Highlights
What are the main findings?
- Highlight the double-encryption issue of the conventional MQTT broker-based, end-to-end (E2E) models.
- Highlight the heavy broker-decrypt-re-encrypt overhead undermining the MQTT efficiency strengths.
- Explore new MQTT broker-based E2E models, which aim to preserve high efficiency and security goals.
What is the implication of the main finding?
- Both the group key-based approach and the client–broker channel, Integrity-only approach are promising solutions for securing MQTT systems while preserving the efficiency strength.
- The proposed approaches are fully compatible with MQTT 5.0 and have been implemented using MQTT 5.0 APIs.
Abstract
MQTT is a publisher–broker–subscriber architecture in which a broker forwards the messages to interested subscribers, which facilitates the broker’s capacity to peek at the message contents; therefore, both academia and industry design and develop end-to-end (E2E) channels to protect the privacy against a curious broker which honestly follows the protocols but would peek at the contents for its benefits. However, we notice that the double-encryption issue of the conventional MQTT broker-based E2E models and the heavy broker-decrypt-re-encrypt overhead undermine MQTT efficiency strengths. In this study, we highlight the weaknesses, propose several solutions, implement the schemes, and experiment with them in the simulated scenarios. Security analysis and formal security proofs are verified to ensure the security goals. The analysis and the evaluations on the implementations confirm both the group key-based approach and the client–broker-channel, integrity-only approach could improve the efficiency performance while preserving security strengths.
1. Introduction
MQTT (message queuing telemetry transport) [1,2], as one of the most popular Internet of Things (IoT) communication protocols, has been widely deployed around the globe. However, its publisher–broker–subscriber architecture allows the broker to peek at the message content, even if a TLS authentication is activated between clients and a broker.
To protect the message privacy from curious brokers, several works like [3,4,5,6,7,8] propose their solutions for the end-to-end (E2E) channel building between a publisher and a subscriber; in such settings, a publisher and a subscriber would build an E2E channel, in addition to the client–broker secure channel. Figure 1 shows the MQTT E2E architecture. Conventional MQTT standards (MQTT 5.0 [2], MQTT 3.1 [1] and its previous versions) encourage users to activate SSL/TLS on the brokers or design their customized secure channel between clients and a broker to protect the security between clients and the broker.
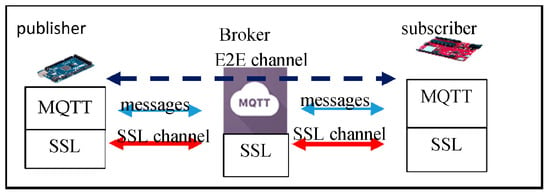
Figure 1.
The MQTT-SSL model.
However, we find that this MQTT E2E model would result in a double-encryption-overhead issue. In Figure 1, assume publisher publishes a message to a group of n subscribers (say , for ); first encrypts using the E2E key between and for ) to get , and then re-encrypts each encryption again using the SSL key between and to get ; upon receiving the double-encrypted message , the broker first decrypts it to get , and then re-encrypts it using the SSL key between it and to get ; finally, decrypts twice to get the plaintext.
In this conventional MQTT E2E model, we would like to point out two critical weaknesses; one is the double-encryption issue from and B, and from B to ; the other is the broker-decrypt-re-encrypt overhead, of which the broker B, for each MQTT message, decrypts once and re-encrypts again n times, which is a huge overhead. The two critical weaknesses undermine the efficiency strengths of conventional MQTT E2E systems.
In this study, we point out the weaknesses, propose our solutions, evaluate the performance, and prove the security. The rest of this work is organized as follows. Section 2 discusses the related work. Section 3 introduces our efficiency-enhanced MQTT E2E solutions. Section 4 presents our implementation and evaluates the performance. Section 5 analyzes the security and gives a formal security proof. Section 6 states our conclusions and future work.
2. Related Work
Most of the existing MQTT security publications, like [4,5,7,8], tackle the security of MQTT 3.1 and its earlier versions, and only a few, like [3,6], focus on MQTT 5.0. MQTT 5.0 was released in 2019; its main enhancements include enhanced authentication, user property, client–server interaction, user data, etc., to provide more flexibility in designing customized functions and security supports; therefore, it is much more convenient to design and implement customized functions like authentication, key agreement, publisher–subscriber interaction, etc.
Due to MQTT’s publisher–broker–subscriber architecture, a broker acts as a message forwarder between a publisher and its subscribers, which facilitates the broker’s capacity to peek at the message contents. This would be a serious privacy threat, especially when the clients and the broker do not belong to the same authority. To address this weakness, some works [3,4,5,6,7,8] focus on building a secure E2E channel between publishers and subscribers: the messages from the publisher and its subscribers are encrypted using the E2E channel keys.
Chien [3] proposes designing two client-initiated E2E scenarios: one is for the publisher-initiated E2E scenario and the other is the subscriber-initiated E2E scenario. Mektoubi et al.’s E2E solution [7] adopts the topic certificate, of which the corresponding public key is used to encrypt the messages for the topic while the private key is used to decrypt the encryptions. This approach demands a huge overhead from the clients, and the private key distribution raises a challenge.
In the MQTLS scheme [4], a publisher initiates its E2E key distribution using the publisher’s–subscriber’s ephemeral Diffie–Hellman session keys, and OpenSSL-based extensions are used to facilitate the E2E topic key distribution. However, their extension implementations do not consider MQTT 5.0 compatibility. Efficiency improvement using a broker-based group key is not applied. Neither the double-encryption issue nor the decrypt-re-encrypt overhead is considered. Their E2E channel establishment is not publisher–subscriber decoupling, either.
SEEMQTT’s E2E scheme [5], based on the secret sharing mechanism, allows a publisher to delegate its decryption authority to a pool of key stores. Those designated subscribers contact the pool of key stores, get verification, and then recover the decryption key. This solution lets the publisher delegate its authority to verify the subscribers to a pool of key stores, which results in lots of extra overhead.
Chein et al. [6] design, implement, and evaluate the performance of their MQTT E2E scheme for MQTT 5.0; The evaluation confirms that building an E2E channel between a publisher and a subscriber only adds non-significant connection latency.
Wang and Chien [8], based on the MQTT E2E channel, improve the security and the efficiency of the MQTT over the air (OTA) updating mechanism. However, the double-encryption issue is not addressed.
In addition to the above schemes, there are some schemes related to our broker-based E2E schemes. Eugster et al. [9] focus on discussing the decoupling properties in terms of space, time, and synchronization for those publish/subscribe interaction schemes. Regarding the decoupling feature of MQTT, we would like to categorize it into two situations. One is the publisher–subscriber E2E-connection decoupling which means that, during the publisher–subscriber E2E channel building process, the two entities need not interact with each other. The other one is message-forwarding decoupling, which means that, when a publisher/subscriber publishes/receives a message, they do not need to be aware or interact with each other. In these senses, the models we discuss and propose in this study satisfy the message-forwarding decoupling but not the publisher–subscriber E2E-connection decoupling.
Now we briefly introduce the potentials/supports of facilitating some coupling designs in MQTT 5.0. MQTT 5.0 supports the enhanced authentication framework (EAF) and User properties, where user properties are user-defined meta shared among publishers, brokers, and subscribers. EAF contains CONNECT, DISCONNECT, and AUTH API; in these APIs, the new fields auth_id, auth_data, and User properties facilitate the customized security designs and the conventional client–server interactions between a publisher and a subscriber in the connection phase. By subscribing to the designated topics and properly setting the fields—the response topic and the correlation data—a publisher and a subscriber can perform conventional client–server interaction between them. The above introduction implies that MQTT 5.0 facilitates the publisher–subscriber E2E-connection coupling and publisher–subscriber message coupling. Interested readers are referred to [2,10,11,12,13] for detailed introductions and to [6] for the implementation examples. That is, MQTT 5.0 facilitates the support of both decoupling designs and coupling designs; the choice depends on the application requirements.
Buccafurri et al. [14] systematically examine the applicability of existent mechanisms for ensuring the MQTT E2E flow integrity; they discuss the MQTT E2E flow integrity in terms of formally-defined properties like Completeness, Correctness, and Liveness. Their MQTT-I scheme combines the message-digest hashing, multiple-topic Merkle hash tree, and round-based signature/verification to amortize the extra signature/verification cost. However, we notice two critical differences between MQTT-I E2E solutions and the MQTT broker-based E2E schemes we focus on here. First, we are concerned with E2E privacy and data integrity protection against a curious broker, but MQTT-I concerns the flow integrity (the integrity property is different from others), but not the privacy. Many works like [3,4,5,6,7,8] have highlighted the importance of privacy protection against a curious broker. Second, in their simulations and evaluation [14], they do not consider the performance impact of increasing the number of clients on the performance of publisher/broker/subscriber; however, many existing studies have confirmed that the increasing number of clients really has great impact on the overall performance, especially when the customized broker has some extra overheads.
MQTT-SN (MQTT for sensor networks) [15] is a more lightweight variant of MQTT; it adjusts MQTT’s features to fit those scenarios and environments where the communications are more restricted. Park and Nam [16] concern the E2E security (privacy and integrity) against a curious broker for MQTT-SN; they employ entity certificates, topic certificates, and public/private keys to facilitate the establishment of the session keys between entities. Their ideas are applicable to the MQTT systems, but they do not concern the double encryption issue and the decrypt then re-encrypt issue.
Singh et al. [17] augment existing MQTT protocols with key/ciphertext policy-attribute-based encryption (KP/CP-ABE) [18,19] for securing MQTT applications in sensor network environments. This attribute-based, encryption-based (ABE-based) approach can be applied and extended to secure both client–broker channels and publisher–subscriber channels; however, this approach has the key weaknesses of poor performance and scalability, especially when the number of attributes increases. This weakness should be seriously tackled as MQTT is targeted for IoT systems where the number of clients and the number of topics are scalable.
In a short summary, even though there are several MQTT E2E schemes proposed, implemented, and evaluated, we notice that they do not focus on the double-encryption issue and the impact of the broker-decrypt-re-encrypt overhead, and do not systematically explore potential approaches to tackle these challenges while preserving the desirable security properties. Therefore, we will discuss and tackle these challenges.
While MQTT remains one of the most widely adopted messaging protocols in IoT due to its lightweight publish/subscribe model and TCP-based reliability, several alternative protocols have been developed to address specific deployment scenarios. AMQP (advanced message queuing protocol) [20] offers robust messaging features such as queuing, routing, and transaction support, making it more suitable for enterprise environments rather than resource-constrained devices. Meanwhile, CoAP over DTLS [21] provides a RESTful communication model optimized for constrained nodes and networks, using UDP and DTLS to achieve lightweight, secure, request/response messaging. The data distribution service (DDS) [22] for real-time systems is an object management group (OMG) machine-to-machine middleware standard that aims to enable dependable, high-performance, interoperable, real-time, scalable data exchanges using a publish–subscribe pattern.
Some other studies are related in a broader sense. Ciphertext matching like [23] could be applied to a general sub/subsystem to ensure the event privacy and the subscription privacy against a curious broker; even though MQTT E2E study also concern the privacy of message contents against a curious broker, both the subscribed topics and the topic of a published message are explicitly sent to the broker in MQTT systems.
Brokerless extensions eliminate the central broker by enabling direct peer-to-peer message routing. One approach is multicast-based MQTT over software-defined networks like Park et al.’s DM-MQTT [24]; DM-MQTT reduces data transfer delays by establishing bidirectional SDN (software defined networking) multicast trees between the publishers and the subscribers by bypassing the centralized broker. Shahriet et al. [25], based on SDN, further apply MQTT 5.0’s User properties to specify the real-time requirements to instantiate corresponding network reservations to achieve the desirable real-time transmissions. ZeroMQ [26] is a lightweight, brokerless messaging library offering direct pub/sub, request/reply, and pipeline patterns with low latency. Our approach aims at improving efficiency by adjusting the MQTT broker-based E2E models; while the brokerless approach adopts transmission reservation facilities (like SDN) to improve the transmission latency. These two approaches are complementary to each other; the idea from either approach can be combined with the other to improve efficiency further.
NIST SP 800-207 “Zero Trust Architecture (ZTA)” [27] enforces a “never trust, always verify” approach to minimize the risk of unauthorized access and lateral movement within networks by continuously validating identities, devices, and contextual signals before granting access to resources. The key functions/components include policy decision point (PDP), policy enforcement point (PEP), resource access policies, and identity management. It provides a complete guide for security system designs and implementations.
The above works are all related to IoT protocols, and this paper focuses on MQTT broker-based E2E systems’ security and efficiency. Therefore, we will only discuss MQTT and MQTT-SN in the rest of this paper. We systematically examine the efficiency of the conventional MQTT broker-based E2E model’s security properties and efficiencies, and explore potential approaches to enhance the efficiencies while preserving the desirable security properties.
There exist some popular mechanisms which formally analyze the security properties of security protocols. The first category of these mechanisms is based on some mathematical reduction proof in the specified formal models. The second category includes those mechanisms [28,29,30,31,32,33,34,35,36] that provide software tools that formally execute logic reasoning on formal specifications of security protocols. Both Burrows–Abadi–Needham (BAN) logic [28] and the AVISPA [29,30] are two popular formal tools of the second category. The BAN logic is a set of rules for defining and analyzing information exchange protocols, and has been successfully applied to protocol conformance testing; however, there are many reports like [32,33] on the limitations, weaknesses, and failures of the BAN logic. On the contrary, the AVISPA is designed to simulate and verify cryptographic protocols formally; it provides the SPAN protocol simulation [34] to examine the interaction flows formally; it contains various verification tools (like OFMC [35], ATSE) to validate the security goals formally. The high-level protocol specification language (HLPSL) [36] is the formal language used to formally define the protocol role, environment, and security goals in AVISPA. Even though the AVISPA and its tools still have some limitations (for example, the limited support of some algebra calculations), they provide formal specifications of the protocols, of the simulated environments, and of the security goals, which can better capture the security semantics. We, therefore, adopt the AVISPA to verify our schemes.
3. Efficiency-Enhanced MQTT E2E Architecture (Model)
Before proposing our efficiency-enhanced MQTT E2E architecture (E-MQTT-E2EA), we review the key features of the conventional MQTT broker-based E2E mechanisms, and then introduce the performance metrics for comparisons.
3.1. Threat Model and Assumptions
Here, we define the threat model and the assumptions for the rest of this paper. In our model, the broker is honest but curious, and the clients might be compromised. An honest but curious broker would honestly execute the protocol, but would peek at the content for their own benefit. A compromised client could impersonate other entities, and replay/modify/intercept/forge the messages.
We assume the system has implemented some kind of intrusion detection system to detect and identify a compromised client. We also assume that some proper policy enforcement functions and access controls have been implemented on the broker such that granting the publish/subscribe/connect requests would follow the policies defined for that client.
3.2. Performance Challenges of Conventional MQTT Broker-Based E2E Mechanisms
Here, we define the conventional MQTT broker-based E2E schemes, be those MQTT secure-channel building schemes which simultaneously achieve the two functions: (1) the client–broker channel provides mutual authentication and privacy protection (for example, TLS aims at providing secure client–broker channels); (2) a publisher builds E2E channels with its subscribers, and the channel provides mutual authentication and privacy protection. Here, the E2E channel building is coupled in the sense that the publisher and the subscriber interact with each other via a broker. Regarding these conventional MQTT broker-based E2E schemes, they inherit the following issues. To simplify the notations, we do not differentiate the terms MQTT broker-based E2E and MQTT E2E for the rest of this paper, when the semantics are clear.
- The double-encryption issue. When a publisher publishes a message, it encrypts the message first using the E2E channel key and then re-encrypts the ciphertext again using the publisher–broker channel key. The same issue happens at the broker-subscriber channel.
- The broker-decrypt-re-encrypt overhead. In the conventional MQTT architectures, a broker needs to decrypt a ciphertext from a publisher using the publisher–broker-channel key, and then re-encrypts the plaintext using its broker–subscriber channel key. If there are many subscribers for the message, it demands lots of re-encryption overhead. This overhead might seem unavoidable as the broker needs to protect the privacy on the broker–subscriber channel. But, it could be improved as the group of subscribers corresponding to the same topic could use the same group key, and, if the MQTT payload in the E2E channel has been encrypted, the re-encryption could be eliminated.
Regarding the performance of an MQTT E2E mechanism, we are concerned about both the security support and efficiency.
- The E2E channel security, which includes the authentication of the participating entities and the privacy/integrity of the message.
- The privacy, authentication, and integrity of the data between a client and a broker.
- The publisher–broker channel overhead.
- The broker–subscriber channel overhead.
- The broker overhead.
3.3. High-Level Designs of MQTT E2E Mechanisms
Before discussing our ideas, we introduce the notation in Table 1.

Table 1.
The Notation.
Since we are concerned with the performance impact of the MQTT E2E architecture, we explore several ideas for improving the efficiency and evaluate their performance. Figure 2 shows the four channel protection models in the MQTT E2E architecture. All four MQTT E2E models support both authentication and integrity protection on the publisher–subscriber E2E channel, as all MQTT E2E models aim at providing authenticity and integrity for the message transmissions in the E2E channel. But, they differ in the client–broker channel security designs and the broker–subscriber channel key selection.
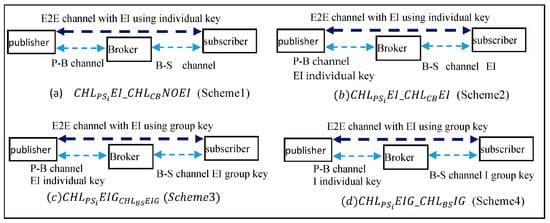
Figure 2.
The four MQTT E2E models, where E denotes Encryption, and I denotes Integrity.
Because this study focuses on comparing the efficiency improvement by simplifying the client–broker channels and using a group key in some models, we, therefore, simplify the group key being chosen and distributed by the sender (a publisher in the E2E channel for the same topic or the broker in the broker-subscriber channels for the same topic) to simplify the presentation and the prototype implementations.
In such a setting, when a publisher P publishes a message for a topic (say , P chooses a group key and distributes the key during the E2E channel establishment phase. Because our E2E channel establishment phase does not decouple the publisher and the subscriber (it corresponds to the subscriber connect block in Figure 3), the publisher has the opportunity to distribute the encrypted group key (encrypted by the publisher–subscriber Diffie–Hellman session key). Likewise, the broker can choose and distribute the broker–subscriber group key in the subscriber connect phase.
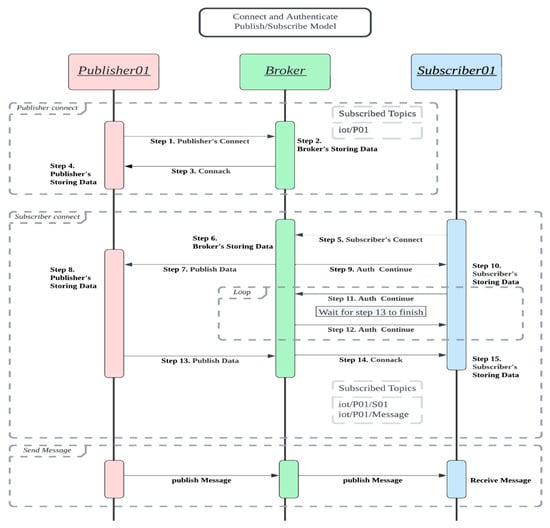
Figure 3.
The protocol flows of the four models.
Regarding the dynamic membership of publisher/subscriber and the dynamic connect/disconnect, one solution is described here. The publisher could periodically choose a new group key and distribute it during the subscriber E2E connect phase. This applies to the broker’s choosing and distributing its broker–subscriber group key. When the broker detects and identifies a compromised subscriber (or publisher), it rejects its connection.
Another approach to determine and update the group key is borrowing Park-Nam’s ideas [16]. In Park-Nam’s work [16], two kinds of certificates (entity certificates and topic certificates) and the corresponding private keys are distributed to the corresponding entities. The CDHP-based group keys could be derived using the corresponding public/private keys and some necessary data to differentiate each session. In such a setting, the group key update is by renewing/distributing the corresponding topic certificate and the public/private key to the authorized entities. Interested readers are referred to Park-Nam’s work [16].
Scheme 1-: (1) the E2E channel with encryption and integrity check using , where the key is set as the individual E2E session key between P and ; (2) the channel without encryption and integrity; (3) the channel without encryption and integrity. This corresponds to the MQTT E2E model without enabling a secure client-broker channel.
Scheme 2-: (1) the E2E channel with encryption and integrity check using , where the key is set as the individual E2E session key between P and ; (2) the channel with encryption and integrity using the key , where the key is the individual session key; (3) the channel with encryption and integrity using the key , where the key is the individual session key. This corresponds to the conventional MQTT E2E model with a secure client–broker channel (like MQTT E2E with TLS client-broker channel).
Scheme 3-: (1) the E2E channel with encryption and integrity check using , where the key is set as the group key chosen and distributed by P; (2) the channel with encryption and integrity using the key , where the key is the individual session key; (3) the channel with encryption and integrity using the key , where the key is the group key chosen and distributed by B. This new model tries to improve the conventional MQTT E2E model performance using the mechanism: it replaces the individual broker-subscriber session key with the corresponding group key, such that the broker can encrypt once for all the subscribers for the same topic.
Scheme 4-: (1) the E2E channel with encryption and integrity check using , where the key is set as the group key chosen and distributed by P; (2) the channel with the integrity only using the key , where the key is the individual session key; (3) the channel with the integrity only using the key , where the key is the group key chosen and distributed by B. This model tries to improve the previous model’s performance further using the two mechanisms: (a) it eliminates the double-encryption issue on the client–broker channels by providing only authentication and integrity checks on the client–broker channel; the rationale for this design is that, as the publisher has encrypted the message using the E2E key, it only needs to ensure the authentication and integrity on the publisher–broker channel; (b) a similar rationale applied on the broker–subscriber channel. Here, we note that all the sensitive data in the E2E channel should be encrypted using the E2E key, and only non-sensitive data fields can be assigned to MQTT plaintext fields. This ensures that the receiver can still authenticate the source and the integrity of the received messages.
The rationale behind the above scheme notations could be explained as follows. refers to that (1) the channel with encryption and integrity using individual session keys—EI, and (2) the channel between a Client (C) and its Broker (B) without (NO) encryption integrity—NOEI. refers to that (1) the channel with encryption and integrity using Group key—EIG, and (2) the channel between a broker (B) with its subscribers (S) with integrity using Group key (G)—IG. Other notations could be inferred similarly.
Scheme 1 () and Scheme 2 act as basic models, and we will compare the performance of other models with that of the basic models.
3.4. Detailed Designs of MQTT E2E Mechanisms
The four models in the previous section have a similar structure,, but with different combinations of the security function supports and of the key selections on the channel and on the channels; we, therefore, will not describe the details of every schemes; instead, we only detail two of them, and then list the differences for the others.
All four models share the same protocol flow in Figure 3.
Publisher–broker connection block. The first block, consisting of Steps 1~3, is referred to as the publisher connection block. In Step 1, a publisher randomly chooses a temporary key pair (public key, private key), sends its CONNECT request including its certificate, the temporary public key as a random challenge, and its signature on the temporary public key and on the current timestamp. The broker checks the certificate and the signature in Step 2. The broker returns its certificate and its signature on Step 3, and the publisher validates the message in Step 4. The publisher’s signature denoted as P.Sig = . Likewise, the broker’s Connack response consists of its certificate, its temporary public key , its timestamp , and its signature B.Sig = . After validating each other’s certificate, timestamp, and signatures, they share the Diffie–Hellman publisher–broker-channel key . This channel key would be used in authentication, in integrity check, or both in the four models.
Subscriber–broker connection E2E building block. The second block, consisting of Steps 5~15 is referred to as the subscriber–broker connection E2E building block. In this block, a subscriber initiates its connection (and its E2E connection request) in Step 5 with its broker which processes the request and forwards the E2E request to the publisher (Step 7); Upon receiving the E2E request in Step 7, the publisher publishes its response in Step 13, and the broker processes the message and sends the Connack response to the subscriber in Step 14. If both the responses from the publisher and the broker confirm the connection request from the subscriber, the subscriber would establish one key with its broker and another key with its publisher. The differences of the four schemes (Scheme 1~4) in this block exist in the key establishments; In Scheme 1, is not set and is set as . In Scheme 2, is set as and is set as . In Scheme 3, is set as and is set as . In Scheme 4, is set as and is set as .
Publisher–Subscriber E2E message block. This block represents the E2E messaging phase after the E2E channel is built. In Scheme 1, both the channel and the channel provide no privacy and no integrity protection while the channel is encrypted and integrity protected using . In Scheme 2, the channel is encrypted and integrity-protected using , the channel is encrypted and integrity-protected using , and the channel is encrypted and integrity protected using . In Scheme 3, the channel is encrypted and integrity-protected using , the channel is encrypted and integrity protected using , and the channel is encrypted and integrity protected using . In Scheme 4, the channel is integrity-protected using , the channel is integrity-protected using , and the channel is encrypted and integrity protected using .
3.4.1. The Details of Scheme 1
In this section, we detail every step of Scheme 1.
- Block 1.
- Step 1. The publisher selects a random number , computes , and sends its CONNECT request, which contains (as a challenge), timestamp , its signature on and , and its long-term certificate.Step 2. Upon receiving the connection request, broker B stores the data in its database.Step 3. B selects a random number , computes , and sends back its connect response (Connack), which contains (as a challenge), timestamp , its signature on , , and its long-term certificate. B also computes the key . This session key would be used as the encryption key and the hash key in the publisher–broker channel.Step 4. P receives and verifies the response, and computes the key .
- Block 2.
- Step 5. The subscriber selects two random numbers and , computes and , and sends its connection request (Connect) to its broker. This connect packet contains , , timestamp , its signature on the previous data, its certificate, and its intention for building an E2E channel.Step 6. B receives the request, verifies the signature, and stores , and the certificate.Step 7. B forwards the rest of the connect request to the publisher.Step 8. Upon receiving the E2E connect request, P verifies the signatures and stores and the certificate.Step 9. Broker B sends its “Auth Continue” back to the subscriber. This “Auth Continue” aims to notify the subscriber that the previous connection request is still processing and please keep waiting.Step 10~12. Broker B and the subscriber S keep on the notification and waiting state.Step 13. P randomly selects , computes , and calculates the E2E key . It sends back its response, which contains its timestamp, , its signature, and its certificate.Step 14. B checks the content and computes . It then forwards P’s response back to the subscriber.Step 15. S receives the response, verifies the signature, and computes two keys: and .
- Block 3
- In Scheme 1, only the E2E channel enables encryption and integrity, but the channel and the channel do not enable encryption/integrity. So, when the publisher P publisher a message Mtxt, it encrypts Mtxt as Ctxt = (Mtxt), and generates the corresponding (Ctxt). It specifies the topic, Ctxt, , etc., as an MQTT message. The broker checks the topic and forwards it to the subscriber, who uses the key to decrypt and verify the content.Scheme 1 provides the authentication, encryption, and integrity check on the E2E channel , and provides mutual authentication between clients (publisher/subscriber) and the broker. But it does not provide message authentication and an integrity check for the message between clients and the broker.
3.4.2. The Details of Scheme 2
The steps 1~15 of Scheme 2 are the same as those of Scheme 1, but they differ in the steps of Block 3. When the publisher P publishes a message Mtxt, it encrypts Mtxt as Ctxt = (Mtxt), and generates the corresponding (Ctxt). This process is for securing the content on the E2E channel . P further encrypts Ctxt as (Ctxt), appends it with the corresponding , and finally specifies the topic, , and in an MQTT message to the broker.
The broker decrypts to get Ctxt, and verifies , using . If they succeed, B further re-encrypts Ctxt as (Ctxt), appends a new , and then forwards the MQTT message to the subscriber.
The subscriber S first decrypts and verifies the message, using the key . It gets the content Ctxt and , and then further decrypts it and verifies it, using the key .
Scheme 2 provides mutual authentication, message authentication, and message integrity check on both the E2E channel and the client-broker channels. The encryption on the client–broker channels is based on the individual session key.
3.4.3. The Details of Scheme 3
Steps 1~15 of Scheme 3 are similar to those of Scheme 1, but they differ in the selections of the channel keys and the steps of Block 3. The E2E channel uses , where the key is set as the group key distributed by P; the channel uses the key , where is the group key distributed by B.
When the publisher P publishes a message Mtxt, it encrypts Mtxt as Ctxt = (Mtxt), and generates the corresponding (Ctxt). This process is for securing the content on the E2E channel . P further encrypts Ctxt as (Ctxt), appends it with the corresponding , and finally specifies the topic, , and in an MQTT message to the broker.
The broker decrypts and verifies , using . If they succeed, B further re-encrypts Ctxt as (Ctxt), appends a new , and then forwards the MQTT message to the subscriber.
The subscriber S first decrypts and verifies the message, using the key . It gets the content Ctxt and , and then further decrypts it and verifies it, using the key .
Scheme 3 provides mutual authentication, message authentication, and message integrity check on both the E2E channel and the client–broker channels. The operations on the client–broker channels are based on the group key. Note that both the E2E channel and the channel use the corresponding group keys: this can reduce some overhead, as the publisher can do the encryption/integrity protection once for all subscribers of the same message; it applies to the broker’s operations too.
3.4.4. The Details of Scheme 4
Steps 1~15 of Scheme 4 are similar to those of Scheme 1, but they differ in the selections of the channel keys and the steps of Block 3. The E2E channel uses , where the key is set as the group key chosen and distributed by P; the channel uses the key , where is the group key chosen and distributed by B.
When the publisher P publishes a message Mtxt, it encrypts Mtxt as Ctxt = (Mtxt), and generates the corresponding (Ctxt). This process is for securing the content on the E2E channel . Please note that P does not further encrypt Ctxt but only appends it with the corresponding , and finally specifies the topic, , and in an MQTT message to the broker.
The broker verifies , using . If they succeed, B does not re-encrypt Ctxt but appends a new , and then forwards the MQTT message to the subscriber.
The subscriber S first verifies the message, using the key . It gets the content Ctxt and , and then further decrypts it and verifies it, using the key .
Scheme 4 provides mutual authentication, message authentication, and message integrity check on both the E2E channel; but it provides only message authentication and integrity checks on the client–broker channels. The operations on the client–broker channels are based on the group key. Note that both the E2E channel and the channel use the corresponding group keys: this can reduce some overhead, as the publisher can perform the integrity protection once for all subscribers of the same message; it applies to the broker’s operations too. Please note that Scheme 4, compared to Scheme 3, further eliminates the double-encryption issue on the client–broker channels.
4. Performance Analysis, Implementations, and Evaluations
To evaluate the performance of the schemes, we first analyze the performance in Section 4.1, and then introduce our implementations and simulation evaluations in Section 4.2.
4.1. The Performance Analysis
Table 2 sorts out the performances in terms of the security supports, the computational performance, and the latency performance. Assume there are n subscribers for one MQTT message from a publisher. Let denote the computational cost for one MQTT message encryption; denotes the computational cost for one MQTT message HAMC calculation.

Table 2.
Functional performances of the four schemes.
From Table 2, we can see that Scheme 2 demands the most expensive computational cost, due to the usage of individual keys. Scheme 4, compared to Scheme 3, slightly improves the computational overhead while keeping the necessary security supports. Even though Scheme 1 is the most efficient one in the above four schemes, Scheme 1 does not provide message authentication on the client-broker channels; therefore, Scheme 4 is the one that can achieve efficiency performance while providing the desirable security.
4.2. The Implementations, Simulations, and Evaluations
We implement the four schemes, using Mosquitto [37] APIs, OpenSSL [38], json-c library [39] and VMware [40]. Mosquitto is a popular open-source MQTT package, and the newest versions support MQTT 5.0. Mosquitto’s plugins facilitate developers to implement customized programs. The clients from the Paho [41] package have been adopted.
We first design and deploy two scenarios in Figure 4. In Figure 4a (Scenario 1), there is one NoteBook (NB) with two VMs: VM1 is for the broker, and VM2 is for one publisher with 10/20/50/100/200 subscribers. In Figure 4b (Scenario 2), there is one NB with three VMs: VM1 is for the broker, and VM2 is for one publisher with 50 subscribers, VM 3 is for 50 subscribers. The hardware and software used are summarized in Table 3.
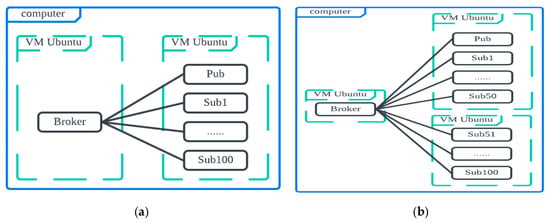
Figure 4.
Simulation scenarios (a) 1 NB with 2 VMs, (b) 1 NB with 3 VMs.

Table 3.
The hardware and the software used in the simulations.
The experiments are conducted as follows. First, the broker starts up, the publisher connects, and then the subscriber connects. Second, the publisher publishes 1000 MQTT messages, and all the subscribers receive the messages. Here, we are concerned about two metrics: one is the connection latencies, and the others are the latencies between a MQTT message travels from the publisher to a subscriber.
- Connection latency
Regarding the connection latencies, we design two scenarios: one is only five subscribers (Table 4), and the other is for a varying number of subscribers.

Table 4.
Summary of 50 connection latencies of publishers and five subscribers (ms).
Table 5 shows the connection latencies for a varying number of subscribers. Figure 5 shows the connection latencies for a varying number of subscribers. From the figure, we can see that the proposed E2E connection is quite stable, and the latency for subscribers is slightly larger than that for the publisher, as it takes more steps for the subscriber. We also notice that, even when there are 200 subscribers, the subscribers’ connection latency is still quite small (less than 300 ms). It confirms that the proposed E2E connection is quite efficient.

Table 5.
The latencies of pub/sub connections with a varying number of subscribers.
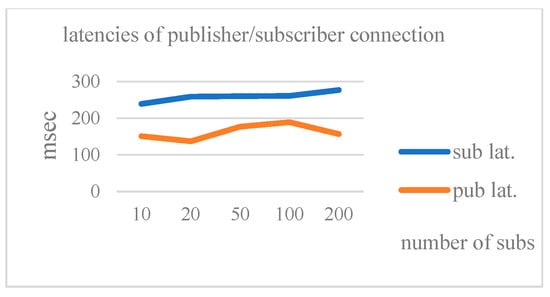
Figure 5.
The latencies of pub/sub connections with varying number of subscribers.
- Publishing–receiving latency
The publishing–receiving latencies in Scenario 1 are summarized in Table 6. Figure 6 shows the latencies of the four schemes for different subscribers in Scenario 1. Here, we can see that, as the number of subscribers increases, the latencies increase in the four schemes. Comparing the latencies of the four schemes, Scheme 1 < Scheme 4 < Scheme 3 < Scheme 2, which confirms our analysis that more overhead on the client–broker channel would have an impact on the latency performance. Obviously, Scheme 2 demands the most cost (shown in Table 2) and demands the longest latency (shown in Figure 6).

Table 6.
The publishing–receiving latencies in Scenario 1.
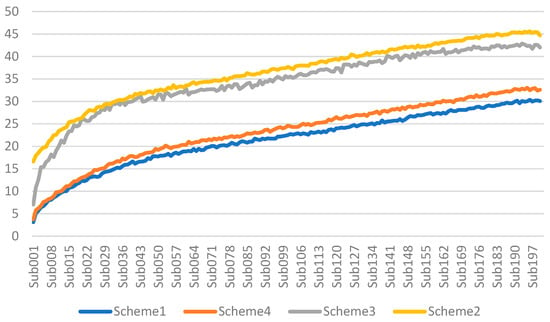
Figure 6.
The latencies of the four schemes for different subscribers in Scenario 1.
Next, we focus on comparing Scheme 1, Scheme 3, and Scheme 4 for Scenario 2. Here, the results (Table 7) again confirm that the latency order is Scheme 1 < Scheme 3 < Scheme 3 < Scheme 2. In these scenarios, we find that the average latency of Scheme 4 is the smallest, and both Scheme 3 and 4 can improve the latency performance while preserving the desirable security. That is, both the group-key-based approach can improve the efficiency and the client–broker channel integrity-only approach can further reduce the average latency.

Table 7.
Publish–receive latencies in Scenario 2.
Next, we focus on Scenario 3 (Figure 7), where subscribers are deployed in two different sub-nets (domains) to evaluate the inter-networking impact on the latencies.
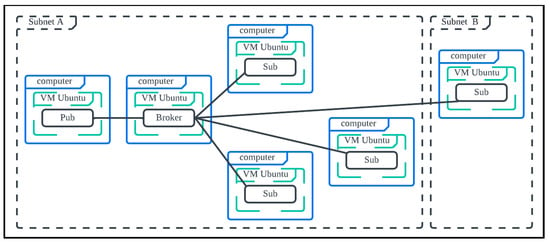
Figure 7.
Simulation scenario: six PCs each hosting one VM (total six VMs).
The results (Table 8) indicate that both Scheme 3 and Scheme 4 could improve the latency performance, compared to Scheme 2 (the conventional MQTT E2E model); that is, the group-key-based approach apparently reduces the latency. In both the 100/200-subscriber simulations, the latency of Scheme 3 > the latency of Scheme 4. This indicates that the client–broker channel integrity-only approach further improves the latency.

Table 8.
Publish–receive latencies in Scenario 3.
Figure 8 shows the memory/CPU utilization in broker VM, the publisher-100subscriber VM2, and the 100subscriber VM3. We can see that the CPU/memory utilization for all three VMs increases after the subscribers become active: it means that the broker, the publisher, and the subscribers need to process more computations and communications.
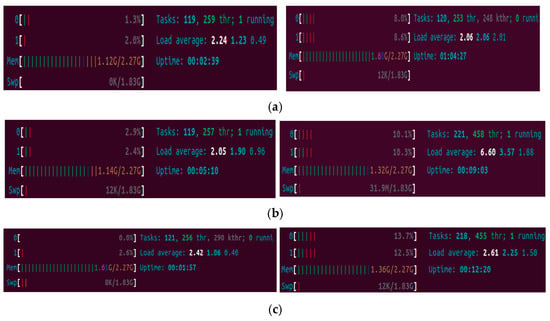
Figure 8.
(a) The CPU/memory utilization of the broker VM1 before/after subscriber subscribers; (b) the CPU/memory utilization of the publisher-100subscriber VM2 before/after subscriber active subscribers; (c) the CPU/memory utilization of the100subscriber VM3 before/after subscriber/active subscribers.
Summarizing the above analysis and the simulations, we confirm that the proposed Scheme 4 () can significantly improve the latency while preserving the desirable security.
4.3. Comparison
Here, we make a comparison among some studies which are related in a broader sense; some of them are MQTT related and some are just general pub/sub systems. Table 9 briefly summarizes the qualitative features of these schemes.

Table 9.
Qualitative comparison among pub/sub systems and MQTT mechanisms.
Here, we have some observations from the table. Regarding the MQTT broker-based E2E models, our work confirms that both the group key-based approach and the client–broker channel integrity-only approach can improve the efficiency while preserving the desirable security properties. When we extend the scope to include brokerless MQTT and SDN communication support, they both have the potential to improve the efficiency, too; these approaches can complement each other and combining the ideas from these approaches might further improve the overall performance; however, further investigations are required.
5. Security Analysis and Proof
This section will examine the security of the proposed scheme. Here, we will focus on the security analysis of Scheme 4 in Section 5.1 and the security proof in Section 5.2. Here, we focus on Scheme 4 as it satisfies the security goals and greatly improves the latency performance (as shown in Section 4).
5.1. Security Analysis
Here, we analyze each security goal of Scheme 4.
- The mutual authentication of the publisher–broker channel . In the channel building phase (Block 1), the publisher and the broker exchange their certificates, their ephemeral public keys ,, timestamps, and their digital signatures on the transmitted data, which enable them to authenticate the participating entities. During the authentication, they establish their Diffie–Hellman key .The privacy and integrity of the MQTT payload in thechannel. After the channel building, the MQTT payload would be encrypted using the Diffie–Hellman key in Schemes 2,3, which ensures the privacy of the MQTT payload in the channel in Schemess 2,3. The MQTT payload would be integrity protected in Schemes 2,3,4.The mutual authentication of the broker–subscriber channel . In the channel building phase (Block 2), the broker and the subscriber exchange their certificates, their ephemeral public keys ,, timestamps, and their digital signatures on the transmitted data, which enable them to authenticate the participating entities. During the authentication, they establish their Diffie-Hellman key , and the broker’s group key is securely distributed in Schemes 3,4.The privacy and integrity of the MQTT payload in thechannel. After the channel building, the MQTT payload would be encrypted using the Diffie–Hellman key in Scheme 2 and using the group key in Scheme 3, which ensures the privacy of the MQTT payload in the in Schemes 2,3. The payload would be integrity protected in Schemes 2,3,4.The mutual authentication of the publisher and the subscriber in an E2E channel. In the E2E channel building phase, the publisher and the subscriber exchange their certificates, their ephemeral public keys ,, timestamps, and their digital signatures on the transmitted data, which enable them to authenticate the participating entities. After that, they can establish their E2E keys ( in Schemes 1,2,3,4, and securely distributed and protected using the session key in Schemes 3,4).The privacy and integrity of the MQTT payload in thechannel. After the channel building, the MQTT payload in the channel would be encrypted using the Diffie–Hellman key in Schemes 1,2 and using the group key in Schemes 3,4, which ensures the privacy of the MQTT payload in the in Schemes 1,2,3,4.
Summarizing all the above security analysis, we can note that Scheme 4 achieves the security functions: (1) mutual authentication in the channels; (2) authenticity and integrity of the MQTT messages in the channels; (3) privacy of the MQTT payload in the channel.
5.2. Security Proofs
We specify the protocol using the HLPSL language, prove the security goals using the AVISPA, and evaluate the security performance.
- Security goals. The security goals of the proposed scheme include: (1) the mutual authentication between a client (publisher or subscriber) and the broker, (2) and the privacy of the shared keys of the channels (), (3) the mutual authentication between a publisher and a subscriber and the privacy of the E2E key.
We formally specify the protocol and its goals using the HLPSL language. The SPAN protocol simulation validates its correctness. We use both the OMFC verifier and the ATSE verifier to prove the security goals. In HLPSL, each entity is modeled as a role which interacts with other roles.
- The HLPSL modeling of MQTT E2E scheme
In the conventional client–server architecture, both server and client can be viewed as independent finite-state machines which interact with their communicating party through messages, which is easy and intuitive to model each entity as an independent role using HLPSL. However, it is a challenge to model a single role for a broker of MQTT, because MQTT is based on the publisher–broker–subscriber architecture, where the broker independently authenticates each client, but it also handles the associations of all clients which involve the same topic. To solve this challenge, we proposed the two-broker-HLPSL model where a broker is separated into two roles, but the two roles (broker1 and broker2) securely share their information through symmetric-key-based encryptions (Figure 9). In this setting, each broker can independently handle the interactions with its client, and the two brokers can share the topic-bounded messages. There are a total of four roles—subscriber, broker1, broker2, publisher—in our MQTT HLPSL modeling. We note that, due to the limited support of exponentiation in the verifiers, we pass symmetric keys as inputs to assign the calculated CDHP keys in the specifications.

Figure 9.
The 2-broker-HLPSL model.
- The SPAN-OMFC simulation/verification
Figure 10 shows the message sequences of the SPAN protocol simulation of our MQTT-E2E HLPSL specification.
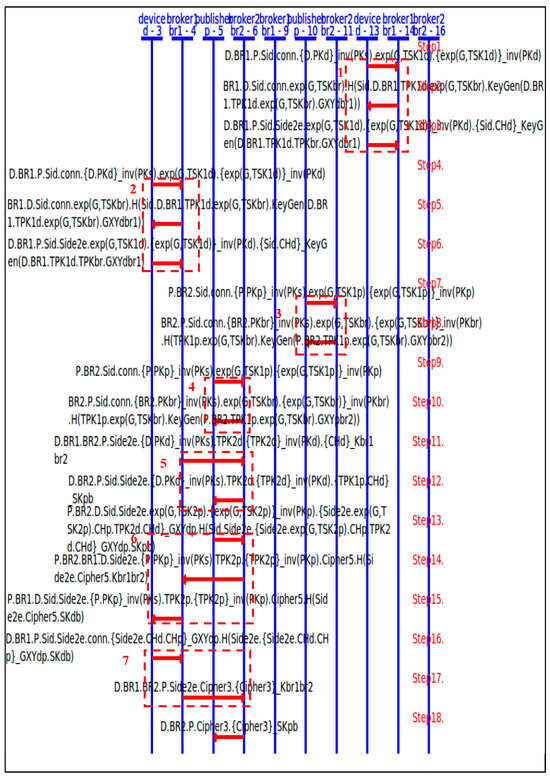
Figure 10.
The SPAN simulation of our MQTT-E2E HLPSL specification.
The first two dashline blocks (Blocks 1, 2) show two pairs of device-broker1 performing the authentications, in which a device refers to a client. Blocks 3 and 4 show two pairs of publisher-broker2 performing the authentications. Block 5 shows broker1 and broker 2 forwarding the E2E request to the publisher, which is followed by block 6 in which the publisher sends back its E2E response with the temporary DH public key to the subscriber. Block 7 shows the subscriber sending the confirmation back to the publisher. The SPAN simulation confirms that the roles successfully execute the specified protocol flow.
The security goals of the specification include the mutual authentication for device–broker1 and for publisher–broker2, the publisher–subscriber authentication, and the privacy of the session keys for device–broker1/publisher–broker2/the end2end session key. We use both the OMFC verifier and the ATSE verifier to validate the security goals. Figure 11 shows both the OMFC verifier and the ATSE verifier verification results—SAFE.
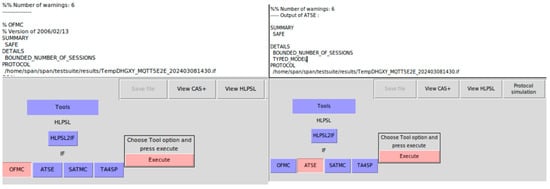
Figure 11.
Both OFMC and ATSE confirm SAFE of our HLPSL specification.
6. Conclusions
In this paper, we have discussed the performance weaknesses of the conventional MQTT broker-based E2E model—the double-encryption issue on the client–broker channel and the heavy broker-decrypt-re-encrypt burden issue. These two issues downgrade the MQTT efficiency advantage. To tackle the challenges and to improve the efficiency of the conventional MQTT broker-based E2E model, we propose two approaches- the group-key-based approach and the client-broker-channel-integrity-only approach. To verify the efficiency performance, we have implemented the schemes and experimented with them in three scenarios. The results confirm that the two approaches could improve the efficiency while preserving the desirable security properties. The security analysis ensures Scheme 4 meets the security requirements, and the formal AVISPA toolsets formally confirm the security goals of the MQTT-E2E HLPSL specification. Some interesting future studies include the integration of the approaches we propose here and ideas like brokerless MQTT or SDN to improve the overall performance further.
Author Contributions
Conceptualization, H.-Y.C.; methodology, H.-Y.C. and A.-T.S.; software, A.-T.S.; validation, H.-Y.C., A.-T.S. and Y.-M.H.; formal analysis, H.-Y.C.; investigation, H.-Y.C. and A.-T.S.; re-sources, H.-Y.C.; data curation, A.-T.S.; writing—H.-Y.C. and A.-T.S.; writing—review and editing, H.-Y.C.; visu-alization, A.-T.S.; supervision, H.-Y.C.; project administration, H.-Y.C.; funding acquisition, H.-Y.C. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the grant number MOST 111-2221-E-260-009-MY3.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The raw data supporting the conclusions of this article will be made available by the authors on request.
Conflicts of Interest
The authors declare no conflict of interest.
References
- ISO/IEC 20922:2016; Information Technology--Message Queuing Telemetry Transport (MQTT) v31.1. ISO: Geneva, Switzerland, 2016. Available online: https://www.iso.org/standard/69466.html (accessed on 25 January 2024).
- OASIS. MQTT Version 5.0. 7 March 2019. Available online: https://docs.oasis-open.org/mqtt/mqtt/v5.0/mqtt-v5.0.html (accessed on 1 March 2024).
- Chien, H.Y. Design of End-to-End Security for MQTT 5. In Proceedings of the 4th International Conference on Science of Cyber Security-SciSec 2022, Matsue City, Japan, 10–12 August 2022. [Google Scholar]
- Lee, H.; Lim, J.; Kwon, T. MQTLS: Toward Secure MQTT Communication with an Untrusted Broker. In Proceedings of the 2019 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Republic of Korea, 16–19 October 2019; pp. 53–58. [Google Scholar]
- Hamad, M.; Finkenzeller, A.; Liu, H.; Lauinger, J.; Prevelakis, V.; Steinhorst, S. SEEMQTT: Secure End-to-End MQTT-Based Communication for Mobile IoT Systems Using Secret Sharing and Trust Delegation. IEEE Internet Things J. 2022, 10, 3384–3406. [Google Scholar] [CrossRef]
- Chien, H.-Y.; Shih, A.-T.; Huang, Y.-M. Design, Implementation, and Evaluation of MQTT5.0-Based End-to-End Security. J. Internet Technol. 2025. accept and to be published. [Google Scholar]
- Mektoubi, A.; Lalaoui, H.; Belhadaoui, H.; Rifi, M.; Zakari, A. New approach for securing communication over MQTT protocol A comparison between RSA and Elliptic Curve. In Proceedings of the 2016 Third International Conference on Systems of Collaboration (SysCo), Casablanca, Morocco, 28–29 November 2016; pp. 1–6. [Google Scholar]
- Wang, N.Z.; Chien, H.Y. Design and Implementation of MQTT-based Over The Air Updating Against Curious Brokers. IEEE Internet Things J. 2023, 11, 10768–10777. [Google Scholar] [CrossRef]
- Eugster, P.T.; Felber, P.A.; Guerraoui, R.; Kermarrec, A.-M. The many faces of publish/subscribe. ACM Comput. Surv. CSUR 2003, 35, 114–131. [Google Scholar] [CrossRef]
- Steve. MQTT v 5.0 New Features Overview Steve Guide. Available online: http://www.steves-internet-guide.com/mqttv5 (accessed on 31 July 2025).
- Steve. Examining MQTTv5 User Properties Steve guide to MQTT. Available online: http://www.steves-internet-guide.com/examining-mqttv5-user-properties (accessed on 31 July 2025).
- HiveMQ. User Properties-MQTT 5 Essentials Part 6. Available online: https://www.hivemq.com/blog/mqtt5-essentials-part6-user-properties (accessed on 31 July 2025).
- Steve. Understanding And Using MQTT v5 Request Response Steve Guide. Available online: http://www.steves-internet-guide.com/mqttv5-request-response (accessed on 31 July 2025).
- Buccafurri, F.; Angelis, V.D.; Lazzaro, S. MQTT-I: Achieving End-to-End Data Flow Integrity in MQTT. IEEE Trans. Dependable Secur. Comput. 2024, 21, 4717–4734. [Google Scholar] [CrossRef]
- Stanford-Clark, A.; Truong, H.L. MQTT for sensor networks (MQTT-SN) protocol specification version 1.2.IBM. Int. Bus. Mach. (IBM) Corp. Version 2013, 1, 1–28. [Google Scholar]
- Park, C.-S.; Nam, H.-M. Security Architecture and Protocols for Secure MQTT-SN. IEEE Access 2020, 8, 226422–226436. [Google Scholar] [CrossRef]
- Singh, M.; Rajan, M.; Shivraj, V.; Balamuralidhar, P. Secure MQTT for internet of things (iot). In Proceedings of the 2015 Fifth International Conference on Communication Systems and Network Technologies, Gwalior, India, 4–6 April 2015; IEEE: Piscataway, NJ, USA; pp. 746–751. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based Encryption for Fine-grained Access Control of Encrypted Data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Ser. CCS ’06, Alexandria, VA, USA, 30 October–3 November 2006; pp. 89–98. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-Policy Attribute-Based Encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy, Ser. SP ’07, Washington, DC, USA, 20–23 May 2007; pp. 321–334. [Google Scholar]
- OASIS Advanced Message Queuing Protocol (AMQP) Version 1.0. OASIS Standard. October 2012. Available online: https://docs.oasis-open.org/amqp/core/v1.0/amqp-core-overview-v1.0.html (accessed on 31 July 2025).
- Tschofenig, H.; Hartke, K.; Bormann, C. DTLS Profile for CoAP, RFC 9147, IETF. April 2022. Available online: https://datatracker.ietf.org/doc/rfc9147/ (accessed on 31 July 2025).
- Object Management Group. Data Distribution Service (DDS), Version 1.4. Available online: https://www.omg.org/spec/DDS/1.4 (accessed on 5 December 2024).
- Pei, J.; Shi, Y.; Feng, Q.; Shi, R.; Lan, L.; Yu, S.; Shi, J.; Ma, Z. An efficient confidentiality protection solution for pub/sub system. Cybersecurity 2023, 6, 34. [Google Scholar] [CrossRef]
- Pei, J.; Shi, Y.; Feng, Q.; Shi, R.; Lan, L.; Yu, S.; Shi, J.; Ma, Z. DM-MQTT: An Efficient MQTT Based on SDN Multicast for Massive IoT Communications. Sensors 2018, 18, 3071. [Google Scholar]
- Shahri, E.; Pedreiras, P.; Almeida, L. Extending MQTT with Real-Time Communication Services Based on SDN. Sensors 2022, 22, 3162. [Google Scholar] [CrossRef] [PubMed]
- IRMOS TechBlog. Data from IoT to Cloud–A Modern Approach. Available online: https://www.irmo.de/2024/01/12/data-from-iot-to-cloud-a-modern-approach/?utm_source=chatgpt.com (accessed on 20 July 2025).
- Rose, S.; Borchert, O.; Mitchell, S.; Connelly, S. Zero Trust Architecture (NIST Special Publication 800-207). Natl. Inst. Stand. Technol. 2020. [Google Scholar] [CrossRef]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. In Proceedings of the 12th ACM Symposium on Operating Systems Principles, Litchfield Park, AZ, USA, 1–13 November 1989. [Google Scholar]
- Armando, A.; Basin, D.; Cuellar, J.; Rusinowitch, M.; Viganò, L. Avispa–A Tool for Automated Validation of Internet Security Protocols. Available online: https://www.ercim.eu/publication/Ercim_News/enw64/armando.html (accessed on 1 May 2024).
- Armando, A.; Basin, D.; Boichut, Y.; Chevalier, Y.; Compagna, L.; Cuellar, J.; Drielsma, P.; Drielsma, P.H.; Héam, P.-C.; Kouchnarenko, O.; et al. The AVISPA Tool for the automated validation of internet security protocols and applications. In Proceedings of the 17th International Conference on Computer Aided Verification, CAV’2005, LNCS3576, Edinburgh, Scotland, 6–10 July 2005; Etessami, K., Rajamani, S., Eds.; Springer: Edinburgh, UK, 2005; pp. 281–285. [Google Scholar]
- Gligor, V.; Kailar, R.; Stubblebine, S.; Gong, L. Logics for cryptographic protocols—Virtues and limitations. In Proceedings of the IEEE 1991 Computer Security Foundations Workshop, Franconia, NH, USA, 18–20 June 1991; pp. 219–226. [Google Scholar]
- Boyd, C.; Mao, W. On a Limitation of BAN Logic. Presented at the Eurocrypt’93, Lofthus, Norway, 24–26 May 1993. [Google Scholar]
- van Oorschot, P.C. An alternate explanation of two BAN-logic ‘failures’. In Proceedings of the Eurocrypt’93, Lofthus, Norway, 24–26 May 1993; Springer LNCS: Berlin/Heidelberg, Germany, 1994; Volume 765, pp. 443–447. [Google Scholar]
- SPAN: A Security Protocol ANimator for AVISPA. Available online: http://people.irisa.fr/Thomas.Genet/span (accessed on 15 May 2024).
- Basin, D.; Mödersheim, S.; Vigano, L. OFMC: A Symbolic Model-Checker for Security Protocols. Int. J. Inf. Secur. 2005, 4, 181–208. [Google Scholar] [CrossRef]
- Von Oheimb, D. Specification language hlpsl developed in the eu project Avispa. In Proceedings of the APPSEM 2005 Workshop, Frauenchiemsee, Germany, 12–15 September 2005. [Google Scholar]
- Eclipse. Mosquitto: Eclipse Mosquitto-An Open Source MQTT Broker. Available online: https://github.com/eclipse-mosquitto/mosquitto (accessed on 11 February 2025).
- OpenSSL. Available online: https://www.openssl.org/ (accessed on 1 March 2025).
- GitHub, GitHub-Json-c/Json-c. Available online: https://github.com/json-c/json-c (accessed on 1 March 2025).
- VMware. Available online: https://www.vmware.com/ (accessed on 18 August 2024).
- Eclipse, An Eclipse Paho C Client Library for MQTT for Windows, Linux and MacOS. Available online: https://github.com/eclipse/paho.mqtt.c (accessed on 1 March 2025).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).