Abstract
After the emergence of the Internet of Things (IoT), the way devices interact with each other changed, as it allowed automation and seamless communication in various fields. However, various challenges related to security and trust have emerged, hindering the widespread adoption of the IoT. Blockchain technology is considered the ideal solution to face these challenges because of its immutable and decentralized nature. This paper explores the potential of blockchain technology to address critical security and trust challenges within the rapidly growing IoT ecosystem. Through a systematic literature review, this study examines how blockchain’s decentralized, immutable, and transparent features contribute to enhancing security and trust in IoT networks. Key findings indicate that blockchain integration can prevent data manipulation, ensure robust identity management, and facilitate transparent, verifiable transactions, supporting both security and trust in IoT systems. These attributes not only improve IoT security but also promote sustainable practices by optimizing resource efficiency, reducing environmental impact, and enhancing resilience in systems like supply chain management and smart grids. Additionally, this study identifies open research challenges and suggests future directions for optimizing blockchain in IoT environments, focusing on scalability, energy-efficient consensus mechanisms, and efficient data processing.
1. Introduction
Blockchain technology is a transformative technology that can change many industries, including the IoT. Due to the rapid growth of the IoT ecosystem, security and trust are the most prominent challenges faced by this interconnected network of devices. Relying on traditional measures alone is not sufficient to protect the IoT from these challenges, such as providing proper authentication and maintaining data integrity. For this reason, this paper presents blockchain as an optimal solution to enhance the reliability and security of the IoT by providing transparency and decentralization and reducing manipulation [1].
The IoT consists of many interconnected devices that can exchange large amounts of data and that need to be protected from unauthorized access or hacking. The increasing reliance on these devices in our daily lives has created security and trust concerns [2].
Blockchain is the underlying technology behind cryptocurrencies such as Bitcoin. It allows multiple parties to maintain consensus through a shared database that is based on distributed ledger technology without relying on a central authority. This is realized by integrating the network’s decentralized intent and cryptographic algorithms. Each transaction in blockchain technology is recorded in an independent block linked to the previous block of the blockchain. Thus, a chain of information is formed that cannot be changed or manipulated. Immutability and transparency are among the most important characteristics of blockchain that enable it to address issues of security and trust in the IoT ecosystem [1]. Blockchain technology uses a distributed consensus mechanism to ensure agreement on the state of the ledger. The transaction is verified and approved by all parties participating in the network before being included in the blockchain. Proof of work (PoW) and proof of stake (PoS) are two of the most prominent examples of consensus mechanisms. The consensus of all parties enhances the flexibility and security of the network, which makes it difficult to hack and manipulate data [3]. Moreover, decentralization is one of the most important advantages of blockchain technology as it enhances the security of the IoT by having multiple nodes participate in validating a common ledger. Decentralization prevents reliance on a single point, which increases the difficulty of hacking the system or a single point of failure. The ledger is distributed and replicated across the network, which leads to enhancing trust in IoT networks [3].
The ability to maintain the integrity of data from unauthorized modification or manipulation is one of the most important features of blockchain technology. Once the data are written on the blockchain and approved by the network parties, they cannot be modified or tampered with until all participating parties accept that change, which ensures the safety of these data from unauthorized access. This feature allows the data path to be audited; its source, known; and its authenticity, verified. This gives IoT networks confidence and builds an ecosystem that cannot be tampered with [3]. Large amounts of data are generated when billions of devices are connected, as in the case of the IoT network. Blockchain uses cryptographic properties to keep these data secure and unchangeable, stored in a distributed ledger. It also ensures that there is no central authority over the data, which reduces the risk of fraud and ensures transparency and decentralization [1].
In short, blockchain technology can provide many advantages to the IoT. It enhances security by providing a decentralized framework. It improves trust by ensuring data are reliable and valid and ensuring that they have not been tampered with. It enables peer-to-peer data exchange without the need for intermediaries. Distributed consensus provides reliability and flexibility to IoT systems. It provives regulatory compliance by simplifying and streamlining compliance and audit processes. In general, blockchain technology is considered a promising solution to address security and trust issues in IoT systems [2].
This paper contributes to the literature by providing a comprehensive analysis of security and trust challenges in IoT and of the ability of blockchain technology to overcome these challenges. This study’s contributions are summarized in the following points:
- Analyze IoT Security and Trust Challenges: To provide an understanding of the major security and trust concerns in IoT systems, IoT security challenges are considered at multiple layers of the IoT reference model while illustrating the weaknesses of conventional security mechanisms.
- Assess Blockchain’s Potential Capabilities for IoT Security: To assess the potential capabilities of blockchain technology, including decentralization, transparency, and immutability, while assessing the application of the proposed solutions for IoT architecture with regard to the specified challenges, including data integrity, authentication, and access control.
- Explore Blockchain’s Role in Enhancing IoT Sustainability: To examine the role that blockchain can play in making IoT sustainable by increasing resource utilization, reducing carbon footprint, and increasing openness and veracity of sources.
- Identify Integration Challenges and Future Directions: To provide insights on some of the areas of experimental or technical challenge related to integrating blockchain into IoT and on future research opportunities to enable efficient, scalable blockchain IoT platforms.
- Provide a Comprehensive Review of Recent Studies: Due to rapid advancements in IoT technology, this scoping review aims to locate and consolidate the latest articles published from 2020 to 2024, including the findings, methods, and shortcomings of blockchain IoT security and trust.
These objectives would help analyze how blockchain can further IoT technology in terms of security while addressing existing loopholes.
This paper is structured as follows: Section 2 shows the methodology used to organize this paper. Section 3 elaborates on the IoT architecture, security threats in the IoT domain, and other issues like trust, data integrity, access controls, and authentication. Section 4 presents a comprehensive overview of blockchain technology, including blockchain history, concept, characteristics, components, and types. In addition, it identifies the possible advantages of combining blockchain with IoT. Section 5 explores state-of-the-art studies in this field. Section 6 presents how utilizing IoT devices in conjunction with blockchain technology will contribute to sustainability and reinforce the connection. Section 7 determines the challenges of integrating blockchain with IoT environments. Finally, Section 8 concludes this paper by summarizing the key findings.
2. Methodology
The methodology used in this paper is a Systematic Literature Review (SLR) [4]. This structured approach ensures an organized review by outlining research queries and identifying applicable studies to analyze their discoveries for valuable insights extraction. This paper involves research studies that were published between 2020 and 2024. In addition, the paper selection followed PRISMA 2020 to ensure transparency and precision in selecting studies related to blockchain technology for IoT security and trust. An SLR includes planning, conducting, and reporting the review. The process starts with creating research queries and establishing criteria for what to include and exclude in the study search process using search strings to find studies. These studies are then evaluated before being narrowed down based on their alignment with the research scope.
2.1. Planning
Here, we added details on the research questions and inclusion/exclusion criteria used in the planning phase.
2.1.1. Research Questions
Key research questions for this SLR included the following:
- What are the main security and trust challenges in IoT environments?
- How can blockchain technology address these IoT security and trust challenges?
- What are the benefits of combining blockchain with IoT systems?
- What are the potential limitations and challenges in implementing blockchain within IoT environments?
- How does blockchain integration contribute to sustainability in IoT security?
- What are future directions for enhancing blockchain applications in IoT security?
2.1.2. Inclusion and Exclusion Criteria
This section allows the readers to reproduce the selection process and understand why few papers pass the selection criteria. In addition, we applied the following inclusion and exclusion criteria to ensure the quality and relevance of the papers selected for this SLR.
- Inclusion Criteria
- –
- Data of publication: This SLR includes papers that were published from 2020 to 2024 to make sure the information is recent.
- –
- Relevance to the field: This SLR concentrates on papers that focus on how blockchain is used to enhance security and trust in IoT systems.
- –
- Language: English-language papers were the focus of this SLR to guarantee accessibility and understanding for all readers.
- –
- Peer-reviewed: Scholarly articles that have undergone peer review were considered for inclusion, such as peer-reviewed journal articles along with conference papers and technical papers.
- –
- Full-text Access: This SLR includes research papers that have full-text access for detailed examination.
- –
- Original research papers: This SLR includes research papers that contain research findings such as outcomes or theoretical examinations that contribute to the field of IoT and blockchain security with innovative methods.
- Exclusion Criteria
- –
- Irrelevant papers: Papers that are not relevant include papers that do not specifically tackle the merging of IoT technologies with blockchain.
- –
- Non-peer-reviewed: Non-peer-reviewed sources, such as gray literature and opinion articles, are not considered in this literature review.
- –
- Non-English Papers: Papers written in a language other than English were excluded to prevent translation errors and ensure a grasp of the content.
- –
- Duplicate Studies: This SLR excluded any studies that were duplicated or redundant across two databases.
- –
- Inaccessible Papers: Papers that cannot be fully accessed were not considered in the selection process.
- –
- Paper length: Short papers that do not provide full understanding or lack detailed information about the topic were excluded.
We made sure to select the most pertinent studies that match the focus of using blockchain technology for securing and establishing trust in IoT systems by following these criteria.
2.2. Conducting
Here, we added details on the data sources and search strings used during the conducting phase.
2.2.1. Search Strings
We used the following search query to find the relevant studies and to enhance the quality of the search results: (“Internet of Things” OR “IoT” OR “connected devices” OR “cyber-physical systems” OR “smart devices” OR “sensor networks”) AND (“Blockchain” OR “distributed ledger” OR “DLT” OR “smart contracts” OR “decentralized technology”) AND (“security” OR “trust” OR “privacy” OR “data integrity” OR “authentication” OR “access control” OR “encryption” OR “cybersecurity”). These keywords are separated with boolean operators like AND, OR, and NOT to improve search results and filter out information.
2.2.2. Data Sources
This review used two scientific databases, Google Scholar and the Saudi Digital Library, to extract papers. Each database was chosen for its pertinence to computer science and cybersecurity.
2.3. Reporting
Here, we provide a structured summary of findings from the screening and selection processes to ensure comprehensive reporting. In addition, we added details of the number of studies found, filtered, and selected in the selection process section.
2.3.1. Screening Process
Initially, all the studies collected from the search phase went through a review based on their titles and abstracts to determine their relevance to our paper. Any studies that did not match the research focus criteria were excluded from consideration. When we moved to the next stage of the process, which involved examining each chosen paper for its methodology, relevance, and impact in the field, any duplicated or irrelevant studies were eliminated at this phase. The tool used for the literature was PRISMA 2020, which considers identification, screening, and inclusion phases, as shown in Figure 1. These phases declare how many papers were reviewed and excluded, as well as how many were selected following some criterion, making SLR scanning systematic.
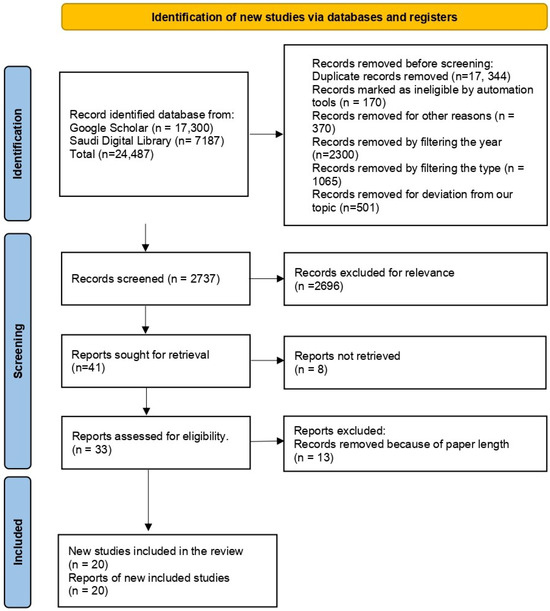
Figure 1.
PRISMA flow diagram for literature selection.
2.3.2. Selection Process
In our research, we applied PRISMA 2020 to efficiently handle and structure the flow of data during the review process [5]. The papers were extracted from two databases, Google Scholar and Saudi Digital Library. Google Scholar yielded 17,300 findings, and the Saudi Digital Library presented 7187 results. A total of 21,750 papers were removed for different reasons, such as the paper being flagged as ineligible. After a comprehensive review process, 2737 papers underwent detailed examination, resulting in the selection of 20 papers that aligned with the research goals (For more details, we added the studies reviewed to improve transparency; please refer to “Appendix A”). The remaining 2717 papers were eliminated due to reasons like being irrelevant to the topic, written in a language other than English, being outside the designated timeframe, or lacking accessibility.
2.4. Threats to Validity in Blockchain and IoT Security Systematic Review
Here are some threats to validity relevant to this SLR:
- Selection bias: The selection of studies may not be generalizable to a broader field, especially when few databases were considered (for instance, Google Scholar and Saudi Digital Library only).
- Publication bias: Using only certified articles obtained from peer-reviewed publications in specific databases.
- Temporal Bias: This review may have excluded studies published earlier and important studies related to blockchain and IoT security and focused on works published within a specific period, from 2020 to 2024 only.
- Technological and Methodological Limitations: Blockchain as well as IoT domains are still developing, so the methodology or technology from several years ago may not be valid.
3. Overview of IoT
IoT networks involve many connected devices that generate a large amount of data that must be protected against different cyberattacks. For example, medical sensors are attached to the human body to detect their status, like temperature, heart rate, blood pressure, and sugar level. In the realm of IoT networks, it is important to verify the authenticity of data to confirm device identities and ensure transmission from sources that are trusted. Moreover, integrity checks were carried out to guarantee data accuracy as the data travel. Validation processes ensure that data meet standards and are formatted correctly for their intended use. These steps protect data from being tampered with or altered and ensure their security and reliability within the system [6].
3.1. IoT Architecture
IoT layers or architecture organize the components of IoT and the interactions between these components systematically. IoT architecture integrates software, protocols, data flow, and interfaces. For instance, smart devices in an IoT environment collect data, which are then sent to the communication protocol. After that, data processing is carried out in the cloud infrastructure, while the users interact with the information using IoT applications [7].
While there are different architectures for IoT, this section presents a three-layer architecture [7], which is a generalized IoT architecture, as shown in Figure 2.
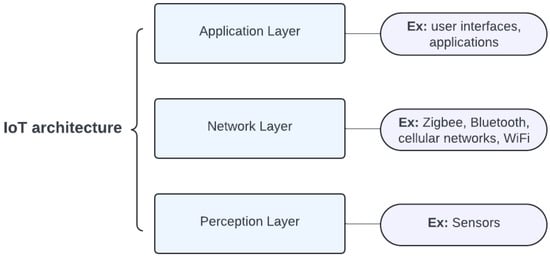
Figure 2.
IoT architecture.
- Perception Layer: The perception layer is also called the physical layer. This layer contains sensors and different collecting tools that are used for collecting information. Furthermore, collecting and processing the information and then transmitting it to the network layer is the main responsibility of this layer. Moreover, it allows collaboration between IoT nodes within the local networks [7].
- Network Layer: The network layer is also called the transport layer. This layer contains different communication protocols and techniques, like Zigbee, Bluetooth, cellular networks, WiFi, and other technologies. Also, it consists of switches, Internet gateways, and routers. In addition, the main responsibility of this layer is safe and faster data transmission from one layer to another [7].
- Application Layer: The application layer is located at the top of the IoT architecture. This layer contains user interfaces, applications, data storage systems, and other services for the users. In addition, the main responsibility of this layer is to provide the interface between the IoT devices and the applications that interact with them. It also ensures the confidentiality, integrity, and availability (CIA) of the data. Also, it is responsible for interpreting the data to make them meaningful and actionable. Some of the protocols implemented in this layer include HTTP, MQTT, and CoAP, with HTTP supporting different functionalities within the IoT due to its resource availability and network constraints. For instance, HTTP is ideal for web-based IoT applications, MQTT is optimal for small data streaming, and CoAP is meant for restricted devices and networks [7].
3.2. Security Challenges in IoT
The connected devices in the IoT environments have limited resources and are targeted by different cyberattacks. In addition, a single point of failure may occur in IoT environments because IoT devices are connected through a centralized server. There are various security challenges in each layer of IoT architecture, and it is not easy to define an IoT security model that considers the IoT architecture’s heterogeneity. The most common attacks in the IoT architecture are data leakage, man-in-the-middle (MiTM) attacks, malicious node injection, phishing, and impersonation [8].
The IoT architecture suffers from various security issues related to each layer. Therefore, the architecture’s security solutions should be addressed [9]. We have to examine the available solutions to cybersecurity issues associated with the IoT model to obtain a more systematic, powerful, and integrated perspective on how to secure the IoT from being vulnerable to different cyberattacks. The IoT has a design of three layers that highlight cybersecurity concerns and solutions at the layer level [9]. Figure 3 groups typical IoT security threats based on the perception, network, and application layers, listing such threats as replay attacks, eavesdropping, DoS, and IP spoofing. From this layer-wise perspective, the threats are shown as utilizing certain points within the IoT framework, and this highlights the importance of security implementation at each layer.
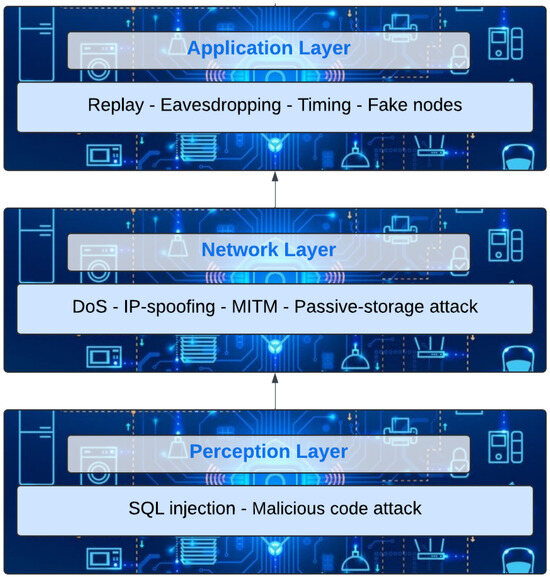
Figure 3.
IoT attacks across layers.
- Perception layer: Replay attacks, eavesdropping, timing, node capture, and malicious and fake nodes are all included in the perception layer. By watching how long it takes for systems to react to input or cryptographic algorithms, attackers can use timing attacks to find security flaws and collect secrets kept within a security system [10]. Replay attacks are ones in which hackers listen in on communications between senders and recipients. Then, by pretending to be the real sender, the intruder utilizes the sender’s information to convince the recipient to carry out specific activities [11]. S. Lazzaro et al. [12] attempted to establish the extent to which replay attack vulnerability was apparent in consumer IoT devices as well as the extent to which they are equipped for local communication protection, and they observed that the standard is low. The authors conducted a practical experiment with 41 contemporary IoT devices employing the REPLIOT tool and succeeded with 51% of those not supporting local connectivity, which is promising offline functionality contrary to reliability standards set by ENISA/NIST. Out of all the devices with local connectivity, 75% of them, that is, 15 out of 20 were assessed to be susceptible to replay attacks. This study also identified that those devices relying on unencrypted or only weakly encrypted communication protocols were especially at risk. For all tested attack scenarios with and without device restarts, the replay attacks were accurate across a broad spectrum of IoT categories, smart plugs, cameras, and speakers. This highlights the importance of authentication for both as well as the acknowledgment of the importance of generally accepted protocols on securing consumer IoT devices.Malicious attacks that include adding nodes to systems and creating fraudulent data inputs are referred to as fake nodes. Mainly, this type of attack aims to prevent actual information from being transmitted. Malicious attackers also add nodes to networks, which they then delete because they use the power needed by legitimate nodes to function. By adopting strategies like gateway nodes, attackers can completely gain control of important nodes in node capture attacks [11]. Senders and recipients of secure information can leak information to each other thanks to these nodes. The perception layer is vulnerable to eavesdropping attacks, in which hackers intercept phone calls, text messages, emails, and video conferences. Private communications are targeted by attackers in an attempt to gain personal data. Significant losses result from the information gathered through these methods, mostly from attackers’ access to private data [13]. As a result, developers of IoT structures in various organizations must undertake in-depth studies on the best security methods to use for their perception layers.
- Network layer: Since the network layer transfers data from physical devices over wired or wireless networks, it is frequently the target of attacks. Active attacks known as Denial of Service (DoS) prevent legitimate users from using other devices or network resources. It is frequently achieved by flooding targeted devices or network resources with repetitive requests, which prevents or makes it difficult for legitimate users to utilize their devices [14]. Attacks known as IP spoofing are used to gain unauthorized access to servers. To keep the server from detecting the attacker’s presence on its network, attackers use trusted IP addresses. In addition to these attacks, IP spoofing can also be used for blind spoofing, man-in-the-middle attacks, and non-blind spoofing. One method that makes it challenging to stop these cybercrime activities is the attacker’s use of trusted IP addresses, as servers are unable to recognize that an attacker is accessing data using the trusted IP address rather than an authorized user [15]. Another tactic used in passive attacks is the MiTM attack. In this scenario, attackers manipulate messages sent between senders and recipients who believe they are speaking with one another in real time. Attackers can modify messages to match their requirements or viewpoints thanks to these secret interceptions. Passive attacks involve the eavesdropping of only the provided information, with no communication breaks between the sender and the recipient [16]. Paracha et al. [17] identified several main flaws that have been identified when it comes to the TLS protocol and its security, which can be attacked through MITM attacks. Other vulnerabilities include failure to verify issues like hostname, where an attacker will be able to provide a wrong name to the certificate authorities and allow untrusted certificate chains, making TLS vulnerable to MITM attacks. However, nowadays, the usage of outdated TLS versions (TLS 1.0 or 1.1) or poorly secured cipher suites (for example, RC4 or DES) is still prevalent, which makes a connection vulnerable to certain threats, including POODLE and Sweet32. Where trust in a CA that has been compromised has not been withdrawn, attackers can use the keys of the compromised CA to issue certificates for man-in-the-middle interception, thus violating TLS’s authentication guarantees. The absence of revocation checking only intensifies such a danger given that clients cannot identify certificates that have been revoked because of security breaches, thus giving hackers a free license to eavesdrop on the parties involved. Also, downgrade attacks in which the attackers compel the clients and servers to agree on a weaker version of TLs are successful in constraining forward cryptographic securities and enabling data decryption. All these weaknesses show that an opponent is able to fully violate TLS thus negating most of its inherent security assurances on data in transit.Storage and exploit attacks are two more types of network layer attacks. Passive storage attacks include data breaches that compromise data stored on multiple devices or in the cloud. The attacker can then modify these data to suit their goals. In order to increase the likelihood of future attacks, attackers also repeat the information they obtain [18]. Illegal attacks on software, data chunks, or command sequences are known as exploit attacks. An attack entails taking over these systems and stealing stored data. These kinds of attacks make use of security flaws in systems, hardware, or other apps. Thus, in order to secure the data used in various network tiers, a thorough investigation into appropriate security techniques is required [19].
- Application layer: Application layer security issues and threats that are frequently encountered include parameter manipulation, HTTP floods, SQL injections, cross-site scripting, and Slowloris attacks. To improve their application layer security systems, organizations deploy web application firewalls and secure web gateway services [20]. Similarly, MQTT and CoAP are other protocols implemented in the application layer that also have specific challenges. For example, MQTT follows a broker-based approach to data exchange, which does raise certain internal security threats. Since the broker is an intermediary, an untrusted broker may intercept or change all transmitted data, violating confidentiality and integrity. These are some of the hard-to-solve problems with reference to traditional security solutions in that the MQTT decoupling principle eliminates secure end-to-end communication and direct device authentication modes [21]. On the other hand, CoAP has been designed for use by constrained devices; it is commonly exposed to such threats as eavesdropping, message manipulation, or replay attacks in cases where secure transmission protocols are not allowed. To improve MQTT and CoAP security, there must be a strong authentication process, encryption and access control of brokers and devices, and frequent updates. They are useful in protecting the integrity, confidentiality of data, and trustworthiness of devices in an IoT network [21].An injection attack known as cross-site scripting occurs when an attacker inserts client-side scripts that, depending on their objectives, entirely change the content of the apps. Another type of attack is a malicious code attack, in which certain software components are utilized as codes to harm particular computers. This attack is especially problematic since anti-virus software is unable to stop or manage it. Furthermore, it is frequently created as a program that requires users’ attention in order to carry out specific tasks or as an activity in and of itself [9]. The vast volumes of data held on this layer also lead to data loss and network disruptions. It is challenging to build data processing security systems that can guarantee that security is enhanced for all users due to the variety of data transmission activities and devices used in data transmission among users. Since these enormous volumes of data raise issues, there has been a growth in data loss and network disruptions.
3.3. The Most Common Solutions to Address Security Challenges in IoT
In the previous section, we delineate the stratum of IoT risk and security challenges within the IoT layered architecture, which is foundational to cybersecurity. Understanding these layers is essential to taking the imperative for proactive measures to mitigate potential threats, which is what the following Table 1 discusses.

Table 1.
The most common solutions to address security challenges in IoT.
4. Overview of Blockchain Technology
It is very difficult to find a generally agreed-upon definition of the blockchain. Some have defined blockchain as “a decentralized software mechanism that allows assets and transactions to be tracked and recorded without the presence of a central trust authority such as a bank”. Blockchain networks create proof of stake (POS) using unique digital signatures, which rely on public encryption keys known to everyone on the network and private keys known only to the owner. So, complex algorithms lead to consensus among users, ensuring that transaction data cannot be tampered with after verification, which reduces risks. Transaction records are stored and linked together in an encrypted way to form a chain of blocks. It is open to any node in the system, and everyone can add new blocks. Therefore, new blocks cannot be added without proof of work (PoW) or agreement on the part of other nodes that are participating in the system. Every participant on the blockchain has two keys: one public and the other private. The body and header are the components of every block on the blockchain. Transactions and operations that the user signs using the private key are located in the body. The public key is utilized to verify the source. The header contains block information like block size, timestamp, and transaction numbers. Once the block is created, it will be distributed to the minors to validate the transactions. When the transactions in the block are approved with the help of the PoW protocol, the block will be added to the blockchain, and it cannot be changed. This feature ensures security and transparency on the blockchain. Blockchain transactions are organized using a Merkle tree to ensure the integrity of the data [6,43].
Blockchain technology is also known as the largest transparent, secure, high-speed, low-cost, decentralized digital database. It is managed by its participants without an intermediary to modify or remove. These blocks are based on three principles: trust, transparency, and mutual oversight, as each user can confirm their data and verify the data’s integrity at all times, which achieves parity between users in exercising mutual collective control over data. Figure 4 shows a sequential block representation of blockchain technology. Every cube additionally includes cryptographic information relating to data that are not amenable to alteration, stressing how blockchain can encourage credible connectivity among IoT devices.
Figure 4.
Blockchain structure diagram.
In summary, blockchain can be defined as an information system based on a decentralized information base distributed among all devices included in the network to record all transaction data and their modifications in a way that includes the approval of all relevant parties on the validity of the data. The power of blockchain technology enables two basic standards: decentralization and high transparency in managing transactions of all kinds, such as payments and bank transfers, registering real estate ownership and national identities, exchanging markets and documents, and voting processes. Figure 5 is a conceptual diagram that depicts the IoT environment based on blockchain technology. The left side of the picture presents the blockchain and the most valuable features of IoT networks, while the right side of the picture presents some of the common technologies used by IoT.
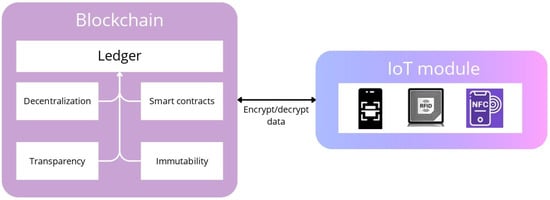
Figure 5.
Blockchain–IoT conceptual diagram.
4.1. History of Blockchain Technology
In 1999, Stuart Haber and Scott Stormetta encrypted electronic files to protect them from tampering, and in the following year, the idea was developed using “the Merkel tree”, and a chain of encrypted blocks was produced [7]. In 2008, a study appeared on the Internet by Satoshi Nakamoto titled “Bitcoin: A Peer-to-Peer Electronic Cash System”. It included a proposal for a digital currency based on a new computer system called blockchain. This technology allows all members of the blockchain to have complete copies of the same content that is encrypted, organized, and saved in serial blocks. Then, any addition to the content will be known to everyone on the blockchain. The added content will be approved after ensuring that it follows the established rules and then added to the database that is updated on all participating devices. The blockchain does not accept any modification to its content, which makes manipulation or hacking attempts almost impossible in light of the high encryption and group participation [7].
4.2. Components of Blockchain
This section identifies the components of blockchain, including hashing, consensus mechanisms, and smart contracts.
- Hash Functions: The main component of the blockchain ensures that stored data will remain as they are without alteration, which ensures data integrity. Hashing utilizes cryptography algorithms to transfer data into hashing code. Additionally, blockchain uses digital signatures and symmetric and asymmetric encryption to secure data from unauthorized access [7].
- Consensus Mechanisms: Blockchain uses different consensus mechanisms like proof of work and proof of stake to ensure IoT data are decentralized, safe from unauthorized access, and reliable. In addition, consensus mechanisms keep records safe from tampering in IoT environments [1].
- –
- Proof of Work (PoW): In Proof of Work (PoWs), miners engage in a competition to decode puzzles to earn the privilege of adding a succeeding block to the blockchain system. This method demands computing capability to enhance network security by deterring entities from seizing control of the network at a high cost and resource investment. Bitcoin serves as an illustration employing the PoW mechanism.
- –
- Proof of Stake (PoS): Proof of stake is a way for participants to validate blocks by holding a number of coins rather than trying to solve difficult puzzles like in proof of work (PoW). This approach minimizes energy usage and promotes dedication to the blockchain network in the run by selecting validators according to their stake. Ethereum has recently made the shift toward utilizing PoS through Ethereum 2. O.
- Smart Contracts: With the management of secure data sharing, automating processes, enabling programmable monetization models, establishing decentralized access control, and improving supply chain traceability for IoT-enabled systems, smart contracts on the blockchain can play an essential role in IoT applications [3].
- Node: Individual computers or any entity that participates in distributing the transactions, validation, and making a full copy of the blockchain [2].
4.3. How Blockchain Works
A blockchain system is viewed as a historical record of transactions in which each block is linked to other blocks in a sequence and immutably recorded across a peer-to-peer network. The system applies a special coding guarantee for each transaction. Through the system, participants maintain an encrypted record of each transaction within a decentralized recording mechanism in order to improve security and availability and allow all participants especially participants who do not trust each other to verify records and transactions. The system is characterized by great scalability and high flexibility, and the system does not require any additional intermediaries [7]. Figure 6 shows how blockchain technology works to ensure the integrity of the data.
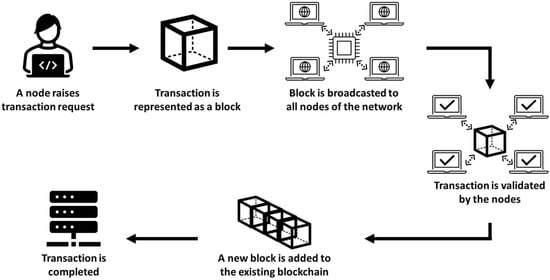
Figure 6.
Blockchain process to ensure data integrity [7].
4.4. Types of Blockchain
This section discusses different blockchain types like public blockchains, consortium blockchains, and private blockchains [2]. The type selection depends on the case requirements. Table 2 presents the features of each type.

Table 2.
Blockchain types.
4.5. Advantages of Combining Blockchain with IoT
This section presents several advantages of combining blockchain technology with IoT environments like the distributed ledger, cryptography, consensus mechanism, decentralized identity, transparency, and auditability:
- Distributed Ledger: The blockchain is used to record IoT data in a distributed ledger that cannot be changed or manipulated by unauthorized users. This feature ensures the traceability and integrity of the data [3].
- Cryptography: Robust cryptography techniques are used in blockchain, like digital signatures and hashing to secure the IoT from disclosure through malicious attacks [2].
- Consensus Mechanism: Blockchain utilizes a consensus protocol to ensure that all participants or nodes in the blockchain agree about the state of the ledger, like proof of work and proof of stake. This feature enhances trust in IoT data and prevents unauthorized editing [43].
- Decentralized Identity: Identity management for IoT devices is decentralized in the blockchain, which means the blockchain identifies, authenticates, and authorizes IoT users, entities, or devices securely. This feature prevents identity theft attacks [6].
- Transparency and Auditability: Transparency and auditability are provided by the uneditable nature of the blockchain ledger, which allows stakeholders to view the history of all activities and transactions stored on the blockchain, which enhances trust [8].
- Prevent Data Manipulation: The blockchain system prevents data manipulation because it does not allow data to be changed without the permission of the participating parties. If you attempt to do so, all participating parties will be notified [7].
4.6. Blockchain’s Cryptographic Techniques and Security Across IoT Layers
Among the features that blockchain offers, cryptographic solutions are exactly what is needed to ensure data protection for IoT networks. These cryptographic techniques are used at the perception, network, and application layers of IoT to mitigate the security concerns at all these layers.
4.6.1. Cryptographic Techniques in Blockchain
Blockchain technology leverages several cryptographic methods to secure data, maintain trust, and control access within IoT systems [1]:
- Digital Signatures: Each of the parties and devices that are involved in an IoT network is validated by digital signatures that employ asymmetric cryptography. Clients possess distinct private–public keys, guaranteeing the ability to sign and ensure the authenticity of the message. This approach is crucial in as much as it helps to verify that the data used have not been interfered with as they were being transmitted.
- Hashing: Applications employing hash functions include SHA-256, which converts plain text data to fixed-length codes, therefore minimizing the possibility of an intruder decrypting the content. IoT data cannot be subjected to unauthorized modification since they use hashing in block headers and transactions. Hashing also facilitates the indexing and storage of IoT data and generally improves the security of distributed systems where data integrity or ‘immutedness’ is paramount.
- Encryption (Symmetric and Asymmetric): Blockchain uses simple key and complex symmetric encryption methods besides using asymmetric or public key encryption methods to encrypt its data. A symmetric key is most often used for IoT secure communication, and an asymmetric key for blockchain identity checks provides secure and peer-to-peer IoT node exchange.
- Consensus Protocols: Not strictly cryptographic in nature, consensus algorithms like proof of work (pow) or proof of stake (PoS) make sure that blockchains are agreed on in terms of data validity. Thus, applying consensus mechanisms allows the blockchain to ensure data transaction safety, which will contribute to the complete protection of IoT systems from data fraud.
4.6.2. Role of Blockchain in Securing IoT Layers
Blockchain’s cryptographic features strengthen security across each layer of IoT architecture [1], as follows:
- Perception Layer: The perception layer involves various IoT physical devices and sensors for data collection. The incorporation of the technology helps to make security better here as information is encrypted and hashed, thereby eliminating the risk of the data collected by sensors being easily accessed by unauthorized entities. Smart contracts, on the other hand, ascertain device identities to help the IoT ecosystem to only allow authorized devices to engage in data exchange. This ensures that no form of access or manipulation at the point of data collection is made by an unauthorized person.
- Network Layer: At the network layer, blockchain uses decentralized and cryptographic functionality to encrypt data transmission across communication channels such as WiFi, Bluetooth, mobile networks, etc. Digital signatures and secure transmission mechanisms help guard against the common forms of attacks that include the man-in-the-middle (MiTM) attacks and Distributed Denial of Service (DDoS). Fourth, blockchain disintermediates the need for any central authorities, thereby eliminating single points of vulnerability and malware attacks that target connected control points in the network.
- Application Layer: This layer provides user interfaces, data storage, and service applications where IoT data are retrieved and processed. Blockchain fortifies this layer by offering unchangeable and intelligible transaction records, which provide compliance and confidence within applications. Three key measures of data reliability include the following: Hashing can ensure data authenticity. The use of digital signatures ensures data authenticity. The use of consensus protocols can also ensure the integrity of the records. It is most effective, especially in high-risk IoT domains, for example, smart health and industrial IoT, where data are highly sensitive and must be accurate.
5. Related Study
This section presents and summarizes the state-of-the-art proposals regarding the integration of blockchain with IoT apps, highlighting trust management, data security and privacy, and scalability and efficiency. Therefore, by categorizing related applications and challenges, this review provides an up-to-date outlook of the current solutions and points out the direction for improvement in the future. A summary of all the studies is provided in Table 3, including methodology, the studies’ limitations, and possible mitigations.
5.1. Trust Management in IoT Networks
Trust is a significant component in IoT environments because various devices operate independently of each other, sending and receiving information, and have no historical interactions. Several research works have tried to build trust in IoT nodes by exploiting the distributed ledger of the blockchain. For instance, BBTM presents a blockchain-inspired trust management scheme that can be directly applied to resource-constraint IoT systems. This system assesses trustworthiness through values quantified from prior settlements while preserving the reliability of nodes causing interaction. In the light of using trust scores and in noting down the transactions that take place in BBTM, for all these issues, a decentralized solution gives protection from malicious attacks on IoT devices. However, BBTM does not include the comprehensive and modeled realistic simulation of actual scenarios, which might be problematic in truly large IoT environments during implementation [5].
In support of this, Sivaganesan D [44] provided a blockchain-based, data-based trust management scheme to protect sensor networks in IoT. Their method preserves reliable information in a block that is stored in a chain, which can be retrieved by any node at the point of verification. As a result, untrusted parties can exchange information while guaranteeing the data’s integrity. One thing to note here is that the decentralization offered by blockchain increases trust as it gets rid of the dependency on a single point, and that is why blockchain is suitable for IoT systems that experience frequent attacks. However, there are some issues in combining the blockchain-based authentication with the actual real-time data transfer due to high latency.
Santis et al. [45] proposed a new audit system using blockchain technology to solve trust issues in IoT environments. The proposed system is used for metrological traceability in a distributed measurement system. Integrating the Physical Unclonable Function (PUF) protocol and a hybrid BIoT architecture allows decentralized operations and enhances trust for IoT devices.
Hameed et al. [46] presented their solution that stores identities and trust metrics on the blockchain in SDN-based IoT networks. In addition, the proposed solution aims to solve key and trust management issues in IoT devices. Also, it improves scalability by achieving this target. The results prove that the proposed solution can improve performance and productivity even with an increase in the number of IoT nodes and data transmitted.
Guntur D et al. [47] proposed a novel decentralized mechanism that depends on attribute-based access control along with a Trust and Reputation System (TRS). The proposed mechanism aims to authorize IoT entities, quantify the scores of trust and reputation for flexible and dynamic access control, use private sidechains to store private information, operate on public blockchains, and evaluate the performance criteria of IoT environments.
Ali et al. [48] introduced a unique system to monitor device behavior and classify trust levels for each zone using deep learning techniques in IoT environments integrated with blockchain. The proposed system aims to solve or mitigate the security challenges in these environments. There are different steps to implementing the system, including catching and verifying the behavior, applying behavior monitoring, deploying the trusted environments, creating and configuring the private blockchain, utilizing auto-cryptography classification, and calculating threshold values.
Shala B et al. [49] focused on the need to build trust in decentralized IoT environments and proposed a novel trust model with multiple adaptive layers. Also, the authors proposed to combine blockchain with a trust system to improve security and authorize new entities based on trust model permissions. The results proved that the proposed model overcomes others’ trust models in terms of reliability and resiliency against different attacks.
Suparna D et al. [50] proposed a novel framework that depends on blockchain technology and zero trust. The proposed framework is used to address security issues, enhance the identification of the device, and provide access control. Moreover, different security issues in IoT environments are presented in this paper.
Djamel K et al. [51] proposed a scalable and hierarchical system that depends on the blockchain and trust management protocol for IoT environments. The proposed system aims to address various security issues, enhance the evaluation of trust processes, and protect against different types of cyberattacks. The efficiency of the proposed system was evaluated using simulations.
5.2. Enhancing Data Security and Privacy
Security and privacy are among the most crucial challenges in IoT systems since tremendous quantities of distinct data transferring through networks are remarkably sensitive. As for this, various works have addressed this in one of the preceding ways by employing blockchain’s cryptographic features to secure IoT data. A good example is the use of an Ethereum-based blockchain by Mohanta et al. [7] to establish the DecAuth protocol for device authentication. This shields the device from attempts at unauthorized connection, which is accredited through a unique digital identity validated by the Ethereum network. The main strength of DecAuth is, of course, its high level of security, but the second drawback connected with the Ethereum infrastructure is still the problem of network scalability for the realization of large-scale IoT networks, which can face the problem of network congestion.
Al-Rakhami et al. [43] proposed a lightweight blockchain incorporating a trust model for the IoT network in the supply chain environment. Consequently, the data within this model will be subject to real-time verification through the use of blockchain, which will enable the participants of the supply chain to have access to and trust the data even without the need for a middleman. Having such decentralized validation is quite important for applications such as asset tracking, where real-time validations are typically needed. However, this model has some drawbacks when applied to real-world problems, especially in computational complexity terms owing to the computational complexity of IoT networks. Further, it is contingent only on well-endowed settings outfitted with the capacity for processing blockchain transactions.
Gugueoth et al. [8] presented a review paper about IoT security and privacy using decentralized blockchain techniques. The paper deeply discussed the security issues in IoT environments. It also discussed blockchain-based solutions, the security features that blockchain can provide, and the challenges that will be solved when integrating blockchain with IoT. In addition, different consensus protocols were briefly explained. Furthermore, open research challenges and future directions were also outlined.
Avishaek D et al. [52] focused on the importance of securing IoT environments and proposed an approach that combines blockchain with IoT environments to meet this objective. The proposed approach guarantees secure and quick authentication in these environments. Furthermore, the efficiency of the proposed approach was measured using simulations. The results proved that security and trust are achieved by enhancing access control, authentication, and data exchange mechanisms.
Al Sadawi A et al. [3] presented a survey on the integration of blockchain with IoT to enhance performance and eliminate challenges. The authors focused on the IoT challenges and proposed an architecture that combines blockchain with IoT in three layers using different approaches like cloudlet and dew computing. This integration aims to enhance the efficiency of authentication, services of data storage, and the performance and security of the proposed architecture. The proposed architecture aims to ensure resilience, efficiency, scalability, security, and decentralized storage of data.
Lee J. et al. [53] proposed a system that utilizes CP-ABE and blockchains to enhance the security of the data through mutual authentication and to improve efficiency. The proposed system enables access control of the data and key agreements in the IoT ecosystem. Furthermore, formal and informal security verification is used to prove the system’s robustness against different attacks, like tracking and guessing attacks.
Jannik L et al. [54] developed and evaluated a new registration and tracking system that is used for monitoring sensor data in blockchain-based IoT environments. The proposed system is used to improve the confidentiality, integrity, and availability of data (CIA) in blockchain-based IoT environments. In addition, different IoT applications are discussed in this paper. Dependence on centralized cloud servers is also discussed. Additionally, how blockchain technology can address the CIA of IoT data is mentioned.
Sun S et al. [55] proposed a new secure and lightweight solution that allows IoT devices to act as specialized nodes in the blockchain. The proposed solution reduces the redundancy in the blockchain and allows the integration of blockchain permissions, attribute-based access control, and identity-based signatures. In addition, the proposed solution improves security and efficiently prevents different types of attacks, like DDOS attacks.
5.3. Scalability and Efficiency Solutions
One important concern that is currently an open issue in blockchain IoT systems is scalability due to the inherent high traffic rate of IoT devices. In response to this, Al Hwaitat et al. [6] presented a blockchain-based authentication framework with AES to lower computational overhead while enhancing data confidentiality. This system saves encrypted IoT data in a cloud environment, but at the same time, through keeping in mind the prospects for further development, it is as secure as possible. It improves the functionality of IoT by reducing the instances in which data have to be re-encrypted, thereby being relevant for applications that will need to access encrypted data in the shortest time possible. Nevertheless, the problems of potential latency in cases of high-level network load are not completely solved, although it also points to further optimizations in the case of the minimum availability of resources.
The second new idea is the Dynamic Practical Byzantine Fault Tolerance consensus Algorithm (DPA-PBFT) designed for industrial IoT systems. This algorithm tackles scalability in the following way so that nodes experience less communication overhead, hence enhancing faster consensus even in a large network. Moreover, DPA-PBFT enhances data synchronization among non-peer nodes and is therefore well adapted for use in industrial IoT settings, where the availability of real-time and reliable data access is critical. However, the DPA-PBFT algorithm benefits from less latency than the PBFT algorithm; it can be somewhat computationally intense, thereby restraining the implementation in the IoT networks that are known to be deprived of resources deeper than a certain level [56,57].
5.4. Insights and Future Directions
With the analysis of these studies, it is very clear that blockchain technology offers the potential to solve the problems of trust, security, and scalability in IoT systems. All of these concepts build upon blockchain’s main features—its state and distributed ledger with a strong focus on consensus. For instance, trust-centered systems aim at ensuring node dependability and standard secure communication, while security-centered studies aim at data privacy and intrusion prevention. Scalability solutions investigate the means of handling performance from the client side and minimize the amount of throughput time, which is essential for real-time IoT applications.
Despite these systems’ useful contributions, some constraints are still present. Higher computational complexity, higher latency, and the problem of connecting IoT’s less powerful devices to a blockchain system pose further research questions. Possible future works may include fine-tuning consensus protocols for IoT, improving encryption algorithms that consume minimal computations, and exploring new architectures such as private and public chains at the same time.
The methodology, advantages, and limitations of each reviewed study are summarized in Table 3, where the table further highlights detailed implementation information.

Table 3.
Existing work in this field.
Table 3.
Existing work in this field.
| Ref. | Year | Proposal | Methodology | Limitations | Suggested Mitigation |
|---|---|---|---|---|---|
| [5] | 2021 |
|
|
|
|
| [44] | 2021 |
|
|
|
|
| [43] | 2021 |
|
|
|
|
| [6] | 2023 |
|
|
|
|
| [8] | 2023 |
|
|
|
|
| [56] | 2020 |
|
|
|
|
| [7] | 2020 |
|
|
|
|
| [45] | 2020 |
|
|
|
|
| [52] | 2024 |
|
|
|
|
| [46] | 2021 |
|
|
|
|
| [47] | 2021 |
|
|
|
|
| [48] | 2020 |
|
|
|
|
| [54] | 2020 |
|
|
|
|
| [50] | 2021 |
|
|
|
|
| [51] | 2020 |
|
|
|
|
| [55] | 2021 |
|
|
|
|
| [49] | 2020 |
|
|
|
|
| [57] | 2021 |
|
|
|
|
| [53] | 2023 |
|
|
|
|
| [3] | 2021 |
|
|
|
|
6. Blockchain-Driven Sustainability in IoT Security
Our research paper contributes to sustainability and reinforces the connection through the following aspects [58,59,60,61]:
- Improving security and trust:
- Data integrity: one of the characteristics of the blockchain is having a tamper-proof and decentralized ledger, which will guarantee that IoT devices remain trustworthy and accurate, mitigating the threat of data manipulation.
- Authentication: Blockchain can prevent unauthorized access and secure device authentication by implementing encryption techniques. This is a very critical point in the smart grid where data integrity is necessary for best sustainable practices.
- Resource efficiency:
- Resource management optimization: Blockchain can facilitate our lives by applying more efficient resource allocation in IoT networks. For instance, in smart agriculture systems, blockchain can contribute to tracking resource usage like the amount of water used, which leads to enhanced input usage and minimizes waste.
- Decentralized energy systems: Peer-to-peer energy trading among IoT devices using blockchain technology can help create decentralized energy systems in energy management that are both resilient and sustainable.
- Accountability and transparency:
- Transparency: Blockchain can enhance transparency by enabling the tracking of products in supply chains and empowering consumers to make informed decisions regarding sustainable products.
- Environmental impact tracking: With the integration of sensors linked to blockchain technology in place, for environmental impact monitoring purposes, companies can actively track their footprint in real time to foster responsibility and advocate for eco-friendly behaviors.
- Reduced carbon footprint:
- Improved efficiency in logistics: Utilizing IoT devices in conjunction with blockchain technology can streamline logistics and transportation processes to minimize fuel usage and emissions—a key factor in maintaining sustainable supply chains.
- Smart waste management: Utilizing blockchain can assist in waste management by offering insights into patterns of waste generation and promoting recycling through incentivized programs.
- Decentralization and resilience:
- Distributed networks: Leveraging the structure of blockchain technology can improve the robustness of IoT systems. This is especially advantageous in emergencies where ensuring communication and data security is crucial, for the distribution of resources.
- Empowerment of local communities: Local communities can gain empowerment through blockchain technology support for decision making and resource management to adopt sustainable practices that suit their unique environments.
- Innovation and collaboration:
- Encouraging research and development: Embracing blockchain technology in the IoT fosters teamwork, across fields and fuels advancements that support the development of eco-friendly technologies.
- Engagement of stakeholders: Collaboration among groups, like governments and businesses, can be improved with the help of blockchain technology to work together toward achieving sustainability goals.
Table 4 summarizes how blockchain-driven IoT contributes to sustainability.

Table 4.
How blockchain-driven IoT contributes to sustainability.
In this section, we showed how security, trust, and sustainability are all linked together. We also discussed real-life examples and possible advancements to support the idea of blockchain contributing to practices in IoT by highlighting how secure and reliable IoT systems can improve resource efficiency and increase transparency. Lastly, the document can demonstrate the significant impact of this research on sustainability.
IoT Integration Challenges and Sustainability
For IoT integration, one of the significant issues encountered is in terms of data integration compatibility. For instance, smart agriculture systems include sensors from different manufacturing companies to check soil moisture and crop status. However, the absence of protocols results in format variations that present challenges in analysis and action. Blockchain comes in handy in this case by creating a standardized, distributed, and auditable system for data exchange and verification across disparate IoT devices [1].
One of the key issues is the question of energy demand. Many IoT devices are installed in areas that are very remote or may have little or no access to resources (e.g., sensors used to monitor climate change in forests), and the sustainability problem arises when batteries need replacement, as this is very expensive and negatively impacts the environment. When leveraging blockchain technology integrated with, of course, energy-friendly consensus algorithms like PoS, datasets do not need to be transmitted or stored when unapproved or deemed suspicious—this greatly improves efficiency while simultaneously cutting energy costs in the process [3].
7. Challenges, Open Issues, and Future Research Directions
7.1. Challenges of Integrating Blockchain with IoT Environments
There are different challenges encountered by integrating blockchain technology with IoT, which are summarized in the following points:
- Blockchain networks are often suitable for small-scale applications, while IoT networks contain a lot of restricted devices that introduce a lot of information.
- The restricted devices in IoT environments have limited memory, computational power, and resources, which make it difficult for blockchain to apply very complex operations on these devices, which will affect their performance.
- Many IoT applications require fast responses, like emergency notifications in medical environments, while the networks of blockchain have lower latency, which may impact the response time.
- IoT devices suffer from many security challenges, like malware, physical tampering, or network-based attacks, which cannot be solved with blockchain. Even if it provides security countermeasures over the network, providing security to IoT devices exceeds its capabilities. Thus, ensuring the full security and privacy of IoT data is impossible.
- Some consensus mechanisms, like proof of work, consume a lot of energy, which may not align with IoT-restricted resources.
7.2. Future Directions
As a solution for some of these challenges, we propose the following points as future directions for other researchers and as other opportunities to conduct valuable research:
- Energy-Efficient Consensus Protocols: Centralized traditional consensus mechanisms such as proof of work (PoW) demand high computational power and energy, which become increasingly infeasible in the IoT context. The suggested future work is on extending stateless and resource-limited lightweight protocols such as PoS and DPoS to IoT networks. In addition, expanding the research focused on the set of adjustments that allow for the inclusion of minimal PoW with other minimal protocols would further help to achieve the balance between security and efficiency.
- Scalability in Large-Scale IoT Networks: Comprising several thousands or sometimes millions of interconnected devices within a distinct IoT network, scalability then becomes a problem within traditional consensus approaches. There is a lack of research on network-wide consensus algorithms like sharding or the use of Directed Acyclic Graphs (DAGs), in which the validation process is split across multiple subnets or in which the transactions can be validated asynchronously. Such approaches could increase the throughput, decrease the latency, and keep security; therefore, these techniques might be useful for a large-scale IoT environment.
- Latency-Optimized Consensus for Real-Time Applications: IoT interface response validity is critical in many interfaces, mainly due to the required real-time feedback in various healthcare monitoring or industrial automation applications. Other consensus mechanisms with fast finality that can also be further researched and modified for IoT consist of the BFT variants and Raft. These protocols reduce the delay by checking and affirming transactions in a more centralized or hierarchical model, making the response time for crucial applications optimum.
- Consensus Mechanisms with Built-In Security and Privacy for IoT: The point is that the IoT is an open and typically unstructured environment, so solutions based on consensus mechanisms, which also include lightweight encryption or even privacy-preserving techniques such as zero-knowledge proofs could boost both security and privacy. Further research can investigate ways of developing consensus algorithms that naturally address permission, privacy, and security issues in achieving consensus across IoT devices with minimal computational cost.
- Adaptive and Flexible Consensus Protocols for Dynamic IoT Environments: Indeed, IoT environments are characterized by continuous device onboarding and disconnection. Dynamic consensus protocols that provide flexibility in parameters such as the number of nodes involved in consensus and validation rules involved in the consensus are required. Studying non-rigid or auto-configurable protocols on which ML or auto-configuration algorithms for the assessment of network states and subsequent fine-tuning of consensus mechanisms could considerably enhance the stability and throughput of consensus across IoT networks.
8. Conclusions
Recently, a new concept has emerged that allows many devices with limited resources to communicate with each other, like sensors and other restricted devices, referred to as the IoT. These are called restricted devices because they use less memory, computing resources, and power. Nowadays, IoT can simplify daily life activities, but we have billions of interconnected devices that introduce a lot of information. So, attackers try to exploit this information for their purposes. In addition, a lot of security threats have occurred in IoT-layered architectures. For this, blockchain is considered an optimum solution to improve security solutions and enhance the reliability of the IoT by providing different features like transparency and decentralization, which leads to minimizing the manipulation of transmitted information over the network. In addition, blockchain helps control access to network resources, allowing the sharing of data securely and managing trust. This paper discussed the challenges of IoT-layered architectures and how blockchain can overcome these challenges. Moreover, this paper explored the most recent papers that were published between 2020 and 2024 to focus on their results and limitations. Furthermore, the advantages of combining blockchain with IoT are also elaborated. Additionally, this paper presents the challenges that need more attention when we integrate blockchain with IoT along with future directions that will help to address these issues.
Author Contributions
Conceptualization, S.A. and A.A.; methodology, S.A. and A.A.; software, S.A. and A.A.; validation, S.A. and A.A.; formal analysis, S.A. and A.A.; investigation, S.A. and A.A.; resources, S.A. and A.A.; writing original draft preparation, S.A. and A.A.; writing review and editing, S.A. and A.A.; supervision, A.A.; project administration, A.A.; funding acquisition, A.A. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the Deanship of Scientific Research, Vice Presidency for Graduate Studies and Scientific Research, King Faisal University, Saudi Arabia [GRANT No. KFU242458].
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
No new data were created or analyzed in this study. Data sharing is not applicable to this article.
Acknowledgments
The authors extend their appreciation to the Deanship of Scientific Research, Vice Presidency for Graduate Studies and Scientific Research, King Faisal University, Saudi Arabia [GRANT No. KFU242458]. The authors would like to thank the anonymous reviewers for their insightful scholastic comments and suggestions, which improved the quality and clarity of the paper.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| IoT | Internet of Things; |
| MiTM | Man in The Middle; |
| SLR | Systematic Literature Review; |
| DoS | Denial of Service; |
| AI | Artificial Intelligence; |
| ML | Machine Learning; |
| VPN | Virtual Private Network; |
| IDS | Intrusion Detection System. |
Appendix A. Included Papers in the SLR
Table A1 presents all papers reviewed in this SLR.

Table A1.
Included papers in the SLR.
Table A1.
Included papers in the SLR.
| Ref. No. | Title | Authors | Year |
|---|---|---|---|
| [5] | A blockchain-based trust management method for Internet of Things | Wu, Xu and Liang, Junbin | 2021 |
| [44] | A data driven trust mechanism based on blockchain in IoT sensor networks for detection and mitigation of attacks | Sivaganesan, D | 2021 |
| [43] | A blockchain-based trust model for the internet of things supply chain management | Al-Rakhami, Mabrook S and Al-Mashari, Majed | 2021 |
| [6] | A new blockchain-based authentication framework for secure IoT networks | Al Hwaitat, Ahmad K and Almaiah, Mohammed Amin and Ali, Aitizaz and Al-Otaibi, Shaha and Shishakly, Rima and Lutfi, Abdalwali and Alrawad, Mahmaod | 2023 |
| [8] | A review of IoT security and privacy using decentralized blockchain techniques | Gugueoth, Vinay and Safavat, Sunitha and Shetty, Sachin and Rawat, Danda | 2023 |
| [56] | A trust-evaluation-enhanced blockchain-secured industrial IoT system | Wu, Di and Ansari, Nirwan | 2020 |
| [7] | Addressing security and privacy issues of IoT using blockchain technology | Mohanta, Bhabendu Kumar and Jena, Debasish and Ramasubbareddy, Somula and Daneshmand, Mahmoud and Gandomi, Amir H | 2020 |
| [45] | Blockchain-based infrastructure to enable trust in IoT environment | De Santis, L and Paciello, Vincenzo and Pietrosanto, Antonio | 2020 |
| [52] | A Novel Distributed Authentication of Blockchain Technology Integration in IoT Services | Deep, Avishaek and Perrusquía, Adolfo and Aljaburi, Lamees and Al-Rubaye, Saba and Guo, Weisi | 2024 |
| [46] | A scalable key and trust management solution for IoT sensors using SDN and blockchain technology | Hameed, Sufian and Shah, Syed Attique and Saeed, Qazi Sarmad and Siddiqui, Shahbaz and Ali, Ihsan and Vedeshin, Anton and Draheim, Dirk | 2021 |
| [47] | Trust-based blockchain authorization for iot | Putra, Guntur Dharma and Dedeoglu, Volkan and Kanhere, Salil S and Jurdak, Raja and Ignjatovic, Aleksandar | 2021 |
| [48] | Towards a secure behavior modeling for iot networks using blockchain | Ali, Jawad and Khalid, Ahmad Shahrafidz and Yafi, Eiad and Musa, Shahrulniza and Ahmed, Waqas | 2020 |
| [54] | Toward trust in Internet of Things ecosystems: Design principles for blockchain-based IoT applications | Lockl, Jannik and Schlatt, Vincent and Schweizer, André and Urbach, Nils and Harth, Natascha | 2020 |
| [50] | Securing IoT devices using zero trust and blockchain | Dhar, Suparna and Bose, Indranil | 2021 |
| [51] | Decentralized blockchain-based trust management protocol for the Internet of Things | Kouicem, Djamel Eddine and Imine, Youcef and Bouabdallah, Abdelmadjid and Lakhlef, Hicham | 2020 |
| [55] | Blockchain-based IoT access control system: towards security, lightweight, and cross-domain | Sun, Shuang and Du, Rong and Chen, Shudong and Li, Weiwei | 2021 |
| [49] | Blockchain and trust for secure, end-user-based and decentralized IoT service provision | Shala, Besfort and Trick, Ulrich and Lehmann, Armin and Ghita, Bogdan and Shiaeles, Stavros | 2020 |
| [57] | Achieving IoT data security based blockchain | Liao, Dan and Li, Hui and Wang, Wentao and Wang, Xiong and Zhang, Ming and Chen, Xue | 2021 |
| [53] | Blockchain-based data access control and key agreement system in iot environment | Lee, JoonYoung and Kim, MyeongHyun and Park, KiSung and Noh, SungKee and Bisht, Abhishek and Das, Ashok Kumar and Park, Youngho | 2023 |
| [3] | A survey on the integration of blockchain with IoT to enhance performance and eliminate challenges | Al Sadawi, Alia and Hassan, Mohamed S and Ndiaye, Malick | 2021 |
References
- Da Xu, L.; Lu, Y.; Li, L. Embedding blockchain technology into IoT for security: A survey. IEEE Internet Things J. 2021, 8, 10452–10473. [Google Scholar]
- Uddin, M.A.; Stranieri, A.; Gondal, I.; Balasubramanian, V. A survey on the adoption of blockchain in iot: Challenges and solutions. Blockchain Res. Appl. 2021, 2, 100006. [Google Scholar] [CrossRef]
- Al Sadawi, A.; Hassan, M.S.; Ndiaye, M. A survey on the integration of blockchain with IoT to enhance performance and eliminate challenges. IEEE Access 2021, 9, 54478–54497. [Google Scholar] [CrossRef]
- Mohamed Shaffril, H.A.; Samsuddin, S.F.; Abu Samah, A. The ABC of systematic literature review: The basic methodological guidance for beginners. Qual. Quant. 2021, 55, 1319–1346. [Google Scholar] [CrossRef]
- Wu, X.; Liang, J. A blockchain-based trust management method for Internet of Things. Pervasive Mob. Comput. 2021, 72, 101330. [Google Scholar] [CrossRef]
- Al Hwaitat, A.K.; Almaiah, M.A.; Ali, A.; Al-Otaibi, S.; Shishakly, R.; Lutfi, A.; Alrawad, M. A new blockchain-based authentication framework for secure IoT networks. Electronics 2023, 12, 3618. [Google Scholar] [CrossRef]
- Mohanta, B.K.; Jena, D.; Ramasubbareddy, S.; Daneshmand, M.; Gandomi, A.H. Addressing security and privacy issues of IoT using blockchain technology. IEEE Internet Things J. 2020, 8, 881–888. [Google Scholar] [CrossRef]
- Gugueoth, V.; Safavat, S.; Shetty, S.; Rawat, D. A review of IoT security and privacy using decentralized blockchain techniques. Comput. Sci. Rev. 2023, 50, 100585. [Google Scholar] [CrossRef]
- Husin, H.S.; Fairuz, A.M.; Beh, D. IoT-Based Recycle Rebate System–Securing Website and Database. J. Comput. Technol. Creat. Content (JTec) 2020, 5, 55–60. [Google Scholar]
- Malhotra, P.; Singh, Y.; Anand, P.; Bangotra, D.K.; Singh, P.K.; Hong, W.C. Internet of things: Evolution, concerns and security challenges. Sensors 2021, 21, 1809. [Google Scholar] [CrossRef]
- Xie, H.; Yang, Z. The risk management mode of construction project management in the multimedia environment of internet of things. Mob. Inf. Syst. 2021, 2021, 1–8. [Google Scholar] [CrossRef]
- Lazzaro, S.; De Angelis, V.; Mandalari, A.M.; Buccafurri, F. Is your kettle smarter than a hacker? a scalable tool for assessing replay attack vulnerabilities on consumer iot devices. In Proceedings of the 2024 IEEE International Conference on Pervasive Computing and Communications (PerCom), Biarritz, France, 20 April 2024; pp. 114–124. [Google Scholar]
- Honar Pajooh, H.; Rashid, M.; Alam, F.; Demidenko, S. Multi-layer blockchain-based security architecture for internet of things. Sensors 2021, 21, 772. [Google Scholar] [CrossRef] [PubMed]
- Gupta, B.B.; Quamara, M. An overview of Internet of Things (IoT): Architectural aspects, challenges, and protocols. Concurr. Comput. Pract. Exp. 2020, 32, e4946. [Google Scholar] [CrossRef]
- Li, Y. Security and Risk Analysis of Financial Industry Based on the Internet of Things. Wirel. Commun. Mob. Comput. 2022, 2022, 6343468. [Google Scholar] [CrossRef]
- Lee, I. Internet of Things (IoT) cybersecurity: Literature review and IoT cyber risk management. Future Internet 2020, 12, 157. [Google Scholar] [CrossRef]
- Paracha, M.T.; Dubois, D.J.; Vallina-Rodriguez, N.; Choffnes, D. IoTLS: Understanding TLS usage in consumer IoT devices. In Proceedings of the Proceedings of the 21st ACM Internet Measurement Conference, Virtual, 2–4 November 2021; pp. 165–178. [Google Scholar]
- Islam, M.R.; Aktheruzzaman, K. An analysis of cybersecurity attacks against internet of things and security solutions. J. Comput. Commun. 2020, 8, 11–25. [Google Scholar] [CrossRef]
- Patel, C.; Doshi, N. A novel MQTT security framework in generic IoT model. Procedia Comput. Sci. 2020, 171, 1399–1408. [Google Scholar] [CrossRef]
- Mrabet, H.; Belguith, S.; Alhomoud, A.; Jemai, A. A survey of IoT security based on a layered architecture of sensing and data analysis. Sensors 2020, 20, 3625. [Google Scholar] [CrossRef]
- Liyanage, M.; Braeken, A.; Kumar, P.; Ylianttila, M. IoT Security: Advances in Authentication; John Wiley & Sons: Hoboken, NJ, USA, 2020. [Google Scholar]
- Murtala Zungeru, A.; Chuma, J.M.; Lebekwe, C.K.; Phalaagae, P.; Gaboitaolelwe, J.; Phalaagae, P.; Zungeru, A.M.; Sigweni, B.; Chuma, J.M.; Semong, T. Security challenges in iot sensor networks. In Green Internet of Things Sensor Networks: Applications, Communication Technologies, and Security Challenges; Springer: Berlin/Heidelberg, Germany, 2020; pp. 83–96. [Google Scholar]
- Singh, K.; Neeru, N. A comprehensive study of the iot attacks on different layers. J. Punjab Acad. Sci. 2023, 23, 140–155. [Google Scholar]
- Chaudhary, J.; Prasad, S. IoT in healthcare sector-a comprehensive analysis of threats and privacy issues. In AIP Conference Proceedings; AIP Publishing: College Park, MD, USA, 2022; Volume 2519. [Google Scholar]
- Wu, C.K.; Wu, C.K. IoT Perception Layer Security. In Internet of Things Security: Architectures and Security Measures; Springer Nature: Singapore, 2021; pp. 95–106. [Google Scholar]
- Sun, P.; Shen, S.; Wan, Y.; Wu, Z.; Fang, Z.; Gao, X.Z. A Survey of IoT Privacy Security: Architecture, Technology, Challenges, and Trends. IEEE Internet Things J. 2024, 11, 34567–34591. [Google Scholar] [CrossRef]
- Wang, J.; Liu, C.; Zhou, L.; Tian, L.; Yu, X. Early detection of node capture attack in the internet of things. In Proceedings of the 2021 IEEE 4th International Conference on Electronics and Communication Engineering (ICECE), Xi’an, China, 17–19 December 2021; pp. 132–135. [Google Scholar]
- Khader, R.; Eleyan, D. Survey of dos/ddos attacks in iot. Sustain. Eng. Innov. 2021, 3, 23–28. [Google Scholar] [CrossRef]
- Wu, C.K.; Wu, C.K. IoT Security Architecture. Internet of Things Security: Architectures and Security Measures; Springer Nature: Singapore, 2021; pp. 27–44. [Google Scholar]
- Sharma, G.; Vidalis, S.; Anand, N.; Menon, C.; Kumar, S. A survey on layer-wise security attacks in IoT: Attacks, countermeasures, and open-issues. Electronics 2021, 10, 2365. [Google Scholar] [CrossRef]
- Patel, N.; Singh, A. Security Issues, Attacks and Countermeasures in Layered IoT Ecosystem. Int. J. Next-Gener. Comput. 2023, 14, 400. [Google Scholar]
- Jahangeer, A.; Bazai, S.U.; Aslam, S.; Marjan, S.; Anas, M.; Hashemi, S.H. A review on the security of IoT networks: From network layer’s perspective. IEEE Access 2023, 11, 71073–71087. [Google Scholar] [CrossRef]
- Al Sukhni, B.; Manna, S.K.; Dave, J.M.; Zhang, L. Machine learning-based solutions for securing IoT systems against multilayer attacks. In Proceedings of the International Conference on Communication, Networks and Computing, Gwalior, India, 8–10 December 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 140–153. [Google Scholar]
- Gupta, N.; Garg, U. A Proposed IoT Security Framework and Analysis of Network Layer Attacks in IoT. In Soft Computing: Theories and Applications, Proceedings of the SoCTA 2020, Virtual, 25–27 December 2020; Springer: Berlin/Heidelberg, Germany, 2022; Volume 1, pp. 85–95. [Google Scholar]
- Arshad, A.; Hanapi, Z.M.; Subramaniam, S.; Latip, R. A survey of Sybil attack countermeasures in IoT-based wireless sensor networks. PeerJ Comput. Sci. 2021, 7, e673. [Google Scholar] [CrossRef]
- Thakkar, H.M.; Agarwal, A.; Singh, A.; Duggal, H.K.; Prajeesha, P. Analysis and prevention of threats to IoT systems. In AIP Conference Proceedings; AIP Publishing: College Park, MD, USA, 2023; Volume 2764. [Google Scholar]
- Pavithra, P.; Durgadevi, P. Threat detection in IOT layers using ML techniques. In AIP Conference Proceedings; AIP Publishing: College Park, MD, USA, 2024; Volume 3037. [Google Scholar]
- Al-Kasassbeh, M.; Almseidin, M.; Alrfou, K.; Kovacs, S. Detection of IoT-botnet attacks using fuzzy rule interpolation. J. Intell. Fuzzy Syst. 2020, 39, 421–431. [Google Scholar] [CrossRef]
- Kumar, N.; Ahmad, S. Security threats in layered architecture of web of things. In Proceedings of the 2020 Fourth International Conference on Inventive Systems and Control (ICISC), Coimbatore, India, 8–10 January 2020; pp. 745–750. [Google Scholar]
- O’Sullivan, W.; Choo, K.K.R.; Le-Khac, N.A. Defending IoT devices from malware. In Cyber and Digital Forensic Investigations: A Law Enforcement Practitioner’s Perspective; Springer: Cham, Switzerland, 2020; pp. 5–29. Available online: https://link.springer.com/chapter/10.1007/978-3-030-47131-6_2 (accessed on 7 July 2023).
- Procopiou, A. ForChaosLR: A Lightweight Multi-Layer IDS to Detect Application Layer DDoS Attacks in the Smart Home-Smart Grid Network. Ph.D. Thesis, University of London, London, UK, 2021. [Google Scholar]
- Khan, N.A.; Awang, A.; Karim, S.A.A. Security in Internet of Things: A review. IEEE Access 2022, 10, 104649–104670. [Google Scholar] [CrossRef]
- Al-Rakhami, M.S.; Al-Mashari, M. A blockchain-based trust model for the internet of things supply chain management. Sensors 2021, 21, 1759. [Google Scholar] [CrossRef]
- Sivaganesan, D. A data driven trust mechanism based on blockchain in IoT sensor networks for detection and mitigation of attacks. J. Trends Comput. Sci. Smart Technol. (TCSST) 2021, 3, 59–69. [Google Scholar]
- De Santis, L.; Paciello, V.; Pietrosanto, A. Blockchain-based infrastructure to enable trust in IoT environment. In Proceedings of the 2020 IEEE International Instrumentation and Measurement Technology Conference (I2MTC), Dubrovnik, Croatia, 25–28 May 2020; pp. 1–6. [Google Scholar]
- Hameed, S.; Shah, S.A.; Saeed, Q.S.; Siddiqui, S.; Ali, I.; Vedeshin, A.; Draheim, D. A scalable key and trust management solution for IoT sensors using SDN and blockchain technology. IEEE Sens. J. 2021, 21, 8716–8733. [Google Scholar] [CrossRef]
- Putra, G.D.; Dedeoglu, V.; Kanhere, S.S.; Jurdak, R.; Ignjatovic, A. Trust-based blockchain authorization for iot. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1646–1658. [Google Scholar] [CrossRef]
- Ali, J.; Khalid, A.S.; Yafi, E.; Musa, S.; Ahmed, W. Towards a secure behavior modeling for iot networks using blockchain. arXiv 2020, arXiv:2001.01841. [Google Scholar]
- Shala, B.; Trick, U.; Lehmann, A.; Ghita, B.; Shiaeles, S. Blockchain and trust for secure, end-user-based and decentralized IoT service provision. IEEE Access 2020, 8, 119961–119979. [Google Scholar] [CrossRef]
- Dhar, S.; Bose, I. Securing IoT devices using zero trust and blockchain. J. Organ. Comput. Electron. Commer. 2021, 31, 18–34. [Google Scholar] [CrossRef]
- Kouicem, D.E.; Imine, Y.; Bouabdallah, A.; Lakhlef, H. Decentralized blockchain-based trust management protocol for the Internet of Things. IEEE Trans. Dependable Secur. Comput. 2020, 19, 1292–1306. [Google Scholar] [CrossRef]
- Deep, A.; Perrusquía, A.; Aljaburi, L.; Al-Rubaye, S.; Guo, W. A Novel Distributed Authentication of Blockchain Technology Integration in IoT Services. IEEE Access 2024, 12, 9550–9562. [Google Scholar] [CrossRef]
- Lee, J.; Kim, M.; Park, K.; Noh, S.; Bisht, A.; Das, A.K.; Park, Y. Blockchain-based data access control and key agreement system in iot environment. Sensors 2023, 23, 5173. [Google Scholar] [CrossRef]
- Lockl, J.; Schlatt, V.; Schweizer, A.; Urbach, N.; Harth, N. Toward trust in Internet of Things ecosystems: Design principles for blockchain-based IoT applications. IEEE Trans. Eng. Manag. 2020, 67, 1256–1270. [Google Scholar] [CrossRef]
- Sun, S.; Du, R.; Chen, S.; Li, W. Blockchain-based IoT access control system: Towards security, lightweight, and cross-domain. IEEE Access 2021, 9, 36868–36878. [Google Scholar] [CrossRef]
- Wu, D.; Ansari, N. A trust-evaluation-enhanced blockchain-secured industrial IoT system. IEEE Internet Things J. 2020, 8, 5510–5517. [Google Scholar] [CrossRef]
- Liao, D.; Li, H.; Wang, W.; Wang, X.; Zhang, M.; Chen, X. Achieving IoT data security based blockchain. Peer-to-Peer Netw. Appl. 2021, 14, 2694–2707. [Google Scholar] [CrossRef]
- Li, C.Z.; Chen, Z.; Xue, F.; Kong, X.T.; Xiao, B.; Lai, X.; Zhao, Y. A blockchain-and IoT-based smart product-service system for the sustainability of prefabricated housing construction. J. Clean. Prod. 2021, 286, 125391. [Google Scholar] [CrossRef]
- Dutta, P.; Chavhan, R.; Gowtham, P.; Singh, A. The individual and integrated impact of Blockchain and IoT on sustainable supply chains: A systematic review. Proc. Supply Chain. Forum Int. J. 2023, 24, 103–126. [Google Scholar] [CrossRef]
- Hasan, H.R.; Musamih, A.; Salah, K.; Jayaraman, R.; Omar, M.; Arshad, J.; Boscovic, D. Smart agriculture assurance: IoT and blockchain for trusted sustainable produce. Comput. Electron. Agric. 2024, 224, 109184. [Google Scholar] [CrossRef]
- Wu, S.R.; Shirkey, G.; Celik, I.; Shao, C.; Chen, J. A review on the adoption of AI, BC, and IoT in sustainability research. Sustainability 2022, 14, 7851. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).