Abstract
The rapid growth of wireless devices, the expansion of the Internet of Things, and the aggregate demand for Ultra-Reliable Low-Latency communications (URLLC) are driving the improvement of next-generation wireless systems. One promising emerging technology in this area is cell-free massive Multiple Input Multiple Output (maMIMO) networks. The distributed nature of Access Points presents unique security challenges that must be addressed to unlock their full potential. This paper studies the key security concerns in Cell Free Massive MIMO (CFMM) networks, including eavesdropping, Denial-of-Service attacks, jamming, pilot contamination, and methods for enhancing Physical Layer Security (PLS). We also provide an overview of security solutions specifically designed for CFMM networks and introduce a case study of a Reconfigurable Intelligent Surface (RIS)-aided secure scheme that jointly optimizes the RIS phase shifts with the artificial noise (AN) covariance under power constraints. The non-convex optimization problem is solved via the block coordinate descent (BCD) alternating optimization scheme. The combined RIS, AN, and beamforming configuration achieves a balanced trade-off between security and energy performance, resulting in moderate improvements over the individual schemes.
1. Introduction
The development of next-generation networks [1,2] has led to an increasing demand for hypermobile connectivity with higher data rates, higher connection density, low latency, and improved security, which transcend the capabilities of existing cellular networks. Next-generation networks are poised to support advanced technologies; however, ensuring privacy, security and operational efficiency presents significant challenges, with trust being a critical element in addressing these issues. Massive MIMO (maMIMO) technology [3,4] has been proposed to enhance the spectral and energy efficiency of cellular systems through straightforward processing. maMIMO is set to enhance user experience and enable new mobile services, remaining a key technology for both developed and emerging markets over the next decade [5]. Spatial multiplexing, spatial diversity, and beamforming are transmission methods offered by the MIMO system in the channel [6]. Channel hardening occurs when the number of antennas increases; the wireless channels behave more like a deterministic channel rather than a fading one, ensuring unpredictable behavior [4].
However, the deployment of numerous distributed antenna systems (DAS), commonly referred to as cell-free maMIMO (CFMM) or distributed MIMO, raises concerns about how to effectively combine high-bandwidth spectrum with massive connectivity [7]. Using MIMO in next-generation wireless networks faces some challenges, including propagation loss issues, hardware cost, and algorithmic complexities, as well as high power consumption, channel estimation, and feedback overhead, in addition to security issues [8]. A key security challenge in maMIMO systems [8] is the heightened risk of physical layer attacks. These include pilot contamination, which disrupts channel estimation and data integrity, as well as difficulties in distinguishing and mitigating unlicensed access and malicious activities due to the expanded attack surface [9]. The estimation error can converge to zero by utilizing large-scale arrays and independent channel paths. The number of independently measured scattered paths can increase linearly with the area of coverage. By increasing the number of antennas, inter-user interference can average out and become negligible due to the randomness in phase shifts [9].
CFMM is an essential technology expected to meet the growing demands by providing seamless coverage and improving spectral efficiency (SE). It does this by deploying many dispersed access points (APs) that can serve multiple users simultaneously, without the constraints of cell boundaries. The main benefits of CFMM include improved coverage, high SE, enhanced reliability, and consistent quality of service (QoS). Decreasing both spatial correlation and average path losses through the successful reduction in broadcast distances is another benefit of CFMM systems [10]. While CFMM networks are less resilient to active attacks than co-located maMIMO [11], which also offers promising performance improvements, they introduce new security challenges due to their decentralized architecture, dense deployment, and increased complexity. Table 1 presents a selection of papers related to the challenges and requirements of next-generation networks (CFMM is one of the futuristic technologies of the next generation), outlining their core research contributions and providing brief descriptions.

Table 1.
The work related to next-generation challenges and requirements.
Recently, several randomness-driven pilot assignment algorithms have been proposed and demonstrated to provide strong performance, even in environments with only a few dominant paths or partially deterministic propagation. In particular, ref. [25] introduced a game-theoretical, randomness-based pilot selection framework that effectively mitigates pilot contamination in crowded time division duplex (TDD) maMIMO systems. Owing to its robustness, scalability, and applicability to practical deployment scenarios, this approach is highly promising, widely applicable, and is anticipated to receive increasing attention in the field. Although CFMM systems offer large coverage areas and reduced interference, scaling them in a frequency division duplex (FDD) setting [26] presents challenges due to high computational complexity for tasks like estimating the channel and the power distribution. Authors of [26] proposed a scalable FDD-based cell-free network with angular reciprocity and dynamic cooperation clustering (DCC), showing through simulations that it outperforms conventional schemes, providing significant improvements in spectral and energy efficiency.
This paper examines the security challenges and summarizes proposed strategies to mitigate them. It explores the threats, vulnerabilities, and countermeasures necessary for ensuring secure communication in CFMM systems. The main contribution of the paper includes (1) A comprehensive survey of security in CFMM networks, and (2) the case study and evaluation of a specific RIS-aided framework designed to address identified gaps.
The rest of the paper is organized as follows: Section 2 introduces the fundamentals of CFMM networks and Section 3 provides the security challenges, including eavesdropping attacks, jamming and DoS attacks, and pilot spoofing and contamination. The state-of-the-art techniques proposed to provide security solutions for CFMM systems are detailed in Section 4. The case study of the RIS-aided PLS scheme is introduced in Section 5. Finally, the conclusions and the future work are introduced in Section 6. Figure 1 shows the study outline.
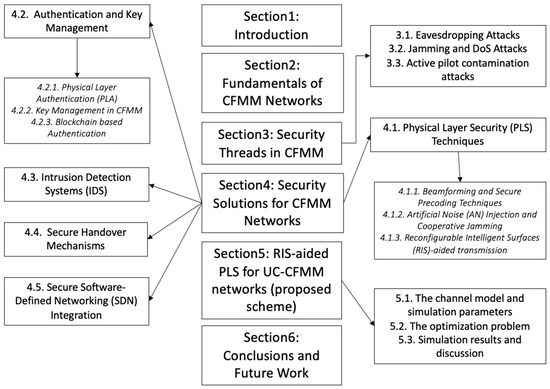
Figure 1.
The Paper Outline.
2. Fundamentals of CFMM Networks
Unlike conventional cellular networks that depend on specific base stations (BSs) or APs to serve users within designated cells, CFMM [27,28] eliminates the concept of “cells.” Instead, it employs multiple distributed low-power APs across a broad geographical area to meet users’ needs. Each AP is equipped with multiple antennas and is connected to a central processing unit (CPU) via high-speed backhaul links [27]. This approach significantly reduces inter-cell interference and improves the overall service quality across the entire coverage area [29], besides its capability to reduce mobile phone interference and enhance the macro-diversity [29] through ubiquitous and distributed APs. The backhaul network must support rapid data exchange to ensure low latency and high throughput. Both the backhaul and fronthaul (the links from users to APs) need to accommodate the high data rates generated by maMIMO systems [27].
Figure 2 shows a classic maMIMO (cellular system) versus a CFMM system [30]. The CPU coordinates all APs in the system. The APs exchange user data and channel state information (CSI) with the CPU, which collaborates to process the incoming signals and optimize transmission for each user. Accurate CSI is crucial for efficient signal processing in CFMM systems. It enables both the APs and the CPU to adjust their beamforming strategies, optimizing data transmission while minimizing both intra-cell and inter-cell interference. Each user in the network is served by a subset of APs chosen based on the user’s location and channel conditions [27].
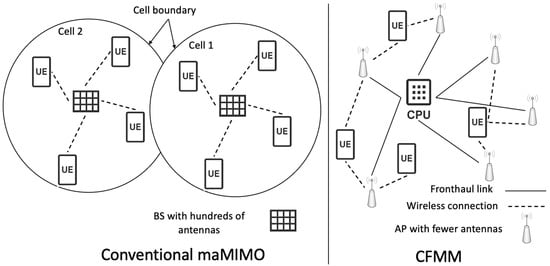
Figure 2.
Classic (Conventional MIMO) versus CFMM systems.
As users move, the group of APs that serve them changes dynamically, ensuring that they always receive service from the APs with the strongest signals. In coherent processing [31], the APs synchronize their transmissions, allowing signals from multiple APs to combine coherently at the user’s device, thereby increasing signal strength. In contrast, non-coherent processing involves each AP serving users independently. While this method is simpler, it is also less efficient. CFMM offers significant advantages over small-cell systems [32] in terms of maximum rate and power efficiency. To increase the reader’s knowledge, a valuable comparison between cellular, cell-free, and intelligent maMIMO is available in [16].
Cellular networks based on macro cells have served as the foundation of mobile systems since 3GPP Release 8 Long-term evolution (LTE), evolving into 5G NR starting with Release 15. Small-cell networks were introduced in Release 9 with femtocell support and were further developed through LTE-Advanced (HetNets) and feature enhancements in Releases 10 to 12, with continued progress into 5G via Integrated Access and Backhaul (IAB) in Release 16. The 3GPP has not formally defined CF or CFMM as standalone, branded network architectures. Instead, it focuses on standardizing the foundational technologies and functional splits that can support CF-like deployments. Several features introduced in Releases 16 to 18, such as coordinated multi-point (CoMP), multi-TRP (Transmission Reception Point), and distributed Radio Access Network (RAN), contribute toward achieving CF performance characteristics, although no dedicated specification currently exists. A comprehensive table of features organized by Release is also available in the 3GPP Work Plan. Table 2 lists the relevant 3rd Generation Partnership Project (3GPP) standards for each network type.

Table 2.
Relevant 3GPP standards for co-located MIMO, cell-free massive MIMO (CFMM), and small cell networks.
CFMM faces several implementation challenges, particularly in ultra-dense scenarios. The key aspects of these environments include simplified system design, efficient processing, and flexible resource scalability with low complexity, limitations in fronthaul, handling massive access, maintaining synchronization, and efficient channel acquisition [33]. Scalability is a key challenge for CFMM because deploying numerous APs over a broad area, along with the necessary infrastructure for coordination and backhaul, requires careful planning. Efficient management of resources, such as power, frequency, and AP coordination, is vital for scaling up CF networks while maintaining high performance levels [28].
CFMM relies on users transmitting pilot (or reference) signals to assist APs in estimating communication channels [27,31]. However, when multiple users use the same pilot sequence, it leads to pilot contamination, creating a significant challenge. Pilot contamination and hardware impairments can result in a non-zero estimation error floor. The increasing number of antennas and radio frequency (RF) chains has significantly raised the complexity of symbol detection in the receiver5. Effectively managing these issues and selecting the right UE hardware are crucial for maintaining system performance.
Paper [13] discusses CFMM system models, key performance metrics like energy efficiency (EE) and channel hardening, and outlines current research trends, open issues, and lessons for advancing this technology in wireless communications. Radio stripes (RS) [34] are a sequential fronthaul network used in CFMM systems. They connect APs to a CPU via a single cable, offering advantages over traditional star topologies. Paper [35] provides a comprehensive overview of the principles and recent advancements in CF and RS networks, discussing key processes such as uplink (UL) pilot transmission, channel estimation (CE), and data exchange between APs and user equipment (UE). Table 3 provides a comparison of CFMM security with co-located MIMO and small cell networks.

Table 3.
Comparison of CFMM, conventional MIMO, and small cell networks.
CFMM is believed to benefit from channel hardening and favorable propagation [31], like cellular MIMO systems. However, these properties are heavily dependent on the propagation environment. Research presented in [41] indicates that channel hardening is generally weak, although deploying multiple antennas per AP can enhance it. Favorable propagation is more likely to occur with smaller path loss exponents, higher antenna density, and spatially separated users. The main takeaway is that channel hardening and favorable propagation should not be relied upon for calculating achievable rates. Instead, CFMM designs should incorporate achievable throughput expressions and resource management schemes that account for impairments such as spatial correlation, pilot contamination, and estimation errors. Achievable rate bounds can be derived using low-complexity linear processing methods [42]. Furthermore, optimal pilot design [43] is crucial; signal detection techniques, including maximum ratio (MR), zero forcing (ZF), and minimum mean square error (MMSE), must be carefully selected to achieve a balance between performance and complexity [5]. In addition to these challenges, the next section will discuss the security issues faced in CFMM networks.
3. Security Threats in CFMM Networks
A standard security system is designed to ensure data integrity, confidentiality, availability, and authentication while protecting against both passive and active attackers [44]. The distributed architecture of the CFMM system offers distinct advantages in terms of secrecy compared to traditional cellular networks. Because APs are geographically dispersed, they create highly unique and uncorrelated wireless channels for different users and potential eavesdroppers. Increasing the number of APs enhances the secrecy rate by providing greater spatial diversity and enabling better alignment of signal energy toward legitimate users while creating interference for eavesdroppers. This spatial diversity makes it significantly harder for eavesdroppers to capture useful information, thereby increasing the system’s secrecy capacity (SC) [11]. However, the distributed architecture of CFMM also introduces certain vulnerabilities. For instance, if an AP is physically compromised, an attacker could potentially take control of the network and access sensitive information. Additionally, APs are often deployed in uncontrolled environments [45], such as rooftops or street furniture, which raises the risk of physical tampering. The lack of a central base station to manage the APs adds complexity to network management and security. The distributed APs must work together to coordinate without creating security gaps that attackers could exploit. The most significant challenges facing CFMM networks include eavesdropping, jamming, denial-of-service (DoS) attacks, and pilot contamination.
3.1. Eavesdropping Attacks
Eavesdropping, whether passive or active [46], is a significant concern in wireless networks since it involves unauthorized parties intercepting communications between legitimate users [47]. The absence of central control in CFMM makes it particularly difficult to secure all communication links. Furthermore, with APs deployed in proximity, an eavesdropper can easily position itself nearby to exploit vulnerabilities at the physical layer. Sophisticated techniques for eavesdropping, especially passive attacks, pose substantial threats to data confidentiality. These methods allow attackers to listen in on communications without interference. On the other hand, active eavesdropping occurs when an eavesdropper not only attempts to intercept transmissions but also actively transmits signals to disrupt or manipulate communication. This presents a more significant security threat compared to passive eavesdropping [48].
3.2. Jamming and DoS Attacks
Malicious entities often attempt to disrupt communication channels through jamming or spoofing. Jamming [49,50] and DoS attacks [22] aim to overwhelm the network with excessive noise or traffic, resulting in service disruption and reducing the reliability and availability of the network. These types of attacks pose significant risks to CFMM networks due to the numerous APs involved and the distributed nature of the system. In jamming attacks, an adversary transmits strong signals that interfere with legitimate user communications, rendering the network unusable. For instance, a jammer may try to disrupt estimating the channel by sending jamming signals during the pilot transmission phase, introducing what is known as pilot contamination [51].
CFMM networks rely on coordination between multiple APs, so the compromise of even a single AP can severely degrade overall network performance and service quality. Furthermore, the decentralized structure of CFMM systems complicates the detection and mitigation of jamming attacks. The spatial diversity in maMIMO technology makes it more challenging for a jammer to simultaneously disrupt communication between all APs and their users. Because the APs are spread over a wide area, a localized jamming attack may only affect a small subset of APs, while others continue to function normally. To effectively disrupt communication, a jammer would need to target multiple locations at the same time. Paper [49] presents a thorough survey of jamming attacks and anti-jamming strategies in various wireless networks.
3.3. Active Pilot Contamination Attacks
One reason for pilot contamination is that attackers can transmit signals during the pilot phase, deceiving APs and causing them to inaccurately estimate the CSI. This leads to degraded communication quality, reduced spectral efficiency, and potential eavesdropping opportunities. Pilot contamination is particularly problematic in CFMM systems due to the lack of coordination among APs, which increases the likelihood of attackers injecting false pilot signals into multiple APs simultaneously [52]. Both pilot contamination and active pilot attacks significantly undermine the secrecy performance of maMIMO systems [53]. The literature contains extensive research on pilot contamination attacks [11,54], pilot spoofing attacks (PSA) [55,56], and optimal pilot strategies [43].
Pilot contamination is a threat during both the training and data transmission phases. Estimation errors in high-dimensional channels can result in inaccurate detection/beamforming during transmission and reception, potentially leading to the leakage of confidential messages to eavesdroppers and compromising the system’s security [57]. To detect spoofing attacks, special tests are required, such as using channel virtual representation with Neyman-Pearson testing in static environments and machine learning-based schemes in dynamic environments [58]. Table 4 highlights the differences between the three attack types. The next section explores different facets of security in cell-free (CF) networks to ensure secure and reliable communication in next-generation wireless networks.

Table 4.
Eavesdropping vs. Jamming/DoS vs. Active Pilot Contamination.
4. Security Solutions for CFMM Networks
Addressing the security challenges in CFMM networks requires a combination of techniques from both the physical layer and higher network layers. Key countermeasures include, in addition to PLS, distributed authentication, trust management, robust jamming detection and mitigation, and advanced pilot contamination mitigation. Additionally, mechanisms such as hybrid relay-reflecting intelligent surfaces (HR-RIS) [59] are vital for securing APs against physical tampering and unauthorized access. These techniques help ensure the integrity of APs in untrusted environments. The main challenges in these networks arise from conflicting objectives: maximizing information transfer (data rate), providing sufficient power transfer for energy harvesting by legitimate users, and mitigating the impact of active eavesdroppers48. This section provides insights into various aspects of CF security, covering everything from physical layer security to energy efficiency optimization and solutions for addressing active eavesdropping and other security challenges.
4.1. Physical Layer Security (PLS) Techniques
Network-layer cryptography faces challenges in dynamic networks, leading to increased interest in PLS30, which offers the potential for perfect security without the complexities of traditional encryption methods [44]. PLS [60,61,62,63] refers to a set of techniques and strategies used to secure communication at the physical layer of the Open Systems Interconnection (OSI) model. This layer, being the lowest in the OSI model, is responsible for the actual transmission and reception of raw bit streams over physical mediums such as cables or wireless channels. PLS aims to protect information from eavesdroppers and unauthorized users by utilizing the unique characteristics of the physical medium. Additionally, PLS has lower computational and communication overhead compared to conventional cryptographic methods, and it can be integrated with higher layers to provide a multi-layered security approach for improved quality of security (QoSec) [64]. PLS leverages the unique properties of wireless channels such as fading, noise, and interference to enhance security at the physical layer in dynamic environments [65]. For instance, CFMM can exploit the inherent randomness present in wireless channels to generate unique keys that are difficult for attackers to guess. Since the channel response between a user and an AP is reciprocal (the same in both directions), this characteristic can be utilized to generate a shared secret key. One significant advantage of PLS is its ability to reduce computational costs and resource consumption [66].
PLS techniques are classified based on various criteria, including fading models, types of eavesdroppers, diversity, and specific applications [65]. For 6G technologies [67], PLS includes channel-based approaches, power allocation strategies, and signal processing methods. Channel-based approaches [60] utilize the characteristics of communication channels for various purposes, including secret key generation and distribution, adaptive coding and modulation, physical layer authentication, dynamic power control, and channel adaptation. They also employ techniques such as artificial fading and channel randomization. These approaches offer real-time adaptability without requiring significant computational power or excessive overhead [65]. On the other hand, power allocation based PLS strategies [68,69] focus on minimizing power consumption while enhancing energy efficiency and ensuring security requirements are met [55]. These power allocation methods, which demonstrate increased resilience to eavesdropping, can be used in conjunction with techniques like artificial noise (AN), MIMO systems, beamforming, cooperative jamming, relay networks, energy harvesting, and rate allocation schemes [2,70].
PLS, which utilizes signal processing [71], is a promising solution for securing wireless communications, particularly in resource-constrained or latency-sensitive environments. As wireless networks advance, these methods are anticipated to play a more significant role in securing next-generation networks. Signal processing based PLS encompasses various techniques, including beamforming and directional transmission, secure precoding, AN injection, channel CSI exploitation, cooperative jamming, secret key generation from physical layer attributes, and frequency hopping and spread spectrum techniques. The authors of [71] presented a comprehensive summary of existing surveys on PLS schemes and defined important secrecy performance metrics such as SC, secrecy outage probability (SOP), and secure energy efficiency (SEE). Book [72] provides an in-depth understanding of the concepts, frameworks, and methods of PLS, as well as its implementation in 5G and other evolving wireless networks. The following subsections discuss key PLS techniques applicable in CFMM networks.
4.1.1. Beamforming and Secure Precoding Techniques
Beamforming [73,74,75,76], a technique that directs the transmission and reception of signals toward specific directions by regulating the phase or amplitude of the original signal. The main categories of beamforming structures are analog (or radio frequency, RF) beamforming, digital beamforming (also known as digital precoding), and hybrid beamforming architectures. While analog beamforming is simple, it is not used in maMIMO due to its performance limitations. Digital beamforming offers better performance than the analog approach but comes with increased complexity. Hybrid beamforming [77] combines the advantages of analog and digital beamforming, making it a common choice in maMIMO systems [78]. Hybrid beamforming emerges as a practical solution for balancing complexity and performance. Secure and adaptive beamforming strategies further fortify the system against eavesdropping and jamming, especially when combined with intelligent antenna selection and power control. Precoding techniques in maMIMO systems, whether linear or nonlinear, enable multi-antenna systems to transmit multiple data streams simultaneously [79]. These techniques involve shaping the transmitted signal based on the known CSI to enhance signal reception at the intended receiver while disrupting it for potential eavesdroppers [73]. Paper [73] provides a comprehensive survey of precoding techniques in maMIMO and beyond 5G networks, covering both linear and nonlinear precoding, machine learning-based precoding algorithms, and strategies for peak-to-average power ratio (PAPR) optimization.
Bit error rate (BER) for real-time implementation is reduced by combining the data detection scheme with various iterative algorithms, achieving near-optimal performance with fewer iterations and significantly reduced complexity across different CSI conditions and modulation schemes [75]. By concentrating transmission energy in specific directions, beamforming not only reduces the likelihood of eavesdropping and jamming attacks but also maximizes the probability of successful signal detection [80]. Implementing secure beamforming techniques requires consideration of the distributed nature of CFMM and the coordination between APs to maintain strong performance in adaptive antenna selection (AAS) [81,82]. Dynamic selection of antennas based on channel quality can help mitigate the effects of jamming. Additionally, beam selection and management using AI [62]. reduces the overhead and complexity associated with beamforming techniques.
Additionally, pilot decontamination strategies are characterized by four key elements: pilot design, pilot allocation strategies, channel estimation techniques, and precoding methods [83]. The joint design of beamforming and user-centric (UC) clustering with multiple cooperating CPUs demonstrates significant performance improvements over traditional architectures, under-scoring the advantages of multi-CPU cooperation in CFMM systems [84]. Conjugate beamforming combined with precoding normalization [85] helps eliminate the need for downlink pilot signals by bridging the performance gap typically associated with conventional conjugate beamforming without training.
Additionally, several studies [86,87,88] present robust approaches to enhance the performance of CF integrated sensing and communication (ISAC) MIMO systems, where distributed APs collaborate in both communication and target sensing tasks. Joint sensing and communication (JSC) beamforming, when integrated with power allocation strategies, can achieve near-optimal SINR for communication and SNR for sensing. However, limitations exist in these studies: study [86] assumes perfect CSI, neglects clutter and multipath effects in sensing, and does not address scalability; [87] relies on idealized propagation models without accounting for practical hardware constraints such as fronthaul limitations; and [88] focuses solely on monostatic sensing with co-located APs, omitting bistatic or multi-static scenarios. Moreover, study [89] leverages machine learning (ML) and deep learning (DL) to dynamically adapt beamforming in evolving ISAC environments, thereby reducing computational overhead. Nevertheless, this approach suffers from challenges, including data dependency, poor generalization to unseen scenarios, and high training complexity.
As a summary, beamforming and secure precoding significantly enhance security and performance in CFMM systems, but their real-world implementation is challenged by several practical issues. These include high computational complexity, real-time and scalability constraints, coordination overhead among distributed APs, and imperfections in CSI due to pilot contamination.
AI-based methods (e.g., DL and graph neural networks (GNNs)) help reduce signaling overhead but are limited by the need for quality training data, generalization ability, and high processing power. Distributed learning can also suffer from inconsistent performance due to local data limitations. Although hybrid beamforming cuts hardware costs, it demands precise analog-digital coordination. Power allocation strategies face trade-offs between performance and energy limits. Overall, while promising in theory, practical deployment requires more adaptive, efficient, and lightweight solutions to overcome these barriers. Table 5 provides a summary of works related to beamforming and secure precoding in CFMM networks.

Table 5.
Beamforming and secure precoding in CFMM networks.
4.1.2. Artificial Noise (AN) Injection and Cooperative Jamming
AN injection, as described in references [46,60], is a technique in which noise is intentionally added to a transmission to confound eavesdroppers while allowing legitimate users to decode the intended message. In the CFMM system, artificial noise can be distributed across multiple APs, which further complicates the process for eavesdroppers attempting to filter out the noise and intercept the communication. By carefully optimizing the power and direction of the noise, legitimate users can maintain a favorable signal-to-noise ratio (SNR), while potential eavesdroppers face a lower SNR, making it more difficult for them to decode the message. The power control method enhanced with AN introduced in [98] boosts the lowest achievable secrecy rate across users and greatly enhances security in CFMM systems facing passive eavesdropping threats. In related work [100], AN is used to shrink the region around users where eavesdropping might occur. A secure beamforming method is introduced to guarantee a minimum SINR for legitimate users while reducing the eavesdropper’s SINR. The idea of cooperative AN is introduced in [101], where all APs spread the AN signal in the null space of the users’ channel to complicate eavesdroppers’ operation without complex beamforming. As a modification of this approach, the APs are divided into two groups: one for transmitting AN and the other for serving the legitimate users, ensuring perfect incorporation into real-world conditions. In CFMM, the APs can cooperate to detect and cancel jamming signals.
For instance, if one AP detects interference, it can share this information with other APs in the network, which can then take corrective measures to avoid disruption. If one AP detects abnormal interference patterns, it can alert other APs in the vicinity to adjust their transmission strategies accordingly. Cooperative jamming [65] uses friendly nodes in the network to actively interfere with potential eavesdroppers. These cooperative nodes transmit interference signals that degrade the eavesdropper’s channel, making it more difficult for them to intercept the communication. Legitimate users can still receive and decode the information because they have a higher SNR relative to the eavesdropper. The system PLS defines two roles of cooperative nodes in the network: the first role is cooperative relaying, and the other is working as a cooperative jammer. Traditional AN can degrade the legitimate channel’s capacity and poses challenges in selecting optimal designs. To overcome these issues, as an alternative recent study [102] introduced a non-orthogonal AN scheme using a pilot information codebook. This approach allows the receiver to identify and cancel the transmitted non-orthogonal AN signal.
Based on the channel state. It boosts secrecy capacity without adding noise to the legitimate channel (without affecting BER), as confirmed by theoretical analysis and simulation results. Table 6 discusses the contributions and limitations of works related to AN injection scheme in CFMM networks.

Table 6.
Artificial noise (AN) injection schemes for CFMM networks.
4.1.3. Reconfigurable Intelligent Surfaces (RIS)-Aided Transmission
The research community has transitioned its focus toward post-5G network architectures, with significant emphasis on physical layer advancements for 6G. Among the most promising technologies are: (1) CFMM systems and (2) intelligent reflecting surfaces (IRS), also referred to as Reconfigurable Intelligent Surfaces (RIS) [106]. These paradigms have emerged as leading physical layer candidates for 6G communication systems and are concurrently regarded as strong enablers for PLS in next-generation wireless networks [38]. RIS [107,108] is recommended for CFMM networks to address the challenges of harsh propagation conditions by maximizing the total user rate through optimally designed beamforming techniques.
The passive nature of RIS technology makes it resilient to receiver noise, facilitates easy deployment, and requires less complex signal processing [71]. Figure 3 illustrates the conceptual diagram of RIS-aided CFMM propagation. RIS-aided CF networks [109] offer several advantages: they enhance signal strength and coverage, improve network throughput and latency, allow for dynamic network adjustments, reduce costs and power consumption, and ultimately increase network security [9].
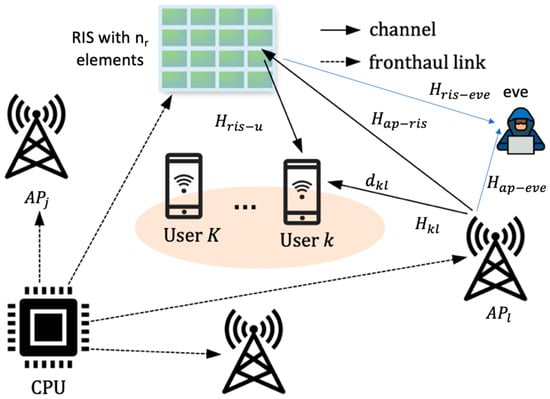
Figure 3.
Conceptual diagram of RIS-aided CFMM propagation.
Combining AN with multiple RISs improves the secrecy rate by finding optimal AP beamforming and joint optimization of RIS phase shift and AN matrix [37,71]. The implementation of IRS effectively enhances the achievable lower bound in the presence of pilot contamination attacks. Furthermore, an increased correlation coefficient between the legitimate and eavesdropping channels does not uniformly degrade the lower bound. Conversely, the secret key rate exhibits a decreasing trend with the escalation of Eve’s transmit power [110].
Table 7 summarizes the work related to this subsection. As indicated in Table 6, efficient implementation of RIS-assisted CFMM for security requires accurate CSI, intelligent beamforming, robust optimization, and scalable deployment strategies. Scientific research directions should focus on practical hardware constraints, real-time adaptability, and AI-driven security enhancements. Showing clear performance gains when combining IRS-aided passive beamforming with AN [111]. However, practical deployment challenges remain, especially regarding incomplete CSI, algorithm scalability, hardware non-idealities, and transmit power trade-offs.

Table 7.
RIS-aided CFMM networks.
4.2. Authentication and Key Management
Authentication techniques [118] play a crucial role in MIMO systems by verifying the identity of users, devices, and network components. In traditional cellular systems, authentication typically occurs between users and a central BS. However, in CFMM networks, multiple distributed APs collaborate without a central control node. This decentralized architecture adds complexity to the authentication process, necessitating more advanced techniques to ensure security while maintaining system efficiency. By leveraging spatial diversity, channel reciprocity, and decentralized architectures, CFMM can provide robust security against evolving wireless threats. The findings in [118] highlight the dependence of authentication performance on the antenna array size, demonstrating that the mutual information-based authentication rate increases as the number of antennas grows. UEs must authenticate themselves to the network to confirm its legitimacy, typically using public-key infrastructure (PKI) or certificate-based systems. Additionally, the network must authenticate itself to the user to prevent security breaches, as malicious APs may attempt to impersonate legitimate ones. Authentication methods are categorized into three main types: traditional cryptographic methods including symmetric and asymmetric cryptography [119,120], physical layer authentication (PLA) [121,122,123] and emerging technologies such as blockchain based authentication [45,124]. In distributed systems like CFMM networks, group-based authentication can be implemented, where a cluster of APs collaborates to authenticate a user, sharing resources and information to enhance security and reliability [125,126]. Due to the large number of antennas and the decentralized architecture of CFMM [127,128], it is essential to guarantee that only authorized devices can access the network and that cryptographic keys are exchanged securely.
4.2.1. Physical Layer Authentication (PLA)
New security methods have emerged at the physical layer, offering lightweight alternatives to traditional techniques. PLA includes three typical architectures [121]: authentication leveraging CSI, device-specific RF features, and identity watermarking. It is observed that channel-based PLA exhibits higher sensitivity to variations in the communication environment and device mobility. In contrast, RF fingerprinting (RFF)-based approaches [122] encounter challenges related to robust feature extraction and classification accuracy in complex network scenarios. Watermark-based PLA shares a structural similarity with traditional cryptographic techniques such as digital signatures, but its security is grounded in key equivocation principles.
Physical layer information from the wireless channel can be captured using metrics like CSI, Received Signal Strength (RSS), channel impulse response (CIR), or signal phase [129]. These characteristics are intrinsically linked to both the wireless environment and the hardware of the device, which makes them stable and resistant to user manipulation. Consequently, they can be reliably used to identify wireless transmitters [123]. The survey [122] offers a comprehensive summary of PLS methods for ensuring confidentiality, authentication, and malicious node detection. It introduces a structured taxonomy that further classifies each of these categories. the paper reviews recent advancements in channel-based, device-based, and tag-based PLA, and examines how PLA integrates with emerging physical layer technologies.
CSI-based approaches [130] rely on the exceptional characteristics of the physical communication channel, which vary over time and space. By using the shared wireless channel as a source of randomness, legitimate users can create identical keys that are challenging for eavesdroppers to predict or replicate. The concept of channel reciprocity [131] refers to the phenomenon where the channel characteristics between two communicating parties are the same in both directions of transmission, uplink and downlink. In CFMM, this property can be leveraged to generate secret keys for encryption without relying on higher-layer cryptographic algorithms [132]. The reciprocity property enables legitimate users to observe the same impulse response within the channel’s coherence time, whereas the inherent variability of the wireless channel has a direct impact on the achievable generating key rate [133]. If legitimate users and an eavesdropper experience different channel condition, signal processing techniques [134] are utilized to adapt the transmission in a way that enhances security.
By employing dynamic and adaptive coding schemes, legitimate users take advantage of the distinct channel conditions to gain an edge over the eavesdropper. With cooperative transmit power allocation at APs the achievable SC is maximized. Physical layer attributes [60,135] such as channel fading, noise, Doppler shifts, the radio channel entropy [136], and channel correlation characteristics [137] can serve to generate shared secret keys between legitimate users, which are unique to the specific communication channel and difficult for eavesdroppers to predict. Techniques such as channel quantization and randomness extraction are used to convert the physical attributes into usable cryptographic keys [131]. In maMIMO systems, having many antennas provides a high spatial resolution, which can be effectively used for generating secure keys. As the antenna count grows, sophisticated signal processing schemes like precoding are used to direct the transmitted energy [132]. For confidentiality, both keyless and key-based approaches were outlined, including techniques such as secrecy-capacity codes and AN. In practice, key-less PLA [61] ensures confidentiality by directly encoding data over the communication channel. As a result, system performance heavily relies on knowledge of the channel’s characteristics, like the SNR, and the capabilities of prospective eavesdroppers. However, accurately assessing an attacker’s profile in advance is often challenging. If an eavesdropper turns out to be more powerful than anticipated, such as possessing numerous antennas or a low-noise receiver, the actual security capacity may fall below the intended data rate, rendering the system inherently insecure. In contrast, key-based PLA relies on well-established symmetric encryption methods to ensure confidentiality, concentrating exclusively on generating keys through channel reciprocity-based techniques. This separation enables flexible key renewal on demand or adjustment of key strength when needed. For these reasons, key-based PLA is more suitable for integration into a practical and comprehensive security framework [136].
Paper [129] proposes an efficient physical layer key generation technique that utilizes the RSS of wireless signals to establish shared keys between communicating parties, based on the channel reciprocity principle. The authentication mechanism’s capability to dynamically switch between CSI-based and cryptographic authentication, contingent on the real-time CSI condition, enhances its adaptability to environments with intermittent or periodic mobility. By continuously monitoring the CSI state, the system can also detect unauthorized physical perturbations or mobility of wireless nodes, thereby enabling anomaly detection and triggering alerts for potential security breaches [138]. Location-based authentication and fingerprint embedding in MIMO systems [131] achieve strong security even with imperfect CSI. Paper [139] examines the application of AN in fingerprint embedded authentication under the condition of imperfect CSI at both the transmitter and receiver. While AN improves security, its effectiveness diminishes as CSI quality worsens. The analysis in [139] highlights operating regimes that optimize AN use, track the adversary’s knowledge of the key, and suggest potential applications for privacy amplification, while noting that increased AN power may disrupt the adversary’s key recovery. Reference [64] discusses the integration of localization-based node authentication with secret key generation (SKG). Additionally, authentication techniques in MIMO systems and adaptive PLA have been studied from an information-theoretic standpoint in [118]. The combination of SKG with physical unclonable function (PUF)-based authentication protocols [140] offers a substantial reduction in both authentication and key generation latency when compared to conventional methods. The proposed authenticated encryption scheme, which incorporates SKG and a resumption protocol, enhances both security and latency performance. Additionally, several studies [123,141,142,143] explore PLA using ML techniques, highlighting their potential in improving wireless communication security [144]. The concept of multifactor authentication (MFA) [145,146,147] is also relevant here, as it strengthens security by combining multiple authentication factors—such as knowledge (something you know), possession (something you have), and inherence (something you are).
4.2.2. Key Management in CFMM
In the communication process, pilot signals used for channel estimation can act as a source of randomness for generating cryptographic keys. Both the UE and APs observe the received pilot signals and extract secret keys from these observations. Furthermore, as noted earlier, the inherent wireless channels noise and interference can enhance the randomness required to generate shared secret keys between UEs and APs [148]. Once authentication is established, whether by traditional cryptographic methods or by key-based PLA, the next step is to securely manage cryptographic keys [20]. A proper key management process includes four operations: key analysis, key assignment, key generation, and key distribution. To achieve this, public-key cryptography methods such as RSA [149,150] or Elliptic Curve Cryptography (ECC) enable the user and APs to securely establish shared secret keys over an insecure channel. This is accomplished using key exchange protocols like Diffie-Hellman (DH) or Elliptic Curve Diffie-Hellman (ECDH) [45], which allow two parties to generate a common shared key. In some scenarios, pre-shared keys may be utilized between the UE and the APs. While this method is less flexible and scalable, it can provide high security in closed environments. For highly secure systems, quantum key distribution [148,151] might be employed, taking advantage of quantum communication channels to exchange encryption keys in a manner that is fundamentally secure against eavesdropping. To ensure continued security, keys must be periodically refreshed. This prevents the reuse of compromised keys and enhances overall security.
In CFMM, key refresh mechanisms need to be synchronized across distributed APs to ensure seamless communication. If a user or AP is compromised, key revocation protocols must be in place to ensure that compromised keys can no longer be used. Revocation lists or blockchain-based methods can track and invalidate keys across the system. Distributed APs must be synchronized in their key management operations to prevent inconsistencies, which could lead to dropped connections or vulnerabilities [124]. Lightweight cryptographic protocols are premeditated to be computationally efficient while still providing strong security. These protocols reduce the processing load on APs and UEs while ensuring secure key exchanges and data encryption. Ensuring scalable key management without overloading the system is a challenge. Key exchange and management protocols must be efficient to avoid introducing excessive latency, which can degrade the performance of real-time applications. paper [152] examined a range of key management protocols designed for group communication in both wired and wireless networks. the paper analysis focused on identifying security vulnerabilities, evaluating the advantages and disadvantages of each protocol, and comparing their performance with related methods. However, due to the diverse requirements of different applications and environments, no single solution can address all challenges. Therefore, the most appropriate protocol should be selected based on the specific needs of each application.
4.2.3. Blockchain-Based Authentication
As a decentralized system, blockchain [45,124,147,153] can be utilized to ensure secure and transparent authentication of devices. In this context, APs can function as nodes within the blockchain, maintaining a secure ledger of user identities and their access rights. Blockchain is a decentralized, distributed digital ledger or database that records transactions across multiple computers in a way that prevents retroactive alteration of the recorded transactions. Each “block” in the blockchain contains a list of transactions [15], and these blocks are sequentially linked, forming an unbroken “chain”. Key advantages of blockchain technology include decentralization, immutability, transparency, and security [124,153]. It enables decentralized access control, ensuring that only authorized devices are permitted to connect to the network. Additionally, blockchain facilitates secure data sharing among different nodes in the network, maintaining data integrity and authenticity. With its numerous security benefits, blockchain is becoming an increasingly popular tool for enhancing data protection, identity management, and secure transactions [147].
Blockchain technology distributes data across multiple nodes, which contributes to its decentralized nature. This decentralization significantly reduces the risk of a single point of failure and makes it more challenging for attackers to compromise the entire network. Since there is no central server to target, blockchain-based systems are generally more resilient to DDoS attacks. Once data is recorded on a blockchain, it becomes immutable. This means that it cannot be altered or deleted without the consensus of the network, ensuring that the history of transactions is permanent and resistant to tampering. Blockchain provides a transparent and verifiable record of all transactions, which creates a clear audit trail. This feature is particularly beneficial in fields such as supply chain management and financial transactions, where accountability is essential [154].
Moreover, blockchain employs cryptographic techniques like public–private key pairs and hashing algorithms to secure transactions and verify the identities of participants. As a result, it becomes extremely difficult for unauthorized parties to alter or manipulate data. Blockchain can also be utilized for secure identity verification and management without relying on centralized intermediaries, thus reducing the risk of identity theft [124]. It can secure communications and data sharing while preventing unauthorized access to systems. By tracking the provenance of goods at every stage, blockchain ensures their authenticity and integrity. Additionally, it enhances the security of digital payments and banking through immutable transaction records. Blockchain also facilitates the creation of decentralized, self-sovereign identities, reducing reliance on centralized identity providers. By leveraging these features, systems can significantly improve their overall security, making it more difficult for attackers to compromise them and ensuring higher levels of data integrity and privacy. The integration of blockchain with CFMM networks is an intriguing area of research, particularly regarding decentralizing network management, enhancing security, and enabling new business models. However, significant technical, scalability, and regulatory challenges must be addressed before this integration can be implemented effectively on a large scale. Papers [155,156,157,158] provide appreciated insights into the incorporation of blockchain in next-generation networks. Table 8 provides scientific research papers interrelated to Authentication and Key Management in the CFMM system.

Table 8.
Authentication and key management approaches in CFMM systems.
4.3. Intrusion Detection Systems (IDS)
IDS is a security technology used to detect and respond to malicious activities or violations within a network. Its primary role is to monitor network traffic, identify suspicious behavior, and alert network administrators to potential threats [47]. In CFMM networks, IDS are essential for identifying and mitigating unauthorized access, cyberattacks, and other security threats [134]. These networks lack fixed cell boundaries, increasing security risks due to open access to multiple users. IDS techniques for CFMM include machine learning-based IDS, distributed IDS, and centralized-distributed coordination. Machine learning-based IDS detects anomalies by analyzing large datasets from multiple APs, leveraging models that can learn the normal behavior of users and detect deviations and unusual patterns in network traffic. Distributed IDS deploys IDS agents across multiple APs, enabling localized detection and response. Distributed IDS can provide real-time threat detection and response. Centralized-distributed coordination IDS uses a hybrid architecture where distributed IDS nodes collect data and report to a central controller, balancing scalability, and response time.
As examined in [160], to detect unauthorized access during the authentication phase, structured datasets are created using statistical features derived from signals received at the AP. These datasets are used to train support vector machine (SVM) classifiers. Artificial training data is generated by simulating the transmission and feature extraction processes at the AP. Two types of SVM classifiers are employed: a twin-class SVM (TC-SVM), suitable when full CSI is available, and a single-class SVM (SC-SVM), more appropriate when only legitimate users’ CSI is known. The effectiveness of these classifiers is assessed based on kernel function selection, feature choice, and the eavesdropper’s transmission power. Results show that achieving over 95Performance metrics, such as outage probability, are useful for detecting pilot attacks, as demonstrated in [161]. Jamming or Sybil attack detection introduced in [122] using either single or multi-parameter strategies. the two categories: Jamming-Attack Detection and Composite Jamming-Attack Detection schemes both relies on the difference in noise variances between two nodes. Signal anomalies, as discussed in [47], can be effectively identified using log-likelihood ratio tests implemented in both centralized and decentralized systems, achieving strong detection performance without notably impacting the SE of data transmission. Randomizing the pilot sequence exchanged between Alice and Bob has also proven to be an effective defense against injection attacks. On the other hand, reactive jamming presents a more advanced threat. In this scenario, the jammer passively monitors the spectrum and activates jamming only when an ongoing transmission is detected. Due to their covert nature and low likelihood of detection, reactive jamming attacks pose a serious challenge to secure and reliable communication [133].
In [162], the authors introduce a lightweight, real-time detector to observe and control performance metrics that are affected by the attacked network in both centralized and distributed modes. The study [163] provides meaningful insights into improving communication security through PLA techniques based on wireless fingerprinting. The fingerprinting differentiates legitimate nodes from potential attackers by utilizing the exceptional characteristics of the wireless channel. To support this approach, various ML techniques for anomaly detection are applied, incorporating a broad set of channel attributes under time-varying conditions. Specifically, four one-class ML strategies are examined and compared: decision-tree-based, kernel-based, clustering-based, and nearest-neighbor-based methods. The results indicate that utilizing multiple channel attributes significantly enhances detection accuracy. Notably, the kernel-based approach delivers the highest accuracy, while the nearest neighbor method offers comparable performance with much lower complexity and no training requirements, making it particularly well-suited for dynamic environments. The remaining two approaches demonstrate slightly lower accuracy but benefit from reduced computational demands.
Current smart grid systems [22] are vulnerable due to manual network management and hardware/software anomalies, leading to the adoption of SD-SGs for automated monitoring, control, and improved security. A supervised learning-based detection scheme for RF jamming attacks in Vehicular Ad hoc Networks employs k-nearest neighbors and random forest algorithms, utilizing features such as the variation in relative speed to effectively distinguish DoS jamming attacks from interference. Additionally, Paper [50] introduces a proactive approach to differentiate RF jamming from interference, emphasizing the significance of relative speed variations and other physical-layer metrics in detecting malicious jamming and enhancing prediction accuracy. Table 9 indicates IDS in CFMM networks.

Table 9.
Intrusion Detection Systems (IDS) in CFMM networks.
4.4. Secure Handover Mechanisms
While scalable CFMM performs well under static conditions, its dynamics related to AP handover in mobile networks have not been fully explored [166]. Handover refers to the process of selecting a suitable AP to serve a UE during mobility. This process involves optimizing user association decisions while managing computational complexity [167]. The unique characteristics of quantum channels between APs and UEs can facilitate secure location tracking and positioning. This capability can assist with resource allocation and mobility management, ensuring that APs effectively serve the correct UEs, even in densely populated environments. Handover in CFMM systems poses significant challenges [24] due to the high density of distributed APs and the need for precise coordination. Effective handover necessitates intelligent AP selection that accounts for network topology, load distribution, signal strength, and interference levels. Achieving seamless transitions also depends on the synchronization of beamforming vectors between UE and APs, that enforces the need for the cooperative beamforming schemes. Interference from adjacent APs further complicates handover, requiring integrated strategies for beamforming coordination and interference suppression. Employing soft handover techniques [168,169] that enable overlapping coverage areas can minimize communication disruptions and improve reliability. Additionally, adaptively adjusting AP clusters based on UE location and mobility facilitates more responsive and efficient handover decisions [170].
ML approaches offer further enhancement by predicting UE mobility patterns, optimizing AP selection, and improving the coordination between beamforming and handover management [171]. Paper [172] explores the secrecy performance of CFMM networks under the effect of active pilot spoofing attacks by multiple Eves. To mitigate the impact of such attacks, a joint AP selection and power control framework aimed at enhancing the PLS of the system. The design aims to augment the sum SE of the legitimate users while ensuring strictly positive secrecy SE for all users compromised by spoofing attacks. Additionally, in support of practical system deployment, two complementary procedures introduced: (1) a detection scheme for identifying the presence of multiple active Eves and associating each with its corresponding targeted user, and (2) an estimation technique for inferring the large-scale fading coefficients between the APs and the Eves based on received pilot statistics [172].
Authentication during handover, along with fast re-authentication techniques [173], helps to prevent attacks and reduces the vulnerability window during the transition from one AP to another. In CFMM networks, the serving cluster of APs changes dynamically as UEs move. One study [174] provides an inclusive analysis of 50 research papers focused on handover approaches in 5G heterogeneous networks, emphasizing their critical role in ensuring seamless connectivity for user equipment. Additionally, another review [175] examines recent handover decision algorithms, focusing on procedural aspects, performance impacts, self-optimization, and associated challenges, while categorizing algorithms and discussing evaluation methods. While SE performance is enhanced with secure handover techniques, there is no discussion on the signaling overhead or computational cost of handovers in scalable deployments. Table 10 describes the contributions and limitations of some related work for this section.

Table 10.
Secure handover mechanisms in CFMM networks.
4.5. Secure Software-Defined Networking (SDN) Integration
Integration of SDN in CFMM Networks is a key innovation to improve the flexibility, scalability, and network security. SDN was developed to streamline network administration and computerize infrastructure distribution in wired and wireless networks [162]. SDN allows centralized control of network resources by decoupling the data plane that handles traffic from the control plane, which makes decisions about traffic [15].
When integrated with CFMM, SDN helps optimize resource management, enable dynamic network adaptation, and enhance network security by dynamically adjust security policies based on immediate network conditions. SDN supports in identifying and isolating malicious traffic, preventing it from spreading across the network [178]. In CFMM networks, the CPU acts as an SDN controller that redirects traffic away from congested or under attack areas of the network, balancing the load across other APs or network segments, and ensuring the optimal coordination between APs [179]. Dynamic and flexible mapping between CPUs and APs enables the real-time reallocation of APs from congested CPUs to underutilized ones. This dynamic reassignment mitigates fronthaul bottlenecks by balancing the computational and communication load across the network. Moreover, such adaptability enhances system robustness, allowing for seamless handling of CPU failure events through automated AP migration mechanisms.
SDN also facilitates network programmability by enabling CPUs to utilize standardized SDN southbound protocols to issue control-plane directives such as configuration commands, status updates, and event notifications to the APs in a scalable and consistent manner. Although distributed SDN has been thoroughly investigated within the domain of traditional computer networks, its application to CF wireless systems remains largely unaddressed. This gap presents a compelling direction for future research, particularly in the context of scalable and resilient next-generation radio access networks (RANs) [178]. While there are few papers specifically combining secure SDN control with CFMM, several works provide architectural and security frameworks relevant to SDN-driven networks. The following works are closely related and offer valuable context as summarized in Table 10.
The SDN controller dynamically coordinates PLS techniques across multiple APs to ensure that key generation processes are synchronized across APs, improving the reliability of the keys generated through wireless channels. SDN dynamically configures beamforming strategies across APs to avoid eavesdroppers or jammers, ensuring that communication remains secure [90]. The southbound interface serves as the communication link between the SDN controller and network devices.
Securing this interface is critical to preventing attacks. OpenFlow [180] is one of the most widely used southbound protocols in SDN. To safeguard OpenFlow communications, encryption methods like TLS (Transport Layer Security) are used. This prevents attackers from intercepting or tampering with control messages exchanged between the controller and the devices. The SDN controller monitors spectrum usage and detects abnormal patterns of interference, which may indicate a jamming attack. If jamming is detected, the controller reconfigures the network dynamically by switching frequencies, adjusting transmission power, or steering beams away from the jammer, minimizing its effect on communication [22]. In multi-controller SDN architectures, the east–west interface facilitates communication between different SDN controllers. It is crucial to encrypt and authenticate this communication to maintain consistency and to protect against attacks that could manipulate control information between the controllers.
SDN enables network slicing, which allows the creation of multiple virtual networks on top of a single physical infrastructure. By integrating ML algorithms with SDN, the controller can detect and respond to anomalies in real time. ML algorithms can be used to detect unusual traffic patterns that indicate potential security threats. Based on real-time network analysis, SDN controllers can adapt security policies to evolving threats, deploying countermeasures dynamically. Blockchain is also used with SDN [180]. SDN enhances the management of the distributed, dynamic nature of CFMM networks, allowing centralized control while offering dynamic, fine-grained security policies. The centralized nature of SDN provides a powerful mechanism for real-time threat detection and mitigation, but it also introduces challenges such as controller security and securing communication across interfaces.
Paper [181] focuses on securing SDN control planes via Graph Convolutional Network (GCN)-based detection and partitioning mechanisms for real-time mitigation of packet injection DoS attacks. By employing strong encryption, distributed security measures, anomaly detection, and real-time traffic control, secure SDN integration can significantly enhance the robustness of CFMM networks, making them more resilient to attacks and ensuring the integrity and confidentiality of wireless communications. Combining CFMM with SDN/NFV (Network Function Virtualization) frameworks could enable dynamic security adaptations (e.g., AP or RIS selection, AN injection policy, beamforming reconfiguration), representing fertile ground for future work [182]. There is minimal literature explicitly integrating SDN/NFV-based controllers into secure CF deployments, despite CFMM being a candidate for open RAN (O-RAN) and virtualization. Additionally, techniques like anomaly detection, trust-based access control, or packet-injection mitigation applied in CF networking remain largely unexplored. Table 11 provides some related papers.

Table 11.
A summary of key papers on secure SDN-CFMM.
5. Case Study: Secure RIS-Aided CFMM Example
This section presents a comprehensive case study evaluating the effectiveness of a joint RIS, AN injection, and RZF precoding framework for PLS enhancement in CFMM networks. The analysis is performed using an extended simulation environment that incorporates cascaded channels, discrete-phase RIS control, alternating optimization BCD, and greedy elementwise RIS updates. Three representative transmission schemes are compared to quantify their relative secrecy performance, robustness, and energy efficiency. In the joint BCD RIS-aided PLS scheme, RIS cycles through a pre-shared pseudo-random sequence of phase profiles, known exclusively to the APs and legitimate UEs. That disrupts pilot contamination attacks. Adapting AN allocation to the instantaneous channel conditions, and joint optimization of AP precoders, AN covariance, and RIS phase shifts provide multi-security levels aim to increase the minimum SR.
5.1. Simulation Framework
The system model is as described in Figure 3 with single antenna APs and single eavesdropper. The channels follow the Rayleigh fading channel distribution [104], the small-scale fading channel h∼CN (0, 1). The channel model is described as:
where d is the path length. All simulation parameters and configuration settings are indicated in Table 12.

Table 12.
Simulation parameters and configuration settings.
The simulator models a CFMM system with L = 24 distributed single-antenna APs, K = 3 users, and a passive NRIS = 64-element RIS arranged on a circular layout. Large-scale fading follows distance-based pathloss with different exponents for AP–user, AP–RIS, and RIS–user links. Monte-Carlo (MC) simulations are executed, each with randomly generated user and eavesdropper positions.
All channel components (direct AP–UE links, cascaded AP–RIS–UE links, RIS–eavesdropper links, and AP–eavesdropper links) are synthesized using complex Gaussian fading combined with large-scale attenuation. The RIS applies a diagonal phase-shift matrix.
the phase shist of element
. For passive RIS |
| = 1. The effective channel with the RIS-aided scheme (far field) is [111]:
and similarly, the effective eavesedropper channel is given by:
The received SINR at user (k) and the eavesdropper are computed following the standard CFMM signal model with interference, AN leakage, and noise.
5.2. The Proposed BCD-Based Joint Optimization
The proposed scheme employs two nested optimization loops:
- (a)
- Precoder + AN design Given current RIS phases, the APs compute a ZF-based precoder. ZF beamforming matrix (the precoding vector) [106]:
Using equal per-user data power allocation, the power allocation with AN injection at the null space of the signal and with AN fraction = AN_fraction (equal 0.3) is:
P_data = P_total (1 − AN_fraction), and P_AN = P_total (AN_fraction)
- (b)
- Greedy elementwise RIS update
For each RIS element (n), the algorithm tests discrete phase candidates phase and selects the phase that maximizes the minimum secrecy rate across users.
- (c)
- Alternating BCD process
The two blocks alternate for several iterations:
- Fix RIS phases and optimize the beamforming with AN.
- Fix the precoder and AN covariance and optimize RIS phases.
- Repeat until convergence or reaching maximum number of iterations.
Five schemes are compared: Baseline CF (no RIS, no AN) Standard CF-ZF transmission without PLS enhancements, CF with RIS (fixed phases) RIS used with random but static phase configuration; no AN, CF with AN (no RIS) AN is injected via null space projection but RIS is absent, Proposed RIS with AN with pilot-hopping model Independent RIS configuration used with AN; eavesdropper receives attenuated pilot-based channel estimate, and Joint BCD (proposed final scheme) Full alternating optimization with greedy RIS updates and ZF with AN design.
5.3. The Performance Metrics
Four evaluation metrics are computed:
- (a)
- Per-user secrecy rate
The user’s and eve’s SINR are calculated based on (5) and (6), respectively:
where
- and are the k-th user’s channel and precoder, respectively.
- is the m-th AN vector.
The secrecy rate as defined in [109] is given by:
- (b)
- Secrecy Outage Probability (SOP):
This captures worst-case risk of secrecy failure.
- (c)
- Energy Efficiency (EE): A simple linear power model is used:
- (d)
- Complexity analysis: Table 13 indicates the complexity of compared scheme.
 Table 13. Complexity per operation and per scheme.
Table 13. Complexity per operation and per scheme.
5.4. The Optimization Problem
The greedy element wise RIS optimization is performed over discrete phase candidates and its objective is to maximize the minimum secrecy rate . The optimization problem: max-min SR (fairness):
Using BCD, (10) can be divided into two blocks:
- (1)
- The first block optimizes the precoder and AN design with fixed , we use the low complexity heuristic method [104,105]. The optimized precoding vector W_ZFopt = [ is selected to meet P_data and to place AN in the null-space of H with H = [ and (HT W_ZFopt) = I (the identity matrix). These ensure near zero interference at legitimate UE.
- (2)
- In the second block, the RIS phase is updated for fixed and . Now the non convex problem is to optimize to solve (10) for a given precoding vector and known AN covariance. In our simulation, we use the element-wise greedy search method as follows:
- For the n-th RIS element, try a small set of candidate phase {0, 2π/L,…, 2π(L − 1)/L}. Then compute for each candidate.
- Pick the more suitable phase that achieve the objective in (10).
- Sweep across all elements for several passes.
5.5. Simulation Results
Based on the equations defined in previous subsections, we evaluated the proposed scheme and its improved version in comparison with the other three schemes. In the training procedure, we used 200 iterations. In addition to the SR, the SOP and the EE are the performance metrics used in our simulation. The SOP and EE are defined in (8) and (9) respectively.
Figure 4 and Figure 5a,b illustrate the comparative performance of various secure transmission schemes in terms of SR, SOP, and EE, respectively. Figure 4 shows the CDF of the user’s SR of various secure transmission schemes. As indicated in Figure 4, the joint BCD scheme outperforms other schemes. highlighting the potential of adaptive optimization of the intelligent surfaces to enhance PLS without requiring knowledge of Eve’s channel, followed by the beamforming with the RIS (fixed) scheme due to the additional passive beamforming gain that strengthens the desired signals and weakens the eavesdropping links.
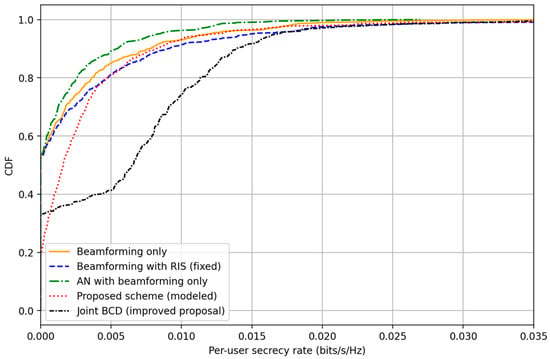
Figure 4.
CDF of per-user SR of various secure transmission schemes in a CFMM network (L = 24, K = 3, nr = 64, iterations = 200).
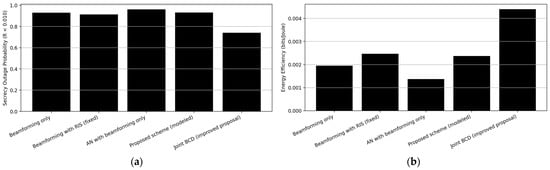
Figure 5.
Comparative performance of various secure transmission schemes in a CFMM network: (a) The SOP; (b) The EE.
The proposed joint BCD demonstrates the most favorable performance, achieving the highest EE and the lowest SOP among all compared schemes. In contrast, employing AN without RIS leads to a slight degradation in EE (Figure 5b) owing to the increased power consumption for noise generation, while only offering limited secrecy gains when AN is not optimally allocated. AN with beamforming only produces the lowest SR and EE with the highest SOP, as shown in Figure 4, Figure 5b and Figure 5a, respectively. AN degrades the user performance more than it helps jam Eve as it is sensitive to power allocation and dimensionality. When not carefully designed, it may degrade overall performance. Simulation results show improvement in SOP by 19% and EE by 76% compared to the second scheme (beamforming with RIS (fixed)), which is the next best model in terms of improved results for the SOP and EE as listed in Table 14.

Table 14.
SOP and EE of various secure schemes.
Figure 6 and Figure 7 compare the computational complexity of the considered schemes as a function of the number of APs and RIS elements based on the complexity equations defined in Table 13. The baseline CF scheme exhibits the lowest complexity. RIS-assisted schemes incur an additional cost due to cascaded channel construction. The proposed joint BCD-based RIS and AN optimization introduces higher complexity due to iterative greedy phase updates; however, the number of BCD iterations is small, resulting in a manageable complexity increase.
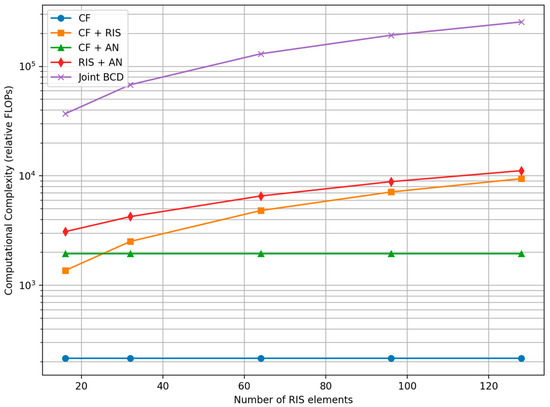
Figure 6.
Computational Complexity vs. RIS Size.
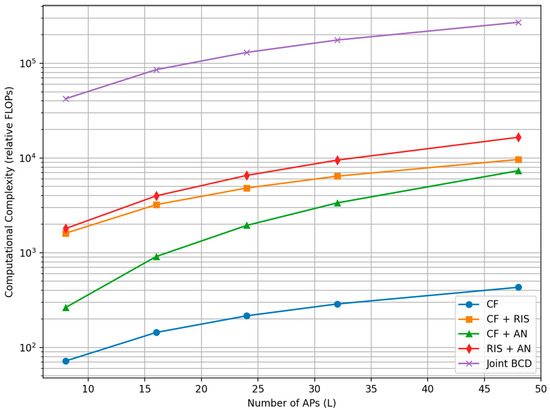
Figure 7.
Computational Complexity vs. Number of APs.
5.6. Discussion
Simulation results show that the baseline CF yields very low secrecy rates, confirming the weakness of purely distributed beamforming without PLS enhancements. Adding RIS (CF with RIS) improves rates moderately. Adding AN only (CF with AN) protects against eavesdropping but degrades multi-user performance, giving mixed results. The proposed RIS with AN scheme (RIS with AN) yields a significant right-shift in the CDF, demonstrating reduced eavesdropper advantage via the RIS-induced channel shaping. Joint BCD (Joint BCD) achieves the best secrecy performance, improving both median and 95%-likely secrecy rates by jointly optimizing all components.
The proposed BCD scheme achieves the lowest SOP, indicating high reliability in maintaining secrecy above the target rate. RIS-only and AN-only designs show partial advantages but are consistently inferior to the joint method.
The proposed joint BCD RIS–AN scheme achieves the highest SR and SOP and improved EE by jointly optimizing precoding, artificial noise, and RIS phase shifts. These performance gains come at the expense of increased computational complexity due to iterative BCD optimization and greedy RIS phase updates. Nevertheless, the required number of iterations is small, and the optimization can be performed over large channel coherence intervals. Therefore, the proposed scheme provides a favorable complexity–performance trade-off, where moderate additional complexity yields substantial secrecy and energy efficiency improvements.
While RIS-based schemes consume additional element power, the joint BCD scheme achieves the highest EE thanks to enhanced secrecy rates, improved channel alignment, and effective AN allocation. This highlights the practicality of intelligently optimized RIS deployment for energy-aware secure communications.
From this case study, the following observations are drawn: RIS, AN, and ZF/RZF must be jointly optimized to realize their full PLS potential. Greedy per-element RIS updates combined with power-split ZF design yield a superior secrecy–EE tradeoff. BCD is effective for non-convex joint RIS–precoder design, outperforming simple fixed or random strategies. Energy efficiency improvements are significant even when accounting for RIS hardware overhead. RIS-aided CFMM is a promising paradigm for secure, low-power 6G access networks.
6. Conclusions and Future Work
The growth of CFMM networks marks a significant advancement in wireless communications. However, the inherent characteristics of CF networks, namely their dense deployment, high user mobility, and continuous data exchange, pose significant challenges to existing authentication mechanisms in terms of scalability, latency, and computational burden. This paper discusses different aspects related to the security in CFMM networks. Securing these networks requires a comprehensive and multi-layered approach. This involves leveraging PLS, implementing robust authentication mechanisms, deploying intrusion detection systems, and embracing emerging technologies such as blockchain and quantum cryptography to ensure resiliency against various security threats. Beamforming and precoding enhance resistance by focusing energy on legitimate users. Power control and dynamic clustering mitigate the impact of jamming. Advanced signal processing techniques like pilot contamination mitigation and anti-jamming beamforming ensure secure communication. BCD is an efficient iterative strategy suitable for non-convex joint optimization problems by dividing the problem into subproblems easier to be handled. The proposed joint BCD-based RIS and AN greedy optimization exhibits the most promising performance. The simulation results confirm that jointly optimizing RIS phase shifts and AN power allocation can significantly enhance both the energy and secrecy efficiency of UC-CFMM systems, emphasizing the importance of coordinated design between passive and active PLS mechanisms.
6.1. Limitations of the Review and Lessons Learned
Although this review aims to provide a comprehensive overview of security challenges and PLS techniques for CFMM, several limitations must be acknowledged to ensure transparency and to guide future research.
- Scope of Included Literature: While major IEEE, Elsevier, and MDPI databases have been surveyed, some emerging works, particularly those in pre-print repositories and specialized workshops, may not be fully captured. Additionally, despite a structured process for inclusion and exclusion, the rapid pace of developments in RIS-aided CFMM and near-field XL-MIMO may result in partial coverage of the most recent advances.
- Limited Discussion on Hardware Impairments: Hardware security—e.g., RIS imperfections, AP synchronization, phase noise, mutual coupling, and hardware spoofing attacks—was not covered in the same depth as software- or algorithm-level PLS methods. This remains a critical dimension for future CFMM deployments.
- Focus on Downlink Case Study Only: The presented case study evaluates downlink secrecy performance. The uplink, joint UL–DL optimization, and full-duplex CFMM security aspects are outside the current scope and thus not addressed.
- Assumptions on CSI Availability: Many works surveyed, including the presented case study, assume perfect or partially known CSI. Realistic issues like RIS-induced pilot contamination, RIS calibration errors, and adversarial pilot spoofing remain underexplored.
- Limited Evaluation Scenarios in the Case Study: The simulation framework focuses on representative but controlled scenarios (e.g., fixed user count, single eavesdropper, fixed RIS size). Broader variability—such as multi-eavesdropper threats, near-field conditions, and large-scale RISs—is not fully examined.
Lessons learned from this study include the following points:
- RIS Deployment Can Dramatically Enhance Security—but Only if Jointly Optimized: Random or fixed RIS phase configurations offer marginal gains. The largest secrecy improvements occur when RIS phases, precoders, and AN strategies are jointly optimized.
- AN Alone Is Insufficient: Artificial noise enhances secrecy only when combined with proper beamforming and RIS control. Otherwise, it can degrade user performance more than it harms the eavesdropper.
- Decentralized Processing Demands New Security Models: CFMM’s inherent distribution of APs introduces new vulnerabilities: insecure backhaul, exposed AP hardware, RIS tampering risks, and localization uncertainty for eavesdroppers.
- Secrecy Performance Is Highly Sensitive to CSI Quality: Both legacy CF-MMSE/ZF algorithms and RIS-assisted designs degrade rapidly under imperfect CSI. Robust estimation and pilot protection remain fundamental design pillars.
- Energy Efficiency Must Be Studied Jointly with Security: Security enhancements (e.g., large RIS, AN injection) can raise energy consumption. However, joint optimization can simultaneously increase secrecy and EE, revealing a promising design direction for 6G.
6.2. Open Research Challenges and Future Directions
Based on the survey and the presented case study, several key research directions emerge for enabling secure and scalable CFMM architectures in 6G systems.
- Near-Field and Polar-Domain Modeling for CF–RIS Security: Recent advances in near-field XL-MIMO, polar-domain channel models, and beam squint mitigation have not yet been integrated into CFMM security analysis. Future work should incorporate spherical-wave RIS–user–AP channels, polar-domain precoding for secrecy, near-field AN shaping, and location-dependent eavesdropping models. These aspects will significantly change RIS design and security guarantees.
- Hardware Security and Physical Validation: Future CFMM systems must account for realistic hardware threats: RIS malfunction, spoofing, or malicious configuration. AP-side hardware impairments (IQ imbalance, clock drift, noise figure variation). low-cost ADC/DAC vulnerabilities. energy-harvesting attackers capable of passive sensing. Testbed validation is necessary to quantify how these impairments affect secrecy rate and SOP.
- Secure and Scalable CSI Acquisition: State-of-the-art pilot-based CSI estimation is fragile in distributed systems. Future directions include RIS-enhanced pilot authentication, joint channel-and-position estimation for eavesdropper detection, blind or semi-blind CSI estimation resistant to spoofing, and secure feedback via federated or encrypted backhaul. Robust CSI is essential for reliable RIS and precoder optimization.
- Joint Optimization of RIS, AP Clustering, and User Scheduling: Most existing works keep AP association and user scheduling unchanged. However, in dense CFMM networks dynamic AP clustering, RIS–AP association maps, secure scheduling policies in the presence of eavesdroppers, and resource allocation under secrecy constraints represent major open design problems.
- Learning-Aided Secure CFMM Architectures: ML and reinforcement learning (RL) provide opportunities to enhance RIS phase selection, adaptive AN generation, secure beam management, eavesdropper identification, and secure AP–UE association. However, ML introduces new vulnerabilities (e.g., model poisoning), so resilient learning frameworks are needed.
- Joint Security–EE Design Under Practical Power Models: Future studies should consider RIS switching power, amplifier nonlinearities, backhaul power consumption, and AP sleep-control mechanisms to jointly optimize secrecy rate, latency, and power efficiency in real deployments.
- Multi-RIS and Three-dimensional Passive/Active RIS Security: Emerging trends include stacked RIS layers and hybrid active–passive RIS. Three-dimensional metasurfaces enabling near-field 6G sensing, RIS-enhanced covert communications. These architectures provide new opportunities for secure CF operations but require fresh models and large-scale optimization methods.
- Investigating quantum-resistant cryptographic algorithms and integrating chaotic maps to prepare for the future advent of quantum computing and other security threats, which could potentially break existing cryptographic schemes.
Author Contributions
Conceptualization, H.M. and A.M.S.; methodology, N.A.; software, H.M.; validation, R.I.A. and, M.E.N.; writing—original draft preparation, H.M.; writing—review and editing, A.M.S.; visualization, N.A.; supervision, M.E.N. and R.I.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Salahdine, F.; Han, T.; Zhang, N. Security in 5g and beyond: Recent advances and future challenges. Secur. Priv. 2023, 6, e271. [Google Scholar] [CrossRef]
- Akbar, M.S.; Hussain, Z.; Ikram, M.; Sheng, Q.Z.; Mukhopadhyay, S.C. On challenges of sixth-generation (6g) wireless networks: A comprehensive survey of requirements, applications, and security issues. J. Netw. Comput. Appl. 2025, 233, 104040. [Google Scholar] [CrossRef]
- Björnson, E.; Hoydis, J.; Sanguinetti, L. Massive MIMO networks: Spectral, energy, and hardware efficiency. Found. Trends Signal Process. 2017, 11, 154–655. [Google Scholar] [CrossRef]
- Vaigandla, K.K.; Venu, N. Survey on massive MIMO: Technology, challenges, opportunities and benefits. YMER Digit. 2021, 20, 271–282. [Google Scholar] [CrossRef] [PubMed]
- Albreem, M.A.; Juntti, M.; Shahabuddin, S. Massive MIMO detection techniques: A survey. IEEE Commun. Surv. Tutor. 2019, 21, 3109–3132. [Google Scholar] [CrossRef]
- Mozaffariahrar, E.; Theoleyre, F.; Menth, M. A survey of wi-fi 6: Technologies, advances, and challenges. Future Internet 2022, 14, 293. [Google Scholar] [CrossRef]
- Quy, V.K.; Chehri, A.; Quy, N.M.; Han, N.D.; Ban, N.T. Innovative trends in the 6g era: A comprehensive survey of architecture, applications, technologies, and challenges. IEEE Access 2023, 11, 39824–39844. [Google Scholar] [CrossRef]
- Qamar, F.; Kazmi, S.H.A.; Ariffin, K.A.Z.; Tayyab, M.; Nguyen, Q.N. Multi-antenna array-based massive MIMO for b5g/6g: State of the art, challenges, and future research directions. Information 2024, 15, 442. [Google Scholar] [CrossRef]
- Hao, W.; Li, J.; Sun, G.; Huang, C.; Zeng, M.; Dobre, O.A.; Yuen, C. Robust security energy efficiency optimization for ris-aided cell-free networks with multiple eavesdroppers. IEEE Trans. Commun. 2024, 72, 7401–7416. [Google Scholar] [CrossRef]
- Gkonis, P.K. A survey on machine learning techniques for massive MIMO configurations: Application areas, performance limitations and future challenges. IEEE Access 2023, 11, 67–88. [Google Scholar] [CrossRef]
- Timilsina, S.; Kudathanthirige, D.; Amarasuriya, G. Physical layer security in cell-free massive MIMO. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–7. [Google Scholar] [CrossRef]
- Chowdhury, M.Z.; Shahjalal, M.; Ahmed, S.; Jang, Y.M. 6g wireless communication systems: Applications, requirements, technologies, challenges, and research directions. IEEE Open J. Commun. Soc. 2020, 1, 957–975. [Google Scholar] [CrossRef]
- Obakhena, H.I.; Imoize, A.L.; Anyasi, F.I.; Kavitha, K.V.N. Application of cell-free massive MIMO in 5g and beyond 5g wireless networks: A survey. J. Eng. Appl. Sci. 2021, 68, 13. [Google Scholar] [CrossRef]
- Pattnaik, S.K.; Samal, S.R.; Bandopadhaya, S.; Swain, K.; Choudhury, S.; Das, J.K.; Mihovska, A.; Poulkov, V. Future wireless communication technology towards 6g iot: An application-based analysis of iot in real-time location monitoring of employees inside underground mines by using ble. Sensors 2022, 22, 3438. [Google Scholar] [CrossRef]
- Scalise, P.; Boeding, M.; Hempel, M.; Sharif, H.; Delloiacovo, J.; Reed, J. A systematic survey on 5g and 6g security considerations, challenges, trends, and research areas. Future Internet 2024, 16, 67. [Google Scholar] [CrossRef]
- Elijah, O.; Rahim, S.K.A.; New, W.K.; Leow, C.Y.; Cumanan, K.; Geok, T.K. Intelligent massive MIMO systems for beyond 5g networks: An overview and future trends. IEEE Access 2022, 10, 102532–102563. [Google Scholar] [CrossRef]
- Abdel Hakeem, S.A.; Hussein, H.H.; Kim, H. Security requirements and challenges of 6g technologies and applications. Sensors 2022, 22, 1969. [Google Scholar] [CrossRef]
- Rathod, T.; Jadav, N.K.; Alshehri, M.D.; Tanwar, S.; Sharma, R.; Felseghi, R.-A.; Raboaca, M.S. Blockchain for future wireless networks: A decade survey. Sensors 2022, 22, 4182. [Google Scholar] [CrossRef] [PubMed]
- Zheng, J.; Zhang, J.; Du, H.; Niyato, D.; Ai, B.; Debbah, M.; Letaief, K.B. Mobile cell-free massive MIMO: Challenges, solutions, and future directions. IEEE Wirel. Commun. 2024, 31, 140–147. [Google Scholar] [CrossRef]
- Salehi Shahraki, A.; Lauer, H.; Grobler, M.; Sakzad, A.; Rudolph, C. Access control, key management, and trust for emerging wireless body area networks. Sensors 2023, 23, 9856. [Google Scholar] [CrossRef]
- Jiang, W.; Schotten, H.D. Cell-free terahertz massive MIMO: A novel paradigm beyond ultra-massive MIMO. In Proceedings of the 2024 IEEE International Mediterranean Conference on Communications and Networking (MeditCom), Madrid, Spain, 8–11 July 2024. [Google Scholar]
- Agnew, D.; Boamah, S.; Bretas, A.; McNair, J. Network security challenges and countermeasures for software-defined smart grids: A survey. Smart Cities 2024, 7, 2131–2181. [Google Scholar] [CrossRef]
- Saeedi Taleghani, E.; Maldonado Valencia, R.I.; Sandoval Orozco, A.L.; García Villalba, L.J. Trust evaluation techniques for 6g networks: A comprehensive survey with fuzzy algorithm approach. Electronics 2024, 13, 3013. [Google Scholar] [CrossRef]
- Ajmal, M.; Siddiqa, A.; Jeong, B.; Seo, J.; Kim, D. Cell-free massive multiple-input multiple-output challenges and opportunities: A survey. ICT Express 2024, 10, 194–212. [Google Scholar] [CrossRef]
- Afshari, H.; Zeinalpour-Yazdi, Z. A game-theoretical and spatial approach to mitigate pilot contamination in crowded massive MIMO systems. IEEE Trans. Wirel. Commun. 2024, 23, 2357–2368. [Google Scholar] [CrossRef]
- Hassan, B.; Baig, S.; Aslam, S. On scalability of fdd-based cell-free massive MIMO framework. Sensors 2023, 23, 6991. [Google Scholar] [CrossRef]
- Demir, Ö.T.; Björnson, E.; Sanguinetti, L. Foundations of user-centric cell-free massive MIMO. Found. Trends Signal Process. 2021, 14, 162–472. [Google Scholar] [CrossRef]
- Chen, S.; Zhang, J.; Zhang, J.; Björnson, E.; Ai, B. A survey on user-centric cell-free massive MIMO systems. Digit. Commun. Netw. 2022, 8, 695–719. [Google Scholar] [CrossRef]
- Sharma, M.; Verma, S.; Verma, S. Optimization of cell-free massive MIMO system. J. Phys. Conf. Ser. 2022, 2327, 012056. [Google Scholar] [CrossRef]
- Tahreem Supervisor, A.; Ikki Deeb Tubail, S. Impact of Hardware Impairments on the Physical Layer Security of Cell-Free Massive Mimo. Master’s Thesis, Lakehead University, Orillia, ON, Canada, 2024. Available online: https://knowledgecommons.lakeheadu.ca/jspui/bitstream/2453/5305/1/TahreemA2024m-1a.pdf (accessed on 1 March 2023).
- Hussain Shaik, Z. Distributed Signal Processing for Out-of-System Interference Suppression in Cell-Free Massive MIMO. In Proceedings of the 2023 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Rhodes Island, Greece, 4–10 June 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–5. [Google Scholar] [CrossRef]
- Demir, Ö.T.; Masoudi, M.; Björnson, E.; Cavdar, C. Cell-free massive MIMO in O-RAN: Energy-aware joint orchestration of cloud, fronthaul, and radio resources. arXiv 2023. [Google Scholar] [CrossRef]
- Ngo, H.Q.; Interdonato, G.; Larsson, E.G.; Caire, G.; Andrews, J.G. Ultra-dense cell-free massive MIMO for 6g: Technical overview and open questions. Proc. IEEE 2024, 112, 805–831. [Google Scholar] [CrossRef]
- Jo, S.; Lee, H.; Park, S.-H. Joint precoding and fronthaul compression for cell-free MIMO downlink with radio stripes. In Proceedings of the GLOBECOM 2023—2023 IEEE Global Communications Conference, Kuala Lumpur, Malaysia, 4–8 December 2023. [Google Scholar]
- Conceicao, F.; Gomes, M.; Silva, V.; Dinis, R. Survey on resource allocation for future 6g network architectures: Cell-free and radio stripe technologies. Electronics 2024, 13, 2489. [Google Scholar] [CrossRef]
- Alnashwan, R.; Gope, P.; Dowling, B. Privacy-awaresecureregion-basedhandoverforsmallcellnetworksin5g-enabled mobile communication. IEEE Trans. Inf. Forensics Secur. 2023, 18, 1898–1913. [Google Scholar] [CrossRef]
- Hu, H.; Xie, W.; Xu, K.; Xia, X.; Li, N.; Wu, H. Multi-intelligent reflecting surfaces and artificial noise-assisted cell-free massive mimo against simultaneous jamming and eavesdropping. Sensors 2024, 24, 7326. [Google Scholar] [CrossRef]
- Alnashwan, R.; Gope, P.; Dowling, B. Unihand: Privacy-preserving universal handover for small-cell networks in 5g-enabled mobile communication with kci resilience. In Proceedings of the 2024 IEEE 37th Computer Security Foundations Symposium (CSF), Enschede, The Netherlands, 8–12 July 2024; IEEE: Piscataway, NJ, USA, 2024. [Google Scholar] [CrossRef]
- Vasudevan, V.A.; Tayyab, M.; Koudouridis, G.P.; Gelabert, X.; Politis, I. An integrated approach for energy efficient handover and key distribution protocol for secure nc-enabled small cells. Comput. Netw. 2022, 206, 108806. [Google Scholar] [CrossRef]
- Wang, X.; Gao, Y.; Zhang, G.; Guo, M.; Xu, K. Security performance analysis for cell-free massive multiple-input multiple-output system with multi-antenna access points deployment in presence of active eavesdropping. Int. J. Distrib. Sens. Netw. 2022, 18, 15501329221114535. [Google Scholar] [CrossRef]
- Chen, Z.; Björnson, E. Channel hardening and favorable propagation in cell-free massive MIMO with stochastic geometry. IEEE Trans. Commun. 2018, 66, 5205–5219. [Google Scholar] [CrossRef]
- Zhou, M.; Zhang, Y.; Qiao, X.; Yang, L. Spatially correlated rayleigh fading for cell-free massive MIMO systems. IEEE Access 2020, 8, 42154–42168. [Google Scholar] [CrossRef]
- Zhu, Q.; Wu, S.; Hua, Y. Optimal pilots for anti-eavesdropping channel estimation. IEEE Trans. Signal Process. 2020, 68, 2629–2644. [Google Scholar] [CrossRef]
- Dang, X.T.; Nguyen, H.V.; Shin, O.S. Physical layer security for IRS-UAV-assisted cell-free massive MIMO systems. IEEE Access 2024, 12, 89520–89537. [Google Scholar] [CrossRef]
- Khan, A.S.; Bin Yahya, M.I.; Zen, K.B.; Bin Abdullah, J.; Rashid, R.B.A.; Javed, Y.; Khan, N.A.; Mostafa, A.M. Blockchain-based lightweight multifactor authentication for cell-free in ultra-dense 6g-based (6-cmas) cellular network. IEEE Access 2023, 11, 20524–20541. [Google Scholar] [CrossRef]
- Wang, X.; Zheng, Z.; Fei, Z.; Han, Z.; Huang, Y. Fighting against active eavesdropper: Distributed pilot spoofing attack detection and secure coordinated transmission in multi-cell massive MIMO systems. IEEE Trans. Wirel. Commun. 2024, 23, 11184–11198. [Google Scholar] [CrossRef]
- Hosseini, S.S.; Chang, X.W.; Champagne, B. New llrt-based methods for active eavesdropper detection in cell-free massive MIMO. IEEE Open J. Commun. Soc. 2023, 4, 153–170. [Google Scholar] [CrossRef]
- Alageli, M.; Ikhlef, A.; Alsifiany, F.; Abdullah, M.A.M.; Chen, G.; Chambers, J. Optimal downlink transmission for cell-free swipt massive MIMO systems with active eavesdropping. IEEE Trans. Inf. Forensics Secur. 2020, 15, 1983–1998. [Google Scholar] [CrossRef]
- Pirayesh, H.; Zeng, H. Jamming attacks and anti-jamming strategies in wireless networks: A comprehensive survey. IEEE Commun. Surv. Tutor. 2022, 24, 767–809. [Google Scholar] [CrossRef]
- Kosmanos, D.; Karagiannis, D.; Argyriou, A.; Lalis, S.; Maglaras, L. Rf jamming classification using relative speed estimation in vehicular wireless networks. Secur. Commun. Netw. 2021, 2021, 9959310. [Google Scholar] [CrossRef]
- Dassanayake, J.K.; Gunasinghe, D.; Aruma Baduge, G.A. Secrecy rate analysis and active pilot attack detection for irs-aided massive MIMO systems. IEEE Trans. Inf. Forensics Secur. 2024, 19, 2664–2679. [Google Scholar] [CrossRef]
- Gao, X.; Li, Y.; Cheng, W.; Dong, L.; Liu, P. Secure optimal precoding for user-centric cell-free massive MIMO system. IEEE Wirel. Commun. Lett. 2023, 12, 31–35. [Google Scholar] [CrossRef]
- Zhang, X.; Guo, D.; An, K.; Ding, Z.; Zhang, B. Secrecyanalysisandactivepilotspoofingattackdetectionformultigroup multicasting cell-free massive MIMO systems. IEEE Access 2019, 7, 57332–57340. [Google Scholar] [CrossRef]
- Akgun, B.; Krunz, M.; Koyluoglu, O.O. Vulnerabilities of massive MIMO systems against pilot contamination attacks. IEEE Trans. Inf. Forensics Secur. 2017, 14, 1251–1263. [Google Scholar] [CrossRef]
- Hoang, T.M.; Ngo, H.Q.; Duong, T.Q.; Tuan, H.D.; Marshall, A. Cell-free massive MIMO networks: Optimal power control against active eavesdropping. IEEE Trans. Commun. 2018, 66, 4724–4737. [Google Scholar] [CrossRef]
- Wang, X.; Gao, Y.; Sha, N.; Zhang, X.; Guo, M.; Zang, G.; Li, N. Detection of pilot spoofing attack in cell-free massive MIMO systems. J. Signal Process. 2022, 38, 1922–1930. [Google Scholar] [CrossRef]
- Xia, X.; Fan, Z.; Luo, W.; Lu, A.; Wang, D.; Zhao, X.; You, X. Joint uplink power control, downlink beamforming, and mode selection for secrecy cell-free massive MIMO with network-assisted full duplexing. IEEE Syst. J. 2023, 17, 720–731. [Google Scholar] [CrossRef]
- Li, W.; Wang, N.; Jiao, L.; Zeng, K. Physical layer spoofing attack detection in mmwave massive MIMO 5g networks. IEEE Access 2021, 9, 60419–60432. [Google Scholar] [CrossRef]
- Nguyen, N.T.; Nguyen, V.-D.; Van Nguyen, H.; Ngo, H.Q.; Chatzinotas, S.; Juntti, M. Spectral efficiency analysis of hybrid relay-reflecting intelligent surface-assisted cell-free massive MIMO systems. IEEE Trans. Wirel. Commun. 2023, 22, 3397–3416. [Google Scholar] [CrossRef]
- Zegrar, S.E.; Furqan, H.M.; Arslan, H. Flexible physical layer security for joint data and pilots in future wireless networks. IEEE Trans. Commun. 2022, 70, 2635–2647. [Google Scholar] [CrossRef]
- Mucchi, L.; Jayousi, S.; Caputo, S.; Panayirci, E.; Shahabuddin, S.; Bechtold, J.; Morales, I.; Stoica, R.-A.; Abreu, G.; Haas, H. Physical-layer security in 6g networks. IEEE Open J. Commun. Soc. 2021, 2, 1901–1914. [Google Scholar] [CrossRef]
- Brilhante, D.d.S.; Manjarres, J.C.; Moreira, R.; Veiga, L.d.O.; de Rezende, J.F.; Müller, F.; Klautau, A.; Mendes, L.L.; de Figueiredo, F.A.P. A literature survey on ai-aided beamforming and beam management for 5g and 6g systems. Sensors 2023, 23, 4359. [Google Scholar] [CrossRef]
- Boodai, J.; Alqahtani, A.; Frikha, M. Review of physical layer security in 5g wireless networks. Appl. Sci. 2023, 13, 7277. [Google Scholar] [CrossRef]
- Srinivasan, M.; Skaperas, S.; Shakiba Herfeh, M.; Chorti, A. Joint localization-based node authentication and secret key generation. In Proceedings of the IEEE International Conference on Communications (ICC), Seoul, Republic of Korea, 16–20 May 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 32–37. [Google Scholar] [CrossRef]
- Yadav, P.; Kumar, S.; Kumar, R. A comprehensive survey of physical layer security over fading channels: Classifications, applications, and challenges. Trans. Emerg. Telecommun. Technol. 2021, 32, e42700. [Google Scholar] [CrossRef]
- Tefera, M.K.; Jin, Z.; Zhang, S. A review of fundamental optimization approaches and the role of ai enabling technologies in physical layer security. Sensors 2022, 22, 3589. [Google Scholar] [CrossRef]
- Zhao, Y.; Zhai, W.; Zhao, J.; Zhang, T.; Sun, S.; Niyato, D.; Lam, K.-Y. A comprehensive survey of 6g wireless communications. arXiv 2020. [Google Scholar] [CrossRef]
- You, L.; Xiong, J.; Yi, X.; Wang, J.; Wang, W.; Gao, X. Energy efficiency optimization for downlink massive MIMO with statistical csit. IEEE Trans. Wirel. Commun. 2020, 19, 2684–2698. [Google Scholar] [CrossRef]
- Ozlem, G.; Demir, T.G.; Masoudi, M.; Björnson, E.; Cavdar, C. Cell-free massive MIMO in virtualized cran: How to minimize the total network power? In Proceedings of the IEEE International Conference on Communications (ICC), Seoul, Republic of Korea, 16–20 May 2022; IEEE: Piscataway, NJ, USA, 2022. [Google Scholar] [CrossRef]
- Zhang, Y.; Yang, K.; Xia, W.; Zhang, J.; Ni, Y.; Lu, W. Secure rsma for cf-mmimo systems with low-resolution dacs. IEEE Wirel. Commun. Lett. 2024, 13, 1660–1664. [Google Scholar] [CrossRef]
- Kaur, R.; Bansal, B.; Majhi, S.; Jain, S.; Huang, C.; Yuen, C. A survey on reconfigurable intelligent surface for physical layer security of next-generation wireless communications. IEEE Open J. Veh. Technol. 2024, 5, 172–199. [Google Scholar] [CrossRef]
- Duong, T.Q.; Zhou, X.S.; Poor, H.V. Trusted Communications with Physical Layer Security for 5G and Beyond; Institution of Engineering and Technology: London, UK, 2017. [Google Scholar]
- Albreem, M.A.; Habbash, A.H.A.; Abu-Hudrouss, A.M.; Ikki, S.S. Overview of precoding techniques for massive MIMO. IEEE Access 2021, 9, 60764–60801. [Google Scholar] [CrossRef]
- Albreem, M.A.; Salah, W.; Kumar, A.; Alsharif, M.H.; Rambe, A.H.; Jusoh, M.; Uwaechia, A.N. Low complexity linear detectors for massive MIMO: A comparative study. IEEE Access 2021, 9, 45740–45753. [Google Scholar] [CrossRef]
- Albreem, M.A.; Abdallah, S.; Alnajjar, K.A.; Aldababsa, M. Efficient detectors for uplink massive MIMO systems. J. Commun. Netw. 2024, 26, 35–48. [Google Scholar] [CrossRef]
- Alshamary, H.A.J. Coherent and Non-Coherent Data Detection Algorithms in Massive MIMO. Ph.D. Thesis, University of Iowa, Iowa City, IA, USA, 2017. [Google Scholar] [CrossRef]
- Kassam, J.; Castanheira, D.; Silva, A.; Dinis, R.; Gameiro, A. A review on cell-free massive MIMO systems. Electronics 2023, 12, 1001. [Google Scholar] [CrossRef]
- Engda, T.K.; Wondie, Y.; Steinbrunn, J. Massive MIMO, mmwave and mmwave-massive MIMO communications: Performance assessment with beamforming techniques. Res. Sq. 2020. [Google Scholar] [CrossRef]
- Bolla, S.; Singh, M. Massive MIMO precoding and beamforming techniques for future generation communication system. J. Electr. Syst. 2024, 20, 290–297. [Google Scholar] [CrossRef]
- Ren, Z.; Xu, J.; Qiu, L.; Ng, D.W.K. Secure cell-free integrated sensing and communication in the presence of information and sensing eavesdroppers. IEEE J. Sel. Areas Commun. 2024, 42, 3217–3231. [Google Scholar] [CrossRef]
- Wang, L.; Chen, C.; Zhang, J.; Fischione, C. Learning-based joint antenna selection and precoding design for cell-free mimo networks. arXiv 2024, arXiv:2404.08607. [Google Scholar] [CrossRef]
- Ayidh, A.A.; Sambo, Y.; Olaosebikan, S.; Ansari, S.; Imran, M.A. Antenna selection based on matching theory for uplink cell-free millimetre wave massive multiple input multiple output systems. Telecom 2022, 3, 448–466. [Google Scholar] [CrossRef]
- Khan, R.; Jan, L.; Khan, S.; Zafar, M.H.; Ahmad, W.; Husnain, G. An effective algorithm in uplink massive MIMO systems for pilot decontamination. Results Eng. 2024, 21, 101873. [Google Scholar] [CrossRef]
- Ito, M.; Fukue, S.; Ando, K.; Kanno, I.; Yamazaki, K.; Ishibashi, K. Clustering and beamforming for user-centric cell-free massive MIMO with backhaul capacity limitation. IEEE Access 2024, 12, 382–395. [Google Scholar] [CrossRef]
- Interdonato, G.; Ngo, H.Q.; Larsson, E.G. Enhanced normalized conjugate beamforming for cell-free massive MIMO. IEEE Trans. Commun. 2021, 69, 2863–2877. [Google Scholar] [CrossRef]
- Demirhan, U.; Alkhateeb, A. Cell-Free ISAC MIMO Systems: Joint Sensing and Communication Beamforming. IEEE Trans. Commun. 2025, 73, 4454–4468. [Google Scholar] [CrossRef]
- Mao, W.; Lu, Y.; Chi, C.-Y.; Ai, B.; Zhong, Z.; Ding, Z. Communication-sensing region for cell-free massive mimo isac systems. IEEE Trans. Wirel. Commun. 2024, 23, 12396–12411. [Google Scholar] [CrossRef]
- Behdad, Z. Integrated Sensing and Communication in Cell-Free Massive MIMO. Ph.D. Thesis, KTH Royal Institute of Technology, Stockholm, Sweden, 2024. [Google Scholar]
- Demirhan, U.; Alkhateeb, A. Learning beamforming in cell-free massive MIMO ISAC systems. In Proceedings of the 2024 IEEE 25th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Lucca, Italy, 10–13 September 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 326–330. [Google Scholar] [CrossRef]
- Hojatian, H.; Nadal, J.; Frigon, J.-F.; Leduc-Primeau, F. Decentralized beamforming for cell-free massive MIMO with unsupervised learning. IEEE Commun. Lett. 2022, 26, 1042–1046. [Google Scholar] [CrossRef]
- Sandoval, I.A.M.; Ando, K.; Taghizadeh, O.; de Abreu, G.T.F. Sum-rate maximization and leakage minimization for multi-user cell-free massive MIMO systems. IEEE Access 2023, 11, 127509–127525. [Google Scholar] [CrossRef]
- Atiya, Y.S.; Mobini, Z.; Ngo, H.Q.; Matthaiou, M. Cell-free massive MIMO with protective partial zero-forcing and active eavesdropping. In Proceedings of the 2023 IEEE 97th Vehicular Technology Conference (VTC2023-Spring), Florence, Italy, 20–23 June 2023; IEEE: Piscataway, NJ, USA, 2023. [Google Scholar] [CrossRef]
- Atiya, Y.S.; Mobini, Z.; Ngo, H.Q.; Matthaiou, M. Secure transmission in cell-free massive MIMO under active eavesdropping. arXiv 2024, arXiv:2408.17169. [Google Scholar] [CrossRef]
- Zafari, M.; Pandey, D.; Doost-Mohammady, R.; Uribe, C.A. Admm for downlink beamforming in cell-free massive MIMO systems. arXiv 2024, arXiv:2409.06106. [Google Scholar] [CrossRef]
- Abdel-Fattah, M.S.; Abouelnaga, T.G.; Hamad, E.K.I.; Elsadek, H.A. Optimizing of 5g base station MIMO antenna performance. Aswan Univ. J. Sci. Technol. 2024, 4, 78–93. [Google Scholar] [CrossRef]
- Liu, J.S.; Lin, C.H.R.; Chang, W.L. Joint beamforming and power splitting design for miso downlink communication with swipt: A comparison between cell-free massive MIMO and small-cell deployments. Eurasip J. Wirel. Commun. Netw. 2024, 2024, 19. [Google Scholar] [CrossRef]
- Meesam, J.; Srivastava, S.; Venkategowda, N.K.D.; Jagannatham, A.K.; Hanzo, L. Cooperative hybrid transmit beamforming in cell-free mmwave MIMO networks. IEEE Trans. Veh. Technol. 2023, 72, 6023–6038. [Google Scholar] [CrossRef]
- Park, J.; Yun, S.; Ha, J. Secure power control for downlink cell-free massive MIMO with passive eavesdroppers. IEEE Trans. Veh. Technol. 2024, 73, 9038–9043. [Google Scholar] [CrossRef]
- Salehi, S.; Mashdour, S.; Tamyigit, O.; Seyedmasoumian, S.; Moradikia, M.; de Lamare, R.C.; Schmeink, A. Machine learning-based ap selection in user-centric cell-free multiple-antenna networks. arXiv 2025, arXiv:2504.09263. [Google Scholar]
- Fu, H.; Zhang, X.; Peng, L. Performance analysis of artificial noise-assisted location-based beamforming in rician wiretap channels. Entropy 2023, 25, 1626. [Google Scholar] [CrossRef]
- Rahmani, M.; Zhao, J.; Bashar, M.; Cumanan, K.; Burr, A.; Tafazolli, R. Securing 5g nr networks: Innovative artificial noise methods for protecting cell-free massive MIMO. In Proceedings of the 2025 IEEE Wireless Communications and Networking Conference (WCNC), Milan, Italy, 24–27 March 2025; IEEE: Piscataway, NJ, USA, 2025. [Google Scholar]
- Gu, Y.; Shen, T.; Song, J.; Wang, Q. Enhancing secrecy capacity in pls communication with noran based on pilot information codebooks. arXiv 2023, arXiv:2310.01453. [Google Scholar] [CrossRef]
- Ma, X.; Lei, X.; Zhou, X.; Tang, X. Secrecy performance evaluation of scalable cell-free massive MIMO systems: A stochastic geometry approach. IEEE Trans. Inf. Forensics Secur. 2023, 18, 2826–2841. [Google Scholar] [CrossRef]
- Tubail, D.A.; Alsmadi, M.; Ikki, S. Physical layer security in downlink of cell-free massive MIMO with imperfect csi. IEEE Trans. Inf. Forensics Secur. 2023, 18, 2945–2960. [Google Scholar] [CrossRef]
- Nizam, F.; Ahmed, S.; Kumar, P.; Tsetse, A.; Kumar, R.; Shanker, B.; Sohu, N. Enhancing physical layer security in MIMO systems through beamforming and artificial noise techniques. J. Indep. Stud. Res. Comput. 2023, 21, 20–24. [Google Scholar] [CrossRef]
- Shi, E.; Zhang, J.; Du, H.; Ai, B.; Yuen, C.; Niyato, D.; Letaief, K.B.; Shen, X. Ris-aided cell-free massive MIMO systems for 6g: Fundamentals, system design, and applications. arXiv 2023, arXiv:2310.00263. [Google Scholar] [CrossRef]
- Munochiveyi, M.; Pogaku, A.C.; Do, D.-T.; Le, A.-T.; Voznak, M.; Nguyen, N.D. Reconfigurable intelligent surface aided multi-user communications: State-of-the-art techniques and open issues. IEEE Access 2021, 9, 118584–118605. [Google Scholar] [CrossRef]
- van Chien, T.; Ngo, H.Q.; Chatzinotas, S.; di Renzo, M.; Ottersten, B. Reconfigurable intelligent surface-assisted cell-free massive MIMO systems over spatially correlated channels. IEEE Trans. Wirel. Commun. 2022, 21, 5106–5128. [Google Scholar] [CrossRef]
- Chen, C.; Xu, S.; Zhang, J.; Zhang, J. A distributed machine learning-based approach for irs-enhanced cell-free MIMO networks. arXiv 2023, arXiv:2301.08077. [Google Scholar] [CrossRef]
- Xia, E.; Hu, B.J.; Shen, Q. Secret key generation with intelligent reflecting surface under the pilot contamination attack. IEEE Wirel. Commun. Lett. 2024, 13, 213–217. [Google Scholar] [CrossRef]
- Hong, S.; Pan, C.; Ren, H.; Wang, K.; Nallanathan, A. Artificial-noise-aided secure MIMO wireless communications via intelligent reflecting surface. IEEE Trans. Commun. 2020, 68, 7851–7866. [Google Scholar] [CrossRef]
- Elhoushy, S.; Ibrahim, M.; Hamouda, W. Exploiting ris for limiting information leakage to active eavesdropper in cell-free massive MIMO. IEEE Wirel. Commun. Lett. 2022, 11, 443–447. [Google Scholar] [CrossRef]
- Hao, W.; Li, J.; Sun, G.; Zeng, M.; Dobre, O.A. Securing reconfigurable intelligent surface-aided cell-free networks. IEEE Trans. Inf. Forensics Secur. 2022, 17, 3720–3733. [Google Scholar] [CrossRef]
- Siddiqi, M.Z.; Munir, A.; Mohsan, S.A.H.; Shah, S.; Chaudhary, S.; Sangwongngam, P.; Wuttisittikulkij, L. Low-complexity beamforming design for a cooperative reconfigurable intelligent surface-aided cell-free network. Sensors 2023, 23, 903. [Google Scholar] [CrossRef]
- Wang, Y.; Fan, J.; Luo, J.; Yu, S.; Zhang, J. Secure transmission in star-ris-assisted cell-free networks: Maximizing weighted sum secrecy rate. IEEE Commun. Lett. 2024, 28, 2001–2005. [Google Scholar] [CrossRef]
- Camana, M.R.; Abdullah, Z.; Garcia, C.E.; Sheemar, C.K.; Lagunas, E.; Chatzinotas, S. Multi-active ris-assisted thz cell-free systems: Spectral and energy efficiency tradeoff. arXiv 2025, arXiv:2505.08287. [Google Scholar]
- Zhao, J.; Zhang, Q.; Ai, T.; Wei, X.; Peng, F. Optimal reconfigurable intelligent surface deployment for secure communication in cell-free massive multiple-input multiple-output systems with coverage area. Electronics 2025, 14, 241. [Google Scholar] [CrossRef]
- Abdrabou, M.; Gulliver, T.A. Secure authentication in MIMO systems: Exploring physical limits. Front. Commun. Netw. 2024, 5, 1370496. [Google Scholar] [CrossRef]
- Gupta, A.; Barthwal, A.; Vardhan, H.; Kakria, S.; Kumar, S.; Parihar, A.S. Evolutionary study of distributed authentication protocols and its integration to uav-assisted fanet. Multimed. Tools Appl. 2023, 82, 42311–42330. [Google Scholar] [CrossRef]
- Dixit, P.; Gupta, A.K.; Trivedi, M.C.; Yadav, V.K. Traditional and hybrid encryption techniques: A survey. In Networking Communication and Data Knowledge Engineering, Proceedings of the International Conference on Recent Advancement in Computer, Communication and Computational Sciences (ICRACCCS 2016), Udaipur, India, 25–26 November 2016; Lecture Notes on Data Engineering and Communications Technologies; Springer: Singapore, 2018; Volume 4, pp. 239–248. [Google Scholar] [CrossRef]
- Bai, L.; Zhu, L.; Liu, J.; Choi, J.; Zhang, W. Physical layer authentication in wireless communication networks: A survey. J. Commun. Inf. Netw. 2020, 5, 237–264. [Google Scholar] [CrossRef]
- Illi, E.; Qaraqe, M.; Althunibat, S.; Alhasanat, A.; Alsafasfeh, M.; de Ree, M.; Mantas, G.; Rodriguez, J.; Aman, W.; Al-Kuwari, S. Physical layer security for authentication, confidentiality, and malicious node detection: A paradigm shift in securing iot networks. IEEE Commun. Surv. Tutor. 2023, 26, 347–388. [Google Scholar] [CrossRef]
- Alhoraibi, L.; Alghazzawi, D.; Alhebshi, R.; Rabie, O.B.J. Physical layer authentication in wireless networks-based machine learning approaches. Sensors 2023, 23, 1814. [Google Scholar] [CrossRef]
- Asim, J.; Khan, A.S.; Saqib, R.M.; Abdullah, J.; Ahmad, Z.; Honey, S.; Afzal, S.; Alqahtani, M.S.; Abbas, M. Blockchain-based multifactor authentication for future 6g cellular networks: A systematic review. Appl. Sci. 2022, 12, 3551. [Google Scholar] [CrossRef]
- Mobini, Z.; Ngo, H.Q.; Matthaiou, M.; Hanzo, L. Cell-free massive MIMO surveillance of multiple untrusted communication links. IEEE Internet Things J. 2024, 11, 33010–33026. [Google Scholar] [CrossRef]
- Martins, J.; Conceição, F.; Gomes, M.; Silva, V.; Dinis, R. Cell-free ap selection and phy security for multi-eavesdropper detection. TechRxiv 2020. [Google Scholar] [CrossRef]
- Solanki, N. Review analysis on cell free MIMO technology. Int. J. Sci. Res. Technol. 2024, 1, 300–303. [Google Scholar]
- Jiang, W.; Schotten, H.D. Cost-effectiveness analysis and design of cost-efficient cell-free massive MIMO systems. arXiv 2024, arXiv:2406.00538. [Google Scholar]
- Lin, R.; Xu, L.; Fang, H.; Huang, C. Efficient physical layer key generation technique in wireless communications. Eurasip J. Wirel. Commun. Netw. 2020, 2020, 13. [Google Scholar] [CrossRef]
- Zhang, X.; Guo, D.; An, K.; Zhang, B. Secure communications over cell-free massive MIMO networks with hardware impairments. IEEE Syst. J. 2020, 14, 1909–1920. [Google Scholar] [CrossRef]
- Mitev, M.; Pham, T.M.; Chorti, A.; Barreto, A.N.; Fettweis, G. Physical layer security—From theory to practice. IEEE BITS Inf. Theory Mag. 2023, 3, 67–79. [Google Scholar] [CrossRef]
- Li, G.; Sun, C.; Zhang, J.; Jorswieck, E.; Xiao, B.; Hu, A. Physical layer key generation in 5g and beyond wireless communications: Challenges and opportunities. Entropy 2019, 21, 497. [Google Scholar] [CrossRef] [PubMed]
- Mitev, M.; Chorti, A.; Belmega, E.V.; Poor, H.V. Protecting physical layer secret key generation from active attacks. Entropy 2021, 23, 960. [Google Scholar] [CrossRef]
- Interdonato, G. Cell-Free Massive MIMO: Scalability, Signal Processing and Power Control; Tech. Rep.; Linköping University Electronic Press: Linköping, Sweden, 2020. [Google Scholar]
- Prashanth, B.U.; Pandurangaiah, Y. Generation of secret key for physical layer to evaluate channel characteristics in wireless communications. arXiv 2013, arXiv:1308.1206. [Google Scholar] [CrossRef]
- Zoli, M.; Barreto, A.N.; Köpsell, S.; Sen, P.; Fettweis, G. Physical-layer-security box: A concept for time-frequency channel-reciprocity key generation. Eurasip J. Wirel. Commun. Netw. 2020, 2020, 114. [Google Scholar] [CrossRef]
- Zhang, J.; Liu, X.; Cui, Y.; Xu, D. Physical-layer secret key generation in power line communication networks. IEEE Access 2022, 10, 48539–48550. [Google Scholar] [CrossRef]
- Liang, X. Authentication Techniques Based on Physical Layer Attributes. Master’s Thesis, KTH, School of Electrical Engineering and Computer Science (EECS), Stockholm, Sweden, 2022. [Google Scholar]
- Perazzone, J.; Yu, P.; Sadler, B.; Blum, R. Artificial noise-aided MIMO physical layer authentication with imperfect csi. IEEE Trans. Inf. Forensics Secur. 2021, 16, 2173–2185. [Google Scholar] [CrossRef]
- Mitev, M.; Chorti, A.; Reed, M.; Musavian, L. Authenticated secret key generation in delay-constrained wireless systems. EURASIP J. Wirel. Commun. Netw. 2020, 2020, 122. [Google Scholar] [CrossRef]
- Fang, H.; Wang, X.; Tomasin, S. Machine learning for intelligent authentication in 5g and beyond wireless networks. IEEE Wirel. Commun. 2019, 26, 55–61. [Google Scholar] [CrossRef]
- Zhao, C.; Du, H.; Niyato, D.; Kang, J.; Xiong, Z.; Kim, D.I.; Shen, X.; Letaief, K.B. Generative ai for secure physical layer communications: A survey. IEEE Trans. Cogn. Commun. Netw. 2024, 11, 3–26. [Google Scholar] [CrossRef]
- Senigagliesi, L.; Ciattaglia, G.; Gambi, E. Autoencoder-based physical layer authentication in a real indoor environment. Phys. Commun. 2025, 70, 102626. [Google Scholar] [CrossRef]
- Meng, R.; Xu, B.; Xu, X.; Sun, M.; Wang, B.; Han, S.; Lv, S.; Zhang, P. A survey of machine learning-based physical-layer authentication in wireless communications. J. Netw. Comput. Appl. 2025, 235, 104085. [Google Scholar] [CrossRef]
- Saqib, R.; Khan, A.S.; Javed, Y.; Ahmad, S.; Nisar, K.; Abbasi, I.A.; Haque, M.R.; Julaihi, A.A. Analysis and intellectual structure of the multi-factor authentication in information security. Intell. Autom. Soft Comput. 2022, 32, 1633–1647. [Google Scholar] [CrossRef]
- Mitev, M.; Shakiba-Herfeh, M.; Chorti, A.; Reed, M.; Baghaee, S. A physical layer, zero-round-trip-time, multifactor authentication protocol. IEEE Access 2022, 10, 74555–74571. [Google Scholar] [CrossRef]
- Le, T.; Lu, C.-F.; Hsu, C.-L.; Do, T.K.; Chou, Y.-F.; Wei, W.-C. A novel three-factor authentication protocol for multiple service providers in 6g-aided intelligent healthcare systems. IEEE Access 2022, 10, 28975–28990. [Google Scholar] [CrossRef]
- Wang, J.; Huberman, B. A guide to global quantum key distribution networks. arXiv 2021, arXiv:2012.14396. [Google Scholar] [CrossRef]
- Dharminder, D.; Mishra, D.; Li, X. Construction of rsa-based authentication scheme in authorized access to healthcare services. J. Med. Syst. 2020, 44, 6. [Google Scholar] [CrossRef] [PubMed]
- Liu, K.; Xu, G.; Cao, Q.; Wang, C.; Jia, J.; Gao, Y.; Xu, G. A rivest-shamir-adleman-based robust and effective three-factor user authentication protocol for healthcare use in wireless body area networks. Sensors 2023, 23, 8992. [Google Scholar] [CrossRef] [PubMed]
- Zapatero, V.; van Leent, T.; Arnon-Friedman, R.; Liu, W.-Z.; Zhang, Q.; Weinfurter, H.; Curty, M. Advances in device-independent quantum key distribution. npj Quantum Inf. 2023, 9, 10. [Google Scholar] [CrossRef]
- Srinivas, K.; Sagar, K. Secure-key management protocols for wireless sensor networks in internet of things. AIP Conf. Proc. 2024, 2971, 020005. [Google Scholar] [CrossRef]
- Femenias, G.; Hinarejos, M.; Riera-Palou, F.; Ferrer-Gomila, J.; Jaume-Barcelo, A. Dynamic spectrum sharing in a blockchain enabled network with multiple cell-free massive MIMO virtual operators. IEEE Access 2024, 12, 70615–70633. [Google Scholar] [CrossRef]
- Hewa, T.; Ylianttila, M.; Liyanage, M. Survey on blockchain based smart contracts: Applications, opportunities and challenges. J. Netw. Comput. Appl. 2021, 177, 102857. [Google Scholar] [CrossRef]
- Morar, C.; Popescu, D. A survey of blockchain applicability, challenges, and key threats. Computers 2024, 13, 223. [Google Scholar] [CrossRef]
- Zhou, Z.; Onireti, O.; Xu, H.; Zhang, L.; Imran, M. Ai and blockchain enabled future wireless networks: A survey and outlook. Distrib. Ledger Technol. Res. Pract. 2024, 3, 1–30. [Google Scholar] [CrossRef]
- Zuo, Y.; Guo, J.; Gao, N.; Zhu, Y.; Jin, S.; Li, X. A survey of blockchain and artificial intelligence for 6g wireless communications. IEEE Commun. Surv. Tutor. 2023, 25, 2494–2528. [Google Scholar]
- Hasan, K.M.B.; Sajid, M.; Lapina, M.; Shahid, M.; Kotecha, K. Blockchain technology meets 6g wireless networks: A systematic survey. Alex. Eng. J. 2024, 92, 199–220. [Google Scholar] [CrossRef]
- da Silva, W.G.I.; Mobini, Z.; Ngo, H.-Q.; Matthaiou, M. Csi acquisition in cell-free massive MIMO surveil-lance systems. arXiv 2024. [Google Scholar] [CrossRef]
- Hoang, T.; Duong, T.; Tuan, H.; Lambotharan, S.; Hanzo, L. Physical layer security: Detection of active eavesdropping attacks by support vector machines. IEEE Access 2021, 9, 31595–31607. [Google Scholar] [CrossRef]
- Shekhar, S.; Srinivasan, M.; Kalyani, S.; Alouini, M.-S. Outage probability analysis of uplink cell-free massive MIMO network with and without pilot contamination. arXiv 2021, arXiv:2101.07737. [Google Scholar] [CrossRef]
- Segura, G.A.N.; Borges Margi, C.; Nunez Segura, G.; Chorti, A. Centralized and distributed intrusion detection for resource constrained wireless sdn networks. IEEE Internet Things J. 2021, 9, 7746–7758. [Google Scholar] [CrossRef]
- Stomaci, A.; Marabissi, D.; Mucchi, L. Comparisonofmachinelearningapproachesbasedonmultiplechannelattributes for authentication and spoofing detection at the physical layer. J. Commun. 2024, 19, 99–106. [Google Scholar] [CrossRef]
- Du, P.; Zhang, C.; Jing, Y.; Fang, C.; Zhang, Z.; Huang, Y. Jamming detection and channel estimation for spatially correlated beamspace massive MIMO. arXiv 2024, arXiv:2410.14215. [Google Scholar] [CrossRef]
- Yang, L.; Naser, S.; Shami, A.; Muhaidat, S.; Ong, L.; Debbah, M. Towards zero touch networks: Cross-layer automated security solutions for 6g wireless networks. IEEE Trans. Commun. 2025, 73, 7650–7679. [Google Scholar] [CrossRef]
- Xiao, Y.; Mähönen, P.; Simić, L. Mobility performance analysis of scalable cell-free massive MIMO. In Proceedings of the ICC 2022—IEEE International Conference on Communications, Seoul, Republic of Korea, 16–20 May 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 2543–2548. [Google Scholar] [CrossRef]
- D’Andrea, C.; Interdonato, G.; Buzzi, S. User-centric handover in mmwave cell-free massive MIMO with user mobility. In Proceedings of the 2021 29th European Signal Processing Conference (EUSIPCO), Dublin, Ireland, 23–27 August 2021; IEEE: Piscataway, NJ, USA, 2021. [Google Scholar] [CrossRef]
- Kim, S. Performance analysis of handover algorithms in scalable cell-free massive MIMO systems. In Proceedings of the 2024 15th International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Republic of Korea, 16–18 October 2024; IEEE: Piscataway, NJ, USA, 2024. [Google Scholar] [CrossRef]
- Zaher, M.; Björnson, E.; Petrova, M. Soft handover procedures in mmwave cell-free massive MIMO networks. arXiv 2023, arXiv:2209.02548. [Google Scholar] [CrossRef]
- Ammar, H.; Adve, R.; Shahbazpanahi, S.; Boudreau, G.; Srinivas, K. Handoffs in user-centric cell-free MIMO networks: A pomdp framework. IEEE Trans. Wirel. Commun. 2024, 23, 10319–10335. [Google Scholar] [CrossRef]
- Zaher, M. Practical Deployment Aspects of Cell-Free Massive MIMO Networks. Ph.D. Thesis, KTH Royal Institute of Technology, Stockholm, Sweden, 2023. [Google Scholar]
- Atiya, Y.S.; Mobini, Z.; Ngo, H.-Q.; Matthaiou, M. Cell-free massive MIMO with multiple active eavesdroppers. IEEE Open J. Commun. Soc. 2025, 1, 1859–1872. [Google Scholar] [CrossRef]
- Ullah, Y.; Roslee Mb Mitani, S.M.; Khan, S.A.; Jusoh, M.H. A survey on handover and mobility management in 5g hetnets: Current state, challenges, and future directions. Sensors 2023, 23, 5081. [Google Scholar] [CrossRef] [PubMed]
- Kiran, K.; Rao, D.R. Analytical review and study on various vertical handover management technologies in 5g heterogeneous network. Infocommun. J. 2022, 14, 28–38. [Google Scholar] [CrossRef]
- Rehman, A.U.; Roslee, M.B.; Jun Jiat, T. A survey of handover management in mobile hetnets: Current challenges and future directions. Appl. Sci. 2023, 13, 3367. [Google Scholar] [CrossRef]
- Vitor, J.; Fraga, O.; Palhano, I.B.; Guerreiro, I.M. Cluster handover analysis for a single-user cell-free MIMO network. In Proceedings of the Brazilian Symposium on Telecommunications and Signal Processing (SBrT), Belém, Brazil, 1–4 October 2024. [Google Scholar]
- Jeong, B.; Lee, S.; Siddiqa, A.; Ajmal, M.; Seo, J.; Kim, D. Experimental analysis of handover process in cell-free networks. In Proceedings of the 2023 Research in Adaptive and Convergent Systems (RACS), Gdansk, Poland, 6–10 August 2023; Association for Computing Machinery: New York, NY, USA, 2023. [Google Scholar] [CrossRef]
- Hoseini, S.A.; Sadeghi, P.; Bouhafs, F.; Aboutorab, N.; Den Hartog, F. Network-controlled physical-layer security: Enhancing secrecy through friendly jamming. In Proceedings of the 2022 IEEE Symposium on Computers and Communications (ISCC), Rhodes, Greece, 30 June–3 July 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–7. [Google Scholar]
- Karakus, M. Gate-bc: Genetic algorithm-powered qos-aware cross-network traffic engineering in blockchain-enabled sdn. IEEE Access 2024, 12, 36523–36545. [Google Scholar] [CrossRef]
- Papazafeiropoulos, A.; Kourtessis, P.; Di Renzo, M.; Chatzinotas, S.; Senior, J.M. Performance analysis of cell-free massive MIMO systems: A stochastic geometry approach. IEEE Trans. Veh. Technol. 2020, 69, 3523–3537. [Google Scholar] [CrossRef]
- Phu, A.T.; Li, B.; Ullah, F.; Huque, T.U.; Naha, R.; Babar, M.A.; Nguyen, H. Defending sdn against packet injection attacks using deep learning. Comput. Netw. 2023, 234, 109935. [Google Scholar] [CrossRef]
- Allaw, Z.; Zein, O.; Ahmad, A.M. Cross-layer security for 5g/6g network slices: An sdn, nfv, and ai-based hybrid framework. Sensors 2025, 25, 3335. [Google Scholar] [CrossRef]
- Chen, X.; Feng, W.; Ge, N.; Zhang, Y. Zero trust architecture for 6g security. IEEE Netw. 2023, 38, 224–232. [Google Scholar] [CrossRef]
- Iliadis, L.A.; Zaharis, Z.D.; Sotiroudis, S.; Sarigiannidis, P.; Karagiannidis, G.K.; Goudos, S.K. The road to 6g: A comprehensive survey of deep learning applications in cell-free massive MIMO communications systems. EURASIP J. Wirel. Commun. Netw. 2022, 2022, 68. [Google Scholar] [CrossRef]
- Ranjbar, V.; Girycki, A.; Rahman, A.; Pollin, S.; Moonen, M.; Vinogradov, E. Cell-free mMIMO support in the o-ran architecture: A phy layer perspective for 5g and beyond networks. IEEE Commun. Stand. Mag. 2022, 6, 28–34. [Google Scholar] [CrossRef]
- Chiti, F.; Degl’Innocenti, A.; Pierucci, L. Secure networking with software-defined reconfigurable intelligent surfaces. Sensors 2023, 23, 2726. [Google Scholar] [CrossRef] [PubMed]
- Bounaqaia, S.; Boulouird, M. Advancements and applications of channel estimation techniques in cell-free massive MIMO architectures for 5g and 6g communication networks. In Proceedings of the International Workshop on Information Technology and Communication (IWITIC), Marrakesh, Morocco, 20 May 2024. [Google Scholar]
- Yadav, R.; Kamran, R.; Jha, P.; Karandikar, A. Applying sdn to mobile networks: A new perspective for 6g architecture. arXiv 2023, arXiv:2307.05924. [Google Scholar] [CrossRef]
- Salaun, L.; Yang, H.; Mishra, S.; Chen, C.S. A gnn approach for cell-free massive MIMO. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Rio de Janeiro, Brazil, 4–8 December 2022; IEEE: Piscataway, NJ, USA, 2024. [Google Scholar] [CrossRef]
- Mohammadi, M.; Mobini, Z.; Ngo, H.Q.; Matthaiou, M. Next-generation multiple access with cell-free massive MIMO. Proc. IEEE 2024, 112, 1372–1420. [Google Scholar] [CrossRef]
- Hua, T.D.; Mohammadi, M.; Ngo, H.Q.; Matthaiou, M. Swipt in cell-free massive MIMO using stacked intelligent metasurfaces. arXiv 2025, arXiv:2503.14032. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2026 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license.