Abstract
Mobile Cognitive Radio Networks (MCRNs) have emerged as a promising solution to address spectrum scarcity by enabling dynamic access to underutilized frequency bands assigned to Primary or Licensed Users (PUs). These networks rely on Cooperative Spectrum Sensing (CSS) to identify available spectrum, but this collaborative approach also introduces vulnerabilities to security threats—most notably, Spectrum Sensing Data Falsification (SSDF) attacks. In such attacks, malicious nodes deliberately report false sensing information, undermining the reliability and performance of the network. This paper investigates the application of machine learning techniques to detect and mitigate SSDF attacks in MCRNs, particularly considering the additional challenges introduced by node mobility. We propose a hybrid detection framework that integrates a reputation-based weighting mechanism with Support Vector Machine (SVM) and K-Nearest Neighbors (KNN) classifiers to improve detection accuracy and reduce the influence of falsified data. Experimental results on software defined radio (SDR) demonstrate that the proposed method significantly enhances the system’s ability to identify malicious behavior, achieving high detection accuracy, reduces the rate of data falsification by approximately 5–20%, increases the probability of attack detection, and supports the dynamic creation of a blacklist to isolate malicious nodes. These results underscore the potential of combining machine learning with trust-based mechanisms to strengthen the security and reliability of mobile cognitive radio networks.
1. Introduction
The faster evolution of the internet and the proliferation of wireless devices and services have led to an unprecedented demand for radio frequency spectrum, creating a spectrum scarcity problem around the world. Traditional static spectrum allocation methods have proven inadequate in addressing this challenge, as they often result in underutilization of available frequencies, especially in mobile networks. In response, Mobile Cognitive Radio Networks (MCRNs) have emerged as a dynamic solution in mobile services, enabling unlicensed users, referred to as Secondary Users (SUs), to opportunistically access underutilized spectrum bands allocated to Primary Users (PUs), with a cognitive protocol the mobile services (voice call or data) are changing their assigned carrier frequencies according to the PU presence [1].
According to this concept, the core functionality of MCRNs hinges on Spectrum Sensing, wherein SUs continuously monitor the radio environment to detect idle spectrum bands for potential use. The PU has the highest priority in the spectrum use, and the SU must find a spectral hole to transmit its information. The SU has issues like fading and hidden terminal problems in this network. One of the standard solutions is the use of CSS, where the information of various SUs is shared. SU transmits the spectrum sensing results to a fusion center (FC), which makes a global decision. The CSS can be centralized, where all the SUs send the report of the PU’s presence in the environment, and distributed where there is no FC. Each SUs senses the radio environment and reports to those in a coverage range, making the decision individually [2].
Although there are numerous advantages, CSS introduces new security vulnerabilities to the network, limiting the use of the cognitive protocol and necessitate constant spectrum sensing. One of the attacks that decreases the performance of the network is the SSDF attack, also known as the Byzantine attack. In these attacks, malicious or compromised SUs send false report-sensing information to the FC and, in a traditional scheme, make a global decision based on the reports, leading to the conclusion that there is a PU present in the network when there is an attacker with a false report. Such falsified reports lead to incorrect spectrum occupancy decisions, resulting in either interference with PUs or denial of spectrum access to legitimate SUs [3].
In the CSS scheme, an alternative to the fusion center is to access a database or centralized data, which can be challenging, depending on the telecommunications operators. The database-based approaches rely on external connectivity and updates, which can incur delays. Localized fusion centers, by processing locally sensed data, can reduce detection latency and respond more quickly to changes in primary user activity [4]. In many mobile scenarios (vehicular networks, rural or ad hoc settings, or when backhaul connectivity is intermittent), access to a centralized database may be unavailable or unreliable. Relying on local fusion ensures robustness even when connectivity to external databases is compromised [5].
Database information is often aggregated or updated at coarse spatial or temporal scales; thus, it may not capture quickly changing PU activity due to mobility, propagation fading, or shadowing. Local spectrum sensing is better suited to capture real-time local conditions [6]. Using a geolocation database may require regulatory permissions, accurate location reporting, and may raise privacy or security issues. Moreover, communicating location and querying databases adds communication overhead (energy, bandwidth, etc.), which may be nontrivial in constrained mobile devices.
Although detection and mitigation of SSDF attacks have been extensively investigated in non-mobile CRNs, these studies generally assume static or low-mobility scenarios [6,7]. In contrast, MCRNs introduce additional challenges such as rapid topology changes, fluctuating channel conditions, and time-varying spectrum availability that can degrade the performance of existing detection schemes. The dynamic topology and varying channel conditions make the identification of malicious behavior difficult, as the network must distinguish between legitimate changes due to mobility and deliberate falsification attempts. In recent years, Machine Learning (ML) techniques have garnered significant attention for their potential in enhancing the security and reliability of CRNs.
The ML-designed algorithms can learn complex patterns and anomalies in data, making them well-suited for detecting SSDF attacks. For instance, SVM has been employed to classify sensing reports as honest or malicious based on features extracted from the data. Similarly, KNN algorithms have been utilized to identify anomalous behavior by comparing the similarity of sensing reports among neighboring nodes, which makes them candidates to explore in MCRN [8].
Another option is to integrate reputation-based mechanisms with ML techniques to mitigate SSDF attacks. This model assigns reputation scores to each SU based on their historical behavior in the network environment. The network can calculate or estimate a weight and include it in its sensing reports accordingly. Combining these reputation scores with ML classifiers enhances the robustness of SSDF detection systems, as demonstrated in studies where such hybrid approaches achieved higher detection accuracy and reduced false alarm rates [9].
Despite these advancements, several challenges remain in effectively detecting and mitigating SSDF attacks in MCRNs. The dynamic nature of mobile networks necessitates adaptive learning models capable of handling non-stationary data distributions. Additionally, the resource constraints of mobile devices impose limitations on the complexity of ML algorithms that can be deployed. Balancing detection performance with computational efficiency is, therefore, a critical consideration in the design of ML-based SSDF detection systems. Moreover, the adversarial nature of SSDF attacks implies that attackers may evolve their strategies to evade detection. This threat landscape highlights the importance of regularly updating and retraining ML models to preserve their detection accuracy. Leveraging adaptive learning techniques that enable models to evolve in real-time with incoming data presents a promising approach to address this challenge [10].
In this paper, we propose a machine learning-based approach for the detection of SSDF attacks in MCRN by using SVM and KNN together with the reputation-based weighting mechanism. Our methodology is grounded in a supervised learning framework, which relies on a pre-constructed database of features, including signal-to-noise ratio (SNR) and the energy of the received power signal. To validate our approach, we deployed the system using SDR devices, creating a realistic MCRN testbed with actual smartphones acting as SU and an SDR-based emulated SSDF attacker.
Our contribution lies in integrating SVM, KNN, and a reputation-based weighting mechanism into a single detection model tailored to MCRNs. This hybrid design leverages the complementary strengths of SVM (strong margin-based classification), KNN (instance-based pattern recognition), and dynamic trust scoring to achieve higher robustness under mobility and adversarial conditions.
The proposed model demonstrated high classification accuracy, with SSDF detection probabilities exceeding 90%. These results consistently outperformed single-feature detectors, and it was validated through theoretical analysis, simulation studies, and real-world SDR experiments. The findings confirm the effectiveness and robustness of our multi-feature, machine learning-based detection framework for securing MCRNs against SSDF threats.
The remainder of this paper is structured as follows: Section 2 presents a review of related work and highlights the main contributions of this study. Section 3 describes the proposed ML-based detection framework for identifying SSDF attacks. In Section 4, we detail the experimental setup using SDR platforms. Section 5 discusses the results and evaluates the system’s performance under various scenarios. Finally, Section 6 concludes the paper with key findings and future research directions.
2. Previous Work
SSDF attacks occur when a malicious SU sends falsified PU detection reports to the FC in CSS cognitive networks, aiming to manipulate decisions regarding spectrum usage. These attacks can be either cooperative or probabilistic and represent a significant challenge to the integrity of the collaborative sensing process. The mitigation or detection schemes for the attack employ traditional approaches, with some utilizing artificial intelligence (AI). For example, a probabilistic attack model in which the attacker adapts their strategy based on the FC’s defense mechanism maximizes damage while reducing attack costs, formulating the problem as a convex linear programming task for efficient solutions [11].
Another approach is to use a reputation-based defense with clusters, based on reputation, to counter cooperative SSDF attacks without requiring prior knowledge of the attackers. This strategy groups users according to their reporting history, improving the separation between normal and malicious users and developing a similarity-based clustering algorithm to detect malicious users in cognitive wireless networks. This approach is notable for its low computational complexity [12]. A scheme based on a beta reputation system to address dynamic SSDF attacks, assigning reputation values to SU according to their behavioral history, is studied in [13]. This mechanism penalizes malicious behavior, enhancing the fairness and robustness of the system.
Deep reinforcement learning has also been used to identify changing patterns in the behavior of secondary users. Their model improves the reliability of cooperative sensing compared to traditional algorithms [3]. Also, reinforcement learning was used to enhance detection under imperfect reporting channels and Byzantine attacks. Unlike approaches that eliminate detected nodes, this model weights each node’s contributions to avoid false positives [14].
On the other hand, energy management in the presence of SSDF attacks has also been thoroughly investigated, recognizing that malicious interference can significantly degrade the energy efficiency of cognitive radio networks. In response, a solution based on deep learning and graph-based models has been proposed [15]. This approach leverages the pattern recognition capabilities of DNN alongside the relational insights provided by graph structures to identify malicious nodes and optimize energy consumption. By modeling the interactions among SU as a graph, the system can detect anomalies in sensing behavior and adjust energy usage accordingly, thereby maintaining network performance while mitigating the influence of attackers.
Furthermore, the challenges associated with spectrum sharing in IoT and emerging 5G/6G networks are critically analyzed, particularly under adversarial conditions. As the number of connected devices continues to surge, the competition for limited spectral resources intensifies, making these systems increasingly vulnerable to coordinated attacks. The study highlights the increased risk posed by SSDF and similar attacks in scenarios where multiple heterogeneous devices share a typical spectrum. In such environments, malicious users can exploit trust-based mechanisms or sensing protocols to disrupt service availability or mislead the spectrum allocation process, leading to reduced quality of service and potential system failures [16].
An Apriori algorithm has been used to detect collusive SSDF attacks. The correlation among malicious nodes allows them to be identified as frequent itemsets, revealing collaborative patterns among attackers [17]. A similar approach combines correlation coefficients and path loss factors to enhance attacker detection in CSS, improving the robustness against spatial and temporal variations [18].
One method to detect the attack is to use the trust or suspicious level. For example, an exclusion scheme based on report history and Hamming distance between users was used. A cumulative suspicion level is calculated, allowing the exclusion of anomalous nodes from the decision-making process [19]. Another author developed a trust model based on Bayesian inference with a sliding window, capable of detecting probabilistic SSDF attackers without prior knowledge. A sigmoid function is used to stabilize trust values [7].
A combined approach that first eliminates untrustworthy nodes based on reputation, then applies an improved q-out-of-m rule at the fusion center to mitigate residual attacks, including in dynamic scenarios, was modeled in [20]. Another reputation-based adaptive clustering algorithm is used to detect cooperative SSDF attacks. This approach does not require prior information about the attackers and enhances detection by distinguishing between normal and malicious users through historical analysis [21].
Another AI model uses an online learning algorithm that selects trustworthy users based on an approximate ground truth of the channel state. The algorithm dynamically updates trust levels and minimizes energy consumption [22]. Another online learning algorithm that selects trustworthy users and dynamically updates their trust levels optimizes both energy efficiency and detection accuracy [23]. An SVM was also used to classify users based on energy values. The model demonstrates asymptotic optimality and is effective even in scenarios with a high number of malicious users [24].
The evidence theory is also used by applying Dempster-Shafer to assign trust weights to node reports. This approach reduces the impact of malicious nodes in cognitive sensor networks [25]. A similar approach uses an exclusion scheme that calculates each node’s cumulative suspicion level based on the Hamming distance from other nodes over multiple observation rounds. Nodes with consistently high suspicion levels are excluded from the decision-making process [26].
The Attack-Aware CSS (ACSS) approach was implemented by estimating the attack strength and optimizing the k parameter in the k-out-of-N rule to minimize Bayesian risk. This technique improves decision-making in the presence of collaborative SSDF attacks [27]. A similar model addresses constrained SSDF attacks by using an architecture that differentiates between interactive and non-interactive users. They employ interaction-based detection and semi-supervised SSFCM clustering to enhance robustness [28].
Another approach uses Q-learning and DBSCAN clustering to improve SSDF defense in Flying Ad Hoc Networks (FANETs). Each node acts as an autonomous agent, performing local data fusion and using sliding-window-based reputation mechanisms [29]. Finally, a method based on K-medoids clustering is used to detect and isolate SSDF attackers without requiring predefined thresholds. The algorithm operates on streaming data, enabling real-time detection [30].
Recent studies have explored the use of deep learning models based on RSS to improve detection performance in wireless communication systems. In particular, the work in [31] proposed a deep learning and image super-resolution–guided beam and power allocation scheme for millimeter-wave (mmWave) networks. By leveraging RSS measurements and advanced neural network architectures, this approach efficiently learns complex channel characteristics, enabling accurate beamforming decisions and improved resource allocation under dynamic channel conditions. Similarly, Ref. [32] presented a deep learning–based low-overhead beam selection framework that utilizes RSS information to reduce training complexity while maintaining high detection accuracy. Both studies demonstrate the capability of deep neural networks (DNNs) to capture intricate non-linear relationships in RSS data, which can significantly enhance the performance of signal detection and decision-making tasks in wireless environments.
3. CSS SSDF MCRN
The proposed model starts with a fast energy detector that allows the system to release a frequency channel while the SSDF is detected, to protect the PU. Each SU sends two variable values to the FC: the signal-to-noise ratio (SNR) and the received power in dBm.
The proposed detection framework operates as a classification model within a supervised learning paradigm. Specifically, the SVM is employed to separate secondary users into two categories—honest or malicious—based on labeled training data that includes features such as SNR and received energy. Similarly, the KNN algorithm functions as an instance-based supervised classifier, assigning each new sensing report to the appropriate class by comparing it with previously labeled samples in the feature space.
To improve the probability of detection (Pd), an SVM is trained and implemented in the FC. In the MCRN, the SU can move dynamically, like the PU, but the FC is fixed in a position. All the SU data is transmitted to the FC, making the MCRN work in a cooperative spectrum sensing scheme (CSS). Thanks to this, the FC can detect the spectrum environment efficiently, mitigating the effect of the hidden node problem.
The SVM model is trained with PU values in the environment with different SNR values and positions. After this, SVM can detect the presence of the PU in normal conditions.
In the presence of an SSDF attack, the energy detection module and the SVM classifier jointly identify the presence of a primary user. The system promptly releases the occupied frequency channel to protect the licensed transmission and prevent interference, but does not recognize the attack. To improve this method, a reputation-based detection along with a KNN detector can detect the SSDF attack, decreasing the probability of false alarm (PFA).
In the first part of the model, the learning process, the algorithms are trained with a database created with the SU in the environment, and data is transmitted to the FC. The FC uses a reputation module and a machine learning module to learn about the environment, SNR, and received power, as can be seen in Figure 1.
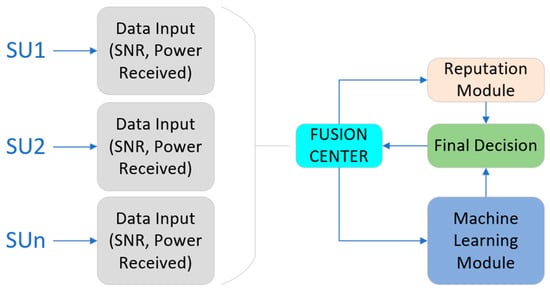
Figure 1.
General Detection Model for the training process (source: own).
In the second part of the process, the fusion center starts to recognize the SSDF attacks based on the previous results of the training process and the new data obtained from the SUs. The reputation module dynamically adapts the results according to the latest data and gives a weight to each SU. Based on the two modules, an SU can be classified as an SSDF attacker, and its information starts to be irrelevant to the final decision. The final decision is transmitted to all SUs present in the environment, and weights are updated, as can be seen in Figure 2.
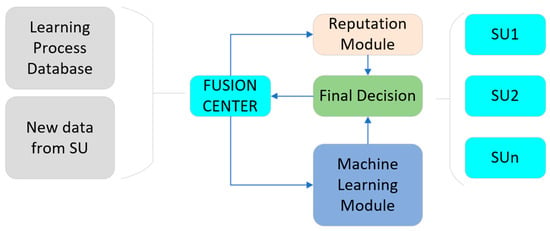
Figure 2.
Detection Model for SSDF attack (source: own).
The attack and each part of the process will be described below.
3.1. SSDF Attack
In SSDF attacks, the MUs deliberately send false sensing reports to the FC during cooperative spectrum sensing, aiming to [33]
- Mislead the global decision on spectrum occupancy.
- Cause interference with the Primary User (PU).
- Gain selfish access to the spectrum.
- Disrupt network performance (e.g., Denial of Service).
These attacks exploit the openness and trust-based nature of MCRNs, where FC assumes participating nodes are cooperative and honest. The SSDF types are [33]
- Always Yes (AP): Always reports PU is present (1), causing false alarms.
- Always No (AA): Always reports PU is absent (0), risking interference with PU.
- Always Opposite (AO): Malicious users falsify their sensing with the opposite sense results.
3.2. Energy Detection
For the energy detection, there is a local detection and a global decision taken in the FC. In the local sensing, each SU performs an energy detection test over a sensing window of N samples. The hypotheses are
- H0: PU is not present and is represented as noise. H1: There is a PU in the selected frequency. The main variables are [34].
- yi(t): Received signal at the i-th SU.
- hi: Channel gain between PU and SU.
- s(t): PU signal.
- : AWGN.
Based on this information, each SU calculates the test statistic, and it is represented in (2):
Each SU i makes a local decision comparing its test statistic Yi to a threshold λi, where yi is the sample of the received signal at the i-th SU, and is represented in (3):
In a CSS detection, a global decision is made using a majority rule. In this proposal, each SU energy and SNR values are transmitted to the FC, which makes a global decision combining the results with the ML techniques.
3.3. Reputation Detection
The Beta Reputation System (BRS) is a probabilistic framework for evaluating the trustworthiness of users based on their historical behavior. In CSS, SUs share sensing reports with FC. If MU sends false reports, it can lead to wrong global decisions. A Beta-based system maintains a reputation score for each SU based on how often their sensing reports agree with the final FC decision [34].
Let
- r: number of correct reports (positive feedback)
- s: number of incorrect reports (negative feedback)
The Beta distribution is shown in (4):
where
- α = r + 1.
- β = s + 1.
- p: probability that the user is trustworthy.
- Γ(·): Gamma function.
The expected value (i.e., reputation score) is represented in (5):
This score R ∈ [0, 1] reflects the user’s reliability:
- R → 1: Highly trustworthy
- R → 0: Highly untrustworthy
After each sensing round,
Compare SU’s local decision di(t) with FC’s global decision u0(t).
If matched, ri ← ri + 1
If not matched, si ← si + 1
If not matched, si ← si + 1
Thus,
Then, the weighted decision fusion u0(t) at the Fusion Center (FC) is represented in (7):
where K is the total number of reporting users.
- di(t) is the local decision.
- Ri(t) is the reputation score.
θ is the global decision threshold. It can be set as a fraction of the total reputation weight. For a weighted majority, it can be represented in (8).
3.4. SVM Detection
SVM is trained with historical feature vectors xi labeled as {honest, malicious}. The SVM decision function can be represented as (9)
where
- K(·,·): kernel function (e.g., RBF).
- yj ∈ {−1, +1}: label.
- αj: Lagrange multipliers.
- b: bias.
The Honest SU is (label = +1), and the Malicious SU is (label = −1). The vector of features is the same as that used in (10).
- xj: Feature vector of the j-th training sample.
- yj ∈ {−1, +1}: Class label of the j-th training sample (+1 = honest, −1 = malicious).
The SVM functions as a robust supervised learning algorithm that constructs an optimal decision boundary to distinguish between honest and malicious secondary users. By utilizing labeled training data that include key features such as SNR and received energy, the SVM determines a hyperplane that maximizes the margin between the two classes, thereby improving the reliability of malicious user detection even under noisy or dynamic channel conditions.
3.5. KNN Detection
KNN is a non-parametric, instance-based, supervised learning algorithm for classification. In CRNs, KNN is used to classify SUs as honest or malicious based on their historical behavior patterns [35].
Each SU data point is represented as a feature vector (10):
where features include
- Δdi(t) = ∣di(t) − FC decision∣. The absolute deviation of the SU’s local decision from the global FC decision.
- Pd(i), Pf(i): empirical detection/false alarm probabilities.
Reputation score Ri.
KNN computes the distance between this SU and all known SUs using a metric (11):
where xj is the feature vector of the j-th training sample, the KNN detection model assigns the class most common among the k-neighbors in a majority vote [30].
The distance between the feature vector of the i-th SU and the j-th training sample is computed to identify the k-nearest neighbors used for classification. Specifically, xil represents the value of the i-th feature (for example, SNR, received energy, or reputation score) of the i-th SU’s current sensing report. At the same time, yjl denotes the value of the same i-th feature in the j-th labeled training sample. The index i ∈ {1, 2, …, l} corresponds to the total number of features l considered in the model, and i and j identify the test and training instances, respectively.
The KNN method operates as an instance-based classifier that evaluates the similarity of new sensing reports to stored labeled samples. By considering the majority class of the k closest neighbors in the feature space, KNN captures complex, non-linear decision boundaries and adapts effectively to real-time variations in the network environment. Together, these algorithms provide a robust dual-layer classification mechanism that enhances detection accuracy and supports the dynamic nature of mobile cognitive radio networks.
4. Experiments
This chapter presents the experimental setup and methodology used to evaluate the proposed model for the SSDF attack detection system in an MCRN environment. The experiment integrates low-cost SDR hardware, real-time phone call traffic, and machine learning algorithms for the learning and detection of SSDF attacks, acquired in Bogota, Colombia.
The core hardware components for our testbed are as follows:
- RTL-SDR 2832U (https://www.rtl-sdr.com/): Low-cost USB software-defined radio dongle used to capture and measure spectrum energy.
- NI USRP-2922 (National Instrument (Austin, TX, USA)): High-performance SDR used to emulate MCRN base station behavior, including frequency hopping.
- GNU Radio v3.10.12.0 (https://www.gnuradio.org/): Used to control USRP devices and define baseband signal processing blocks.
- OpenBTS 5.1.0: Software stack that emulates a real cellular network, enabling real phone call generation.
- Midrange smartphones (Samsung (https://www.samsung.com/)): Used to simulate legitimate mobile communication over the MCRN.
- PC (Ubuntu) (HP): Central controller for signal processing, ML algorithm training, and data fusion.
The entire experimental testbed is illustrated in Figure 3.
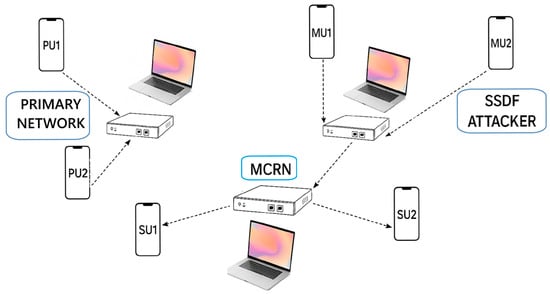
Figure 3.
Testbed for SDR experiments (source: own).
In this testbed, the MCRN uses an RTL-SDR to scan the frequencies in the selected range and connects the SUs to empty frequencies. The MCRN-USRP serves as the FC, while the Primary Network USRP connects the PUs, and the SSDF-USRP generates the SSDF with the MUs. The functions of devices are
- The RTL-SDR made the energy measurement and raw IQ data collection.
- The NI USRP-2922 (MCRN) acts as an MCRN base station with GNURadio.
- The NI USRP-2922 (Primary Network) acts as base station with GNURadio.
- The NI USRP-2922 (SSDF Attacker) simulates an SSDF attack transmitting false SU signals with Mus connected to MCRN.
- Smartphones generate real traffic for energy analysis.
- The PC with Ubuntu controls the base station, implements ML models, and fuses results.
4.1. Learning Process Overview
The experiment is divided into learning and classification phases. For the learning process, the system records and labels data under two conditions: with an active SSDF attacker and without an SSDF attacker.
The model collects
- Energy: Averaged over time from RTL-SDR.
- SNR: Estimated using signal peak-to-noise ratio.
These features are extracted using real-time voice communication traffic from phone calls.
4.2. Classification and Detection Process
After the learning phase, the system uses the trained classifiers to detect potential SSDF attacks in the environment.
For each signal segment received,
- Extract the feature vector.
- Feed into ML models: SVM, KNN, and Reputation Logic.
- Perform classification and flag attack presence (1 = Attack, 0 = No attack).
- Combine results in FC.
- Transmit results to all SUs.
While the learning phase is performed once, the dataset is continuously updated with new labeled samples.
5. Results
In this section, the numerical results are presented for the proposed hybrid model for SSDF detection.
The detection phase uses the trained classifiers and dynamically updated reputation scores to assess the trustworthiness of new sensing reports. Each new SU report is processed to extract its feature vector, which is evaluated by both ML models. The system then combines these evaluations with the current reputation score to determine the presence of malicious behavior. A final decision is generated at the FC, which broadcasts the result and updates each SU’s reputation. The following algorithm outlines this two-phase process.
The process begins with a learning phase where the system captures features such as SNR and received energy from multiple SUs under both normal and adversarial conditions. These data points are used to train SVM and KNN classifiers. Simultaneously, a reputation score is assigned to each SU based on the alignment of its sensing reports with the final decision made by the FC.
5.1. General Learning and Detection Process
The following algorithm summarizes the detection process.
- Initialization: Define feature set (SNR, received energy), and set initial reputation scores.
- Learning Phase:
- a.
- Collect labeled data with and without SSDF attackers.
- b.
- Train SVM and KNN classifiers with extracted features.
- c.
- Update reputation scores based on agreement with FC decisions.
- Detection Phase:
- a.
- For each new sensing report, extract the feature vector.
- b.
- Classify report using trained SVM and KNN models.
- c.
- Combine results with current reputation score.
- d.
- Make final decision and update SU reputation.
- e.
- Broadcast final decision to all SUs.
The detection process is illustrated in Figure 4.
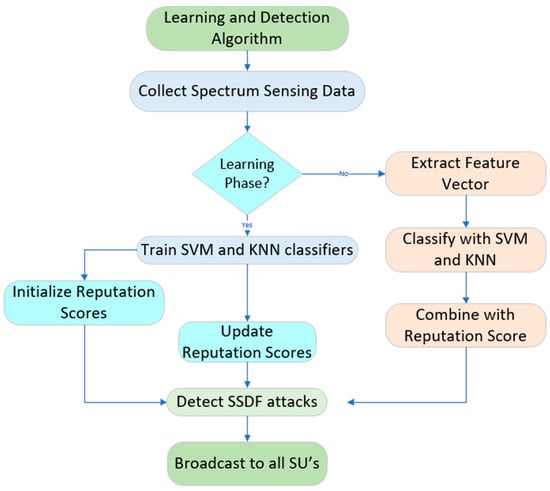
Figure 4.
Learning and Detection Process Flowchart (source: own).
The model input is the data from several distances and SNR values around the environment taken by the SUs. This data is associated with a variable that records whether there is an SDDF attack or not, and sends it to the FC for the model decision.
5.2. Experimental Results
The proposed system was evaluated under two conditions: with and without active SSDF attackers. The following performance metrics were measured:
- Detection Accuracy: The combined model measures the detection probabilities of SVM/KNN classifiers.
- False Alarm Rate: Measure the misclassifications of honest secondary users.
The experimental testbed was composed of SDR devices, including RTL-SDR and USRP-2922 platforms, real smartphone traffic, and GNU Radio processing.
Once the system is trained, the energy and SNR are the input vectors. The weighted fusion strategy, which combines machine learning output with dynamically updated trust scores in a CSS model, improved final decision reliability and attacker exclusion.
For the experimental evaluation of the MCRN, signal measurements were conducted within the 850 MHz frequency band. An RTL-SDR device was employed to capture the incoming radio signals. Energy detection was performed by aggregating every 100 individual signal samples into a single energy estimate. To ensure statistical robustness and enable reliable training of the machine learning models, a dataset comprising 10,000 aggregated samples, including the (attack/no attack) state, was collected across a diverse range of SNR conditions. There are three SUs and 1 MU in the radio environment.
5.2.1. SVM Algorithm Results
The SVM-based classification was implemented by structuring the input dataset into a data frame format. A linear kernel was selected within the C-classification mode, as prior analysis indicated that the data distribution supports linear separability. The model converged with the support vectors, reflecting an efficient boundary definition between the classes, and can be seen in Figure 5. This figure illustrates the results of the SVM classifier trained to distinguish the PU under an SSDF attack in an MCRN environment. The classifier uses two features: SNR on the x-axis and received energy (in dBm) on the y-axis. The colored background represents the classifier’s decision regions, while the red and green points indicate the training data for PU-present and No PU samples, respectively.
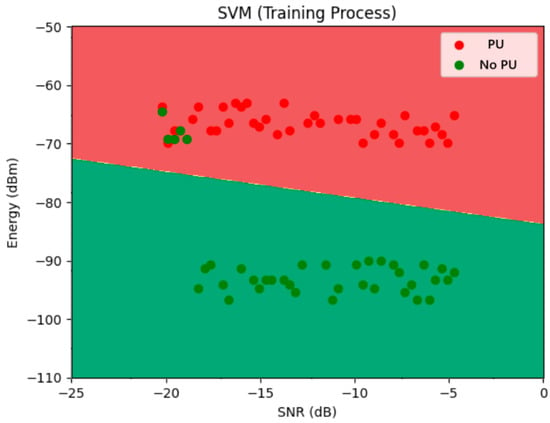
Figure 5.
SVM Results for SSDF Detection (source: own).
The SVM model in this case employs a linear kernel, as evidenced by the straight decision boundary separating the two classes. This line represents the optimal hyperplane that maximizes the margin between the closest points (support vectors) of each class. The red region above the boundary corresponds to the classifier predicting PU presence, while the green region below predicts no PU. The boundary effectively captures the overall trend: PU signals are generally observed at higher energy levels, even at low SNR values, while no PU samples remain in the lower energy zone.
It shows a detection above 96% of a PU under an SSDF attack. According to the SNR and received energy, the model can recognize a truth value in these terms.
5.2.2. KNN Algorithm Results
The classification results of a KNN model trained to distinguish between the presence and absence of a PU under an SSDF attack are based on energy measurements and SNR values. The x-axis represents the SNR in dB, ranging from −25 dB to 0 dB, while the y-axis shows the energy level in dBm, ranging from −110 dBm to −50 dBm. Each dot corresponds to a sample from the training dataset, colored by its class: red for samples where the PU is present and green where the PU is absent in the environment under an SSDF attack. This can be seen in Figure 6.
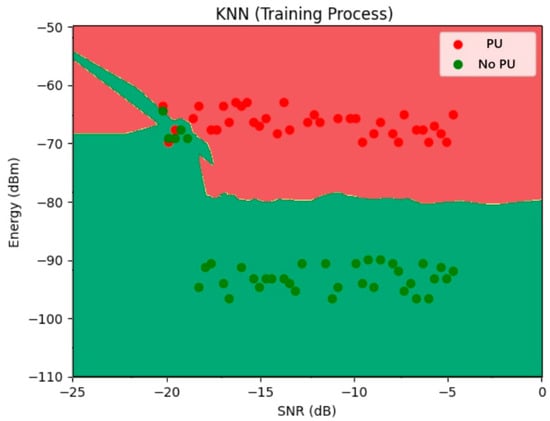
Figure 6.
KNN Results for SSDF Detection (source: own).
The non-linear and irregular boundaries between these regions highlight one of KNN’s strengths—its ability to capture complex class distributions without assuming any prior statistical model. This flexibility allows KNN to adapt to real-world noise and nonlinear relationships that commonly occur in spectrum sensing environments. It shows a detection above 88% of a PU under an SSDF attack.
The results demonstrate that KNN performs well in separating the classes based on local decision boundaries shaped by nearby labeled data, which is particularly useful in online or dynamic environments, and if it is combined within the FC, detection results are higher.
5.2.3. Reputation Algorithm Results
The SVM-based classification was implemented by structuring the input dataset into a data frame format. A linear kernel was selected within the C-classification mode, as prior analysis indicated that the data distribution supports linear separability. The model converged with the support vectors, reflecting an efficient boundary definition between the classes.
The simulation parameters of the reputation algorithm are
- Number of SUs: 20
- PUE attackers (malicious SUs): 6 (30%)
- Sensing rounds: 100
- Honest users match the FC decision with probability 0.9.
- Malicious users match FC decision with probability 0.3 (OR-type SSDF).
- Update rule (12):
The evolution of average reputation scores for honest and malicious SUs over a series of 100 sensing rounds can be seen in Figure 7. The reputation is calculated using the Beta distribution’s expected value formula, where ri and si represent the number of matches and mismatches with the FC global decision. The green curve, representing honest users, shows a consistent increase, stabilizing near a reputation score of 0.95, which reflects high reliability over time. In contrast, the red curve, representing malicious users, shows a gradual decline, ending below 0.3. This apparent divergence confirms the effectiveness of the Beta reputation system in distinguishing between trustworthy and malicious users based on their long-term sensing behavior, enabling the FC to dynamically filter out attackers in later stages of the decision-making process.
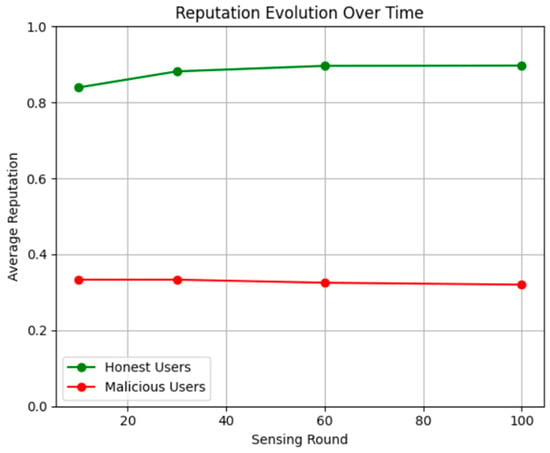
Figure 7.
Reputation over sensing rounds (source: own).
The impact of the SSDF attack detection system’s reputation system, with and without the Beta reputation filter, is illustrated in Figure 8. Three key performance metrics are shown: detection accuracy, false positive rate, and false negative rate. Without reputation filtering, the detection accuracy is 83.5%, with relatively high false positive (14.1%) and false negative (18.3%) rates. After applying the Beta reputation model to filter low-trust users, detection accuracy rises sharply to 94.2%, while false positive and false negative rates drop to 5.6% and 6.4%, respectively. These results demonstrate that incorporating Beta-based trust evaluation into the system significantly improves the reliability of cooperative sensing by minimizing the impact of SSDF attackers on the global decision.
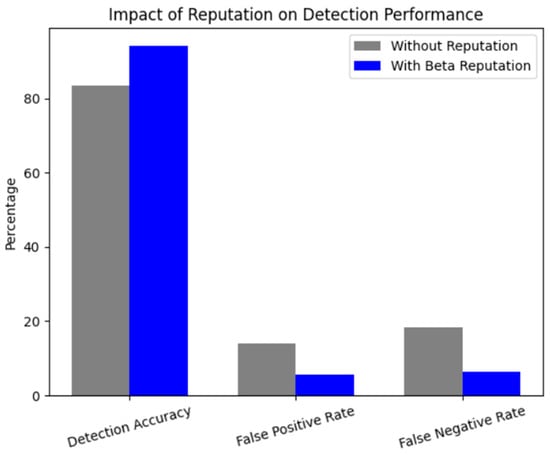
Figure 8.
Impact of Reputation on Detection Performance (source: own).
5.2.4. Hybrid Algorithm Results
The section shows the evaluation of the performance of a hybrid detection framework that integrates
- SVM for decision boundary classification.
- KNN for behavior-based anomaly detection.
- Beta reputation system for long-term trust assessment.
This demonstrates how these techniques, when combined, improve the detection of malicious SUs attempting to launch an SSDF attack. The simulation parameters for the Hybrid model are
- Number of SUs: 30.
- Malicious SUs: 9 (30%).
- Total sensing rounds: 100.
- Input features per SU:
- ○
- Energy (in dBm)
- ○
- SNR (in dB)
- ○
- Beta reputation score (dynamically updated)
Malicious users report falsely in 70% of cases; honest users report truthfully in 90% of cases. In the simulations of the Hybrid algorithms, we obtain the results of Figure 9.
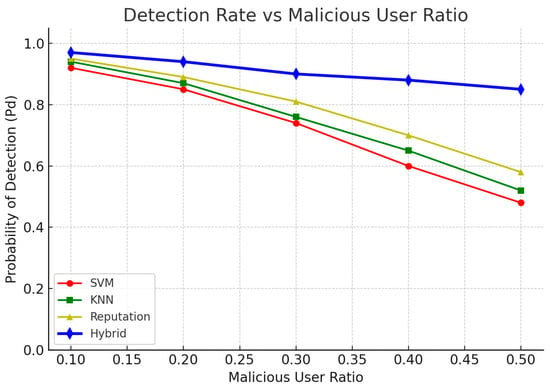
Figure 9.
Hybrid Detection Rate vs. Malicious User Ratio (source: own).
This figure presents the impact of increasing the malicious user ratio on the detection rate (Pd) for four different detection methods.
The x-axis represents the proportion of SUs that are acting maliciously (i.e., sending falsified sensing reports), ranging from 10% to 50% of the network. The y-axis represents the detection rate—the probability that the system correctly identifies the presence of a PU despite the presence of attackers.
All methods experience a decline in detection rate as the number of malicious users increases. This decline is expected, as more attackers make it increasingly difficult for the system to distinguish between true and false sensing reports. However, the rate of decline and overall performance vary significantly between models.
The combined Hybrid solution (SVM + KNN + Reputation) clearly outperforms all others, maintaining a high detection rate (>0.88) even with 50% malicious users. This result demonstrates the value of combining short-term classification (SVM, KNN) with long-term trust modeling.
The performance in SDR devices of four SSDF attack detection methods as a function of SNR with a malicious user ratio of 0.25 (1 MU and 3 SU) is shown in Figure 10. The horizontal axis shows SNR values ranging from −25 dB to 0 dB, simulating increasingly favorable communication conditions for SUs detecting PU activity. The vertical axis shows the Pd, showing that the detection system correctly identifies the presence of the PU. It performs under varying noise and interference levels.
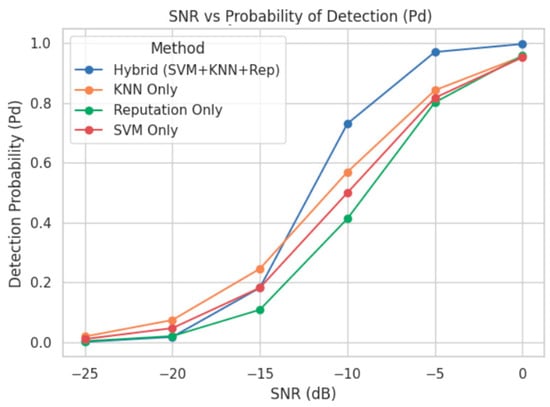
Figure 10.
Probability of detection vs. SNR (source: own).
It shows that detection performance improves with increasing SNR. Among the methods, the Hybrid model consistently achieves the highest detection probability across SNR values. It outperforms individual model results under challenging low-SNR conditions, such as −15 dB and −10 dB, showing the ability to cross-validate user behavior using both real-time classifiers (SVM, KNN) and long-term reputation scores. These results reinforce the value of hybrid frameworks in dynamic environments where signal quality is variable and attackers may exploit low-SNR conditions to evade detection.
6. Discussion
The proposed hybrid detection framework combining SVM, KNN, and reputation-based mechanisms demonstrates a robust and adaptive approach to mitigating SSDF attacks in MCRNs. The integration of machine learning classifiers and trust evaluation facilitates a multi-layered assessment of secondary users (SUs), enhancing detection reliability and minimizing the impact of malicious behavior.
The experimental results from the SDR-based testbed show that each method contributes uniquely to the overall system performance. The SVM model, benefiting from its ability to establish a linear boundary between classes, provided high detection accuracy above 96%. The KNN classifier, leveraging instance-based decision-making, reached over 88% accuracy, highlighting its effectiveness in recognizing subtle similarities across user reports. More importantly, the reputation mechanism allowed the system to adapt over time by identifying consistent malicious behavior and dynamically penalizing untrustworthy SUs.
A key finding is that while each method has individual strengths, their combination offers a higher performance compared to standalone detection strategies. The reputation module effectively filters unreliable nodes, reducing false positives and enhancing classifier outputs. The hybrid model not only improved detection accuracy to 94.2% at −5 dB but also significantly reduced false alarm and false negative rates, thus ensuring more stable and secure cooperative spectrum sensing.
Additionally, the model’s adaptability to varying SNR levels and SU mobility makes it suitable for real-world MCRNs. Its reliance on energy and SNR features ensures low-complexity implementation without compromising detection quality. Overall, the system demonstrates resilience, accuracy, and practicality for dynamic wireless environments.
The proposed hybrid detection framework, which combines SVM, KNN, and a reputation-based mechanism, leverages the strengths of both short-term feature-based classification and long-term behavioral analysis. The SVM provides a linear decision boundary with high detection accuracy (above 96% in experiments). At the same time, KNN captures non-linear patterns in the data, making it effective in dynamic environments with variable SNRs. The reputation module further strengthens the system by continuously updating trust scores for each SU, enabling the dynamic exclusion of malicious users even as attack strategies evolve. This multi-layered approach ensures a high probability of detection (>90%) and low false alarm rates while maintaining adaptability to real-world conditions such as SU mobility and fluctuating SNR levels.
The hybrid design requires the training and maintenance of multiple machine learning models, which can introduce computational overhead during the learning phase and increase resource consumption, particularly in networks with a large number of users or rapidly changing conditions. The reputation mechanism improves long-term resilience; it relies on the availability of sufficient sensing rounds to accurately estimate trust scores, which may delay detection in fast-changing environments or when new users join the network.
Collusion among malicious SUs can reduce the diversity of sensing reports and artificially reinforce false decisions, thereby increasing the difficulty of detection compared to independent attackers. Our hybrid model mitigates some of these challenges through the reputation-based weighting mechanism, which gradually penalizes nodes whose reports consistently diverge from the fusion center’s global decision. Even when colluding attackers share similar falsified reports, long-term discrepancies with the actual channel state reduce their reputation scores over multiple sensing rounds, limiting their influence on the final decision. However, if a sufficiently large coalition of attackers dominates the reporting set, they could temporarily skew the global decision before the reputation system has collected enough evidence to isolate them.
As future work, the integration of RSS-based DNN models with the current hybrid SVM–KNN–reputation approach will be explored. A possible enhancement would be to use a DNN to pre-process RSS and other physical-layer features, providing richer input vectors for the SVM and KNN classifiers or serving as an additional detection layer. Such a multi-stage system could exploit the superior feature extraction capabilities of DNNs while retaining the interpretability and low-complexity benefits of the existing hybrid framework. This combination is expected to further improve the probability of SSDF attack detection, particularly in highly dynamic MCRN environments where user mobility and channel variability create complex data patterns.
7. Conclusions
This study presents a comprehensive hybrid model for detecting SSDF attacks in MCRN. By combining SVM, KNN, and a reputation-based scoring mechanism, the model successfully identifies and isolates malicious SU. Experimental validation on a software-defined radio platform confirms that the system achieves high accuracy and adaptability under realistic wireless conditions.
The proposed approach enhances the robustness of cooperative spectrum sensing, addressing both the technical challenges posed by dynamic node mobility and the strategic threat of coordinated SSDF attacks. The integration of trust mechanisms into the machine learning workflow enables long-term performance improvements through continuous reputation updates. This framework meets the critical requirements of MCRNs by balancing computational efficiency and detection performance, making it well-suited for real-world deployment in energy and resource-constrained wireless networks.
The results show that the proposed model outperforms individual methods above −13 dB, and at −10 dB it achieves an improvement in detection of nearly 20%. The hybrid model mitigates the weaknesses of individual techniques by cross-verifying decisions and leveraging user reputation, which enhances robustness in adversarial environments. The findings also confirm that as attacker coordination increases, systems relying solely on stateless classifiers such as SVM or KNN become less effective, highlighting the need for trust-aware hybrid frameworks in real-world cognitive radio networks.
Experimental validation using SDR testbeds confirmed the model’s practical applicability and high accuracy in dynamic environments, achieving detection probabilities above 90% even under low SNR conditions. The hybrid approach proved significantly more effective than standalone models, particularly in environments with a high proportion of malicious users. The system maintained reliable detection performance even when up to 50% of users were acting maliciously.
Author Contributions
The methodology, software, and hardware proposed in this paper have been conceived by L.M.Y.C. and E.C.M.; experiment design, E.C.M., L.M.Y.C. and R.C.S.; performed the experiments, L.M.Y.C., E.C.M. and R.C.S.; Results analysis, review, and edited the paper, L.M.Y.C., E.C.M. and R.C.S. All authors participated in the discussion and proofreading work. All authors have read and agreed to the published version of the manuscript.
Funding
This research and the APC were funded by Universidad Santo Tomas, Proyecto FODEIN 2024. Universidad Distrital Francisco José de Caldas provided the devices.
Data Availability Statement
The original contributions presented in the study are included in the article; further inquiries can be directed to the corresponding authors.
Acknowledgments
We thank Universidad Santo Tomas for funding this project and the APC. And to Universidad Distrital Francisco José de Caldas for the provided resources.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| AI | Artificial Intelligence |
| AO | Always Opposite |
| AP | Always Yes |
| AA | Always No |
| BRS | Beta Reputation System |
| CSS | Cooperative Spectrum Sensing |
| CRN | Cognitive Radio Network |
| dBm | Decibel-milliwatts |
| DNN | Deep Neural Network |
| FANET | Flying Ad Hoc Network |
| FC | Fusion Center |
| GNU | GNU’s Not Unix |
| IQ | In-phase and Quadrature |
| IoT | Internet of Things |
| KNN | K-Nearest Neighbors |
| ML | Machine Learning |
| MCRN | Mobile Cognitive Radio Network |
| MU | Malicious User |
| PU | Primary User |
| Pd | Probability of Detection |
| PFA | Probability of False Alarm |
| SDR | Software Defined Radio |
| SNR | Signal-to-Noise Ratio |
| SSDF | Spectrum Sensing Data Falsification |
| SU | Secondary User |
| SVM | Support Vector Machine |
| USRP | Universal Software Radio Peripheral |
References
- Solanki, S.; Dehalwar, V.; Choudhary, J. Deep learning for spectrum sensing in cognitive radio. Symmetry 2021, 13, 147. [Google Scholar] [CrossRef]
- Manoranjan, G.; Chandan, M.; Karthik, G.; Satpathy, R.; Sugumaran, S. Security against ssdf attacks using novel attack mitigation mechanism for cognitive radio networks. In Proceedings of the 2021 Fourth International Conference on Electrical, Computer and Communication Technologies (ICECCT), Coimbatore, India, 15–17 September 2021; pp. 1–6. [Google Scholar]
- Paul, A.; Mishra, A.K.; Shreevastava, S.; Tiwari, A.K. Deep reinforcement learning based reliable spectrum sensing under SSDF attacks in cognitive radio networks. J. Netw. Comput. Appl. 2022, 205, 103454. [Google Scholar] [CrossRef]
- Muzaffar, M.U.; Sharqi, R. A review of spectrum sensing in modern cognitive radio networks. Telecommun. Syst. 2024, 85, 347–363. [Google Scholar] [CrossRef]
- Chen, S.; Shen, B.; Wang, X.; Yoo, S.-J. Geo-location information aided spectrum sensing in cellular cognitive radio networks. Sensors 2019, 20, 213. [Google Scholar] [CrossRef] [PubMed]
- Keshavamurthy, B.; Michelusi, N. Learning-based spectrum sensing and access in cognitive radios via approximate POMDPs. IEEE Trans. Cogn. Commun. Netw. 2021, 8, 514–528. [Google Scholar] [CrossRef]
- Liu, Y.; Shaikh, A.H.; Khoso, W.M. Impact of Spectrum Sensing Data Falsification Attack and Imperfect Reporting Channel on Cooperative Spectrum Sensing. In Proceedings of the 2023 9th International Conference on Computer and Communications (ICCC), Chengdu, China, 8–11 December 2023; pp. 470–474. [Google Scholar]
- Sarmah, R.; Taggu, A.; Marchang, N. Detecting Byzantine attack in cognitive radio networks using machine learning. Wirel. Netw. 2020, 26, 5939–5950. [Google Scholar] [CrossRef]
- Banerjee, S.; Singh, T.; Singh, K.R. Mitigation of spectrum sensing data falsification attack (ssdf) in cognitive radio network. J. Inst. Eng. India Ser. B 2022, 103, 1249–1257. [Google Scholar] [CrossRef]
- Wan, R.; Ding, L.; Xiong, N.; Zhou, X. Mitigation strategy against spectrum-sensing data falsification attack in cognitive radio sensor networks. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719870645. [Google Scholar] [CrossRef]
- Ahmadfard, A.; Jamshidi, A.; Keshavarz-Haddad, A. Probabilistic spectrum sensing data falsification attack in cognitive radio networks. Signal Process. 2017, 137, 1–9. [Google Scholar] [CrossRef]
- Chatterjee, S.; Chatterjee, P.S. A comparison based clustering algorithm to counter SSDF attack in CWSN. In Proceedings of the 2015 International Conference on Computational Intelligence and Networks, Odisha, India, 12–13 January 2015; pp. 194–195. [Google Scholar]
- Zhi, X.; Cao, Y.; Liu, X. Anti-Dynamic SSDF Attack Scheme Based on Credit Mechanism. In Proceedings of the 2024 4th International Conference on Electronic Information Engineering and Computer (EIECT), Shenzhen, China, 15–17 November 2024; pp. 875–879. [Google Scholar]
- Kumar, R.; Parmar, A.; Captain, K.; Patel, J. Reinforcement learning for performance improvement in cooperative spectrum sensing. Phys. Commun. 2023, 59, 102112. [Google Scholar] [CrossRef]
- Antoinette, A.; Buvaneswari, S. Security and Energy Management in Cooperative Spectrum Sensing. Procedia Comput. Sci. 2023, 230, 716–724. [Google Scholar] [CrossRef]
- Rachakonda, L.P.; Siddula, M.; Sathya, V. A comprehensive study on IoT privacy and security challenges with focus on spectrum sharing in Next-Generation networks (5G/6G/beyond). High-Confid. Comput. 2024, 4, 100220. [Google Scholar] [CrossRef]
- Liu, M.; Liu, L.; Xu, D.; Zhang, L. Cognitive IoT Collusion SSDF Attack Detection Based on FP-Growth Algorithm. J. Netw. Syst. Manag. 2025, 33, 25. [Google Scholar] [CrossRef]
- Feng, J.; Zhang, M.; Xiao, Y.; Yue, H. Securing cooperative spectrum sensing against collusive SSDF attack using XOR distance analysis in cognitive radio networks. Sensors 2018, 18, 370. [Google Scholar] [CrossRef] [PubMed]
- Zardosht, F.; Derakhtian, M.; Jamshidi, A.; Eshaghi, H. Recognition and elimination of SSDF attackers in cognitive radio networks. Telecommun. Syst. 2022, 81, 53–66. [Google Scholar] [CrossRef]
- Peng, T.; Chen, Y.; Xiao, J.; Zheng, Y.; Yang, J. Improved soft fusion-based cooperative spectrum sensing defense against SSDF attacks. In Proceedings of the 2016 International Conference on Computer, Information and Telecommunication Systems (CITS), Kunming, China, 6–8 July 2016; pp. 1–5. [Google Scholar]
- Li, L.; Li, F.; Zhu, J. A method to defense against cooperative SSDF attacks in Cognitive Radio Networks. In Proceedings of the 2013 IEEE International Conference on Signal Processing, Communication and Computing (ICSPCC 2013), Kunming, China, 5–8 August 2013; pp. 1–6. [Google Scholar]
- Chatterjee, P.S. Systematic survey on SSDF attack and detection mechanism in cognitive wireless sensor network. In Proceedings of the 2021 International Conference on Intelligent Technologies (CONIT), Karnataka, India, 25–27 June 2021; pp. 1–5. [Google Scholar]
- Fu, Y.; He, Z. An online learning approach for cooperator selection in CSS under SSDF attack. IEEE Commun. Lett. 2022, 26, 1479–1483. [Google Scholar] [CrossRef]
- Reddy, A.A.; Gandlapalli, V.S.A.; Sai, K.V.; Battula, R.B. Secure spectrum sensing in CRNs: A study on SSDF attacks and countermeasure using USRP. In Proceedings of the 2024 15th International Conference on Computing Communication and Networking Technologies (ICCCNT), Mandi, India, 18–22 June 2024; pp. 1–5. [Google Scholar]
- Yao, D.; Yuan, S.; Lv, Z.; Wan, D.; Mao, W. An enhanced cooperative spectrum sensing scheme against SSDF attack based on Dempster-Shafer evidence theory for cognitive wireless sensor networks. IEEE Access 2020, 8, 175881–175890. [Google Scholar] [CrossRef]
- Liu, S.; Liu, Q.; Gao, J.; Guan, J. Attacker-exclusion scheme for cooperative spectrum sensing against SSDF attacks based on accumulated suspicious level. In Proceedings of the 2011 IEEE International Conference on Cyber Technology in Automation, Control, and Intelligent Systems, Kunming, China, 20–23 March 2011; pp. 239–243. [Google Scholar]
- Sharifi, A.A.; Niya, M.J.M. Defense against SSDF attack in cognitive radio networks: Attack-aware collaborative spectrum sensing approach. IEEE Commun. Lett. 2015, 20, 93–96. [Google Scholar] [CrossRef]
- Cheng, Z.; Zhang, J.; Song, T.; Hu, J.; Bao, X. Detection strategy against restricted SSDF attack with potential interaction assistance. IEEE Trans. Cogn. Commun. Netw. 2020, 7, 553–566. [Google Scholar] [CrossRef]
- Wu, X.; Tang, Z.; Lu, Y.; Wu, D.; Xiao, H.; Tang, Y. Cooperative spectrum sensing method against spectrum sensing data falsification attack. In Proceedings of the 2023 24st Asia-Pacific Network Operations and Management Symposium (APNOMS), Sejong, Republic of Korea, 6–8 September 2023; pp. 66–70. [Google Scholar]
- Nath, S.; Marchang, N.; Taggu, A. Mitigating SSDF attack using K-Medoids clustering in cognitive radio networks. In Proceedings of the 2015 IEEE 11th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Abu Dhabi, United Arab Emirates, 19–21 October 2015; pp. 275–282. [Google Scholar]
- Cao, Y.; Ohtsuki, T.; Maghsudi, S.; Quek, T.Q. Deep learning and image super-resolution-guided beam and power allocation for mmWave networks. IEEE Trans. Veh. Technol. 2023, 72, 15080–15085. [Google Scholar] [CrossRef]
- Echigo, H.; Cao, Y.; Bouazizi, M.; Ohtsuki, T. A deep learning-based low overhead beam selection in mmWave communications. IEEE Trans. Veh. Technol. 2021, 70, 682–691. [Google Scholar] [CrossRef]
- Ye, F.; Zhang, X.; Li, Y. Comprehensive reputation-based security mechanism against dynamic SSDF attack in cognitive radio networks. Symmetry 2016, 8, 147. [Google Scholar] [CrossRef]
- Bai, P.; Zhang, X.; Ye, F. Reputation-based Beta reputation system against SSDF attack in cognitive radio networks. In Proceedings of the 2017 Progress in Electromagnetics Research Symposium-Fall (PIERS-FALL), Singapore, 19–22 November 2017; pp. 792–799. [Google Scholar]
- Musuvathi, A.S.S.; Archbald, J.F.; Velmurugan, T.; Sumathi, D.; Renuga Devi, S.; Preetha, K. Efficient improvement of energy detection technique in cognitive radio networks using K-nearest neighbour (KNN) algorithm. EURASIP J. Wirel. Commun. Netw. 2024, 2024, 10. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).