Abstract
Fragile watermarking algorithms for 3D models has attracted extensive research attention in recent years. Although many literatures have proposed lots of solutions on this issue, low embedding capacity and inaccurate located tampered region are still presented. Higher embedding capacity can reduce the probability of false alarms for authentication, while accurate tamper localization can detect all the modified vertices with fewer unaltered ones. This study proposes three strategies to enhance the embedding capacity and the detection accuracy of our previous algorithm. First, the modified message-digit substitution table can increase the embedding capacity by 11.5%. Second, the modified embedding ratio generation method can be integrated to raise the embedding capacity by about 47.74%. Finally, the strategy adopting a reduced number of reference vertices for authentication code generation accompanying the above two ones improves the embedding capacity up to 123.74%. Extensive experiments show that the proposed algorithm can achieve superior performance in terms of embedding capacity and tamper localization accuracy. Further, the model distortion between the original and the marked ones is small.
1. Introduction
The rise of Internet changes human behavior significantly. Multimedia content can be rapidly shared and dispersed all over the world with the advanced network technology. However, Internet also breeds new information security problems, such as piracy, reproduction, and tampering. Copyright marking algorithms [1] can prevent the above problems from occurring, and robust watermarking and fragile watermarking are two main branches according to their different applications.
Robust watermarking algorithms [2,3,4] can detect copyright information and protect intellectual property rights even when the protected multimedia content is under different malicious attacks. However, fragile watermarking algorithms [5,6,7] can effectively detect and locate the tampered locations even if the protected multimedia content has minimum modifications. Some fragile watermarking algorithms even have the capacity for self-recovery. Recently, some authors [8] proposed a distributed and tamper-proof media transaction framework. The unique watermark information contains a cryptographic hash of the transaction histories in the blockchain and an image hash preserving retrievable original media content. The first part of the watermark is to retrieve the historical transaction trail and the latter part is used to identify the tampered regions. Consequently, copyright marking is still a research topic that deserves our attention.
Whereas fragile watermarking has been extensively studied in images [9,10,11,12,13,14], videos [15,16], and audio [17,18], there are still few studies discussing its application in 3D models. According to the size of the tampered region localization, 3D fragile watermarking algorithms can be classified as either vertex-based or region-based ones. A vertex-based algorithm can exactly locate a modified vertex, whereas a region-based one can only locate a rough region with some unaltered vertices inside. However, a region-based fragile watermarking algorithm has the ability to detect the modification of the topological relationship between vertices.
The first fragile watermarking algorithm on 3D polygonal models was proposed by Yeo and Yeung [19]. They iteratively moved the vertices to new positions to make the location and value indexes, calculated from pre-defined hash functions, consistent. Lin et al. [20] proposed a local mesh parametrization approach to perturb the coordinates of invalid vertices to eliminate the causality problem caused by Yeo and Yeung. Molaei et al. [21] proposed a QIM-based fragile watermarking for 3D triangular mesh models. Watermark data is embedded into the middles of three sides of a marked triangle in the spherical coordinate system. The recognition accuracy and the embedding capacity can be enhanced by increasing the number of marked triangles. To solve the problem of low embedding capacity, Tsai et al. [6] proposed a low-complexity, high-capacity, distortion-controllable, region-based fragile watermarking algorithm with a high embedding rate for 3D polygonal models. A vertex traversal scheme subdivides the input polygonal model into several overlapping embedding blocks, each with one embeddable vertex and its reference vertices. The authentication code is generated by feeding the local geometrical properties of each block into a hash function. The embeddable vertex is then embedded with the authentication code and its vertex coordinates are modified based on a simple message-digit substitution scheme.
Tsai et al.’s proposed algorithm had a higher embedding rate and higher embedding capacity than up-to-date literature. However, the problems of low embedding capacity and inaccurately located tampered regions have not been resolved. The proposed algorithm comprehensively considers three issues that are not discussed in our previous scheme. Thus, the proposed algorithm offers three advantages over the previous method, including higher embedding capacity, higher embedding rate, and accurate tamper localization. In this paper, we employ modified message grabbing and modified embedding ratio generation methods to resolve the problem of low embedding capacity. In addition, we adopt a reduced number of reference vertices for authentication code generation, providing a significant improvement on embedding capacity and embedding rate. Furthermore, the accuracy of tamper localization is consequently raised. Finally, extensive experimental results demonstrate the feasibility of the proposed algorithm.
The rest of paper is organized as follows. In Section 2, Tsai et al.’s proposed algorithm is introduced. In Section 3, we give detailed descriptions of our three strategies to improve the embedding capacity. Section 4 shows the experimental evaluations; finally, conclusions and future studies are made in Section 5.
2. Tsai et al.’s Proposed Algorithm
This section provides a review of Tsai et al.’s proposed algorithm, and its flowchart is shown in Figure 1. The proposed algorithm inputs a polygonal model with vertices and its topological information and then constructs a vertex neighboring table in the preprocessing process. The polygonal model is subdivided into lots of overlapping embedding blocks, each with one embeddable vertex and its reference vertices, based on an iterative vertex traversal mechanism. Each block is the basic element for the authentication code generation, embedding, reconstruction, and tamper localization processes. Taking the embedding block shown in Figure 2 for example, is the embeddable vertex and , , , and are the reference vertices of . is the center of the reference vertices of .
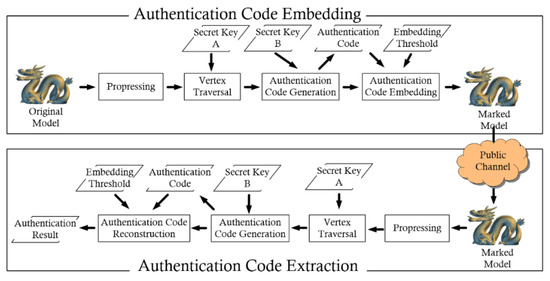
Figure 1.
Flowchart of Tsai et al.’s proposed algorithm.
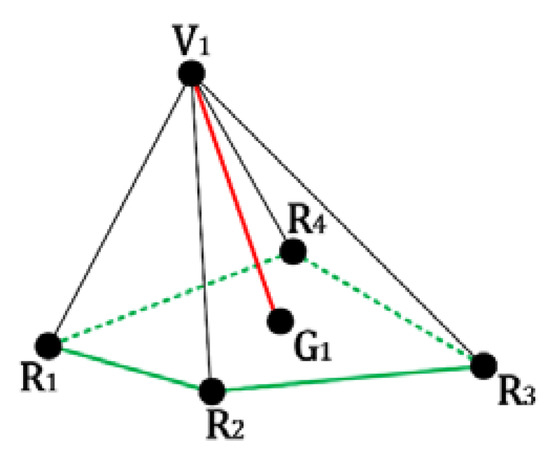
Figure 2.
One embedding block of Tsai et al.’s proposed algorithm.
For each embedding block, the local geometrical property concerning the topological relationship is fed into the hash function to obtain the authentication code. Thereafter, the authors calculated the embedding ratio between the length of the embeddable vertex to the center of its reference vertices and the summation of all sides of the reference vertices for message embedding. Continuing the example in Figure 2, the embedding ratio is shown in (1), where is the summation of all sides , , , and .
Finally, the authors select parts of the authentication code to embed into above ratio. The data-embedded ratio is derived by modifying the next few decimal digits after the first non-zero one of using a simple message-digit substitution mechanism shown in Table 1. The data-embedded vertex can be then obtained following the direction of with a data-embedded ratio. Figure 3 shows the modification example, where is the vertex with the authentication code embedded. Experimental results demonstrate the feasibility of the proposed algorithm.

Table 1.
Tsai et al.’s message-digit substitution table.
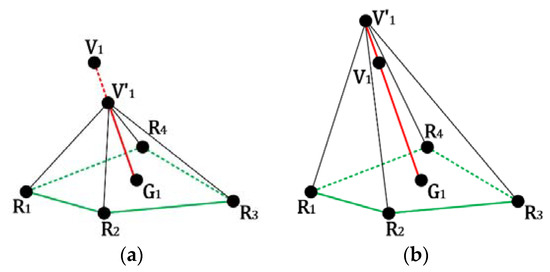
Figure 3.
The modification example for the embeddable vertex after the authentication code is embedded: (a) ; (b) .
3. The Proposed Algorithm
This section shows three improvement methods to provide higher embedding capacity than Tsai et al.’s proposed algorithm, including modified message grabbing, modified embedding ratio generation [22], and a reduced number of reference vertices for message embedding. The proposed algorithm can also support higher embedding rate and accurate tamper localization.
3.1. Modified Message Grabbing Method
The authentication code embedding process in Tsai et al.’s proposed algorithm used a simple message-digit substitution scheme shown in Table 1 to modify the embedded ratio. The distance with the center of its reference vertices for each embeddable vertex is consequently modified. Three-bit authentication code is grabbed one time and one more bit can be grabbed again if the above three-bit code equals 110 or 111. In our test, the embedding capacity rises effectively if a four-bit authentication code is firstly grabbed and the last bit is left for the next iteration if the grabbed four-bit binary code is larger than one-bit decimal digit. Table 2 shows our message-digit substitution table. The bit with a strikeout sign means that the bit should be left for next iteration because the decimal value for the grabbed four-bit binary code is larger than nine.

Table 2.
Our proposed message-digit substitution table.
3.2. Modified Embedding Ratio Generation Method
From the above message-digit substitution table, we can know one decimal digit can have a three- to four-bit authentication code embedded. However, from the experimental results in Tsai et al.’s proposed algorithm, the number of most used decimal digits is three. It means most embedding ratios equal to 0.0XEEEN, where X is the first non-zero digit, E is the decimal digit that can have the authentication code embedded, and N is the digit without a message embedded for avoiding extraction error. If we can change the embedding ratio with the value of 0.0XEEEN to 0.XEEEEN, one more decimal digit can be used to further raise the embedding capacity.
We then modify the embedding ratio generation method shown in (1) from the summation of all sides of the reference vertices to maximum, minimum, and average side length (see blue line in Figure 4) between the reference vertices for each embeddable vertex. The experimental results show that the embedding ratio using minimum side length can achieve highest embedding capacity.
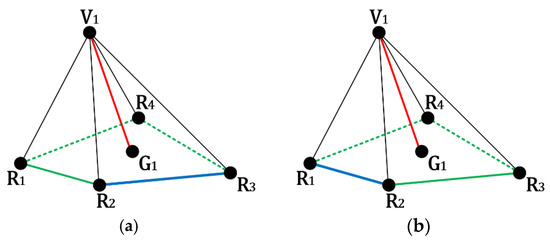
Figure 4.
Modified embedding ratio generation method: (a) Maximum side length; (b) Minimum side length.
3.3. Reduced Number of Reference Vertices for Authentication Code Generation
Tsai et al.’s proposed algorithm uses all the reference vertices for authentication code generation. Therefore, only 24 to 30 percent of vertices [6] can be message-embedded. This improvement adopts a user-defined embedding parameter within 0 and 1 to control the ratio of used reference vertices for each embeddable vertex. Equation (2) shows the controlling mechanism, where and are the original and final number of used reference vertices for the embeddable vertex . We then randomly obtain reference vertices for the remaining process.
However, not each vertex pair in the original input model has one edge to connect them. For the example shown in Figure 2, assume that , , and are the selected reference vertices for the embeddable vertex . Comparing Figure 2 with Figure 5, no edges are presented to connect the vertices and . To make the following processes correctly performed, we construct the ‘virtual’ edge to connect the corresponding two unconnected vertices. becomes the center of the used reference vertices , , and . Further, the minimum number of used reference vertices is set as 3.
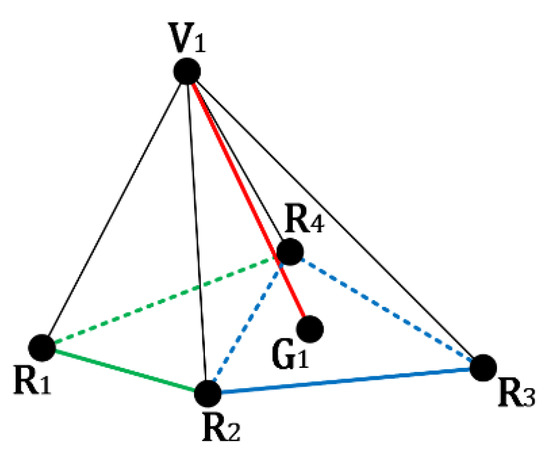
Figure 5.
One example of a reduced number of reference vertices for authentication code generation.
4. Experimental Evaluations
This section presents the experimental results obtained from twenty-five 3D polygonal models shown in Figure 6, where and mean the number of vertices and faces separately. Microsoft Visual C++ programming language was used to implement the proposed algorithm on a personal computer with an Intel Core i7-6700K 4.00 GHz processor and 16 GB RAM. The distortion between the original and marked models was measured by normalized root-mean-squared error, which is derived from dividing the root-mean-squared error by the model size.
Figure 6.
Visual effects of our twenty-five test models.
First, this section presents the embedding capacity comparison for each improved strategy with Tsai et al.’s proposed algorithm. We also show the model distortion for different embedding ratio generation methods. Finally, we present the experimental results for tamper detection to demonstrate the feasibility of our proposed algorithm.
Table 3 shows the embedding capacity comparison under different embedding thresholds between Tsai et al.’s and our message grabbing method. The experimental results show that our message grabbing method can effectively raise the embedding capacity, exceeding 11.5% on average for all embedding thresholds.

Table 3.
Experimental results for our message grabbing method.
Table 4 shows the embedding capacity comparison for different embedding ratio generation methods, including maximum (MAX), minimum (MIN), and average (AVE) of all the side lengths with the embedding threshold . The embedding capacity using the summation (SUM) method for each model is shown in Table 3. Obviously, the embedding ratio generation method using the minimum side length can have the maximum embedding capacity, improving by about 47.74% on average, with our modified message grabbing method. From the experimental results, we also found that the highest embedding capacity for each embeddable vertex in each 3D polygonal model is between 14 and 16. Four decimal digits of the calculated embedding ratio are used for data embedding, each with three or four bits. Table 5 shows the model distortion for each test model under different embedding ratio generation methods. The model distortion using the MIN method is only 0.009% of the model size, on average.

Table 4.
Experimental results for our embedding ratio generation method.

Table 5.
Model distortion between the original and marked models.
This section shows the experimental results for adopting a reduced number of reference vertices during the authentication code generation. When not all reference vertices are used, the residual unused reference vertices may be the embeddable ones in some iterations. Because the number of embedded vertices is increased, and the total embedding capacity can be effectively raised. Table 6 shows the embedding rate under different embedding parameters for each test model. Obviously, the embedding rate can be effectively raised from 23.93~31.25% to 35.32~42.80%. Table 7, Table 8 and Table 9 show the embedding capacity comparison for each model under different embedding parameters. When the value of the embedding parameter is smaller, it means the ratio of used reference vertices is decreased. The total embedding capacity is increased with more embeddable vertices. The improved ratio, on average, can be improved from 47.74% (see Table 4), 94.13%, or 121.37%, to 123.74% with different embedding parameters using the minimum side length for authentication code generation.

Table 6.
Embedding rate under different embedding parameters for each test model.

Table 7.
The embedding capacity comparison for each model under .

Table 8.
The embedding capacity comparison for each model under .

Table 9.
The embedding capacity comparison for each model under .
Finally, Table 10 shows the number of detected suspicious vertices for each model under different embedding parameters. We randomly add or subtract 0.01% of the length, width, and height of the bounding volume of input model from the x, y, and z coordinate values of 50 vertices separately. The proposed algorithm is then used to perform tamper localization. Recall that a region-based tamper detection algorithm can only locate a rough region with some unaltered vertices inside. Therefore, any one vertex that is altered in the embedding block may lead to all the vertices within the block being regarded as suspicious. As the value of embedding parameter is decreased, the embedding block is smaller with fewer vertices. Thus, the number of suspicious vertices is decreased and the accuracy of the located tampered region is higher. The only exception is the results of embedding parameter 0.50 and 0.25 because their numbers of reference vertices for each embeddable vertex are similar.

Table 10.
Number of suspicious vertices detected for each model under different embedding parameters.
5. Conclusions and Future Studies
This paper proposes three strategies to improve Tsai et al.’s proposed algorithm. We firstly modified the message grabbing method to raise the embedding capacity above 11.5%. Further, we also modified Tsai et al.’s embedding ratio generation method, increasing the embedding capacity to 47.74%. Finally, the strategy adopting a reduced number of reference vertices for message embedding accompanying the above two ones improves the embedding capacity up to 123.74%. The experimental results demonstrate the feasibility of the proposed algorithm with higher embedding capacity, higher embedding rate, and accurate tamper localization. Further, the model distortion between the original and the marked ones is small.
Future studies could fruitfully explore the proposed algorithm further for point geometries without topological relationship between vertices. Thereafter, providing self-recovery ability is another important research issue to be discussed.
Author Contributions
Y.-Y.T. supervised the whole work, designed the experiments, analyzed the performance of the proposed idea and wrote the paper. Y.-S.T. and C.-C.C. perform experiments simulations and collect the results.
Funding
This research was funded by Ministry of Science and Technology of Taiwan under the grant numbers MOST 106-2221-E-468-022, MOST 106-2218-E-468-001, and MOST 106-2632-E-468-003.
Acknowledgments
The authors would like to thank the editor and three anonymous reviewers for their constructive suggestions in improving the paper significantly.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Petitcolas, F.A.P.; Anderson, R.J.; Kuhn, M.G. Information Hiding—A Survey. Proc. IEEE 1999, 87, 1062–1078. [Google Scholar] [CrossRef]
- Bors, A.G.; Luo, M. Optimized 3D Watermarking for Minimal Surface Distortion. IEEE Trans. Image Process. 2013, 22, 1822–1835. [Google Scholar] [CrossRef] [PubMed]
- Chen, H.K.; Chen, W.S. GPU-accelerated Blind and Robust 3D Mesh Watermarking by Geometry Image. Multimedia Tools Appl. 2016, 75, 10077–10096. [Google Scholar] [CrossRef]
- Hou, J.U.; Kim, D.G.; Lee, H.K. Blind 3D Mesh Watermarking for 3D Printed Model by Analyzing Layering Artifact. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2712–2725. [Google Scholar] [CrossRef]
- Chen, T.Y.; Hwang, M.S.; Jan, J.K. Adaptive Authentication Schemes for 3D Mesh Models. Int. J. Innov. Comput. Inf. Control 2009, 5, 4561–4572. [Google Scholar]
- Tsai, Y.Y.; Chen, T.C.; Huang, Y.H. A Low-complexity Region-based Authentication Algorithm for 3D Polygonal Models. Secur. Commun. Netw. 2017, 2017, 1096463. [Google Scholar] [CrossRef]
- Wang, J.T.; Chang, Y.C.; Yu, C.Y.; Yu, S.S. Hamming Code Based Watermarking Scheme for 3D Model Verification. Math. Probl. Eng. 2014, 2014, 241093. [Google Scholar]
- Bhowmik, D.; Feng, T. The Multimedia Blockchain: A Distributed and Tamper-proof Media Transaction Framework. In Proceedings of the 22nd International Conference on Digital Signal Processing, London, UK, 23–25 August 2017. [Google Scholar]
- Fan, M.; Wang, H. An Enhanced Fragile Watermarking Scheme to Digital Image Protection and Self-Recovery. Signal Process. Image Commun. 2018, 66, 19–29. [Google Scholar] [CrossRef]
- Huynh-The, T.; Banos, O.; Lee, S.; Yoon, Y.; Le-Tien, T. Improving Digital Image Watermarking by Means of Optimal Channel Selection. Expert Syst. Appl. 2016, 62, 177–189. [Google Scholar] [CrossRef]
- Lo, C.C.; Hu, Y.C. A Novel Reversible Image Authentication Scheme for Digital Images. Signal Process. 2014, 98, 174–185. [Google Scholar] [CrossRef]
- Qin, C.; Zhang, X.; Dong, J.; Wang, J. Fragile Image Watermarking with Pixel-wise Recovery Based on Overlapping Embedding Strategy. Signal Process. 2017, 138, 280–293. [Google Scholar] [CrossRef]
- Singh, D.; Singh, S.K. DCT Based Efficient Fragile Watermarking Scheme for Image Authentication and Restoration. Multimedia Tools Appl. 2017, 76, 953–977. [Google Scholar] [CrossRef]
- Wang, X.Y.; Zhang, J.M. A Novel Image Authentication and Recovery Algorithm Based on Chaos and Hamming Code. Acta Phys. Sin. 2014, 63, 020701. [Google Scholar]
- Asikuzzaman, M.; Pickering, M.R. An Overview of Digital Video Watermarking. IEEE Trans. Circuits Syst. Video Technol. 2017. accepted. [Google Scholar] [CrossRef]
- Fallahpour, M.; Shirmohammadi, S.; Semsarzadeh, M.; Zhao, J. Tampering Detection in Compressed Digital Video Using Watermarking. IEEE Trans. Instrum. Meas. 2014, 63, 1057–1072. [Google Scholar] [CrossRef]
- Qian, Q.; Wang, H.X.; Hu, Y.; Zhou, L.N.; Li, J.F. A Dual Fragile Watermarking Scheme for Speech Authentication. Multimedia Tools Appl. 2016, 75, 13431–13450. [Google Scholar] [CrossRef]
- Renza, D.; Ballesteros, L.D.M.; Lemus, C. Authenticity Verification of Audio Signals Based on Fragile Watermarking for Audio Forensics. Expert Syst. Appl. 2018, 91, 211–222. [Google Scholar] [CrossRef]
- Yeo, B.L.; Yeung, M.M. Watermarking 3-D Objects for Verification. IEEE Comput. Graph. Appl. 1999, 19, 36–45. [Google Scholar]
- Lin, H.Y.S.; Liao, H.Y.M.; Lu, C.S.; Lin, J.C. Fragile Watermarking for Authenticating 3-D Polygonal Meshes. IEEE Trans. Multimedia 2005, 7, 997–1006. [Google Scholar] [CrossRef]
- Molaei, A.M.; Ebrahimnezhad, H.; Sedaaghi, M.H. A Blind Fragile Watermarking Method for 3D Models Based on Geometric Properties of Triangles. 3D Res. 2013, 4, 4. [Google Scholar] [CrossRef]
- Tsai, Y.Y.; Tsai, Y.S.; Chang, C.C. An Improved Region-based Tampered Detection Algorithm for 3D Polygonal Models. In Proceedings of the 4th IEEE International Conference on Applied System Innovation, Chiba, Japan, 13–17 April 2018. [Google Scholar]
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).