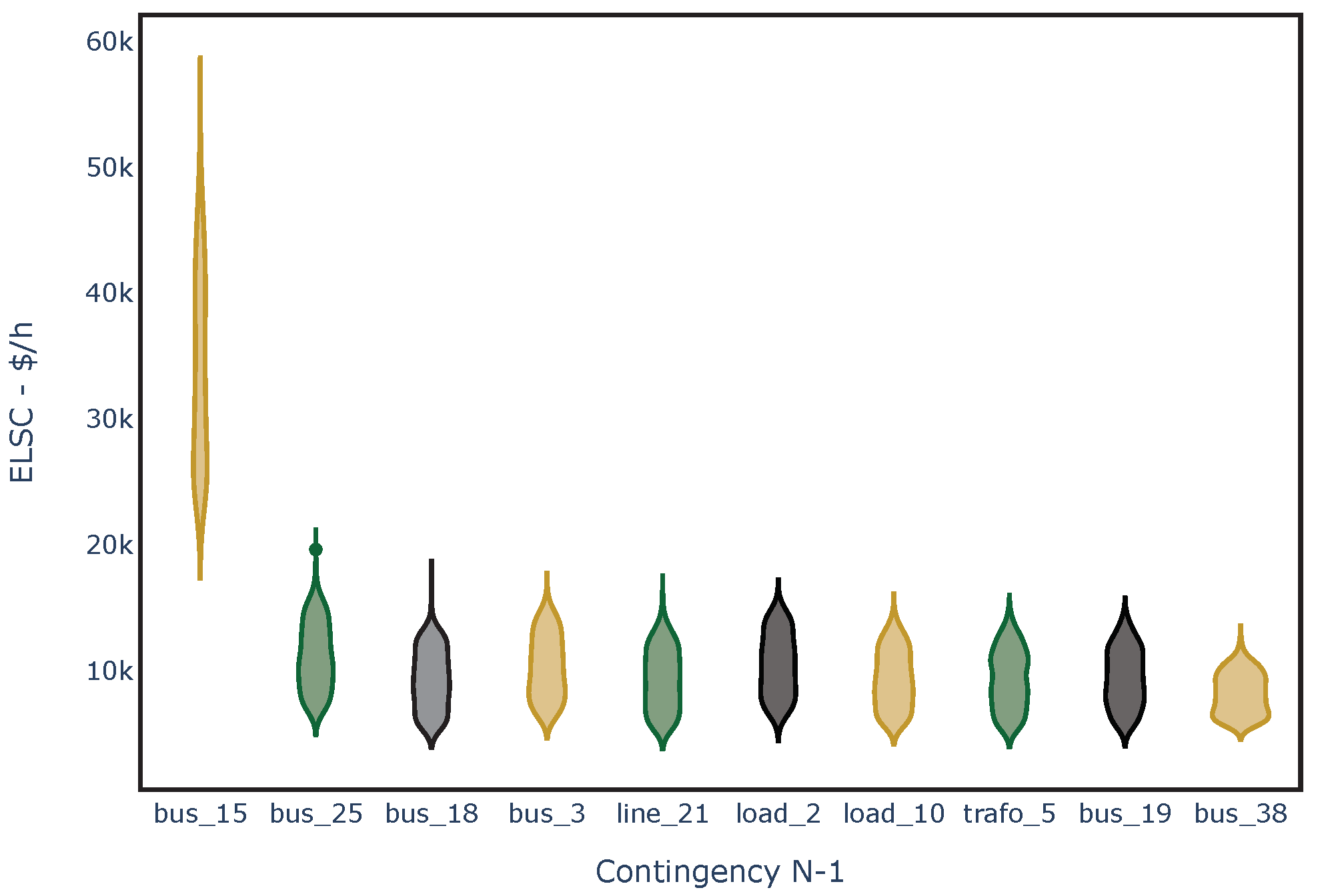Abstract
This paper presents a methodology for static security assessment of transmission network planning using machine learning (ML). The objective is to accelerate the probabilistic risk assessment of the Hydro-Quebec (HQ) TransÉnergie transmission grid. The model takes the expected power supply and the status of the elements in a contingency scenario as inputs. The output is the reliability metric Expecting Load Shedding Cost (). To train and test the regression model, stochastic data are performed, resulting in a set of and contingency scenarios used as inputs. Subsequently, the output is computed for each scenario by performing load shedding using an optimal power flow algorithm, with the objective function of minimizing . Experimental results on the well-known IEEE-39 bus test system and PEGASE-1354 system demonstrate the potential of the proposed methodology in generalizing during an contingency. For up to the coefficient of determination obtained was close to 98% for both case studies, achieving a speed-up of over four orders of magnitude with the use of a Multilayer Perceptron (). This approach and its results have not been addressed in the literature, making this methodology a contribution to the state of the art.
1. Introduction
Modern Power Systems (PSs) seek to supply energy with certain economic, sustainable, reliable and secure levels. According to Singh et al. [1], security studies usually focus on generation, transmission, protection, distribution, interconnection and, industrial and commercial systems. Power transmission systems are widely regarded as the backbone of PS and their security assessment determines the system’s capacity to supply uninterrupted power from generation to the demand in a secure manner [2]. Nevertheless, performing power transmission planning of large networks to guarantee reliability is a challenging task if multiple scenarios and a high penetration of renewable power sources are considered, primarily due to the size and complexity of modern grids.
Lumbreras et al. [3] proposed a methodology to simplify large networks for expansion planning considering a set of scenarios for minimizing investments, operation costs and penalties for non-served power. The cost and penalties are computed using DC power flow. The control actions such as load shedding or generator response, as well as reactive power and voltages issues, are not considered. The definition of critical branches is labeled in a deterministic way.
Ideally, security assessment analysis should be performed under criterion, where N is a set of equipment and k the number of disconnected elements simultaneously during a contingency. If corrective actions are required the well-known Security Constrain Optimal Power Flow (SCOPF) algorithm is usually employed [4] as extension of the Optimal Power Flow algorithm (OPF). SCOPF takes into account operational constraints for a set of contingencies while minimizing impact of the contingency. However, this problem is a nonlinear, non-convex, mixed variable and large scale, being their solution a changeling task and time consuming. Therefore, different approximations, methods and assumptions such as , DC power flows, contingency screening [5] and high-performance computing [6], among others, are used to solve SCOPF in a reasonable time. More advanced methods suggest quantum computation to deal with the computational complexity of the contingency analysis problem [7]. However, with the existing quantum computation technology, their application is not possible.
Nowadays, PSs are operating in more stressed conditions, because both the demand and the generation are increasing while the capacity of the transmission system is reaching their limits. This condition, along with the penetration of renewable generation, increases the uncertainty in the planning being necessary to refine the security assessment. Probabilistic risk assessment for [8,9] has emerged as an option to face this challenge; however, this method is time demand. Recently, the use of Machine Learning (ML) to generalize security assessment seeking increased computational speed [10] has gained popularity.
Table 1 presents a literature review of recent proposed methods for reliability assessment, where ENS, AC, AI, PF, and Plan. are energy not supplied, alternating current power flow, artificial intelligence, power flow, and planning application, respectively. In the table, the following characteristics of each method are identified: numerical analysis model, objective function, consideration of contingencies and if was developed for system planning. The main differences between models used for operation or operation planning and system planning involves the consideration of unit comment, generation costs, and generator ramp for the first one, while for system planning, the impact on the demand as last remedial action is commonly the main issue to evaluate.

Table 1.
Methodologies for security constraint assessment proposed in the literature.
In recent years, Hydro-Quebec (HQ) has been developing a global methodology for Risk-Informed decision making [22]. That methodology integrates a power grid reliability simulator to estimate the Value of Lost Load () when a contingency occurs. However, conducting this assessment for the HQ’s entire transmission network is a time-demanding task, because the AC-SCOPF algorithm is required to minimize for a set of contingency scenarios. Implementing the simulator with the entire set of equipment poses a bottleneck. According to Table 1, a comparable model to address this challenge is currently unavailable in the existing literature. Moreover, there is a need for accelerating the method for large power networks. To meet this challenge, we present in this paper a reliability security assessment using ML, focusing on the static operation [2] of PS. Our objective is to accelerate the evaluation of contingencies to support decision making processes within an asset management framework. Our approach incorporates constraints such as the voltage limits of buses, generator capabilities and the thermal limits of branches. The objective function is the minimization of when disturbances occur under different operating scenarios.
The main contributions addressed in this paper are as follows:
- We propose a ML methodology for generalizing for different time scopes and scenarios, allowing to reduce the computational cost;
- We describe the procedure to fit the ML model executing for multiple contingency scenarios;
- We present a real-size case study base on European Union transmission system PEGASE-1354 case to evaluate the performance in the generalization of for large networks. Our approach achieves high accuracy compared to traditional AC-OPF formulations.
This paper is structured as follows: a comprehensive review of ML for PF, OPF, SCOPF is presented in Section 2. Our proposed methodology for generalization of LS-OPF under scenarios using ML is addressed in Section 3. Section 4 presents the case studies where the application of the methodology is performed. Lastly, this paper is concluded in Section 5.
2. Related Work
ML for security assessment of power systems is a well-known application given its versatility to generalize complex phenomena [23]. For static security assessment, ML applications are related to reduce computational burden during contingency analysis, allowing to perform probabilistic risk assessment. Duchesne et al. [24] presents a complete review for ML for PS reliability management, addressing applications in the field of PF, OPF and SC-OPF.
2.1. Power Flow—PF
Donnot et al. [25] present a method to rank N-1 and N-2 contingencies using ANN. The ranking is performed using a probabilistic risk assessment that considers thermal limits of OHLs. Oliveira et al. [26] propose to assess power system operation security under multiple contingencies using decision tree (DT). The security criterion involves the computation of bus voltage through load flow simulation.
2.2. Optimal Power Flow—OPF
Zhang et al. [27] propose solving DCOPF using a convex neuronal network to guarantee its generalization. Recent efforts have focused on extending the use of ML to ACOPF problems considering the majority of constraints. Pan et al. [28] used ANN for solving ACOPF, considering the feasibility and optimality during generation of solutions. The objective function is to minimize the total cost of generation. The inputs are the active and reactive power of each load. The outputs are the voltage magnitude of the slack bus, the active power by generator, and the voltage magnitude of the PV-V buses. The feasibility in the solutions obtained was greater than 99%, with a speed-up of 123×. Jia et al. [29] propose a ML approach using Convolutional Neural Networks (CNN), where the load and network topology are labeled as inputs, and the state variables bus voltage magnitude and angle are labeled as outputs for training the ML model. A 350× speed-up with a prediction accuracy close to 100% was reached compared with Matpower for a 2000 bus system. At a distribution level, Liu and Wu [30] proposed a Reinforced Learning algorithm to minimize active power loss through voltage control, considering both voltage and reactive power constraints. A similar optimization problem is addressed by Liao et al. [31] using capsule networks. While these proposed methods exhibit high performance, their formulation is limited to distribution networks.
2.3. Security Constrained Optimal Power Flow—SCOPF
The use of ML for OPF has extended their variant SCOPF. Pan et al. [32] develop an approach for solving SC-DCOPF problems using DNN. The objective function is to minimize the generation cost. The inputs and outputs of the DNN are the power load and power generation, respectively. A 328× speed-up with a prediction error less than 0.1% was reached compared with the Gurobi solver for a 300 bus system. Zhou et al. [33] extend the OPF problem formulation to Load Shedding SCOPF (LS-SCOPF) using an AC model for emergency operations. The objective function consists only of cost of load reduction. The inputs and outputs were the PF data and load shedding, respectively. For the IEEE 14-bus systems, the errors obtained were between 8% and 98% for a single line outage.
Table 2 compares recent studies of application of ML for security assessment with the method addressed in this work. The column Bus is the system with maximum number of bus where the model was tested, limits describe the security criteria, where full denotes thermal, voltage and generators limits. The columns Method, Inputs, Outputs are the ML algorithm employed, the ML inputs and the ML outputs, respectively.

Table 2.
Summary of recent studies on machine learning to accelerate the solution of PF problems.
In this work, we generalize by ML the estimation of using as inputs the topology and the expected load to supply. As the scope of this approach is grid planning, the estimation the state variables are not required avoid post-processing or reconstruction of system, as required in [29,32]. Hence, according to Huang et al. [34], who present a review of recent progress in grid dispatch using deep learning, alongside the findings from the review [24] and Table 1 and Table 2, this paper introduces a novel method to accelerate static security assessment. The method achieves this by generalizing the to obtain the for multiple contingencies in large power networks with high accuracy.
3. Machine Learning Approach for LS-OPF
This section addressees the formulation of the Load Shedding Optimal Power Flow (LS-OPF) problem for load shedding under contingency. This formulation enables the generation of the raw data set used for training the ML model. Lastly, the background of the employed ML algorithm is provided.
3.1. Load Shedding Security Constrained Optimal Power Flow
In order to perform a static security assessment for power systems planning, a grid power flow model is necessary. The DC power flow model focuses on active power flow calculations, while the AC load flow (ACLF) model considers both active and reactive power flows. The evaluation of reactive capability of generation, the security voltage limits of buses and reactive compensation necessities the inclusion of reactive power flow.
The mathematical formulation of ACLF requires the specification of one or a set of reference buses . Typically, the phase angle of these reference buses is constraint to 0, as shown below:
To model the power flow in the set of branches , the Ohm’s Law is described by the following equations that must be satisfied:
where P and Q represent the active and reactive branch power flow, V the bus voltage and Y and refers to he -section parameters. Branches consist of transmission lines and power transformers. To ensure the active and reactive power equilibrium between load, losses and generation, the following equalities must be satisfied for each bus:
where and are the set of generators, loads, shunt and buses, respectively. denote active and reactive power generation, and active and reactive power demand. Finally, and are the conductance and susceptance of branch.
The PF model allows the assessment of the impact of a contingency on the secure operation of the system. Security violation encompass the limits the buses, branches and generators. Regarding buses, the voltage magnitude is bound by and as follows:
To prevent branch overloading, the following inequality constraints for the maximum allowable power flow must be satisfied for all power transformers and lines:
Lastly, the active and reactive power for generators are bounded by the following limits:
Since the objective in this approach is static security assessment during system planning, factors such as generator power ramps, unit comment and line switching are not considered in the aforementioned formulation.
In the event of security violations, remedial actions such as redispatch and/or load shedding become necessary. Therefore, to ensure secure system operation and minimize the impact of these remedial actions, an optimization problem must be formulated. The optimization problem takes the following general form:
where f and are the objective function and optimization variables , respectively. The optimization problem is subjected to equality (Equations (1)–(7)) and inequality (Equations (8)–(11)) constraints in order to guarantee power balance and secure operation. The objective function can take various forms, such as minimizing generation cost, maximizing market surplus, or minimizing expected load shedding cost , among others. In long term planning for PS, is commonly considered as a reliability index to minimize. The minimization of can be formulated as the maximization (negative minimization) of the value of the supply load. Hence, is calculated as the expected supply load cost in pre-contingency minus the supply load cost in post-contingency, as shown below:
Therefore, to consider load curtailment as remedial action, the objective function is formulated by minimizing the negative , as follows:
where P and c represent the supplied load and the unitary cost of the energy not supplied, respectively. If load shedding is not required, the will be zero, as indicated by Equations (13) and (14). Finally, if LS is assumed with a constant power factor, the load can be modeled as generator with negative power injection as shown below:
where r is the ratio where the index p denotes the pre-contingency value. In summary, each contingency is assessed by minimizing load shedding (LS-OPF) through the adjustment of generator and load capabilities to achieve an optimal and secure operating point.
3.2. ML Algorithm—ANN
The idea we proposed involves generalizing the relation between an contingency with . Hence, given a set of features , the target is to predict by a function f as follows:
where represents a set of parameters that fit the function f. The goal is to find the values of that minimize the loss function L for a set of known samples as illustrated below:
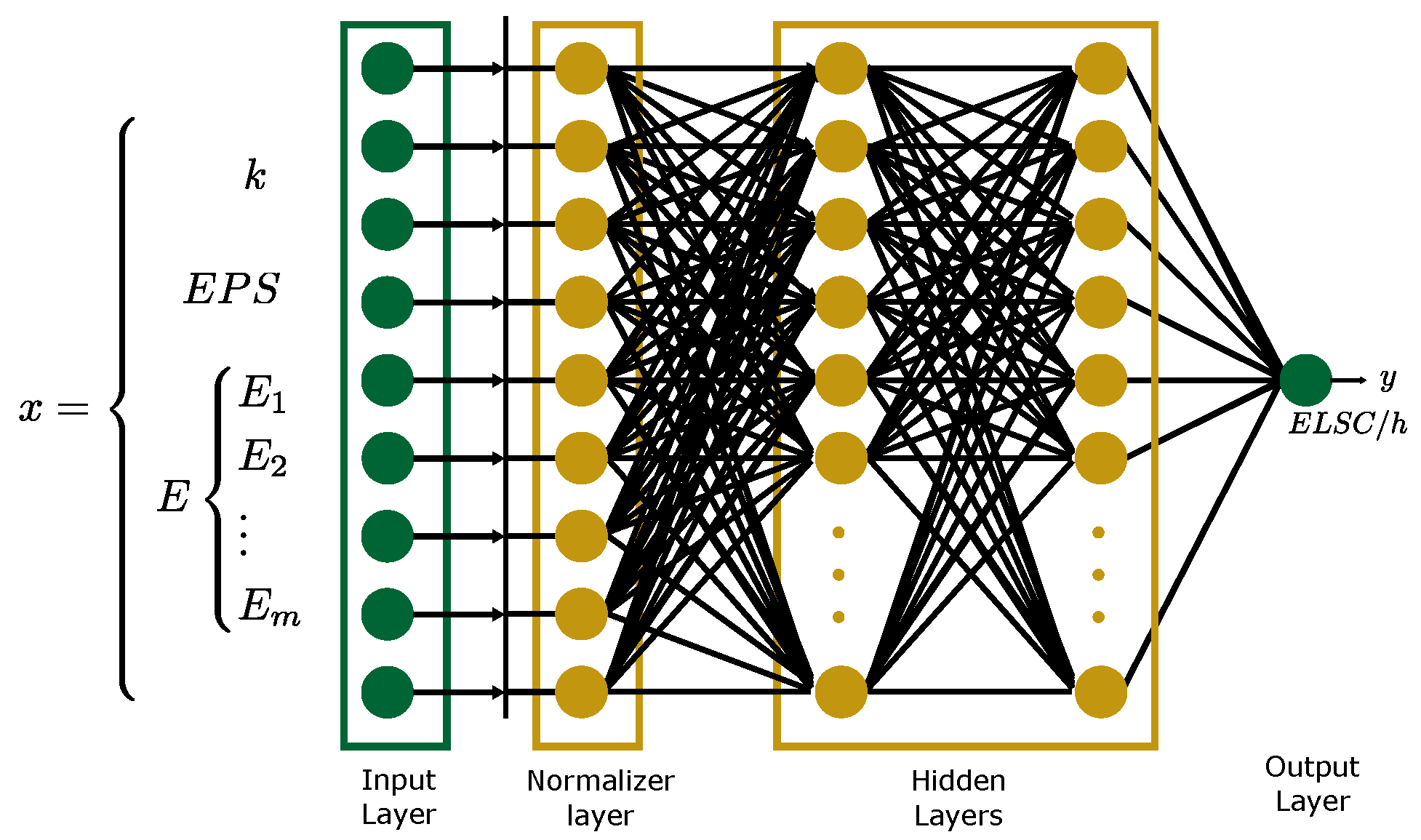
where and . The optimization problem in the form of Equation (18) can be solved using regression ML algorithms, with ANN widely adopted for its high performance [24]. For the prediction of with ML in this paper, the selected set of features are and , where and represent the expected power to supply and a binary value indicating if element i is connected, respectively. The training data set is obtained using the methodology addressed in Section 3.1 for multiple contingency scenarios. Figure 1 illustrates the generic architecture of an for the generalization of , where the number of inputs must be adjusted to each network.
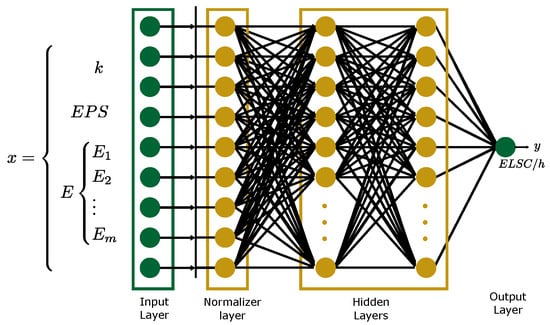
Figure 1.
Proposed ANN architecture for generalization of given an contingency.
4. Numerical Analysis
To assess the performance of the proposed approach, two case studies are evaluated by comparing the results obtained with the proposed method against the well-known interior point algorithm (IP) for an formulation. The results of the IP algorithm are considered as true values and are used for both fitting and evaluating the ML model.
4.1. Case Studies Description
The IEEE-39 bus and the PEGASE-1354 cases are used to demonstrate the practical applicability of the proposed ML model. The IEEE-39 case serves didactic purposes, providing a detailed illustration of the model’s performance, while the PEGASE-1354 model is employed to evaluate the ML performance in large power grids. The raw data for both networks was taken from matpower cases [35] and is summarized in Table 3.

Table 3.
Network data of the two case studies.
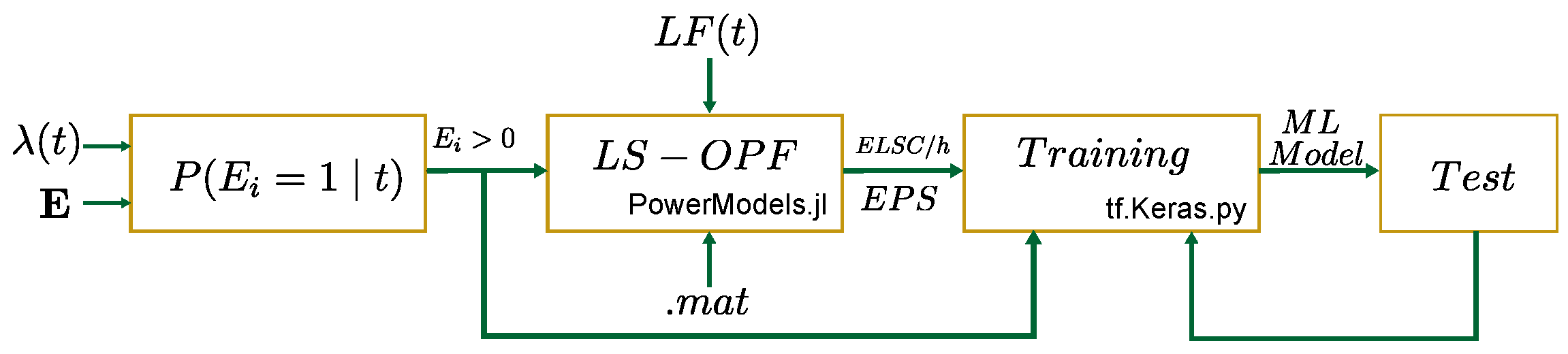
Figure 2 summarized the procedure employed to generate the raw data, train the ML and test the fit. A detailed explanation is presented in the following subsections.
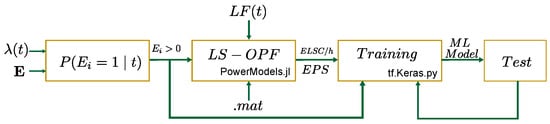
Figure 2.
Procedure used in case studies for estimation of using ML.
4.2. Raw Data
The set of contingencies was generated stochastically, assuming a failure rate failures/h (approx. 99.8% availability per year) for each element () over a one-year period, . Thus, the set of contingencies is selected from scenarios where a least one element fails . Table 4 shows the number of scenarios for each contingency used for training and testing in each case study. A total of and scenarios were used for IEEE-39 and PEGASE-1354, respectively. In the IEEE-39 bus system, m = 115 elements, including circuit breakers (CB) associated with loads, buses, generators, power transformers and lines were considered as equipment to fail. For the PEGASE-1354 network, equipment considered for failure included CBs of loads greater than 1 , generators, power transformers, and lines, totaling m = 2528 equipment. The selection of power limits in the chosen loads was made to enhance the robustness of the LS-OPF algorithm. Only synchronous machines are considered, as they currently constitute the majority in HQ’s transmission grid. However, Inverted-Based Resources will be addressed in future research.

Table 4.
Number of contingencies used to train the ANN.
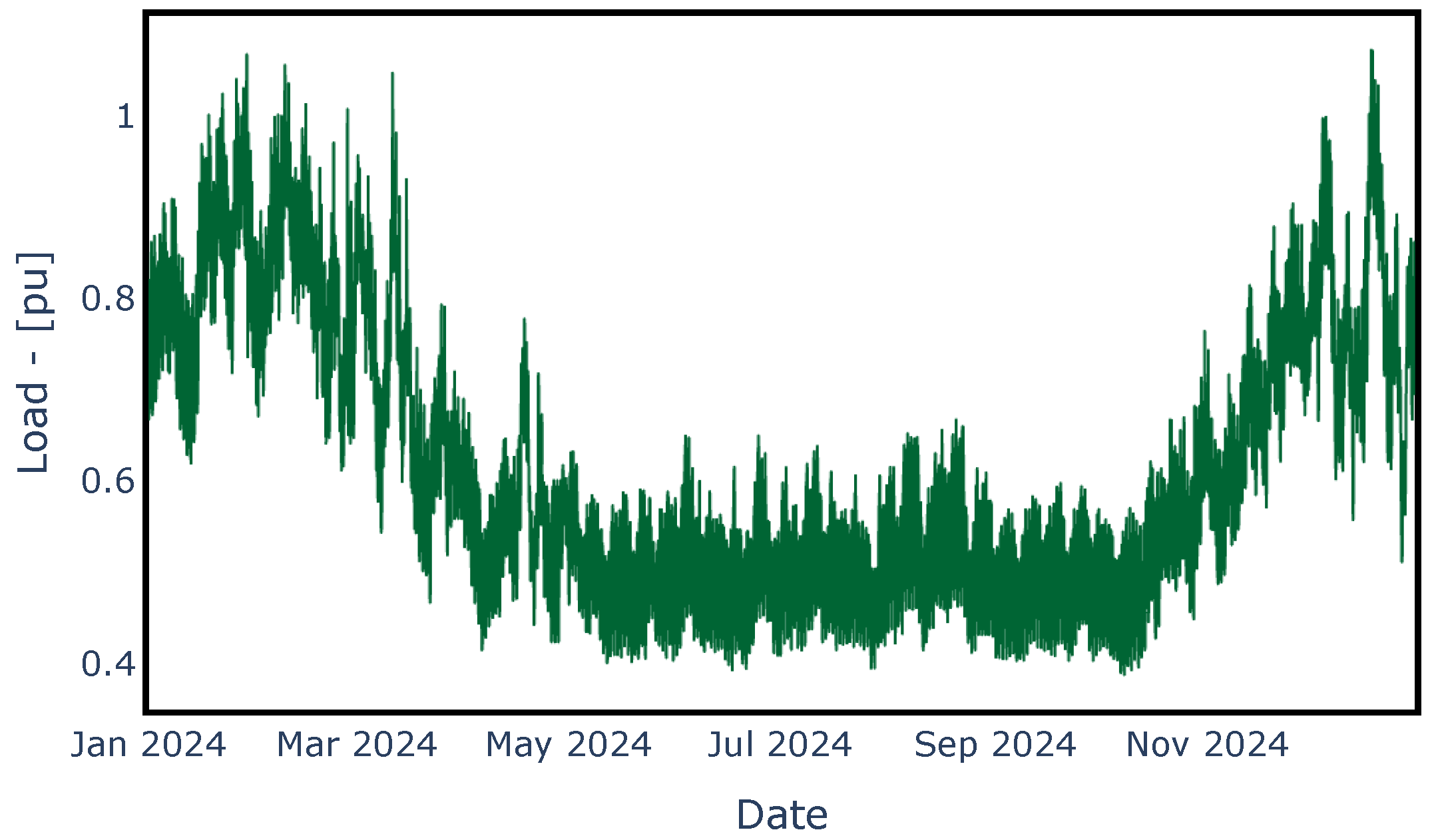
Before executing the LS-OPF algorithm, a load update is performed for each scenario, assuming the HQ’s demand pattern shown in Figure 3. This is performed to simulate the load changes over the course of 1 year. Lastly, LS-OPF was executed for each contingency scenario.
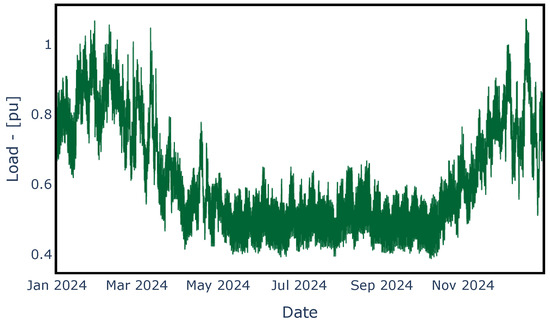
Figure 3.
HQ’s demand pattern used in the different contingency scenarios.
4.3. LS-OPF Using PowerModels.jl
The LS-OPF algorithm was implemented using the open-source platform PowerModels.jl [36]. The abstract model shows in Listing 1 was written in the Julia Programming Language to evaluate for each contingency scenario, based on the formulation addressed in Section 3.1. The load shedding model was implemented in the Julia function as shown Listing 2. The loads are treated as generators and are labeled as “Load”.
The LS-OPF problem was solved using the non-linear solver IPOPT [37], which was restricted to a maximum of 200 iterations and 150 for each scenario. As linear solver, the MA57 library was used with a tolerance of 1 × 10−6. The evaluation of the entire set of contingencies was performed using a 2.2 GHz Intel Core i5-9500T CPU with 16 GB of RAM. On average, each LS-OPF simulation took approx. in for the IEEE-39 case study and around 5 for the PEGASE-1354 case study.
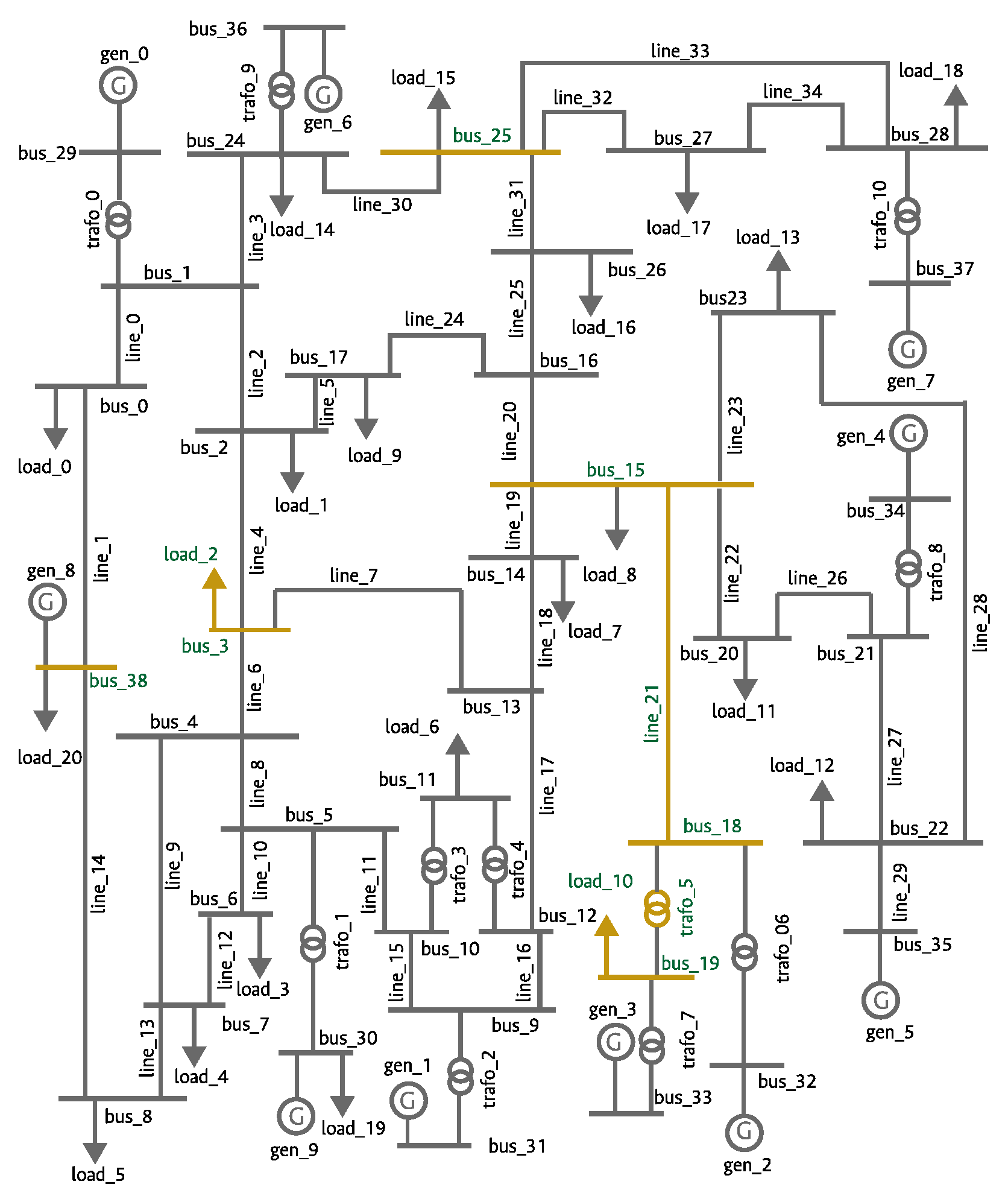
To verify the LS-OPF results and procedure, a visual assessment is performed. Figure 4 shows the distribution of contingencies with the highest . These results are further explained using Figure 5, where the top contingencies are highlighted. The disconnection of bus 15 leads to the isolation of a part of the network, including five loads and four generators. Since the simulation did not permit operation in islanding mode, bus 15 emerges as the most critical failure in the system.
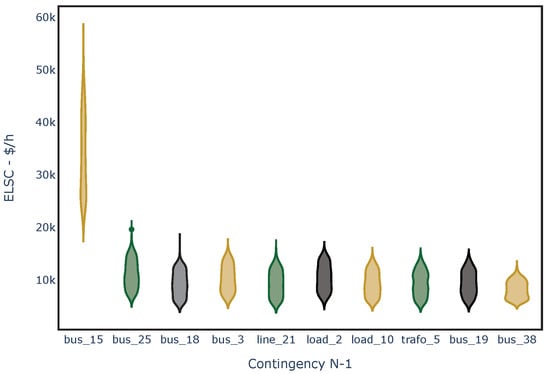
Figure 4.
Violin plot ranking of contingencies with the highest for the IEEE-39 bus system.
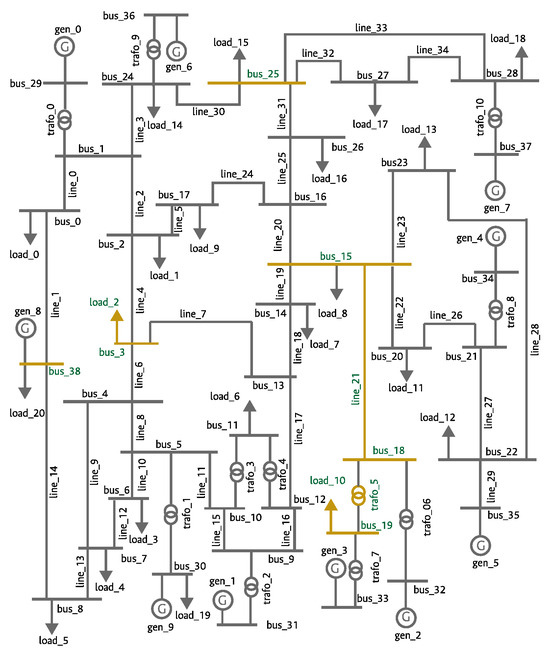
Figure 5.
Location of contingencies in the network with the highest for the IEEE-39 bus system.
| Listing 1. Implemented PowerModels Abstract LS-OPF Model. |
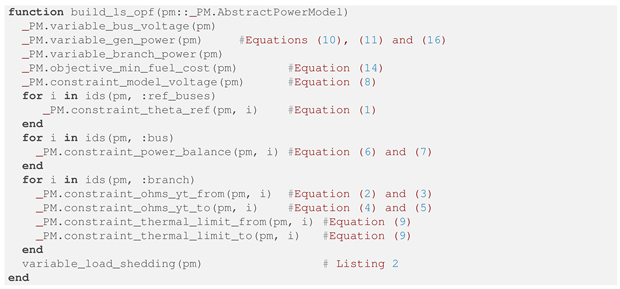 |
| Listing 2. Function implemented in PowerModels.jl for modeling load shedding. |
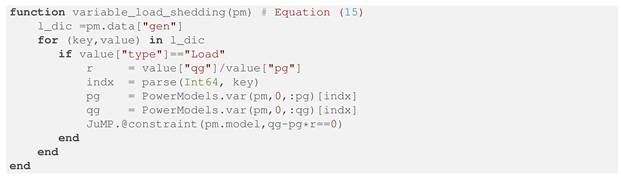 |
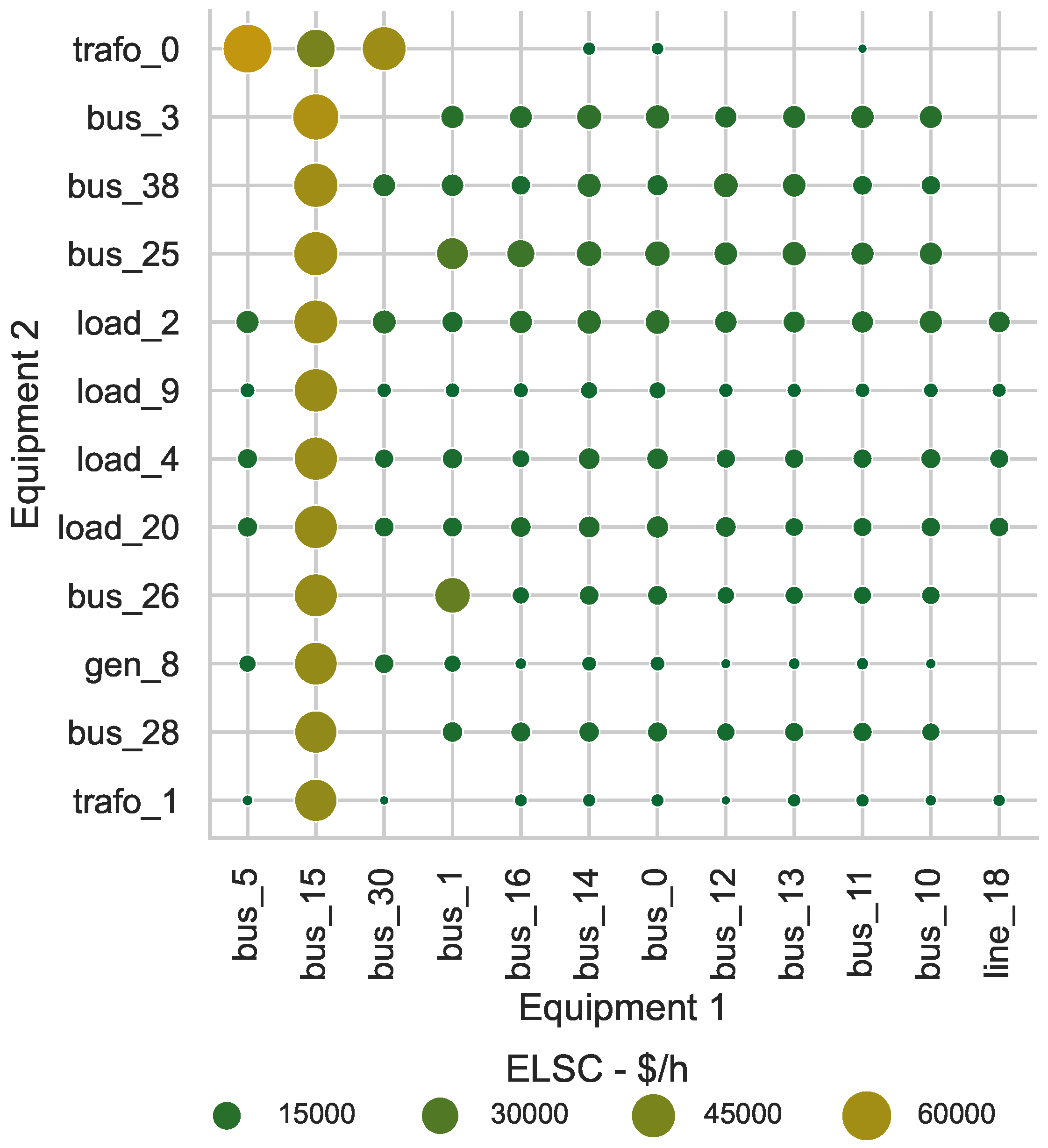
Figure 6 shows the top with contingencies, reaffirming that scenarios involving bus 15 have the highest , except for the situation when bus 16 and line 18 fail. As shown in Figure 5, a simultaneous failure of these two elements would have a similar impact as the disconnection of bus 15 with the disconnection of load 7.
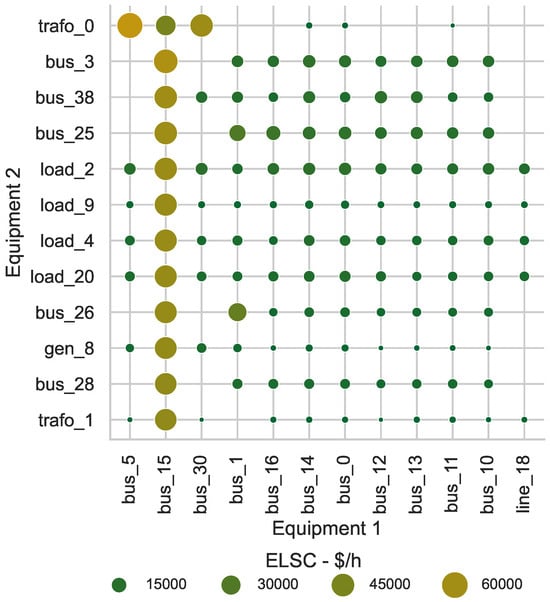
Figure 6.
contingencies with the highest for the IEEE-39 bus system.
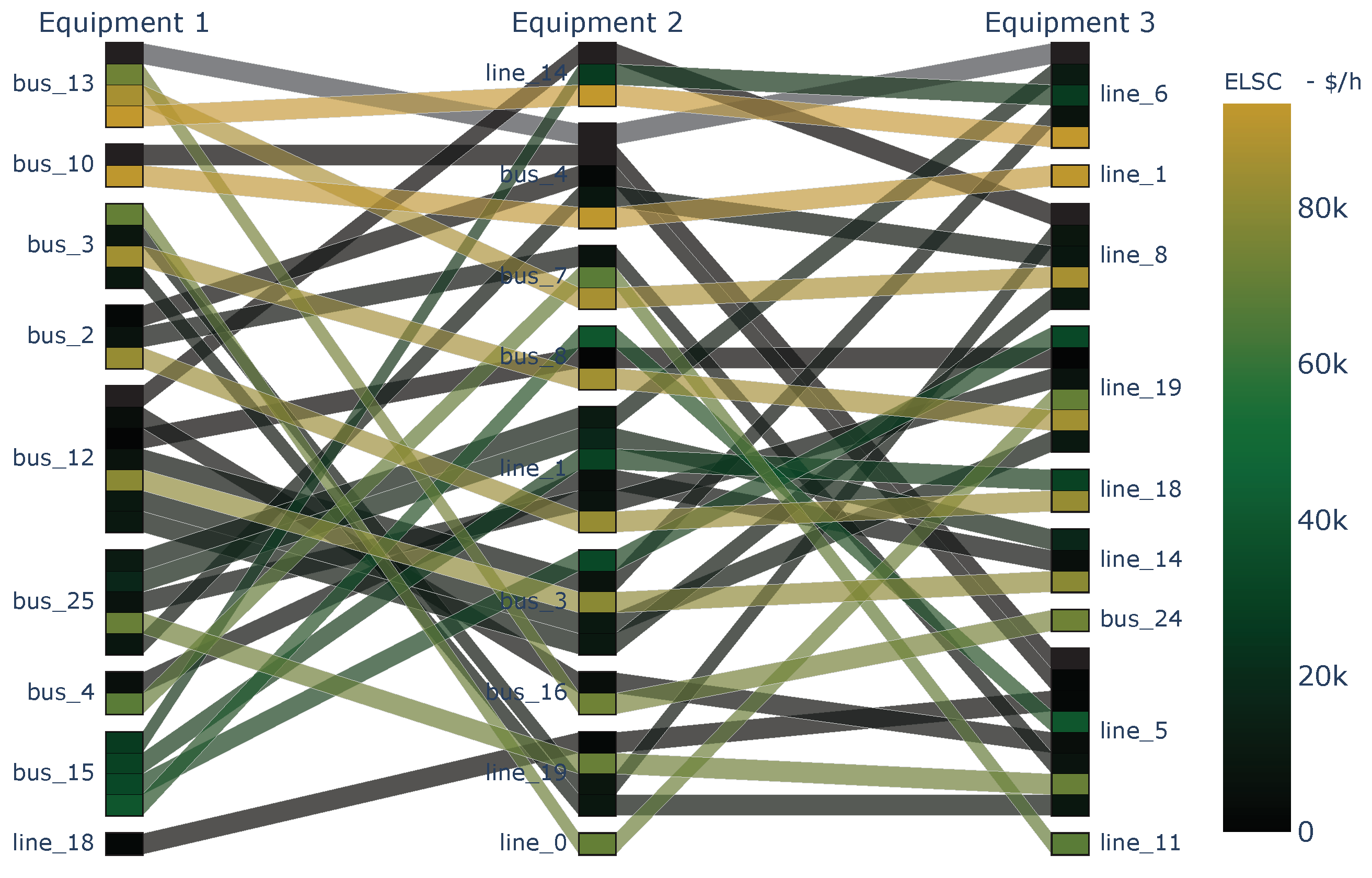
Lastly, Figure 7 shows the top N-3 contingencies, with those related to bus to bus 15 presenting the highest impacts. Based on the previous visual assessment, the results obtained during the raw data generation align with the expected outcomes.
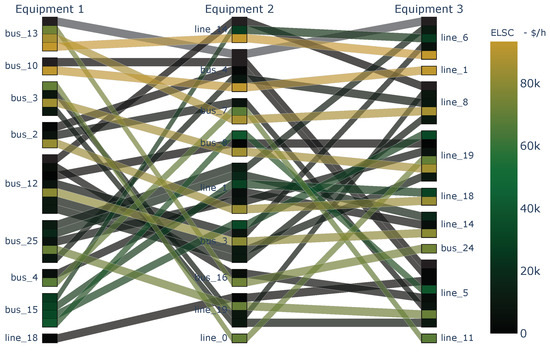
Figure 7.
contingencies with the highest for the IEEE-39 bus system.
4.4. ELSC Regression
The proposed ML algorithm, as illustrated in Figure 1, was implemented using the TensorFlow-Keras API in Python. The number of inputs is 117 for IEEE-39 and 2530 for PEGASE-1354, respectively. These quantities result from the number of equipment to fail, the consideration of contingency level (k), and the as inputs. The output was the . The optimization solver used was the ADAM algorithm, set with a learning rate of 1 × 10−4. For the loss function, the Mean Square Error was selected. Among the various architectures evaluated, an ANN with three hidden layers consisting of 400, 200 and 100 neurons, each using the Relu activation functions was chosen for both the IEEE-39 System and the PEGASE-1354 network. Additionally, a normalization layer was included to improve the model’s fit. To prevent negative values of , a Relu activation function was added to the output layer. Listing 3 provides the Python script with the implemented ANN architecture.
| Listing 3. TensorFlow-Keras ANN Model for STLF. |
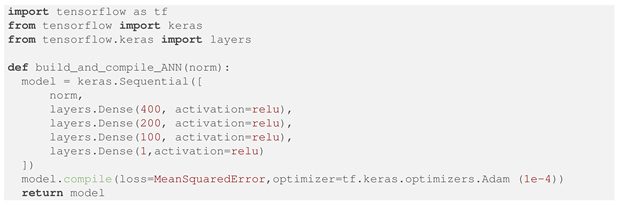 |
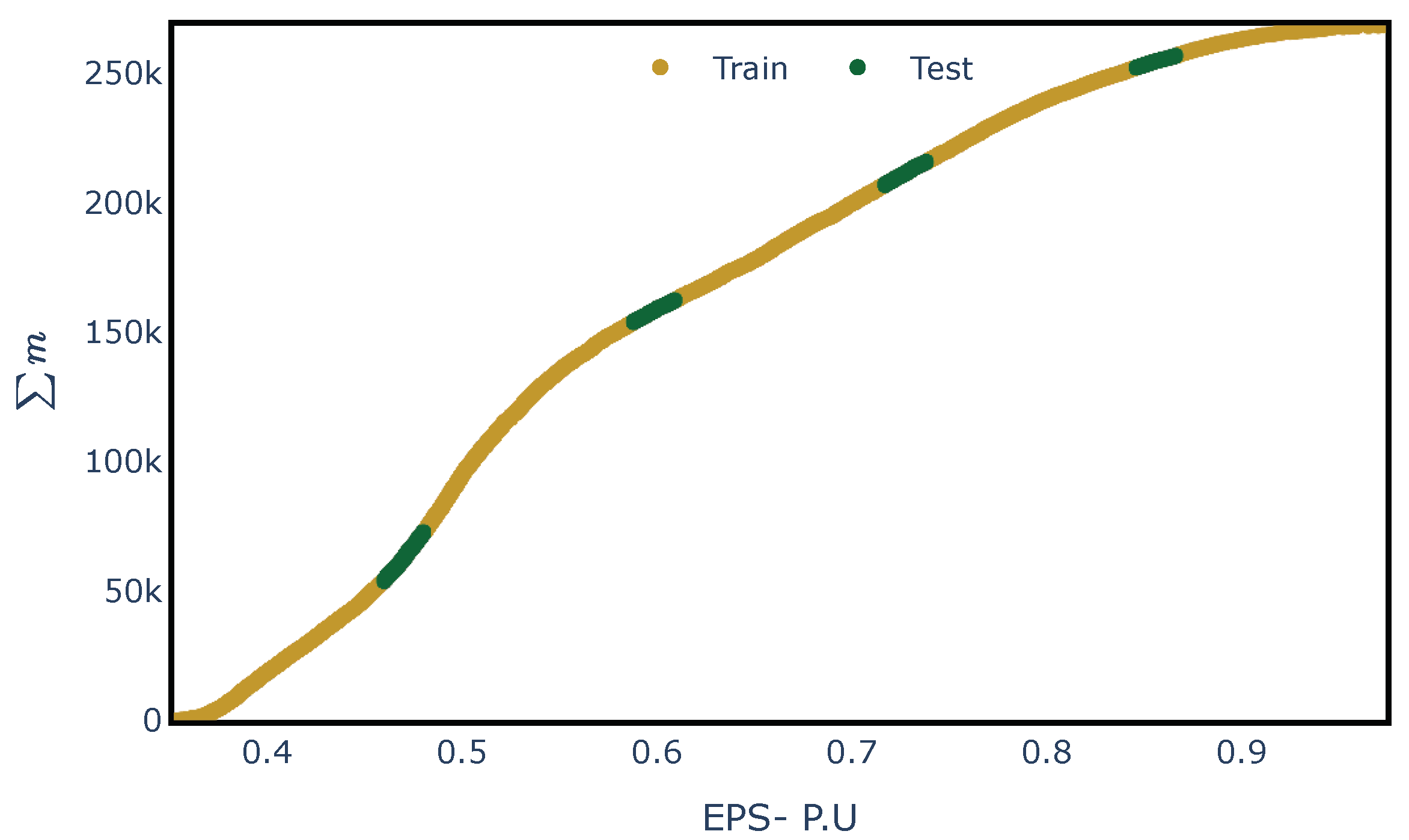
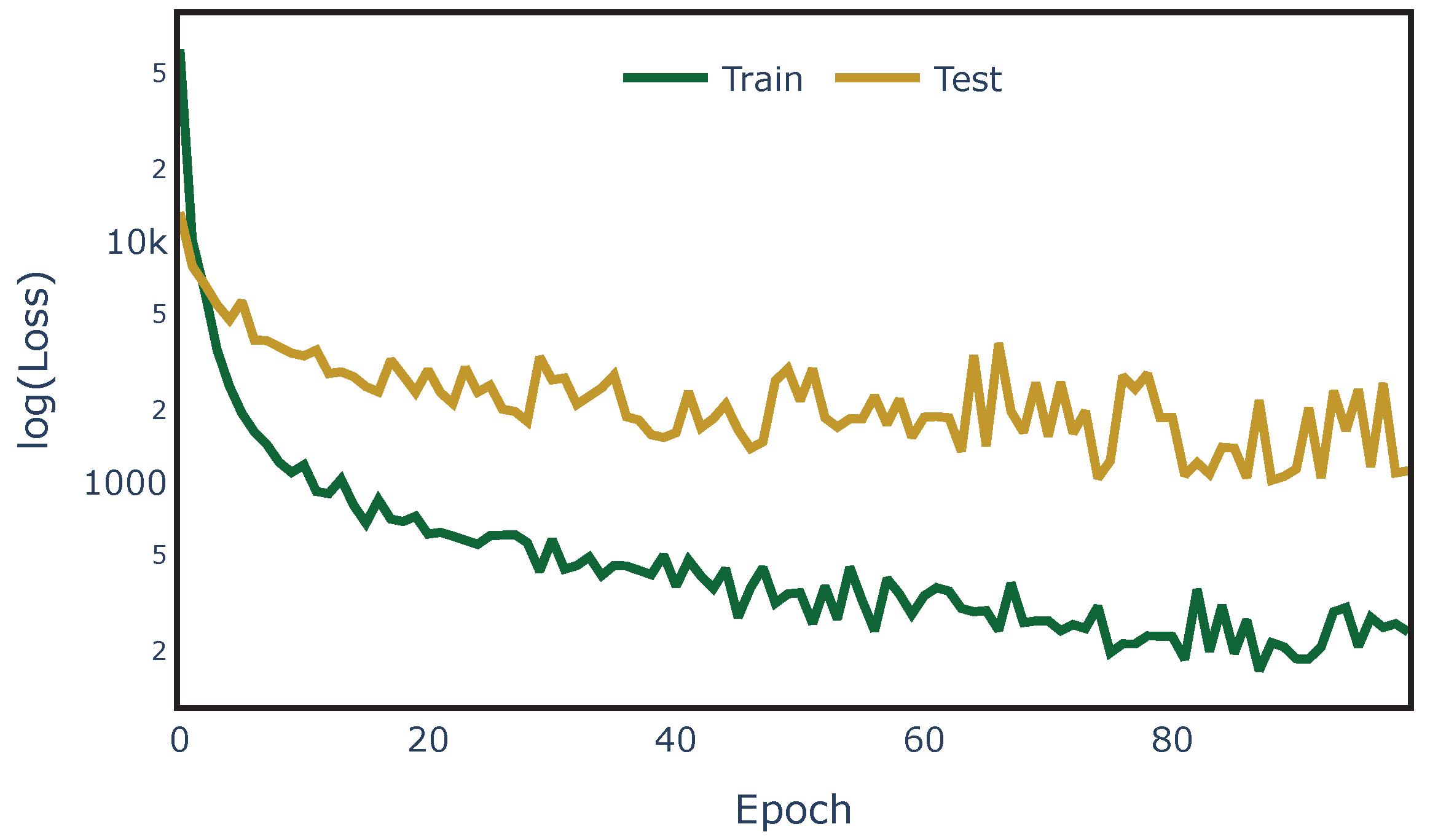
With the established architecture, the model for each network was fitted and tested. Listing 4 provides the Python code developed to fit the proposed ANN model. To assess the learning capacity of the ML model, unknown load conditions and contingencies were used for testing. Hence, the training and test datasets were split as shown in Figure 8, with 85% of the samples used for training and 15% for testing, using the raw data generated in Section 4.2. Figure 9 shows the testing and training loss obtained during the fitting processes for PEGASE-1354.
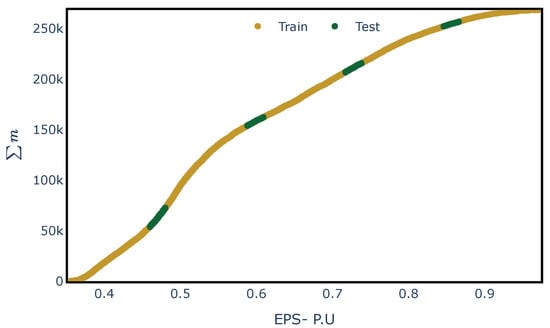
Figure 8.
Split of the dataset to assess the ANN model’s learning capability under unknown Expected Power to Supply (EPS).
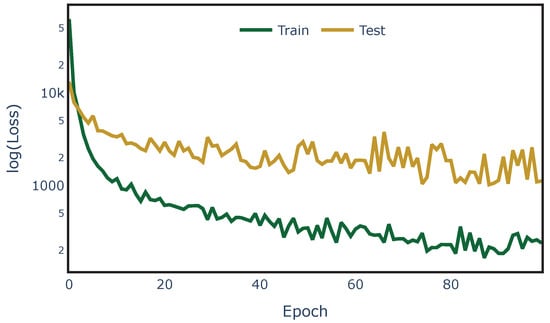
Figure 9.
Convergence analysis for on the PEGASE-1354 network.
| Listing 4. Python Code to fit the ANN-model. |
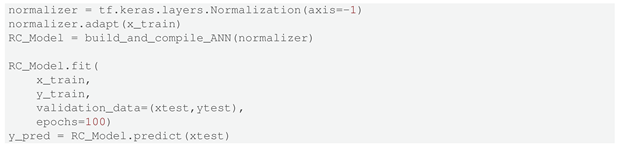 |
4.5. Regression Assessment
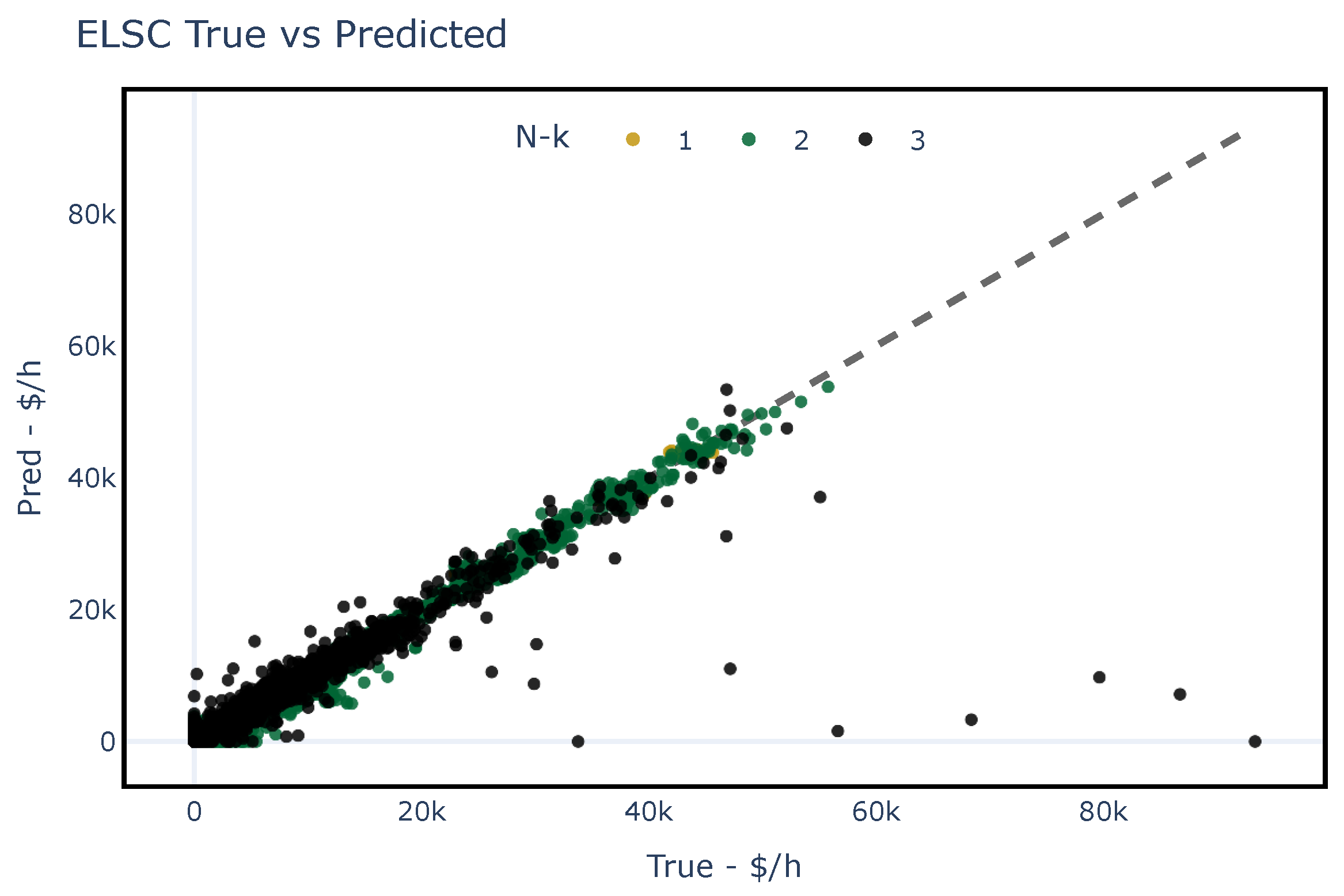
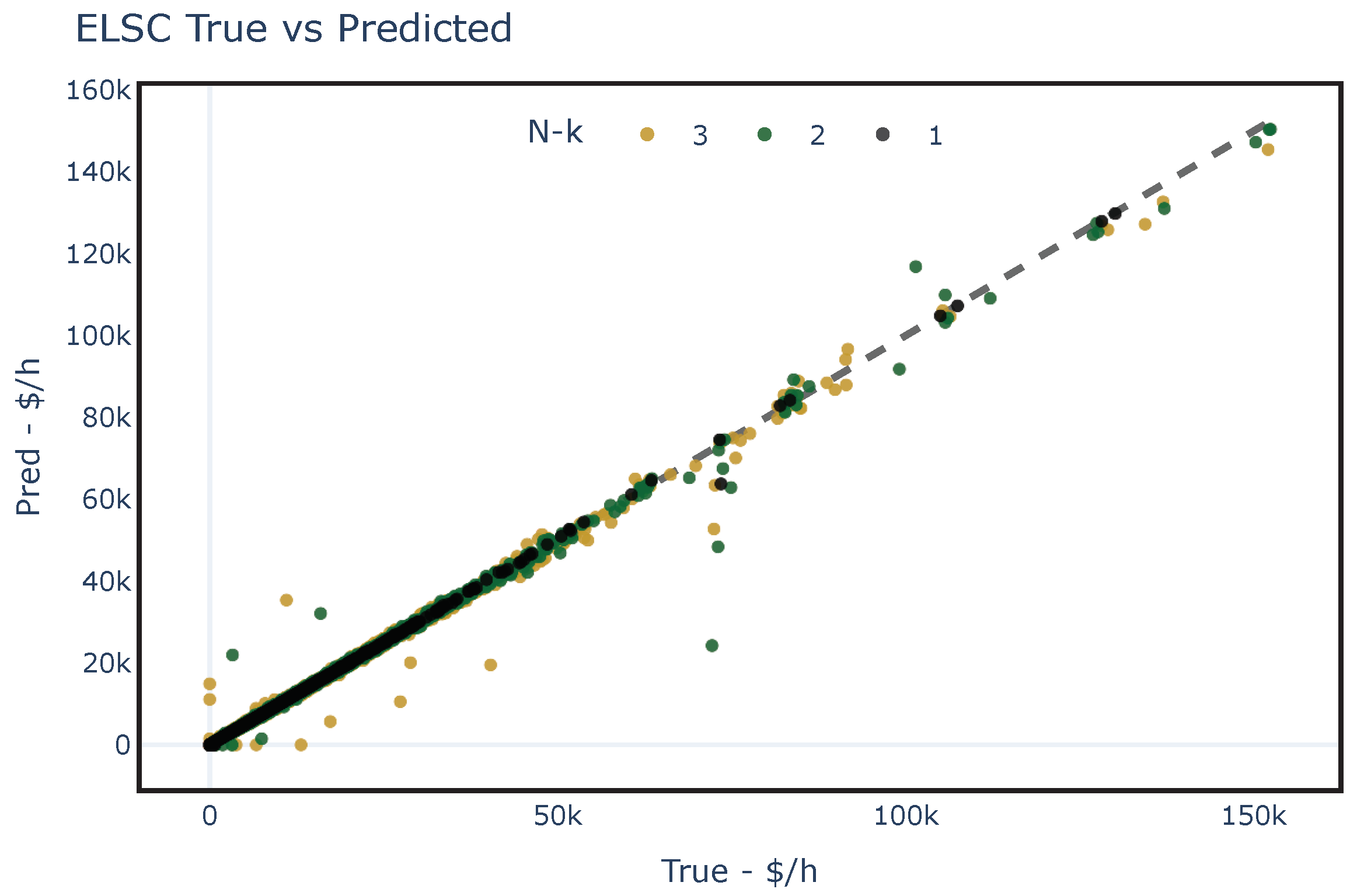
Figure 10 and Figure 11 show the predicted and the true values of using the testing dataset for each studied network. These figures illustrate the model’s capability to generalize accurately when the status of the elements is known. It should be noted that two outliers were obtained for the PEGASE-1354 case and were subsequently excluded from the assessment.
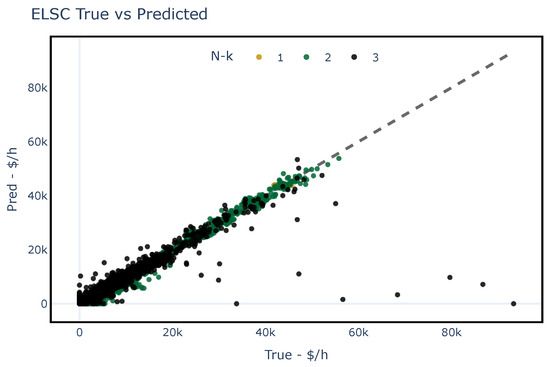
Figure 10.
Predicted values obtained by assessing the fit of the proposed regression ML model for the IEEE-39 bus system with different contingencies. The dashed line represents an assumed perfect fit.
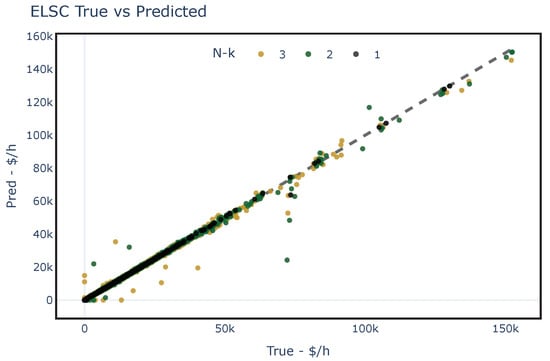
Figure 11.
Predicted values obtained by assessing the fit of the proposed regression ML model for the PEGASE-1354 network with different contingencies. The dashed line represents an assumed perfect fit.
To evaluate the overall performance of the fit, four regression metrics were used: R-Squared coefficient of determination (), Mean Absolute Error (MAE), Root Mean Square Error (rMSE) and Relative Root Mean Square Error (rrMSE). These metrics were computed comparing the LS-OPF results with the ML fit. Table 5 presents the results of these metrics for both case studies. Notice that, based on the dimensionless metric and rrMSE, the fit demonstrates high performance in generalizing when a contingency occurs.

Table 5.
Regression performance metrics obtained to generalize the for IEEE-39 bus and PEGASE-1354 network.
The average time for predicting was and for the IEEE-39 and PEGASE-1354 networks, respectively. This significant reduction in execution time demonstrates the substantial speed-up achieved when using ANN compared to LS-OPF, resulting in speed-up factors of 12,500× and 45,000× for each case, respectively.
Table 6 shows the rrMSE for each set of contingencies. As expected, the error increases as k increases. This consequence is attributed to the exponential growth in the number of combinations when k increases, given that criterion involves contingency scenarios. In other words, as k increases, more training scenarios are required. This can be observed by comparing the size of scenarios used to train the ANN in Table 4 with the performance results provided in Table 5. For instance, the IEEE-39 case, which has fewer scenarios, also has the lower performance.

Table 6.
rrMSE between test and predicted values of for different k contingencies.
4.6. Discussion
Based on the assessment of LS-OPF simulations, it is observed that in the majority of cases with a contingency , the expected load shedding is the summation of under contingencies; in other words, , where C is the set of elements that fails. To illustrate, considering the case , the aforementioned expression is valid for 75% of 188,452 scenarios for the IEEE-39 bus system, and for 99% of 982 scenarios for PEGASE-1354. The reduced number of N-2 scenarios, compared to those shown in Table 4, is attributed to the limited number of contingencies, which corresponds for specific EPS (Figure 3). This implies that only a small subset of the entire dataset can be used to compute as the sum of contingencies. This could explain the fast convergence of the ANN shown in Figure 9. Despite the presence of a strong linear dependence of for higher-order contingencies , the ANNs shows the ability to generalize the for unknown training values of .
The proposed approach is limited to static topologies with synchronous generation at transmission level, and outlier detection techniques should be implemented to identify abnormal contingencies. Additionally, uncertainties in generation, dynamic stability limits, and demand response, among others, are beyond the scope of this work. Future research should aim to address these limitations by exploring new approaches, such as graph neural networks.
5. Conclusions
In this paper, we propose an approach for fast security assessment in power transmission planning using ANN to accelerate contingency evaluation. The training is performed by executing Load Shedding Optimal Power Flow (LS-OPF), which minimizes the for a set of contingencies generated stochastically. The ANN predicts using the connection status of elements such as lines, generators, and power transformers, among others, as features. As a result, an accuracy close to 98% and acceleration gains of 12,500× and 45,000× were obtained for the IEEE-39 bus system and PEGASE-1354 system, respectively, demonstrating great effectiveness. These results highlight the high accuracy and efficiency of our proposal, making it an attractive option for probabilistic grid planning using criterion within a reasonable execution time. A similar approach and its results have not addressed in the literature. As potential areas for future research, we suggest extending this method to distribution networks with distributed generation, the classification of problematic contingencies, and applying the approach to resilience assessment.
Author Contributions
Conceptualization, D.L.A., A.C. and T.J.-M.M.; Methodology, D.L.A.; Software, D.L.A. and J.P.; Validation, M.G. and J.P.; Formal analysis, M.G., A.C. and G.A.-N.; Investigation, D.L.A.; Resources, T.J.-M.M.; Data curation, J.P.; Writing—original draft, D.L.A.; Writing—review & editing, D.L.A., M.G., A.C. and G.A.-N.; Supervision, M.G., A.C. and G.A.-N.; Project administration, G.A.-N. and T.J.-M.M.; Funding acquisition, G.A.-N. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The raw data supporting the conclusions of this article will be made available by the corresponding author on request.
Acknowledgments
Our work was supported by Hydro-Québec TransÉnergie and the PRIAD.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| AC | Alternating current |
| ANN | Artificial neural network |
| CB | Circuit breaker |
| CNN | Convolutional Neural Networks |
| DC | Direct current |
| DT | Decision tree |
| ESLC | Expected supply load cost |
| ELSC | Expecting load shedding cost |
| ENS | Energy not supplied |
| HQ | Hydro-Quebec |
| LS | Load Shedding |
| MAE | Mean absolute error |
| ML | Machine learning |
| MLP | Multilayer Perceptron |
| OPF | Optimal power flow |
| PF | Power flow |
| PS | Power systems |
| R-Squared coefficient of determination | |
| rMSE | Root Mean Square Error |
| rrMSE | Relative Root Mean Square Error |
| SCOPF | Security constrain optimal power flow |
| SLC | Supply load cost |
| VoLL | Value of lost load |
References
- Singh, C.; Jirutitijaroen, P.; Mitra, J. Introduction to Power System Reliability; John Wiley & Sons, Inc.: New York, NY, USA, 2018; pp. 185–191. [Google Scholar] [CrossRef]
- Alvarez-Alvarado, M.S.; Donaldson, D.L.; Recalde, A.A.; Noriega, H.H.; Khan, Z.A.; Velasquez, W.; Rodriguez-Gallegos, C.D. Power System Reliability and Maintenance Evolution: A Critical Review and Future Perspectives. IEEE Access 2022, 10, 51922–51950. [Google Scholar] [CrossRef]
- Lumbreras, S.; Ramos, A.; Banez-Chicharro, F.; Olmos, L.; Panciatici, P.; Pache, C.; Maeght, J. Large-scale transmission expansion planning: From zonal results to a nodal expansion plan. IET Gener. Transm. Distrib. 2017, 11, 2778–2786. [Google Scholar] [CrossRef]
- Capitanescu, F.; Ramos, J.M.; Panciatici, P.; Kirschen, D.; Marcolini, A.M.; Platbrood, L.; Wehenkel, L. State-of-the-art, challenges, and future trends in security constrained optimal power flow. Electr. Power Syst. Res. 2011, 81, 1731–1741. [Google Scholar] [CrossRef]
- Heidari, H.; Hagh, M.T.; Salehpoor, P. Accurate, simultaneous and Real-Time screening of N-1, N-k, and N-1-1 contingencies. Int. J. Electr. Power Energy Syst. 2022, 136, 107592. [Google Scholar] [CrossRef]
- Rodriguez, D.; Gomez, D.; Alvarez, D.; Rivera, S. A Review of Parallel Heterogeneous Computing Algorithms in Power Systems. Algorithms 2021, 14, 275. [Google Scholar] [CrossRef]
- Golestan, S.; Habibi, M.; Mousavi, S.M.; Guerrero, J.; Vasquez, J. Quantum computation in power systems: An overview of recent advances. Energy Rep. 2023, 9, 584–596. [Google Scholar] [CrossRef]
- Sundar, K.; Coffrin, C.; Nagarajan, H.; Bent, R. Probabilistic N-k failure-identification for power systems. Networks 2018, 71, 302–321. [Google Scholar] [CrossRef]
- Heylen, E.; Ovaere, M.; Proost, S.; Deconinck, G.; Hertem, D.V. A multi-dimensional analysis of reliability criteria: From deterministic N-1 to a probabilistic approach. Electr. Power Syst. Res. 2019, 167, 290–300. [Google Scholar] [CrossRef]
- Gholami, M.; Sanjari, M.J.; Safari, M.; Akbari, M.; Kamali, M.R. Static security assessment of power systems: A review. Int. Trans. Electr. Energy Syst. 2020, 30, e12432. [Google Scholar] [CrossRef]
- Karangelos, E.; Perkin, S.; Wehenkel, L. Probabilistic Resilience Analysis of the Icelandic Power System under Extreme Weather. Appl. Sci. 2020, 10, 5089. [Google Scholar] [CrossRef]
- Majidi-Qadikolai, M.; Baldick, R. Integration of Contingency Analysis N-1 With Systematic Transmission Capacity Expansion Planning: ERCOT Case Study. IEEE Trans. Power Syst. 2016, 31, 2234–2245. [Google Scholar] [CrossRef]
- Karangelos, E.; Wehenkel, L. Probabilistic Reliability Management Approach and Criteria for power system real-time operation. In Proceedings of the 2016 Power Systems Computation Conference (PSCC), Genoa, Italy, 20–24 June 2016; pp. 1–9. [Google Scholar] [CrossRef]
- Heylen, E.; Labeeuw, W.; Deconinck, G.; Hertem, D.V. Framework for Evaluating and Comparing Performance of Power System Reliability Criteria. IEEE Trans. Power Syst. 2016, 31, 5153–5162. [Google Scholar] [CrossRef]
- Moreira, A.; Street, A.; Arroyo, J.M. An Adjustable Robust Optimization Approach for Contingency-Constrained Transmission Expansion Planning. IEEE Trans. Power Syst. 2015, 30, 2013–2022. [Google Scholar] [CrossRef]
- Karangelos, E.; Wehenkel, L. An Iterative AC-SCOPF Approach Managing the Contingency and Corrective Control Failure Uncertainties With a Probabilistic Guarantee. IEEE Trans. Power Syst. 2019, 34, 3780–3790. [Google Scholar] [CrossRef]
- Perkin, S.; Hamon, C.; Kristjansson, R.; Stefansson, H.; Jensson, P. Framework for trajectory-based probabilistic security assessment of power systems. IET Gener. Transm. Distrib. 2019, 13, 1088–1094. [Google Scholar] [CrossRef]
- Delavari, A.; Prevost, J.; Cote, A. Hydro-Québec’s Experience of Implementing Power-system Node-Breaker Model for Planning Studies. In Proceedings of the 2021 IEEE 9th International Conference on Smart Energy Grid Engineering (SEGE), Oshawa, ON, Canada, 11–13 August 2021; pp. 100–103. [Google Scholar] [CrossRef]
- Duchesne, L.; Karangelos, E.; Wehenkel, L. Machine learning of real-time power systems reliability management response. In Proceedings of the 2017 IEEE Manchester PowerTech, Manchester, UK, 18–22 June 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Duchesne, L.; Karangelos, E.; Sutera, A.; Wehenkel, L. Machine learning for ranking day-ahead decisions in the context of short-term operation planning. Electr. Power Syst. Res. 2020, 189, 106548. [Google Scholar] [CrossRef]
- Donnot, B.; Guyon, I.; Marot, A.; Schoenauer, M.; Panciatici, P. Optimization of computational budget for power system risk assessment. In Proceedings of the 2018 IEEE PES Innovative Smart Grid Technologies Conference Europe (ISGT-Europe), Sarajevo, Bosnia and Herzegovina, 21–25 October 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Gaha, M.; Chabane, B.; Komljenovic, D.; Côté, A.; Hébert, C.; Blancke, O.; Delavari, A.; Abdul-Nour, G. Global Methodology for Electrical Utilities Maintenance Assessment Based on Risk-Informed Decision Making. Sustainability 2021, 13, 9091. [Google Scholar] [CrossRef]
- Wehenkel, L. Machine learning approaches to power-system security assessment. IEEE Expert 1997, 12, 60–72. [Google Scholar] [CrossRef]
- Duchesne, L.; Karangelos, E.; Wehenkel, L. Recent Developments in Machine Learning for Energy Systems Reliability Management. Proc. IEEE 2020, 108, 1656–1676. [Google Scholar] [CrossRef]
- Donnot, B.; Guyon, I.; Schoenauer, M.; Marot, A.; Panciatici, P. Anticipating contingengies in power grids using fast neural net screening. In Proceedings of the 2018 International Joint Conference on Neural Networks (IJCNN), Rio de Janeiro, Brazil, 8–13 July 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Oliveira, W.D.; Vieira, J.P.; Bezerra, U.H.; Martins, D.A.; Rodrigues, B.D.G. Power system security assessment for multiple contingencies using multiway decision tree. Electr. Power Syst. Res. 2017, 148, 264–272. [Google Scholar] [CrossRef]
- Zhang, L.; Chen, Y.; Zhang, B. A Convex Neural Network Solver for DCOPF with Generalization Guarantees. IEEE Trans. Control. Netw. Syst. 2022, 9, 719–730. [Google Scholar] [CrossRef]
- Pan, X.; Chen, M.; Zhao, T.; Low, S.H. DeepOPF: A Feasibility-Optimized Deep Neural Network Approach for AC Optimal Power Flow Problems. IEEE Syst. J. 2023, 17, 673–683. [Google Scholar] [CrossRef]
- Jia, Y.; Bai, X.; Zheng, L.; Weng, Z.; Li, Y. ConvOPF-DOP: A Data-Driven Method for Solving AC-OPF Based on CNN Considering Different Operation Patterns. IEEE Trans. Power Syst. 2023, 38, 853–860. [Google Scholar] [CrossRef]
- Liu, H.; Wu, W. Federated Reinforcement Learning for Decentralized Voltage Control in Distribution Networks. IEEE Trans. Smart Grid 2022, 13, 3840–3843. [Google Scholar] [CrossRef]
- Liao, W.; Chen, J.; Liu, Q.; Zhu, R.; Song, L.; Yang, Z. Data-driven Reactive Power Optimization for Distribution Networks Using Capsule Networks. J. Mod. Power Syst. Clean Energy 2022, 10, 1274–1287. [Google Scholar] [CrossRef]
- Pan, X.; Zhao, T.; Chen, M.; Zhang, S. DeepOPF: A Deep Neural Network Approach for Security-Constrained DC Optimal Power Flow. IEEE Trans. Power Syst. 2021, 36, 1725–1735. [Google Scholar] [CrossRef]
- Zhou, Y.; Park, J.; Zhu, H. Scalable Learning for Optimal Load Shedding Under Power Grid Emergency Operations. In Proceedings of the 2022 IEEE Power & Energy Society General Meeting (PESGM), Denver, CO, USA, 17–21 July 2022; pp. 1–5. [Google Scholar] [CrossRef]
- Huang, G.; Wu, F.; Guo, C. Smart grid dispatch powered by deep learning: A survey. Front. Inf. Technol. Electron. Eng. 2022, 23, 763–776. [Google Scholar] [CrossRef]
- Zimmerman, R.D.; Murillo-Sanchez, C.E.; Thomas, R.J. MATPOWER: Steady-State Operations, Planning, and Analysis Tools for Power Systems Research and Education. IEEE Trans. Power Syst. 2011, 26, 12–19. [Google Scholar] [CrossRef]
- Coffrin, C.; Bent, R.; Sundar, K.; Ng, Y.; Lubin, M. PowerModels. JL: An Open-Source Framework for Exploring Power Flow Formulations. In Proceedings of the 2018 Power Systems Computation Conference (PSCC), Dublin, Ireland, 11–15 June 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Wächter, A.; Biegler, L.T. On the implementation of an interior-point filter line-search algorithm for large-scale nonlinear programming. Math. Program. 2006, 106, 25–57. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).