Abstract
We review and compare three algebraic methods to compute the nonlinearity of Boolean functions. Two of them are based on Gröbner basis techniques: the first one is defined over the binary field, while the second one over the rationals. The third method improves the second one by avoiding the Gröbner basis computation. We also estimate the complexity of the algorithms, and, in particular, we show that the third method reaches an asymptotic worst-case complexity of operations over the integers, that is, sums and doublings. This way, with a different approach, the same asymptotic complexity of established algorithms, such as those based on the fast Walsh transform, is reached.
Keywords:
boolean functions; gröbner basis; nonlinearity; fast fourier transform; multivariate polynomials MSC:
Primary: 06E30; 11T71; Secondary: 11T06; 13P25
1. Introduction
Any function that maps binary strings of fixed length to the set is called a Boolean function (B.f.). Besides being mathematically interesting combinatorial objects, Boolean functions have turned to be a fundamental tool for their relations to coding theory (to the covering radii of Reed–Muller codes), combinatorics (difference set) and cryptography, in particular for the design of symmetric and, recently, also homomorphic ciphers. Due to this, researchers have uninterruptedly studied these objects for more than four decades.
Modern symmetric ciphers are designed to achieve the principles of confusion and diffusion [1]. Diffusion aims at distributing uniformly the dependence of the output bits from all the input bits. This property is usually optimally achieved by means of linear operations. On the other hand, confusions aims at complicating the relationship between the output bits, the input bits and the key. This is usually achieved by exploiting relations that are not linear. In symmetric cryptography, Boolean functions are often used in the confusion layer of ciphers. An affine B.f. does not provide an effective confusion. To overcome this, functions that are as far as possible from being an affine function are needed. The effectiveness of these functions is measured by several parameters, one of these is called “nonlinearity”. In particular, it is hard to approximate a B.f. with high nonlinearity by an affine (or linear) function, which is a fundamental property in the defense against linear cryptanalysis. Furthermore, B.f.s with highest nonlinearity (so called “bent” functions [2]), have two fundamental properties: they achieve optimal diffusion (similarly to linear functions) and their derivative takes on each value exactly half the time, i.e., they are balanced, which makes them ideal to be resistant against differential cryptanalysis. Unfortunately, bent functions are not balanced. When used to build stream ciphers, for example, they make them susceptible to correlation attacks. In these case, bent functions need to be replaced with a B.f. that is both balanced and highly non-linear. Due to the extremely high number of B.f. and the scarcity of B.f.s with cryptographically interesting properties, one can either build B.f.s with predetermined nonlinearity (often this approach implies the lost of some desirable properties such as good diffusion, see, e.g., [3], or high algebraic degree, for example symmetric functions with highest nonlinearity are quadratic [4,5]), or to run a brute-force search among the available B.f.s. In this last case, it becomes crucial to be able to compute the nonlinearity of a B.f. efficiently. We refer to [6,7,8] for other applications of B.f.s in cryptography.
1.1. Related Works
Techniques to compute the nonlinearity of Boolean functions have been known for many years, since the seminal work of Rothaus in 1976 [2], where he introduced “bent” functions (even though his first paper in English on bent functions was written in 1966 [9]), Boolean functions achieving maximal nonlinearity. These functions were also studied by Dillon in 1974 [10], and it is claimed that they were already known also by Eliseev and Stepchenko in the Soviet Union in the early 1960s, but their technical reports have never been declassified [11]. A good overview and surveys on B.f. can be found, for example, in [12], or, specifically for bent functions, in [9,11,13].
All methods to compute the nonlinearity of a generic B.f. f rely on butterfly algorithms such as the Fast Fourier transform, or the fast Möbius transform, which are exponential in the number of variables of f. These methods allow to compute the so called Walsh spectrum, from which the nonlinearity can be directly quantified (see Section 2). With these methods, usually one can compute the nonlinearity up to about 40 variables, on a relatively powerful personal laptop. When f has a particular structure, there might be faster methods to compute the nonlinearity. For example, in 2013, Çalik [14,15] showed that, when f is sparse, the task of nonlinearity computation can be reduced to solving an associated binary integer programming problem. The algorithm is used to compute the nonlinearity of some sparse functions (up to 100 monomials) with 60 variables. Other kinds of properties of a B.f. are reflected in the structure of the Walsh spectrum, which becomes easier to determine. This is the case, for example, of quadratic functions, Maiorana–McFarland’s functions [16], or normal functions [17,18] (see [19] for more details).
When computing the nonlinearity is not feasible, it becomes interesting to provide lower bounds for this value. In 2008, Carlet [20], improving previous results from [21,22,23], introduces a recursive method for lower bounding the nonlinearity profile of a B.f. and deduces bounds on the second order nonlinearity for several classes of cryptographic Boolean functions, including the Welch and the multiplicative inverse functions (used in the S-boxes of the AES block cipher). Some more recent results [24] improve the lower bounds on the second-order nonlinearity of three classes of Boolean functions whose form is related to the absolute trace map.
Recently, in the context of defining a homomorphic encryption cipher, Carlet, Méaux, and Rotella [19] have studied the main cryptographic features, including nonlinearity, of Boolean functions when the input to these functions is restricted to some subset. The nonlinearity with restricted input is the focus of [25].
Cryptographic attack have also pushed to generalization of the concept of nonlinearity, as recently done for example by Semaev in [26], where “multidimensional” nonlinearity parameters for conventional and vectorial Boolean functions are introduced.
Techniques that are similar to those presented in this work, have also been applied in [27,28] to compute the minimum distance and the weight distribution of, respectively, systematic nonlinear codes, and generic binary nonlinear codes.
1.2. Our Contribution
In this paper, we review three methods to compute the nonlinearity, which are based on the theory of multivariate polynomials instead of the standard approach in terms of the Walsh transform. These three methods are unpublished and have been partially presented only in conference (the method from Section 4.1 in WCC 2007 [29], the one from Section 4.2 in MEGA 2015 [30], and the one from Section 4.3 in YACC 2014 [31]). All three methods compute the nonlinearity of Boolean functions by starting from their truth table (i.e., evaluation vector) representation (see Section 2). Moreover, we give an estimate of the complexity of our methods, comparing it with the complexity of the classical method which uses the fast Walsh transform and the fast Möbius transform.
The first method, described in Section 4.1, computes the nonlinearity of a B.f. f from the evaluation vector (truth table) of f. We construct a polynomial system of equations over the binary field with two elements, representing the set of all affine functions with a given distance t from f. Then, using Gröbner basis algorithms, we solve the system for , and, if there is no solution, we increase t and try with the newly derived system. We repeat the procedure until a solution is found. At this point, the value of t returns the nonlinearity of the B.f. f. As already mentioned, this method, not only returns the nonlinearity of f, but also all affine functions with distance t from f (and thus also all the best affine approximations of f, i.e., those affine functions g for which the distance between f and g is minimal), compactly represented as a polynomial system of equations over the binary field. Traditional methods to compute the nonlinearity only return the set of distances of all affine functions from f in the form of the so called Walsh table. Although all such affine functions could be deduced from the Walsh table, this does not provide a compact algebraic representation for them. This is the main reason why this method is considerably less efficient than those based on the fast Fourier transform.
At the cost of losing the information of all affine functions, we improve the efficiency of the previous method. Again, starting from the evaluation vector of f, we construct a polynomial, that we call the nonlinearity polynomial, whose evaluation contains all the distances of f from all possible affine functions, and the minimum such distance will be the nonlinearity. This evaluation can be found again using Gröbner basis algorithms over the rational or a prime field (see Section 4.2) or by using a more traditional butterfly algorithm (see Section 4.3). This last option let us compute the nonlinearity of f with the same asymptotical complexity of the traditional technique using the Fast Walsh transform. Notice that, though we are not aware of any proof, the asymptotic complexity of seems to be already optimal. This claim is enforced by the fact that the input of the problem has a dimension of .
1.3. Outline of the Paper
In Section 2 and Section 3 we recall the basic notions and statements, especially regarding Boolean functions, which are necessary for our methods. In Section 4, we present our original algorithms, and we introduce the notion of nonlinearity polynomial and describe its properties. Finally, in Section 5 we analyze the complexity of the proposed methods, both experimentally and theoretically.
2. Preliminaries and Notation on Boolean Functions
In this chapter we summarize some definitions and known results from [12,32], concerning Boolean functions and the classical techniques to determine their nonlinearity.
We denote by the binary field . The set is the set of all binary vectors of length n, viewed as an -vector space. Let . The Hamming weight of the vector v is the number of its nonzero coordinates. For any two vectors , the Hamming distance between and , denoted by , is the number of coordinates in which the two vectors differ. A Boolean function is a function . The set of all Boolean functions from to will be denoted by .
2.1. Representations of Boolean Functions
We assume implicitly to have ordered , so that . A Boolean function f can be specified by a truth table, which gives the evaluation of f at all ’s.
Definition 1.
We consider the evaluation map such that
The vector is called the evaluation vector of f.
Once the order on is chosen, i.e., the ’s are fixed, it is clear that the evaluation vector of f uniquely identifies f.
A B.f. can be expressed in a unique way as a square free polynomial in , i.e., where . This representation is called the Algebraic Normal Form (ANF).
Definition 2.
The degree of the ANF of a B.f. f is called the algebraic degree of f, denoted by , and it is equal to .
Let be the set of all affine functions from to , i.e., the set of all Boolean functions in with algebraic degree 0 or 1. If then its ANF can be written as There exists a simple divide-and-conquer butterfly algorithm [12] (p. 10) to compute the ANF from the truth-table (or vice versa) of a Boolean function, which requires bit sums, while bits must be stored. This algorithm is known as the fast Möbius transform.
In [33], a useful representation of Boolean functions for characterizing several cryptographic criteria (see also [34,35]) is introduced.
Boolean functions can be represented as elements of , where is the ideal generated by the polynomials , and is , , or .
Definition 3.
Let f be a function on taking values in a field . We call the numerical normal form (NNF) of f the following expression of f as a polynomial:
with and .
It can be proved that any B.f. f admits a unique numerical normal form. As for the ANF, it is possible to compute the NNF of a B.f. from its truth table by mean of an algorithm similar to a fast Fourier transform, thus requiring additions over and storing elements of .
From now on let . The truth table of f can be recovered from its NNF by the formula where . Conversely, it is possible to derive an explicit formula for the coefficients of the NNF by means of the truth table of f.
Proposition 1.
Let f be any integer-valued function on . For every , the coefficient of the monomial in the NNF of f is:
2.2. Nonlinearity and Walsh Transform of a Boolean Function
Definition 4.
Let . Then .
Lemma 1.
Let . Then
Definition 5.
Let . The nonlinearity of f is the minimum of the distances between f and any affine function
The maximum nonlinearity for a B.f. f is bounded by:
Definition 6.
The Walsh transform of a B.f. is the function such that where is the scalar product.
Fact.
Definition 7.
The set of integers is called the Walsh spectrum of the B.f. f.
It is possible to compute the Walsh spectrum of f from its evaluation vector in integer operations, while storing integers, by means of the fast Walsh transform (the Walsh transform is the Fourier transform of the sign function of f). Thus, the computation of the nonlinearity of a B.f. f, when this is given either in its ANF or in its evaluation vector, requires integer operations and a memory of .
3. Preliminary Results
Here we present the main results from [29,36]. The same techniques are also applied in [27,37].
Polynomials and Vector Weights
Let be a field and be a set of variables. We denote by the multivariate polynomial ring in the variables X. If , we denote by the ideal in generated by . Let q be the power of a prime. We denote by the set of field equations in , where is an integer, understood from now on. We write when .
Definition 8.
Let and . We say that is a square free monomial of degree t (or a simple t-monomial) if:
i.e., a monomial in such that for any . We denote by the set of all square free monomials of degree t in .
Let , with and let be the following ideal
where are the elementary symmetric functions:
We also denote by the ideal . For any , let be the set which contains all vectors in of weight i, , and let be the set which contains all vectors of weight up to i, .
Theorem 1.
Let t be an integer such that . Then the vanishing ideal of is and its reduced Gröbner basis G is
Let be a polynomial ring over . Let , . For any polynomial vector W in the module , , we denote by the following polynomial in :
Example 1.
Let , and . Then
4. Computing the Nonlinearity of a Boolean Function
In this section, we present three methods to compute the nonlinearity of a B.f. f. The first exploits Gröbner basis algorithms over the binary field, and is somehow inefficient, but beside the nonlinearity, also returns all affine functions of a given distance from f. The second methods is more efficient and uses Gröbner basis algorithms over the rational or a prime field. Finally, the third method, the most efficient, is based on a butterfly structure similar to a fast Fourier transform.
4.1. Gröebner Bases over the Biniary Field
In this section, we show how to use Theorem 1 to compute the nonlinearity of a given B.f. . We want to define an ideal such that a point in its variety corresponds to an affine function with distance at most from f.
Let A be the variable set . We denote by the following polynomial:
According to Lemma 1, determining the nonlinearity of is the same as finding the minimum weight of the vectors in the set . We can consider the evaluation vector of the polynomial as follows:
Example 2.
Let be a general affine function in . Then . We consider vectors in ordered as follows (note that, in all the examples, we first list the vectors from smaller to higher Hamming weight. Among vectors of the same weight, we list first those having a smaller integer representation, with least significant bit on the right):
Thus, we have that the evaluation vector of is
Definition 9.
We denote by the ideal in :
Remark 1.
As , is zero-dimensional and radical ([38]).
Lemma 2.
For the following statements are equivalent:
- 1.
- ,
- 2.
- ,
- 3.
- .
Proof.
(2)⇔(3). Obvious.
(1)⇒(2). Let and . We have that for all . Thus, and, thanks to Theorem 1, , i.e., .
(2)⇒(1). It can be proved by reversing the above argument. □
From Lemma 2 we immediately have the following theorem.
Theorem 2.
Let . The nonlinearity is the minimum t such that .
From this theorem we can derive an algorithm to compute the nonlinearity for a function , by computing any Gröbner basis of .
Remark 2.
If f is not affine, we can start our check from .
Example 3.
Let be the Boolean function: We want to compute and clearly f is not affine. We compute vector and we take a general affine function (as in Example 2), so that , Thus, . The ideal is the ideal generated by We compute any Gröbner basis of this ideal and we obtain that it is trivial, so and . Now we have to compute a Gröbner basis for . We obtain, using degrevlex (graded reverse lexicographic order, also known as grevlex, or degrevlex for degree reverse lexicographic order, compares the total degree first, then uses a reverse lexicographic order as tie-breaker, but it reverses the outcome of the lexicographic comparison so that lexicographically larger monomials of the same degree are considered to be degrevlex smaller). Ordering with , that . Thus, by Theorem 2. By inspecting , we also obtain all affine functions having distance 2 from f:
Example 4.
Let be the Boolean function As it is obvious that f is not affine, we start from the ideal . The Gröbner basis of is trivial with respect to any monomial order for . For , we obtain the Gröbner basis with respect to the degrevlex order with : Then , that is, there is only one affine function α that has distance equal to 4 from f: .
4.2. Gröebner Bases over the Rational Field
Here we present an algorithm to compute the nonlinearity of a B.f. using Gröbner bases over rather than over , which turns out to be much faster than Algorithm 1. The same algorithm can be slightly modified to work over the field , where p is a prime. The complexity of these algorithms will be analyzed in Section 5.
| Algorithm 1. Basic algorithm to compute the nonlinearity of a B.f. using Gröbner basis over . |
| Input: a B.f. f |
| Output: the nonlinearity of f |
| 1: |
| 2: while do |
| 3: |
| 4: end while |
| 5: return |
As we have seen in Section 4.1, the nonlinearity of a B.f. can be computed using Gröbner bases over . It is sufficient to find the minimum j such that the variety of the ideal is not empty. Recall that
This method becomes impractical even for small values of n, since monomials have to be evaluated. A first slight improvement could be achieved by adding to the ideal one monomial evaluation at a time and check if 1 has appeared in the Gröbner basis. Even this way, the algorithm remains very slow.
For each , let us denote:
the B.f. where as usual are the variables representing the coefficient of a generic affine function. In this case we have that:
Note that the polynomials are affine polynomials. We also denote by
the NNF of each (obtained as in [33], Theorem 1).
Definition 10.
We call the integer nonlinearity polynomial (or simply the nonlinearity polynomial) of the B.f. f. For any we define the ideal as follows:
Note that the evaluation vector represents all the distances of f from all possible affine functions (in n variables).
Theorem 3.
The variety of the ideal is non-empty if and only if the B.f. f has distance t from an affine function. In particular, , where t is the minimum positive integer such that .
Proof.
Note that and so Therefore, if and only if such that . Let such that . By definition we have and Hence and our claim follows directly. □
To compute the nonlinearity of f we can use Algorithm 2 over the rational field (), with input f.
| Algorithm 2. To compute the nonlinearity of the B.f. f using Gröbner basis over a field . |
| Input:f |
| Output: nonlinearity of f |
| 1: Compute |
| 2: |
| 3: while do |
| 4: |
| 5: end while |
| 6: return j |
4.3. Fast Polynomial Evaluation
Once the nonlinearity polynomial is defined, we can use another approach to compute the nonlinearity avoiding the computations of Gröbner bases. We have to find the minimum nonnegative integer t in the set of the evaluations of , that is, in . To compute the evaluations we can use a Fast Polynomial Evaluation algorithm (), such as the fast Möbius transform. In Algorithm 3, we explicitly show the above steps.
| Algorithm 3. To compute the nonlinearity of the Boolean function, using Nonlinearity Polynomial () and Fast Polynomial Evaluation (). | |
| Input:f | |
| Output: nonlinearity of f | |
| 1: if then | |
| 2: return 0 | |
| 3: else | |
| 4: Compute | // Algorithm 4: |
| 5: Compute | // |
| 6: return m | |
| 7: end if | |
Example 5.
Consider the case , . We have that and . Let us compute all and , for :
Then and since
then the nonlinearity of f is 1. Observe that the vector represents all the distances of f from all possible affine functions in 2 variables, that is, from .
4.4. Properties of the Nonlinearity Polynomial
From now on, with abuse of notation, we sometimes consider 0 and 1 as elements of and other times as elements of . We have the following simple lemma:
Lemma 3.
Given
where the sum on the right is in .
It is easy to show that . We give a theorem to compute the coefficients of the nonlinearity polynomial.
Theorem 4.
Let , , and be such that . Then the coefficients of can be computed as:
Proof.
The nonlinearity polynomial is the integer sum of the numerical normal forms of the affine polynomials , each identified by the vector , i.e.,:
which is a polynomial in . The NNF of is a polynomial with terms, i.e.,:
for some , and by Proposition 1
Let us prove Equation (3). When we have
Let us prove Equation (4). Suppose . Now the coefficient of the monomial of the nonlinearity polynomial is such that:
We claim that each u such that yields a zero term in the summation. If then s.t. , i.e., . We show now that s.t. s.t. and
It is sufficient to choose and for all . Clearly and since . By direct substitution we obtain
Now we consider fixed, and . There are exactly vectors a such that , i.e.,:
Now we want to study the internal summation in (7). If then we have . Otherwise, if we can consider the following set of indices , which has size . Since and then by transitivity. For all we have , and then . Thus, for any we have
and each of the two cases happens for exactly one half of the vectors . Clearly the two halves are disjointed. This yields, from (5) and (7), the following chain of equalities:
which proves the theorem. □
In particular we have:
Corollary 1.
Let and the nonlinearity polynomial
Then, we have that:
Furthermore, we have:
Corollary 1 shows that it is sufficient to store half of the coefficients of , precisely the coefficients of the monomials where does not appear.
Corollary 2.
Each coefficient c of the nonlinearity polynomial is such that .
Corollary 3.
Given the nonlinearity polynomial of f as
then the nonlinearity polynomial of is related to that of f by the following rule:
A scheme that shows how to derive the coefficients of the nonlinearity polynomial in the case can be seen in Table 1 and Table 2.

Table 1.
Computation of the coefficients of the nonlinearity polynomial with . Each line represents the NNF coefficients of the terms of not containing .

Table 2.
Computation of the coefficients of the nonlinearity polynomial with . Each line represents the NNF coefficients of the terms of containing .
5. Complexity Considerations
In this section, we analyze the complexity of constructing the nonlinearity polynomial and of running Algorithms 1–3 to compute the nonlinearity. Recall that, using the Fast Möbius and the Fast Walsh Transform, the complexity of computing the nonlinearity of a B.f. with n variables, having as input its coefficients vector, is .
5.1. Complexity of Constructing the Nonlinearity Polynomial
In Algorithm 4, we provide the pseudo code to compute the coefficients of the nonlinearity polynomial in integer operations. In Figure 1, Algorithm 4 is visualized for .
| Algorithm 4. Algorithm to calculate the nonlinearity polynomial in integer operations. |
| Input: The evaluation vector of a B.f. |
| Output: the vector of the coefficients of |
| Calculation of the coefficients of the monomials not containing |
| 1: |
| 2: for do |
| 3: |
| 4: repeat |
| 5: for do |
| 6: |
| 7: if then |
| 8: |
| 9: else |
| 10: |
| 11: end if |
| 12: end for |
| 13: |
| 14: until |
| 15: end for |
| Calculation of the coefficients of the monomials containing |
| 16: |
| 17: for do |
| 18: |
| 19: end for |
| 20: return c |
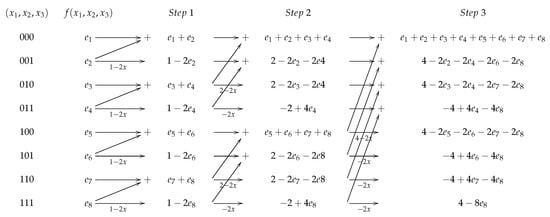
Figure 1.
Butterfly scheme to efficiently compute the coefficients of the nonlinearity polynomial, where (see Algorithm 4: ).
Theorem 5.
Algorithm 4 requires:
- 1.
- integer sums and doublings, in particular about integer sums and about integer doublings.
- 2.
- The storage of integers of size less than or equal to .
Proof.
In the first part of Algorithm 4 (the computation of the coefficients of the monomials not containing ) the iteration on i is repeated n times. For each i, Step 9 and Step 11 or 13 are repeated times (since b goes from 0 to by a step of and x performs steps). In Step 9 only one integer sum is performed, in Steps 11 we have one integer sum and one doubling, and in Step 13 only one doubling. Then the total amount of integer operation is . Finally the computation of the coefficients of the monomials containing requires only integer doublings. To store all the monomials of the nonlinearity polynomial we have to store integers, although Corollary 1 shows that it is sufficient to store only the first half of them, i.e., integers. By Corollary 2, their size is less than or equal to . □
5.2. Some Considerations on Algorithm 1
In Algorithm 1, almost all the computations are wasted evaluating all possible simple-t-monomials in variables, which are . This number grows enormously even for small values of n and t. We investigated experimentally how many of the monomials are actually needed to compute the final Gröbner basis of . Our experiment ran over all possible Boolean functions in 3 and 4 variables. The results are reported in Table 3, Table 4 and Table 5. In this tables, for each there are four columns. Let be the Gröbner basis of . Under the column labeled #C we report the average number of checked monomials in variables before obtaining . Under the column labeled #S we report the average number of monomials which are actually sufficient to obtain . Under the columns labeled “m” e “M” we report, respectively, the minimum and the maximum number of sufficient monomials to find running through all possible Boolean functions in n variables. For example, to compute the Gröbner basis of the ideal associated with a B.f. f whose nonlinearity is 2, we needed to check on average 24 monomials before finding the correct basis. Between the 24 monomials only (on average) were sufficient to obtain the same basis, where the number of sufficient monomials never exceeded the range 8–11.

Table 3.
Number of monomials needed to compute the Gröbner basis of the ideal , using Algorithm 1: .

Table 4.
Number of monomials needed to compute the Gröbner basis of the ideal , , using Algorithm 1: .

Table 5.
Number of monomials needed to compute the Gröbner basis of the ideal ,, using Algorithm 1: .
5.3. Algorithms 1 and 2
Since it is not easy to estimate the complexity of a Gröbner basis computation theoretically, we give some experimental results, shown in Table 6.

Table 6.
Experimental comparisons of the coefficients of growth of the analyzed algorithms.
In this table we report the coefficients of growth of the analyzed algorithms (to compute the values in the columns and we tested 15,000 random Boolean functions from , since for there are only Boolean functions), comparing them with the value . For each algorithm we compute the average time to compute the nonlinearity of a B.f. with n variables and the average time to compute the nonlinearity of a B.f. with variables. Then we report in the table the value . When Gröbner bases are computed, then graded reverse lexicographical order is used, with Magma [39] implementation of the Faugère algorithm [40]. Since the ideal of Definition 9 is derived from the evaluation of monomials (generating at most the same number of equations), then the complexity of Algorithm 1 is equivalent to the complexity of computing a Gröbner basis of at most equations of degree d (where ) in variables over the field . This method becomes almost impractical for . We recall that (see Equation (2)).
The complexity of Algorithm 2 is equivalent to the complexity of computing a Gröbner basis of only field equations plus one single polynomial of degree at most in variables over the rational field, i.e., (or over a prime field, i.e., ) with coefficients of size less then or equal to . As shown in Table 6, computing this Gröbner basis over a prime field with is much faster than computing the same base over . It may be investigated if there exist better size for the prime p.
5.4. Algorithm 3
Theorem 6.
Algorithm 3 returns the nonlinearity of a B.f. f with n variables in integers operations (sums and doublings).
Proof.
Algorithm 3 can be divided in three main steps:
- Calculation of the nonlinearity polynomial . This step, as shown in Theorem 5, requires integer operations and memory.
- Evaluation of the nonlinearity polynomial . This step can be performed using fast Möbius transform in integer sums and memory. We refer to this algorithm as the Fast Polynomial Evaluation () algorithm.
- Computation of the minimum with . This step requires no more than checks.
The overall complexity is then integer operations and memory. □
6. Conclusions
We presented three approaches to compute the nonlinearity of a Boolean function using multivariate polynomials. In particular we show that the problem of computing the distance of a generic B.f. f from the set of affine functions is equivalent to the problem of solving a multivariate polynomial system over the binary field. This system can be reformulated over the rationals by considering the associated pseudo Boolean function, and we can exhibit a multivariate polynomial whose evaluations solve the problem. Moreover, we evaluate our polynomial using fast Fourier techniques and solve the problem very efficiently. In particular, with our polynomial-based approach we compute the nonlinearity of any B.f. in operations, reaching the same asymptotic complexity of classical methods. The first of the presented methods returns the nonlinearity of f and a compact algebraic representation of all affine functions with distance t from f, opposed to traditional methods to compute the nonlinearity which only allow to deduce these affine functions from the Walsh table, not yielding a compact algebraic representation. Regarding the two other methods, they make use of a special polynomial, namely the nonlinearity polynomial, which is an interesting mathematical object per se. Studying his properties might open interesting research directions, and, possibly, finding a more efficient way of determining its minimum value, will determine a more efficient way of computing the nonlinearity.
Author Contributions
Conceptualization, E.B., M.S. and I.S.; methodology, E.B., M.S. and I.S.; software, E.B.; validation, E.B., M.S.; formal analysis, E.B., M.S. and I.S.; investigation, E.B., M.S. and I.S.; resources, E.B., M.S. and I.S.; data curation, E.B., M.S. and I.S.; writing—original draft preparation, E.B., M.S. and I.S.; writing—review and editing, E.B., M.S. and I.S.; visualization, E.B., M.S. and I.S.; supervision, M.S.; project administration, M.S.; funding acquisition, not applicable. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Acknowledgments
These results have been partially presented in three conferences, WCC 2007 [29], YACC 2014 [31], MEGA 2015 [30], and in the Ph.D. thesis [41,42]. The first two authors would like to thank the third author (their supervisor).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Shannon, C.E. Communication theory of secrecy systems. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Rothaus, O.S. On “bent” functions. J. Comb. Theory Ser. A 1976, 20, 300–305. [Google Scholar] [CrossRef]
- Adams, C.M.; Tavares, S.E. The Use of Bent Sequences to Achieve Higher-Order Strict Avalanche Criterion in S-Box Design; Technical Report TR 90-013; Queen’s University: Kingston, ON, Canada, 1990. [Google Scholar]
- Maitra, S.; Sarkar, P. Maximum nonlinearity of symmetric Boolean functions on odd number of variables. IEEE Trans. Inf. Theory 2002, 48, 2626–2630. [Google Scholar] [CrossRef]
- Savickỳ, P. On the bent Boolean functions that are symmetric. Eur. J. Comb. 1994, 15, 407–410. [Google Scholar] [CrossRef]
- Cusick, T.W.; Stanica, P. Cryptographic Boolean Functions and Applications; Academic Press: Cambridge, MA, USA, 2017. [Google Scholar]
- Carlet, C. Boolean Functions for Cryptography and Coding Theory; Cambridge University Press: Cambridge, UK, 2021. [Google Scholar]
- Wu, C.-K.; Feng, D. Boolean Functions and Their Applications in Cryptography; Springer: Berlin/Heidelberg, Germany, 2016. [Google Scholar]
- Carlet, C.; Mesnager, S. Four decades of research on bent functions. Des. Codes Cryptogr. 2016, 78, 5–50. [Google Scholar] [CrossRef]
- Dillon, J.F. Elementary Hadamard Difference Sets. Ph.D. Thesis, University of Maryland, College Park, MD, USA, 1974. [Google Scholar]
- Tokareva, N. Bent Functions: Results and Applications to Cryptography; Academic Press: Cambridge, MA, USA; Elsevier: Amsterdam, The Netherlands, 2015. [Google Scholar]
- Carlet, C. Boolean functions for cryptography and error correcting codes, Boolean Models and Methods in Mathematics. Comput. Sci. Eng. 2010, 2, 257–397. [Google Scholar]
- Mesnager, S. Bent Functions; Springer: Berlin/Heidelberg, Germany, 2016. [Google Scholar]
- Çalık, Ç. Nonlinearity computation for sparse boolean functions. arXiv 2013, arXiv:1305.0860. [Google Scholar]
- Çalık, Ç. Computing Cryptographic Properties of Boolean Functions from the Algebraic Normal form Representation. Ph.D. Thesis, Middle East Technical University, Ankara, Turkey, 2013. [Google Scholar]
- Carlet, C. On the confusion and diffusion properties of Maiorana–McFarland’s and extended Maiorana–McFarland’s functions. J. Complex. 2004, 20, 182–204. [Google Scholar] [CrossRef][Green Version]
- Dobbertin, H. Construction of bent functions and balanced Boolean functions with high nonlinearity. In International Workshop on Fast Software Encryption; Springer: Berlin/Heidelberg, Germany, 1994; pp. 61–74. [Google Scholar]
- Charpin, P. Normal boolean functions. J. Complex. 2004, 20, 245–265. [Google Scholar] [CrossRef][Green Version]
- Carlet, C.; Méaux, P.; Rotella, Y. Boolean functions with restricted input and their robustness; application to the flip cipher. IACR Trans. Symmetric Cryptol. 2017, 2017, 192–227. [Google Scholar] [CrossRef]
- Carlet, C. Recursive lower bounds on the nonlinearity profile of boolean functions and their applications. IEEE Trans. Inf. Theory 2008, 54, 1262–1272. [Google Scholar] [CrossRef]
- Iwata, T.; Kurosawa, K. Probabilistic higher order differential attack and higher order bent functions. In International Conference on the Theory and Application of Cryptology and Information Security; Springer: Berlin/Heidelberg, Germany, 1999; pp. 62–74. [Google Scholar]
- Carlet, C. On the higher order nonlinearities of algebraic immune functions. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2006; pp. 584–601. [Google Scholar]
- Carlet, C.; Dalai, D.K.; Gupta, K.C.; Maitra, S. Algebraic immunity for cryptographically significant boolean functions: Analysis and construction. IEEE Trans. Inf. Theory 2006, 52, 3105–3121. [Google Scholar] [CrossRef]
- Yan, H.; Tang, D. Improving lower bounds on the second-order nonlinearity of three classes of boolean functions. Discret. Math. 2020, 343, 111698. [Google Scholar] [CrossRef]
- Mesnager, S.; Zhou, Z.; Ding, C. On the nonlinearity of boolean functions with restricted input. Cryptogr. Commun. 2019, 11, 63–76. [Google Scholar] [CrossRef]
- Semaev, I. New non-linearity parameters of boolean functions. arXiv 2019, arXiv:1906.00426. [Google Scholar]
- Guerrini, E.; Orsini, E.; Sala, M. Computing the distance distribution of systematic nonlinear codes. J. Algebra Its Appl. 2010, 9, 241–256. [Google Scholar] [CrossRef]
- Bellini, E.; Sala, M. A deterministic algorithm for the distance and weight distribution of binary nonlinear codes. Int. J. Inf. Coding Theory 2018, 5, 18–35. [Google Scholar]
- Sala, M.; Simonetti, I. An algebraic description of Boolean Functions. International Workshop on Coding and Cryptography (WCC) 2007, Versailles, France, 2007. Available online: https://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.74.3211&rep=rep1&type=pdf (accessed on 2 November 2021).
- Bellini, E.; Mora, T.; Sala, M. Algorithmic Approach Using Polynomial Systems for the Nonlinearity of Boolean Functions, Computation Presentation. In Proceedings of the The thirteen conference on Effective Methods in Algebraic Geometry, Trento, Italy, 15–19 June 2015. [Google Scholar]
- Bellini, E. Yet Another Algorithm to Compute the Nonlinearity of a Boolean Function. In Proceedings of the Yet Another Conference on Cryptography, Porquerolles, France, 9–13 June 2014; Available online: http://veron.univ-tln.fr/YACC14/Bellini.pdf (accessed on 2 November 2021).
- MacWilliams, F.J.; Sloane, N.J.A. The Theory of Error-Correcting Codes; North-Holland Publishing Co. Amsterdam, North-Holland Mathematical Library: Amsterdam, North-Holland, 1977; Volume 16. [Google Scholar]
- Carlet, C.; Guillot, P. A new representation of Boolean functions. In Applied Algebra, Algebraic Algorithms and Error-Correcting Codes; Springer: Berlin/Heidelberg, Germany, 1999; pp. 94–103. [Google Scholar]
- Carlet, C.; Guillot, P. Bent, resilient functions and the Numerical Normal Form. DIMACS Ser. Discret. Math. Theor. Comput. Sci. 2001, 56, 87–96. [Google Scholar]
- Carlet, C. On the coset weight divisibility and nonlinearity of resilient and correlation-immune functions. In Sequences and Their Applications; Springer: Berlin/Heidelberg, Germany, 2002; pp. 131–144. [Google Scholar]
- Simonetti, I. On the non-linearity of Boolean functions. In Gröbner Bases, Coding, and Cryptography; RISC Book Series; Sala, M., Mora, T., Perret, L., Sakata, S., Traverso, C., Eds.; Springer: Heidelberg, Germany, 2009; pp. 409–413. [Google Scholar]
- Guerrini, E. On Distance and Optimality in Non-Linear Codes. Master’s Thesis, Department of Mathematics, University of Pisa, Pisa, Italy, 2005. [Google Scholar]
- Seidenberg, A. Constructions in algebra. Trans. Amer. Math. Soc. 1974, 197, 273–313. [Google Scholar] [CrossRef]
- MAGMA: Computational Algebra System for Algebra, Number Theory and Geometry, The University of Sydney Computational Algebra Group. 2020. Available online: http://magma.maths.usyd.edu.au/magma (accessed on 16 December 2021).
- Faugere, J.-C. A new efficient algorithm for computing gröbner bases (f4). J. Pure Appl. Algebra 1999, 139, 61–88. [Google Scholar] [CrossRef]
- Simonetti, I. On Some Applications of Commutative Algebra to Boolean Functions and Their Non-Linearity. Ph.D. Thesis, Department of Mathematics, University of Trento, Trento, Italy, 2007. [Google Scholar]
- Bellini, E. Computational Techniques for Nonlinear Codes and Boolean Functions. Ph.D. Thesis, Department of Mathematics, University of Trento, Trento, Italy, 2014. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).