Abstract
The exponential growth of Internet infrastructure and the widespread adoption of smart sensing devices have empowered industrial personnel to conduct remote, real-time data analysis within the Industrial Internet of Things (IIoT) framework. However, transmitting this real-time data over public channels raises significant security and privacy concerns. To prevent unauthorized access, user authentication mechanisms are crucial in the IIoT environment. To mitigate security vulnerabilities within IIoT environments, a novel user authentication and key agreement protocol is proposed. The protocol is designed to restrict service access exclusively to authorized users of designated smart sensing devices. By incorporating cryptographic hash functions, chaotic maps, Physical Unclonable Functions (PUFs), and fuzzy extractors, the protocol enhances security and functional integrity. PUFs provide robust protection against tampering and cloning, while fuzzy extractors facilitate secure biometric verification through the integration of smart cards, passwords, and personal biometrics. Moreover, the protocol accommodates dynamic device enrollment, password and biometric updates, and smart card revocation. A rigorous formal security analysis employing the Real-or-Random (ROR) model was conducted to validate session key security. Complementary informal security analysis was performed to assess resistance to a broad spectrum of attacks. Comparative performance evaluations unequivocally demonstrate the protocol’s superior efficiency and security in comparison to existing benchmarks.
1. Introduction
The Industrial Internet of Things (IIoT) employs numerous devices for real-time data sensing, transmission, and analysis, improving industrial control, productivity, and product quality while reducing costs and resource consumption. However, as IIoT expands with Industry 5.0, the rapid proliferation and interaction of IoT devices introduce critical security challenges [1,2,3,4]. Many IIoT devices incorporate lightweight software and hardware to minimize costs, limiting their ability to support robust security comparable to traditional Internet environments. This limitation creates vulnerabilities, making devices prone to attacks. Furthermore, deployment in remote, unmonitored environments exacerbates risks, exposing critical industrial processes to malicious disruptions [5,6,7].
In general, a typical IIoT system comprises smart sensing devices, such as temperature and humidity sensors, vibration sensors, and RFID tags, alongside users and gateway nodes, collectively forming a wireless sensor network (WSN) [8,9,10]. However, the dependence on wireless communication technologies exposes IIoT systems to substantial security vulnerabilities, as malicious adversaries can compromise system security through attacks such as eavesdropping and message tampering [11,12,13]. Authentication and key agreement mechanisms are regarded as one of the most effective countermeasures against these threats [14,15,16]. Nevertheless, given the intrinsic resource limitations of sensing devices, authentication protocols deployed in such settings must carefully balance computational efficiency with robust security guarantees.
1.1. Existing Research and Motivation
Recently, numerous research efforts have focused on developing anonymous and lightweight authenticated key agreement protocols, aiming to enhance security, privacy, and efficiency in IIoT environments [17,18,19,20]. Turkanović et al. [21] proposed a mutual authentication scheme that relied on a pre-shared cryptographic key between the sensor node and the user. Their scheme employed simple hash and XOR operations to accommodate the resource constraints of WSN. However, a subsequent analysis by Tai et al. [22] demonstrated that the protocol developed by Turkanović et al. fails to provide anonymity and is susceptible to sensor-capture attacks. Chen et al. [23] introduced an authentication and key agreement protocol for industrial control systems. Nevertheless, their proposed solution suffers from high computational and communication overheads, susceptibility to ephemeral secret leakage (ESL) attacks, and a lack of perfect forward secrecy. Shuai et al. [24] proposed an authentication protocol utilizing the Rabin cryptosystem. However, their protocol remains vulnerable to offline guessing, user impersonation, privileged insider, eavesdropping, and stolen smart card attacks. Gong et al. [25] propose a certificateless anonymous mutual authentication scheme ensuring privacy, traceability, and scalability for IoT. The schemes presented in [26,27] rely on a clock synchronization assumption, limiting their applicability in practical IIoT deployments. Zhai et al. [28] proposed a lightweight authentication protocol that combines blockchain with chaotic maps to enable mutual authentication between smart devices and edge gateways in IIoT systems. However, their protocol relies solely on the security of the chaotic-map discrete logarithm problem and fails to provide anonymity and untraceability. Aman et al. [29] proposed a PUF-based device authentication protocol for IoT systems. However, subsequent analyses demonstrated that the protocol is susceptible to replay attacks and non-invasive physical attacks [30], and it does not account for the influence of environmental noise on PUF responses.
Rafique et al. [31] addressed a critical challenge in the IIoT concerning secure data transmission. Their research proposed a multifactor authentication key agreement protocol that balanced robust security with resource limitations. This protocol utilized bitwise XOR, cryptographic hash functions, and symmetric cryptography to create a secure system tailored for resource-constrained environments, ensuring high-level security while enabling remote access to sensing devices. However, ref. [32] identified that Rafique’s protocol is vulnerable to attacks involving the loss of smart cards or devices. Eldefrawy et al. [33] proposed a user authentication method for IIoT systems, focusing on computational and communication efficiency. While this protocol was efficient, it did not provide mutual authentication between users and the smart devices or sensor nodes within the system. Harishma et al. [34] developed a method for securing data transmission in cyber-physical systems with heterogeneous components. Nevertheless, their approach was found vulnerable to the ESL attack under the Canetti and Krawczyk (CK) adversary model [35]. Additionally, the protocol did not support the dynamic incorporation of new IoT smart devices, limiting its practical application. Chen et al. [36] designed a key agreement and user authentication system for IoT environments. Although their protocol was efficient in terms of computational and communication costs, it was vulnerable to insider attacks, node-capturing attacks, and gateway node-bypassing attacks, and lacked untraceability [37,38,39].
In summary, although several commendable AKA protocols have been proposed for IIoT systems, most remain impractical for deployment on resource-constrained smart sensing devices due to their substantial resource overhead [40,41,42]. Furthermore, their incomplete security and functional guarantees further diminish their applicability in real-world deployments. Addressing these limitations is critical to enabling the efficient and secure operation of IIoT environments. The comparative summary is given in Table 1.

Table 1.
Existing Authentication Protocols: A Comparative Summary.
1.2. Contribution
This paper proposes an anonymous and efficient Chaotic Map-based authentication protocol for the IIoT environment that ensures both efficiency and security. The main contributions are as follows:
- We propose a novel chaotic map-based mutual authentication and session key agreement protocol for the IIoT environment, where independent session keys are generated between users and smart sensing devices to ensure secure communications.
- We design the proposed protocol by integrating a one-way cryptographic hash function, chaotic map, physical unclonable function (PUF), and fuzzy extractor to enhance security and functional integrity. The PUF component provides robust protection against tampering and cloning attacks on the smart sensing device.
- We conduct a formal security analysis of the protocol using the real-or-random (ROR) model to rigorously assess and ensure session key security. Additionally, we provide an informal security analysis to demonstrate resistance to a broad spectrum of attacks.
- A rigorous comparative performance evaluation was conducted to assess the security, functionality, communication overhead, and computational efficiency of the proposed protocol in relation to existing benchmarks. The study clearly demonstrates the proposed protocol’s superior efficiency and enhanced security features compared to existing protocols.
1.3. Novelty
The proposed protocol introduces several key innovations that collectively address critical gaps in existing IIoT authentication protocols. First, it pioneers a hybrid security architecture that uniquely integrates authentication based on chaotic-map and lightweight cryptographic hashing with PUF-based device identity verification, achieving both algorithmic robustness and hardware-rooted trust. Unlike existing protocols that rely solely on lightweight cryptography or PUF, the proposed protocol further incorporates a fuzzy extractor to mitigate the impact of environmental disturbances on PUF responses in industrial settings. In addition, the protocol establishes an independent session key directly between the user and the device without involving a central entity, ensuring genuine end-to-end confidentiality for sensitive information. By avoiding the use of timestamps for replay protection, it also eliminates the dependence on strict clock synchronization. Finally, under a unified framework, the proposed protocol achieves the most comprehensive set of security features with exceptionally high efficiency, as demonstrated in its multidimensional comparison with existing protocols in terms of computational, runtime, communication, and storage overhead, an advantage unmatched by prior works. These contributions collectively position the proposed protocol as a holistic authentication framework expressly tailored to the distinct security and performance demands of IIoT environments.
1.4. Paper Organization
The remainder of this paper is organized as follows: Section 2 presents the background, including network and threat models, and foundational concepts. The proposed protocol is detailed in Section 3. A comprehensive security analysis is provided in Section 4 and formal security analysis is presented in Section 5. Section 6 offers a performance comparison with existing state-of-the-art protocols. Finally, the paper is concluded in Section 7.
2. Background
This section provides a comprehensive overview of the authentication model, threat model, and cryptographic foundations.
2.1. System Models
This section delineates the authentication model and threat models employed in the design of the proposed authentication and key agreement protocol.
2.1.1. Authentication Model
As illustrated in Figure 1, the proposed Internet of Things (IoT)-based smart sensing system for industrial monitoring aims to establish intelligent factories through the integration of IoT sensors and a robust authentication framework. This integrated system is designed to optimize supply chain, production, safety, and energy management. To address the challenges of securing real-time data transmission from resource-constrained IoT devices operating in inherently insecure wireless environments, a comprehensive authentication model is essential. This model safeguards data integrity and confidentiality while enabling authorized industrial personnel to securely access and utilize real-time data from smart sensing devices. A trusted registration authority (RA) establishes secure communication by registering all network entities and issuing cryptographic credentials. Authorized users, authenticated by the gateway node, can access the collected data through these gateway nodes, ensuring secure and reliable data transmission. The subsequent sections detail the proposed authentication protocol, which provides a secure and efficient mechanism for user authentication and data protection within the smart manufacturing environment [43,44,45].
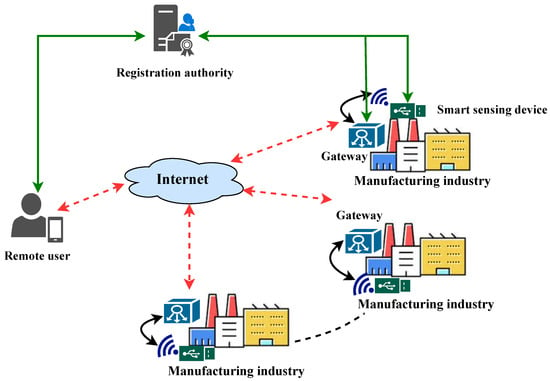
Figure 1.
IoT-based industrial monitoring system architecture.
2.1.2. Threat Model
To assess the security of the proposed protocol, this study adopts the widely recognized Dolev-Yao (DY) threat model [46,47]. Within this framework, an adversary is endowed with the capability to intercept, modify, delete, or inject spurious messages during communication over an insecure channel. Given the inherently hostile nature of the IIoT environment, IoT sensing devices are susceptible to physical compromise by , both internal and external. Such breaches can lead to the unauthorized acquisition of sensitive credentials stored within these devices. Furthermore, an may physically acquire an authorized user’s smart card, thereby enabling sophisticated power analysis attacks to compromise the stored secret credentials. Leveraging these credentials, the can potentially extract sensitive user data, including identity, password, and biometric information. This compromised position facilitates a range of attack vectors, such as privileged insider attacks, replay attacks, man-in-the-middle (MitM) attacks, and impersonation attacks. Recently, the CK adversary model [48,49,50] has emerged as the de facto standard for evaluating the security of authenticated key agreement protocols. This model extends the DY adversary’s capabilities by granting the attacker the power to compromise secret credentials, session states, and session keys. Consequently, a robust user authentication protocol for the IIoT must safeguard against the exposure of sensitive information, limiting the adversary’s ability to compromise additional credentials even if some secrets are compromised. In addition, gateway nodes are protected by hardware security boundaries (for example, HSM/TEE) to safely store . However, their databases are only semi-trusted and may be subject to physical capture attacks, allowing to extract the hashed credentials stored within them. The symbols used in this paper and respective description is given in Table 2.

Table 2.
Symbols and their definitions.
2.2. Preliminaries
This section provides a foundational overview of relevant cryptographic primitives, including PUFs, fuzzy extractors, and chaotic maps.
2.2.1. Physical Unclonable Function
The PUF is a cryptographic mechanism that relies on challenge-response pairs (CRPs). The core process of a PUF involves generating a unique response (output) when given a specific challenge (input) [51,52], which can be formalized with . Here, denotes the unique challenge presented to different devices (), while signifies the corresponding unique response. PUFs function as irreversible mathematical functions, deriving cryptographic secrets from inherent physical variations found in integrated circuits (ICs). These variations, stemming from the manufacturing process, ensure that each IC generates a unique response to specific challenges. PUFs provide a cost-effective solution with minimal computational requirements and energy consumption, making them highly suitable for lightweight and physically secure cryptographic applications. They are advanced circuit primitives used to generate secret keys for cryptographic operations. For example, the Static Random Access Memory (SRAM) PUF is widely adopted due to SRAM’s critical role in electronic control units (ECUs). The SRAM PUF exploits random disparities in SRAM threshold voltages to establish a distinctive digital fingerprint for each device. Unlike traditional methods of key storage, the secret key is dynamically regenerated from the SRAM PUF within a secure environment. This approach ensures that even in the event of a memory breach, the secret key remains protected and immune to compromise. Importantly, any attempt to manipulate or tamper with a PUF alters the device’s behavior, thereby invalidating the PUF and facilitating tamper detection. However, in real-world noisy environments, factors such as temperature variations, voltage fluctuations, and device aging may cause a PUF to produce different responses even when supplied with the same challenge, which can result in the erroneous rejection of secret parameters generated solely from PUF responses during authentication. To address this important issue, we integrate a fuzzy extractor with the PUF. During the registration phase, the device first generates a response . Subsequently, in an authentication session, the device regenerates a new response . When the Hamming distance falls within the tolerable error threshold t, the fuzzy extractor is used to reconcile , thereby ensuring stable key derivation.
2.2.2. Fuzzy Extractors
Fuzzy extractors are cryptographic mechanisms designed to derive stable and secure cryptographic keys from inherently noisy data sources, such as biometric measurements or PUFs [53]. By mitigating the impact of noise and variations inherent in these data types, fuzzy extractors enhance the robustness and security of recognition systems. A fuzzy extractor consists of two primary components:
- Generation: Given a unique biometric or PUF measurement of entity i, the generation algorithm produces a cryptographic key and public auxiliary data .
- Reproduction: Utilizing the public auxiliary data and a noisy measurement approximating , the reproduction algorithm reconstructs the original key . For sufficiently similar input measurements (typically within a predetermined Hamming distance), will be identical to .
2.2.3. Chaotic Map
Chaotic map encryption leverages the intrinsic unpredictability and extreme sensitivity to initial conditions of chaotic systems for cryptographic applications [54,55,56]. This method employs the enhanced Chebyshev polynomial, defined as , where is a large prime number, , and . Alternatively, . The semigroup property of Chebyshev polynomials, expressed as , forms the basis for the encryption process. The security of this encryption scheme relies on the computational intractability of the chaotic map discrete logarithm problem (CMDLP). An adversary’s ability to solve this problem within a given time frame is quantified as , where and . Some existing studies [57,58,59] indicate that, may be able to solve the CMDLP problem in polynomial time, thereby compromising the security of cryptographic systems based on Chebyshev polynomials. However, this attack capability requires to obtain both
and x simultaneously. To counteract this, the proposed protocol maintains the encryption of x during transmission. The protocol is grounded in the computational Diffie-Hellman (CDH) problem adapted to the chaotic map domain. Even with knowledge of and , computing remains computationally infeasible for an adversary, providing the cryptographic strength of the system.
2.3. Design Objectives
The protocol aims to achieve the following design goals:
- Anonymity: Protect user privacy by ensuring that their identities cannot be inferred from messages, maintaining anonymity throughout communications.
- Mutual Authentication: Verify the authenticity of users, gateways, and smart sensing devices to establish trust within the network.
- Session Key Agreement: Securely establish session keys between users and smart sensing devices, independent of the gateway, for protected communication.
- Unlinkability: Prevent the correlation of intercepted messages with specific users, preserving message anonymity.
- Forward Security: Protect the confidentiality of past communications by ensuring the compromise of current session keys does not affect the security of previous sessions.
- Resistance to Common Attacks: Strengthen the protocol’s defenses against replay, offline password guessing, and impersonation attacks to enhance overall IIoT network security.
3. The Proposed Protocol
This section presents a secure protocol tailored for IIoT environments to guarantee that only authorized users can access smart sensing devices. The protocol incorporates SHA-256 hashing, XOR operations, and PUFs to safeguard smart sensing devices against physical tampering. Furthermore, to address replay attacks, the protocol avoids reliance on clock synchronization among network entities. The subsequent subsections outline the various phases of the proposed protocol.
3.1. Pre-Deployment Phase
In this phase, the RA is responsible for registering the GWNs and smart sensing devices prior to their deployment. A secure channel is assumed for this one-time setup, as commonly adopted in IIoT protocols, typically ensured through administrator-supervised or trusted in-person registration.
3.1.1. GWN Registration
The RA performs the following operations to register a GWN denoted as .
- Step GR-1: The RA selects a distinct and unique identity, , and a secret parameter, . These are then transmitted securely to through a secure channel.
- Step GR-2: securely stores the received parameters, , in its secure database.
3.1.2. Smart Sensing Device Registration
To register a smart sensing device, such as , the RA follows these steps:
- Step DR-1: The RA starts the registration process by generating a unique challenge parameter, . This parameter is securely transmitted to over a secure channel.
- Step DR-2: Upon receiving from the RA, uses a to generate the response parameter . This response is then securely sent back to the RA.
- Step DR-3: The RA selects an identity and sends the pair to the appropriate gateway node through a secure channel.
- Step DR-4: Upon receiving the from the RA, generates a random number and computes . It then stores the parameters for in its database and sends back to the RA through a secure channel.
- Step DR-5: The RA finally transmits the parameters to , which then stores these parameters in its memory.
3.1.3. User Registration
To ensure secure communication with an SD that has been accessed, must securely register at the RA through the following steps.
- Step UR-1: User submits their registration request to the RA, along with their identity , through a secure channel.
- Step UR-2: The RA then assesses whether the request originates from a legitimate user. It computes using a hash function, where is the master secret key of the RA and is the registration timestamp. Based on the computed hash, it consults the database for the corresponding status. If the status indicates that the user is already registered (), the registration process ceases. Otherwise, the RA proceeds with registration and picks a unique temporary identity , a unique pseudo-identity , and a random number . The user’s smart card is configured with <>. The RA stores <> in its database and forwards the following parameters to the corresponding gateway node as <> via a secure channel and dispatches to .
- Step UR-3: Upon receiving <> from the RA, computes . then stores the parameters as <> in its database.
- Step UR-4: Upon receipt, inserts into a card reader, reads the biometric data , and enters their and password and picks a random number . The smart card then proceeds to compute the following:where is a fuzzy extractor generator function and is an authentication parameter. Finally, the smart card replaces the parameters <> with <> and stores <>.
3.2. Login Phase
A legitimate user, for instance, , must first authenticate themselves using their credentials and smart card. The specific steps are as follows:
- Step L-1: User inserts their designated smart card and subsequently enters their unique identity (), password (), and provides biometric data () via the designated sensor.
- Step L-2: Based on the provided inputs, the following computations are carried out:The is verified against as follows: If the verification fails, the login procedure is aborted. If the verification succeeds, the sign-in process is considered successful, and the following parameters are computed: .
3.3. Authentication and Key Agreement Phase
The following steps are essential for completing this phase, as illustrated in Figure 2.
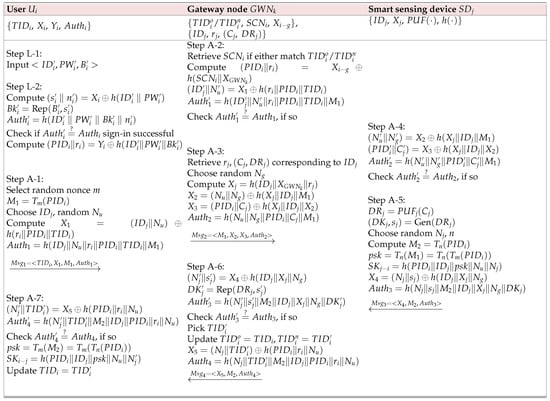
Figure 2.
Login and authentication phases.
- Step A-1: generates a random nonce m and uses it to compute as a chaotic-map variable. Then, chooses and selects random nonce , and calculates . Additionally, computes . Afterward, constructs and sends it to the gateway node through an open insecure channel.
- Step A-2: Upon receiving from , searches for , which should match either or . The following computations are then performed:The calculated is checked for equality with , i.e., . If they do not match, the process is terminated. If they match, the procedure continues to the next steps.
- Step A-3: For , retrieves and selects a random nonce . The following computations are then performed:Finally, constructs as and transmits it to through an open insecure channel.
- Step A-4: Upon receiving from , retrieves and and performs the following:The resulting is compared with to verify if . If they do not match, the process is aborted. If they match, the procedure proceeds to the next step.
- Step A-5: inputs the challenge into the function to obtain a device-specific but potentially noisy response, . Due to the inherent variability of PUFs caused by environmental and hardware factors, employs a fuzzy extractor to ensure reliable key derivation. Specifically, the fuzzy extractor generates a stable and reproducible secret key and corresponding helper data , denoted as . This process ensures that even if slightly fluctuates under different conditions, the same can be reliably recovered using the helper data during key reconstruction. Next, selects a random integral string n and a random nonce , and computes the following: , , , , and , where is the generated secret session key between and . Finally, constructs as and sends it to via an open insecure channel.
- Step A-6: Upon receiving from , performs the following computations:accepts the message if holds true. Next, picks a unique temporary identity and updates the old and new temporary identities as and . Then, computes and . Finally, sends to to via an open insecure channel.
- Step A-7: Upon receiving from , computes and . accepts if holds true. Next, computes , and . Finally, stores the session key and updates the temporary identity as .
3.4. Password and Biometrics Update Phase
The proposed protocol allows users to locally update their passwords without needing to interact with the RA. Users can modify both their password () and biometric information () by following these steps:
- Step PBU-1: The legitimate user inserts their smart card and authenticates themselves with their credentials to update their password and biometrics. The following calculations are then performed using the provided inputs:The is verified against as follows: If the verification fails, the login procedure is aborted. If the verification succeeds, can reset the password and update the biometrics data, and the following parameters are computed: .
- Step PBU-1: Next, inputs new information ( and ), and the card executes the following computations:Subsequently, the system updates the existing parameters in the smart card with the new configurations .
3.5. Smart Card Revocation
The protocol enables smart card replacement without altering the user’s identity. If user loses or has their smart card stolen, they can request a replacement from the RA using the following procedure:
- Step SCR-1: Initially, securely transmits their identity (), credentials, and a replacement request to RA. The RA assesses these credentials and the validity of the request. Following confirmation, RA issues a replacement smart card, , a unique pseudo-identity , and a random number . Consequently, the freshly configured smart card is configured with <>. The RA stores <> in its database and forwards the following parameters to the corresponding gateway node as < > via a secure channel and dispatches to .
- Step SCR-2: Furthermore, upon receipt of the card, inserts it into a card reader and performs the same steps as outlined in Section 3.1.3 (“User Registration”). Finally, the smart card stores .
3.6. Dynamic Smart Device Addition Phase
This phase is essential for subsequent deployment of new smart sensing devices. To integrate a new device, denoted as , the RA performs the following offline steps:
- Step DA-1: The RA starts the registration process by generating a unique challenge parameter, . This parameter is securely transmitted to over a secure channel.
- Step DA-2: Upon receiving from the RA, uses a to generate the response parameter . This response is then securely sent back to the RA.
- Step DA-3: The RA selects an identity and sends the pair to the appropriate gateway node through a secure channel.
- Step DA-4: Upon receiving the from the RA, generates a random number and computes . It then stores the parameters for in its database and sends back to the RA through a secure channel.
- Step DA-5: The RA finally transmits the parameters to , which then stores these parameters in its memory.
Once is deployed, the /RA will notify all registered users, enabling them to access services from if needed.
4. Informal Security Analysis
In this section, security and functional attributes of the proposed protocol are examined through a descriptive analysis.
4.1. Smart Sensing Device Capture Attack
The physical unclonability of PUF technology safeguards smart sensing devices, such as , against unauthorized access. Any tampering with the PUF-based sensor will significantly alter its response or disable the device entirely. Consequently, extracting sensitive information from the PUF-equipped becomes extremely challenging for potential attackers.
4.2. Gateway Node Capture Attack
Assume that is a privileged insider within the IIoT system who is capable of physically compromising a gateway node and thereby obtaining the secret credentials stored on it, namely and , where . However, due to the one-way property of the cryptographic hash function, the secret credentials and , which are bound to , remain protected since is stored within a hardware-isolated region that is inaccessible to . Moreover, does not store the identity , password , or biometric template of . Given only and the hashed credential , even if simultaneously acquires the user’s smart card, no valid information can be inferred that would compromise the security of the session key.
4.3. Anonymity and Untraceability
Considering the threat model described in Section 2.1.2, suppose that intercepts the transmitted messages to during the login and authentication processes, as illustrated in Figure 2, over an insecure public channel. These intercepted messages contain secret random nonces, which are crucial for maintaining confidentiality. This confidentiality makes it extremely difficult for to determine critical identifiers such as the user’s identity (), the user’s pseudo-identity (), or the smart sensing device’s identifier (). This mechanism ensures the anonymity of users and their associated smart sensing devices within the network. Additionally, the use of unique random nonces for each session prevents from tracking users across different sessions. Even if identifies the temporary identities of from the intercepted messages, the protocol’s design requires frequent renewal of these identifiers to new temporary ones () with each session. This ensures that tracking users and devices over time is not possible. Consequently, the proposed protocol effectively guarantees the anonymity and untraceability of participants, establishing a robust security foundation within the system.
4.4. De-Synchronization Attack
In our protocol, users are assigned unique temporary identities () during the registration phase. The gateway node () stores the parameters for each user . To counter de-synchronization attacks, the protocol maintains both the old and new temporary identities in the gateway node’s database, ensuring synchronization between and . This design ensures the protocol’s functionality remains unaffected even if the final confirmation message is delayed or lost, thereby providing robust protection against de-synchronization attacks.
4.5. Replay Attack
The proposed protocol safeguards against replay attacks where an adversary intercepts and attempts to reuse previously exchanged messages ( to ), where , , , and . The strength of the protocol lies in its use of unpredictable, one-time random values (nonces) within each transmitted message. These nonces guarantee that each message is unique to a specific session, rendering them useless in any subsequent attempt by to replay them. This effectively prevents replay attacks and ensures the protocol’s robustness.
4.6. MitM Attack
Even if an attacker ( ) intercepts messages ( to ) intending to tamper with them and impersonate a user, the protocol’s design thwarts such attempts. Modifying the initial message () requires access to secret information like , , and , which are beyond ’s reach. Similarly, for messages , , and , the protocol relies on confidential data like , , , and others to generate valid nonces. Without this information, cannot forge messages that appear legitimate. This ensures the protocol’s resistance to MitM attacks.
4.7. Mutual Authentication
The proposed protocol establishes mutual authentication between user , gateway , and sensor via the subsequent three steps: (1) validates by checking and ; (2) authenticates directly by verifying and indirectly by matching from the transcripts with ; (3) verifies to confirm directly and also indirectly confirms , establishing the session key independently of the gateway node.
4.8. Session Key Security
The proposed protocol ensures session key security through a multi-layered approach. An adversary cannot bypass local user authentication or access sensitive credentials such as and stored on the smart card in encrypted form. This protection is due to the requirement of all three factors (password, biometric data, and smart card) for login. Additionally, the session key is derived using a combination of a one-way hash function and unique, secret parameters specific to each user, device, and communication session. These parameters include , , , , and . The one-way nature of the hash function ensures that even without knowledge of these secret parameters, deriving the session key remains computationally infeasible. This approach safeguards the confidentiality and integrity of communication within the protocol.
4.9. Perfect Forward Secrecy
In the proposed protocol, the session key established between and is derived through a hybrid mechanism that combines random values, long-term secrets, and chaotic-map–based secrets, thereby ensuring perfect forward secrecy. First, these parameters are unique to each session and each communicating entity, preventing from correlating information across different sessions or participants. Second, in every authentication session, the random values used to compute the chaotic-map encryption outputs are randomly selected, and remains hidden from . Due to the inherent hardness of the CMDLP, can not derive that satisfies and . Moreover, the random values and long-term secrets that contribute to are protected by the cryptographic hash function and thus remain concealed from . Overall, through this hybrid derivation mechanism that incorporates both long-term and ephemeral secrets, the proposed protocol ensures that the security of does not rely on any single cryptographic component, thereby providing perfect forward secrecy.
4.10. ESL Attack
In the proposed protocol, the session key is generated between and with the help of . This key relies on session-specific and entity-specific secret information as well as random parameters. To assess the resilience of the key against ESL attacks, we examine two distinct scenarios:
- Scenario 1: If the attacker manages to obtain the temporary secrets , , , , and , the hash function ’s collision-resistant properties make it difficult for to derive the session key without also having access to the long-term secrets , , , , , and .
- Scenario 2: Even if gains possession of the long-term secrets , , , , , and , the absence of short-term secrets still makes it impractical for to compute the session key.
4.11. Stolen Smartcards and Privileged-Insiders Attacks
These scenarios explore the implications of a lost or stolen smartcard, , belonging to a registered user. The registration process commences with user transmitting to the RA via a secure channel. Suppose a privileged-insider within the RA, denoted as adversary , has access to the information . Subsequent to registration completion, it is assumed that adversary has gained possession of user ’s stolen smartcard, denoted as and then extracted the data from using power analysis attacks. Extracting or guessing from the values without knowing and of is computationally infeasible, as and are protected by a collision-resistant hash function . This demonstrates that identity guessing attacks are challenging for . Similarly, deriving from without and is computationally infeasible due to ’s collision resistance. Additionally, it is computationally infeasible for the adversary to derive from the extracted parameters. Thus, the system is robust against offline password guessing attacks, even in the case of stolen smartcards or privileged insider threats.
4.12. Resistance to Modeling Attacks
The proposed protocol prevents modeling attacks by avoiding challenge-response transmission over insecure channels. Using collision-resistant hash function and XOR to encrypt secret parameters, adversary cannot extract useful information from intercepted messages, ensuring security with minimal overhead.
4.13. Impersonation Attacks
To mitigate impersonation attacks, three scenarios are examined: Case I (User Impersonation Attack): Suppose an adversary intercepts the message . Using this information, tries to impersonate the user by crafting a modified message to deceive others. However, without knowledge of , , and , cannot produce a valid , rendering it incapable of establishing a credible communication with and thus preventing successful user impersonation.
Case II (Gateway Node Impersonation Attack): Consider the scenario where intercepts . To impersonate a gateway node, would need to fabricate to convince a smart sensing device of its authenticity. However, without knowledge of and , cannot compute , , and . Therefore, cannot create a valid to impersonate a gateway node, and similarly, cannot compute to deceive . Thus, fails to impersonate a gateway node.
Case III (Smart Sensing Device Impersonation Attack): When intercepts the message from to , impersonating requires crafting a credible . Nonetheless, lacking crucial information like , , , , , , and , fails to generate a legitimate . This inability to forge a valid message demonstrates the protocol’s effectiveness in thwarting attempts at impersonating the smart sensing device, underscoring its security against such types of attacks.
5. Formal Security Analysis
This section analyzes the security of the proposed protocol using the ROR model, formally proving session key security. Before presenting the session key proof (Theorem 1), we introduce essential ROR model primitives.
Participants. The proposed protocol involves three primary participants: the user , the gateway node , and the smart sensing device . Instances of these participants are represented as , , and , corresponding to the th instance of , the th instance of , and the th instance of , respectively. Each instance is treated as an oracle, and is occasionally used to denote the tth instance of any given entity.
Partnership. Entities and in the protocol are considered partners if they meet the following criteria: (1) Both entities have reached an acceptance state; (2) They share the same session identifier ; and (3) A session key has been established between them.
Freshness. An entity is considered to be fresh if its established session key has not been compromised by the adversary . An entity is deemed fresh if its established session key remains uncompromised by the adversary .
Adversary. In the ROR model, the adversary ’s capabilities are represented by conducting specific oracle queries: In the ROR model, the capabilities of the adversary are represented through specific oracle queries defined in Table 3. It is important to emphasize that, while is granted the ability to extract the secret credentials stored in a user’s smart card via the query, deriving either the long-term or ephemeral secrets from the hashed credentials remains well beyond ’s capability.

Table 3.
Adversary queries in the ROR model.
Definition 1
(Semantic Security). In the context of the RoR model, the adversary is tasked with distinguishing between the actual session key and a random string during the query. The adversary attempts to correctly guess the value of b to succeed in this challenge. The advantage of the adversary in compromising the semantic security of the proposed protocol P is denoted as and is defined by the equation . If there exists a sufficiently small function ϵ such that , then the proposed protocol P is considered to be semantically secure.
Definition 2
(Security of PUF). For two secure functions and , given any inputs and in , the probability that the Hamming distance exceeds d is . Here, d represents the fault tolerance level.
Definition 3
(CMDLP). The advantage of an adversary in solving the Chaotic Map Discrete Logarithm Problem (CMDLP) within a runtime of is considered negligible if it satisfies , where ϵ is a negligible function.
Theorem 1.
For the proposed protocol P, the adversary operates within polynomial time, aiming to compromise semantic security. Let denote the number of hash queries, the number of PUF queries, and the number of send queries. Additionally, let l represent the length of the biometric data, D be the uniformly distributed password dictionary, and the PUF has a key length of . Combining the aforementioned definitions, denotes the advantage of solving the CMDLP problem within time . Thus, we have:
We establish the provable security of the proposed protocol by defining a series of games . Specifically, in our protocol P, let denote the event where the adversary successfully guesses the value of b in the query within the game .
This game models an attack scenario where the adversary targets the protocol P. At the start, is tasked with determining the value of the bit b. The advantage of in this context is given by:
where represents the probability of succeeding in guessing b.
In this game, simulates an eavesdropping attack by performing multiple queries. Assume intercepts all messages through transmitted within the protocol. To determine the session key , must have access to specific long-term and short-term secret parameters. However, based on the informal security analysis, obtaining these parameters is impractical for . Therefore, the probability of successfully winning remains unchanged. Consequently, we have .
The primary distinction between and its predecessor, , lies in the incorporation of simulated and queries. In , performs an active attack, trying to deceive a participant into accepting forged messages. Although the adversary may conduct multiple hash queries on , , , and to identify potential collisions, the inclusion of random nonces, unique identifiers ( and ), and long-term secrets associated with each message renders this a highly improbable event. As a result, the likelihood of the adversary encountering a collision during queries is negligible. Moreover, applying the birthday paradox reinforces this assertion by indicating that
In , we simulate PUF queries. Applying the definition of secure PUF functions (Definition 2), we derive the following inequality:
The transition from to involves the addition of the query. By utilizing this query, the adversary will acquire the credentials and . To correctly identify and for from ( and , must have both the secret credential and the biometric key . By capping the number of unsuccessful identity/password or biometric verifications, the system upholds the following condition:
The final game involves endeavoring to compute the shared session key between and by exploiting intercepted communications and simultaneously solving the CMDLP instance (cf. Definition 3). To calculate the session key , needs and , where . It is evident that even with knowledge of , computing necessitates access to n. Similarly, determining requires knowledge of m, despite possessing . Consequently, must solve the CMDLP within a runtime of at most to obtain the session key . Therefore,
Taking into account all the games described earlier, after all the oracle queries have been executed, the adversary does not gain any extra advantage in correctly guessing the bit b in the query. Consequently, . Additionally, based on the calculations, we get:
Combining the results yields:
6. Performance Evaluation
In this section, we compare the proposed protocol with five state-of-the-art schemes [60,61,62,63,64], focusing on computational overhead, communication overhead, and security and functionality features.
6.1. Computational Overhead
This section analyzes the computational cost of our proposed protocol compared to existing ones. Core cryptographic operations underpinning user login and authentication are considered. We exclude basic operations like XOR and concatenation from the analysis. For the efficiency evaluation, we implemented all cryptographic primitives involved in the proposed protocol and the baseline protocols using Python 3.9.13, leveraging libraries such as hashlib, pypuf, and ecpy. We then measured their average execution times, including hash function (), ECC point multiplication (), PUF (), fuzzy extractor (), and chaotic map (). In addition, to support the testing procedures, a Raspberry Pi 4 equipped with 2 GiB of memory and running Raspberry Pi OS (32-bit) was used as the resource-constrained Platform I to simulate smart sensing devices, whereas a 64-bit Windows 10 machine with 8 GiB of memory and an Intel® Core™ i5-8300H CPU @ 2.30GHz was employed as the resource-rich Platform II to emulate gateway nodes and user devices. For each platform and cryptographic primitive, 1000 test runs were conducted. The resulting average execution times in milliseconds are tabulated in Table 4.

Table 4.
Average execution time of various primitives.
Table 5 summarizes the computational overheads of different protocols. Our protocol incurs a computation overhead of approximately on resource-constrained smart sensing devices (Platform-I). This is lower than the overhead of protocols proposed by the benchmark protocols of Hammad et al. [60], Wazid et al. [61], and Sutrala et al. [63]. This indicates better suitability for resource-constrained settings. While the total computation overhead of our protocol ( ms) exceeds that of some existing solutions Yang et al. [62] and Srinivas et al. [64], it offers superior security and functionality features, as detailed in Table 5. This trade-off between efficiency and security is a crucial consideration for real-world deployments.

Table 5.
Computation overheads comparison (ms).
6.2. Runtime Comparison
In this subsection, a comprehensive performance evaluation is conducted by implementing the complete workflows of both the proposed protocol and its baseline protocols in Python on a Windows 10 experimental machine equipped with an Intel® Core™ i5-8300H CPU @ 2.30GHz processor and 8 GiB of memory. Each protocol underwent 100 runs, and the average execution time for the integrated login and AKA phase is recorded; comparative results appear in Figure 3. Empirical data indicate that the proposed protocol attains an average runtime of 1013.86 ms, outperforming the protocols of Hammad et al. [60] (1016.38 ms), Sutrala et al. [63] (1024.63 ms), Wazid et al. [61] (1041.15 ms), and Yang et al. [62] (1019.19 ms). Although its overhead is marginally higher than that of the protocol proposed by Srinivas et al. [64], this slight increase is offset by the additional security features and functional enhancements delivered by the proposed protocol (see Table 8).
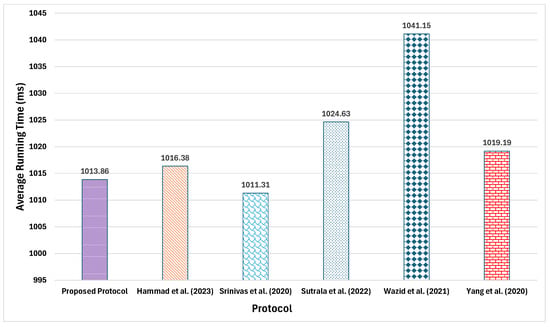
Figure 3.
Comparison of computation overheads.
6.3. Communication Overhead
Table 6 presents a comparison of the communication overhead of various protocols, highlighting the number of bits needed for message exchanges. The communication overhead is quantified in bits for each protocol. To ensure a fair evaluation, the following assumptions are made: timestamps are considered to be 32 bits; identities, random numbers, chaotic map-based encryption outputs, and PUF responses are considered to be 128 bits; hash digest outputs are 256 bits; and ECC points are 320 bits. The analysis reveals that the total communication overhead of the proposed protocol is 2944 bits, which is lower than the 3616 bits, 3360 bits, 5376 bits, and 3200 bits required by the benchmark protocols Hammad et al. [60], Wazid et al. [61], Yang et al. [62], and Sutrala et al. [63], respectively. Thus, the proposed protocol is more resource-efficient. Moreover, while the proposed protocol’s communication overhead is slightly higher than that of Srinivas et al. [64], this increase is justified by its enhanced and comprehensive security features, as outlined in Table 8.

Table 6.
Communication overheads comparison.
6.4. Storage Overhead
Building on the experimental configuration in Section 6.3, Table 7 presents a systematic comparison of the storage overhead incurred by the proposed protocol versus baseline protocols. The focus is on the secret credentials that user devices, gateways/servers, and smart sensing units must store after initialization and registration to support subsequent AKA operations. To illustrate scalability, Table 7 also presents the storage cost of each entity as a function of the number of smart sensing devices, denoted by N. For resource-constrained smart sensing devices, the proposed protocol requires only 384 bits of local storage-substantially less than the 1280 bits of Wazid et al. [61] and the 1984 bits of Sutrala et al. [63], and equal to the requirements of Srinivas et al. [64] and Yang et al. [62]. Given the enhanced security and functionality delivered by our protocol (see Table 8), this minimal storage footprint is justified. From a system-wide perspective, the total storage burden introduced by the proposed protocol grows linearly as bits-markedly lower than Wazid et al.’s [61] bits, Yang et al.’s [62] bits, and Sutrala et al.’s [63] bits. While slightly higher than the schemes of Hammad et al. [60] and Srinivas et al. [64], the proposed protocol offers stronger security guarantees and richer functionality (refer to Table 8), making this trade-off reasonable and acceptable.

Table 7.
Comparison of storage overheads (bits).

Table 8.
Security and functionality features comparison.
Table 8.
Security and functionality features comparison.
| Feature | [60] | [61] | [62] | [63] | [64] | Our |
|---|---|---|---|---|---|---|
| ✓ | × | × | × | × | ✓ | |
| ✓ | ✓ | × | ✓ | ✓ | ✓ | |
| ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| × | ✓ | ✓ | ✓ | ✓ | ✓ | |
| ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| × | × | ✓ | × | × | ✓ | |
| ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
Note: : Smart sensing device capture attack; : Anonymity; : Untraceability; : De-synchronization attack; : Replay attack; : MitM attack;  : Mutual authentication; : Independent session key establishment; : Perfect forward secrecy; : No clock synchronization; : ESL attack; : Stolen smartcard and privileged-insider attacks; and : Impersonation attacks; ✓: indicates feature availability; ×: indicates feature unavailability or inapplicability.
: Mutual authentication; : Independent session key establishment; : Perfect forward secrecy; : No clock synchronization; : ESL attack; : Stolen smartcard and privileged-insider attacks; and : Impersonation attacks; ✓: indicates feature availability; ×: indicates feature unavailability or inapplicability.
 : Mutual authentication; : Independent session key establishment; : Perfect forward secrecy; : No clock synchronization; : ESL attack; : Stolen smartcard and privileged-insider attacks; and : Impersonation attacks; ✓: indicates feature availability; ×: indicates feature unavailability or inapplicability.
: Mutual authentication; : Independent session key establishment; : Perfect forward secrecy; : No clock synchronization; : ESL attack; : Stolen smartcard and privileged-insider attacks; and : Impersonation attacks; ✓: indicates feature availability; ×: indicates feature unavailability or inapplicability.6.5. Security and Functionality Features
Table 8 presents a comparison of the proposed protocol against the benchmark protocols: Hammad et al. [60], Wazid et al. [61], Yang et al. [62], Sutrala et al. [63], and Srinivas et al. [64]. The comparison evaluates thirteen security and functionality features: : Smart sensing device capture attack; : Anonymity; : Untraceability; : De-synchronization attack; : Replay attack; : MitM attack;  : Mutual authentication; : Independent session key establishment; : Perfect forward secrecy; : No clock synchronization; : ESL attack; : Smartcard theft and insider threats; and : Impersonation attacks. In Table 8, a check mark (✓) denotes the presence of a feature, while a cross (×) indicates its absence or inapplicability. The comparison reveals that the proposed protocol is the only one to encompass all the essential and critical security and functionality features. Conversely, the benchmark protocols show shortcomings, either missing certain features or failing to counter specific security threats.
: Mutual authentication; : Independent session key establishment; : Perfect forward secrecy; : No clock synchronization; : ESL attack; : Smartcard theft and insider threats; and : Impersonation attacks. In Table 8, a check mark (✓) denotes the presence of a feature, while a cross (×) indicates its absence or inapplicability. The comparison reveals that the proposed protocol is the only one to encompass all the essential and critical security and functionality features. Conversely, the benchmark protocols show shortcomings, either missing certain features or failing to counter specific security threats.
 : Mutual authentication; : Independent session key establishment; : Perfect forward secrecy; : No clock synchronization; : ESL attack; : Smartcard theft and insider threats; and : Impersonation attacks. In Table 8, a check mark (✓) denotes the presence of a feature, while a cross (×) indicates its absence or inapplicability. The comparison reveals that the proposed protocol is the only one to encompass all the essential and critical security and functionality features. Conversely, the benchmark protocols show shortcomings, either missing certain features or failing to counter specific security threats.
: Mutual authentication; : Independent session key establishment; : Perfect forward secrecy; : No clock synchronization; : ESL attack; : Smartcard theft and insider threats; and : Impersonation attacks. In Table 8, a check mark (✓) denotes the presence of a feature, while a cross (×) indicates its absence or inapplicability. The comparison reveals that the proposed protocol is the only one to encompass all the essential and critical security and functionality features. Conversely, the benchmark protocols show shortcomings, either missing certain features or failing to counter specific security threats.6.6. Critical Discussion
The proposed AKA protocol delivers a balanced solution for real-time IIoT environments by integrating PUFs, fuzzy extractors, and chaotic maps, ensuring strong resistance to attacks and meeting all targeted security and functionality objectives. It maintains moderate computational and communication overheads, making it suitable for resource-constrained devices, with superior runtime performance. Limitations include PUF reliability under environmental variations, computational overhead from fuzzy extractors, and reliance on simulations lacking real-world insights. Trade-offs involve latency, storage overhead, and implementation complexity. Future work targets real-world testbed implementation, IIoT communication stack integration, robust key management, recovery mechanisms, and energy efficiency evaluation under diverse scenarios.
7. Conclusions
To address the threats posed by various known attacks on wireless data communication between users, gateway nodes, and smart sensing devices in Industrial Internet of Things (IIoT) network scenarios, this paper proposes an anonymous and secure authentication and key agreement protocol for IIoT settings. The proposed protocol is based on PUF, cryptographic hash, XOR, and Chaotic Map, providing strong security features while maintaining resource efficiency, making it more suitable for resource-constrained IIoT environments. Furthermore, a comprehensive comparison with existing protocols demonstrates that the proposed protocol significantly reduces computational and communication overhead while offering superior security features, representing a substantial advancement in the field. Future work includes the exploration of post-quantum cryptographic primitives to ensure long-term resistance against quantum-capable adversaries, and the experimental deployment of the proposed protocol in real-world IIoT testbeds to validate its performance under diverse and dynamic environmental conditions.
Author Contributions
Conceptualization, D.Z., X.A., S.T. and A.B.; Methodology, D.Z., X.A., S.T. and A.B.; Software, D.Z.; Validation, D.Z., X.A., S.T., M.W. and M.T.K.; Formal analysis, D.Z., X.A., S.T., A.B. and M.W.; Investigation, D.Z., X.A., S.T., A.B., M.W. and M.T.K.; Resources, X.A. and H.A.; Data curation, M.T.K.; Writing—original draft, D.Z., X.A. and A.B.; Writing—review & editing, S.T., A.B., H.A. and M.W.; Visualization, S.T., A.B., H.A., M.W. and M.T.K.; Supervision, S.T., A.B., H.A. and M.W.; Project administration, A.B. and H.A.; Funding acquisition, H.A. All authors have read and agreed to the published version of the manuscript.
Funding
The authors extend their appreciation to the Deanship of Scientific Research at King Khalid University for funding this work through Large Groups Project under grant number RGP.2/637/46.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are available from the authors upon reasonable request.
Conflicts of Interest
The authors declared that no conflict of interest exist.
References
- Kebande, V.R.; Awad, A.I. Industrial Internet of Things ecosystems security and digital forensics: Achievements, open challenges, and future directions. ACM Comput. Surv. 2024, 56, 131. [Google Scholar] [CrossRef]
- Awaisi, K.S.; Ye, Q.; Sampalli, S. A survey of industrial AIoT: Opportunities, challenges, and directions. IEEE Access 2024, 12, 96946–96996. [Google Scholar] [CrossRef]
- Nallakaruppan, M.K.; Dhanaraj, R.K.; Shukla, S.; Subbaraj, K.; Fuladi, S.; Selvarajan, S.; Alkhayyat, A.; Alturki, N. Reliable secured consumer IIoT framework with multi-layer attack interpretation and prevention. IEEE Trans. Consum. Electron. 2025, 71, 5036–5043. [Google Scholar] [CrossRef]
- Sah, D.K.; Vahabi, M.; Fotouhi, H. A comprehensive review on 5G IIoT test-beds. IEEE Trans. Consum. Electron. 2025, 71, 4139–4163. [Google Scholar] [CrossRef]
- Khan, W.Z.; Aalsalem, M.Y.; Khan, M.K. Communal acts of IoT consumers: A potential threat to security and privacy. IEEE Trans. Consum. Electron. 2019, 65, 64–72. [Google Scholar] [CrossRef]
- Sun, G.; Xu, Z.; Yu, H.; Chang, V. Dynamic network function provisioning to enable network in box for industrial applications. IEEE Trans. Ind. Inform. 2021, 17, 7155–7164. [Google Scholar] [CrossRef]
- Yu, F.; Wang, X.; Guo, R.; Ying, Z.; Cai, S.; Jin, J. Dynamical analysis, hardware implementation, and image encryption application of new 4D discrete hyperchaotic maps based on parallel and cascade memristors. Integration 2025, 104, 102475. [Google Scholar] [CrossRef]
- Sun, G.; Song, L.; Yu, H.; Chang, V.; Du, X.; Guizani, M. V2V routing in a VANET based on the autoregressive integrated moving average model. IEEE Trans. Veh. Technol. 2019, 68, 908–922. [Google Scholar] [CrossRef]
- Zhang, M.; Wei, E.; Berry, R.; Huang, J. Age-dependent differential privacy. IEEE Trans. Inf. Theory 2024, 70, 1300–1319. [Google Scholar] [CrossRef]
- Luo, T.; Zhou, Y.; He, Z.; Jiang, G.; Xu, H.; Qi, S.; Zhang, Y. StegMamba: Distortion-free immune-cover for multi-image steganography with state space model. IEEE Trans. Circuits Syst. Video Technol. 2025, 35, 4576–4591. [Google Scholar] [CrossRef]
- Han, F.; Yang, P.; Du, H.; Li, X.-Y. Accuth++: Accelerometer-based anti-spoofing voice authentication on wrist-worn wearables. IEEE Trans. Mob. Comput. 2024, 23, 5571–5588. [Google Scholar] [CrossRef]
- Hu, J.; Jiang, H.; Liu, D.; Xiao, Z.; Dustdar, S.; Liu, J. A wireless self-service system for library using commodity RFID devices. IEEE Internet Things J. 2024, 11, 4998–5010. [Google Scholar] [CrossRef]
- Xu, G.; Lei, L.; Mao, Y.; Li, Z.; Chen, X.; Zhang, K. CBRFL: A framework for committee-based Byzantine-resilient federated learning. J. Netw. Comput. Appl. 2025, 238, 104165. [Google Scholar] [CrossRef]
- Yanambaka, V.P.; Mohanty, S.P.; Kougianos, E.; Puthal, D. PMsec: Physical unclonable function-based robust and lightweight authentication in the Internet of medical things. IEEE Trans. Consum. Electron. 2019, 65, 388–397. [Google Scholar] [CrossRef]
- Ai, X.; Badshah, A.; Tu, S.; Waqas, M.; Ahmad, I. An improved ultra-lightweight anonymous authenticated key agreement protocol for wearable devices. IEEE Trans. Mob. Comput. 2025, 24, 4543–4557. [Google Scholar] [CrossRef]
- Zhou, Z.; Shojafar, M.; Alazab, M.; Abawajy, J.; Li, F. AFED-EF: An energy-efficient VM allocation algorithm for IoT applications in a cloud data center. IEEE Trans. Green Commun. Netw. 2021, 5, 658–669. [Google Scholar] [CrossRef]
- Chen, Y.; Liang, X.; Zhou, H.; Yang, X.; Wu, L.; Lv, G. GENDN: A geospatially enhanced NDN framework for location-related pub/sub services in NTN-enabled IoT. IEEE Internet Things J. 2025, 12, 8381–8393. [Google Scholar] [CrossRef]
- Xu, G.; Xu, S.; Fan, X.; Cao, Y.; Mao, Y.; Xie, Y.; Chen, X. RAT ring: Event-driven publish/subscribe communication protocol for IIoT by report and traceable ring signature. IEEE Trans. Ind. Inform. 2025, 21, 6670–6678. [Google Scholar] [CrossRef]
- Xu, Y.; Liu, Y.; Lei, M.; Gao, M.; Fang, Z.; Jiang, C. Joint pseudo-range and Doppler positioning method with LEO satellites’ signals of opportunity. Satell. Nav. 2025, 6, 10. [Google Scholar] [CrossRef]
- Ding, F.; Liu, Z.; Wang, Y.; Liu, J.; Wei, C.; Nguyen, A.; Wang, N. Intelligent event-triggered lane keeping security control for autonomous vehicle under DoS attacks. IEEE Trans. Fuzzy Syst. 2025, 33, 3595–3608. [Google Scholar] [CrossRef]
- Turkanović, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Tai, W.-L.; Chang, Y.-F.; Li, W.-H. An IoT notion-based authentication and key agreement scheme ensuring user anonymity for heterogeneous ad hoc wireless sensor networks. J. Inf. Secur. Appl. 2017, 34, 133–141. [Google Scholar] [CrossRef]
- Chen, Y.; Yin, F.; Hu, S.; Sun, L.; Li, Y.; Xing, B.; Chen, L.; Guo, B. ECC-based authenticated key agreement protocol for industrial control system. IEEE Internet Things J. 2022, 10, 4688–4697. [Google Scholar] [CrossRef]
- Shuai, M.; Xiong, L.; Wang, C.; Yu, N. A secure authentication scheme with forward secrecy for industrial Internet of Things using Rabin cryptosystem. Comput. Commun. 2020, 160, 215–227. [Google Scholar] [CrossRef]
- Gong, B.; Wu, Y.; Badshah, A.; Waqas, M. Privacy-preserving and traceable certificateless anonymous mutual authentication scheme for IoT. IEEE Trans. Dependable Secur. Comput. 2025, 22, 7508–7520. [Google Scholar] [CrossRef]
- Zeng, D.; Badshah, A.; Tu, S.; Waqas, M.; Han, Z. A security-enhanced ultra-lightweight and anonymous user authentication protocol for telehealthcare information systems. IEEE Trans. Mob. Comput. 2025, 24, 4529–4542. [Google Scholar] [CrossRef]
- Hammad, M.; Badshah, A.; Almeer, M.A.; Waqas, M.; Song, H.H.; Chen, S.; Han, Z. Lightweight and robust key agreement for securing IIoT-driven flexible manufacturing systems. IEEE Internet Things J. 2025, 12, 17197–17209. [Google Scholar] [CrossRef]
- Zhai, Z.; Liu, J.; Liu, X.; Mao, Y.; Zhang, X.; Ma, J.; Jin, C. A lightweight authentication method for Industrial Internet of Things based on blockchain and Chebyshev chaotic maps. Future Internet 2025, 17, 338. [Google Scholar] [CrossRef]
- Aman, M.N.; Basheer, M.H.; Sikdar, B. A lightweight protocol for secure data provenance in the Internet of Things using wireless fingerprints. IEEE Syst. J. 2021, 15, 2948–2958. [Google Scholar] [CrossRef]
- Modarres, A.M.A.; Sarbishaei, G. An improved lightweight two-factor authentication protocol for IoT applications. IEEE Trans. Ind. Inform. 2023, 19, 6588–6598. [Google Scholar] [CrossRef]
- Rafique, F.; Obaidat, M.S.; Mahmood, K.; Ayub, M.F.; Ferzund, J.; Chaudhry, S.A. An efficient and provably secure certificateless protocol for industrial Internet of Things. IEEE Trans. Ind. Inform. 2022, 18, 8039–8046. [Google Scholar] [CrossRef]
- Yi, F.; Zhang, L.; Xu, L.; Yang, S.; Lu, Y.; Zhao, D. WSNEAP: An efficient authentication protocol for IIoT-oriented wireless sensor networks. Sensors 2022, 22, 7413. [Google Scholar] [CrossRef]
- Eldefrawy, M.H.; Ferrari, N.; Gidlund, M. Dynamic user authentication protocol for industrial IoT without timestamping. In Proceedings of the 2019 15th IEEE International Workshop on Factory Communication Systems (WFCS), Sundsvall, Sweden, 27–29 May 2019; pp. 1–7. [Google Scholar]
- Harishma, B.; Patranabis, S.; Chatterjee, U.; Mukhopadhyay, D. POSTER: Authenticated key-exchange protocol for heterogeneous CPS. In Proceedings of the 2018 Asia Conference on Computer and Communications Security, Incheon, Republic of Korea, 4–8 June 2018; pp. 849–851. [Google Scholar]
- Mutlaq, K.A.-A.; Nyangaresi, V.O.; Omar, M.A.; Abduljabbar, Z.A. Symmetric key based scheme for verification token generation in Internet of Things communication environment. In Proceedings of the EAI International Conference on Applied Cryptography in Computer and Communications, Virtual Event, 14–15 May 2022; pp. 46–64. [Google Scholar]
- Chen, Y.; Martínez, J.-F.; Castillejo, P.; López, L. A privacy protection user authentication and key agreement scheme tailored for the Internet of Things environment: PriAuth. Wirel. Commun. Mob. Comput. 2017, 2017, 5290579. [Google Scholar] [CrossRef]
- Patel, C.; Doshi, N. Cryptanalysis of ECC-based key agreement scheme for generic IoT network model. In Proceedings of the 2019 10th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Kanpur, India, 6–8 July 2019; pp. 1–7. [Google Scholar]
- Chen, P.; Song, Y.; Xia, Y. Adaptively diagnosing system faults in microservice architecture: An autonomous predictive model construction framework. Future Gener. Comput. Syst. 2025, 177, 108256. [Google Scholar] [CrossRef]
- Jiang, H.; Ye, L.; Hu, J.; Chen, X.; Chen, S.; Zhang, W.; Yang, K. WarmGait: Thermal array-based gait recognition for privacy-preserving person re-ID. IEEE Trans. Mob. Comput. 2025, 1–14. [Google Scholar] [CrossRef]
- Luo, H.; Li, Q.; Cheng, H.; Li, W.; Sun, W.; Zhao, W.; Liu, Z. A2Tformer: Addressing temporal bias and non-stationarity in transformer-based IoT time series classification. IEEE Internet Things J. 2025, 12, 42198–42213. [Google Scholar] [CrossRef]
- Zhang, K.; Wang, H.; Chen, M.; Chen, X.; Liu, L.; Geng, Q.; Zhou, Y. Leveraging machine learning to proactively identify phishing campaigns before they strike. J. Big Data 2025, 12, 124. [Google Scholar] [CrossRef]
- Xu, G.; Wang, L.; Chen, S.; Zhu, L.; Guizani, M.; Shi, L. MPAEE: A multi-path adaptive energy-efficient routing scheme for low earth orbit-based industrial Internet of Things. IEEE Internet Things J. 2025, 12, 34793–34805. [Google Scholar] [CrossRef]
- Sun, Q.; Jian, X.; Han, C.; Li, Y. An improved opportunistic localization algorithm using LEO signals based on PSODC. IEEE Trans. Instrum. Meas. 2025, 74, 8512110. [Google Scholar] [CrossRef]
- Liu, X.; Zhao, L.; Jin, J. A noise-tolerant fuzzy-type zeroing neural network for robust synchronization of chaotic systems. Concurr. Comput. Pract. Exp. 2024, 36, e8218. [Google Scholar] [CrossRef]
- Shen, X.; Li, L.; Ma, Y.; Xu, S.; Liu, J.; Yang, Z.; Shi, Y. VLCIM: A vision-language cyclic interaction model for industrial defect detection. IEEE Trans. Instrum. Meas. 2025, 74, 2538713. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Guo, X.; Zhang, J.; Meng, X.; Li, Z.; Wen, X.; Girard, P.; Liang, B.; Yan, A. HALTRAV: Design of a high-performance and area-efficient latch with triple-node-upset recovery and algorithm-based verifications. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2024, 44, 2367–2377. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Universally composable notions of key exchange and secure channels. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Amsterdam, The Netherlands, 28 April–2 May 2002; pp. 337–351. [Google Scholar]
- Yang, J.; Liu, Y.; Wang, W.; Wu, H.; Chen, Z.; Ma, X. PATNAS: A path-based training-free neural architecture search. IEEE Trans. Pattern Anal. Mach. Intell. 2024, 47, 1484–1500. [Google Scholar] [CrossRef]
- Zhao, Z.; Li, X.; Luan, B.; Jiang, W.; Gao, W.; Neelakandan, S. Secure Internet of Things using a novel Brooks–Iyengar quantum Byzantine agreement-centered blockchain networking model in smart healthcare. Inf. Sci. 2023, 629, 440–455. [Google Scholar] [CrossRef]
- Herder, C.; Yu, M.-D.; Koushanfar, F.; Devadas, S. Physical unclonable functions and applications: A tutorial. Proc. IEEE 2014, 102, 1126–1141. [Google Scholar] [CrossRef]
- Zhou, Z.; Abawajy, J.; Chowdhury, M.; Hu, Z.; Li, K.; Cheng, H.; Alelaiwi, A.A.; Li, F. Minimizing SLA violation and power consumption in cloud data centers using adaptive energy-aware algorithms. Future Gener. Comput. Syst. 2018, 86, 836–850. [Google Scholar] [CrossRef]
- Delvaux, J.; Gu, D.; Verbauwhede, I.; Hiller, M.; Yu, M.-D. Efficient fuzzy extraction of PUF-induced secrets: Theory and applications. In Cryptographic Hardware and Embedded Systems—CHES 2016; Gierlichs, B., Poschmann, A.Y., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; pp. 412–431. [Google Scholar]
- Lee, T.-F. Efficient three-party authenticated key agreements based on Chebyshev chaotic map-based Diffie–Hellman assumption. Nonlinear Dyn. 2015, 81, 2071–2078. [Google Scholar] [CrossRef]
- Wu, Z.Y.; Ismail, M.; Zhang, J.; Zhang, J. Tidal-like concept drift in RIS-covered buildings: When programmable wireless environments meet human behaviors. IEEE Wireless Commun. 2025, 1–8. [Google Scholar] [CrossRef]
- Zhang, K.; Zheng, B.; Xue, J.; Zhou, Y. Explainable and trust-aware AI-driven network slicing framework for 6G IoT using deep learning. IEEE Internet Things J. 2025. [Google Scholar] [CrossRef]
- Bergamo, P.; D’Arco, P.; De Santis, A.; Kocarev, L. Security of public-key cryptosystems based on Chebyshev polynomials. IEEE Trans. Circuits Syst. I Regul. Pap. 2005, 52, 1382–1393. [Google Scholar] [CrossRef]
- Yoshioka, D. Security of public-key cryptosystems based on Chebyshev polynomials over Z/pkZ. IEEE Trans. Circuits Syst. II Express Briefs 2020, 67, 2204–2208. [Google Scholar]
- Xiao, L.; Zhao, L.; Jin, J. Preset-time convergence fuzzy zeroing neural network for chaotic system synchronization: FPGA validation and secure communication applications. Sensors 2025, 25, 5394. [Google Scholar] [CrossRef]
- Hammad, M.; Badshah, A.; Abbas, G.; Alasmary, H.; Waqas, M.; Khan, W.A. A provable secure and efficient authentication framework for smart manufacturing industry. IEEE Access 2023, 11, 67626–67639. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Alazab, M. Designing authenticated key management scheme in 6G-enabled network in a box deployed for industrial applications. IEEE Trans. Ind. Inform. 2021, 17, 7174–7184. [Google Scholar] [CrossRef]
- Yang, Z.; He, J.; Tian, Y.; Zhou, J. Faster authenticated key agreement with perfect forward secrecy for industrial Internet-of-Things. IEEE Trans. Ind. Inform. 2020, 16, 6584–6596. [Google Scholar] [CrossRef]
- Sutrala, A.K.; Obaidat, M.S.; Saha, S.; Das, A.K.; Alazab, M.; Park, Y. Authenticated key agreement scheme with user anonymity and untraceability for 5G-enabled softwarized industrial cyber-physical systems. IEEE Trans. Intell. Transp. Syst. 2022, 23, 2316–2330. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Wazid, M.; Kumar, N. Anonymous lightweight chaotic map-based authenticated key agreement protocol for industrial Internet of Things. IEEE Trans. Dependable Secur. Comput. 2020, 17, 1133–1146. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).