Abstract
Aiming at the problem of resource allocation optimization of heterogeneous mobile wireless sensor (HMWS) networks in bridge structural health monitoring, this study proposes an enhanced coverage strategy for heterogeneous sensors based on an improved Hiking Optimization Algorithm (HOA). This paper integrates the Good Point Set theory with a heterogeneous degree-of-freedom t-distribution perturbation mechanism to improve the basic HOA, developing the GPTHOA with global optimization characteristics. Based on this, a virtual force-guided HMWS coverage enhancement strategy (the VF-GPTHOA) is proposed. After determining the optimal deployment scheme, the GPTHOA is further employed to optimize node movement trajectories, minimizing the movement distance. Simulation results show that when deploying 60 heterogeneous sensors of three types in a 40 m × 200 m bridge model (BM), the coverage rate (CR) of the VF-GPTHOA reaches 97.07%, which represents improvements of 13.81%, 4.18%, 15.81%, 2.52%, and 12.44% over DE, MA, GWO, SSA, and HOA, respectively. In dynamic node scale scenarios, the VF-GPTHOA maintains optimal coverage performance, demonstrating its robustness and applicability in engineering practice.
1. Introduction
As critical components of modern transportation systems, bridges constitute essential infrastructure that directly influences national economic development and public safety. Throughout their designed service lifespan, these civil engineering structures must maintain structural integrity and serviceability while withstanding cumulative traffic loads and extreme environmental challenges, including seismic events, hydrodynamic forces during floods, and wind-induced vibrations during storms [1]. However, prolonged exposure to such operational stressors inevitably leads to progressive performance degradation, manifested through material fatigue, structural damage accumulation, and surface irregularities. These structural deteriorations not only compromise the load-bearing capacity but also adversely affect vehicular dynamics, potentially triggering catastrophic failure mechanisms that could result in incalculable socioeconomic consequences [2,3].
As of the end of 2023, China has built 1.0793 million highway bridges, an increase of 46,100 bridges compared with the previous year. In recent years, the growth rate of bridges has remained steady, with an average annual increase of 45,500 bridges. While maintaining an annual increase of several tens of thousands of new bridges, China is also tasked with managing and maintaining nearly one million existing bridges. Therefore, achieving efficient and safe operational management of this many bridges has become a pressing challenge. Indeed, many developed countries are facing the challenge of aging and inadequate infrastructure, coupled with limited financial resources for their maintenance. However, reliable bridge structural health-monitoring systems (BHMSs) offer the potential to transition from time-based inspection schedules to more cost-effective, condition-based maintenance strategies [4]. Currently, over 500 bridges in China are equipped with BHMSs, which play an increasingly significant role in bridge safety and lifespan prediction. By deploying a network of sensors on bridges, it is possible to continuously monitor environmental factors, load effects, and local and global structural responses [5]. The data provided by health-monitoring systems can be used to study the damage and performance degradation of in-service bridge structures and analyze and establish quantitative models for assessing the service safety and remaining lifespan of the structures, which is a critical research topic for improving the safety and durability of road bridges [6].
With the rapid development of Internet of Things (IoT) technology and Wireless Sensor Networks (WSNs), BHMSs are now capable of the real-time collection and transmission of various physical parameter data, such as structural status, strain, displacement, acceleration, and temperature, through the self-organizing communication of wireless sensors. Compared with traditional wired deployment methods, wireless sensors can significantly reduce installation costs, saving at least 50% of expenses [7]. For example, on the Bill Emerson Memorial Bridge, 84 wired accelerometers were used, with installation costs exceeding USD 15,000 per channel, half of which was attributed to cable wiring costs [8,9,10]. Mobile wireless sensors are sensor devices capable of moving flexibly in physical space and transmitting data via wireless communication technologies. These sensor systems exchange data with remote data acquisition and processing systems through built-in wireless network modules, enabling them to perform data-monitoring tasks in various dynamic environments [11]. Due to their mobility, flexibility, low-cost, and wireless characteristics, the application of HMWSs in bridge monitoring not only improves accuracy and efficiency but also reduces maintenance costs, enhances emergency response capabilities, and contributes to extending the lifespan of bridges.
This paper addresses the issues of the rational deployment and coverage enhancement of HMWSs, focusing on maximizing the coverage area and minimizing the movement distance of HMWSs. The Hiking Optimization Algorithm (HOA) [12] features a novel structure with few control parameters, demonstrating strong optimization performance in solving numerous numerical optimization and engineering problems. This paper proposes an improved HOA (GPTHOA) based on Good Point Set theory and t-distribution perturbation with heterogeneous degrees of freedom, which is then combined with the virtual force algorithm (VFA) to form the VF-GPTHOA. This method is applied to optimize the deployment of HMWSs for bridge monitoring in a bridge model (BM). The core innovations and contributions of this paper include the following:
- Two strategies are adopted to improve the HOA and address the strong dependence on initial solutions and the lack of mechanisms to escape local optima in the HOA. First, the Good Point Set theory generates an evenly distributed initial population, enhancing the algorithm’s exploration and stability. Second, a t-distribution perturbation operator with heterogeneous degrees of freedom is introduced to perturb individuals randomly, and the Metropolis criterion is applied to accept poorer solutions with a certain probability, helping the algorithm escape local optima.
- The VFA is introduced and combined with the GPTHOA to form the VF-GPTHOA, improving the algorithm’s convergence speed and accuracy in solving the HMWS deployment optimization problem in the band-like deployment environment of bridges. Once optimization is completed, the GPTHOA determines the optimal paths for sensor nodes to minimize energy consumption.
- The performance of the GPTHOA is tested on the CEC2022 benchmark test functions. In the bridge model (BM), the VF-GPTHOA is applied to optimize the deployment of HMWS nodes. Simulation results demonstrate that the proposed VF-GPTHOA outperforms other algorithms in multiple performance metrics.
2. Related Works
Experts and scholars have primarily focused on virtual force algorithms and swarm intelligence optimization algorithms to improve WSN coverage and service quality. Especially in recent years, with the rapid development of swarm intelligence optimization algorithms, multiple approaches have been developed to address complex problems such as WSN coverage optimization.
2.1. Virtual Force Algorithm
The virtual force algorithm draws inspiration from the principles of mechanics in physics, treating the interactions between sensor nodes as manifestations of virtual forces. By properly adjusting the magnitude and direction of attraction and repulsion forces, nodes can autonomously adjust their positions based on the current network conditions, thereby reducing overlap between nodes and achieving better coverage [13]. Fei et al. [14] defined the attraction of grid points to sensor nodes and their thresholds and, by incorporating the virtual force between nodes and obstacles, improved the traditional algorithm. Simulation results demonstrate that this method exhibits superior performance in terms of coverage, energy consumption, redundancy, and connectivity. Kiani et al. [15] investigated the relationship between the repulsive force of adjacent nodes and the attractive force of target points by using the minimum number of sensor nodes. They proposed a greedy algorithm that optimizes network coverage performance through this strategy. To reduce coverage holes and achieve uniform distribution, Qin et al. [16] divided the monitoring area into a cellular grid, using heterogeneous sensor nodes with different sensing radii. They analyzed the virtual forces between nodes based on their distances and constructed a bipartite graph between the cellular grid and sensor nodes. Subsequently, they employed the vampire bat algorithm to match these two components, enhancing coverage and optimizing energy. Chao et al. [17] optimized the distribution of sensor nodes by setting two types of virtual forces. The first type of virtual force acts between sensor nodes, while the second type is the force generated between concentric rings after dividing the network into multiple equal-width concentric rings. Compared with other methods, this strategy shows significant advantages in improving coverage and extending network lifetime. To balance coverage and network lifetime in WSNs, Qi et al. [18] derived the minimum required number of sensors through mathematical analysis and enhanced WSNs’ coverage capability by combining the traditional virtual force algorithm with the Voronoi diagram (VFVG) while also reducing the movement distance of sensor nodes. Furthermore, based on the trust relationships between nodes, they proposed a novel trust-driven topology construction and maintenance method, which effectively extends the network’s lifespan.
N. Boufares et al. [19] extended the original virtual force algorithm (VFA) to three dimensions, resulting in the Three-Dimensional Virtual Force Algorithm (3DVFA), suitable for three-dimensional environments. Based on the dodecahedral tessellation principle, the 3DVFA defines distance thresholds and restricts the movement range of nodes, thereby improving network coverage and connectivity. However, the 3DVFA overlooks the feasibility of truncated octahedra in stacking three-dimensional regions, leading to inadequate coverage performance. Meanwhile, their team [20] proposed a distributed deployment algorithm based on an improved virtual force strategy. The algorithm ensures network connectivity, eliminates node oscillations, and reduces network energy consumption by deploying mobile sensor nodes within the three-dimensional region. Luo et al. [21] proposed the Three-Dimensional Virtual Force Coverage Algorithm (3D-VFCA), which enables the redeployment of underwater WSN nodes to restore higher coverage.
Although the virtual force algorithm plays a positive role in improving coverage performance, it is vulnerable to oscillation because it only considers the virtual force of a single node and ignores the layout of the whole network, which limits the coverage optimization effect of WSNs to a certain extent.
2.2. Intelligent Optimization Algorithm
Swarm intelligence-based coverage optimization algorithms do not rely on the problem itself and offer advantages such as scalability, robustness, and efficiency [11,22]. Inspired by the predation behavior of army ants, a novel Army Ant Search Optimization Algorithm was proposed in [23] and demonstrated superior performance in both local search and global exploration, showing to be particularly effective in optimizing the positions of sensor nodes. Wang et al. [24] improved the Gray Wolf Optimization (GWO) algorithm and introduced a new method for addressing perception blind spots and calculating three-dimensional surface coverage areas. This approach not only reduces network costs but also achieves broader coverage for Wireless Sensor Networks (WSNs). To address deployment issues in complex environments, the team optimized the GWO position update formula by incorporating a nonlinear convergence factor and elite strategy, thus improving the convergence accuracy of the algorithm. In WSN deployment, the improved algorithm achieved greater coverage with the minimum number of sensor nodes [25]. Wang et al. [26] proposed the Adaptive Multi-Strategy Artificial Bee Colony (SaMABC) algorithm to address the coverage optimization problem in Wireless Sensor Networks (WSNs). The algorithm introduces a new adaptive selection mechanism and search strategy, forming a multi-strategy pool. Additionally, by combining simulated annealing and dynamically adjusting the search step size, the overall performance of the algorithm is further improved. Simulation experiments demonstrate that this algorithm outperforms traditional methods across various deployment scenarios. Chowdhury et al. [27] combined Voronoi diagrams, the Firefly Algorithm, and k-means clustering to propose a novel energy-efficient coverage technique that effectively enhances coverage and reduces network energy consumption. Deepa et al. [28] introduced an enhanced whale optimization algorithm based on Levy flights to achieve coverage optimization. Syed et al. [29] proposed the Weighted Tunicate Swarm Algorithm based on weighted distance position updates, effectively balancing WSN coverage efficiency and energy consumption. In [30], the authors presented the Improved Gravitational Search Coverage Control Algorithm (IGSCCA), aimed at improving coverage and node utilization in WSNs while minimizing overlap between sensor nodes. The algorithm combines the virtual force algorithm with the gravity disturbance of grid points in an improved gravitational search algorithm during the coverage enhancement phase and introduces a sleep strategy based on safe sets during the node sleep phase, thereby optimizing network performance. Yao et al. [31] proposed the Virtual Force-Guided Improved Moth-Flame Optimization (VF-IMFO) algorithm. This algorithm enhances the moth search process by improving the position update formula, incorporating an adaptive inertia weight strategy, and using the collective force of nodes as a disturbance factor, thus effectively optimizing the search path of the moths. This method not only improves network coverage but also reduces the displacement of sensor nodes. Cao et al. [32] improved the original Swarm Spider Optimization (SSO) algorithm by incorporating neighborhood search, global search, and matching radius techniques to enhance the algorithm’s optimization performance. In addressing the coverage enhancement issue of heterogeneous WSNs, this algorithm significantly improves network coverage, thereby effectively reducing the number of coverage blind spots.
Biomimetic mechanism-based swarm intelligence optimization algorithms perform global optimal solution search for complex optimization problems by simulating the cooperative behavior of biological populations. These algorithms demonstrate significant advantages in multidimensional search and efficient parallel computation in the field of area coverage optimization. However, such algorithms still face technical bottlenecks in terms of parameter configuration and sensitivity to initial population distribution.
In summary, the virtual force algorithm drives nodes to rapidly respond to coverage holes through local force fields, demonstrating high timeliness in dynamic adjustments. However, its single-node force guidance mechanism is prone to inducing oscillations in complex and elongated bridge structures, leading to coverage fluctuations. In contrast, swarm intelligence optimization algorithms perform global optimal search through population collaboration, but their performance is highly sensitive to parameter settings and initial distribution, making them susceptible to premature convergence in complex and elongated bridge structures.
Relevant studies indicate that combining swarm intelligence optimization algorithms with virtual force algorithms can significantly improve the coverage and overall performance of WSNs [33]. Additionally, it is important to note, in accordance with the “No Free Lunch Theorem” [34], that no optimization algorithm performs best for all engineering problems. Given that the HOA has advantages such as fewer parameters and strong optimization capability, this paper proposes the VF-GPTHOA and successfully applies it to the key technology of HMWS coverage optimization in bridge monitoring.
3. Models and Definitions
3.1. Bridge Model (BM)
The WSN nodes required for bridge structural health monitoring are typically deployed at key locations on the bridge after its construction, based on specific monitoring needs and objectives. By deploying various types of wireless sensor nodes, the precise monitoring of the bridge’s health status can be achieved, enabling the timely detection of potential structural issues such as cracks, corrosion, and overloads. This provides a scientific basis for the maintenance and repair of the bridge, extending its service life and ensuring traffic safety [5,35]. HMWSs can adaptively adjust the deployment location according to the monitoring requirements and structural changes of the bridge so as to focus on monitoring the key parts of the bridge, especially in different areas of the bridge, or when abnormalities occur, it can quickly adjust the location to optimize the monitoring coverage. As shown in Figure 1, in order to quickly validate the theoretical method proposed in this paper, the BM treats the entire bridge as a two-dimensional plane with dimensions of , where represents the width of the bridge deck, represents its length, and . The HMWS is deployed in this model, and the base station can remotely control the HMWS through instructions.
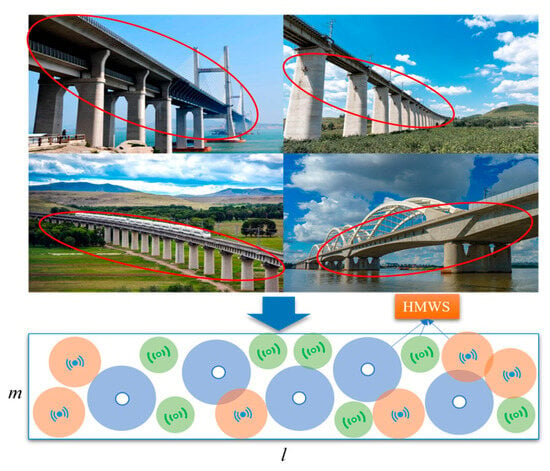
Figure 1.
The bridge monitoring model (Different colors and symbols represent different types of sensors).
3.2. Coverage Model
Currently, there are two primary sensing models in research on the coverage theory of WSNs: the Boolean sensing model and the probabilistic sensing model. The Boolean sensing model defines the coverage area of sensors through geometric relationships. Due to its simplicity, intuitiveness, and high computational efficiency, it has become a commonly used model for verifying the feasibility and effectiveness of proposed methods. Therefore, this paper adopts the Boolean sensing model to validate the coverage optimization method.
As shown in Figure 2, is the target monitoring point. The sensing range of a node is a circular area with as the center and as the radius (determined by the hardware characteristics of the node). Only the points within this area can be sensed and covered by the node. The communication radius of nodes generally satisfies . For ease of calculation, the monitoring area is divided into grid points. Let us suppose that the coordinate of the target monitoring point (that is, a grid point) is , and the coordinate of node is . Then, the mathematical expression of the Boolean perception model is shown in Equation (1).
where represents the sensing probability of node to target monitoring point and represents the Euclidean distance between two nodes, which is calculated by Equation (2).
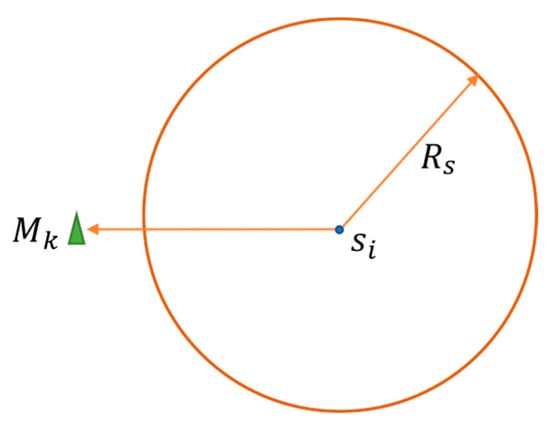
Figure 2.
Boolean sensing model.
3.3. Definitions
Definition 1 (coverage rate (CR)).
In the Boolean sensing model, when a target monitoring point is sensed by the sensor nodes set , the point is considered to be coverable. A monitoring point is not covered if none of the sensor nodes in set detect it. Therefore, as shown in Equation (3), the CR is defined as the ratio of the total number of grid points covered to the total number of grid points in the BM.
Definition 2 (coverage efficiency (CE)).
CE measures the effective utilization of sensor nodes. Larger values of CE result in a more uniform distribution of nodes and lower redundancy. As shown in Equation (4), CE is defined as the ratio of the total area of the monitoring area covered by all nodes to the total sensing area that all nodes should have covered.
Definition 3 (overlap ratio (OR)).
The OR is defined as the ratio of the total number of monitoring points covered repeatedly to the total number of grid points in the BM. When two or more sensor nodes in node set S cover monitoring point , then the grid point is repeatedly covered. A smaller OR represents a smaller overlap area and, at the same time, fewer redundant nodes. The OR of a monitoring point can be expressed by Equation (5).
When a monitoring point is covered by both nodes and (), it means that is covered repeatedly. The total probability of the repeated coverage of monitoring points in the BM of the whole monitoring area can be calculated according to Equation (6).
Therefore, the OR can be expressed by Equation (7).
Definition 4 (Average Moving Distance (AMD)).
Mobile sensor nodes can be re-deployed autonomously by moving, and the energy consumption in this process is mainly generated by node movement, which is mainly determined by the moving distance of the node [36]. Therefore, in this paper, the moving distance is used as a measure of node energy consumption. In the process of re-autonomous deployment, the moving distance of the sensor node is ; then, the average moving distance of all nodes in the network can be expressed by Equation (8).
3.4. The Theory of Optimal Coverage
The minimum number of sensor nodes to achieve complete coverage of the monitoring area is called optimal coverage [37]. As shown in Figure 3, when there is no overlap in the sensing range of the sensors, this scheme theoretically maximizes the sensing coverage of the sensor nodes. However, coverage gaps exist between any three nodes. To achieve complete coverage, the sensing ranges of any pair of adjacent sensor nodes should overlap by a constant amount, and the sensing ranges of any three adjacent sensor nodes should intersect at a single point. This deployment strategy allows the minimum number of sensor nodes to achieve complete coverage.
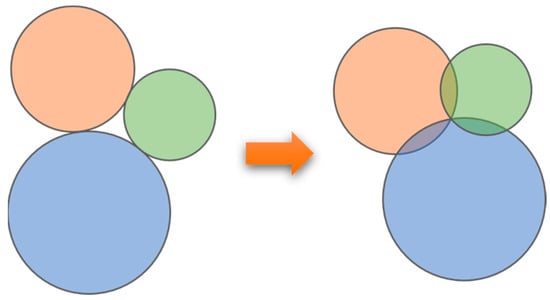
Figure 3.
Diagram of optimal deployment.
4. Hiking Optimization Algorithm (HOA)
The HOA was proposed by Sunday O. Oladejo et al. [12] in 2024, inspired by the experience of hikers attempting to ascend mountain ranges, hills, or rock peaks. During the hiking process, hikers consciously or unconsciously consider the steepness of the terrain, avoiding steep areas and narrow paths to maintain their hiking speed. The HOA simulates the characteristics of a hiking expedition where the ultimate goal is to reach the summit, with the environment being a rugged terrain that includes both local maxima and the global maximum. The situation experienced by hikers during the ascent is analogous to an agent trying to find a local or global optimum in an optimization problem.
The mathematical basis of the HOA is Tobler’s Hiking Function (THF), proposed by famous Swiss geographer Waldo Tobler in 1993, also known as Tobler’s walking equation [38]. This model describes the relationship between human movement speed and terrain slope, and its specific mathematical form is shown in Equation (9).
where represents the walking speed (in km/h) of traveler at time and is the slope of the terrain, which is given by Equation (10).
where and are the elevation and distance, respectively, and is the slope of the terrain or trail, and its value ranges within [0, 50°].
Figure 4 gives an image of the THF, which indicates that hikers move slower as the slope of the terrain increases. The negative exponential term in the equation captures this relationship. It should be noted that this function provides an estimate of walking speed and is based on the averaging assumption. Individual differences, physical fitness, road conditions, and other factors may affect the actual walking speed. Nonetheless, the Tobler walking function is widely used in Geographic Information Systems (GISs) and related fields to model pedestrian movement and accessibility analysis.
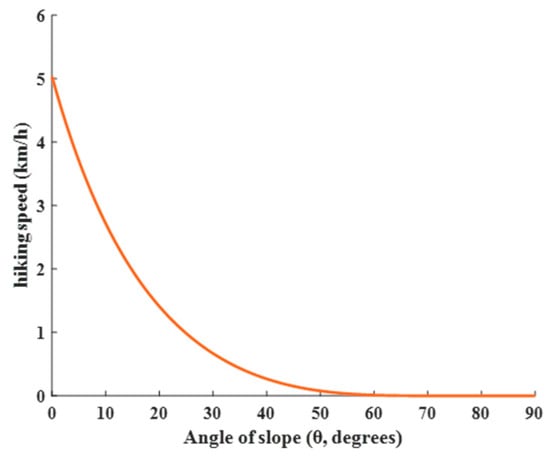
Figure 4.
Image of THF.
The HOA uses the hiker group’s social thinking and the individual hiker’s personal cognition to update the location. The current speed update formula of the traveler in the HOA is as follows:
where is a random number in [0, 1], and represent the current and initial velocities of traveler , is the position of the leader, is the position of traveler at time , and is the sweep factor (SF) of traveler in the range [1, 3], which ensures that the traveler does not stray too far from the leader, clearly sees the direction of the leader, and receives the signal from the leader.
By considering the velocity of the traveler in Equation (9), the position update of traveler is given by Equation (12).
Like most metaheuristic optimization algorithms, the HOA uses a random initialization technique to set the initial positions of the agents. The exploration and exploitation tendencies of the HOA are influenced by the SF, which affects the distance between the leader and other hikers. The slope of the terrain or path impacts the hiker’s speed. The HOA tends to favor the exploitation phase as the SF range increases, while a decrease in the SF range promotes the exploration phase. Additionally, a decrease in the slope leads the HOA to lean towards the exploitation phase.
The HOA is a global optimization algorithm that fully leverages hikers’ experience when traversing mountains and ascending peaks. At the beginning of the hike, the initial positions of the hikers are determined, and the THF is used to estimate the new positions of the travelers after a given time. The physical condition of all hikers is evaluated, and the fittest individual becomes the leader. In each iteration, the leader’s position is reassessed to ensure that the most suitable hiker is designated as the leader. Figure 5 presents the flowchart of the HOA.
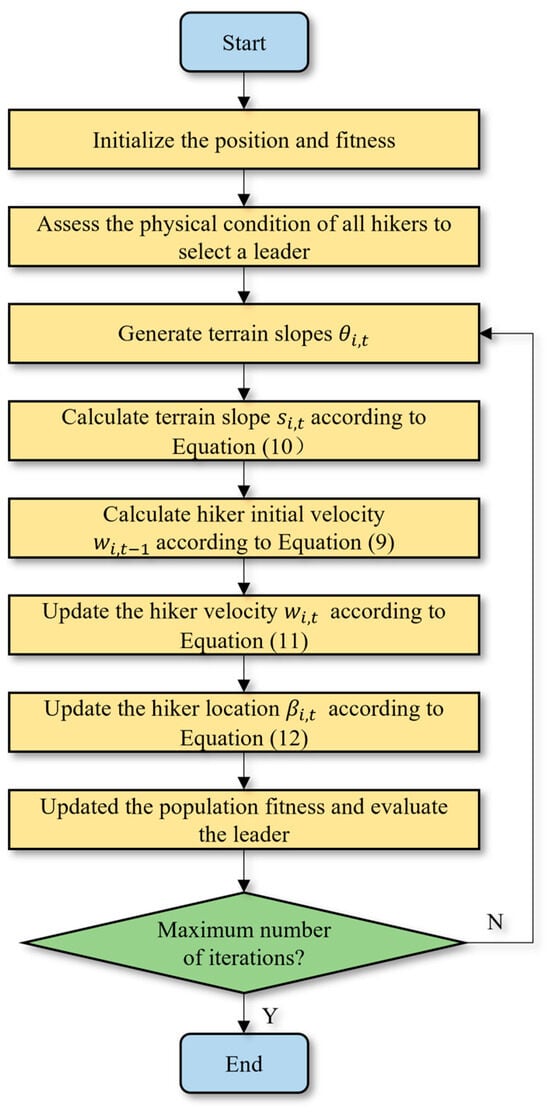
Figure 5.
The flowchart of the HOA.
5. HMWS Deployment Optimization Algorithm Based on GPTHOA
To improve the performance of HMWSs in secondary autonomous deployment optimization within BMs, this paper proposes a Hiking Optimization Algorithm based on the Good Point Set theory and heterogeneous-degree-of-freedom t-distribution perturbation (GPTHOA). The GPTHOA significantly enhances stability and the ability to escape local optima compared with the original HOA. Furthermore, this paper analyzes the virtual forces between HMWS nodes in the monitoring area. It uses the total virtual force at each node as an interference factor for updating the hiker’s search position. This guides the nodes to move towards the direction of coverage gaps, thus completing the secondary autonomous deployment optimization.
5.1. Initializing the Population by the Good Point Set
Using the Good Point Set strategy [39] to improve the population random initialization of the HOA can improve the convergence speed and stability of the HOA. The Good Point Set is defined as follows:
- Set is an unit cube in European space, namely, , where .
- Set contains a set of points , where .
- For any given point in , let denote the number of points in that satisfy the system of inequalities in (13).where and point set is considered to have a deviation . If, for any n, , then is considered to be uniformly distributed on with a deviation of .
- Let and the deviation of satisfy , where is a constant that depends only on and (with being an arbitrarily small positive number). In this case, is called a Good Point Set, and is called a good point.
- Let , where is the smallest prime number that satisfies , or let , . In this case, is a good point.
As shown in Figure 6, assuming a population size of 100, when initializing the population in a two-dimensional space, it can be visually observed that the population distribution initialized by using the Good Point Set strategy is more uniform. Therefore, this paper completes population initialization by mapping Good Point Set to the feasible region of the population, and the specific operation can be expressed as in (14).
where and denote the lower and upper bounds of the dimensional decision variable in the optimization problem, respectively.
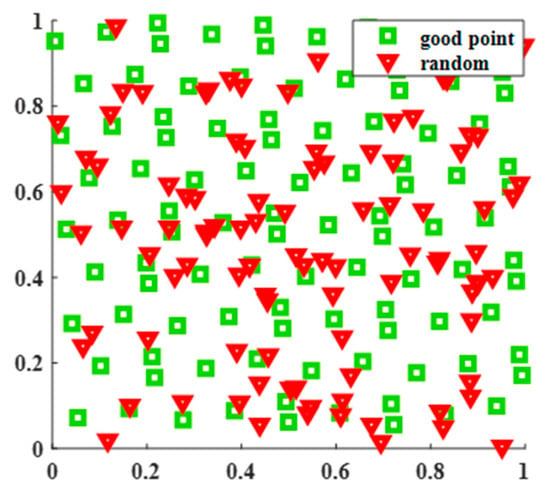
Figure 6.
Comparison of Good Point Set and random initialization.
5.2. Heterogeneous-Degree-of-Freedom t-Distributed Perturbation
The standard HOA lacks a mutation mechanism when performing a global search and can easily fall into a locally optimal solution. This paper introduces the t-distribution perturbation operator with heterogeneous degrees of freedom to randomly perturb the individuals, which endows the algorithm with diversity and stronger exploration ability. The proposed heterogeneous-degree-of-freedom t-distribution mutation perturbation formula is shown in (15).
where is the t-distribution with 10 degrees of freedom and is the t-distribution with 2 degrees of freedom. The selection of 2 degrees of freedom represents the minimum effective configuration (as variance becomes undefined at 1 degree of freedom), while that of 10 degrees of freedom approximates a normal distribution (which essentially coincides with the Gaussian distribution at 30 degrees of freedom). This parameter design ensures significant divergence between the two distributions while preventing computational instability caused by extreme parameter selection.
Figure 7 illustrates the t-distribution probability plots for different degrees of freedom. In the early stage of algorithm operation, plays a leading role, which makes the algorithm stable in global exploration and avoids falling into local optimal solutions. plays a leading role in the late iteration to achieve accurate local search and improve the optimization accuracy of the algorithm.
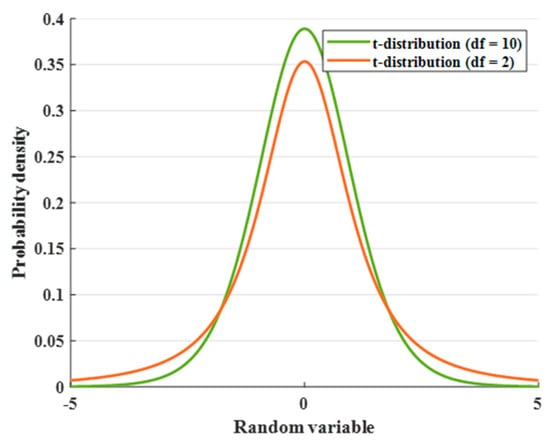
Figure 7.
Probability density plot of t-distribution.
After the new solution is generated by using t-distribution disturbance with different degrees of freedom, the simulated annealing algorithm is referred to according to the Metropolis criterion [40]. The worse solution is accepted with a certain probability to jump out of the local optimal value, to make up for the algorithm defects of the HOA. The parameters of the Metropolis criterion are set as initial temperature and cooling coefficient . The setting ensures adequate exploration capability in the solution space. The cooling rate of facilitates a smooth transition from global exploration to local exploitation. This parameter combination effectively balances the algorithm’s exploration–exploitation trade-off, significantly mitigating the risk of premature convergence.
The improved HOA in this paper is named GPTHOA, and its flow chart is shown in Figure 8.
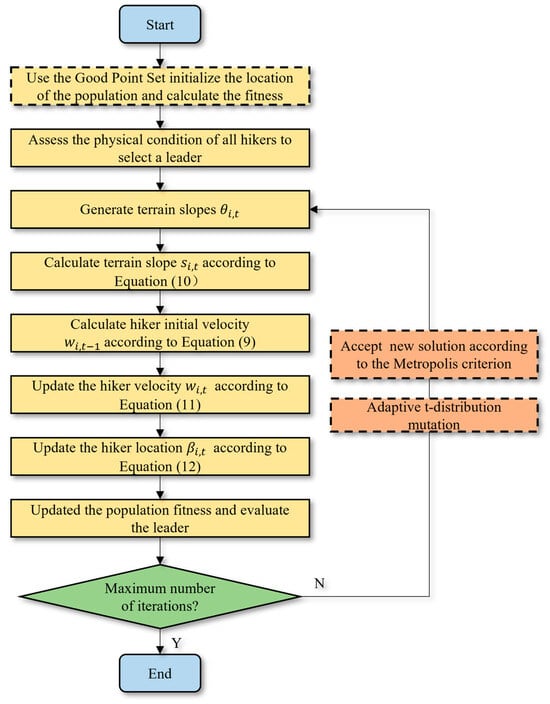
Figure 8.
The flowchart of the GPTHOA.
5.3. Performance Test of GPTHOA
To test the performance of the GPTHOA in terms of solution accuracy, convergence speed, and stability, the GPTHOA was compared with the HOA, the SSOA [41], and LCA [42,43] on the benchmark function CEC2022. Table 1 presents the relevant information on the test functions. The population size was set to 100, and the number of iterations was set to 500, with dimensions of 10 and 20. To eliminate randomness, 30 experiments were conducted to ensure accuracy. Table 2 shows the mean, maximum, minimum, and Friedman mean of the optimal solutions obtained by the four algorithms in different dimensions, where the best values for each evaluation criterion are in bold.

Table 1.
CEC2022.

Table 2.
The mean, maximum, minimum, and Friedman mean of the optimal solutions obtained by the four algorithms in different dimensions (the best values for each evaluation criterion are in bold).
Table 2 presents the optimization results of the SSOA, LCA, the HOA, and the GPTHOA on the benchmark function CEC2022 in different dimensions. Whether in the 10-dimensional or 20-dimensional case, the proposed GPTHOA significantly outperforms other algorithms in overall performance. Moreover, in the Friedman test, the GPTHOA achieves smaller mean values in different dimensions, indicating that the GPTHOA exhibits greater stability and consistency across multiple experiments. This is due to the GPTHOA’s use of an optimal point set to initialize the population, ensuring that the initial population includes individuals close to the optimal solution. The GPTHOA does not need to explore the entire search space from scratch, reducing the time required for search space exploration. Additionally, the t-distribution perturbation and simulated annealing operations help the algorithm escape local optima, enhancing its diversity. To visually observe the optimization performance of the algorithms, Figure 9 and Figure 10 show the four algorithms’ convergence processes and box plots while optimizing CEC2022 in different dimensions. The GPTHOA performs the best in convergence accuracy, speed, and stability compared with the other three algorithms. Whether in the 10-dimensional or 20-dimensional case, the GPTHOA demonstrates stronger optimization capabilities on over 10 functions, with the fastest and most stable convergence speed.
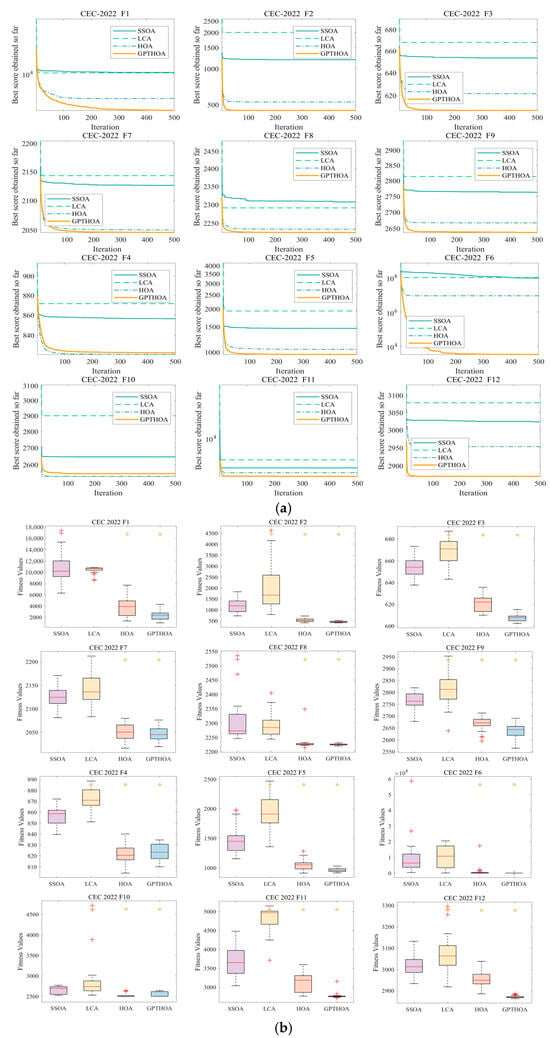
Figure 9.
Optimizing CEC2022 in 10 dimensions. (a) Convergence process and (b) box plots (red plus signs and orange asterisks indicate low and high outliers, respectively).
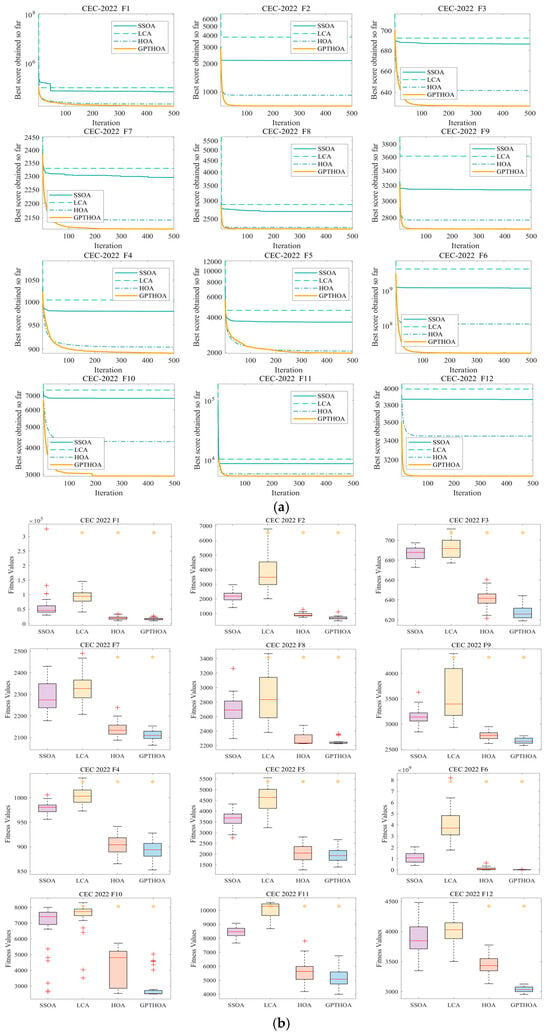
Figure 10.
Optimizing CEC2022 in 20 dimensions. (a) Convergence process and (b) box plots (red plus signs and orange asterisks indicate low and high outliers, respectively).
In summary, the GPTHOA’s advantages in convergence speed and optimization performance allow it to be applied to the optimization of HMWS deployment for bridge monitoring.
5.4. Virtual Force-Guided Coverage Optimization
Given that the virtual force algorithm (VFA) [13] has high convergence speed and can effectively overcome the issues of slow convergence and susceptibility to local optima in swarm intelligence optimization algorithms, this paper introduces the virtual force mechanism into the algorithm’s search process. The virtual force consists of three components: first, the virtual force between adjacent sensor nodes; second, the virtual attraction force for uncovered grid points; and third, the virtual repulsion force at the boundaries. The virtual resultant force , composed of these three forces, acts as a disturbance factor and guides the nodes to move toward the coverage holes. Under the influence of the virtual resultant force , the sensor moves from its original position () to the optimal position (), and the expression for the optimal position can be represented by Equation (16).
where and represent the projections of the resultant force on the x-axis and y-axis, respectively, and Mov_step represents the step size of the sensor node’s movement in each iteration. In the early stages of the algorithm, a larger step size is set to accelerate convergence. As the number of iterations increases, a smaller step size is adopted to prevent oscillation in the algorithm. The virtual movement step size gradually decreases throughout the iteration process, and its variation can be expressed by Equation (17).
where Max_st and Min_st represent the maximum and minimum movement step sizes, with values of 2 and 0.1, respectively. The parameter selection of a maximum step size of 2 and a minimum step size of 0.1 fundamentally reflects a trade-off between exploratory capacity (extensive spatial coverage) and exploitation precision (fine-grained adjustments) while incorporating sensor physical constraints and algorithmic convergence requirements.
The GPTHOA is combined with the VFA to form an effective bridge monitoring wireless sensor node deployment optimization strategy, called the Virtual Force-Guided GPTHOA (VF-GPTHOA). Table 3 shows the correspondence between HMWS deployment optimization and the VF-GPTHOA. Each hiker corresponds to a deployment scheme, with the hiker’s position and fitness value corresponding to the sensor node’s position and network coverage rate (CR), respectively.

Table 3.
Correspondence between deployment optimization and VF-GPTHOA.
The VF-GPTHOA is used to solve the bounded constrained optimization problem of maximizing the coverage of BWSN nodes, and its main steps are as follows (the pseudocode is shown in Algorithm 1):
Step 1: Initialize the BM’s size, the number of sensor nodes, the coverage range, the relevant parameters of the VF-GPTHOA, and the maximum number of iterations.
Step 2: Initialize the deployment solution set by using Equation (14), and calculate each individual’s fitness value by using Equation (3). It is important to note the conversion between the maximization problem and the minimization problem.
Step 3: The VF-GPTHOA begins optimization. Calculate the hiker’s initial velocity by using Equation (9), update the hiker’s velocity by using Equation (11), and update the hiker’s position by using Equation (12).
Step 4: After perturbation generates a new solution by using Equation (15), accept the worse solution with a certain probability based on the Metropolis criterion to avoid getting trapped in local optima.
Step 5: For hikers with poor fitness values, use the virtual force represented by Equations (16) and (17) to perturb and update their position.
Step 6: Update the hiker’s fitness value, and save the best individual, i.e., the leader.
Step 7: Check if the iteration count has reached the upper limit. If not, return to Step 3; if yes, proceed to Step 8.
Step 8: Output the leader’s information, including the leader’s position and final fitness value.
| Algorithm 1 VF-GPTHOA |
| Require: Sensor node set: ; Perceived distance: ; Total number of hikers: N and Maximum iterations: iter_max. Ensure: Sensor nodes’ location and CR. 1: Initialize the set of deployment scheme using (14). 2: for do //Iterate over all hikers (population individuals) 3: Evaluate a hiker’s fitness using (3). 4: end for 5: Generate initial optimal deployment schemes: //Record the current optimal deployment scheme t (highest fitness) 6: while //Main optimization loop (iteration number control) 7: for do //An independent search is performed for each hiker 8: Extract initial position of hiker i: 9: Determine terrain angle of elevation: 10: Compute the slope using (10). 11: Compute the initial hiking velocity using (11). 12: Determine the actual velocity using (11). 13: Update the hiker’s position using (12). 14: end for 15: Generate new deployment scheme by (15). 16: Decide whether to accept the new deployment scheme by Metropolis criterion. 17: Update the deployment schemes with poor CR by (16) and (17). 18: Update if there is a better solution. //Retain the historical best solution 19: //Iterate counter increment 20: end while 21: return //Return the optimal deployment and its coverage |
6. Simulation Results
To verify the comprehensive performance of the VF-GPTHOA proposed in this paper, the experiment uses Matlab R2022b as the simulation platform, with the hardware environment configured as an Intel(R) Xeon(R) Silver 4210R CPU, 64 GB of RAM (Lenovo Beijing, China), and a Windows Server 2016 Standard operating system. In the experimental design, a heterogeneous deployment scenario is constructed to compare and analyze the VF-GPTHOA with DE [44], MA [45], GWO [46], SSA [47], and the HOA in terms of key performance indicators (CR, CE, OR, and AMD) for sensor network coverage optimization. The relevant algorithm parameters are set in accordance with the original papers. Among them, DE is a classical global optimization algorithm in the field of evolutionary computation which has a mature parameter adjustment mechanism. MA is a new swarm intelligence algorithm proposed in recent years, which simulates mayfly mating and flight behavior and performs well in continuous optimization problems. GWO and SSA are designed based on the social hierarchy of animals and the foraging behavior of birds, respectively, and are representative methods in the field of swarm intelligence. These four comparison algorithms include classical and cutting-edge methods and are widely used to solve complex optimization problems, which can comprehensively verify the performance advantages of the new method.
The simulation experiment sets up deployment schemes for sensor nodes of varying scales to further investigate the algorithm’s adaptability to different scenarios. To reduce the impact of random errors on the results, it performs 20 independent repeated samples for each experiment by using the Monte Carlo method. The detailed experimental parameter configurations are shown in Table 4.

Table 4.
Details of simulation parameters.
6.1. Experiment 1
In this experiment, 20 heterogeneous sensor nodes with sensing radii of 10 m, 8 m, and 6 m are deployed in a monitoring area of 40 m × 200 m. According to the optimal deployment principle, these 60 sensor nodes can theoretically achieve full coverage of the monitoring area. The experimental results show that the VF-GPTHOA achieves over 96% CR. After optimizing heterogeneous sensor node deployment, the CR, CE, OR, and AMD performance metrics obtained from the VF-GPTHOA are evaluated and compared with the other five algorithms. The performance differences among the algorithms are shown in Figure 11, based on the mean statistics of 20 independent experiments.
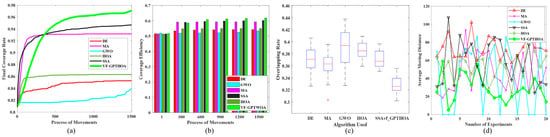
Figure 11.
Comparison of performance metrics of six algorithms. (a) The evolution of the CR; (b) The evolution of the CE; (c) The statistical results of the OR; (d) The statistical results of the AMD.
Figure 11a,b shows the evolution of the CR and CE for the six algorithms with the number of iterations. Figure 11c,d present the statistical results of the OR and AMD after 20 iterations of optimization by each algorithm during the experiment. Figure 11a shows that as the number of iterations increases, the CR of all six algorithms increases. Among them, the convergence curves of MA and SSA rise sharply in the early stages but clearly get trapped in local optima in the later stages. In contrast, the convergence curve of the VF-GPTHOA shows a steady increase, indicating that the algorithm combines fast convergence with the ability to escape local optima. This is demonstrated by its ability to avoid local optima even in the later stages of the algorithm. The superior performance of the VF-GPTHOA can be primarily attributed to its virtual force mechanism, which guides sensor nodes in directional migration through the attractive force exerted by uncovered grid points. In contrast, due to its single position update mechanism, the original HOA is prone to getting trapped in local optima and fails to achieve a global optimum. Experimental data show that the final iteration CR of the VF-GPTHOA reaches 97.07%, representing improvements of 13.81%, 4.18%, 15.81%, 2.52%, and 12.44% over DE, MA, GWO, SSA, and the HOA, respectively. In terms of the CE metric, the VF-GPTHOA leads with a value of 0.62, showing improvements ranging from 2.52% to 15.73% compared with the other algorithms. In terms of the OR metric, after 20 experimental repetitions, the OR value of the VF-GPTHOA remains stable within the range of 27–35%, fully verifying its optimization stability. For the AMD index, the VF-GPTHOA optimizes nodes’ initial and terminal position allocation before and after coverage optimization by the GPTHOA, significantly reducing the node migration distance.
To visually demonstrate the performance of the VF-GPTHOA, Figure 12 shows the deployment results after 1500 iterations for six algorithms. It is clearly evident that VF-GPTHOA optimization achieves the best coverage results. Table 5 and Table 6 present the average results and standard deviation of the CR, CE, OR, and AMD after 20 experimental tests for the six algorithms, respectively. The VF-GPTHOA performs the best in all four evaluation metrics.
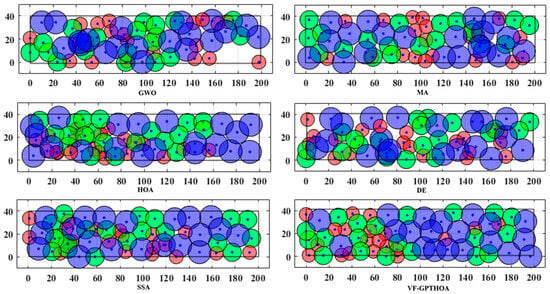
Figure 12.
Visualization of coverage effect of six algorithms.

Table 5.
Average results of six algorithms in 20 tests.

Table 6.
Standard deviation of six algorithms in 20 tests.
6.2. Experiment 2
To address factors such as the actual physical characteristics of sensor node deployment locations and the uncertainty in the number of nodes, a multi-node deployment scheme is implemented within the target monitoring area to validate the proposed algorithm’s optimization performance and generalization ability. The experiment is conducted in a 40 m × 200 m monitoring area, with 45, 51, 57, 63, and 69 nodes being deployed. The VF-GPTHOA is compared with five other algorithms—DE, MA, GWO, SSA, and the HOA—across four performance metrics: CR, CE, OR, and AMD. The experimental results are shown in Figure 13.
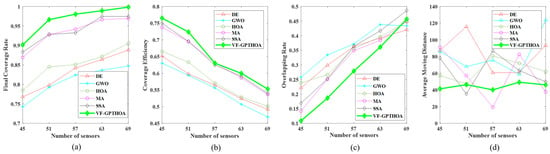
Figure 13.
Relationship between performance metrics and number of sensor nodes. (a) Comparison of the CR; (b) Comparison of the CE; (c) Comparison of the OR; (d) Comparison of the AMD.
After optimization with the six algorithms, the variation patterns of each metric with the number of sensor nodes show significant differences. As shown in Figure 13a, with the increase in the number of nodes, the CR values of all algorithms show an upward trend. The VF-GPTHOA consistently outperforms DE, MA, GWO, SSA, and the HOA for the same number of nodes in terms of the CR. As shown in Figure 13b, for the CE metric, all six algorithms exhibit a gradual decrease as the number of nodes increases, indicating a reduction in the uniformity of network node distribution and an increase in node redundancy. Notably, for the same node scale, the VF-GPTHOA, with its higher CR values, demonstrates superior CE performance compared with the other five algorithms, indicating lower coverage redundancy and better node distribution uniformity.
In terms of the OR metric, as shown in Figure 13c, with the network coverage approaching saturation, the OR values of all six algorithms increase with the number of nodes. When the number of deployed nodes is small, higher node dispersion helps improve network coverage. However, when the number of nodes exceeds 63, the network approaches full coverage, and further increases in nodes lead to intensified overlap in the sensing areas. As a result, the OR value of the VF-GPTHOA gradually becomes higher than that of DE, MA, and GWO. Figure 13d shows that the AMD metric of the VF-GPTHOA fluctuates less with the number of nodes, reflecting the stability advantage of the VF-GPTHOA. Regardless of the node deployment scale, the AMD of the VF-GPTHOA is always lower than that of the comparison algorithms. This is because other algorithms prioritize optimizing the CR and neglect the AMD metric, causing their AMD values to remain relatively high.
7. Conclusions
This paper investigates the problem of deployable and coverage enhancement of mobile heterogeneous wireless sensor nodes in bridge monitoring scenarios. It proposes a sensor node coverage optimization algorithm based on virtual force and the improved HOA called the VF-GPTHOA. Building upon the original HOA, the algorithm’s stability and global exploration capability are improved by introducing the theory of optimal point sets and the t-distribution perturbation of heterogeneous degrees of freedom. At the same time, by deeply analyzing the virtual force interaction mechanism between sensor nodes, the virtual force acting on the nodes is used as a perturbation factor for updating the hiker’s position. The virtual force and the step size decrease gradually with the number of iterations, further improving the coverage performance and avoiding oscillations in the later stages of the algorithm. After optimizing the node positions, the GPTHOA finds the shortest movement path for the nodes, reducing energy consumption. Simulation results show that the VF-GPTHOA effectively improves the coverage rate of heterogeneous sensor nodes, resulting in a more uniform node distribution than the other five algorithms.
It should be noted that this study still has the following limitations: First, the Boolean model uses binary coverage decision (complete coverage or no coverage) and ignores signal attenuation and obstacle interference, which leads to the overestimation of the effective coverage area and cannot reflect the actual change in the perceptual gradient in the complex bridge structure environment. Future research will extend this approach by using a probabilistic sensing model to enhance practical applicability. Second, this paper only presents simulation results. In the future, further validation of the proposed method’s practical applicability is required on a physical bridge or test platform. Third, the VF-GPTHOA faces scalability or time complexity issues, which need to be addressed in the future. Fourth, the deployment of Wireless Sensor Networks is essentially a multimodal multi-objective optimization problem. How to achieve Pareto-optimal deployment in the monitoring area through multi-objective algorithms will be a direction worthy of further exploration in the future.
Author Contributions
Conceptualization, methodology, C.M.; software, validation, C.M. and J.Y.; formal analysis, C.M. and J.Y.; investigation, C.M. and J.Y.; resources, J.H.; data curation, C.M. and J.Y.; writing—original draft preparation, C.M.; writing—review and editing, J.Y.; visualization, J.Y.; supervision, J.H.; project administration, J.H.; funding acquisition, J.H. All authors have read and agreed to the published version of the manuscript.
Funding
This research study was funded by National Nature Science Foundation of China, grant number 62262038; The Gansu Province Science and Technology Program-Innovation Fund for Small and Medium-Sized Enterprises, grant number 25CXGA014; Technology Innovation Guidance Program of Gansu Province—Science and Technology Specialist, grant number 25CXGA030; and 2025 “Innovation Star” Project for Postgraduates of Colleges and Universities in Gansu Province, grant number 2025CXZX-637.
Data Availability Statement
Data are contained within the article.
Acknowledgments
The authors would like to thank all the staff of 1301 Laboratory, School of Electronic and Information Engineering, Lanzhou Jiaotong University, for their support to this work.
Conflicts of Interest
The authors declare that there are no conflicts of interest in this paper.
References
- Civera, M.; Sibille, L.; Fragonara, L.Z.; Ceravolo, R. A DBSCAN-based automated operational modal analysis algorithm for bridge monitoring. Measurement 2023, 208, 112451. [Google Scholar] [CrossRef]
- Zheng, S.; Huo, J.; Yang, J.; Cao, F. An energy-efficient multi-hop routing protocol for 3D bridge wireless sensor network based on secretary bird optimization algorithm. IEEE Sens. J. 2024, 24, 38045–38060. [Google Scholar] [CrossRef]
- Deng, Z.; Huang, M.; Wan, N.; Zhang, J. The current development of structural health monitoring for bridges: A review. Buildings 2023, 13, 1360. [Google Scholar] [CrossRef]
- Martucci, D.; Civera, M.; Surace, C. Bridge monitoring: Application of the extreme function theory for damage detection on the I-40 case study. Eng. Struct. 2023, 279, 115573. [Google Scholar] [CrossRef]
- Yang, J.; Huo, J.; Mu, C. A Novel Clustering Routing Algorithm for Bridge Wireless Sensor Networks Based on Spatial Model and Multi-Criteria Decision Making. IEEE Internet Things J. 2024, 11, 27775–27789. [Google Scholar] [CrossRef]
- He, Z.; Li, W.; Salehi, H.; Zhang, H.; Zhou, H.; Jiao, P. Integrated structural health monitoring in bridge engineering. Autom. Constr. 2022, 136, 104168. [Google Scholar] [CrossRef]
- Wang, H.; Tao, T.; Li, A.; Zhang, Y. Structural health monitoring system for Sutong Cable-stayed Bridge. Smart Struct. Syst. 2016, 18, 317–334. [Google Scholar] [CrossRef]
- Chae, M.J.; Yoo, H.S.; Kim, J.Y.; Cho, M.Y. Development of a wireless sensor network system for suspension bridge health monitoring. Autom. Constr. 2012, 21, 237–252. [Google Scholar] [CrossRef]
- Linderman, L.E.; Mechitov, K.A.; Spencer, B.F., Jr. TinyOS-based real-time wireless data acquisition framework for structural health monitoring and control. Struct. Control Health Monit. 2013, 20, 1007–1020. [Google Scholar] [CrossRef]
- Zhou, G.D.; Yi, T.H.; Li, H.N. Wireless Sensor Placement for Bridge Health Monitoring Using a Generalized Genetic Algorithm. Int. J. Struct. Stab. Dyn. 2014, 14, 1440011. [Google Scholar] [CrossRef]
- Temene, N.; Sergiou, C.; Georgiou, C.; Vassiliou, V. A survey on mobility in wireless sensor networks. Ad Hoc Netw. 2022, 125, 102726. [Google Scholar] [CrossRef]
- Oladejo, S.O.; Ekwe, S.O.; Mirjalili, S. The Hiking Optimization Algorithm: A novel human-based metaheuristic approach. Knowl.-Based Syst. 2024, 296, 111880. [Google Scholar] [CrossRef]
- Li, Y.; Zhao, L.; Wang, Y.; Wen, Q. Improved sand cat swarm optimization algorithm for enhancing coverage of wireless sensor networks. Measurement 2024, 233, 114649. [Google Scholar] [CrossRef]
- Zhou, F.; Gao, J.; Fan, X.; An, K. Covering algorithm for different obstacles and moving obstacle in wireless sensor networks. IEEE Internet Things J. 2018, 5, 3305–3315. [Google Scholar] [CrossRef]
- Kiani, V. A greedy virtual force algorithm for target coverage in distributed sensor networks. In Proceedings of the 2020 10th International Conference on Computer and Knowledge Engineering (ICCKE), Mashhad, Iran, 29–30 October 2020; pp. 317–322. [Google Scholar]
- Wen, Q.; Zhao, X.-Q.; Cui, Y.-P.; Zeng, Y.-P.; Chang, H.; Fu, Y.-J. Coverage enhancement algorithm for WSNs based on vampire bat and improved virtual force. IEEE Sens. J. 2022, 22, 8245–8256. [Google Scholar] [CrossRef]
- Sha, C.; Ren, C.; Malekian, R.; Wu, M.; Huang, H.; Ye, N. A type of virtual force-based energy-hole mitigation strategy for sensor networks. IEEE Sens. J. 2019, 20, 1105–1119. [Google Scholar] [CrossRef]
- Qi, C.; Huang, J.; Liu, X.; Zong, G. A novel mobile-coverage scheme for hybrid sensor networks. IEEE Access 2020, 8, 121678–121692. [Google Scholar] [CrossRef]
- Boufares, N.; Khoufi, I.; Minet, P.; Saidane, L.; Saied, Y.B. Three dimensional mobile wireless sensor networks redeployment based on virtual forces. In Proceedings of the 2015 International Wireless Communications and Mobile Computing Conference (IWCMC), Dubrovnik, Croatia, 24–28 August 2015; pp. 563–568. [Google Scholar]
- Boufares, N.; Minet, P.; Khoufi, I.; Saidane, L. Covering a 3D flat surface with autonomous and mobile wireless sensor nodes. In Proceedings of the International Wireless Communications & Mobile Computing Conference, Valencia, Spain, 26–30 June 2017. [Google Scholar]
- Luo, C.; Cao, Y.; Xin, G.; Wang, B.; Lu, E.; Wang, H. Three-dimensional coverage optimization of underwater nodes under multiconstraints combined with water flow. IEEE Internet Things J. 2021, 9, 2375–2389. [Google Scholar] [CrossRef]
- Singh, A.; Sharma, S.; Singh, J. Nature-inspired algorithms for wireless sensor networks: A comprehensive survey. Comput. Sci. Rev. 2021, 39, 100342. [Google Scholar] [CrossRef]
- Yao, Y.-D.; Wen, Q.; Cui, Y.-P.; Zhao, F.; Zhao, B.-Z.; Zeng, Y.-P. Coverage enhancement strategy in WMSNs based on a novel swarm intelligence algorithm: Army ant search optimizer. IEEE Sens. J. 2022, 22, 21299–21311. [Google Scholar] [CrossRef]
- Wang, Z.; Xie, H. Wireless sensor network deployment of 3D surface based on enhanced grey wolf optimizer. IEEE Access 2020, 8, 57229–57251. [Google Scholar] [CrossRef]
- Wang, Z.; Xie, H.; Hu, Z.; Li, D.; Wang, J.; Liang, W. Node coverage optimization algorithm for wireless sensor networks based on improved grey wolf optimizer. J. Algorithms Comput. Technol. 2019, 13, 1748302619889498. [Google Scholar] [CrossRef]
- Wang, J.; Liu, Y.; Rao, S.; Zhou, X.; Hu, J. A novel self-adaptive multi-strategy artificial bee colony algorithm for coverage optimization in wireless sensor networks. Ad Hoc Netw. 2023, 150, 103284. [Google Scholar] [CrossRef]
- Chowdhury, A.; De, D. Energy-efficient coverage optimization in wireless sensor networks based on Voronoi-Glowworm Swarm Optimization-K-means algorithm. Ad Hoc Netw. 2021, 122, 102660. [Google Scholar] [CrossRef]
- Deepa, R.; Venkataraman, R. Enhancing Whale Optimization Algorithm with Levy Flight for coverage optimization in wireless sensor networks. Comput. Electr. Eng. 2021, 94, 107359. [Google Scholar] [CrossRef]
- Syed, M.A.; Syed, R. Weighted Salp Swarm Algorithm and its applications towards optimal sensor deployment. J. King Saud Univ.-Comput. Inf. Sci. 2022, 34, 1285–1295. [Google Scholar] [CrossRef]
- Yao, Y.; Liao, H.; Li, X.; Zhao, F.; Yang, X.; Hu, S. Coverage control algorithm for DSNs based on improved gravitational search. IEEE Sens. J. 2022, 22, 7340–7351. [Google Scholar] [CrossRef]
- Yao, Y.; Hu, S.; Li, Y.; Wen, Q. A node deployment optimization algorithm of WSNs based on improved moth flame search. IEEE Sens. J. 2022, 22, 10018–10030. [Google Scholar] [CrossRef]
- Cao, L.; Yue, Y.; Cai, Y.; Zhang, Y. A novel coverage optimization strategy for heterogeneous wireless sensor networks based on connectivity and reliability. IEEE Access 2021, 9, 18424–18442. [Google Scholar] [CrossRef]
- Yao, Y.; Li, Y.; Xie, D.; Hu, S.; Wang, C.; Li, Y. Coverage enhancement strategy for WSNs based on virtual force-directed ant lion optimization algorithm. IEEE Sens. J. 2021, 21, 19611–19622. [Google Scholar] [CrossRef]
- Meng, Z.; Zhong, Y.; Yang, C. CS-DE: Cooperative strategy based differential evolution with population diversity enhancement. Inf. Sci. 2021, 577, 663–696. [Google Scholar] [CrossRef]
- Yang, J.; Huo, J.; Mu, C. A Spatial Model and Multi-objective Fuzzy Inference-Based Clustering Routing Algorithm for Bridge Monitoring. IEEE Sens. J. 2024, 25, 1669–1681. [Google Scholar] [CrossRef]
- Liao, Z.; Wang, J.; Zhang, S.; Cao, J.; Min, G. Minimizing movement for target coverage and network connectivity in mobile sensor networks. IEEE Trans. Parallel Distrib. Syst. 2014, 26, 1971–1983. [Google Scholar] [CrossRef]
- Ammari, H.M.; Das, S.K. Coverage, connectivity, and fault tolerance measures of wireless sensor networks. In Proceedings of the 8th International Symposium, SSS 2006, Dallas, TX, USA, 17–19 November 2006; pp. 35–49. [Google Scholar]
- Goodchild, M.F. Beyond Tobler’s Hiking Function. Geogr. Anal. 2020, 52, 558–569. [Google Scholar] [CrossRef]
- Zhang, X.; Chen, H. An improved NSGA-III integrating a good point set for multi-objective optimal design of power inductors. J. Braz. Soc. Mech. Sci. Eng. 2024, 46, 586. [Google Scholar] [CrossRef]
- Amine, K. Multiobjective simulated annealing: Principles and algorithm variants. Adv. Oper. Res. 2019, 2019, 8134674. [Google Scholar] [CrossRef]
- Alzoubi, S.; Abualigah, L.; Sharaf, M.; Daoud, M.S.; Khodadadi, N.; Jia, H. Synergistic Swarm Optimization Algorithm. Comput. Model. Eng. Sci. 2024, 139, 2557–2604. [Google Scholar] [CrossRef]
- Houssein, E.H.; Oliva, D.; Samee, N.A.; Mahmoud, N.F.; Emam, M.M. Liver cancer algorithm: A novel bio-inspired optimizer. Comput. Biol. Med. 2023, 165, 107389. [Google Scholar] [CrossRef]
- Kalita, K.; Ramesh, J.V.N.; Čep, R.; Pandya, S.B.; Jangir, P.; Abualigah, L. Multi-objective liver cancer algorithm: A novel algorithm for solving engineering design problems. Heliyon 2024, 10, e26665. [Google Scholar] [CrossRef]
- Storn, R.; Price, K. Differential Evolution—A Simple and Efficient Heuristic for global Optimization over Continuous Spaces. J. Glob. Optim. 1997, 11, 341–359. [Google Scholar] [CrossRef]
- Zervoudakis, K.; Tsafarakis, S. A mayfly optimization algorithm. Comput. Ind. Eng. 2020, 145, 106559. [Google Scholar] [CrossRef]
- Mirjalili, S.; Mirjalili, S.M.; Lewis, A. Grey wolf optimizer. Adv. Eng. Softw. 2014, 69, 46–61. [Google Scholar] [CrossRef]
- Xue, J.; Shen, B. A novel swarm intelligence optimization approach: Sparrow search algorithm. Syst. Sci. Control Eng. 2020, 8, 22–34. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).