Abstract
Energy harvesting (EH) from radio frequency (RF) signals provides a promising approach for supplying sustainable and convenient energy to low-power Internet of Things (IoT) devices. In this work, we investigate short-packet communications in a full-duplex (FD) relay system, where RF signals from a source are utilized to power an energy-constrained relay through the time switching protocol. Specifically, hardware impairments in each node and residual self-interference caused by FD are jointly considered. To ensure reliable transmission, two antennas are symmetrically arranged according to the position of the relay station, both of which are used for energy harvesting. Furthermore, we explored two practical schemes based on symmetric channel correlation, i.e., an independent channel for energy harvesting and an identical channel for energy harvesting. For both scenarios, we derive closed-form approximations for the overall average block error rate (BLER) and effective throughput. The validity of our analysis is confirmed through computer simulations, demonstrating that the proposed scheme enhances the reliability and throughput of the system compared with the existing scheme in the literature at low transmission rates and transmit signal-to-noise-ratios (SNRs).
1. Introduction
The forthcoming wireless networks are anticipated to facilitate pervasive connectivity for Internet of Things (IoT) devices, in addition to traditional human communication [1]. In practical applications like industrial automation and autonomous vehicles, low latency and high reliability are essential quality-of-service (QoS) prerequisites. To address these needs, the fifth-generation (5G) standardization delineates the use cases for ultra-reliable low-latency communications (URLLC) and prescribes stringent QoS requirements, including a packet error rate not surpassing a delay range of 1 ms [2,3,4]. Achieving low latency fundamentally involves utilizing short-packet transmission. However, within the constraints of finite blocklength mechanisms, even when the transmission rate falls below Shannon’s capacity, the reliability of transmission is no longer arbitrary. Specifically, ref. [5] characterized the correlation between achievable rate, transmission delay, and decoding error probability in short-packet communications. Subsequently, the analysis of short-packet communications has been expanded to encompass diverse system models, e.g., relay systems [6] and multi-user scenarios [7].
Due to the limited energy provided by batteries, IoT devices in 5G systems require alternative power sources [8,9]. Fortunately, various energy harvesting (EH) technologies have been proposed to address this issue, enabling IoT devices to collect energy from sources such as wind, solar, and electromagnetic waves. Among these methods, harvesting energy from radio frequency (RF) signals is particularly advantageous because it allows for controlled energy extraction from signals that also carry information [10,11,12]. Since practical circuits cannot achieve simultaneous data detection and energy harvesting, refs. [13,14,15] proposed two strategies for wireless energy harvesting and information processing. The first strategy is power splitting, where the receiver splits the received signal for information processing and energy harvesting. The second strategy is time switching, where the receiver performs information processing and energy harvesting separately according to time. A multi-agent deep reinforcement learning algorithm was proposed in [16] to jointly maximize energy efficiency and throughput of a Device-to-Device (D2D) communication network. Subsequently, the authors in [17] developed a deep deterministic policy gradient (DDPG) algorithm for a wireless power transfer network integrated with unmanned aerial vehicles (UAV). In particular, harvesting energy from RF signals is well-suited for cooperative networks [18,19,20]. RF signals from a source can be utilized to power an energy-constrained relay, which subsequently assists in transmitting information from the source. This approach not only prolongs the relay’s lifespan but also facilitates information relay.
Recently, full-duplex (FD) technology has been widely applied in cooperative networks, where the ability of the relay to transmit and receive data simultaneously reduces round-trip time in communication processes [21,22,23,24,25,26,27,28,29]. In [21], an FD multi-user two-way communication system was analyzed, and the closed-form expression for the block error rate (BLER) was obtained for an adaptive relaying protocol combining amplify-and-forward (AF) and decode-and-forward (DF). Subsequently, ref. [22] investigated the performance of a cooperative nonorthogonal multiple access (NOMA) short-packet communications system, where a near user serves as an FD relay to facilitate information transmission to a far user. To enhance short-packet communications in multi-hop FD relay networks, ref. [23] incorporated multiple-input multiple-output (MIMO) technology. In scenarios where multiple FD relays assist short-packet communications, ref. [24] developed a deep learning framework capable of achieving accurate performance predictions with significantly lower complexity and faster execution times compared with conventional approaches. In [25], the authors explored the reliability of an energy harvesting FD cooperative network by deriving the closed-form expression for BLER. Subsequently, ref. [26] proposed a relay selection strategy for an IoT network with multiple users, where multiple FD relays are powered by a power beacon. For a multi-FD relay network, ref. [27] aimed to maximize end-to-end signal-to-noise ratio (SNR) and improve throughput by relay selection. The authors in [28] analyzed an energy harvesting multi-user FD communication network aided by a dedicated reconfigurable intelligent surface (RIS), and evaluated its performance via the BLER for finite blocklength transmissions. In [29], the authors conducted a performance analysis of the Age of Information in a FD cooperative NOMA system integrated with simultaneous wireless information and power transfer (SWIPT).
Notably, the previously mentioned studies [21,22,23,24,25,26,27,28,29] on FD relay networks employing short packets all assumed ideal transceiver hardware. However, it is essential to acknowledge the impact of RF impairments stemming from imperfect transceiver hardware, including in-phase/quadrature (I/Q) imbalance, nonlinear power amplifiers, and phase noise, on wireless systems [30,31]. In [31], the authors investigated the impact of hardware impairments on the outage performance in an energy harvesting FD relay network. Considering nonlinear power amplifiers, imperfect channel state information (CSI), hardware impairments, ref. [32] derived closed-form expressions of outage probability for a two-way FD relay network with energy harvesting. The authors in [33] employed a hybrid relaying protocol and a hybrid SWIPT receiver, and examined the outage performance for an overlay FD cooperative cognitive radio network under hardware impairments. For a wireless-powered FD relay network with transceiver hardware impairments, ref. [34] exploited a power beacon to resolve the energy-constraint problem.
Enlightened by the above observations, the objective of this paper is to investigate the reliable performance of a FD relay system, where RF signals from a source are utilized to power an energy-constrained relay through the time switching protocol. Both antennas at the relay are employed for energy harvesting, enhancing the harvested energy to guarantee reliable transmission. In addition, a practical scenario is explored in this work where each node is affected by hardware impairments, in contrast to the prior works [21,22,23,24,25,26,27,28,29] that only accounted for ideal transceiver devices. Differing from [31,32,33,34], where infinite blocklength coding is considered for reliable transmission, we utilize finite blocklength coding to reduce transmission latency. The key contributions of this paper are summarized as follows:
- (1)
- We investigate short-packet communications in an energy-constrained FD relay system with hardware impairments, where both antennas at the relay are employed for energy harvesting. We further explore independent and identical channels for energy harvesting.
- (2)
- We derive closed-form approximations for the overall average BLER and effective throughput under both scenarios, which characterize the impact of key system parameters on the reliable performance of the FD relay system.
- (3)
- We validate our analysis through computer simulations, which demonstrate that the proposed scheme improves the reliability and throughput of the system compared with the existing scheme in the literature at low transmission rates and transmit SNRs.
Table 1 provides a summary of the differences between the contributions of this work and the existing related works.

Table 1.
Comparison of this work with related papers.
The rest of this paper is organized as follows. The system model and transmission scheme are introduced in Section 2. The closed-form expressions for the overall average BLER and effective throughput under the independent and identical channels are derived in Section 3. Numerical results are presented in Section 4 to validate the derived expressions and provide insights into system characteristics. Finally, concluding remarks and potential future research directions are provided in Section 5. For notational convenience, a list of the fundamental variables is provided in Table 2.

Table 2.
List of fundamental variables.
2. System Model
In this work, we consider a dual-hop FD relay wireless communication system illustrated in Figure 1, where a source (S) transmits information to a destination (D) with the assistance of a relay (R). We assume that direct communication from S to D does not exist due to significant distance and severe fading. Additionally, we consider a scenario where R operates without a fixed energy source and relies solely on harvesting energy from received RF signals [13,18,25]. To reduce system implementation complexity, we adopt the time switching protocol for wireless EH and information processing, as depicted in Figure 2. This protocol divides each communication process into two distinct phases: an EH phase and an information transmission phase.
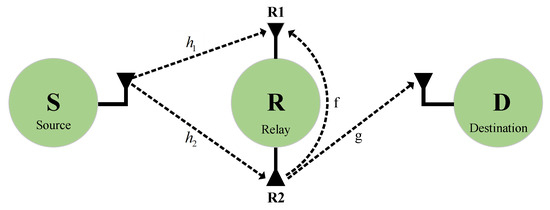
Figure 1.
System model.
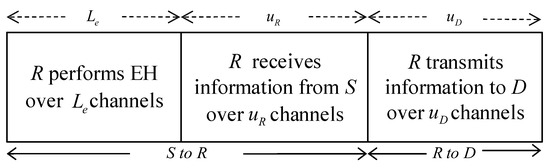
Figure 2.
The time switching protocol.
We assume that R has two antennas to enable FD transmission, while both S and D have a single antenna each. Note that information transmission and EH occur in separate time periods. Thus, to fully capitalize on the advantages of dual antennas at R and enable reliable transmission, EH is performed using both antennas simultaneously during the EH phase. In practical communication systems, spatial correlation among fading channels arises due to the antennas’ limited spacing. Consequently, the EH links in the FD relay system exhibit correlation [35]. This correlation is characterized by a correlation coefficient, which determines the degree of similarity between the two EH links. Motivated by this, we analyze the reliability of the system under two cases: independent channel for energy harvesting and identical channel for energy harvesting.
When energy harvesting links are independent, the harvested energy at R can be expressed as
where is the energy conversion efficiency, is the transmit power of S, is the number of channels used for EH, is the transmission duration of each channel, and are the channel coefficients from S to R. As in [25,36], we assume that all harvested energy is utilized to assist S in forwarding the information, given that transmission power is the primary factor determining energy consumption. Therefore, the transmit power at R is given by
where is the number of channels utilized for information transmission from R to D.
When energy harvesting links are identical, the harvested energy at R can be expressed as
In this case, the transmit power at R is given by
To ensure highly reliable transmission, R employs DF protocol to avoid noise amplification [31,37]. In the DF protocol, R initially decodes the original signal from S and subsequently encodes it for forwarding to D. Hence, the received signals at R and D can be, respectively, expressed as
where is the transmit power of R, and are the normalized signals from S and R, is the self-interference channel at R, is the channel coefficient from R to D, denotes the hardware distortion noise caused by the transmitter of S, denotes the hardware distortion noise caused by the receiver of R, denotes the hardware distortion noise caused by the transmitter of R, denotes the hardware distortion noise caused by the receiver of D, and are the additive white Gaussian noise (AWGN) at R and D, respectively. The parameters and characterize the levels of imperfections in the hardware of transmitter and receiver, respectively [38]. These parameters can be measured by the error vector magnitudes (EVMs). According to 3GPP Long-Term Evolution (LTE) requirements, EVMs typically range from to [39].
Based on (5) and (6), the received SNRs at R and D can be, respectively, formulated as
end
3. Performance Analysis
In this section, we assess the reliability and effectiveness of the FD relay system by analyzing overall average BLER and effective throughput under independent and identical channels. Before proceeding with detailed analysis, we first introduce preliminary concepts on short-packet communications and overall average BLER calculation. Following this, we provide the statistics of the received SNRs at R and D.
3.1. Preliminaries
Considering short-packet communications, the maximum achievable rate of the FD relay system can be given as [5]
where , is the Shannon capacity, is the channel dispersion, is the number of channels utilized for information transmission from S to R, is the instantaneous BLER, is the inverse of the Gaussian Q-function. In the information transmission phase, S sends b bits of information to D, then the maximum achievable rate can be formulated as . Without loss of generality, we assume that and are equal, ensuring that the coding rates of the S-to-R link and R-to-D link are equal [40].
According to (9), the instantaneous BLER can be obtained as
Then, the average BLER can be given as
where is the probability density function (PDF) of the received SNR . Note that directly obtaining a closed-form expression for is mathematically challenging due to the complexity of the Q-function. For analysis feasibility, a linear approximation of the Q-function is adopted [41], which is given by
where , , , . With this tight approximation, we have
Since the DF protocol is used at R, errors can arise from two events: R fails to correctly recover information, and R successfully recovers information but D fails to do so. Thus, the overall average BLER of the FD relay system can be expressed as
3.2. Statistical Characterization of the SNRs
According to (2) and (7), the cumulative density function (CDF) of under the independent channel is given by
where and .
Proof.
See Appendix A. □
According to (2) and (8), the CDF of under the independent channel is given by
where , and is the v-th-order modified Bessel function of the second kind.
Proof.
See Appendix B. □
According to (4) and (7), the CDF of under the identical channel is given by
where .
Proof.
See Appendix C. □
According to (4) and (8), the CDF of under the identical channel is given by
where .
Proof.
See Appendix D. □
3.3. Overall Average BLER Under the Independent Channel
The overall average BLER of the FD relay system under the independent channel can be expressed as
where
end
with , , , , , and N being a parameter for complexity accuracy tradeoff.
Proof.
See Appendix E. □
3.4. Overall Average BLER Under the Identical Channel
The overall average BLER of the FD relay system under the identical channel can be expressed as
where
end
with , , , , , and M being a parameter for complexity accuracy tradeoff.
Proof.
The above result can be readily derived by conducting a similar analysis to that presented in the Appendix E. □
From (19) and (22), it is evident that the overall average BLER equals one when . Here, represents the level of hardware impairments. The values of and depend solely on the transmission rates from S to R and from R to D, respectively. Moreover, both and increase monotonically with the transmission rate. This indicates that, for a given level of hardware impairments, an outage threshold exists, which is entirely dependent on the hardware impairments. Furthermore, reliable communication cannot be achieved if the transmission rate exceeds this threshold, regardless of the transmit SNR.
3.5. Effective Throughput
The effective throughput, as defined in [36], is derived as the transmission rate multiplied by the complementary probability of overall average BLER. Thus, the effective throughput is given by for the independent channel and for the identical channel.
The effective throughput serves as a crucial performance metric by quantifying the number of successfully transmitted bits per channel use. Analysis of effective throughput reveals a significant finding: longer channel lengths used for information transmission enhance reliability but also introduce higher latency and lower transmission rates. This tradeoff results in an optimal number of channels used for information transmission that maximizes effective throughput.
4. Numerical Results and Discussions
In this section, we present Monte Carlo simulations using Matlab to validate our analytical findings and examine the influence of key system parameters on reliability and effectiveness performance. For the Monte Carlo simulations, numerical results are obtained by averaging over channel trials. Unless otherwise stated, some simulation parameters are given in Table 3. Moreover, let denote the transmit SNR.

Table 3.
List of simulation parameters.
Figure 3 plots the overall average BLER and the corresponding percentage reliability improvement compared with the existing scheme in [25] versus the transmit SNR with . In this scenario, we assume a fixed value of b and manipulate the transmission rate by adjusting . It can be observed from Figure 3 that there is excellent agreement between Monte Carlo simulation results and the analytical approximation of overall average BLER, validating our analytical findings. Figure 3 also shows that when , the overall average BLER remains constant at 1 irrespective of the transmit SNR value. This is because there is an outage threshold that solely depends on the level of hardware impairments, and when the transmission rate exceeds this threshold, reliable communication cannot be achieved no matter what the transmit SNR is. Moreover, Figure 3 shows that the overall average BLER first decreases and then reaches a floor as the transmit SNR increases. This is due to the fact that the received SNRs at R and D do not always increase with the transmit SNR, as self-interference and hardware impairments are the primary limiting factors in the high SNR regime. However, when , the overall average BLER under the identical channel decreases continuously as the transmit SNR increases. This is because the floor under the identical channel is close to 0, when . Finally, Figure 3 shows that the proposed scheme enhances the reliability of the system compared with the existing scheme in [25] at low transmission rates and transmit SNRs.
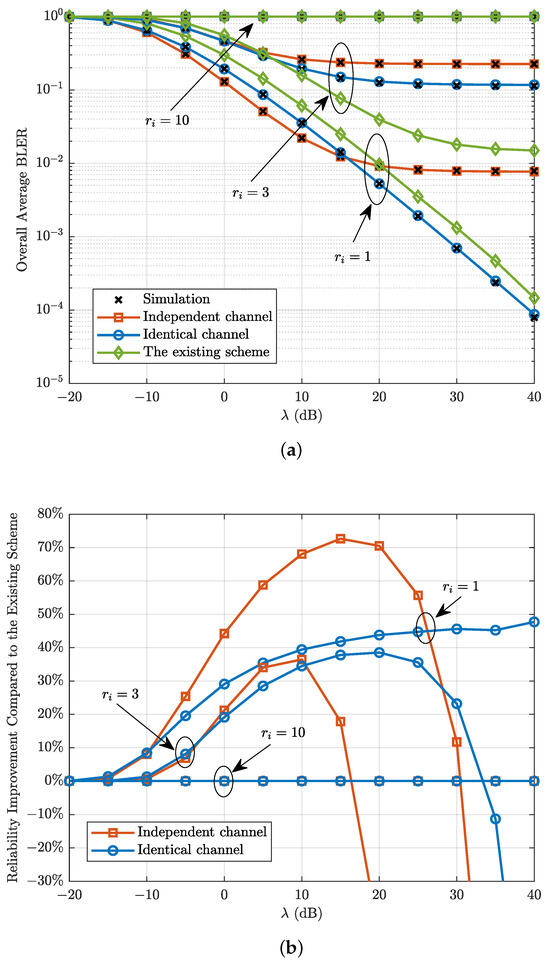
Figure 3.
(a) Overall average BLER and (b) the corresponding percentage reliability improvement compared with the existing scheme in [25] versus the transmit SNR with .
Figure 4 plots the overall average BLER versus the number of channels with dB. It can be observed from Figure 4 that the overall average BLER under the independent channel decreases gradually and slowly with the increase in , while the overall average BLER under the identical channel decreases rapidly with the increase in and remains essentially unchanged when is greater than a certain value. This phenomenon occurs because when b remains constant, increasing reduces the transmission rate, thereby enhancing the reliability of the system. Similarly, when remains constant, reducing b also improves reliability.
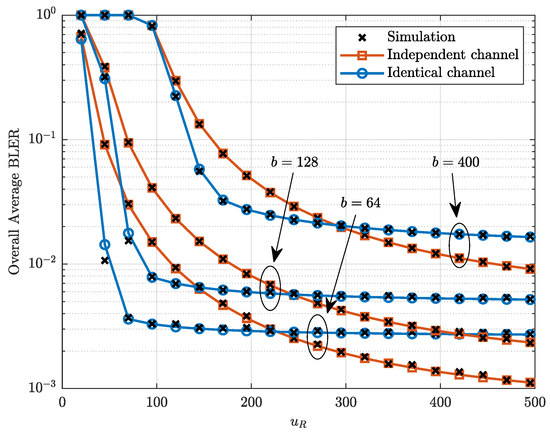
Figure 4.
Overall average BLER versus the number of channels with dB.
Figure 5 plots the overall average BLER versus the level of hardware impairments with and . It can be observed from Figure 5 that increasing the level of hardware impairments leads to a gradual rise in the overall average BLER, eventually approaching 1. When the overall average BLER reaches 1, reliable transmission becomes unattainable. Consequently, in practical systems, it is necessary to rigorously manage hardware impairments. Moreover, Figure 5 shows that higher transmission rates result in the overall average BLER converging to one more rapidly. This phenomenon arises due to a trade-off between transmission rate and hardware impairments. Specifically, with increasing hardware impairments, the system’s ability to maintain reliable transmission diminishes. In addition, Figure 5 also shows that at low transmission rates, the independent channel outperforms the identical channel in terms of the overall average BLER, while at high transmission rates, the identical channel exhibits better performance than the independent channel.
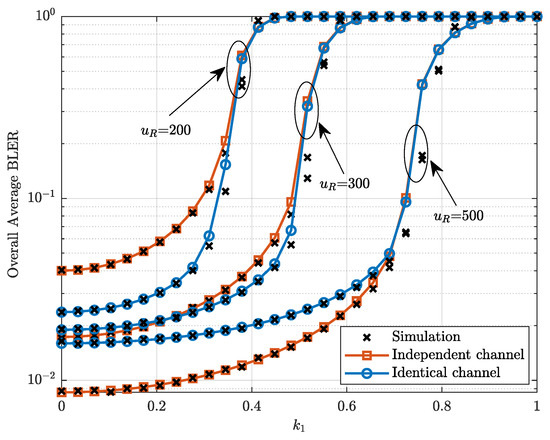
Figure 5.
Overall average BLER versus the level of hardware impairments with and .
Figure 6 plots the overall average BLER versus the number of channels with . It can be observed from Figure 6 that the overall average BLER under the identical channel decreases with the increase in . However, the overall average BLER under the independent channel first decreases and then increases with the increase in when the transmit SNR is high. This phenomenon occurs due to the increase in transmit power of the relay as increases, which enhances the reliability of the destination and compromises the reliability of the relay. The trade-off relationship leads to the existence of an optimal that minimizes the overall average BLER under the independent channel, when the transmit SNR is high. However, in the case of the identical channel, the benefit of increased transmit power at the relay outweigh the drawback, leading to a continuous decrease in the overall average BLER.
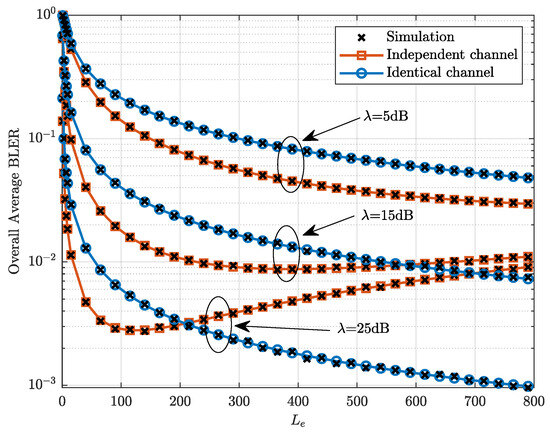
Figure 6.
Overall average BLER versus the number of channels with .
Figure 7 plots the effective throughput versus the number of channels with dB. It can be observed from Figure 7 that as the number of channels increases, the effective throughput initially increases and reaches a maximum value at an optimal number of channels. Beyond this optimal value, the effective throughput begins to decrease. This phenomenon occurs because increasing the number of channels allocates more time to information transmission, which enhances the system’s reliability. However, as the number of channels increases, the system’s transmission rate decreases, which in turn reduces overall efficiency. When the number of channels is below its optimal value, the benefit of increased time for information transmission dominate, leading to higher effective throughput. Once the number of channels exceeds the optimal value, the negative impact of the reduced transmission rate becomes more significant, resulting in decreased effective throughput. Specifically, the optimal increases with the increase in b. This is because the decoding error becomes more significant as the number of transmitted bits b increases. Consequently, the optimal also increases accordingly.
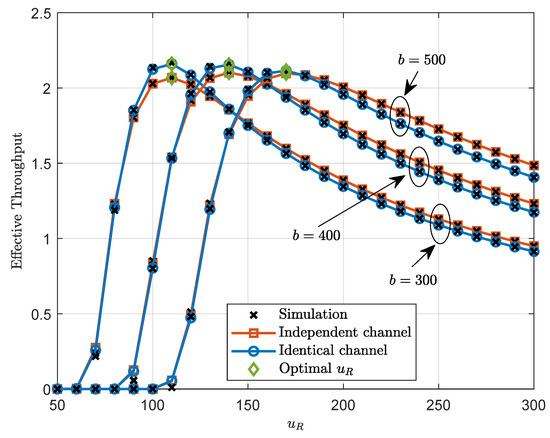
Figure 7.
Effective throughput versus the number of channels with dB.
Figure 8 plots the effective throughput and the corresponding percentage throughput improvement compared with the existing scheme in [25] versus the transmit SNR with different transmission rates, where . It can be observed from Figure 8 that the effective throughput increases as the transmit SNR increases and becomes saturated at high transmit SNR due to the transmission rate constraint. Moreover, the effective throughput floor is improved by increasing the transmission rate. Figure 8 also shows that the smaller the transmission rate, the closer effective throughput floor is to the transmission rate. This is due to the fact that the loss of reliability increases with the increase in transmission rate. Finally, Figure 8 shows that the proposed scheme enhances the throughput of the system compared with the existing scheme in [25] at low transmission rates and transmit SNRs.
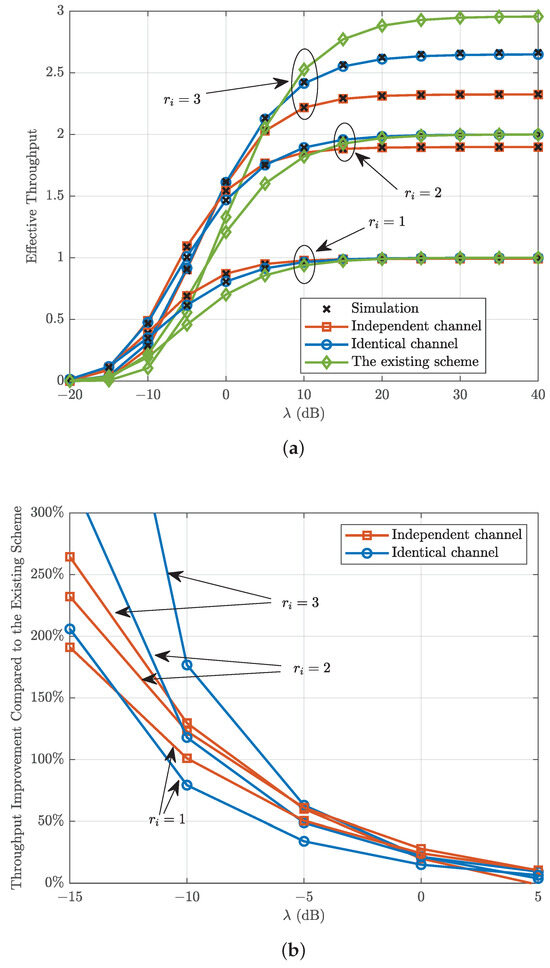
Figure 8.
(a) Throughput and (b) the corresponding percentage throughput improvement compared with the existing scheme in [25] versus the transmit SNR with different transmission rates.
5. Conclusions
In this work, we investigated short-packet communications in a FD relay system, where hardware impairments in each node and residual self-interference caused by FD are jointly considered. Specifically, the relay is an energy-constrained node, which harvests energy from the received RF signals through the time switching protocol. In this case, both antennas at the relay are used for energy harvesting, augmenting the harvested energy to ensure reliable transmission. Additionally, we explore independent and identical channels for energy harvesting based on channel correlation. We derived analytical expressions for two key metrics: the overall average BLER and effective throughput. Our analysis is validated through computer simulations, demonstrating that the proposed scheme enhances the system’s reliability and throughput compared with the existing approach in the literature at low transmission rates and SNRs. Future work will further explore the characteristics of short-packet communications and aim to address more general scenarios and constraints, including the impact of overhead on short-packet communications, full-duplex operation for all users, and non-linear energy harvesting.
Author Contributions
Conceptualization, C.Y.; methodology, C.Y. and D.C.; validation, C.Y.; formal analysis, C.Y.; investigation, M.Y., J.L., and P.J.; resources, J.L. and P.J.; writing—original draft, C.Y. and D.C.; writing—review and editing, C.Y., J.H. and D.C.; visualization, C.Y.; supervision, D.C. and J.L.; project administration, J.H.; funding acquisition, J.H. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the Henan Engineering Research Center of Rare Earth Alloys.
Data Availability Statement
The raw data supporting the conclusions of this article will be made available by the authors on request.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| FD | full-duplex |
| RF | radio frequency |
| BLER | block error rate |
| SNRs | signal-to-noise-ratios |
| IoT | Internet of Things |
| QoS | quality-of-service |
| 5G | fifth-generation |
| URLLC | ultra-reliable low-latency communications |
| EH | energy harvesting |
| RIS | reconfigurable intelligent surface |
| NOMA | nonorthogonal multiple access |
| SWIPT | simultaneous wireless information and power transfer |
| IQ | in-phase/quadrature |
| CSI | channel state information |
| DF | decode-and-forward |
| AWGN | additive white Gaussian noise |
| probability density function | |
| CDF | cumulative density function |
| D-2-D | Device-to-Device |
| DDPG | deep deterministic policy gradi-ent |
| UAV | unmanned aerial vehicles |
| AF | amplify-and-forward |
| MIMO | multiple-input multiple-output |
| EVMs | error vector magnitudes |
| LTE | Long-Term Evolution |
Appendix A
In order to derive the CDF of under the independent channel, we first define two random variables and with and . Given that X and Y are independent, the joint distribution of X and Y is expressed as
Based on the expressions of H and T, it is easy to obtain and . Therefore, we can calculate the Jacobian of the transformation from to as
Due to the invertibility of the transformation, we have
Hence, it is evident that random variables H and T are independent. The PDFs of H and T can be, respectively, expressed as
and
According to (2) and (7), the CDF of under the independent channel is given by
where the approximation is obtained by neglecting the noise term in the numerator [18]. Then, two cases have been considered to derive the CDF of under the independent channel. When , we have .
When , with the help of (A4), we have
Appendix B
According to (2) and (8), the CDF of under the independent channel is given by
Then, two cases have been considered to derive the CDF of under the independent channel. When , we have .
When , with the help of (A5) and ([42], 3.471.9), we have
Appendix C
According to (4) and (7), the CDF of under the identical channel is given by
where the approximation is obtained by neglecting the noise term in the numerator [18]. Then, two cases have been considered to derive the CDF of under the identical channel. When , we have . When , we have .
Appendix D
According to (4) and (8), the CDF of under the identical channel is given by
Then, two cases have been considered to derive the CDF of under the identical channel. When , we have . When , with the help of ([42], 3.324.1), we have
Appendix E
According to (12), (13), and (15), it is necessary to examine three distinct cases in order to formulate the closed-form expression for . When , we have
When , can be derived as
Then, using the partial integration method and Gaussian–Chebyshev quadrature method [43], (A14) can be rewritten as
When , we have
The closed-form expression for can be readily derived by performing a similar analysis to that of .
References
- Guo, F.; Yu, F.R.; Zhang, H.; Li, X.; Ji, H.; Leung, V.C.M. Enabling Massive IoT Toward 6G: A Comprehensive Survey. IEEE Internet Things J. 2021, 8, 11891–11915. [Google Scholar] [CrossRef]
- López, O.L.A.; Mahmood, N.H.; Shehab, M.; Alves, H.; Rosabal, O.M.; Marata, L. Statistical Tools and Methodologies for Ultrareliable Low-Latency Communication—A Tutorial. Proc. IEEE 2023, 111, 1502–1543. [Google Scholar] [CrossRef]
- Popovski, P.; Stefanović, Č.; Nielsen, J.J.; de Carvalho, E.; Angjelichinoski, M.; Trillingsgaard, K.F. Wireless Access in Ultra-Reliable Low-Latency Communication (URLLC). IEEE Trans. Commun. 2019, 67, 5783–5801. [Google Scholar] [CrossRef]
- You, X.; Sheng, B.; Huang, Y.; Xu, W.; Zhang, C.; Wang, D. Closed-Form Approximation for Performance Bound of Finite Blocklength Massive MIMO Transmission. IEEE Trans. Commun. 2023, 71, 6939–6951. [Google Scholar] [CrossRef]
- Polyanskiy, Y.; Poor, H.V.; Verdu, S. Channel Coding Rate in the Finite Blocklength Regime. IEEE Trans. Inf. Theory 2010, 56, 2307–2359. [Google Scholar] [CrossRef]
- Tu, N.H.; Lee, K. Performance Analysis and Optimization of Multihop MIMO Relay Networks in Short-Packet Communications. IEEE Trans. Wirel. Commun. 2022, 21, 4549–4562. [Google Scholar] [CrossRef]
- Hu, Y.; Ozmen, M.; Gursoy, M.C.; Schmeink, A. Optimal Power Allocation for QoS-Constrained Downlink Multi-User Networks in the Finite Blocklength Regime. IEEE Trans. Wirel. Commun. 2018, 17, 5827–5840. [Google Scholar] [CrossRef]
- Benbuk, A.A.; Kouzayha, N.; Costantine, J.; Dawy, Z. Charging and Wake-Up of IoT Devices using Harvested RF Energy with Near-Zero Power Consumption. IEEE Internet Things Mag. 2023, 6, 162–167. [Google Scholar] [CrossRef]
- Hu, Y.; Yuan, X.; Zhang, G.; Schmeink, A. Sustainable Wireless Sensor Networks with UAV-Enabled Wireless Power Transfer. IEEE Trans. Veh. Technol. 2021, 70, 8050–8064. [Google Scholar] [CrossRef]
- Sun, X.; Yang, W.; Cai, Y.; Wang, M. Secure mmWave UAV-Enabled SWIPT Networks Based on Random Frequency Diverse Arrays. IEEE Internet Things J. 2021, 8, 528–540. [Google Scholar] [CrossRef]
- Sun, X.; Yang, W.; Cai, Y.; Xiang, Z.; Tang, X. Secure Transmissions in Millimeter Wave SWIPT UAV-Based Relay Networks. IEEE Wirel. Commun. Lett. 2019, 8, 785–788. [Google Scholar] [CrossRef]
- Tao, L.; Yang, W.; Lu, X.; Wang, M.; Song, Y. Achieving Covert Communication in Uplink NOMA Systems via Energy Harvesting Jammer. IEEE Commun. Lett. 2021, 25, 3785–3789. [Google Scholar] [CrossRef]
- Nasir, A.A.; Zhou, X.; Durrani, S.; Kennedy, R.A. Relaying Protocols for Wireless Energy Harvesting and Information Processing. IEEE Trans. Wirel. Commun. 2013, 12, 3622–3636. [Google Scholar] [CrossRef]
- Kalamkar, S.S.; Banerjee, A. Secure Communication via a Wireless Energy Harvesting Untrusted Relay. IEEE Trans. Veh. Technol. 2017, 66, 2199–2213. [Google Scholar] [CrossRef]
- Agrawal, K.; Jee, A.; Prakriya, S. Performance of SWIPT in Cooperative Networks with Direct Link and Nonlinear Energy Harvesting at the Battery-Assisted Relay. IEEE Trans. Green Commun. Netw. 2022, 6, 1198–1215. [Google Scholar] [CrossRef]
- Ouamri, M.A.; Barb, G.; Singh, D.; Adam, A.B.M.; Muthanna, M.S.A.; Li, X. Nonlinear Energy-Harvesting for D2D Networks Underlaying UAV with SWIPT Using MADQN. IEEE Commun. Lett. 2023, 27, 1804–1808. [Google Scholar] [CrossRef]
- Ouamri, M.A.; Machter, Y.; Singh, D.; Alkama, D.; Li, X. Joint Energy Efficiency and Throughput Optimization for UAV-WPT Integrated Ground Network Using DDPG. IEEE Commun. Lett. 2023, 27, 3295–3299. [Google Scholar] [CrossRef]
- Chen, D.; Cheng, Y.; Wang, X.; Yang, W.; Hu, J.; Cai, Y. Energy-efficient secure multiuser scheduling in energy harvesting untrusted relay networks. J. Commun. Netw. 2019, 21, 365–375. [Google Scholar] [CrossRef]
- Li, X.; Li, J.; Li, L. Performance Analysis of Impaired SWIPT NOMA Relaying Networks Over Imperfect Weibull Channels. IEEE Syst. J. 2020, 14, 669–672. [Google Scholar] [CrossRef]
- Chen, D.; Li, J.; Hu, J.; Zhang, X.; Zhang, S.; Wang, D. Secrecy Performance Analysis of Energy Harvesting Untrusted Relay Networks with Hardware Impairments. Int. J. Distrib. Sens. Netw. 2024, 2024, 4806603. [Google Scholar] [CrossRef]
- Kurma, S.; Sharma, P.K.; Dhok, S.; Singh, K.; Li, C.-P. Adaptive AF/DF Two-Way Relaying in FD Multiuser URLLC System with User Mobility. IEEE Trans. Wirel. Commun. 2022, 21, 10224–10241. [Google Scholar] [CrossRef]
- Yuan, L.; Du, Q.; Fang, F. Performance Analysis of Full-Duplex Cooperative NOMA Short-Packet Communications. IEEE Trans. Veh. Technol. 2022, 71, 13409–13414. [Google Scholar] [CrossRef]
- Tu, N.H.; Lee, K. Multihop MIMO Full-Duplex Relay Networks with Short-Packet URLLCs. IEEE Syst. J. 2024, 18, 1975–1986. [Google Scholar] [CrossRef]
- Nguyen, T.-V.; Huynh-The, T.; Bao, V.-N.Q. Short-Packet Communications in Wireless Energy Transfer Full-Duplex IoT Networks with Deep Learning Design. J. Commun. Netw. 2024, 26, 297–307. [Google Scholar] [CrossRef]
- Raut, P.; Sharma, P.K.; Tsiftsis, T.A.; Zou, Y. Power-Time Splitting-Based Non-Linear Energy Harvesting in FD Short-Packet Communications. IEEE Trans. Veh. Technol. 2020, 69, 9146–9151. [Google Scholar] [CrossRef]
- Nguyen, T.-V.; Huynh-The, T.; An, B. A Deep CNN-based Relay Selection in EH Full-Duplex IoT Networks with Short-Packet Communications. In Proceedings of the ICC 2021—IEEE International Conference on Communications, Montreal, QC, Canada, 14–23 June 2021. [Google Scholar]
- Nguyen, T.-V.; Huynh-The, T.; Quoc Bao, V.N. Performance Analysis and Deep Learning Evaluation of URLLC Full-Duplex Energy Harvesting IoT Networks over Nakagami-m Fading Channels. In Proceedings of the 2023 IEEE Statistical Signal Processing Workshop (SSP), Hanoi, Vietnam, 2–5 July 2023. [Google Scholar]
- Sharma, P.K.; Sharma, N.; Dhok, S.; Singh, A. RIS-Assisted FD Short Packet Communication with Non-Linear EH. IEEE Commun. Lett. 2023, 27, 522–526. [Google Scholar] [CrossRef]
- Kaboyo, S.; Abd El-Malek, A.H.; Muta, O.; Abo-Zahhad, M.; Elsabrouty, M. Age of Information Analysis for Full Duplex Cooperative SWIPT NOMA System. In Proceedings of the 2024 IEEE Wireless Communications and Networking Conference (WCNC), Dubai, United Arab Emirates, 21–24 April 2024. [Google Scholar]
- Li, X.; Wang, Q.; Liu, M.; Li, J.; Peng, H.; Piran, M.; Li, L. Cooperative Wireless-Powered NOMA Relaying for B5G IoT Networks with Hardware Impairments and Channel Estimation Errors. IEEE Internet Things J. 2021, 8, 5453–5467. [Google Scholar] [CrossRef]
- Liu, Z.; Ye, Y.; Lu, G.; Hu, R.Q. System Outage Performance of SWIPT Enabled Full-Duplex Two-Way Relaying with Residual Hardware Impairments and Self-Interference. IEEE Syst. J. 2023, 17, 337–348. [Google Scholar] [CrossRef]
- Kumar, D.; Singya, P.K.; Nebhen, J.; Bhatia, V. Performance of SWIPT-Enabled FD TWR Network with Hardware Impairments and Imperfect CSI. IEEE Syst. J. 2023, 17, 1224–1234. [Google Scholar] [CrossRef]
- Kumar, D.; Singya, P.K.; Krejcar, O.; Bhatia, V. On Performance of a SWIPT Enabled FD CRN with HIs and Imperfect SIC Over α–μ Fading Channel. IEEE Trans. Cogn. Commun. Netw. 2023, 9, 99–113. [Google Scholar] [CrossRef]
- Kumar, D.; Singya, P.K.; Bhatia, V. On Performance of Wireless-Powered FD Relaying Network with Imperfect SIC and Hardware Impairments. In Proceedings of the 2023 National Conference on Communications (NCC), Guwahati, India, 23–26 February 2023. [Google Scholar]
- Kam, S.; Kim, D.; Lee, H.; Hong, D. Bidirectional full-duplex systems in a multispectrum environment. IEEE Trans. Veh. Technol. 2015, 64, 3812–3817. [Google Scholar] [CrossRef]
- Chen, D.; Li, J.; Hu, J.; Zhang, X.; Zhang, S.; Wang, D. Interference-Assisted Energy Harvesting Short Packet Communications with Hardware Impairments. Int. J. Intell. Netw. 2024, 5, 231–240. [Google Scholar] [CrossRef]
- Zheng, D.; Yang, Y.; Wei, L.; Jiao, B. Decode-and-Forward Short-Packet Relaying in the Internet of Things: Timely Status Updates. IEEE Trans. Wirel. Commun. 2021, 20, 8423–8437. [Google Scholar] [CrossRef]
- Solanki, S.; Singh, V.; Upadhyay, P.K. RF energy harvesting in hybrid two-way relaying systems with hardware impairments. IEEE Trans. Veh. Technol. 2019, 68, 11792–11805. [Google Scholar] [CrossRef]
- Holma, H.; Toskala, A. LTE for UMTS: Evolution to LTE-Advanced, 2nd ed.; Wiley: Hoboken, NJ, USA, 2011. [Google Scholar]
- Gu, Y.; Chen, H.; Li, Y.; Vucetic, B. Ultra-Reliable Short-Packet Communications: Half-Duplex or Full-Duplex Relaying? IEEE Wirel. Commun. Lett. 2018, 7, 348–351. [Google Scholar] [CrossRef]
- Xia, C.; Xiang, Z.; Meng, J.; Liu, H.; Pan, G. Reliable Transmission of Short Packets in Cognitive Radio Inspired NOMA Network. IEEE Syst. J. 2023, 17, 6148–6158. [Google Scholar] [CrossRef]
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series and Products, 7th ed.; Academic Press: New York, NY, USA, 2007. [Google Scholar]
- Abramowitz, M.; Stegun, I.A. Handbook of Mathematical Functions with Formulas, Graphs, and Mathematical Tables, 9th ed.; US Govt. Print: Washington, DC, USA, 1972.
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).