Abstract
The broadcast nature of wireless channels introduces significant security vulnerabilities in information transmission, particularly when the eavesdropper is close to the legitimate destination. In such scenarios, the eavesdropping channel often exhibits high spatial correlation with, or even superior quality to, the legitimate channel. This makes it challenging for traditional power optimization methods to effectively suppress the eavesdropping rate. To address this challenge, this paper proposes an optimization method for the secrecy capacity of unmanned aerial vehicle (UAV) relaying based on the dynamic adjustment of the power allocation factor. By injecting artificial noise (AN) during signal forwarding and combining it with real-time channel state information, the power allocation factor can be dynamically adjusted to achieve precise jamming of the eavesdropping link. We consider a four-node communication model consisting of a source, a UAV, a legitimate destination, and a passive eavesdropper, and formulate a joint optimization problem to maximize the secrecy rate. Due to the non-convexity of the original problem, we introduce relaxation variables and apply successive convex approximation (SCA) to reformulate it into an equivalent convex optimization problem. An analytical solution for the power allocation factor is derived using the water-filling (WF) algorithm. Furthermore, an alternating iterative optimization algorithm with AN assistance is proposed to achieve global optimization of the system parameters. Simulation results demonstrate that, compared to traditional power optimization schemes, the proposed algorithm substantially suppresses the eavesdropping channel capacity while enhancing transmission efficiency, thereby significantly improving both secrecy performance and overall communication reliability.
1. Introduction
In recent years, UAVs have revolutionized wireless communication paradigms by capitalizing on their exceptional mobility, flexible deployment, and cost-effectiveness. They facilitate the rapid establishment of temporary communication links, significantly extend network range, and enhance signal transmission quality [1], thereby serving as pivotal aerial relays in diverse application scenarios such as informatized warfare, disaster response, remote area connectivity, and heterogeneous networking [2,3]. Within integrated space-air-ground networks, UAVs effectively bridge coverage gaps by provisioning reliable line-of-sight (LoS) links, thereby bolstering overall network connectivity and resilience [4,5]. However, the inherent broadcast nature of wireless channels makes transmitted signals susceptible to interception by unauthorized parties, leading to potential information leakage risks, which presents security challenges for UAV communication systems [6].
Traditional secure communication systems predominantly rely on cryptographic techniques (e.g., asymmetric encryption, authentication, and access control) to safeguard information integrity and confidentiality [7,8,9]. While these methods effectively ensure security by increasing computational complexity, they often incur substantial computational overhead and require complex key management protocols [10]. Furthermore, the rapid advancement of quantum computing has begun to erode the computational complexity assumptions underlying many classical cryptographic algorithms, thereby elevating the risk of their compromise [11,12,13].
Concurrently, the open nature of wireless channels in UAV communication systems has spurred interest in physical layer security (PLS) techniques [14,15]. PLS enhances security by exploiting inherent channel characteristics—such as fading, noise, and interference—to actively degrade the signal reception conditions at potential eavesdroppers [16]. Compared to traditional cryptographic approaches, PLS offers advantages in lower computational complexity and greater adaptability to dynamic environments. However, existing PLS frameworks face challenges in achieving optimal performance in complex and dynamic scenarios, particularly when the eavesdropper is in close proximity to the legitimate destination. Under such conditions, the highly correlated CSI between the legitimate and eavesdropping channels severely limits the effectiveness of PLS mechanisms [17,18,19].
The application of UAVs for information transmission was pioneered in [20], where trajectory design and power allocation were optimized via convex optimization methods, laying the groundwork for subsequent research in secure communications. Ref. [21] extended this framework by introducing the presence of an eavesdropper and proposing an iterative difference-of-convex (DC) programming algorithm to maximize the secrecy capacity through adaptive power allocation based on channel disparity. However, this single power optimization algorithm requires a certain degree of separation between the legitimate and eavesdropping channels, implying that information transmission is effective only when the legitimate channel is superior to the eavesdropping channel. This inherent constraint limits its applicability in scenarios where channel conditions are highly correlated or adversarial. To tackle this issue, refs. [22,23,24] jointly optimized UAV trajectory and power under eavesdropper position uncertainty, ensuring worst-case secrecy rate guarantees by enlarging legitimate-eavesdropper channel differences via trajectory design. Refs. [25,26,27] propose to maximize the secrecy capacity by optimizing the UAV’s hovering position (3D coordinates), where the optimal hovering location is determined through analyzing channel gain disparities. Nevertheless, when the eavesdropper is in close proximity to the legitimate destination, such location-trajectory-power methods can’t effectively suppress the eavesdropping rate.
To counteract eavesdropping threats, the study in [28] proposed deploying a UAV as a friendly jammer, optimizing its placement strategy to minimize the eavesdropper’s interception probability without requiring prior knowledge of the eavesdropper’s location. In [29], the secure remote control (RC) problem in multi-UAV systems was investigated, introducing cooperative jamming (CJ) among UAVs to safeguard control data transmitted between UAVs and ground base stations. Similarly, ref. [30] employed cooperative jamming with multi-node AN to degrade the eavesdropper’s channel conditions effectively. Further advancing this field, ref. [31] integrated AN with three-dimensional trajectory optimization for multi-user and multi-eavesdropper scenarios, achieving significant secrecy gains in dense urban environments. Ref. [32] overcame the limitations of traditional power allocation by jointly optimizing the energy allocation between the signal and the AN, thereby reducing the eavesdropper’s interception probability while maintaining robustness across diverse scenarios.
To address the challenge of traditional power optimization methods failing to effectively suppress eavesdropping capacity when eavesdroppers are in close proximity to legitimate destinations, this paper proposes a physical-layer security enhancement technique for UAV relay systems assisted by AN. The proposed technique adaptively controls interference on eavesdropping channels by adjusting the signal-to-AN power allocation factor based on the UAV’s dynamic position and real-time CSI. Considering the information causality constraint, which ensures that the UAV relay can only forward information received from the source, we jointly optimize the source transmission power and the power allocation factor to improve both information transmission efficiency and system security. An alternating iterative algorithm is designed to adjust these parameters, maximizing the secrecy capacity while satisfying all constraints. The secrecy capacity maximization problem is inherently non-convex and computationally intractable. The main contributions of this paper are as follows: (1) A dynamic and precise jamming control mechanism for UAV is proposed, targeting severe “proximity eavesdropping” scenarios. This paper overcomes the inherent reliance on channel disparity in traditional UAV secure communication research and effectively addresses the challenge of traditional methods failing when the eavesdropper is in close proximity to the legitimate destination. (2) By integrating slack variables with the SCA technique, analytical solutions for the optimal source power allocation and UAV jamming power allocation factors are derived. This avoids the high computational complexity of traditional iterative algorithms, reducing the complexity to . (3) The algorithm achieves a synergistic optimization of security performance and communication efficiency. While maintaining secrecy capacity without degradation, the proposed scheme intelligently schedules resources to reduce eavesdropping capacity by approximately and improve communication efficiency by about , thereby breaking the traditional trade-off between security and efficiency.
2. System Model
Consider a wireless communication system comprising a source node (Alice), a legitimate destination (Bob), a UAV relay, and an eavesdropper (Eve). Due to terrain obstructions, the line-of-sight (LoS) link between Alice and Bob is blocked, and the channel gain is negligible due to severe shadow fading. To facilitate reliable communication, a UAV is deployed as a mobile relay node to dynamically forward data between Alice and Bob. To mitigate the risk of sensitive information leakage, we assume that Eve has compromised a node in close proximity to Bob, necessitating robust countermeasures to prevent data interception and ensure secure communication. For clarity, as shown in Figure 1, we adopt a Cartesian coordinate system to represent positions. Alice, Eve, and Bob are positioned at coordinates (), (), and (), respectively. The UAV is initially located directly above Alice at a fixed altitude (H) and moves toward Bob’s position. The flight duration mobile(T) is discretized into (N) equally spaced time slots, and the UAV’s position coordinates can be expressed as .
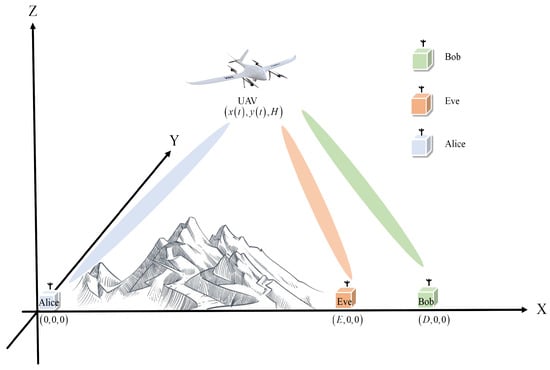
Figure 1.
The illustration of the UAV uplink and downlink.
During the flight, the UAV continuously receives information from Alice and forwards it to Bob under the condition of secure transmission. To ensure communication security, the UAV injects AN while relaying information, thereby interfering with the eavesdropping channel. To enable simultaneous information reception and forwarding by the UAV, mitigate multipath interference and adjacent-channel interference, and enhance the anti-jamming capability of both uplink and downlink, we assume the UAV operates in Frequency Division Duplexing (FDD) mode with an infinite data buffer and allocates equal bandwidth to Alice and Bob. The channel gains for the Alice–UAV, UAV–Eve, and UAV–Bob links are denoted as , and ; it follows the Free Space Path Loss (FSPL) model:
The link distance of Alice–UAV is denoted as ; the link distance of UAV–Eve is denoted as ; and the link distance of UAV–Bob is denoted as . denotes channel power gain at the reference distance m.
Let denote the signal-to-noise ratio (SNR), where is the noise power. Without AN injection, the SNR of each link is expressed as follows:
We assume the power allocation factor to control the transmission power of the signal and AN. Assuming the UAV’s total transmit power in a unit time slot is P, the AN is shared between the UAV and Bob. Since Bob has prior knowledge of the AN, the AN’s interference does not degrade Bob’s reception performance. After being interfered with by AN, the signal-to-interference-plus-noise ratio (SINR) of the UAV–Eve link is expressed as follows:
where satisfies the constraint ; when , it indicates that no AN is added, and all the power P is used for information transmission. When , it means no information is transmitted, and all the power P is used for sending AN. To optimize the system’s energy efficiency, a power-shutdown strategy can be implemented during the period, in which the transmission power is set to zero during that time.
According to the Shannon formula, the theoretical information transmission rates of the UAV, Eve, and Bob are given by the following:
3. Enhance Security by Designing Alternating Iterative Algorithms
To ensure the feasibility of the optimization problem, it is necessary to introduce information-causal constraints, power limitations, and other conditions to ensure that the optimal solution for the system parameters lies within the feasible domain. Based on the dynamic changes in CSI and the three-dimensional spatial coordinates of the UAV, the power allocation factor is adjusted to control the power ratio between the UAV transmission signals and AN, thereby achieving precise interference suppression of eavesdropping channels and significantly improving physical-layer security performance. This section has conducted in-depth analysis and optimization with the goal of maximizing confidentiality capacity.
3.1. Problem Formulation
To ensure the rationality of the transmission power and that the total transmission power of Alice in each time slot does not exceed the preset average power limit, there is a power constraint:
Assuming Eve and Bob have the same channel conditions, define the difference between and as the secrecy capacity within a unit time slot. The total secrecy capacity of the system is as follows:
Moreover, to ensure that the UAV can only forward information received from Alice, there is an information causality constraint:
where
In summary, the secure transmission problem of the proposed UAV relay system can be formulated as a constrained secrecy capacity maximization (SCM) problem:
This paper formulates an optimization problem that contains both a non-convex objective function and non-convex constraints. The specific process is illustrated in Figure 2. First, to handle the non-convex components, a convex approximation approach is adopted: by introducing slack variables and employing the SCA technique, the original problem is transformed into a convex optimization problem. Subsequently, the Lagrangian dual method is applied to solve the convex problem, yielding an optimal analytical solution. Finally, an alternating iterative algorithm is used to iteratively optimize the variables, which ultimately converges to the global optimum.
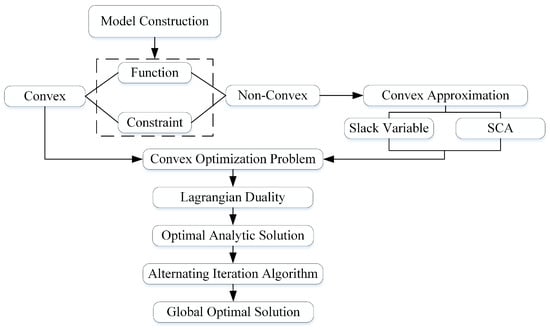
Figure 2.
Convex Optimization Framework.
3.2. Convex Approximation to the SCM Problem
The optimization problem is non-convex due to the (10a) and (10b), since non-convex problems may contain multiple local optima, direct solving methods are prone to getting trapped in local optimality, leading to unstable algorithm performance. Therefore, in this section, we first equivalently reformulate the original problem into a convex approximation.
For the non-convex constraint (10b), an equivalent secrecy capacity maximization problem is derived by introducing relaxation variables :
To further reduce the complexity of (11a), the SCA method is employed to transform problem (11a) into a sequence of convex subproblems. In essence, this involves approximating the objective function at a feasible point using its first-order Taylor expansion for the SCM problem:
Note that (12) is a convex problem, which can be solved by standard convex optimization techniques. Compared to the original problem, it has a tighter convergence property, manifested as follows:
- 1.
- The feasible domain shrinks, and by introducing relaxation variables, the solution space of the original problem is constrained to a more compact convex set.
- 2.
- The objective function is simpler and easier to solve.
- 3.
- The convergence speed is improved, and the equivalent convex problem can quickly converge to the global optimal solution.
3.3. Secrecy Capacity Optimization Through Alternating Iterative Algorithm Design
To reduce the complexity of the feasible domain for equivalent convex optimization problems, this paper uses Lagrange dual functions to incorporate causal constraints (11b) into the objective function, thereby transforming the constraints into penalty terms of the objective function and avoiding dealing with complex constraints.
Introducing dual variables and using Lagrange dual functions to solve (12):
where
Based on the variables , and , the objective problem can be divided into two sub-problems:
where . To ensure that the optimal solution of (15) is bounded, it is necessary to ensure that , i.e.,
Equation (12) satisfies the Slater condition, so the optimal solution of the original problem is equal to the optimal solution of the dual problem. The proof is detailed as follows:
Proof.
Assume , where . Simultaneously, let , where . Under this parameter construction, the power constraints are strictly satisfied:
Since and , and both are continuous, strictly increasing functions of their arguments, we can choose sufficiently small and such that
Using the approximation for small x, we have the following:
By choosing sufficiently larger than (e.g., with ), the strict inequality holds.
The rate constraint (11c) may choose appropriately close to but strictly less than . Since all constraints can be satisfied with strict inequalities, Slater’s condition holds. □
(1) For any given , using the Lagrange multiplier method to solve (14) and (15), we obtain the following:
Equation (21) satisfies the following KKT condition:
where is the parameter ensuring the equality , while is Lagrange multiplier corresponding to .
When , , from Equation (23a), we can obtain the following:
When , it follows that .
Equation (22) satisfies the following KKT condition:
where is the parameter ensuring the equality holds, and are Lagrange multipliers corresponding to .
When and it follows that .
When and , it follows that
When and , it follows that .
Lemma 1.
If is non-increasing, and is non-decreasing, is non-increasing and non-decreasing over n, for any given dual variables, Alice’s optimal power allocation and UAV’s optimal power allocation factor is as follows:
where η is the parameter that ensures , , and .
Proof of Lemma 1.
The proof of Lemma 1 can refer to the Lagrange dual function process in 3.3. (1). □
The proposed algorithm-based gradient descent to solve (27) is summarized in Algorithm 1.
| Algorithm 1 An iterative algorithm based on gradient descent to solve with fixed |
| initialization: 1. Set Alice’s average output power , initial variable . 2. Set initial dual variables to satisfy constraints . 3. Set error tolerance , the iteration index , maximum number of iterations . whiledo 1. Compute and the gradient based on (27); 2. Update using the Newton’s iterative method; 3. If 4. break; 5. else 6. ; 7. end if end while Output: and . |
Where the convergence tolerance , based on the following rationale:
- 1.
- Engineering precision: This tolerance ensures that the computational error in power allocation remains below , which significantly exceeds the implementation precision of actual RF chains;
- 2.
- Computational efficiency: Sensitivity analysis indicates that when , further improvement in the system secrecy capacity becomes saturated (less than ), while computational cost increases significantly. Therefore, represents an ideal trade-off point.
- 3.
- Coordinated global convergence: To ensure the stability of the outer-layer alternating iteration optimization (with a threshold of ), the inner-layer Newton’s method must maintain higher precision, adhering to the principle that .
We set , this setting satisfies the constraint , and assigns equal initial weight to the constraint of each time slot.
(2) For the given and , assuming that the Lagrange dual function has a subgradient of at , where , the optimization problem of the can be expressed as follows:
Lemma 2.
If is non-increasing, is non-decreasing, and is non-increasing and non-decreasing over n, the dual optimal solution must satisfy
Proof of Lemma 2.
Please refer to the Appendix A. □
For any , define the total transmission rate of Alice is with total transmission power , and as the corresponding power allocation for slot n, with satisfying . This leads to the following result.
Theorem 1.
If is non-increasing, is non-decreasing, and is non-increasing and non-decreasing over n, the optimal power allocation can be relaxed without loss of optimality.
where satisfying and .
Proof of Theorem 1.
Please refer to the Appendix B. □
The (29) is a typical optimization problem, which can be solved by the interior point method. The proposed algorithm-based alternative and iterative algorithm to solve (29) is summarized in Algorithm 2.
| Algorithm 2 An alternative and iterative algorithm to solve and |
| initialization: 1. Set initial feasible point . 2. Set UAV’s transmit power P and error tolerance . repeat 1. Compute by Algorithm 1 and based on (28); 2. Update ; 3. Compute the subgradient ; 4. Update using interior point method based on (29) until converges to . Output: , and . |
Where This setting assumes that the signal and AN power are equally allocated at the initial moment, serving as an unbiased initialization strategy.
To evaluate the algorithm’s sensitivity to initial values, we conducted Monte Carlo simulations by randomly generating 100 distinct sets of initial points and , All experiments converged to the same final solution (with a secrecy capacity difference of less than ), demonstrating that the algorithm is insensitive to the initial point and exhibits favorable stability.
The Algorithm 2 adopts the relative L2-norm variation of the dual variables as the convergence criterion, where , the selection of the threshold is based on the following considerations:
- 1.
- A trade-off between numerical accuracy and computational cost: The choice of must balance computational accuracy and algorithmic efficiency. An overly small (e.g., ) would lead to unnecessary iterations and increased computation time, while an overly large (e.g., ) may compromise the optimality of the solution;
- 2.
- Engineering practice standards: In communication system optimization, when the relative change in the objective function (secrecy capacity) is on the order of , its impact on system performance enhancement becomes negligible. According to the convergence properties of first-order optimization methods, the accuracy of the dual variables typically aligns with the accuracy of the objective function. Therefore, we set to ensure that the algorithm terminates efficiently while achieving sufficient engineering precision.
- 3.
- Simulation verification: We tested the convergence behavior for ranging from to . When , the improvement in secrecy capacity was less than , while the number of iterations increased significantly. Hence, = represents an ideal compromise.
After obtaining the dual optimal solution , the throughput of Alice, Bob, and Eve can be obtained through and . We will analyze the following four cases.
Case 1: and , which is equivalent to and . In this case, both and strictly positive vector, (14) and (15) are strictly convex optimization problems, and there exists a unique solution. Furthermore, (14) and (15) demonstrate that the optimal allocation results all satisfy the WF solution.
Case 2: and , which is equivalent to . We can obtain and . In this case, Alice’s optimal power allocation is not unique. Bob’s optimal power allocation factor is given by , where must satisfy . Under the given power allocation factor, we can obtain Alice’s primal optimal solution that satisfies the information causality constraint.
Case 3: and , which is equivalent to and . We can obtain and . In this case, Alice’s optimal power allocation solution is classic WF power allocation with a constant water level, i.e., , with satisfying . Due to , the optimal solution for Bob will not be unique. We can obtain Bob’s primal optimal solution with Alice’s given power allocation.
Case 4: and mean that needs to satisfy both and at the same time, which are contradictory to each other. This case is obviously impossible to happen.
3.4. Computational Complexity
While the computation of the proposed method in this paper mainly consists of the following parts:
- 1.
- Newton iteration for : .
- 2.
- Compute and : .
- 3.
- Compute the subgradient : .
- 4.
- Interior-Point Method (IPM) for (29): .
The overall computational complexity is , Simulation results indicate that, under the set convergence tolerance, the algorithm converges in an average of only iterations, compared to the traditional SDP method, which typically has a complexity of at least , the proposed algorithm exhibits lower computational complexity.
4. Simulation and Discussion
In this section, to evaluate the effectiveness of the proposed optimization algorithm, conduct a simulation analysis. The simulation settings parameters are as follows: , , , , , , the acceleration of the UAV is , the maximum speed of the UAV is , the UAV flies from Alice to Bob at a constant altitude H. The communication bandwidth per link is 20 MHz with the carrier frequency at 5 GHz, the noise power spectrum density is −169 dBm/Hz and . All numerical results are calculated based on the raw simulation data.
Two algorithms were considered as baseline algorithms in the simulation: the throughput maximization algorithm without considering the influence of eavesdroppers, abbreviated as “baseline 1”, which considers maximizing the information reception rate of legitimate destinations as much as possible [20]; The algorithm for maximizing security capacity considering the influence of eavesdropping location, abbreviated as “baseline 2”, which is based on the differences between legitimate channel and eavesdropping channel to maximum security capacity [21].
To quantitatively evaluate the security performance of the algorithm, this paper defines the following core performance metrics. Among them, the eavesdropping capacity suppression percentage is a key indicator for assessing the algorithm’s ability to degrade Eve’s capability, and its calculation method is described below.
Let denote the instantaneous achievable rate of Eve in the n time slot under a given algorithm. The cumulative amount of eavesdropped information under that algorithm, denoted as , is obtained by integrating the instantaneous rate over the communication duration. Since the time is discretized into N time slots, the integration translates to
where is the time slot duration.
Consequently, the percentage reduction in eavesdropping capacity achieved by the proposed algorithm compared to the baseline algorithm is as follows:
This metric reflects the extent to which the proposed algorithm suppresses the total amount of information that can be acquired by the eavesdropper. The closer is to , the more significant the security enhancement achieved.
Figure 3 shows the WF situation of the optimal power of Alice’s transmitter as the UAV flight time (s) changes. As the UAV moves away from Alice, the Alice–UAV link is affected by the increase in link distance, and the signal-to-noise ratio of the link gradually decreases. When the 1/SNR is higher than the water level, the preset information transmission conditions are no longer met, and power is no longer injected.
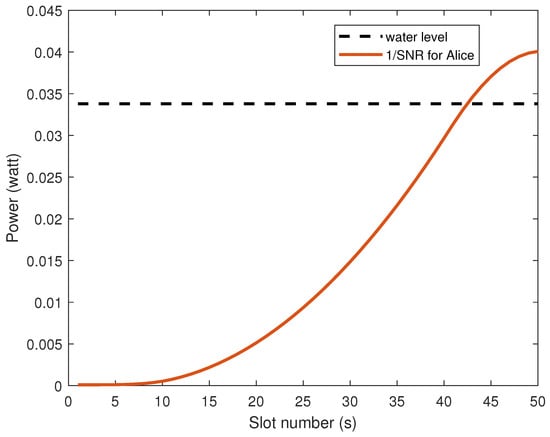
Figure 3.
Alice’s optimal power allocation diagram.
Figure 4 illustrates the WF situation of power allocation factor as a function of UAV flight time (s). 32∼40 s, the noise power required to jam Eve increases as the UAV–Eve link distance decreases, resulting in a lower water level. Conversely, 40∼50 s, when the UAV–Eve link distance grows and the UAV–Bob link distance shortens, the noise power diminishes while the information transmission power rises, resulting in a recovery of the water level. 50∼67 s, the UAV arrived and hovered above Bob, but due to the presence of Eve, the UAV still needs to inject AN to suppress the eavesdropping rate. It is noteworthy that during 50∼67 s, the optimal solution for the power allocation factor may exhibit minor fluctuations as the employed algorithm iteratively approaches the global optimum. The optimal power allocation factor result is shown in Figure 5:
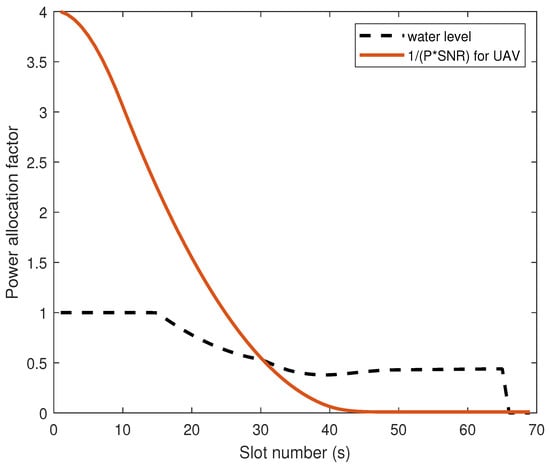
Figure 4.
Bob’s optimal power allocation diagram.
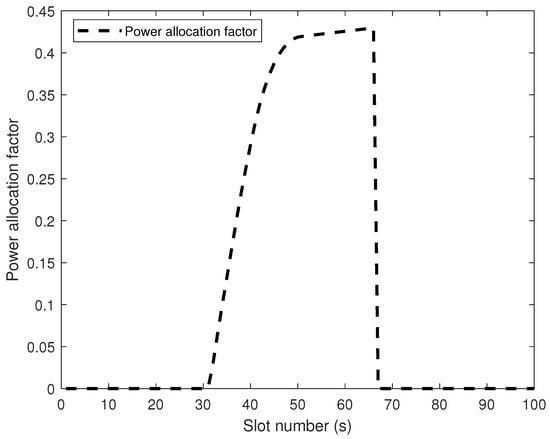
Figure 5.
The optimal power allocation factor result chart for the UAV.
Figure 6 illustrates the suppression effect of AN on Eve channel conditions. The proposed algorithm dynamically suppresses eavesdropping channel conditions by controlling the AN injection power, thereby widening the gap between legitimate and eavesdropping channels.
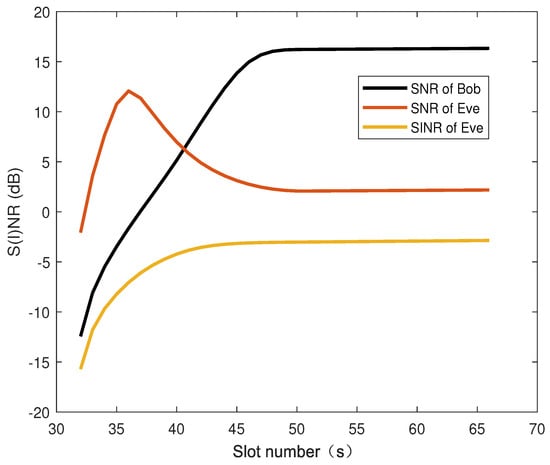
Figure 6.
The effect of artificial noise on channel conditions.
Figure 7 illustrates the relationship between the cumulative information sent by Alice and the cumulative information received by Bob over time. The total information received by Bob is always less than or equal to the total information sent by Alice, proving that the proposed algorithm satisfies the information causality constraint.
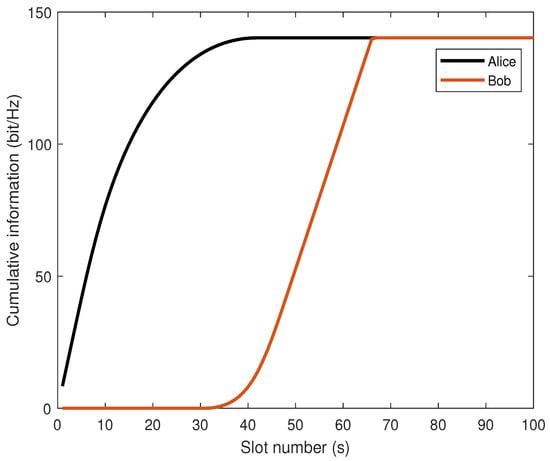
Figure 7.
Comparison of cumulative information received/sent.
Figure 8 shows the comparison of throughput between the proposed algorithm and baseline 1 and 2 for Bob and Eve. The curve of Baseline 1 exhibits an anomalous peak when the UAV flies near Eve. This phenomenon stems from a design flaw in the algorithm: its sole objective is to maximize the amount of information received by Bob, while security risks are not taken into account. When the UAV is closest to Eve, the eavesdropper’s channel quality is optimal. Although the power allocated to this segment is intended to increase Bob’s rate, it simultaneously causes Eve’s interception rate to spike sharply. Given the same total power, due to the UAV using a portion of its power to inject AN, Bob’s information reception rate will be lower than Bob’s information reception rate in baseline 1 and 2. However, minimizing the eavesdropping rate of Eve is equally important. The proposed algorithm achieves a significantly lower eavesdropping rate compared to baseline 2, according to Equation (33), the the calculation shows that the eavesdropping capacity is reduced by . (The cumulative secrecy capacity of the proposed algorithm differs by compared to that of baseline 2.) It is worth noting that the legitimate and eavesdropping channel conditions of baseline 1 are only determined by the link distance. The proposed algorithm introduces AN, expands the scope of secure communication, and improves 9% transmission efficiency. Overall, Algorithm 1 outperforms the two baseline algorithms.
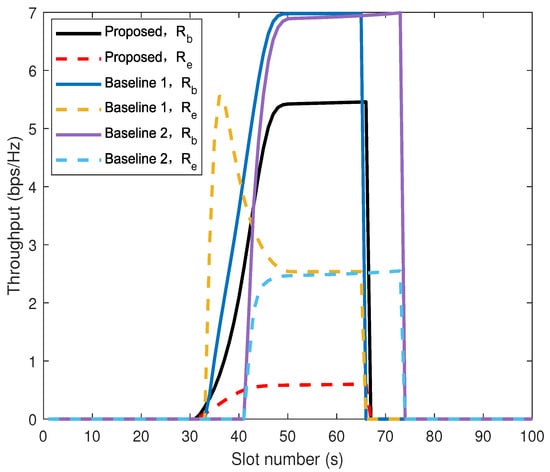
Figure 8.
Comparison of throughput between the proposed algorithm and baseline algorithms on Bob and Eve.
Figure 9 reveals the impact of temporal characteristics and signal-to-noise ratio (SNR) on the system’s secure transmission performance. Experimental results demonstrate that for every 2 dB increase in the total system SNR: (1) the average secure rate improves by approximately 0.37 bps/Hz; (2) the UAV’s average secure communication range (the interval during which the channel conditions of Bob are superior to those of Eve) expands by 35%; (3) the system’s communication efficiency enhances by 4.5%.
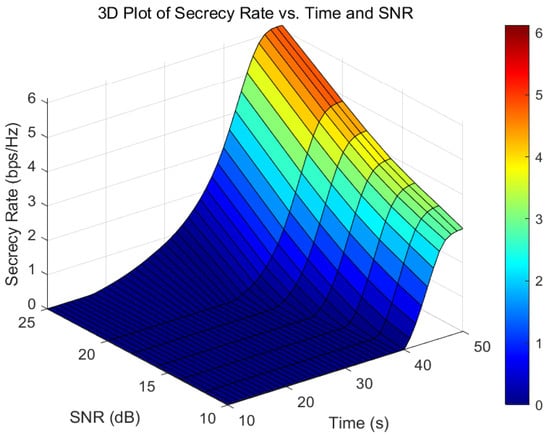
Figure 9.
Three-dimensional comparison chart of Secrecy Rate, Time, and SNR.
Figure 10 illustrates the impact of different power allocation factors on the system secrecy rate as the distance between Eve and Bob decreases (i.e., the value of E increases). Assuming the UAV hovers at and the total power is constant, Eve’s channel condition is superior to Bob’s initially. As Eve gradually moves closer to Bob, the interference effect of AN on Eve weakens. However, the increasing distance of the UAV–Eve link also leads to a degradation of Eve’s channel quality. In summary, the system’s secrecy rate is enhanced. As the power allocation factor decreases, the proportion of power allocated to AN increases. This actively amplifies interference to artificially widen the disparity between Bob’s channel and Eve’s channel, thereby compensating to some extent for the security performance loss caused by Eve’s proximity. However, as the proportion of AN power continues to increase, the marginal improvement in secrecy rate it can provide gradually diminishes. The secrecy capacity curves corresponding to different power allocation factors may intersect. This occurs because the suppression effect of a high-power AN on the Eve can no longer outweigh the enhancement in the upper limit of transmission rate brought by allocating more power to the information-bearing signal. Consequently, under a total power constraint, a trade-off between the power allocated to the information signal and that allocated to the AN is necessary. This balance aims to maximize the secrecy capacity while simultaneously improving the information transmission efficiency.
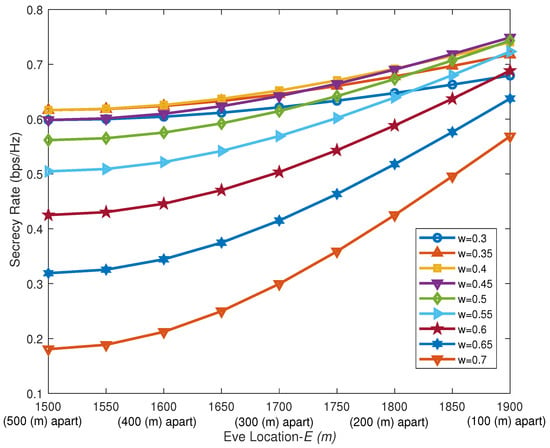
Figure 10.
Impact of different Eve positions on algorithm performance.
5. Conclusions
This paper proposes an AN-assisted UAV relay secure communication system, which effectively enhances physical-layer security by injecting AN through the UAV during signal forwarding. Leveraging real-time CSI and dynamic UAV positioning, the system adaptively adjusts the power allocation factor to precisely control interference on the eavesdropping channel, effectively addressing the challenge of suppressing the eavesdropping rate when the eavesdropper is close to the legitimate destination. To tackle the non-convex optimization problem induced by information causality constraints and Shannon capacity, a novel algorithm integrating relaxation variables and SCA is designed, successfully deriving an Algorithm for optimal power allocation with AN-assistance. Simulation results demonstrate that, under the same total power constraint, the proposed scheme significantly reduces the eavesdropping channel capacity, expands the secure communication range, and simultaneously improves the system’s security performance and communication efficiency, providing a new theoretical and practical foundation for optimizing the security of UAV relay communication systems. In the future, deterministic optimization and stochastic covert communication strategies can be integrated to construct a multi-dimensional defense-in-depth architecture.
Author Contributions
Conceptualization, Y.H., Y.X. and J.T.; methodology, Y.H.; software, Y.H., Y.X. and J.T.; validation, Y.H., Y.X., Q.D., D.H., C.D. and J.T.; formal analysis, D.H.; investigation, Y.H., Y.X. and J.T.; resources, Y.H.; data curation, X.L. and J.T.; writing—original draft preparation, Y.H.; writing—review and editing, J.T.; visualization, Y.H. All authors have read and agreed to the published version of the manuscript.
Funding
The research was funded by the CAEP Foundation (grants YZJJZL2024076 and YZJJZQ2023012), the National Natural Science Foundation of China under grant 62441111, and the Sichuan Science and Technology Program under grants 2024NSFSC0476 and 2025YFHZ0199.
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding author(s).
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A
We use the method of contradiction to prove Lemma 2. Assuming that , . Thus, the transmission rate of Alice and Bob can be expressed as
where
Since both and is non-increasing over n, the is non-increasing:
Under the above assumption, the information causality constraints are active from n to , UAV must immediately forward all received data in each time slot:
This implies that the UAV cannot store data, which limits the flexibility of .
Lemma A1.
If is non-increasing, is non-decreasing, and is non-increasing and non-decreasing over n, before the UAV completes the information transmission task, is non-decreasing.
Proof of Lemma A1.
Assuming the closest slot between UAV and Eve is , is increasing within and non-increasing within , and is non-decreasing over n.
(1) If , i.e., , we need to increase AN to suppress higher eavesdropping gain, so there are .
Due to the limited power P, even if , may still be greater than . During this time period, the secrecy capacity is negative, which is not allowed for maximizing the secrecy capacity,
Assuming the existence of makes .
During this time period, the eavesdropping channel can be suppressed by rationally allocating power P to AN, thereby achieving , while ensuring a positive secrecy capacity.
If , , for the same , we have . Therefore, we can increase the power used for information transmission . There will be , which contradicts our hypothesis.
(2) Assuming the existence of makes .
If , , the channel quality for Eve degrades, we can increase the power used for information transmission, so there are . There will be , which also contradicts our hypothesis.
In summary, the is non-decreasing.
Appendix B
For Case 3, Alice’s optimal power allocation is given by the classic WF solution with all power budget, i.e., The transmission rate of Alice is , with denoting the water level. The optimal power of the UAV can be obtained by .
According to Lemma 2, the information causality constraint can be ignored from slot 2 to slot .
Lemma A2.
Proof of Lemma A2.
Note that problem (A7) is a relaxation of (A6). If the optimal solution of (A7) is also applicable to (A6), then problem (A7) and (A6) are equivalent.
Suppose, on the contrary, assume the information causality constraint is active on partial time slots from 2 to . Suppose there exists such that both and . Then we have . Appendix A has proven that is non-increasing and is non-decreasing, we have
Combining the assumption , we have
which contradicts the information causality constraint of problem (A6). Thus, the assumption is invalid. This completes the proof of Lemma A2. □
References
- Mitev, M.; Chorti, A.; Poor, H.V.; Fettweis, G.P. What physical layer security can do for 6G security. IEEE Open J. Veh. Technol. 2023, 4, 375–388. [Google Scholar] [CrossRef]
- Nguyen, L.-M.-D.; Vo, V.N.; So-In, C.; Dang, V.-H. Throughput analysis and optimization for NOMA Multi-UAV assisted disaster communication using CMA-ES. Wirel. Netw. 2021, 27, 4889–4902. [Google Scholar] [CrossRef]
- Dai, M.; Luan, T.H.; Su, Z.; Zhang, N.; Xu, Q.; Li, R. Joint channel allocation and data delivery for UAV-assisted cooperative transportation communications in post-disaster networks. IEEE Trans. Intell. Transp. Syst. 2022, 23, 16676–16689. [Google Scholar] [CrossRef]
- Gao, Y.; Yuan, X.; Yang, D.; Hu, Y. UAV-assisted MEC system with mobile ground terminals: DRL-based joint terminal scheduling and UAV 3D trajectory design. IEEE Trans. Veh. Technol. 2024, 73, 10164–10180. [Google Scholar] [CrossRef]
- Wu, M.; Xiao, Y.; Gao, Y.; Xiao, Y.; Gao, Y.; Xiao, M. Digital twin for uav-ris assisted vehicular communication systems. IEEE Trans. Wirel. Commun. 2023, 23, 7638–7651. [Google Scholar] [CrossRef]
- Dhakal, G.; Kumar, D.R.; Sahoo, S.; Shim, J.J. Litchi seed biowaste-derived activated carbon supporting matrix for efficient symmetric and asymmetric supercapacitors. IEEE BITS Inf. Theory Mag. 2023, 3, 67–79. [Google Scholar] [CrossRef]
- Umapathy, B.; Kalpana, G. A novel symmetric cryptographic method to design block complexity for data security. Comput. Electr. Eng. 2022, 104, 108467. [Google Scholar] [CrossRef]
- Jiang, R.; Han, S.; Yu, Y.; Ding, W. An access control model for medical big data based on clustering and risk. Inf. Sci. 2023, 621, 691–707. [Google Scholar] [CrossRef]
- Ghaffari, F.; Bertin, E.; Crespi, N.; Hatin, J. Distributed ledger technologies for authentication and access control in networking applications: A comprehensive survey. Inf. Sci. 2023, 50, 100590. [Google Scholar] [CrossRef]
- Oesch, S.; Ruoti, S. That was then, this is now: A security evaluation of password generation, storage, and autofill in browser-based password managers. In Proceedings of the 29th USENIX Conference on Security Symposium, Boston, MA, USA, 12–14 August 2020; pp. 2165–2182. [Google Scholar]
- Xiao, Q.; Zhao, J.; Feng, S.; Li, G.; Hu, A. Securing NextG networks with physical-layer key generation: A survey. Secur. Saf. 2024, 3, 2023021. [Google Scholar] [CrossRef]
- Mucchi, L.; Jayousi, S.; Caputo, S.; Panayirci, E.; Shahabuddin, S.; Bechtold, J.; Morales, I.; Stoica, R.-A.; Abreu, G.; Haas, H. Physical-layer security in 6G networks. IEEE Open J. Commun. Soc. 2021, 2, 1901–1914. [Google Scholar] [CrossRef]
- Schuld, M.; Killoran, N. Quantum machine learning in feature Hilbert spaces. Phys. Rev. Lett. 2019, 122, 040504. [Google Scholar] [CrossRef] [PubMed]
- Kamboj, A.K.; Jindal, P.; Verma, P. Machine learning-based physical layer security: Techniques, open challenges, and applications. Wirel. Netw. 2021, 27, 5351–5383. [Google Scholar] [CrossRef]
- Sun, X.; Ng, D.W.K.; Ding, Z.; Xu, Y.; Zhong, Z. Physical layer security in UAV systems: Challenges and opportunities. IEEE Wirel. Commun. 2019, 26, 40–47. [Google Scholar] [CrossRef]
- Wang, J.; Wang, X.; Gao, R.; Lei, C.; Feng, W.; Ge, N.; Jin, S.; Quek, T.Q.S. Physical layer security for UAV communications: A comprehensive survey. China Commun. 2022, 19, 77–115. [Google Scholar] [CrossRef]
- Li, J.; Kang, H.; Sun, G.; Liang, S.; Liu, Y.; Zhang, Y. Physical layer secure communications based on collaborative beamforming for UAV networks: A multi-objective optimization approach. In Proceedings of the IEEE INFOCOM 2021—IEEE Conference on Computer Communications, Vancouver, BC, Canada, 10–13 May 2021; pp. 1–10. [Google Scholar]
- Cao, K.; Ding, H.; Wang, B.; Lv, L.; Tian, J.; Wei, Q.; Gong, F. Enhancing physical-layer security for IoT with nonorthogonal multiple access assisted semi-grant-free transmission. IEEE Internet Things J. 2022, 9, 24669–24681. [Google Scholar] [CrossRef]
- Gao, N.; Han, Y.; Li, N.; Jin, S.; Matthaiou, M. When physical layer key generation meets RIS: Opportunities, challenges, and road ahead. IEEE Wirel. Commun. 2024, 31, 355–361. [Google Scholar] [CrossRef]
- Wu, M.; Xiao, Y.; Gao, Y.; Xiao, M. Throughput maximization for UAV-enabled mobile relaying systems. IEEE Trans. Wirel. Commun. 2016, 64, 4983–4996. [Google Scholar]
- Wang, Q.; Chen, Z.; Mei, W.; Fang, J. Improving physical layer security using UAV-enabled mobile relaying. IEEE Wirel. Commun. Lett. 2017, 6, 310–313. [Google Scholar] [CrossRef]
- Zhang, G.; Wu, Q.; Cui, M.; Zhang, R. Securing UAV communications via joint trajectory and power control. IEEE Trans. Wirel. Commun. 2019, 18, 1376–1389. [Google Scholar] [CrossRef]
- Yuan, Z.; Yang, Y.; Wang, D.; Ma, X. Energy-efficient trajectory optimization for UAV-enabled cellular communications based on physical-layer security. Aerospace 2022, 9, 50. [Google Scholar] [CrossRef]
- Wang, J.; Zhou, X.; Zhang, H.; Yuan, D. Joint trajectory design and power allocation for UAV assisted network with user mobility. IEEE Trans. Veh. Technol. 2023, 72, 13173–13189. [Google Scholar] [CrossRef]
- Rao, B.; Hu, J.; Al-Nahari, A.; Yang, K.; Jäntti, R. On the physical layer security of UAV-aided backscatter communications. IEEE Wirel. Commun. Lett. 2023, 13, 274–278. [Google Scholar] [CrossRef]
- Wang, D.; Bai, B.; Zhang, G.; Han, Z. Optimal placement of low-altitude aerial base station for securing communications. IEEE Wirel. Commun. Lett. 2019, 8, 869–872. [Google Scholar] [CrossRef]
- Wang, D.; Yang, Y. Joint obstacle avoidance and 3D deployment for securing UAV-enabled cellular communications. IEEE Access 2020, 8, 67813–67821. [Google Scholar] [CrossRef]
- Zhou, Y.; Yeoh, P.L.; Chen, H.; Li, Y.; Schober, R.; Zhuo, L.; Vucetic, B. Improving physical layer security via a UAV friendly jammer for unknown eavesdropper location. IEEE Trans. Wirel. Commun. 2018, 67, 11280–11284. [Google Scholar] [CrossRef]
- Chen, Y.; Liu, G.; Zhang, Z.; He, L.; He, S. Improving physical layer security for multi-UAV systems against hybrid wireless attacks. IEEE Trans. Veh. Technol. 2023, 73, 7034–7048. [Google Scholar] [CrossRef]
- Huang, S.; Huang, X.; Chen, W.; Zhao, S. Physical layer security of vehicular networks with cooperative jamming helpers. Phys. Commun. 2022, 53, 101762. [Google Scholar] [CrossRef]
- Li, A.; Zhang, W.; Dou, S. UAV-enabled secure data dissemination via artificial noise: Joint trajectory and communication optimization. IEEE Access 2020, 8, 102348–102356. [Google Scholar] [CrossRef]
- Li, B.; Zhang, M.; Rong, Y.; Han, Z. Artificial noise-aided secure relay communication with unknown channel knowledge of eavesdropper. IEEE Trans. Wirel. Commun. 2021, 20, 3168–3179. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2026 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license.