scholar]
- Shang, Z.; Zhang, T.; Liu, Y.; Cai, Y.; Yang, W. Secrecy Performance Analysis of Cognitive Radio Networks with Full-duplex Relaying. In Proceedings of the 2019 IEEE 8th CIC International Conference on Communications in China (ICCC), Changchun, China, 11–13 August 2019; pp. 700–705. [Google Scholar]
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series, and Products, 7th ed.; Academic: San Diego, CA, USA, 2007. [Google Scholar]
- Yang, M.; Zhang, B.; Huang, Y.; Yang, N.; Costa, D.B.d.; Guo, D. Secrecy enhancement of multiuser MISO networks using OSTBC and artificial noise. IEEE Trans. Veh. Technol. 2017, 66, 11394–11398. [Google Scholar] [CrossRef]
- Wang, Y.; Zhang, T.; Yang, W.; Guo, J.; Liu, Y.; Shang, X. Secure transmission for differential quadrature spatial modulation with artificial noise. IEEE Access 2019, 7, 7641–7650. [Google Scholar] [CrossRef]
- Hu, J.; Cai, Y.; Yang, N.; Yang, W. A new secure transmission scheme with outdated antenna selection. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2435–2446. [Google Scholar] [CrossRef]
- Afana, A.; Asghari, V.; Ghrayeb, A.; Affes, S. Cooperative relaying in spectrum-sharing systems with beamforming and interference constraints. In Proceedings of the 2012 IEEE 13th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Cesme, Turkey, 17–20 June 2012; pp. 429–433. [Google Scholar]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).