Detection of Misconfigured BYOD Devices in Wi-Fi Networks
Abstract
1. Introduction
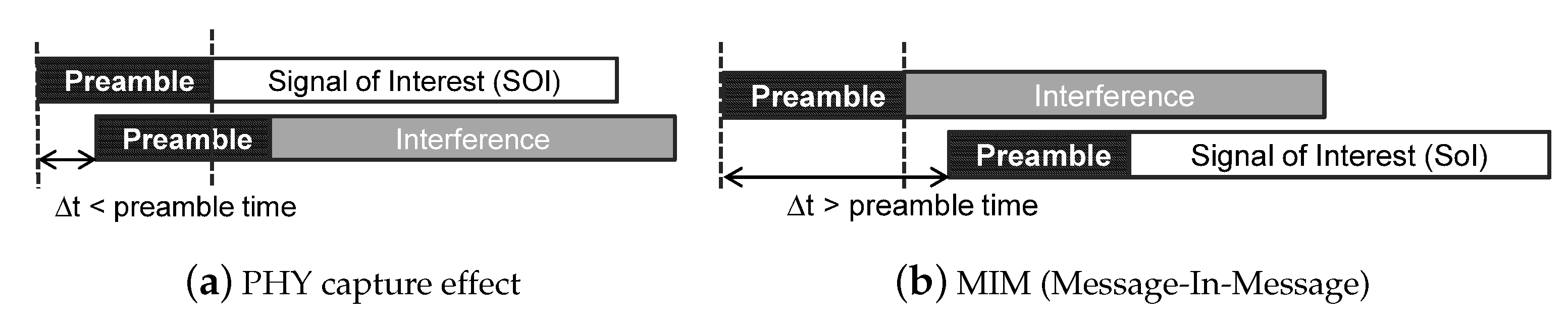
- We observe that concurrent transmission mechanisms, e.g., PHY capture or message-in-message (MIM), can be abused by selfish nodes, and study the impact of the selfish Wi-Fi tethering behavior on the throughput performance of other nearby well-behaving nodes.
- We propose a selfish misbehavior detection mechanism, called CUBIA, which can accurately identify the cause of frame losses and detect selfish behavior under strict detection latency requirements.
- We design a two-step detection process using an online change detection algorithm, i.e., CUSUM, which is based on passive monitoring of frame loss rates at multiple APs. We also study the impact of detection thresholds on detection latency/accuracy performance.
- We perform extensive simulation-based evaluation for various network conditions. Our evaluation results show that CUBIA can promptly detect selfish behavior with high accuracy in realistic wireless environments.
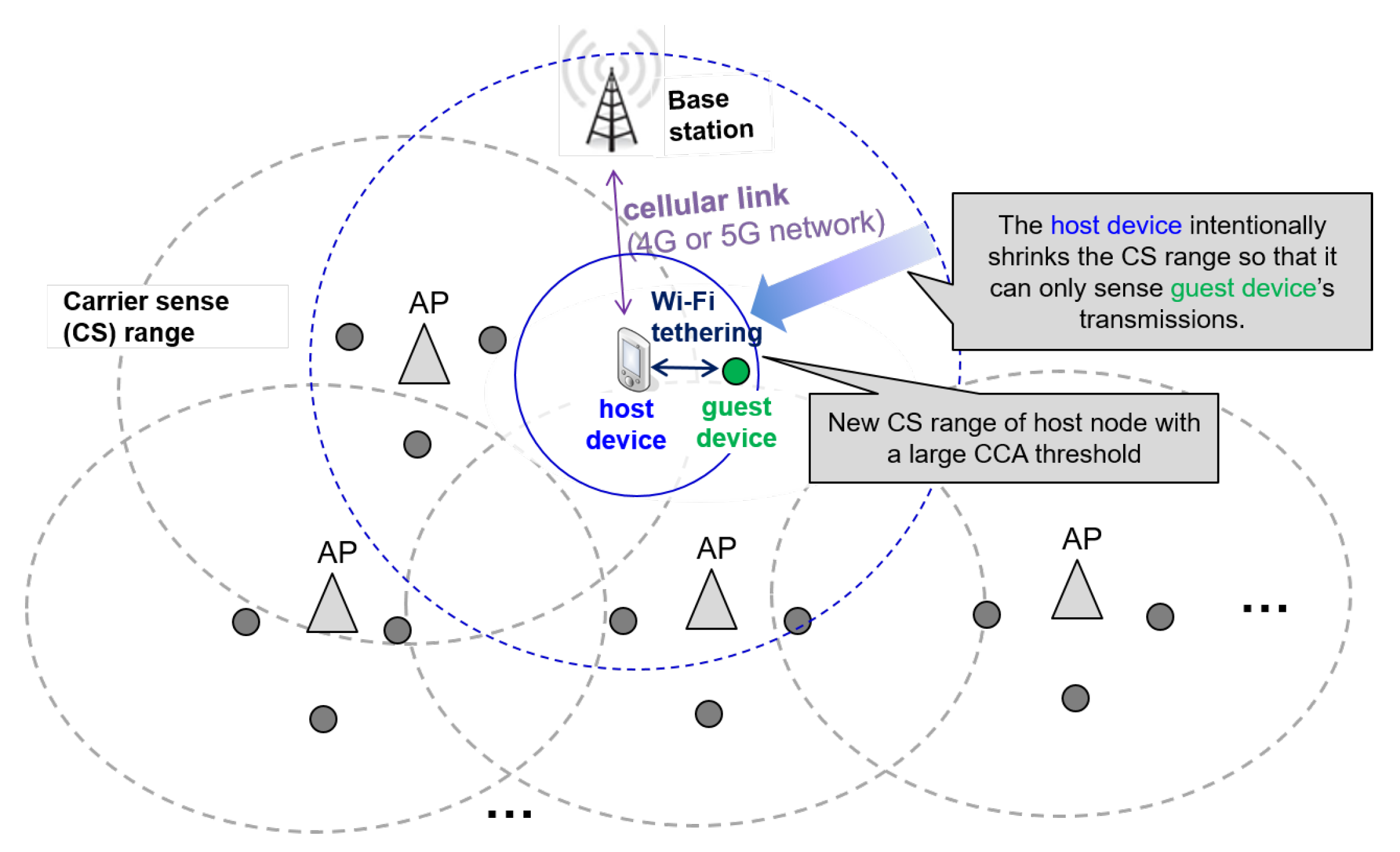
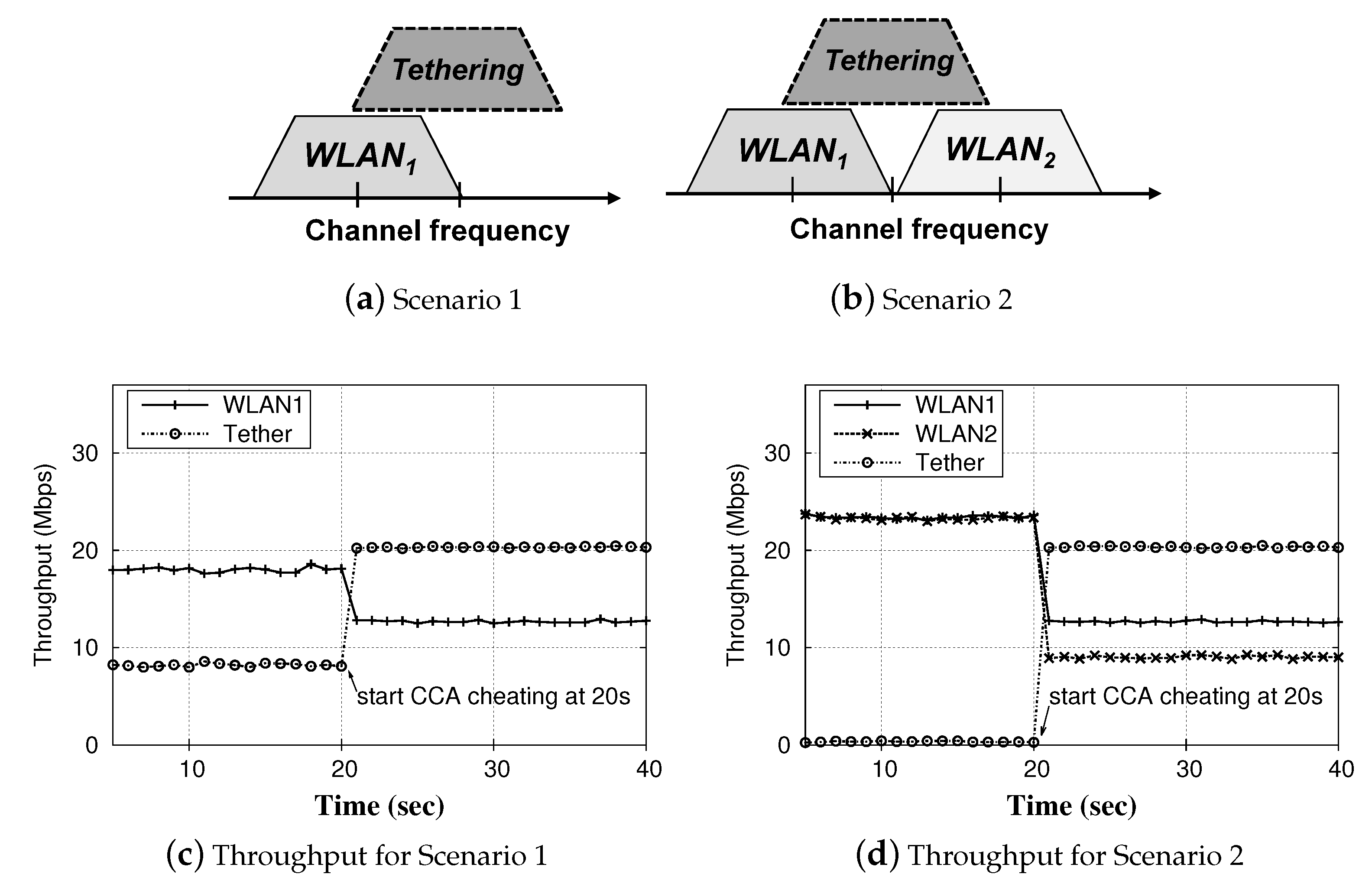
2. Selfish Configuration in Unauthorized Wi-Fi Tethering
2.1. System Model and Assumption
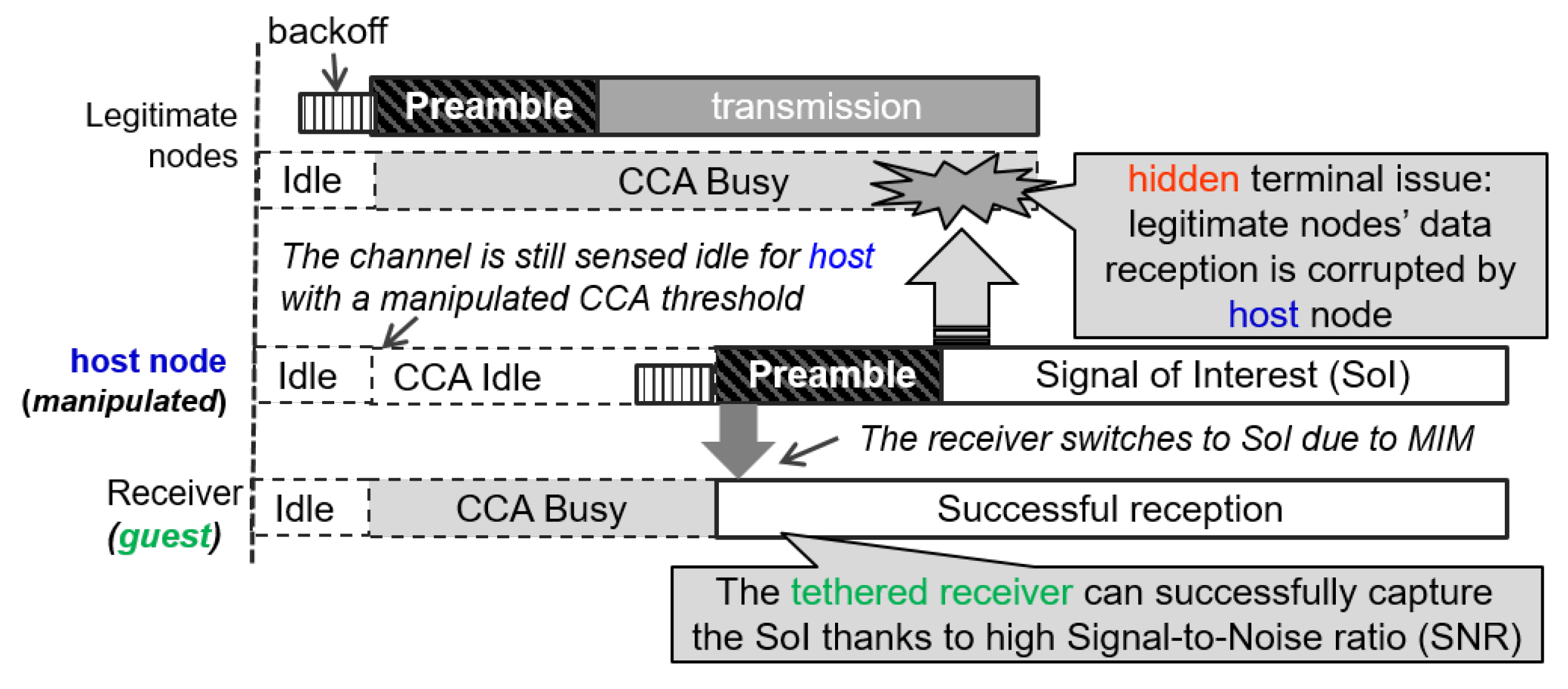
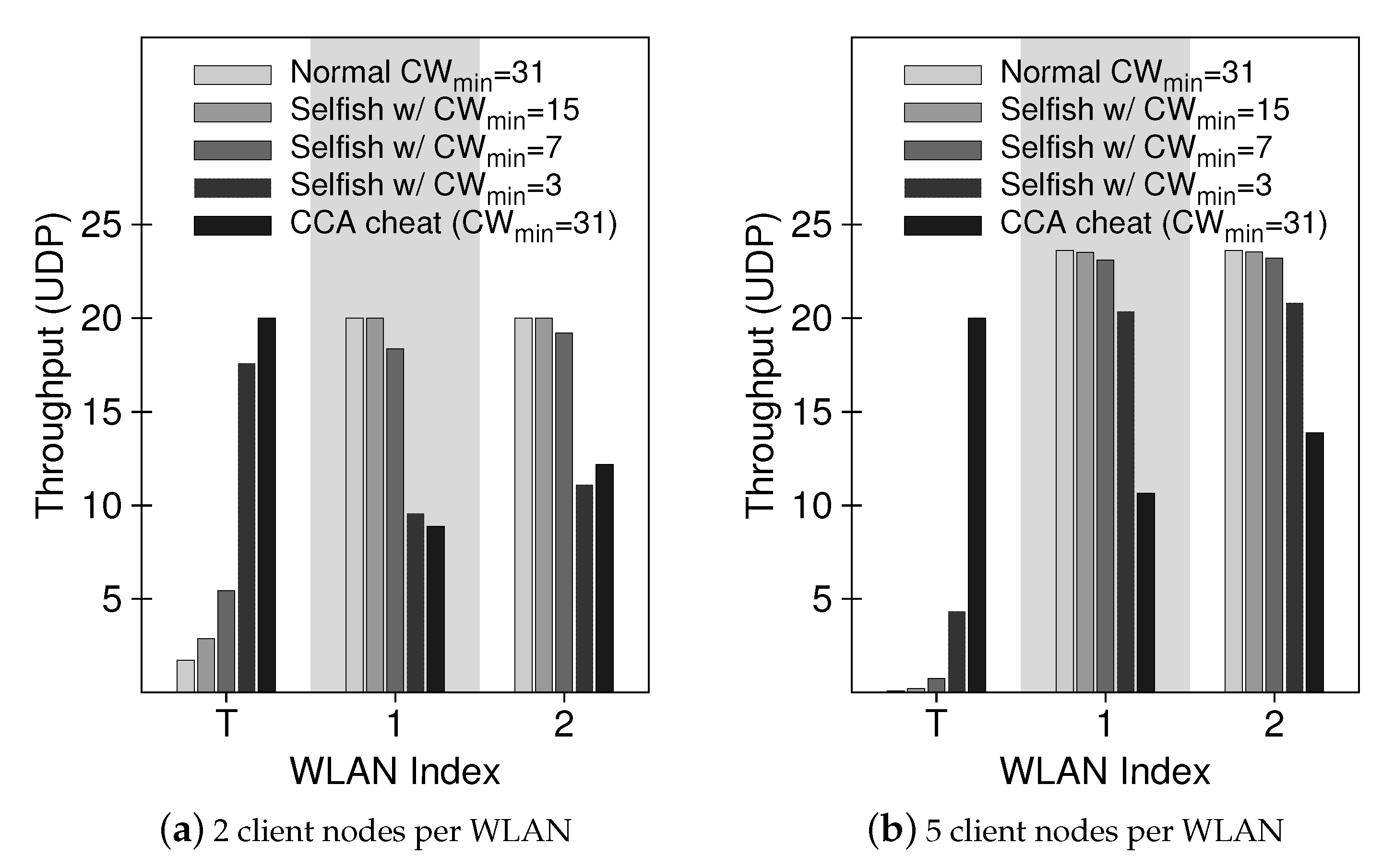
2.2. Selfish Configuration in Wi-Fi Tethering
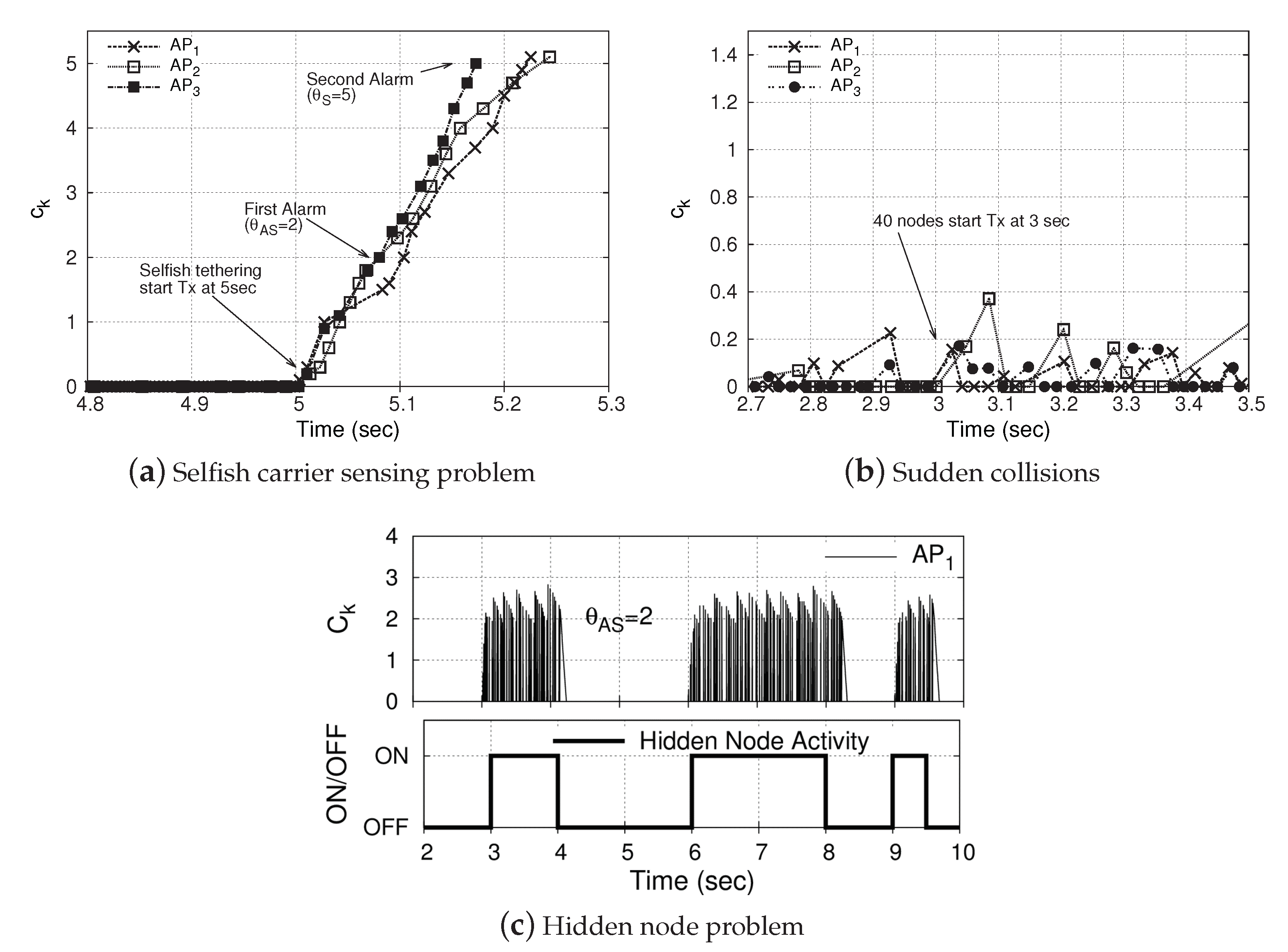
3. A Proposed Online Detection Algorithm
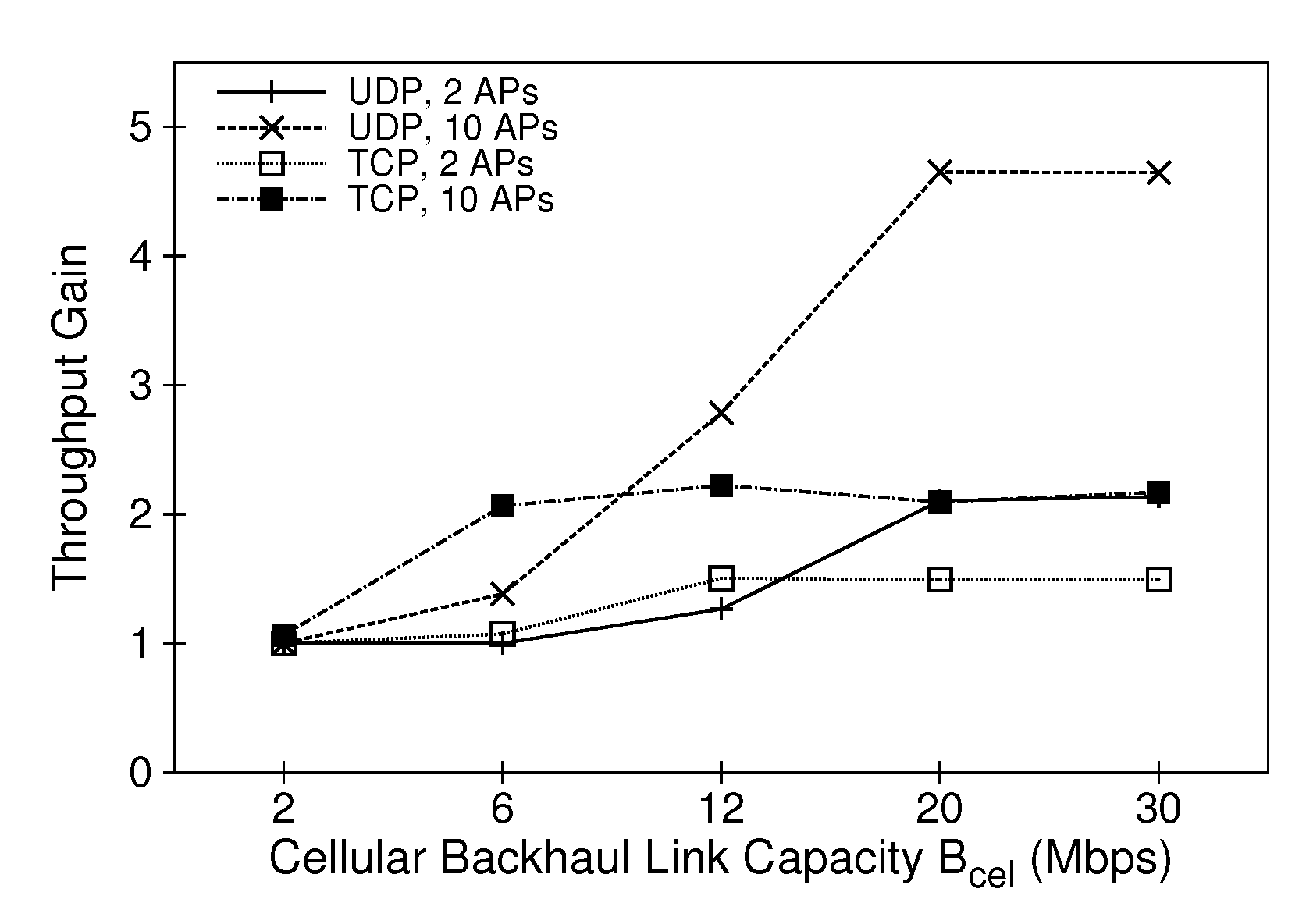
4. Performance Evaluation
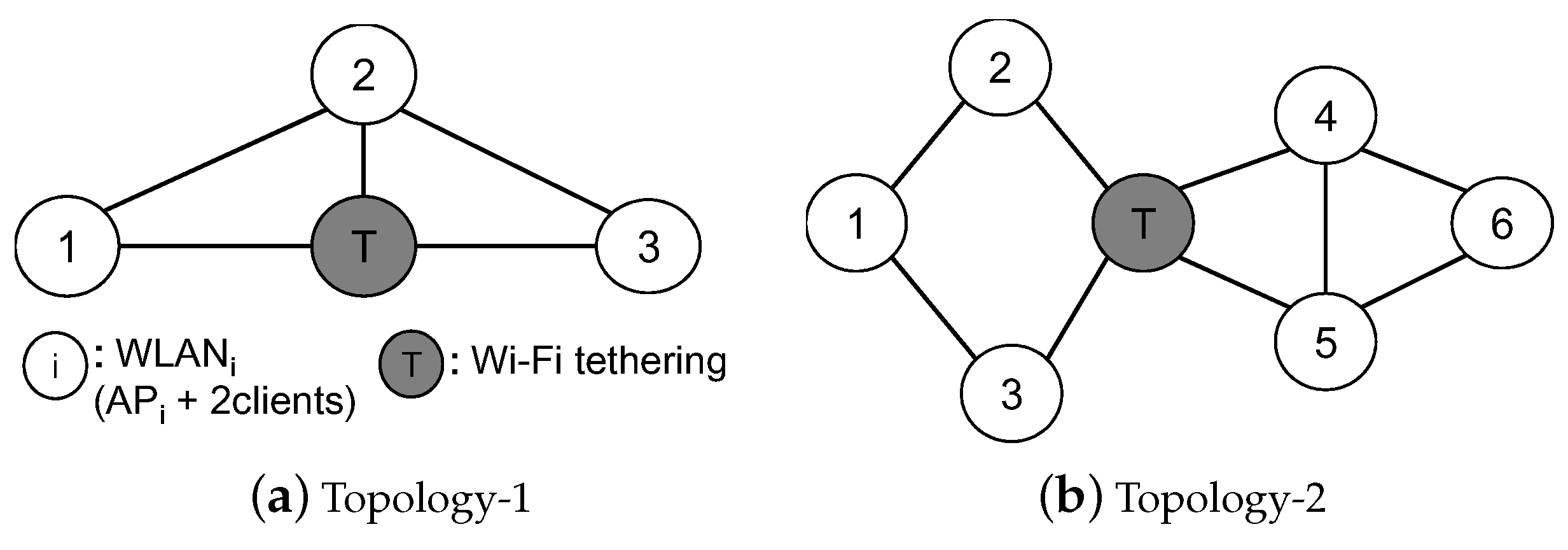
4.1. Simulation Setup
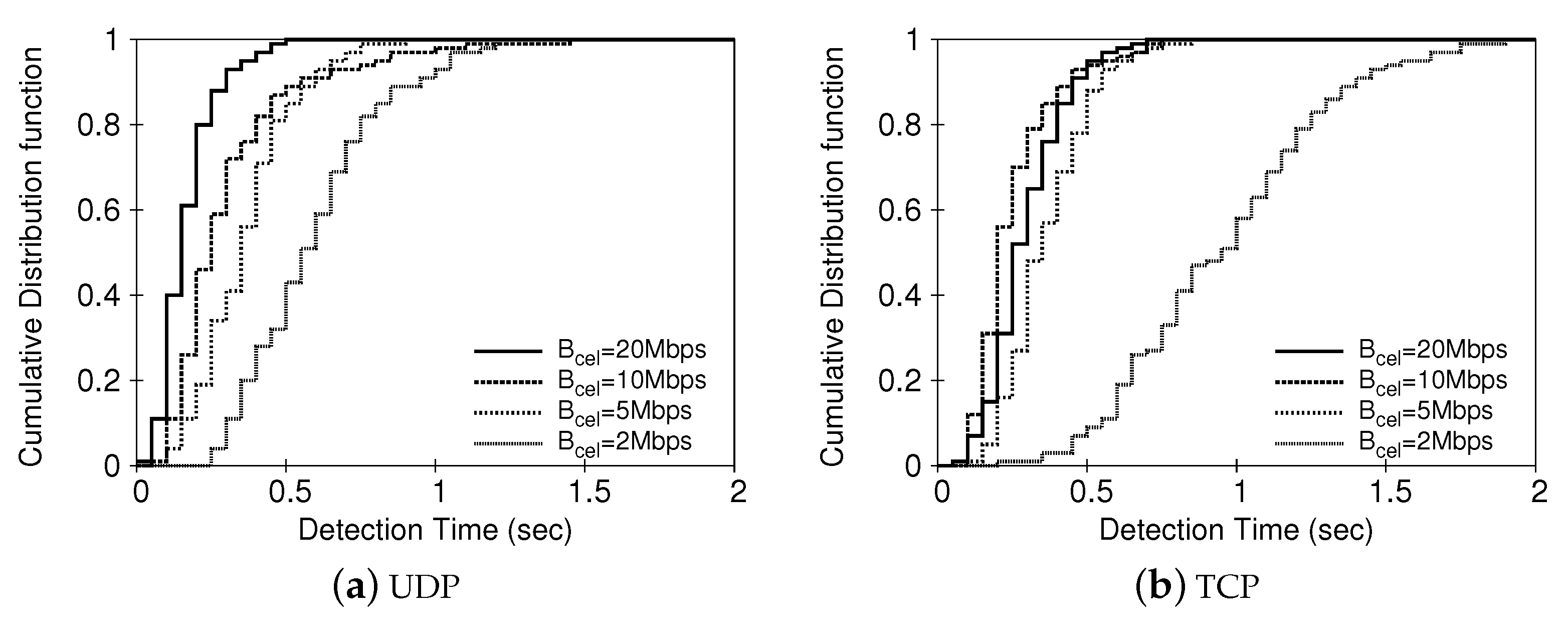
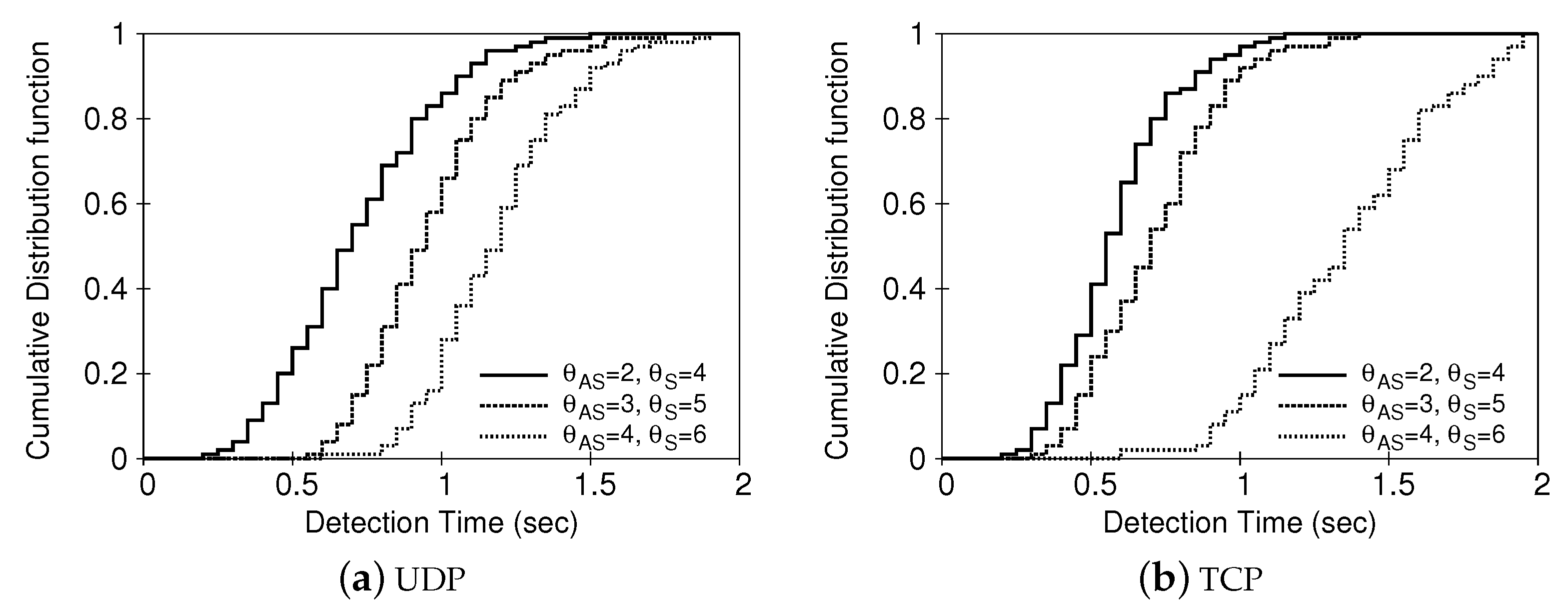
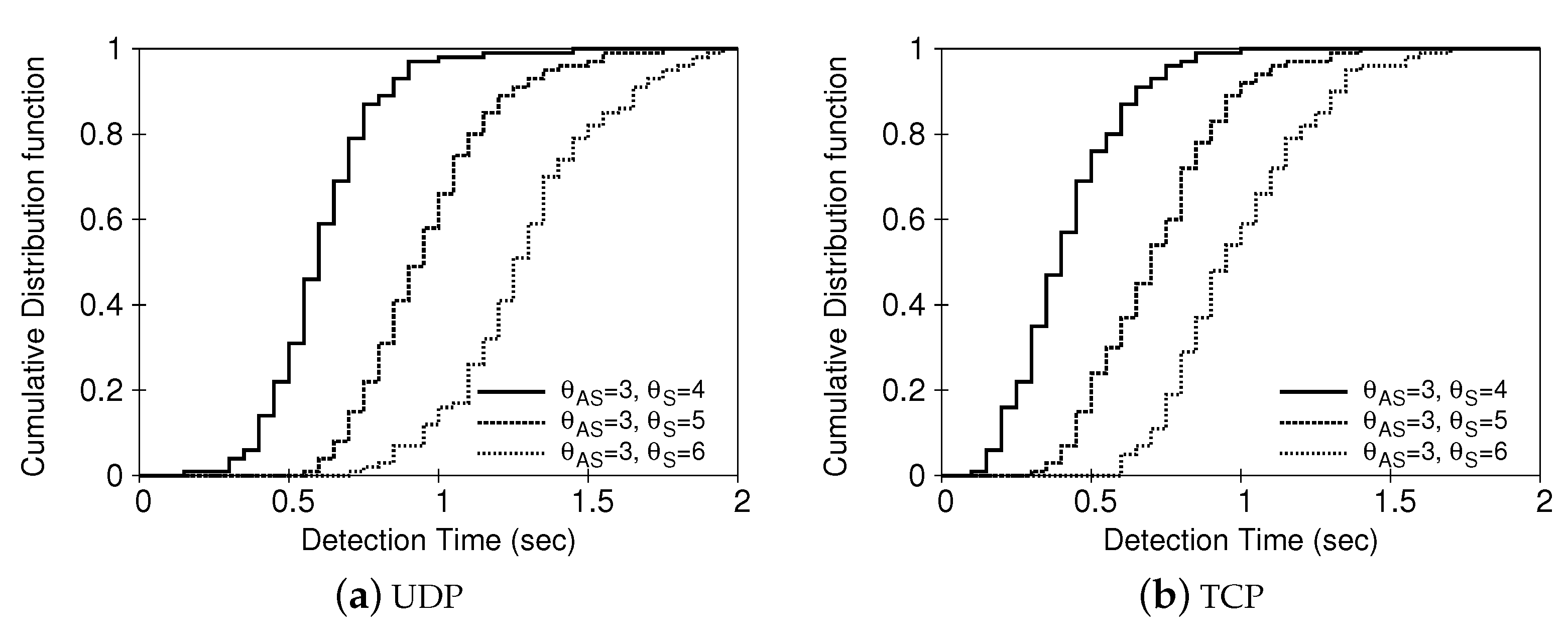
4.2. Detection Performance
4.2.1. Accuracy of Frame Loss Differentiation
4.2.2. Detection Performance
5. Related Work
6. Conclusions and Future Work
Funding
Conflicts of Interest
Abbreviations
| AP | Access Point |
| CCA | Clear channel assessment |
| CST | Carrier sensing threshold |
| CUSUM | cumulative sum |
| FER | frame error rate |
| MIM | Message-In-Message |
| SIR | signal to interference ratio |
| SoI | the Signal of Interest |
| WLAN | Wireless LAN |
| SIR threshold for modulation scheme m | |
| MIM threshold for modulation scheme m | |
| target frame error rate |
References
- Bitglass. 2018 BYOD Security Report. Available online: https://pages.bitglass.com/MissionImpossibleSecuringBYOD_LP.html (accessed on 1 August 2020).
- Syntonic. Syntonic 2016 Employer Report: BYOD Usage in the Enterprise. Available online: https://syntonic.com/wp-content/uploads/2016/09/Syntonic-2016-BYOD-Usage-in-the-Enterprise.pdf (accessed on 1 August 2020).
- Hoffman, C.; Summerson, C. How to Tether Your Android Phone and Share Its Internet Connection with Other Devices. Available online: https://www.howtogeek.com/170302/the-htg-guide-to-tethering-your-android-phone/ (accessed on 1 August 2020).
- Doherty, J. Wireless and Mobile Device Security; Jones & Bartlett Publishers: Boston, MA, USA, 2015. [Google Scholar]
- Khorov, E.; Kiryanov, A.; Lyakhov, A.; Bianchi, G. A Tutorial on IEEE 802.11ax High Efficiency WLANs. IEEE Commun. Surv. Tutor. 2019, 21, 197–216. [Google Scholar] [CrossRef]
- Aijaz, A.; Kulkarni, P. On performance evaluation of dynamic sensitivity control techniques in next-generation wlans. IEEE Syst. J. 2019, 13, 1324–1327. [Google Scholar] [CrossRef]
- Wang, W.; Zhang, F.; Zhang, Q. Managing channel bonding with clear channel assessment in 802.11 networks. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–6. [Google Scholar]
- Choi, J.; Shin, K.G. Out-of-band sensing with ZigBee for dynamic channel assignment in on-the-move hotspots. In Proceedings of the 2011 19th IEEE International Conference on Network Protocols, Vancouver, BC, Canada, 17–20 October 2011; pp. 216–225. [Google Scholar]
- Leentvaar, K.; Flint, J. The capture effect in FM receivers. IEEE Trans. Commun. 1976, 24, 531–539. [Google Scholar] [CrossRef]
- Lee, J.; Kim, W.; Lee, S.; Jo, D.; Ryu, J.; Kwon, T.T.; Choi, Y. An experimental study on the capture effect in 802.11a networks. In Proceedings of the Second ACM InternationalWorkshop onWireless Network Testbeds, Experimental Evaluation and Characterization, Montreal, QC, Canada, 9–14 September 2007; pp. 19–26. [Google Scholar]
- Manweiler, J.; Santhapuri, N.; Sen, S.; Choudhury, R.; Nelakuditi, S.; Munagala, K. Order matters: Transmission reordering in wireless networks. IEEE/ACM Trans. Netw. 2012, 20, 353–366. [Google Scholar] [CrossRef]
- The Network Simulator-ns2. Available online: www.isi.edu/nsnam/ns (accessed on 3 September 2018).
- Wiggle: Wireless Geographic Logging Engine. Available online: http://www.wigle.net/ (accessed on 3 September 2018).
- Garetto, M.; Salonidis, T.; Knightly, E.W. Modeling per-flow throughput and capturing starvation in csma multi-hop wireless networks. IEEE/ACM Trans. Netw. 2008, 16, 864–877. [Google Scholar] [CrossRef]
- Choi, J.; Shin, K.G. QoS provisioning for large-scale multi-AP WLANs. Ad Hoc Netw. 2012, 10, 174–185. [Google Scholar] [CrossRef][Green Version]
- Zhang, X.; Shin, K.G. Adaptive subcarrier nulling: Enabling partial spectrum sharing in wireless lans. In Proceedings of the 2011 19th IEEE International Conference on Network Protocols, Vancouver, BC, Canada, 17–20 October 2011; pp. 311–320. [Google Scholar]
- Mishra, A.; Rozner, E.; Banerjee, S.; Arbaugh, W. Exploiting partially overlapping channels in wireless networks: Turning a peril into an advantage. In Proceedings of the 5th ACM SIGCOMM Conference on Internet Measurement, Berkeley, CA, USA, 19–21 October 2005; p. 29. [Google Scholar]
- Kyasanur, P.; Vaidya, N.H. Selfish MAC layer misbehavior in wireless networks. IEEE Trans. Mob. Comput. 2005, 4, 502–516. [Google Scholar] [CrossRef]
- Gustafsson, F. Adaptive Filtering and Change Detection; John Wiley & Sons, Ltd.: London, UK, 2000. [Google Scholar]
- Kim, J.; Kim, S.; Choi, S.; Qiao, D. CARA: Collision-aware rate adaptation for IEEE 802.11 WLANs. In Proceedings of the IEEE INFOCOM 2006, Barcelona, Spain, 23–29 April 2006; pp. 1–11. [Google Scholar]
- Jensen, T.; Kant, S.; Wehinger, J.; Fleury, B. Fast link adaptation for MIMO OFDM. IEEE Trans. Veh. Technol. 2000, 59, 3766–3778. [Google Scholar] [CrossRef]
- Joshi, K.; Hong, S.; Katti, S. PinPoint: Localizing interfering radios. In Proceedings of the 10th USENIX NSDI, Lombard, IL, USA, 2–5 April 2013; pp. 241–254. [Google Scholar]
- Raya, M.; Aad, I.; Hubaux, J.-P.; Fawal, A.E. DOMINO: Detecting MAC layer greedy behavior in IEEE 802.11 hotspots. IEEE Trans. Mob. Comput. 2006, 5, 1691–1705. [Google Scholar] [CrossRef]
- Radosavac, S.; Baras, J.; Koutsopoulos, I. A Framework for MAC Protocol Misbehavior Detection in Wireless Networks. In Proceedings of the WiSE05: 2005 ACM Workshop on Wireless Security (Co-Located with Mobicom 2005 Conference), Cologne, Germany, 2 September 2005; pp. 33–42. [Google Scholar]
- Toledo, A.; Wang, X. Robust Detection of Selfish Misbehavior in Wireless Networks. IEEE J. Sel. Areas Commun. 2007, 25, 1124–1134. [Google Scholar] [CrossRef]
- Tang, J.; Cheng, Y. Selfish Misbehavior Detection in 802.11 Based Wireless Networks: An Adaptive Approach Based on Markov Decision Process. In Proceedings of the IEEE INFOCOM, Turin, Italy, 14–19 April 2013; pp. 1357–1365. [Google Scholar]
- Samy, I.; Lazos, L.; Xiao, Y.; Li, M.; Krunz, M. LTE misbehavior detection in Wi-Fi/LTE coexistence under the LAA-LTE standard. In Proceedings of the 11th ACM Conference on Security & Privacy in Wireless and Mobile Networks (WiSec’18), Stockholm, Sweden, 18–20 June 2018; pp. 87–98. [Google Scholar]
- Liew, J.T.; Hashim, F.; Sali, A.; Rasid, A.; Cumanan, K. Performance Evaluation of Backoff Misbehaviour in IEEE 802.11ah Using Evolutionary Game Theory. In Proceedings of the 2019 IEEE 89th Vehicular Technology Conference (VTC2019-Spring), Kuala Lumpur, Malaysia, 28 April–1 May 2019; pp. 1–7. [Google Scholar]
- Szott, S.; Konorski, J. Selfish Attacks in Two-Hop IEEE 802.11 Relay Networks: Impact and Countermeasures. IEEE Wirel. Commun. Lett. 2018, 7, 658–661. [Google Scholar] [CrossRef]
- BenSalem, N.; Buttyan, L.; Hubaux, J.P.; Jakobsson, M. A Charging and Rewarding Scheme for Packet Forwarding in Multihop Cellular Networks. In Proceedings of the 4th ACM International Symposium on Mobile Ad Hoc Networking & Computing (MobiHoc), Annapolis, MD, USA, 1–3 June 2003; pp. 13–24. [Google Scholar]
- Pu, C.; Lim, S.; Chae, J.; Jung, B. Active detection in mitigating routing misbehavior for MANETs. Wirel. Netw. 2017, 25, 1669–1683. [Google Scholar] [CrossRef]
- Zhang, Y.; Lazos, L. Countering selfish misbehavior in multi-channel MAC protocols. In Proceedings of the IEEE INFOCOM, Turin, Italy, 14–19 April 2013; pp. 2787–2795. [Google Scholar]
- Akella, A.; Seshan, S.; Karp, R.; Shenker, S. Selfish Behavior and Stability of the Internet: A Game-Theoretic Analysis of TCP. In Proceedings of the ACM SIGCOMM, Pittsbugh, PA, USA, 19–23 August 2002; pp. 117–130. [Google Scholar]
- Gao, Y.; Roy, S. Achieving Proportional Fairness for LTE-LAA and Wi-Fi Coexistence in Unlicensed Spectrum. IEEE Trans. Wirel. Commun. 2020, 19, 3390–3404. [Google Scholar] [CrossRef]
- Yang, E.; Choi, J.; Lee, S. On selfish behavior using asymmetric carrier sensing in IEEE 802.11 wireless networks. In Proceedings of the 2008 33rd IEEE Conference on Local Computer Networks (LCN), Montreal, QC, Canada, 14–17 October 2008; pp. 527–529. [Google Scholar]
- Pelechrinis, K.; Yan, G.; Eidenbenz, S.; Krishnamurthy, S.V. Detecting Selfish Exploitation of Carrier Sensing in 802.11 Networks. In Proceedings of the IEEE INFOCOM, Rio de Janeiro, Brazil, 19–25 April 2009; pp. 657–665. [Google Scholar]
- Afaqui, M.; Brown, S.; Farrell, R. Detecting MAC Misbehavior of IEEE 802.11 Devices within Ultra Dense Wi-Fi Networks. In Proceedings of the 2018 25th International Conference on Telecommunications (ICT), St. Malo, France, 26–28 June 2018; pp. 213–219. [Google Scholar]


| Topology | Collision Prob. | Capture Effect | MIM |
|---|---|---|---|
| 1 | 71.5 | 17.9 | 53.6 |
| 2 | 91.8 | 28.3 | 63.5 |
| Parameter | Value |
|---|---|
| Transmission range | 75 |
| Carrier range | 150 |
| Data rate/ACK rate | 54 Mbps/6 Mbps |
| CBR rate per AP-client pair (UDP) | 20 Mbps |
| payload size of UDP, TCP | 1000, 1500 bytes |
| (in Equation (3)) | 0.05 |
| (in Equation (1)) | 0.1 |
| m (number of transmissions for in Equation (1)) | 10 |
| the maximum allowed latency of detection | 2 s |
| () | 20 Mbps | 10 Mbps | 5 Mbps | 2 Mbps |
|---|---|---|---|---|
| (2, 3) | 1.00 | 1.00 | 0.99 | 0.73 |
| (2, 4) | 1.00 | 1.00 | 0.99 | 0.74 |
| (2, 5) | 1.00 | 1.00 | 0.97 | 0.61 |
| (3, 4) | 1.00 | 0.94 | 0.05 | 0.00 |
| (3, 5) | 1.00 | 0.93 | 0.07 | 0.00 |
| (3, 6) | 0.99 | 0.92 | 0.07 | 0.00 |
| (4, 5) | 1.00 | 0.27 | 0.00 | 0.00 |
| (4, 6) | 1.00 | 0.33 | 0.00 | 0.00 |
| (4, 7) | 0.95 | 0.27 | 0.00 | 0.00 |
| () | 20 Mbps | 10 Mbps | 5 Mbps | 2 Mbps |
|---|---|---|---|---|
| (2, 3) | 1.00 | 1.00 | 1.00 | 0.99 |
| (2, 4) | 1.00 | 1.00 | 1.00 | 0.47 |
| (2, 5) | 1.00 | 1.00 | 1.00 | 0.03 |
| (3, 4) | 1.00 | 1.00 | 0.99 | 0.80 |
| (3, 5) | 1.00 | 1.00 | 0.98 | 0.28 |
| (3, 6) | 1.00 | 1.00 | 0.93 | 0.03 |
| (4, 5) | 0.87 | 0.86 | 0.11 | 0.01 |
| (4, 6) | 0.84 | 0.84 | 0.07 | 0.00 |
| (4, 7) | 0.63 | 0.72 | 0.02 | 0.00 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Choi, J. Detection of Misconfigured BYOD Devices in Wi-Fi Networks. Appl. Sci. 2020, 10, 7203. https://doi.org/10.3390/app10207203
Choi J. Detection of Misconfigured BYOD Devices in Wi-Fi Networks. Applied Sciences. 2020; 10(20):7203. https://doi.org/10.3390/app10207203
Chicago/Turabian StyleChoi, Jaehyuk. 2020. "Detection of Misconfigured BYOD Devices in Wi-Fi Networks" Applied Sciences 10, no. 20: 7203. https://doi.org/10.3390/app10207203
APA StyleChoi, J. (2020). Detection of Misconfigured BYOD Devices in Wi-Fi Networks. Applied Sciences, 10(20), 7203. https://doi.org/10.3390/app10207203





