Abstract
Although the copyright protection schemes supported by blockchain have significantly changed traditional copyright data management, there are still some data security challenges that cannot be ignored, especially the secure access and controllable management of copyright data. Quantum computing attacks also pose a threat to its security. Targeting these issues, we design and propose a blockchain copyright protection scheme based on attribute-based encryption (ABE). In this scheme, the security advantages of blockchain technology are utilized to ensure the authenticity and integrity of copyright data. Based on lattice cryptography and the decision ring learning with errors (R-LWE) problem, a new ABE algorithm that supports searchable ciphertext and policy updates is designed. Then, we introduce it into the blockchain copyright protection scheme, which enables secure access to copyright data and fine-grained control. In addition, the lattice cryptography can strengthen this scheme against quantum attacks. Through security analysis, our scheme can prove to be secure against adaptive chosen keyword attacks, selective chosen plaintext attacks, and adaptive chosen policy attacks in the random oracle model. More importantly, the comparison analysis and experimental results show that our proposed approach has lower computation costs and storage costs. Therefore, our scheme has better security and performance in copyright protection.
1. Introduction
Traditional digital copyright protection faces multiple challenges, with frequent piracy and infringement. In the digital era, the reproduction and dissemination of works become extremely easy, leading to the prosperity of the piracy market, causing huge economic losses to copyright owners, and it is still very difficult to trace and maintain copyright on the Internet. At the same time, the vulnerabilities and risks of the centralized platform cannot be ignored. The centralized copyright protection platform is vulnerable to hacker attacks, resulting in copyright information being tampered with or disclosed [1]. In view of the many problems existing in copyright protection, blockchain technology, as an emerging technical means, is widely used in the field of digital copyright protection. Blockchain technology provides a new solution for digital copyright protection through the characteristics of decentralization, tamper proof, and transparency [2]. First, blockchain technology can ensure the uniqueness and tamper resistance of digital content. By storing copyright information on distributed ledgers and using encryption algorithms for verification, the ownership and integrity of works can be effectively protected [3]. Secondly, blockchain can establish smart contracts to manage and protect copyright. Smart contracts can automate the implementation of copyright use rules and trading conditions, reducing the risk of copyright disputes. In addition, blockchain technology can also realize the transparency and traceability of copyright information, providing a fairer and more reliable environment for copyright transactions [4]. In 2019, Zhang et al. proposed a decentralized digital rights management and transaction system architecture based on blockchain technology [5], which is built in a way that consumes fewer resources and throughput.
Although blockchain has shown great potential in digital copyright protection, there are also some new data security challenges, especially data privacy protection [6]. Consensus and storage of copyright data in the blockchain public ledger while ensuring sensitive privacy is not compromised and resisting quantum computing attack is an urgent issue that needs to be addressed [7,8]. Attribute-based encryption (ABE) is an extension of identity-based encryption and is applied in areas such as the Internet of Things and cloud computing [9]. It has encryption advantages and can achieve user privacy and security management in access control. More specifically, in the ABE scheme, the encryptor formulates access policies based on the user’s characteristic information. The user determines whether they can decrypt the ciphertext based on their own characteristics, and the user’s characteristic information is defined as an attribute. Wang et al. proposed a special ABE scheme with revocation support and flexible access structure on the lattice by using a binary tree [10]. Meanwhile, public-key encryption with keyword search (PEKS) enables users to search target encrypted data by keywords, which increases data privacy [11]. In 2019, Liu et al. proposed a KS-ABE scheme to enhance the security of ciphertext search in cloud storage. Meanwhile, this scheme can resist quantum attacks under the LWE assumption [12]. In 2020, Behnia et al. proposed two PEKS schemes using the NTRU lattice and the LWE lattice and implemented these schemes on the Amazon Web Services cloud infrastructure [13]. In 2021, Zuo et al. proposed a blockchain-based ciphertext-policy attribute-based encryption (CP-ABE) scheme for cloud data secure sharing without relying on any trusted third parties [14]. Then, Zhang et al. proposed a new lattice-based ABE algorithm, which is used as an access control method for blockchain data to protect its security [15].
In practical applications, CP-ABE is more suitable for scenarios of distributed storage and update policy, as it allows data owners to define authorized attribute sets as access control policies embedded in ciphertext [16]. Each user can obtain a key corresponding to their attribute set, and the condition for successful decryption is that the attribute set meets the access policy. Therefore, CP-ABE is often combined with blockchain technology to achieve data security [17]. Moreover, the policy updates of decision-makers on user attributes are constantly changing, so policy updates are particularly important in the ABE scheme’s practical application. This approach can ensure the privacy and security of blockchain-based copyright data and update user access policies to ensure data security [18]. Therefore, in this study, we design a blockchain copyright protection scheme based on CP-ABE. In our scheme, the security advantages of blockchain technology are utilized to ensure the authenticity and integrity of copyright data. Based on lattice cryptography and the decision ring learning with errors (R-LWE) problem, we propose a new CP-ABE algorithm that supports searchable ciphertext and policy updates. Then, we introduce it into the blockchain copyright protection scheme. This scheme enables secure access to copyright data and fine-grained control. The security of the proposed scheme can be reduced to the problem and significantly improve users’ privacy and system data security in blockchain-enabled systems and applications.
Then, the main contributions of this paper are summarized as follows:
- We propose a lattice-based CP-ABE scheme to improve anti-quantum security for blockchain copyright protection. The lattice assumption can make our scheme more secure against quantum attacks.
- We construct a new blockchain copyright protection scheme based on the CP-ABE scheme with a policy update, which enables secure access to copyright data and fine-grained control. We provide detailed descriptions of the copyright protection processes. The proposed scheme can significantly protect the copyright and system security.
- We prove our scheme is secure against adaptive chosen keyword attacks, selective chosen plaintext attacks, and adaptive chosen policy attacks in the random oracle model. Furthermore, we compare the proposed scheme with similar literature that shows that it has lower computation costs and storage costs.
The rest of the paper is organized as follows. In Section 2, some definitions and lemmas of the lattice theories are presented. In Section 3, we propose a CP-ABE scheme with policy update. The security proof is presented in Section 4. In Section 5, we give the performance analysis and efficiency comparison of our scheme with other schemes. In Section 6, a blockchain copyright protection scheme based on CP-ABE is designed. The conclusions are provided in Section 7.
2. Preliminaries
Some definitions and lemmas of the lattice theories are presented in this section, which are in relation to our scheme.
denote the set of all reals and the set of positive integers, respectively. Let be the m-dimensional Euclidean vector space with its usual topology. and denote the lattice; the orthogonal lattice corresponding to is represented by , vector in the space , and its Euclidean norm .
Definition 1.
(Lattice) Given n-linearly independent vectors, lattice L generated by them is the set of vectors.
is known as the basis of the lattice L. The same lattice can be represented by different lattice bases. Given a prime number q, a matrix defines:
Definition 2.
(Lattice SIS problem) Given an integer q, a matrix , and a real constant , find a nonzero vector such that and .
Based on the hardness of the SIS problem, for any polynomial-bounded m, v, and any prime , solving SIS on the average is as hard as approximating the shortest independent vector problem (SIVP) in the worst case.
Ring learning with errors (R-LWE) was proposed by Lyubashevsky [19]. It operates on the ring , where f is an irreducible polynomial, and q is a prime. In most cases, , where n is a power of 2.
Definition 3.
(Decision R-LWE problem) For , , , , , are uniformly and randomly selected, is an error vector that follows a discrete Gaussian distribution . Let , . The decision R-LWE problem is to distinguish between vector group (a,b) and vector group uniformly and randomly selected on .
Definition 4.
(Random oracle model based on decision R-LWE problem) Random oracle O will be sampled with equal probability through two samplers defined as follows:
Pseudo-random oracle O1 outputs pseudo-random sampling , where is a uniform random vector, , the small error term e satisfies discrete Gaussian distribution.
True random oracle O2 outputs uniformly random and mutually independent sample on the domain , which are truly completely random.
The decision R-LWE problem allows adversaries to query the oracle many times and make guesses Or, about the sampler based on the obtained samples. Due to the difficulty of the decision R-LWE problem, the advantages Pr[r = 1] − Pr[r = 2] of any adversary’s guess Or on O are negligible.
Lemma 1.
For a lattice L with dimensional m and rank n, , positive real and for random such that .
Lemma 2.
Let q > 2, a matrix , B is the basis of , and Gaussian parameter . Then, any vector algorithm SamplePre(A, B, y, s) outputs a vector from a distribution that is statistically close to .
Lemma 3.
For any prime and any , there is a probabilistic polynomial-time algorithm that outputs a matrix and a full-rank set . The distribution of A is statistically close to uniform over and the length .
Lemma 4.
Given a matrix and an m-dimensional lattice , input a basis T of the lattice , which has a nonsingular matrix and , then input Gaussian parameter , BasisDel(A, R, T, s) can output a basis B of with overwhelming probability .
3. CP-ABE Scheme with Policy Update
3.1. Formal Definition
Our ABE scheme consists of six probabilistic polynomial time (PPT) algorithms, such as Setup, Index sharing, KeyGen, Encrypt, Decrypt, and Update, as follows:
- (1)
- Setup. The algorithm takes security parameters as input, and the system generates public key PK and master key MK. Among them, the MK is kept by the system.
- (2)
- Index sharing. The algorithm mainly includes Index-generation, Trapdoor algorithm, and Test algorithm, which returns a result that stores data and data indexes.
- (3)
- KeyGen. The algorithm takes PK, MK, and user access control policy as input. The system generates secret key sk for users according to attribute policy T.
- (4)
- Encrypt. The algorithm takes public key PK, attribute policy T, and message M as input and outputs ciphertext C1.
- (5)
- Decrypt. The algorithm takes the public key PK, secret key sk, and ciphertext C as inputs. Only if the access control policy matches the user attribute policy T does the algorithm output plaintext M.
- (6)
- Update. Input the main public key, update the access policy, ciphertext, and random trapdoors used in the encryption algorithms, and output new ciphertext C2.
3.2. Our Proposed Scheme
According to the algorithm definition in Section 3.1, the specific process of our proposed CP-ABE scheme with policy update is as follows.
Setup.
- (1)
- Set user attribute set and the access policy corresponding to its attribute .
- (2)
- Calculate , select parameters . Then, calculate the Gram–Schmidt norm as follows.
If , continue; otherwise, go back to select parameters again.
- (3)
- Calculate by using the extended Euclidean algorithm as follows. , ,where , . If or , go back to select parameters; otherwise, continue.
- (4)
- Run extended Euclidean algorithm to get , and satisfying and . Calculate , , . Thus, reduce F and G as follows:.
- (5)
- Calculate , , , . Output public key and master key .
Index sharing. Index sharing includes the Index-generation algorithm, Trapdoor algorithm, and Test algorithm. During the index-sharing process, the data owner first establishes an index trapdoor to generate a data index and records the data index in the information storage. When data users need to obtain data, they send a request to search the information storage and extract the corresponding data index to obtain the corresponding search results.
- (1)
- Index-generation. N is a power-of-two integer, and the Trapdoor algorithm corresponds to the encrypted keywords and , . Then, randomly select parameters , where , . At last, calculate , and generate index results .
- (2)
- Trapdoor. Run SamplePre algorithm , which satisfies . Output corresponding trapdoor for keywords k.
- (3)
- Test. Calculate ; If , and return d = 1; otherwise, return d = 0.
Keygen. Calculate the hash value of the attribute access control policy . Run SamplePre algorithm , which satisfies . In this way, output the secret key sk = s2.
Encrypt. Randomly select . Calculate , . Then, calculate , and return the ciphertext .
Decrypt. Calculate , .Output the original message .
Update. Define access structure , message , which is expressed as polynomial ; randomly and uniformly sample each attribute , and ; select random numbers and sample , , calculate and ; for each attribute , calculate separately based on the following conditions.
- (1)
- If , sample and calculate ;
- (2)
- If , sample and calculate ;
- (3)
- If , sample , calculate and ;
At last, return the updated ciphertext .
4. Security Analysis
4.1. Correctness
Theorem 1.
The proposed CP-ABE scheme satisfies the correctness of keyword indexing.
Proof.
Given the master key , public key , data index structure , and keyword trapdoor , this scheme is the output of the correct dependency test algorithm . In this calculation process, the parameter are short vectors, so in the interval . And
According to the Formula (5), we have . Thus, it is proven that the keyword index in our ABE scheme satisfies correctness. □
Theorem 2.
The proposed ABE scheme satisfies the correctness of the policy update.
Proof.
If the access policy formulated by the decision-maker is consistent with the user’s attribute set , then there is , . If there is
, so we can have
According to the above Formulas (6) and (7), it is proven that the proposed ABE scheme satisfies the correctness of the policy update. □
4.2. ABE Keyword Index Security
Theorem 3.
The proposed ABE scheme satisfies keyword index security, which satisfies the indistinguishability against adaptive chosen keyword attack (IND-CKA) in the random oracle model.
Proof.
Assume Eve is a polynomial-time malicious adversary, and Charlie is a challenger who wants to solve the hard problem with the query results from Eve. Adversary Eve first specifies the challenge keywords and . Adversary Eve and challenger Charlie conduct the following query response game. □
- (1)
- Setup. Challenger Charlie sets the algorithm to generate a public key and a master key ; that is, Challenger Charlie saves the master key and sends the public key to adversary Eve.
- (2)
- Queries 1. Adversary Eve queries about hash query, index generation query, and trapdoor query with polynomial time. The specific process is as follows.
H1-query. Challenger Charlie initializes two empty lists, L1 and L2, to save the query results. Adversary Eve queries the hash function H1 of the non-target access control policy. Challenger Charlie initializes empty lists and uses them to store the query results of the hash function. If the result is already on the lists L1 and L2, Charlie will return the result and give it to Eve; if the result does not appear on the list, Challenger Charlie will randomly select parameters , where , , and calculate . Challenger Charlie sends the and to adversary Eve and respectively stores the new result and in list L1 and list L2.
Index generation query. Adversary Eve queries the Index-generation algorithm for keyword . Challenger Charlie initializes a new list L3 to store the index-generated query results. When the generated result already exists in L1, Challenger Charlie directly gives the result to adversary Eve. Otherwise, Challenger Charlie first performs a hash H1 algorithm to get and , then randomly selects and calculates , and finally gives the result to adversary Eve and stores in L3.
Trapdoor query. Adversary Eve performs a polynomial time inquiry on the Trapdoor algorithm of the attribute set . Assuming that adversary Eve has already inquired about the keyword, challenger Charlie runs the Trapdoor algorithm and generates using the sampling algorithm . Afterward, Charlie returns to adversary Eve.
- (3)
- Challenge. Adversary Eve randomly selects keywords k1 and k2. Challenger Charlie randomly selects keywords ki (). If i = 1, challenger Charlie executes the Index-generation algorithm and Trapdoor algorithm to regenerate a new index, which is returned to adversary Eve. If i = 2, challenger Charlie returns the searchable ciphertext to adversary Eve.
- (4)
- Queries 2. Adversary Eve repeats the Query 1 operations multiple times, sets the hash function H1-query h times, and queries the Trapdoor algorithms for non-target sets.
- (5)
- Guess. Based on the query results, adversary Eve gives a guess about i. If return 1. Otherwise, return 0. If adversary Eve can give a correct conjecture i with an undeniable probability , challenger Charlie can solve the R-LWE difficulty problem with probability . As the h times of query increases, challenger Charlie needs to solve the R-LWE difficulty problem less frequently. Therefore, given the difficulty of the R-LWE problem, the proposed ABE scheme satisfies the keyword index security.
4.3. ABE Ciphertext Security
Theorem 4.
The proposed ABE scheme satisfies ciphertext security, which satisfies the indistinguishability under selective chosen plaintext attack (IND-sCPA) in the random oracle model.
Proof.
As described in the previous subsection, suppose that Eve is a polynomial-time malicious adversary who can successfully attack the proposed scheme with non-negligible probability , and Charlie is a challenger who wants to solve the SVP problem on the NTRU lattice with the query results from Eve. Adversary Eve and challenger Charlie conduct the following query response game. □
- (1)
- Setup. Adversary Eve assigns the challenge attribute set . Challenger Charlie sets the algorithm to generate a public key and a master key ; that is, Challenger Charlie saves the master key and sends the public key to adversary Eve.
- (2)
- Queries 1. Adversary Eve queries about hash query, private key query, and ciphertext query with polynomial time. The specific process is as follows.
H1-query. Challenger Charlie initializes two empty lists, L3 and L4, to save the query results. Eve queries the hash function H1 of the non-target access control policy . Challenger Charlie initializes empty lists and uses them to store the query results of the hash function. If the result is already on list L3 and list L4, Charlie returns the result and gives it to Eve. Otherwise, Charlie randomly selects parameters , where , , and calculates . Charlie sends the and to Eve and respectively stores the new result and in list L1 and list L2.
Private key query. Eve queries the private key related to access control policies for message mi. Charlie initializes a new list L3 to store the query results. If the attribute satisfies the access control policy , Charlie’s returns continue. Otherwise, Charlie executes the Keygen algorithm and uses to obtain and return it to Eve.
Ciphertext query. Eve performs a polynomial time inquiry on the Trapdoor algorithm of the attribute set . If the attribute satisfies the access control policy , Charlie’s returns continue. Otherwise, according to the encrypt algorithm, Charlie executes to obtain ciphertext and return it to Eve.
- (3)
- Challenge. Adversary Eve randomly selects messages m1 and m2. Charlie randomly selects messages mi (). If i = 1, challenger executes the encrypt algorithm and sends the corresponding ciphertext to adversary. If i = 2, Charlie randomly selects one ciphertext from the ciphertext set to Eve.
- (4)
- Queries 2. Eve repeats the Query 1 operations n times and queries the private key query and ciphertext query for non-target attribute sets .
- (5)
- Guess. Based on these query results, Eve gives a guess about i. If , return 1. Otherwise, return 0. If the Adversary can give a correct guess with an undeniable probability , the challenger can solve the problem with probability . Therefore, under the difficulty of the problem, the proposed ABE scheme satisfies the keyword index security.
4.4. ABE Update Policy Security
Theorem 5.
Under the assumption of the R-LWE decision, the proposed ABE scheme satisfies the updated policy security, which satisfies the IND-sCPA in the random oracle model.
Proof.
As described in the previous subsection, assuming there is an adversary Eve who wins the IND-sCPA game with an undeniable probability , the probability of challenger Charlie solving the R-LWE problem is ε/2. Eve and Charlie conduct the following query response game. □
- (1)
- Setup. Eve declares a query access structure and sends it to Charlie. Charlie interacts under the oracle machine after receiving the access structure , and the oracle machine randomly selects uniform random samples and pseudo-random samples. Thus, Charlie obtains .
- (2)
- Private key query. Eve queries the private key related to access control policies for message mi. This step is the same as the step shown in the proof of Theorem 4.
- (3)
- Challenge. Charlie randomly selects messages from those submitted by Eve. And according to the Update algorithm, he calculates , . If , . If , . If , and . Afterward, Charlie sends to Eve.
- (4)
- Guess. Eve repeats the private key query as many times as before. Then, Eve outputs a guess on . If , the oracle performs pseudo-random sampling on R-LWE. Otherwise, the oracle implements true random sampling.
The results can be divided into two situations. Assuming that the oracle is an R-LWE sampler, the updatable strategy is an effective challenge to ciphertext, and the distribution of ciphertext is consistent with the distribution of the challenger’s and adversary’s games. It can be inferred that the advantage of the adversary is in making correct guesses; otherwise, if the oracle samples are truly random instances, it proves that the updatable strategy is uniformly distributed, so the adversary can obtain a correct guess with a probability of 1/2. Therefore, according to Definition 3 and Definition 4 in Section 2, the proposed ABE scheme satisfies the updated policy security, which satisfies the IND-sCPA in the random oracle model.
5. Efficiency
In this section, we analyze the privacy protection scheme for blockchain data based on ABE. The specific analysis mainly includes efficiency analysis and performance analysis. Efficiency analysis mainly focuses on parameter size analysis and calculation time analysis. Efficiency analysis and performance analysis demonstrate the excellent efficiency and performance of this scheme by comparing it with similar schemes.
The parameter sizes of the proposed scheme are compared with similar schemes, mainly including the sizes of public key, private key, index, trapdoor, and ciphertext. The specific comparison results are shown in Table 1.

Table 1.
Comparison with other schemes based on lattice.
Furthermore, the performance and efficiency of these schemes are also analyzed and verified by simulation experiments. The secret key size and ciphertext size of our proposed scheme and those in ABE-PEKS (Liu, L. 2019) [12], LWE-PEKS (Behnia, R. 2020) [13], and Zhang, J. 2021 [15] are compared, respectively. According to the actual requirements in these schemes, under reasonable parameters, we set n = 256, q = 210, and m = 5211 () with 80-bit security and n = 512, q = 211, m = 11312 () with 192-bit security. The message length is set to l = 64 bit. The public key, private key, and ciphertext sizes of each scheme are compared. The results of the simulation experiments are shown in Figure 1a and Figure 1b, respectively. Here, LWE-PEKS’s ciphertext size is not shown in Figure 1 because the encryption phase does not exist. Through the comparison results, under the same conditions, the public key, private key, and ciphertext sizes in our scheme are significantly reduced, which is conducive to saving the computational overhead in blockchain and optimizing the operation efficiency for our scheme.
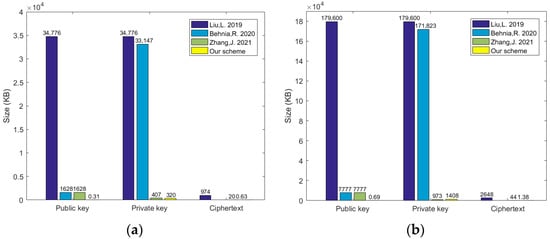
Figure 1.
Comparison sizes with other schemes. (a) 80-bit security; (b) 192-bit security.
In this section, the computational costs of the proposed scheme and similar schemes are analyzed and compared, mainly considering the computational costs of the proposed Index-generation, Trapdoor, Test, Keygen, Encrypt, and Decrypt. As shown in Table 2, Th, Tgs, Tsp, Tmul, Tm, and Te are set to represent the average consumption time of the following algorithms: Hash, Gaussain-samplepre, Samplepre, Modulo-multiplication, Matrix operation, and Encode operation, respectively. According to the comparison results in Table 2, it can be concluded that compared with the literature, our proposed scheme has a lower computational time in terms of index generation, encryption algorithm, decryption algorithm, etc. Therefore, our scheme has lower overall computational time costs and higher efficiency.

Table 2.
Time cost comparison with other schemes.
6. Novel Copyright Protection Scheme
6.1. Scheme Design
In this section, a blockchain copyright protection scheme based on the CP-ABE scheme with policy update is designed. As shown in Figure 2, this scheme combines the immutability of blockchain with the flexibility of ABE, aiming to provide a secure and efficient digital copyright protection mechanism. The detailed working process of our new scheme is as follows:
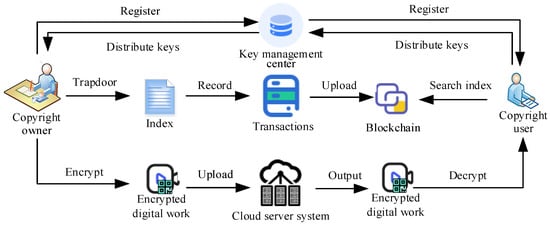
Figure 2.
Overview of novel copyright protection scheme.
- (1)
- Initialization. The blockchain platform serves as the infrastructure for digital copyright protection. There is a secure and reliable key management center in the system, which is responsible for generating and managing the required public key PK and master key MK for ABE through the Setup algorithm and defining the attribute sets and access policies. The attribute set includes various features of digital content, such as author, work name, and release date. The access policy defines which combinations of attributes allow users to access digital content. In addition, through the index sharing algorithm, after the three processes of index generation, trapdoor, and testing mentioned above, a data index structure containing storage addresses and keywords for digital works can be constructed.
- (2)
- Copyright registration. Copyright owner registers digital copyright information on the blockchain, including work content, attribute sets, and access policies. By using the Keygen algorithm in our ABE scheme, the Key management center generates key sk based on registration information and securely distributes them to the corresponding content creators.
- (3)
- Encryption. Copyright owner uses attribute-based encryption algorithms to encrypt digital content and embed access policies into ciphertext . The encrypted digital content is uploaded to the cloud server system, and it is constructed as a transaction record in the blockchain for other users to verify.
- (4)
- Access control and decryption. By using the Index sharing algorithm, the copyright owner establishes an index trapdoor to generate an index that is recorded in the blockchain. Thus, users can find the desired digital work index through keyword indexing and then request the corresponding digital content from the system. Among them, users need to provide their own attribute set proof. Smart contracts on the blockchain are proven based on access policies and user attribute sets to determine whether the user meets the access conditions. If the user meets the access conditions, the smart contract will obtain the corresponding public key from the blockchain and send it to the user. Users use the secret key to decrypt encrypted digital content and obtain the original content.
- (5)
- Policy Update. When the copyright owner needs to update the access policy, they execute the Update algorithm based on the new access structure, generate new encrypted files, and store them in the system. Smart contracts on the blockchain will automatically update access policies, ensuring that only users who meet the new policies can access digital works.
- (6)
- Copyright tracing and protection. If infringement is discovered, the copyright owner can search for registration information and transaction records of digital copyright on the blockchain to prove their copyright ownership. The consensus mechanism of the blockchain ensures the authenticity and integrity of copyright information and provides strong evidence for rights protection.
- (7)
- Audit and regulation. Regulatory authorities can regularly audit digital copyright information on the blockchain to ensure the compliance and effectiveness of copyright protection schemes. For discovered violations, regulatory authorities can take corresponding punitive measures to maintain order in the digital copyright market.
Through the above seven stages of work, the blockchain digital copyright protection scheme based on attribute-based encryption with updatable policies can achieve secure, efficient, and flexible digital copyright protection. This not only protects the legitimate rights and interests of creators but also promotes the legitimate dissemination and sharing of digital content.
6.2. Advantages of CP-ABE and Blockchain
We design a lightweight blockchain-based copyright protection scheme by recording copyrights on-chain while storing the actual works off-chain. Specifically, the index structure, which contains the storage address and keywords of digital copyright data, is uploaded to the on-chain ledger. Meanwhile, the digital content data, which occupies a substantial storage space, is stored on local servers or cloud servers of various digital media. This approach, combined with CP-ABE and searchable ciphertext, achieves efficient and secure solutions. The specific advantages are as follows:
- (1)
- Unlike traditional copyright protection systems, in our scheme, the on-chain ledger records only lightweight information, such as data storage, verification, operation, and transaction records. Upon generation of the original copyright data, it forms an index structure that is associated with real data, encompassing keywords, storage addresses, and signatures of digital content. This approach enables the proposed scheme to reduce the cost of storage space and enhance the efficiency of blockchain copyright data recording. In addition, the data storage method of blockchain enhances the copyright data’s traceability and integrity.
- (2)
- After encrypting data using the proposed CP-ABE scheme with a searchable encryption algorithm, a trapdoor containing copyright data keywords is generated. Subsequently, the index is recorded as a transaction in the blockchain ledger. Users can search for the desired digital works by embedding keywords in the data index structure beforehand. Upon passing the preset trapdoor verification, access to the data is granted, and the actual digital works can be downloaded from the cloud server through the address information in the index. Additionally, the keyword search functionality of this scheme is highly suitable for cross-institutional sharing of copyright data. On public cloud platforms, this indexing method can establish an effective channel to find the required digital work data through keywords. Furthermore, this approach prevents damage caused by direct human contact with data, thereby effectively protecting the security of digital works.
- (3)
- Due to the large size of digital work files, copyright protection systems have storage requirements for a large amount of audio and video data. However, placing this massive amount of data on the blockchain is impractical. Therefore, utilizing local servers and cloud storage technology, as described in this article, is a more promising and resource-efficient way to address this data storage challenge.
- (4)
- For copyright data, it is first encrypted by CP-ABE, and the encrypted data are stored on the blockchain. Incorporating the attributes of data into the secret key enables users to control their respective copyright data in a more granular manner. Only by verifying the correct attribute access policy can permission to view real data be obtained, thereby ensuring copyright data security.
6.3. Scheme Security Analysis
For the copyright protection scheme’s security, firstly, it is necessary to target complex user access and achieve fine-grained management of data access. Secondly, it is extremely important to ensure the copyright data’s security, including copyright data encryption security and privacy security. In addition, the data stored within the system cannot be maliciously tampered with, and the copyright protection system resists single points of failure and data silos. Based on the above security requirements, in this subsection, we conduct a detailed security analysis of the proposed copyright protection scheme.
6.3.1. Fine-Grained Access Control
Our CP-ABE scheme focuses on access control for attribute encryption in copyright protection. The CP-ABE scheme allows for the association of access control policies with encrypted ciphertext data and uses user attributes to define access rules. Only users who meet these attribute conditions can decrypt and access copyright data and conduct copyright transactions. Meanwhile, through the previous security analysis of the CP-ABE scheme, it is proven that the CP-ABE scheme satisfies the correctness of encryption. This CP-ABE technology provides fine-grained access control capabilities while protecting data privacy and ensuring data security. Therefore, our scheme satisfies the security requirements for copyright data’s fine-grained management in copyright protection systems.
6.3.2. Data Security and Privacy Protection
On the one hand, in this paper, CP-ABE is applied to copyright data so that user who satisfies the attributes can decrypt the data, ensuring the privacy and security of the data. Only when the user’s attribute satisfies the access policy can the data be decrypted and obtained. Otherwise, there is no other way to obtain copyright information or complete copyright transactions. The correctness and ciphertext security analysis of the attribute encryption scheme proven in Section 4 proves that the scheme can ensure the privacy and security of copyright data. On the other hand, the proposed CP-ABE scheme is based on lattice. Lattice-based cryptography is generally considered to have the advantage of resisting quantum computing attacks, and it can deal with the threat of quantum computers in the future [20]. Researchers have advocated for the development of novel strategies to include data encryption in the post-quantum era. Subsequently, lattice-based cryptography has garnered significant attention and focus in recent years, with its applications expanding rapidly across multiple domains [21,22]. Therefore, by using the theory of random lattice and the corresponding lattice basis, in this paper, we propose a new lattice-based CP-ABE scheme to improve anti-quantum security for blockchain copyright protection, which can protect data security in the future.
6.3.3. Resist Tampering Attack
If an adversary intends to tamper with existing copyright data and transaction information on the blockchain through tampering attacks, the blockchain can effectively resist tampering attacks through timestamp proof, distributed ledger, digital signature, SHA-256 algorithm, consensus mechanism, etc. Only if the consensus is successful can this transaction be verified and submitted to the blockchain distributed ledger. Therefore, by introducing blockchain technology into this copyright protection scheme, it can effectively prevent individual malicious nodes from tampering with transaction data.
6.3.4. Resist Single Point of Failure and Data Island
By harnessing the power of blockchain technology for decentralized distributed storage and robust authentication of copyright data, this innovative copyright protection scheme addresses the critical issues of single-point failure and data isolation that plague traditional, centralized copyright protection systems, thereby ensuring a more secure and reliable approach. This scheme utilizes the distributed ledger feature of blockchain technology to back up copyright data in a distributed manner on multiple nodes. In this way, even if some nodes fail or are attacked, other nodes can still work normally, ensuring the safe operation of the system and copyright data’s integrity. At the same time, the advantages of secure sharing of blockchain data can improve data island problems and achieve interconnectivity of copyright data. Therefore, by using blockchain for decentralized distributed storage and secure authentication of copyright data, this new copyright protection scheme can effectively solve the single point of failure and data island problems faced by traditional centralized copyright protection systems. In addition, the transparency and traceability of blockchain enhance the transparency of copyright usage and the verifiability of historical change records, providing strong evidence support for copyright protection.
7. Conclusions
The application of blockchain in fields such as the Internet of Things and digital copyright has become a trend. This study focuses on the urgent challenges of data privacy security and fine-grained access control that need to be addressed. We have studied and designed an innovative blockchain copyright protection scheme based on CP-ABE, which effectively addresses the data security and privacy challenges in traditional copyright data management, particularly in defense against quantum computing attacks. By utilizing the security and lattice cryptography of blockchain technology, this scheme not only ensures the authenticity and integrity of copyright data but also achieves secure access and fine-grained control of copyright data. In addition, the use of lattice-based cryptography can significantly enhance the scheme’s ability to resist quantum attacks. After security analysis and experimental verification, this scheme demonstrates resistance to multiple attacks under the random oracle model while having lower computational and storage costs, providing an efficient and secure new method for copyright protection.
Author Contributions
Conceptualization, J.J.; methodology, J.J. and Y.G. (Yulong Gao); formal analysis, J.J. and Y.G. (Yulong Gao); writing—original draft preparation, J.J., Y.G. (Yulong Gao) and Y.G. (Yufei Gong); writing—review and editing, Y.G. (Yulong Gao) and Z.J.; J.J. and Y.G. (Yulong Gao) contributed equally to this work and should be considered joint first authors. All authors have read and agreed to the published version of the manuscript.
Funding
This work is supported in part by the National Key R&D Program of China (2021ZD0111404), the Fundamental Research Funds for the Central Universities (CUC24QT04, CUC230D016), the National Natural Science Foundation of China (62172005), the National Key Research and Development Program of China (2022YFC3302103-01), and the Strategic Research Program of Science and Technology Commission of the Ministry of Education of China (JYB2022-01).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are contained within the article.
Acknowledgments
The authors extend their appreciation to the State Key Laboratory of Media Convergence and Communication in the Communication University of China for funding this research work through Fundamental Research Funds for the Central Universities.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Aberna, P.; Agilandeeswari, L. Digital image and video watermarking: Methodologies, attacks, applications, and future directions. Multimed. Tools Appl. 2024, 83, 5531–5591. [Google Scholar] [CrossRef]
- Hwang, J.S.; Kim, H.G. Blockchain-based copyright management system capable of registering creative ideas. J. Internet Comput. Serv. 2019, 20, 57–65. [Google Scholar]
- Lu, Z.; Shi, Y.; Tao, R.; Zhang, Z. Blockchain for digital rights management of design works. In Proceedings of the 2019 IEEE 10th International Conference on Software Engineering and Service Science (ICSESS), Beijing, China, 18–20 October 2019. [Google Scholar]
- Ma, Z.F.; Ming, J.; Gao, H.M.; Zhen, W. Blockchain for digital rights management. Future Gener. Comput. Syst. 2018, 89, 746–764. [Google Scholar] [CrossRef]
- Zhang, X.; Yin, Y. Research on Digital Copyright Management System Based on Blockchain Technology. In Proceedings of the 2019 IEEE 3rd Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Chengdu, China, 15–17 March 2019. [Google Scholar]
- Feng, Q.; He, D.B.; Zeadally, S.; Khan, M.K.; Kumar, N. A survey on privacy protection in blockchain system. J. Netw. Comput. Appl. 2019, 126, 45–58. [Google Scholar] [CrossRef]
- Fernández-Caramès, T.M.; Fraga-Lamas, P. Towards Post-Quantum Blockchain: A Review on Blockchain Cryptography Resistant to Quantum Computing Attacks. IEEE Access. 2020, 8, 21091–21116. [Google Scholar] [CrossRef]
- Gao, Y.L.; Chen, X.B.; Chen, Y.L.; Sun, X.; Niu, X.X.; Yang, Y.X. A Secure Cryptocurrency Scheme Based on Post-Quantum Blockchain. IEEE Access. 2018, 6, 27205–27213. [Google Scholar] [CrossRef]
- Yu, G.S.; Zha, X.; Wang, X.; Ni, W.; Yu, K.; Yu, P.; Zhang, J.A.; Liu, R.P.; Guo, Y.J. Enabling Attribute Revocation for Fine-Grained Access Control in Blockchain-IoT Systems. IEEE Trans. Eng. Manag. 2020, 67, 1213–1230. [Google Scholar] [CrossRef]
- Wang, S.; Zhang, X.; Zhang, Y. Efficient revocable and grantable attribute-based encryption from lattices with fine-grained access control. IET Inf. Secur. 2018, 12, 141–149. [Google Scholar] [CrossRef]
- Zhang, X.; Xu, C.; Wang, H.; Zhang, Y.; Wang, S. FS-PEKS: Lattice-Based Forward Secure Public-Key Encryption with Keyword Search for Cloud-Assisted Industrial Internet of Things. IEEE Trans. Dependable Secur. Comput. 2021, 18, 1019–1032. [Google Scholar] [CrossRef]
- Liu, L.; Wang, S.; He, B.; Zhang, D. A Keyword-Searchable ABE Scheme from Lattice in Cloud Storage Environment. IEEE Access 2019, 7, 109038–109053. [Google Scholar] [CrossRef]
- Behnia, R.; Ozmen, M.O.; Yavuz, A.A. Lattice-Based Public Key Searchable Encryption from Experimental Perspectives. IEEE Trans. Dependable Secur. Comput. 2020, 17, 1269–1282. [Google Scholar] [CrossRef]
- Zuo, Y.; Kang, Z.; Chen, Z. BCAS: A blockchain-based ciphertext-policy attribute-based encryption scheme for cloud data security sharing. Int. J. Distrib. Sens. Netw. 2021, 17, 1–16. [Google Scholar] [CrossRef]
- Zhang, J.; Xin, Y.; Gao, Y.; Lei, X.; Yang, Y. Secure ABE Scheme for Access Management in Blockchain-Based IoT. IEEE Access 2021, 9, 54840–54849. [Google Scholar] [CrossRef]
- Li, J.; Yao, W.; Han, J.; Zhang, Y.; Shen, J. User Collusion Avoidance CP-ABE with Efficient Attribute Revocation for Cloud Storage. IEEE Syst. J. 2017, 12, 1767–1777. [Google Scholar] [CrossRef]
- Zhang, Z.; Ren, X. Data security sharing method based on CP-ABE and blockchain. J. Intell. Fuzzy Syst. 2021, 40, 2193–2203. [Google Scholar] [CrossRef]
- Liu, S.; Yu, J.; Chen, L.; Chai, B. Blockchain-Assisted Comprehensive Key Management in CP-ABE for Cloud-Stored Data. IEEE Trans. Netw. Serv. Manag. 2023, 20, 1745–1758. [Google Scholar] [CrossRef]
- Lyubashevsky, V.; Peikert, C.; Regev, O. On ideal lattices and learning with errors over rings. In Proceedings of the Advances in Cryptology–EUROCRYPT 2010: 29th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Riviera, French, 30 May–3 June 2010. [Google Scholar]
- Nejatollahi, H.; Dutt, N.; Ray, S.; Regazzoni, F.; Banerjee, I.; Cammarota, R. Post-quantum lattice-based cryptography implementations: A survey. ACM Comput. Surv. 2019, 51, 1–41. [Google Scholar] [CrossRef]
- Asif, R. Post-quantum cryptosystems for Internet-of-Things: A survey on lattice-based algorithms. IoT 2021, 2, 71–91. [Google Scholar] [CrossRef]
- Liu, Z.; Choo, K.; Grossschadl, J. Securing edge devices in the post-quantum internet of things using lattice-based cryptography. IEEE Commun. Mag. 2018, 56, 158–162. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).