Hacking Exposed: Leveraging Google Dorks, Shodan, and Censys for Cyber Attacks and the Defense Against Them
Abstract
1. Introduction
- Provide a brief overview of Google dorks, Shodan, and Censys, highlighting their functionalities and how they work; also highlight the latest state of the art with their application context and major contributions.
- Explore the potential for cyberattacks enabled by these tools, presenting use cases where these platforms have been used for both offensive and defensive purposes.
- Propose proactive defense strategies to mitigate exploitation risks associated with Google dorks, Shodan, and Censys, aiming to enhance the resilience of critical digital infrastructure against evolving cyber threats.
- Introduce an automated all-in-one tool designed to consolidate the functionalities of Google dorks, Shodan, and Censys, offering a streamlined solution for vulnerability detection and analysis.
2. Background and Overview of Script Kiddies, Google Dorks, Shodan, and Censys
2.1. Who Are Script Kiddies?
2.2. Google Dorks
2.3. Shodan
2.4. Censys
3. Use Cases of Employment of Google Dorks, Shodan, and Censys for Offensive Exploitation
3.1. Offensive Exploitation Use Cases of Google Dorks
3.2. Offensive Exploitation Use Cases of Shodan
3.3. Offensive Exploitation Use Cases of Censys
4. Defensive Use of Google Dorks, Shodan, and Censys
4.1. Google Dorks for Defense
4.2. Shodan for Defense
4.3. Censys for Defense
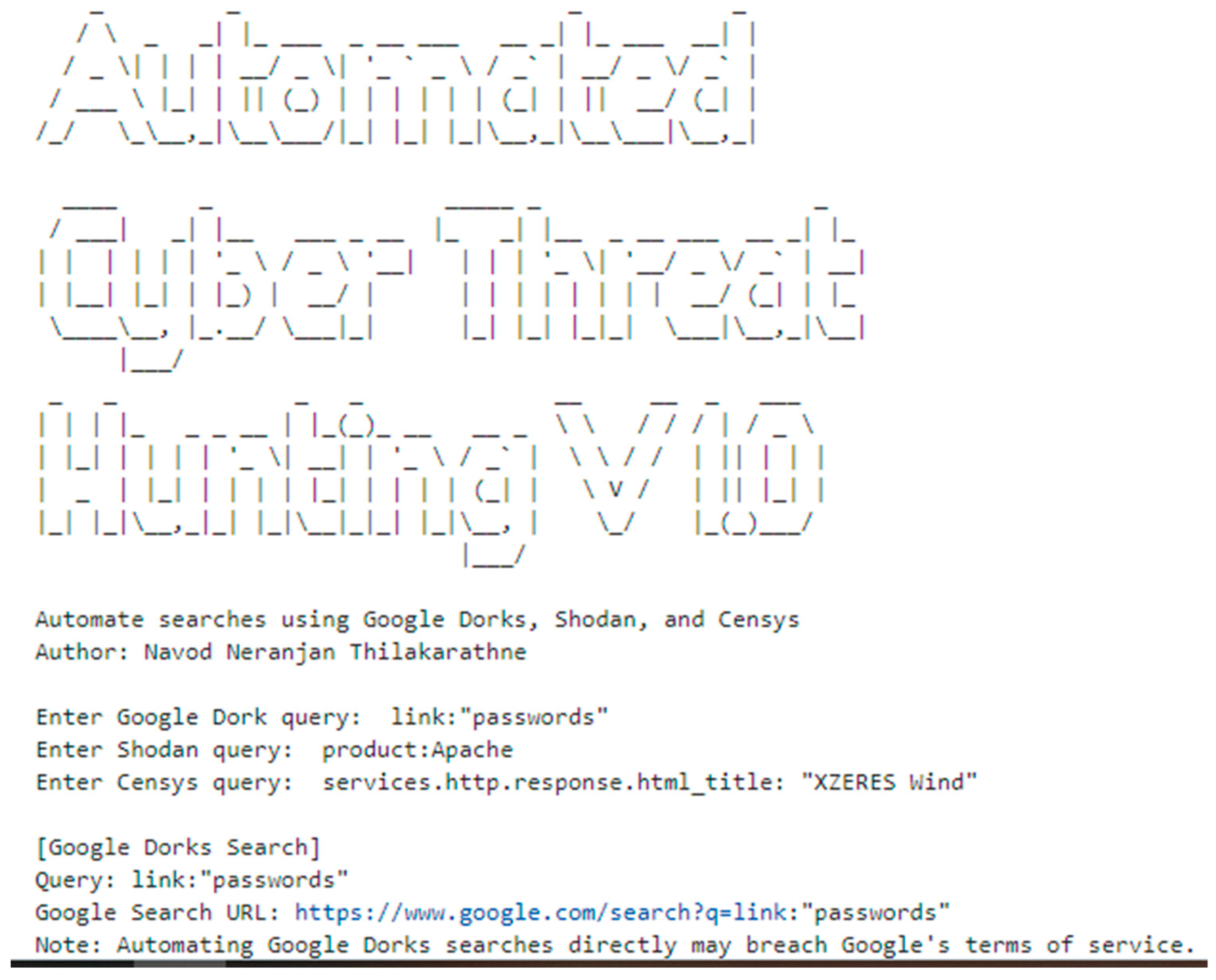
5. Development of Automated Cyber Threat Hunting Tool
5.1. Performance Metrics and Scalability Analysis
- Response timeThe tool’s efficiency was measured by the average time it takes to retrieve and process results from Google dorks, Shodan, and Censys based on various queries.
- AccuracyThe precision of the results was evaluated by comparing the tool’s findings with manually verified vulnerabilities and exposed systems.
- Resource utilizationThe tool’s CPU and memory usage were monitored to assess its efficiency during the scanning and data consolidation processes.
- Success rateThe percentage of successful queries and retrieved results from each platform was tracked to measure the reliability of the tool.
- ThroughputThe tool was assessed on how many queries it could handle within a given time frame, ensuring it can scale up to support enterprise-level operations.
- API limitationsThe tool’s scalability is also influenced by the API limits imposed by Shodan and Censys, which may impact its ability to handle large-scale data retrieval.
5.2. Tool Workflow and User Interaction
5.3. Limitations
6. Proactive Defense Strategies Against Exploitation
- Vulnerability management and patch managementOne of the fundamental strategies in proactive defense is the identification and management of vulnerabilities in an organization’s systems. Regular vulnerability assessments using tools like Shodan, Censys, and Google dorks can help identify exposed assets, outdated software, and security misconfigurations that may be susceptible to exploitation [2,3,4]. Once vulnerabilities are identified, patch management becomes crucial. This involves applying security patches, updates, and fixes promptly to prevent attackers from exploiting known vulnerabilities. Implementing automated patch management systems can reduce the risk of human error and ensure that updates are applied across the organization in a timely manner, making it more difficult for attackers to exploit known flaws.
- Network segmentation and least privilege accessAnother proactive defense measure is network segmentation, which involves dividing the network into smaller, isolated segments to limit the impact of a breach. If an attacker compromises one segment, they are restricted from moving laterally across the entire network [10,11]. This reduces the potential for exploitation of other critical systems. Additionally, the principle of least privileged access should be enforced, ensuring that users and systems are granted only the minimum permissions necessary to perform their tasks. This minimizes the attack surface and prevents attackers from gaining unauthorized access to sensitive data or critical infrastructure if they breach one part of the system [10,11].
- Continuous monitoring and threat intelligenceProactive defense strategies rely heavily on continuous monitoring to detect unusual activities and early indicators of compromise. Security information and event management (SIEM) tools can aggregate and analyze log data from across the network to identify suspicious patterns or signs of an attack in real-time. Threat intelligence services, such as those provided by vendors like FireEye, CrowdStrike, or open-source platforms like MISP, offer actionable insights into emerging threats and known attack methods that can be integrated into security protocols to prepare defenses accordingly [40,41,42,43]. By continuously monitoring the environment and incorporating threat intelligence, organizations can quickly identify and respond to potential attacks, even before they fully materialize [54].
- Red teaming and penetration testingAnother highly effective proactive strategy is red teaming or penetration testing, where cybersecurity professionals simulate real-world attacks on the organization’s systems to identify vulnerabilities that could be exploited. Unlike traditional security audits, which focus on identifying specific vulnerabilities, red teaming provides a more comprehensive, adversarial approach that simulates the tactics, techniques, and procedures (TTPs) of actual cyber attackers [46,47,48,49,55,56]. This allows organizations to assess how well their defenses hold up against sophisticated attacks and identify weaknesses that may not be apparent through conventional testing. Penetration testing tools, like Metasploit and Nessus, help security teams uncover hidden vulnerabilities and flaws that could be exploited by attackers, providing them with actionable information to strengthen security before an attack occurs [46,47,48,49].
- User awareness and security trainingHuman error remains one of the most significant factors in security breaches, making security awareness training a critical component of proactive defense. Organizations should provide ongoing training to employees on recognizing phishing emails, avoiding suspicious links, and adhering to best security practices, such as strong password policies and multi-factor authentication (MFA). Social engineering attacks, such as phishing, remain a major vector for exploitation, and training users to be aware of these tactics is essential in preventing initial access to systems. Regular drills, phishing simulations, and cybersecurity workshops can help build a security-conscious culture, reducing the likelihood of successful exploitation through human vulnerabilities [50,51,52,53].
- Incident response planning and simulationProactive defense also includes having a well-defined incident response plan in place, which outlines the steps to take in the event of a breach. The plan should include procedures for containment, eradication, and recovery, ensuring that teams can respond swiftly to minimize damage. Conducting tabletop exercises and live simulations of cyberattacks can help prepare the response teams for real-world incidents. These exercises can identify gaps in the response plan and improve the organization’s ability to recover quickly from an attack [50,51,52,53].
- Regular vulnerability scanning
- Implementation of strong access controls
- Encryption and proper configuration
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- IoT Analytics. State of IoT 2024: Number of connected IoT devices growing 13% to 18.8 Billion Globally. Available online: https://iot-analytics.com/number-connected-iot-devices/ (accessed on 27 October 2024).
- AI and the Global ‘Datasphere’: How Much Information Will Humanity Have By 2025? Available online: https://www.datauniverseevent.com/en-us/blog/general/AI-and-the-Global-Datasphere-How-Much-Information-Will-Humanity-Have-By-2025.html (accessed on 27 October 2024).
- LinkedIn. Are Your Smart Devices Putting Your Company at Risk? A Guide to Securing Your Connected Future. Available online: https://www.linkedin.com/pulse/your-smart-devices-putting-company-risk-guide-securing-connected-iiwsf/ (accessed on 27 October 2024).
- Cyber Security Breach Statistics 2024. Available online: https://www.stationx.net/cyber-security-breach-statistics/ (accessed on 27 October 2024).
- Palo Alto Networks. The 2024 Benchmark Report on IoT Security. Available online: https://www.paloaltonetworks.com/resources/research/the-2024-benchmark-report-on-iot-security (accessed on 27 October 2024).
- Evolve Security. The Actual Cost of Cybercrime. Available online: https://www.evolvesecurity.com/blog-posts/actual-cost-of-cybercrime (accessed on 27 October 2024).
- Kanakasabai, J.N.; Othman, S.H.; Siraj, M.M.; Rahman, M.H.; Darus, M.Z.A. Google Dorking Commands-based Approach for Assisting Forensic Investigators in Gender Identification of Social Media Text Data. In Proceedings of the 2023 3rd International Conference on Intelligent Cybernetics Technology & Applications (ICICyTA), Denpasar, Indonesia, 13–15 December 2023; pp. 466–471. [Google Scholar] [CrossRef]
- Toffalini, F.; Abbà, M.; Carra, D.; Balzarotti, D. Google Dorks: Analysis, Creation, and New Defenses. In Detection of Intrusions and Malware, and Vulnerability Assessment; Caballero, J., Zurutuza, U., Rodríguez, R.J., Eds.; Lecture Notes in Computer Science; Springer International Publishing: Cham, Switzerland, 2016; Volume 9721, pp. 255–275. [Google Scholar] [CrossRef]
- Phulre, A.K.; Kamble, M.; Phulre, S. Content Management Systems hacking probabilities for Admin Access with Google Dorking and database code injection for web content security. In Proceedings of the 2nd International Conference on Data, Engineering and Applications (IDEA), Bhopal, India, 28–29 February 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Evangelista, J.R.G.; Sassi, R.J.; Romero, M. Google Hacking Database Attributes Enrichment and Conversion to Enable the Application of Machine Learning Techniques. Res. Sq. 2022. [Google Scholar] [CrossRef]
- Korneev, N. The Attack Vector on the Critical Information Infrastructure of the Fuel and Energy Complex Ecosystem. CEUR Workshop Proc. 2021, 3035, 59–65. [Google Scholar]
- Mansfield-Devine, S. Google hacking 101. Netw. Secur. 2009, 2009, 4–6. [Google Scholar] [CrossRef]
- Matherly, J. Complete Guide to Shodan. Available online: https://ia800705.us.archive.org/17/items/shodan-book-extras/shodan/shodan.pdf (accessed on 1 December 2024).
- Bada, M.; Pete, I. An exploration of the cybercrime ecosystem around Shodan. In Proceedings of the 2020 7th International Conference on Internet of Things: Systems, Management and Security (IOTSMS), Paris, France, 14–16 December 2020; pp. 1–8. [Google Scholar] [CrossRef]
- Mulero-Palencia, S.; Baeza, V.M. Detection of Vulnerabilities in Smart Buildings Using the Shodan Tool. Electronics 2023, 12, 4815. [Google Scholar] [CrossRef]
- Rae, J.S.; Chowdhury, M.M.; Jochen, M. Internet of Things Device Hardening Using Shodan.io and ShoVAT: A Survey. In Proceedings of the 2019 IEEE International Conference on Electro Information Technology (EIT), Brookings, SD, USA, 20–22 May 2019; pp. 379–385. [Google Scholar] [CrossRef]
- Bodenheim, R.; Butts, J.; Dunlap, S.; Mullins, B. Evaluation of the ability of the Shodan search engine to identify Internet-facing industrial control devices. Int. J. Crit. Infrastruct. Prot. 2014, 7, 114–123. [Google Scholar] [CrossRef]
- Zaidi, N.; Kaushik, H.; Bablani, D.; Bansal, R.; Kumar, P. A Study of Exposure of IoT Devices in India: Using Shodan Search Engine. In Information Systems Design and Intelligent Applications; Bhateja, V., Nguyen, B.L., Nguyen, N.G., Satapathy, S.C., Le, D.-N., Eds.; Advances in Intelligent Systems and Computing; Springer: Singapore, 2018; Volume 672, pp. 1044–1053. [Google Scholar] [CrossRef]
- Albataineh, A.; Alsmadi, I. IoT and the Risk of Internet Exposure: Risk Assessment Using Shodan Queries. In Proceedings of the 2019 IEEE 20th International Symposium on “A World of Wireless, Mobile and Multimedia Networks” (WoWMoM), Washington, DC, USA, 10–12 June 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Bennett, C.; Abdou, A.; Van Oorschot, P.C. Empirical Scanning Analysis of Censys and Shodan. In Proceedings of the 2021 Workshop on Measurements, Attacks, and Defenses for the Web, Virtual, 25 February 2021. [Google Scholar] [CrossRef]
- Daskevics, A.; Nikiforova, A. ShoBeVODSDT: Shodan and Binary Edge based vulnerable open data sources detection tool or what Internet of Things Search Engines know about you. In Proceedings of the 2021 Second International Conference on Intelligent Data Science Technologies and Applications (IDSTA), Tartu, Estonia, 15–17 November 2021; pp. 38–45. [Google Scholar] [CrossRef]
- Genge, B.; Enăchescu, C. ShoVAT: Shodan-based vulnerability assessment tool for Internet-facing services. Secur. Comm. Netw. 2016, 9, 2696–2714. [Google Scholar] [CrossRef]
- Zolotykh, M. Study of Crawlers of Search Engine ‘Shodan.io’. In Proceedings of the 2021 Ural Symposium on Biomedical Engineering, Radioelectronics and Information Technology (USBEREIT), Yekaterinburg, Russia, 13–14 May 2021; pp. 0419–0422. [Google Scholar] [CrossRef]
- Fernández-Caramés, T.M.; Fraga-Lamas, P. Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases. Sensors 2020, 20, 3048. [Google Scholar] [CrossRef] [PubMed]
- Alsmadi, I.; Dwekat, Z.; Cantu, R.; Al-Ahmad, B. Vulnerability assessment of industrial systems using Shodan. Clust. Comput 2022, 25, 1563–1573. [Google Scholar] [CrossRef]
- Al-Alami, H.; Hadi, A.; Al-Bahadili, H. Vulnerability scanning of IoT devices in Jordan using Shodan. In Proceedings of the 2017 2nd International Conference on the Applications of Information Technology in Developing Renewable Energy Processes & Systems (IT-DREPS), Amman, Jordan, 6–7 December 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Munir, R.; Mufti, M.R.; Awan, I.; Hu, Y.F.; Disso, J.P. Detection, Mitigation and Quantitative Security Risk Assessment of Invisible Attacks at Enterprise Network. In Proceedings of the 2015 3rd International Conference on Future Internet of Things and Cloud, Rome, Italy, 24–26 August 2015; pp. 256–263. [Google Scholar] [CrossRef]
- Chen, Y.; Lian, X.; Yu, D.; Lv, S.; Hao, S.; Ma, Y. Exploring Shodan from the Perspective of Industrial Control Systems. IEEE Access 2020, 8, 75359–75369. [Google Scholar] [CrossRef]
- Fagroud, F.Z.; Lahmar, E.H.B.; Toumi, H.; Achtaich, K.; El Filali, S. IOT Search Engines: Study of Data Collection Methods. In Advances on Smart and Soft Computing; Saeed, F., Al-Hadhrami, T., Mohammed, F., Mohammed, E., Eds.; Advances in Intelligent Systems and Computing; Springer: Singapore, 2021; Volume 1188, pp. 261–272. [Google Scholar] [CrossRef]
- Durumeric, Z.; Adrian, D.; Mirian, A.; Bailey, M.; Halderman, J.A. A Search Engine Backed by Internet-Wide Scanning. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; pp. 542–553. [Google Scholar] [CrossRef]
- Lee, S.; Shin, S.-H.; Roh, B. Abnormal Behavior-Based Detection of Shodan and Censys-Like Scanning. In Proceedings of the 2017 Ninth International Conference on Ubiquitous and Future Networks (ICUFN), Milan, Italy, 4–7 July 2017; pp. 1048–1052. [Google Scholar] [CrossRef]
- Fagroud, F.Z.; Lahmar, E.H.B.; Amine, M.; Toumi, H.; El Filali, S. What does mean search engine for IOT or IOT search engine. In Proceedings of the 4th International Conference on Big Data and Internet of Things, Rabat, Morocco, 23–24 October 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Ueda, T.; Sasaki, T.; Yoshioka, K.; Matsumoto, T. An Internet-Wide View of Connected Cars: Discovery of Exposed Automotive Devices. In Proceedings of the 17th International Conference on Availability, Reliability and Security, Vienna, Austria, 23–26 August 2022; pp. 1–8. [Google Scholar] [CrossRef]
- Zhang, J.; Notani, J.; Gu, G. Characterizing Google Hacking: A First Large-Scale Quantitative Study. In International Conference on Security and Privacy in Communication Networks; Tian, J., Jing, J., Srivatsa, M., Eds.; Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering; Springer International Publishing: Cham, Switzerland, 2015; Volume 152, pp. 602–622. [Google Scholar] [CrossRef]
- Lee, S.; Im, S.; Shin, S.-H.; Roh, B.; Lee, C. Implementation and vulnerability test of stealth port scanning attacks using ZMap of censys engine. In Proceedings of the 2016 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Republic of Korea, 19–21 October 2016; pp. 681–683. [Google Scholar] [CrossRef]
- Krebs on Security. As Scope of 2012 Breach Expands, LinkedIn to Again Reset Passwords for Some Users. Available online: https://krebsonsecurity.com/2016/05/as-scope-of-2012-breach-expands-linkedin-to-again-reset-passwords-for-some-users/ (accessed on 15 November 2024).
- Lee, N. Cyberattacks, Prevention, and Countermeasures. In Counterterrorism and Cybersecurity; Springer International Publishing: Cham, Switzerland, 2024; pp. 295–342. [Google Scholar] [CrossRef]
- Khan, S.; Kabanov, I.; Hua, Y.; Madnick, S. A Systematic Analysis of the Capital One Data Breach: Critical Lessons Learned. ACM Trans. Priv. Secur. 2023, 26, 1–29. [Google Scholar] [CrossRef]
- UpGuard. Losing Face: Two More Cases of Third-Party Facebook App Data Exposure. Available online: https://www.upguard.com/breaches/facebook-user-data-leak (accessed on 15 November 2024).
- Cervini, J.; Rubin, A.; Watkins, L. Don’t Drink the Cyber: Extrapolating the Possibilities of Oldsmar’s Water Treatment Cyberattack. ICCWS 2022, 17, 19–25. [Google Scholar] [CrossRef]
- Lonergan, E.D.; Lonergan, S.W. Cyber Operations, Accommodative Signaling, and the De-Escalation of International Crises. Secur. Stud. 2022, 31, 32–64. [Google Scholar] [CrossRef]
- Lehman, G.; Maras, P. Cyber-Attack Against Ukrainian Power Plants. Prykarpattyaoblenergo and Kyivoblenergo. Available online: https://nsarchive.gwu.edu/media/15331/ocr (accessed on 1 December 2024).
- API Security News. Issue 111: API Vulnerabilities in AWS, Tesla Backup Gateway, Twitter. Available online: https://apisecurity.io/issue-111-api-vulnerabilities-aws-tesla-backup-gateway-twitter/ (accessed on 18 November 2024).
- Hackers Are Targeting Internet-Connected Gas Stations. Available online: https://www.vice.com/en/article/hackers-are-targeting-internet-connected-gas-stations/ (accessed on 18 November 2024).
- Margolis, J.; Oh, T.T.; Jadhav, S.; Kim, Y.H.; Kim, J.N. An In-Depth Analysis of the Mirai Botnet. In Proceedings of the 2017 International Conference on Software Security and Assurance (ICSSA), Altoona, PA, USA, 24–25 July 2017; pp. 6–12. [Google Scholar] [CrossRef]
- Palo Alto Networks. The Right Approach to Zero Trust Security for Medical IoT Devices. Available online: https://www.paloaltonetworks.com/resources/whitepapers/right-approach-zero-trust-medical-iot (accessed on 18 November 2024).
- Alshamsi, O.; Shaalan, K.; Butt, U. Towards Securing Smart Homes: A Systematic Literature Review of Malware Detection Techniques and Recommended Prevention Approach. Information 2024, 15, 631. [Google Scholar] [CrossRef]
- McGrath, J.K. Will Updated Electricity Infrastructure Security Protect the Grid? A Case Study Modeling Electrical Substation Attacks. Infrastructures 2018, 3, 53. [Google Scholar] [CrossRef]
- Khattak, A.M.; Khanji, S.I.; Khan, W.A. Smart Meter Security: Vulnerabilities, Threat Impacts, and Countermeasures. In Proceedings of the 13th International Conference on Ubiquitous Information Management and Communication (IMCOM) 2019, Phuket, Thailand, 4–6 January 2019; Lee, S., Ismail, R., Choo, H., Eds.; Advances in Intelligent Systems and Computing; Springer International Publishing: Cham, Switzerland, 2019; Volume 935, pp. 554–562. [Google Scholar] [CrossRef]
- Cyberintel Magazine. Dahua Cameras That Haven’t Been Fixed Are Susceptible to Unauthenticated Remote Access. Available online: https://cyberintelmag.com/iot/dahua-cameras-that-havent-been-fixed-are-susceptible-to-unauthenticated-remote-access/ (accessed on 18 November 2024).
- Zhang, Z.; He, W.; Li, W.; Abdous, M. Cybersecurity awareness training programs: A cost–benefit analysis framework. Ind. Manag. Data Syst. 2021, 121, 613–636. [Google Scholar] [CrossRef]
- Ahmad, A.; Desouza, K.C.; Maynard, S.B.; Naseer, H.; Baskerville, R.L. How integration of cyber security management and incident response enables organizational learning. J. Assoc. Inf. Sci. Technol. 2020, 71, 939–953. [Google Scholar] [CrossRef]
- Theseus. The Role of Security Patch Management in Vulnerability Management. Available online: https://www.theseus.fi/handle/10024/511059 (accessed on 19 November 2024).
- Alabdulatif, A.; Thilakarathne, N.N. A Novel Cloud-Enabled Cyber Threat Hunting Platform for Evaluating the Cyber Risks Associated with Smart Health Ecosystems. Appl. Sci. 2024, 14, 9567. [Google Scholar] [CrossRef]
- Elhoseny, M.; Thilakarathne, N.N.; Alghamdi, M.I.; Mahendran, R.K.; Gardezi, A.A.; Weerasinghe, H.; Welhenge, A. Security and Privacy Issues in Medical Internet of Things: Overview, Countermeasures, Challenges and Future Directions. Sustainability 2021, 13, 11645. [Google Scholar] [CrossRef]
- Lin, Y.; Xie, Z.; Chen, T.; Cheng, X.; Wen, H. Image privacy protection scheme based on high-quality reconstruction DCT compression and nonlinear dynamics. Expert Syst. Appl. 2024, 257, 124891. [Google Scholar] [CrossRef]
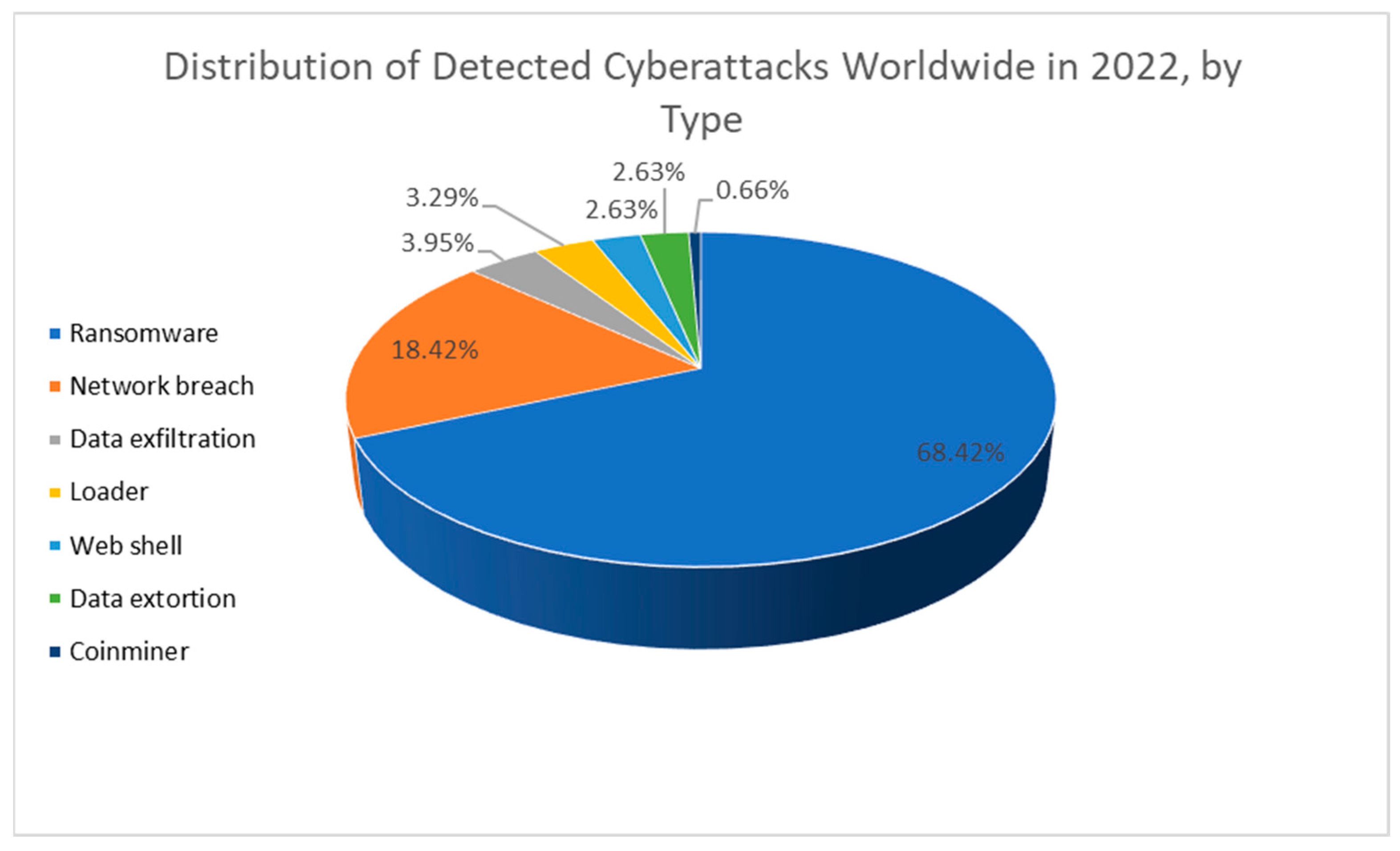
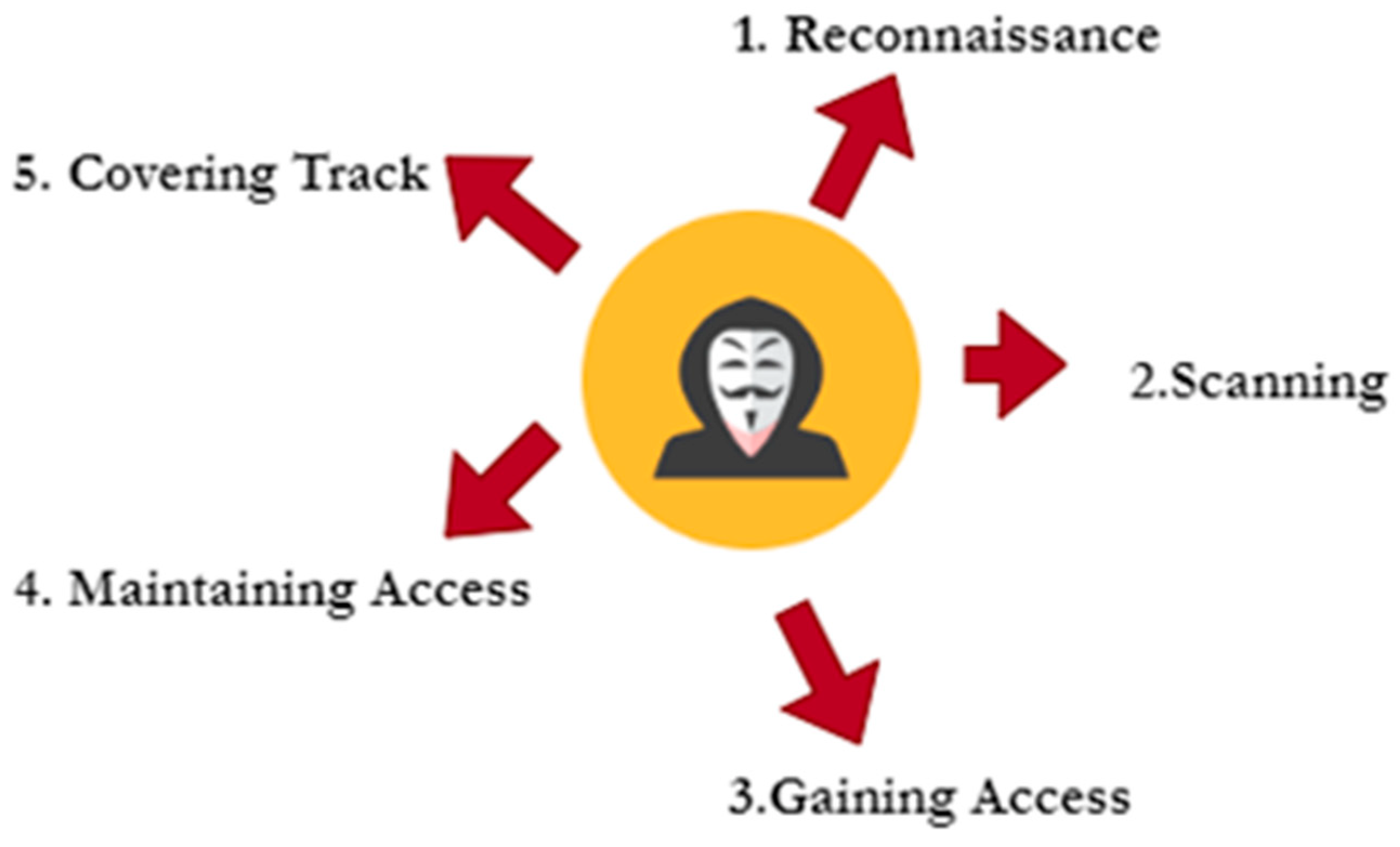

| Google Dork Query | Action |
|---|---|
| filetype:pdf | Searches for specific file types (e.g., PDF). For instance, filetype:pdf confidential finds PDF files containing the word “confidential” |
| intitle:index of | Locates directory listings indexed by search engines. This is often used to find open directories containing files or folders not meant for public access. |
| allintext:password filetype:log | Finds log files containing passwords. This dork searches for pages where the entire text includes “password” and specifies .log files. |
| intext:“ssn” filetype:xls | Locates files that may contain sensitive information, like social security numbers (SSNs), in Excel file formats. This can help find publicly accessible spreadsheets with sensitive data. |
| intitle:“login” “password” | Finds login pages or files that mention “login” and “password” in the title or content, which might provide insight into potentially unsecured login pages. |
| inurl:/phpmyadmin | Looks for PhpMyAdmin web interfaces. This can identify exposed database management pages, which are critical if left unprotected. |
| inurl:edu “login” | Searches for websites on .edu domains that contain the words “login”. This dork searches for school websites that contain student login information. |
| filetype:txt “email” | Finds text files that contain email addresses |
| inurl:“.env” “DB_PASSWORD” | Searches for exposed .env files containing database passwords. |
| inurl:“view/view.shtml” | Searches for publicly accessible IP cameras. |
| Reference | Application Context | Major Contributions |
|---|---|---|
| [7] | Scam detection | This paper introduces a method for identifying gender from social media text, focusing on challenges like emoticons and special characters to improve scam detection. It leverages tools like Google dorking and web scraping for comprehensive analysis, aiding forensic investigators in understanding scammer profiles and enhancing online safety. |
| [8] | Security of web applications | The paper addresses the misuse of Web 2.0 technologies through Google dorking. It presents a three-step solution: first, a large-scale analysis of dorks to understand how attackers identify targets; second, a defense mechanism to neutralize URL-based dorks; and third, a method to prevent fingerprinting by using only generic word combinations, thereby protecting web applications effectively. |
| [9] | Security of content management systems | This paper examines the vulnerabilities of popular content management systems (CMSs), like WordPress and Joomla, which are attractive targets for hackers due to exploitable themes and plugins. It stresses the importance of regular updates, security-focused design, and removing outdated components to protect against cyber threats. |
| [10] | Employ Natural Language Processing (NLP) to enhance the Google Hacking database. | This paper explores using NLP to enhance the Google Hacking database by converting textual dork values to numerical ASCII, enabling the application of machine learning techniques. The study conducted a seven-step process to enrich the database, and results showed the methodology successfully met its goals, yielding positive outcomes in machine learning evaluations. |
| [11] | Security of critical infrastructure | The paper analyzes the digital transformation of the fuel and energy market, proposing an ecosystem for major participants while addressing new attack vectors targeting critical infrastructure. It utilizes classical testing theories on Web applications and the Modbus protocol, with penetration testing examples on APCS and supervisory control and data acquisition (SCADA) systems, guided by OWASP standards and customized Google dorks for enhanced security analysis. |
| Shodan Query | Action |
|---|---|
| http | Shows devices with HTTP servers open on any port (80, 8080, etc.). |
| port:23 | Identifies devices with Telnet service (port 23) open |
| port:3389 | Returns systems with Remote Desktop Protocol enabled on port 3389 |
| http.title:“webcam” | Targets devices labeled as webcams in the HTTP title |
| “SCADA” port:502 | Lists SCADA systems on port 502, often associated with the Modbus protocol, used in industrial applications. |
| port:21 “230 Login successful” | Targets FTP servers allowing anonymous login, which can be exploited for unauthorized access. |
| product:Redis “authentication required” false | Finds Redis instances that do not require authentication |
| port:5060 | Targets devices using Session Initiation Protocol on port 5060, commonly found in VoIP systems. |
| product:OpenSSL version:<1.1.1 | Finds systems running vulnerable versions of OpenSSL. |
| ssl.cert.expired:true | Identifies servers using expired SSL certificates. |
| Reference | Application Context | Major Contributions |
|---|---|---|
| [14] | Passive information gathering | This research examines IoT-related discussions on underground forums, focusing on how hackers use the Shodan search engine for cybercriminal activities. The findings reveal that Shodan is commonly used for passive information gathering, with key applications in remote device control, botnet creation, DDoS attacks, and accessing open databases. |
| [15] | Security of smart infrastructure | This study explores vulnerabilities in smart buildings, introducing a novel Shodan-based assessment method to identify and evaluate security risks in building systems. The findings highlight primary security concerns and propose a framework to improve smart building resilience through targeted mitigation strategies, enhancing security and safety in interconnected urban spaces. |
| [16] | Security of smart infrastructure | This paper examines security assessment methods and hardening techniques for IoT infrastructure, focusing on Shodan’s impact on identifying and probing IoT devices. It provides example attacks and an in-depth analysis of device hardening techniques and aims to equip security professionals to tackle emerging IoT security challenges. |
| [17] | Security of critical infrastructure | This paper examines Shodan’s capabilities in identifying Internet-exposed industrial control systems, which pose significant risks to critical infrastructure security. |
| [18] | Security of the IoT | As IoT devices become more prevalent, security threats related to IP are increasing, particularly in developing countries like India, where preventing these threats is challenging. This paper provides an overview of Shodan in the Indian context, evaluating various IoT devices and discussing how they can be exploited using the search engine. |
| [19] | Security of the IoT | This paper investigates Shodan’s use in assessing IoT device vulnerabilities, revealing that many publicly known query terms still expose devices to security risks. The study expands on original Shodan queries to include additional terms for backdoor access, finding persistent vulnerabilities, particularly default or weak passwords, in IoT devices across the US and globally. |
| [20] | Internet scanning search engines | This paper provides an empirical evaluation of Internet-scanning engines like Censys and Shodan, focusing on result freshness, resource consumption, and operational differences. Preliminary findings show that both engines update device information within 24 h and consume minimal resources, making them valuable tools for the research community. |
| [21] | Vulnerability detection | The paper introduces ShoBeVODSDT, a tool that uses OSINT and IoT search engines to detect vulnerabilities in open data sources like MySQL, MongoDB, and Redis, assessing their visibility and value to attackers. The tool provides scalable, non-intrusive testing for both rational and NoSQL databases, revealing potential security risks from unprotected data sources accessible outside the organization. |
| [22] | Security of the IoT/Internet-facing services | This paper introduces ShoVAT, a novel Shodan-based vulnerability assessment tool that enhances Shodan’s capabilities by performing an in-depth analysis of service-specific data, such as service banners, to identify vulnerabilities. ShoVAT uses advanced algorithms and in-memory data structures to accurately reconstruct platform names and extract vulnerabilities from the national vulnerability database, offering automated vulnerability detection, historical analysis, and high accuracy, as demonstrated by experiments on 1501 services across 12 institutions. |
| [23] | Security of the IoT | This study examines Shodan, a widely used IoT search engine, and its probing behavior on newly connected IPv4 hosts, revealing insights into its scanning algorithms and detection patterns for different network services. Over 331 days, researchers analyzed Shodan’s interaction with traffic traps, identifying both regular and covert crawlers, and proposed mechanisms to shield protected hosts from Shodan’s reach, reducing their exposure to potential threats. |
| [24] | Security of the IoT | This study presents Shodan as a tool for cybersecurity audits on IoT devices, enabling researchers to identify vulnerabilities from weak security mechanisms and poor configurations without direct scanning. It proposes a use case-based methodology for teaching users to assess and secure IoT devices and includes guidance on automating vulnerability assessments with Shodan scripts, making it a practical introduction to IoT cybersecurity. |
| [25] | Security of ICSs | This study addresses security concerns for industrial control systems (ICSs), which are increasingly connected to the public Internet, exposing them to potential intrusions. By evaluating ICS communication protocols, the research found that certain ports are more vulnerable due to the nature of their services, though no direct correlation exists between the number of open ports and total vulnerabilities. |
| [26] | Security of the IoT | This paper explores the security and privacy challenges in the IoT, emphasizing vulnerability scanning of IoT devices in Jordan using Shodan to highlight their susceptibility to attacks. The findings aim to raise awareness among IoT users in Jordan about the security risks to help improve device protection and maintain privacy standards. |
| [27] | Security of ICSs | This paper investigates the impact of Shodan on ICSs using honeypots and a DFA-SVM recognition model to detect Shodan scans based on traffic features, surpassing traditional IP-reversal methods. Through three months of data analysis, the study examines Shodan’s scanning behavior, including frequency, ports, and protocol preferences, and suggests defensive measures to reduce ICS vulnerabilities to Shodan’s exposure. |
| Censys Query | Action |
|---|---|
| services.http.title: “webcam” | Finds devices with “webcam” in the HTTP title, typically used to find Internet-connected cameras. |
| services.port: 3389 AND services.service_name: “rdp” | Identifies devices running RDP on port 3389, which is commonly used for remote access. |
| services.http.html: “SCADA” | Detects SCADA systems, often used in industrial environments. |
| services.port: 3306 AND services.service_name: “mysql” | Locates publicly accessible MySQL databases, potentially exposing sensitive data. |
| services.http.title: “NAS” OR services.http.html: “Network Attached Storage” | Finds NAS devices, which often contain sensitive files and should be secured from public access. |
| services.port: 6379 AND services.service_name: “redis” | Detects open Redis servers, which may allow unauthorized access and data manipulation. |
| services.port: 5432 AND services.service_name: “postgresql” | Identifies PostgreSQL databases exposed to the internet, which could risk data breaches. |
| services.port: 5060 AND services.service_name: “sip” | Finds VOIP servers using the SIP protocol on port 5060, which can be exploited in VOIP attacks. |
| services.port: 27017 AND services.mongodb.status: “Unauthorized” | Identifies MongoDB databases with no authentication, exposing data publicly. |
| services.port: 9200 AND services.elasticsearch.version: “*” | Finds open Elasticsearch databases, which may be vulnerable to unauthorized access. |
| Reference | Application Context | Major Contributions |
|---|---|---|
| [30] | Vulnerability detection | This paper introduces Censys, a search engine and data processing platform for Internet-wide security research, enabling quick identification of vulnerabilities and device trends through full-text protocol searches and various field queries. By significantly reducing the time and effort for obtaining data on Internet-connected devices, Censys facilitates answering complex security questions and provides valuable insights into global usage patterns. |
| [31] | Security of Internet connected devices | This study proposes a detection method for Shodan and Censys scans to prevent unauthorized disclosure of IP device information by monitoring and identifying abnormal packet behavior. By combining traditional scan detection methods and using stateful TCP inspection, the approach classifies suspicious activities, such as SYN Scans and Banner Grabbing, helping to block these search engines from indexing vulnerable devices. |
| [33] | Security of OBE | This study examines the security risks of Internet-facing on-board equipment (OBE) in connected cars, discovering 2532 exposed devices across 27 countries that could serve as entry points for cyberattacks on in-vehicle networks. The findings reveal that most of these devices have vulnerabilities, including outdated software and Telnet access, with some even exposing sensitive information, like GPS location, underscoring the security risks in connected automotive systems. |
| Reference | Incident | How Google Dorks Have Used | Impact of the Incident |
|---|---|---|---|
| [36] | LinkedIn data breach in 2016: LinkedIn faced a significant data breach where information from 167 million accounts, including hashed passwords, was stolen. This breach had initially started with an attack in 2012 but was expanded in 2016 with additional data being sold on the dark web. | In this incident, cyber attackers used Google dorks to locate unsecured databases and leaked login credentials related to LinkedIn. Simple search queries were used to find database backups that had been improperly indexed. | The stolen credentials were later sold on the dark web, making LinkedIn accounts vulnerable to identity theft and account takeovers. |
| [37] | Adobe’s data breach in 2013: The data breach that endangered Adobe in 2013 exposed 153 million user records, including login credentials and encrypted passwords. Nonetheless, the source code for several Adobe products was also stolen. | Attackers used Google dorks to discover unsecured databases and configuration files containing sensitive information, which helped them to locate files that contained password hints and encryption keys. | This breach emphasized the importance of securing backup files and avoiding indexing sensitive documents. Exposed source code further impacted Adobe’s reputation, as it highlighted weaknesses in its security practices. |
| [38] | Capital One data breach in 2019: A former Capital One employee exploited a misconfigured firewall, gaining access to the sensitive data of over 100 million individuals. | Google dorks queries were used by attackers and researchers alike to locate exposed S3 buckets and misconfigured cloud databases, that contained Capital One’s sensitive customer information. | This breach led to lawsuits, regulatory scrutiny, and a $80 million fine for Capital One. It also highlighted the importance of securing cloud environments and limiting search engine indexing. |
| [39] | Facebook data exposure in 2019: Facebook accidentally exposed hundreds of millions of records due to third-party applications improperly storing user data on public cloud servers. | Dorking techniques were used by attackers to locate and access unsecured S3 buckets holding user data. | This incident led to severe privacy concerns and intensified scrutiny of Facebook’s data practices. Eventually, Facebook took measures to restrict data access for third-party applications, but this event emphasized the risks of misconfigurations in cloud storage. |
| Reference | Incident | How Shodan Used | Impact of the Incident |
|---|---|---|---|
| [40] | USA water treatment plant attack (Oldsmar, Florida, 2021): In February 2021, hackers accessed the water treatment plant in Oldsmar, Florida, and attempted to raise the sodium hydroxide levels in the water supply to dangerous levels. While the intrusion was quickly detected and reversed, it exposed significant vulnerabilities in industrial systems. | Although Shodan was not directly cited in this attack, it has been widely reported that water treatment facilities across the USA have unsecured ICS devices accessible via Shodan searches. | The attack underscored the risks of remote access in critical infrastructure and led to a reevaluation of cybersecurity practices across water treatment facilities nationwide. |
| [41] | Iranian pipeline attacks: Iran and other Middle Eastern countries have seen frequent attacks targeting ICSs, including pipelines and petrochemical facilities. In many instances, attackers have used Shodan to locate and exploit vulnerable devices connected to critical infrastructure. | Attackers leveraged data retrieved from Shodan to probe and compromise the ICSs, causing disruptions in operations. | These attacks revealed the ease with which ICS devices could be located and exploited using search engines like Shodan, prompting countries to reassess their ICS security protocols. |
| [42] | Ukrainian power grid attack (2015): The 2015 Ukrainian power grid attack, attributed to a state-sponsored group, led to a massive blackout affecting hundreds of thousands of people. Attackers remotely accessed control systems and shut down power substations across Ukraine. | Shodan was reportedly used by attackers to identify Internet-facing ICS endpoints in Ukraine. | This incident was the first publicly acknowledged power grid attack, drawing attention to the vulnerability of power infrastructure. |
| [43] | Tesla Powerpack System Exposure (2018): In 2018, a security researcher discovered that several Tesla Powerpack systems, part of the renewable energy infrastructure, were exposed online without authentication. These systems were accessible to unauthorized users who could potentially control energy distribution and monitor performance. | Using Shodan, the researcher found Tesla Powerpack systems with open ports and weak security. A simple Shodan query revealed connected devices that were left exposed on the Internet. | This incident highlighted the risks of poorly configured IoT and ICS devices in the renewable energy sector. Tesla took immediate action to secure exposed systems, but it raised awareness of the need for better security in the IoT-connected energy infrastructure. |
| [44] | Vulnerable gas stations in the USA (2015): A researcher in 2015 found that numerous gas stations in the United States had unsecured tank monitoring systems exposed online. These systems could be manipulated to shut down pumps or alter fuel levels. | Shodan searches, such as “country: US inurl:/Gascard” or “port:10001” for specific tank monitoring systems, revealed vulnerable devices accessible without authentication. | The discovery led to increased scrutiny of ICS security in the fuel and energy sectors. The US Department of Homeland Security issued guidelines for securing these systems against unauthorized access. |
| Reference | Incident | How Google Dorks Have Used | Impact of the Incident |
|---|---|---|---|
| [45] | Mirai botnet attack on IoT devices (2016): The Mirai botnet, one of the most notorious IoT botnets, exploited vulnerabilities in thousands of IoT devices, including IP cameras, routers, and printers, to launch massive DDoS attacks. It caused widespread Internet outages, affecting popular services like Netflix, Twitter, and PayPal. | Censys helped security researchers track exposed IoT devices vulnerable to Mirai’s default username/password combinations. On the other hand, searches like “tags:” “mirai” OR “dvr” OR “ipcam” OR “router” allowed researchers and attackers to locate vulnerable devices with ease. | This attack demonstrated the dangers of insecure IoT devices, as they can be exploited at scale to disrupt major Internet services. |
| [46] | Research on Medical IoT Device Vulnerabilities (2019): In 2019, security researchers used Censys to investigate vulnerabilities in IoT devices within healthcare facilities, including infusion pumps, heart monitors, and MRI machines. Many devices were found to be exposed online without proper security protections. | Censys allowed researchers to search for devices by protocol and filter results by keywords related to health care. This revealed the presence of medical devices with open ports and outdated firmware, making them vulnerable to cyberattacks. | The findings raised alarms in the healthcare industry, leading to new guidelines for securing medical IoT devices. It underscored the potential risks to patient safety and healthcare service continuity. |
| [47] | Vulnerable smart home devices exposure (2020): Researchers found that several smart home devices, including smart thermostats, security cameras, and smart locks, were exposed online and vulnerable to attacks. Censys was instrumental in identifying these devices and their specific vulnerabilities. | By using Censys search researchers pinpointed devices that were improperly configured, revealing open ports and weak credentials. | This research highlighted the privacy risks associated with smart home devices. The findings encouraged manufacturers to improve device security and prompted consumers to adopt better security practices for IoT devices. |
| [48] | Power grid substation exposure (2021): In 2021, researchers discovered that various IoT devices used in power grid substations were accessible online without proper authentication or encryption, potentially allowing attackers to manipulate energy distribution systems. | Censys enabled the discovery of these devices revealing unprotected entry points into the power infrastructure. | This vulnerability raised serious concerns about the security of critical infrastructure. It led to federal mandates and regulations to secure IoT devices in the power sector and improve network monitoring. |
| [49] | Smart meter hacking in smart cities (2019): Several smart cities deployed Internet-connected meters to monitor energy and water usage. In 2019, researchers discovered that many of these devices were vulnerable to attacks due to weak security settings. | Censys was instrumental in identifying insecure smart meters with searches like “tag:smart-meter” and “service:modbus city:nyc”, revealing devices that were publicly accessible and could potentially be manipulated to disrupt utilities. | This exposure raised concerns about the security of smart city infrastructure. Municipalities started adopting more robust security measures for their IoT deployments to protect against tampering and data breaches. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alabdulatif, A.; Thilakarathne, N.N. Hacking Exposed: Leveraging Google Dorks, Shodan, and Censys for Cyber Attacks and the Defense Against Them. Computers 2025, 14, 24. https://doi.org/10.3390/computers14010024
Alabdulatif A, Thilakarathne NN. Hacking Exposed: Leveraging Google Dorks, Shodan, and Censys for Cyber Attacks and the Defense Against Them. Computers. 2025; 14(1):24. https://doi.org/10.3390/computers14010024
Chicago/Turabian StyleAlabdulatif, Abdullah, and Navod Neranjan Thilakarathne. 2025. "Hacking Exposed: Leveraging Google Dorks, Shodan, and Censys for Cyber Attacks and the Defense Against Them" Computers 14, no. 1: 24. https://doi.org/10.3390/computers14010024
APA StyleAlabdulatif, A., & Thilakarathne, N. N. (2025). Hacking Exposed: Leveraging Google Dorks, Shodan, and Censys for Cyber Attacks and the Defense Against Them. Computers, 14(1), 24. https://doi.org/10.3390/computers14010024








