Abstract
Damage is the main form of conflict, and the characterization of damage information is an important component of conflict evaluation. In the existing research, damage mainly refers to the damage effect of a damage load on the target structure. However, in the actual conflict environment, damage is a complex process that includes the entire process from the initial introduction of the damage load to the target function. Therefore, in this paper, the transfer logic of the damage process is analyzed, and the damage process is sequentially divided into being discovered, being attacked, being hit, and being destroyed in succession. Specifically, first considering the multiple types of each process, the transmission of damage is likened to the flow of damage, a network model to characterize damage information based on heterogeneous network meta-path and network flow theory (HF-MCDI) is established. Then, the characteristics of damage information are analyzed based on the capacity of the damage network, the correlation of the damage path, and the importance of the damage node. In addition, HF-MCDI can not only represent the complete damage information and the transmission characteristics of the damage load but also the structural characteristics of the target. Finally, the feasibility and effectiveness of the established HF-MCDI method are fully demonstrated by the example analysis of the launch platform.
1. Introduction
In the existing research, damage mainly refers to the damage effect of a damage load on the target structure. For example, the damage response of structures under damage loads, such as shock waves or fragments [1], damage effect of energetic fragments on a target plate [2], and other structural damage characteristics in the conflict environment [3]. However, in the actual conflict environment, damage is a complicated transmission process that includes the whole process from the launch of the damage load to the target function. This process includes: (1) After reconnaissance finds the target, determining whether or not to attack; (2) After determining the target value, initiating the damage charge to the target; (3) After the target evades protection, the damage charge begins to impact the target structure; (4) Until the core structure is destroyed, determining the target is destroyed. Therefore, how to systematically characterize this logical process becomes the key to operational assessment.
At present, the characterization of damage information mainly includes test methods and model methods. Among them, the reliability of the results of the experimental method is high [4], but the research cost is also relatively high, and for some complex systems, it is even difficult to conduct experimental studies. Model methods are divided into two categories according to the underlying theory: evaluation methods based on mathematical statistics [5,6] and knowledge inference [7,8], among which the evaluation methods based on mathematical statistics have a simple model-building process and easy calculation and are widely used for the characterization of destructive information in areas such as vulnerability and conflict effectiveness [9]. The evaluation method based on knowledge inference is relatively higher than the evaluation method based on mathematical statistics in terms of evaluation accuracy and credibility [10], but it relies on prior knowledge and subjective judgment of experience, therefore, the calculation process is more complicated. In summary, the current method of representing damage information is influenced by subjective empowerment and probability statistics, and suffers from a lack of objectivity and physical interpretation, and has a poor correlation between the representation process and reality.
Network analysis is one of the research hotspots in the field of information representation. Most of the current information network analysis work is on homogeneous information networks, i.e., the same type of nodes and network link relationships [11]. Homogeneous information networks mainly extract part of the information of the interactive systems without distinguishing the differences between the interactive systems, which easily leads to the loss of semantic information extraction. Therefore, researchers have proposed heterogeneous information networks with multi-type nodes [12]. In addition, meta-path is an important concept defined in heterogeneous information networks to extract semantic information from heterogeneous networks [13,14]. Compared to homogeneous information networks, heterogeneous information networks contain more comprehensive structural information and rich semantic information.
Based on the above description, this paper first proposes a network model to characterize damage information based on heterogeneous network meta-path and network flow theory. This network model is divided into an efficiency attribute sub-network, an avoidance attribute sub-network, a structure attribute sub-network, and a function attribute sub-network according to the transmission logic of the damage process. Each sub-network is connected based on the network flow theory, and the damage process is represented by the damage network flow. The comparison between the proposed damage information characterization method and the existing damage information characterization method is illustrated in Figure 1. Then, the characteristics of the damage information are analyzed in terms of damage network capacity, damage path correlation, and damage node significance. HF-MCDI can represent not only the complete damage information and the transmission characteristics of the damage load, but also the structural characteristics of the target. The innovations and contributions of this research can be summarized as follows:
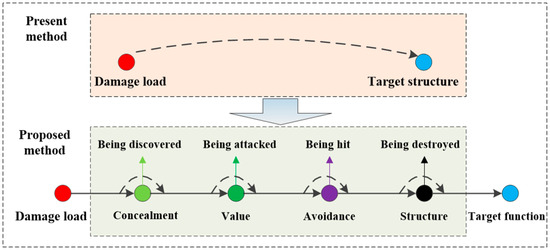
Figure 1.
The comparison of the characterization method between proposed and existing.
- The proposed network model can represent the damage process more completely and is more a in line with the actual conflict environment;
- The proposed network model is no longer attacker-centered, but defender-centered, which can analyze the structure–function characteristics of the defender in more detail, and the probability representation is no longer required.
- The established damage capacity model, damage path model, and damage node model can evaluate the damage process more objectively.
2. Network Model
2.1. Conceptions
Definition 1.
Heterogeneous network [15]. In the digraph , V represents a set of nodes and E represents a set of edges. There is a node-type mapping function : , and an edge-type mapping function : , where is node-type, is edge-type, and if there is , this type of network is defined as a heterogeneous network, and is defined as network mode.
Definition 2.
Meta-path [15]. A meta-path is a path defined on a network mode as:
This path describes a composite relationship between specific nodes :
where represents the composition operator on the composite relation .
Definition 3.
Network capacity [16]. is a non-negative function defined on the set of connected edges, and if there are connected edges , then defined is the capacity on the connected edges . Similarly, is defined as the capacity on the node .
Definition 4.
Network flow [16]. is a function defined on a connected edge set ; if there is an edge , is defined as a flow on a connected edge .
Based on the above theoretical conceptions and the transfer logic of the damage process, the conceptions of the network model are defined as follows.
Definition 5.
Damage node. This refers to the conditions that affect the load transfer between the failure load and the target function. The tolerance of each condition is defined as the damage capacity of the damaged node.
Definition 6.
Damage path. This refers to the connection edge of the damaged node through which the damage load is transferred to the target function. The load that can pass through each edge is defined as the damage flow.
Definition 7.
Damage information. This refers to all the contents contained in the directed heterogeneous network formed by the combination of damage load, damage node, and damage path.
Based on the above definition, the framework of HF-MCDI is shown in Figure 2. According to the attributes of damaged nodes, HF-MCDI is divided into four sub-networks. The efficiency attribute sub-network is composed of virtual nodes and logical associations that affect load transfer. The avoidance attribute sub-network consists of protection nodes and logical associations that affect load transfer. The structural attribute sub-network consists of structural nodes and installation associations that affect load transfer. The functional attribute sub-network consists of functional nodes that represent the results of load transfer. Additionally, the four sub-networks are elaborated in the following sections.
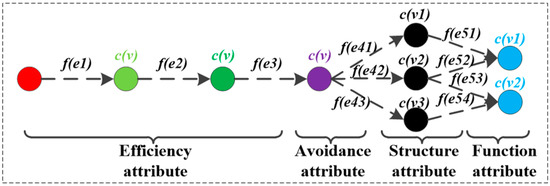
Figure 2.
The framework of HF-MCDI.
2.2. Efficiency Attribute Sub-Network
The efficiency attribute sub-network is defined as . It can be seen from Figure 2 that the transmission of damage load in is tandem in nature and does not weaken. Therefore, has the following two characteristics:
- There is only one path for the damage load to be transmitted in , and the damage flow on the path was , where is the damage load.
- The damage capacity of damaged nodes is determined by node performance, and obeys step function distribution.
In addition, the framework of is shown in Figure 3. For there is:
where is damage flow of , is damage capacity of , is the conditional degree value of the damaged node, and is the critical point of the conditional degree value of the damaged node.
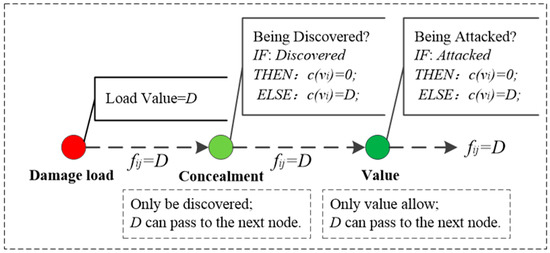
Figure 3.
The framework of .
2.3. Avoidance Attribute Sub-Network
The efficiency attribute sub-network is defined as . The damaged node in is determined by the subjective judgment of the damage load avoidance amount. After the judgment, the damaged path will be divided into multiple paths according to the target structure. Therefore, has the following two characteristics:
- The damage load avoidance amount is related to the target avoidance degree , and obeys the logistic function distribution, which can be described as [17]:where is the coefficient of the avoidance degree and is the midpoint of the avoidance degree.
- The damage flow on the damage path is related to the exposed area of the target structure. If the number of exposed parts of the target is , and is the exposed area of part , then the path coefficient is .In addition, the framework of is shown in Figure 4. For there is:where is damage flow of and is damage capacity of .
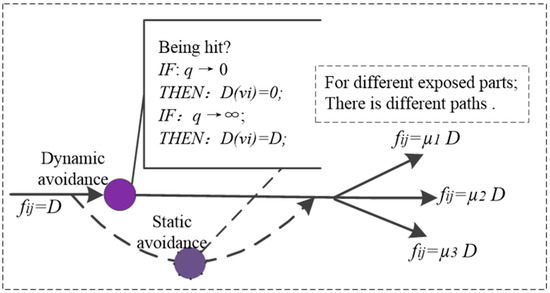 Figure 4. The framework of .
Figure 4. The framework of .
2.4. Structural Attribute Sub-Network
The structural attribute sub-network is defined as . The modular arrangement of the structure makes hierarchical and clustered, and in , the transmission of damage loads is a failure-resistant process of each node, and has the following characteristics.
- The damage flow along the damage path is the blocking effect of the structure on the damage load, and the smaller the blocking effect, the greater the damage flow.
- Damage capacity is the extreme limit of deformation of a structure under a damage load. When the damage load transferred to the node is greater than the damage capacity of the node, the damage load overflows, and the remaining damage load continues to be transferred to the next node.
Therefore, assume that the structure is composed of a number of structural element units, the energy method is used to calculate the structural element deformation as [18]:
where and are bending strain energy and midplane strain energy. For rigid plastic materials: , is the yield limits of materials. The mask force , and are equal to , and . is the material thickness.
The strain energy of structural element is calculated as:
where is the size function, and is the deformation deflection of the structural center.
When the damage load transferred to the structural element unit is , let represent the blocking effect of the structural element unit on the damage load, and is the response state of the structural element.
Taking the structural unit as the reference, the displacement at the boundary is 0 and the angle is 0. In this paper, the bit triangular function is utilized to simulate the equations of flexural lines as:
where is the size of the material in direction , and is the size of the material in direction .
According to the maximum deformation and maximum deformation volume of the material and based on the following formula, the maximum strain energy of structural element can be calculated.
In addition, the framework of is shown in Figure 5. For there is:
where is damage flow of , is damage capacity of .
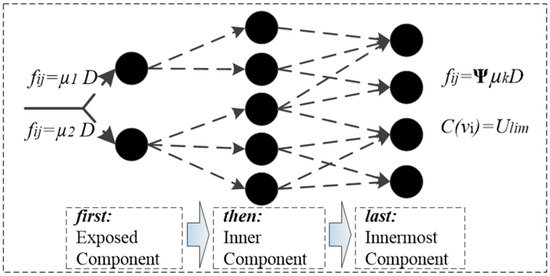
Figure 5.
The framework of .
2.5. Functional Attribute Sub-Network
The structural attribute sub-network is defined as . The functional attribute sub-network consists of functional nodes that display the results of load transfer. Since function is the display of structure, is the display of the running state of . Therefore, for there is:
In summary, a heterogeneous network model can be obtained to fully characterize the damage information, and a meta-path can also be obtained to characterize the transfer process of a damage load. The path is defined as the meta-path of the damaged information heterogeneous network, where is the node set of . This meta-path is represented as:
3. Characteristics
3.1. Damage Capacity
The damage path is shown in Figure 6; the starting point of the damage path of HF-MCDI is the damage load in , which is defined as . The ending point is any functional node in , which is defined as . is the number of functional nodes. Then, there is:
where is the damage path of Article .
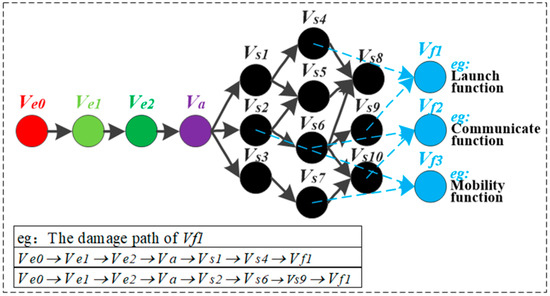
Figure 6.
The damage path.
The damage capacity of each damage path is the sum of the damage capacities of nodes in different subnetworks on this damage path. That is, the damage capacity of is , where are the damage capacity vectors of nodes of the damage paths in different subnetworks. When the damage capacity coefficient is defined as the ratio of damage capacity to damage load, , the damage capacity coefficient matrix of the damage path can be established as .
Then, the residual damage load coefficient transfer to the function on the damage path is:
where is the sum of the row vectors of .
Obviously, when appears, it means that the damage capacity of the damage path is filled by the damage load, and the function of the target is in a critical state of damage. When appears, the damage load exceeds the damage capacity, and the target function is damaged. When appears, the damage load is blocked by the damage capacity, and the function of the target is not damaged.
3.2. Correlation of Damage Path
The correlation of the damage path can be used to measure the similarity of the damage load to the function; the higher the correlation of a damage path, the more dangerous this damage path is. In network flow theory, the damage flow on the damage path is the weight of the connecting edges between nodes, and the weight matrix can be defined as . When the weight matrix is mapped to the same space, according to the subnetwork, it can be obtained by:
where is the weight value after mapping, and .
Assume that is the node number on the damage path, and is the neighbor node of node on the damage path . The WsRel method is a typical path measurement method [19], which is suitable for obtaining accurate information between the source node and the target node. Based on the WsRel method, the correlation of damage paths is defined as:
Since the HF-MCDI has many damage paths, the correlation of the HF-MCDI is:
where is the weight of the damage path in Article , and is related to the connection strength . According to the Shi algorithm, in Article is calculated as:
where is out degree and is in degree. Additionally, the connection strength of the damaged path can be defined by the Softmax function as:
3.3. Importance of Damaged Nodes
The importance of the damaged node lies in its influence on the network model. Considering the heterogeneity of HF-MCDI, this paper selects the node shrinkage method to calculate the importance of the damaged nodes [20] and improves the node shrinkage method according to the correlation attributes of HF-MCDI. Considering the heterogeneity and rapidity of convergence of HF-MCDI, this paper selects the node shrinkage method to calculate the importance of the damaged nodes, improves the node shrinkage method according to the correlation attributes of HF-MCDI, and makes HF-MCDI more comprehensive.
The cohesion degree of HF-MCDI is defined as , and , where is the number of nodes in the network, is the average path length, , and is the distance between node and node . The cohesion degree of HF-MCDI can be updated as:
In addition, the importance of the damaged node is defined as:
where is the network after node was shrunk.
Based on the above formula, there is:
where is the number of neighbor nodes of .
Due to the connectivity between neighboring nodes in HF-MCDI, it is not sufficient to consider only the number of neighboring nodes; the importance of neighboring nodes should also be considered. Therefore, the improved importance of damaged nodes is defined as:
where is the neighboring node of , and are the proportional relationship of importance, , which can be allocated based on damage capacity according to the following formula:
4. Analysis
4.1. Illustrative Example
In order to demonstrate the effectiveness of the proposed method in this paper, a special equipment platform was taken as the research object. The special equipment platform is a complex body combining structure and function. According to the establishment method of HF-MCDI in Section 2, a special equipment platform HF-MCDI with 4 node types, 40 network nodes, and 121 directed edges was established, as shown in Figure 7.
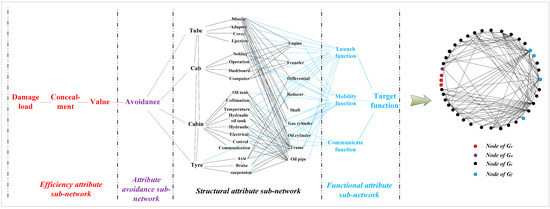
Figure 7.
HF-MCDI of the special equipment platform.
4.2. Basic Features of HF-MCDI
In this paper, MATLAB is used to calculate the model shown in Figure 7, where the nodes are numbered from 1 to 40, from left to right, and from top to bottom, and the visual description in MATLAB is shown in Figure 8. The basic characteristics of HF-MCDI are then analyzed in terms of degree distribution, clustering coefficients, and node centrality according to complex network theory.
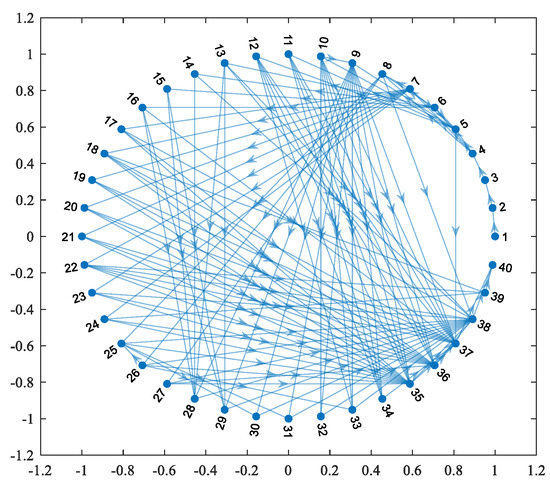
Figure 8.
The visual description of HF-MCDI of the special equipment platform in MATLAB.
4.2.1. Degree Distribution
The degree distribution of HF-MCDI of the special equipment platform is shown in Figure 9.
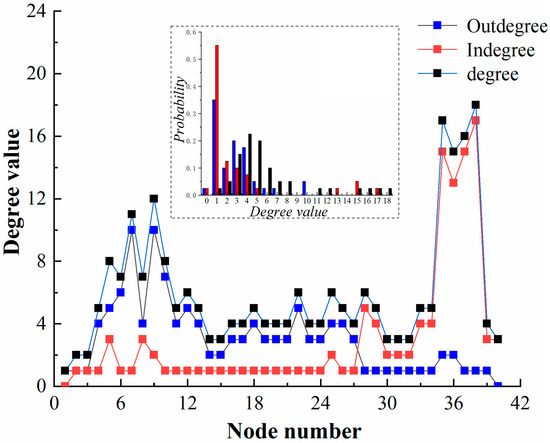
Figure 9.
The degree distribution of HF-MCDI of the special equipment platform.
Figure 9 shows that:
- (1)
- The node degree of the network is mainly distributed in two parts: and . The proportion of is 65%. Among them, has the largest proportion, which is 22.5%, and the nodes of and are 20% and 15%, respectively. The results show that there are 3–5 connecting edges in most nodes of this network, which accords with the characteristics of four-sided adjacency of structural components in space. The proportion of is 35%, indicating that there are some nodes with high passing frequencies in the network, which are the key to damage flow, and they are mainly distributed in the front of and .
- (2)
- The maximum indegree of the nodes in this network is in , . The maximum outdegree of the nodes in this network is in , . has the largest ratio, which is 55%, while has 85%. This shows that the transmission of damage information in this launch platform is mainly stratified and dispersed, which is determined by the integration and modularity of the launch platform.
4.2.2. Clustering Coefficient
The clustering coefficient of HF-MCDI of the special equipment platform is shown in Figure 10.
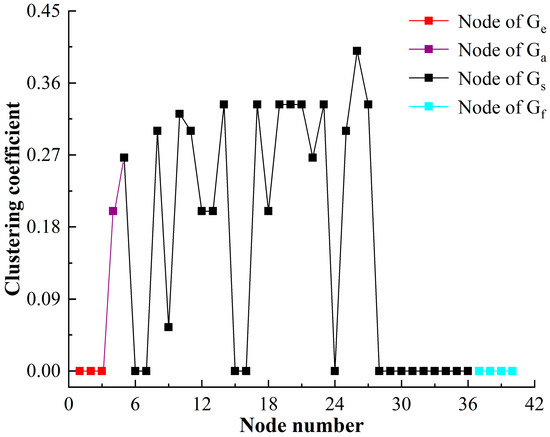
Figure 10.
The clustering coefficient of HF-MCDI of the special equipment platform.
Figure 10 shows that:
- (1)
- The clustering coefficient of the network is 0 at nodes 1, 2, 3, and 28 to 40. The clustering coefficients of other nodes, especially those in , all fluctuate around 0.25. The results show that there is a local aggregation phenomenon in the structure attribute subnetwork of the launching platform, and it is relatively uniform. When a node is damaged, it is easy to spread to the neighboring nodes, which is determined by the structural characteristics of the launching platform.
- (2)
- The clustering coefficient is 0 in . The result shows that the nodes in are not tightly connected because the concealment of the target and the value of the target don’t affect each other but are only logically connected, and this result is in line with reality.
- (3)
- The clustering coefficient is 0 in . Because the nodes in are connected to the nodes in , and the nodes in are not related to each other, the aggregation of function is reflected in the aggregation of structure.
4.2.3. Node Centrality
The node centrality of HF-MCDI of the special equipment platform is shown in Figure 11.
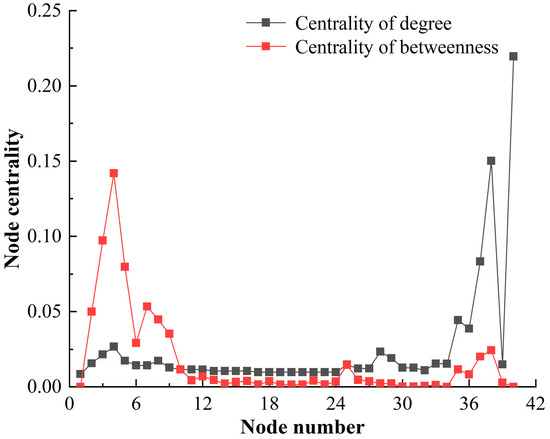
Figure 11.
The node centrality of HF-MCDI of the special equipment platform.
Figure 11 shows that:
- (1)
- From the centrality of degree: The node with the highest centrality of degree of the launch platform is the total function (0.2196), followed by the mobility function (0.1502) and the launch function (0.0834). This indicates that the node of has greater influence because the centrality of degree describes the centrality of nodes in the network, indicating that the launch platform operates according to the function. Therefore, the center of the network is concentrated in .
- (2)
- From the centrality of betweenness: The centrality of betweenness is distributed in three levels. ① There are 5 nodes with a centrality value greater than 0.05, including avoidance (0.1420), value (0.0973), tube (0.0798), concealment (0.0534), and cabin (0.0506); ② There are 3 nodes with a centrality value greater than 0.02 and less than 0.05, which are the exposed nodes of ; ③ The centrality value of the remaining 80% of the nodes is less than 0.02. This suggests that the avoidance node has the greatest impact due to the fact that mesoscopic centrality describes the role of damage paths, and avoidance is a critical node in the damage path of the special equipment platform.
4.3. Damage Capacity for HF-MCDI
Following the calculation process in Section 3.1, it can be calculated that there are 15 damage paths for launch function, 17 damage paths for mobility function, and 3 damage paths for communicate function, and the damage path of the mobility function accounts for the largest proportion. The residual damage load coefficient calculated on each damage path is shown in Figure 12, Figure 13 and Figure 14.
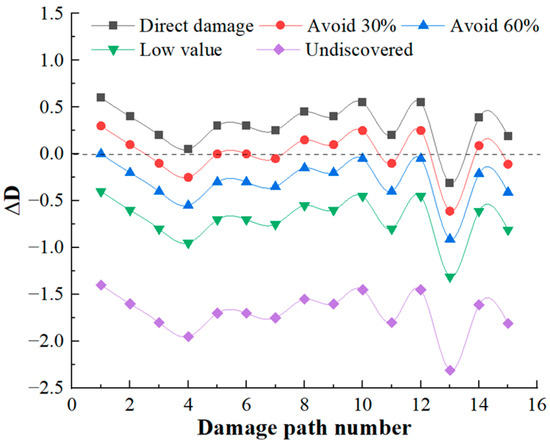
Figure 12.
Residual damage load coefficient of launch function.
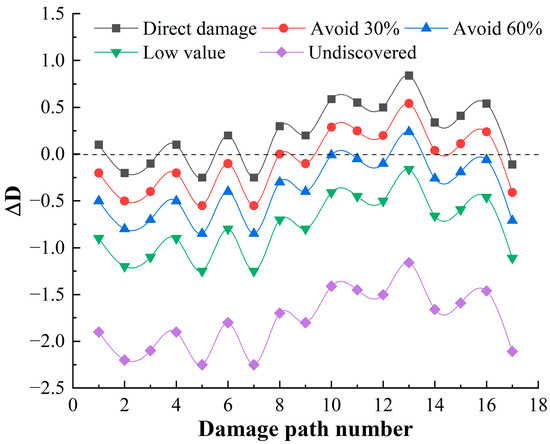
Figure 13.
Residual damage load coefficient of mobility function.
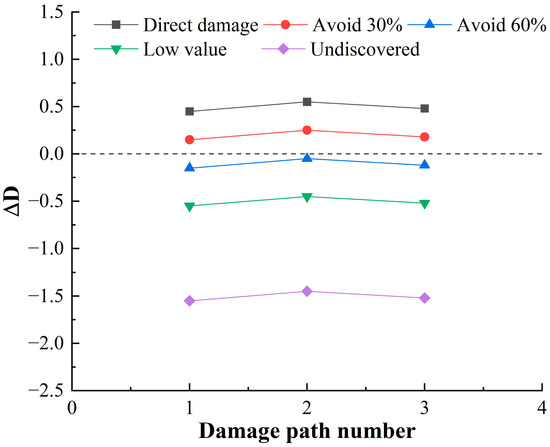
Figure 14.
Residual damage load coefficient of communicate function.
- (1)
- When the target is discovered, and has a high value, and does not avoid direct damage, the launch function has 1 damage path with a residual damage load factor less than 0. The maneuver function has 5 damage paths with a residual damage load factor less than 0, and 0 damage paths with a residual damage load factor less than 0 for the communication function. It can be seen that the launch platform relies only on structural protection, which has little deterrent effect on damage loads, and the percentage of safe paths is 17.14%. Among these safe paths, the safe path for the launch function is 2.86%; the safe path for the mobility function is 14.28%; and the safe path for the communication function is 0, reflecting the poor protection of the launch platform.
- (2)
- When the target is discovered and has a high value and some avoidance, that is, , the value of the residual damage load coefficient begins to decrease. When the degree of avoidance is 30%, the proportion of safe paths is 42.86%; when the degree of avoidance is 60%, the proportion of safe paths is 91.43%. When the target is not discovered or the value is low, that is, , showing that reducing the discovery probability of the target can fundamentally block the transmission of damage load.
- (3)
- There are 29 damage paths of when the target is discovered, and has a high value, and does not avoid direct damage, among which the damage path of the launch function accounts for the highest proportion (48.28%), which indicates that the launch function is the most likely to be damaged. In the damage path of , the damage path through the cabin accounts for the highest proportion, which indicates that the damage of the launch platform is mainly from the cabin.
4.4. Correlation of Damage Path for HF-MCDI
Following the calculation process in Section 3.2, the correlation of the damage path is shown in Figure 15.
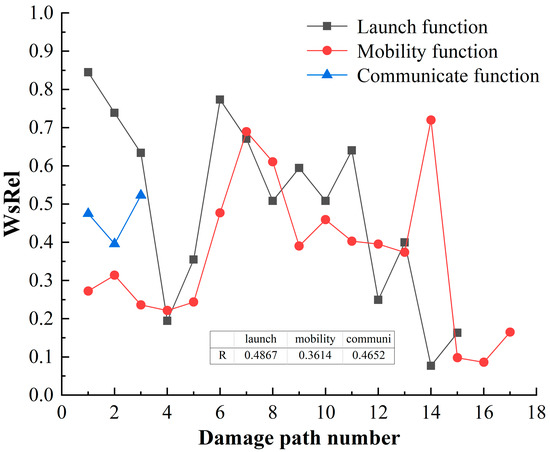
Figure 15.
The correlation of damage path.
Figure 15 shows that:
- (1)
- On the whole, the correlation distribution between the damage and the emission function is large. The damage path of Damage load–Concealment–Value–Avoidance–Tube–Launch function has the greatest correlation, , which indicates that damage load is most likely to destroy the function from this path.
- (2)
- The damage path of Damage load–Concealment–Value–Avoidance–Tube–Launch function has the greatest correlation, , which indicates that damage load is most likely to destroy the launch function from this path. The average WsRel value of launch function is 0.4901, and the correlation of the HF-MCDI of launch function is , which indicates that the correlation between launch function and damage load is highest, which is consistent with the damage capacity analysis results in Section 4.3.
- (3)
- The damage path of Damage load–Concealment–Value–Avoidance–type–Mobility function has the greatest correlation in the damage path of mobility function, , which indicates that damage load is most likely to destroy the mobility function from this path. The average WsRel value of mobility function is 0.3589, and the correlation of the HF-MCDI of mobility function is , which indicates that the correlation between mobility function and damage load is higher.
- (4)
- Damage load and communication function have few damage paths, the average WsRel value of communication function is 0.4647, and the correlation of the HF-MCDI of communication function is .
4.5. Importance of Damaged Node for HF-MCDI
Following the calculation process in Section 3.3, the importance of the damaged node is shown in Figure 16.
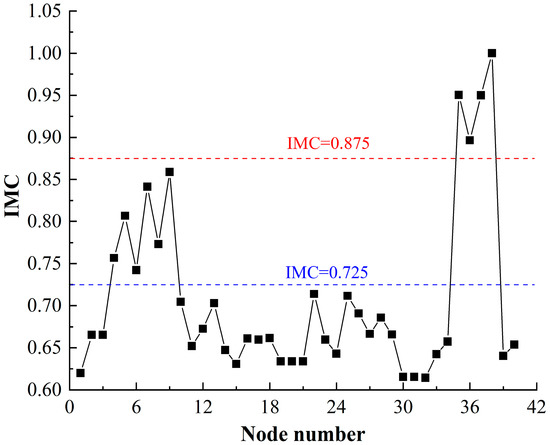
Figure 16.
Importance of damaged node.
Figure 16 shows that:
- (1)
- The importance of damaged nodes is divided into three levels: ① There are 4 nodes with IMC values greater than 0.875, which are: Mobility function (1), Launch function (0.9681), Frame (0.9504), and Oil pipe (0.8965). This shows that these nodes are most important to the HF-MCDI of the launch platform. At the same time, it reflects that the launch platform takes the mobility function as the core function and the frame as the main structure; ② There are 6 nodes with IMC values greater than 0.725 and less than 0.875, in descending order of the largest to smallest, including the Missile, Compartment, Tube, Tyre, Cab, and Avoidance nodes, indicating that these nodes are of high importance to the HF-MCDI of the launch platform, that is, the exposed portion and avoidance have significant impact on transferring damage load; therefore, these nodes can be used in the optimization of protection; ③ For the remaining 30 nodes, the IMC value is less than 0.725 and greater than 0.6, and the importance of these nodes is small.
- (2)
- The importance of nodes based on IMC values, which integrate the centrality of degree to measure the structure of the HF-MCDI and the centrality of betweenness to measure the transmission of the HF-MCDI, provides a more comprehensive measure of the importance of the HF-MCDI.
5. Conclusions
The logic of the transfer process of a damage load is analyzed, and a damage information characterization method based on heterogeneous network theory and network flow theory is established. From the obtained results, the following conclusions could be drawn.
- (1)
- Compared with the existing methods, the proposed method can describe the damage process more completely from the viewpoint of damage transfer, and is more consistent with the actual conflict evaluation.
- (2)
- By analyzing the basic features of the HF-MCDI, the degree distribution can indicate the structural characteristics of the damage target, the clustering coefficient can indicate the correlation characteristics of the damage information, and the node centrality can indicate the nodes with a strong influence on the damage process. The digital characterization of these fundamental features can make the study of the damage process more objective.
- (3)
- HF-MCDI establishes the damage process in the form of a network from the initiation of the damage load to the impact on the target. The correlation of damage capacity and damage path can be used to analyze the critical links of damage information, and the importance of damage nodes can be used to analyze the critical nodes of damage information. These analyses can point out the direction for the protection of the target.
Author Contributions
T.H. proposed the main idea and finished the draft manuscript; Q.G. and Z.L. participated in the discussion of diagnostic thinking and provided correction of English grammar; D.W. and D.M. drew the figures and tables; and L.G. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Lai, E.; Zhao, J.; Li, X.; Hu, K.; Chen, G. Dynamic responses and damage of storage tanks under the coupling effect of blast wave and fragment impact. J. Loss Prev. Process Ind. 2021, 73, 104617. [Google Scholar] [CrossRef]
- Tian, S.; Du, X.; Yan, Q.; Wu, J.; Zhuang, T. Damage effect of pile wharf under underwater explosion load. Mech. Adv. Mater. Struct. 2023, 30, 29–47. [Google Scholar] [CrossRef]
- Guo, Y.; Han, Z.; Guo, H.; Wang, T.; Liu, B.; Wang, D. Numerical simulation damage analysis of pipe-cement-rock combination due to the underwater explosion. Eng. Fail. Anal. 2019, 105, 584–596. [Google Scholar] [CrossRef]
- Yang, F.; Li, Z.; Zhuang, Z.; Liu, Z. Evaluating the blast mitigation performance of hard/soft composite structures through field explosion experiment and numerical analysis. Acta Mech. Sin. 2022, 38, 27–36. [Google Scholar] [CrossRef]
- Zhao, K.; Jia, F.; Shao, H. A novel conditional weighting transfer Wasserstein auto-encoder for rolling bearing fault diagnosis with multi-source domains. Knowl.-Based Syst. 2023, 262, 110203. [Google Scholar] [CrossRef]
- Zhao, K.; Hu, J.; Shao, H.; Hu, J. Federated multi-source domain adversarial adaptation framework for machinery fault diagnosis with data privacy. Reliab. Eng. Syst. Saf. 2023, 236, 109246. [Google Scholar] [CrossRef]
- Yao, T.; Miao, R.; Wang, W.; Li, Z.; Dong, J.; Gu, Y.; Yan, X. Synthetic damage effect assessment through evidential reasoning approach and neural fuzzy inference: Application in ship target. Chin. J. Aeronaut. 2022, 35, 143–157. [Google Scholar] [CrossRef]
- Jin, B.; Cruz, L.; Gonçalves, N. Deep Facial Diagnosis: Deep Transfer Learning from Face Recognition to Facial Diagnosis. IEEE Access 2020, 8, 123649–123661. [Google Scholar] [CrossRef]
- Jin, B.; Cruz, L.; Gonçalves, N. Pseudo RGB-D Face Recognition. IEEE Sens. J. 2022, 22, 21780–21794. [Google Scholar] [CrossRef]
- Zhao, K.; Jiang, H.; Wang, K.; Pei, Z. Joint distribution adaptation network with adversarial learning for rolling bearing fault diagnosis. Knowl.-Based Syst. 2021, 222, 106974. [Google Scholar] [CrossRef]
- Triana, J.; Delgado, C.A.; Martinez-Mendoza, K.L. Whale optimization algorithm guided by complex networks. Int. J. Artif. Intell. 2023, 21, 55–66. [Google Scholar]
- Nasser, A.M.; Chiang, T.S.; Ping, C.W. Distributed parallel deep learning with a hybrid backpropagation-particle swarm optimization for community detection in large complex networks. Inf. Sci. 2022, 600, 94–117. [Google Scholar] [CrossRef]
- Luo, J.; Bao, Y.; Chen, X.; Shen, C. Metapath-based deep convolutional neural network for predicting miRNA-Target association on heterogeneous network. Interdiscip. Sci. Comput. Life Sci. 2021, 13, 547–558. [Google Scholar] [CrossRef] [PubMed]
- Tan, L.; Gong, D.; Xu, J.; Li, Z.; Liu, F. Meta-path fusion based neural recommendation in heterogeneous information networks. Neurocomputing 2023, 529, 236–248. [Google Scholar] [CrossRef]
- Liu, Q.; Tan, H.S.; Zhang, Y.M.; Wang, G.Y. Dynamic heterogeneous network representation method based on meta-path. Acta Electron. Sin. 2022, 50, 1830–1839. [Google Scholar]
- Wang, L.F.; Li, H.; Zhao, G.T. Improved load re-allocation strategy based on maximum residual capacity of node. J. Northeast. Univ. (Nat. Sci.) 2020, 41, 1223–1230. [Google Scholar]
- Dong, Y.; Ma, S.; Zhang, H.; Yang, G. Wind power prediction based on multi-class autoregressive moving average model with logistic function. J. Mod. Power Syst. Clean Energy 2022, 10, 1184–1193. [Google Scholar] [CrossRef]
- Huang, X.; Liu, X.; Li, J.; Chen, Y.; Wei, D.; Ding, G. Machining deformation analysis of aircraft monolithic components based on the energy method. Int. J. Adv. Manuf. Technol. 2022, 119, 5797–5805. [Google Scholar] [CrossRef]
- Symeonidis, P.; Tiaksa, E. Transitive node similarity: Predicting and recommending links in signed social networks. World Wide Web 2014, 17, 743–776. [Google Scholar] [CrossRef]
- Liu, N.; Shen, J.; Yu, K.P. Weighted supply chain network node importance assessment based on improved node contraction method. J. Tianjin Univ. (Sci. Technol.) 2018, 51, 1056–1064. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).